 Physical (that is, biometric device to secure a door)
Physical (that is, biometric device to secure a door)Access Control Methods and Models
Logical Access Control Methods
Physical Access Security Methods
The Security+ exam identifies their third domain as access control. This encompasses quite a few areas of Information Technology (IT) security knowledge and requires that you have a very solid understanding of what access control is, what the elements of access control are, and how it all works together. To cover all this material, we will be breaking it up into two sections. The first (covered in this chapter) is network access and all the elements associated with general network access control. The next chapter will be all about authentication. While we will absolutely be touching on authentication in this chapter, the next will be a “deeper dive” into all of the types of authentication mechanisms and how they work.
With that in mind, in this chapter, we’ll be going over general access control, industry best practices for access control, how access control works and is organized, and logical and physical access methods. All this will be done with an eye toward being as vendor agnostic as possible. There are some topics that are specific to one vendor or another, and where that is appropriate, it will be called out.
The Access Control portion of the Security+ exam counts for 17 percent of your overall score. That marks it as the third most critical portion of the exam. This should in no way diminish the importance of understanding access control and how to implement access control best practices. After all, if there is no access control, there is no point to network security.
When you are working with information security, the heart and soul of security is controlling access to objects. All other security measures and techniques are pointless if the objects they are meant to protect have no access controls. The Security+ exam requires that you know and understand access control as well as all the relationships between access control and other security concepts.
Gaining access to network resources is based on identifying yourself, proving that you are you, requesting access, and being granted the requested access. In this chapter, we will be covering some level of detail around authentication (with more detail in the following chapter) as well as covering the subject of access control in depth. We will also be delving into the concepts of identity versus authentication and their differences.
So what is access control? Access control encompasses the security controls, processes, or procedures whereby access to specific objects is either granted or denied based on preestablished policies or rules. Access control is made up of many different parts but at its roots it is a very simple concept. The goal of access control is to allow objects to be accessed by those authorized to access it (and limit the manner in which it is accessed) while denying access to those who are not authorized.
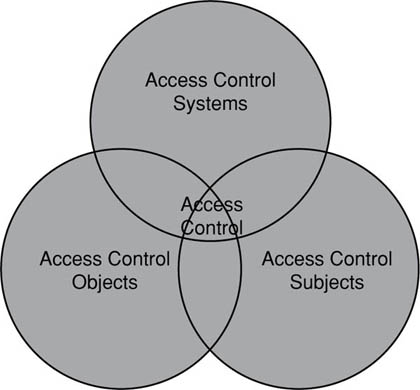
To understand access control, you must first break it down to its individual parts. First, there are the objects that need to be accessed. We refer to these objects as Access Control Objects as they are objects which need to have access to them controlled in some manner. By object, we are referring not only to data, but also to hardware devices, data networks, and even buildings. When working with information security, almost anything can be considered an access control object.
The next part of access control is Access Control Subjects. These are the users, programs, and processes which are requesting permission to access control objects. It is these access control subjects that must be identified, authenticated, and either granted or denied access to the access control objects.
The final part of access control is the procedures, processes, and controls in place to verify the authenticity of the request and the identity of the access control subject, and determine the levels of access that the subject should be granted to the object. These are called Access Control Systems and interface directly with the access control objects and access control subjects.
When all three parts of access control are combined, you have an overall security approach that determines what should be accessed by whom and at what level. It is upon this foundation that all information security is really based. A diagram of how all this ties together is shown in Figure 8.1.
Access control can be implemented in many different ways, all of which have the end result of controlling access to data, systems, or hardware.
 Physical (that is, biometric device to secure a door)
Physical (that is, biometric device to secure a door)
 Hardware (that is, a dedicated firewall)
Hardware (that is, a dedicated firewall)
 Software (that is, built-in application security)
Software (that is, built-in application security)
 Policy (that is, a workplace security policy)
Policy (that is, a workplace security policy)
 Network (that is, secure networking protocols)
Network (that is, secure networking protocols)
In this chapter, we will be going over the parts of access control and delving into how they work together. Different access control systems will be discussed as well as how they are implemented and how they operate.
Most access control systems are based on several basic access control models. These models define the operating parameters for the access control system and define the manner in which they operate. The access control model also defines the way that permissions are set on access control objects and how authorization is handled in the access control system.
There are several access control models that we are going to go over in this section. These are the major models that you’ll run into in the field and are the models you are expected to understand to pass the Security+ exam. Studying these models also gives you a good understanding of the basis for access control models in general and you should be able to understand the concepts behind any proprietary access control model quickly and easily.
Before we cover the individual access control models, there are some authoritative reference books on the subject of access controls that need to be mentioned. The first is the “Department of Defense Trusted Computer System Evaluation Criteria” book or the “Orange” book. It is called the Orange book based on the color of the spine in its printed form. This set of guidelines provides the necessary information necessary to classify the security rating of systems and define the degree of trust that they earn.
Using Orange book guidelines, there are four primary grades (A to D) with varying levels in each grade designated by a number. For example, some prior versions of Microsoft Windows can earn a C2 grade with the correct patches and hardening procedures performed. Table 8.1 shows the available grades and levels as well as some examples of systems earning each level.
There are several problems with the Orange book definitions that don’t work well with current information systems. First, the Orange book requires that the system be configured as stand alone. No network connectivity can be allowed. That really makes the system rather difficult to be practical. In addition, it can take anywhere from 1 to 2 years to certify a system. In this day of constant technology upgrades, that means that by the time a product is certified, it’s outdated. Also, any new patches, service packs, or changes to the product break the certification and require that the system get reevaluated. On top of this, applying for the certification is expensive.
There is an upgrade to the Orange book available called the “Red” book. Again, this is due to the spine color of its original printed form (known as the Rainbow series). The Red book is actually two separate books that work together to extend the Orange book’s guidelines to include network systems. The two books which make up the Red book are “Trusted Network Interpretation of the TCSEC” and “Trusted Network Interpretation Environments Guideline: Guidance for Applying the Trusted Network Interpretation.” I much prefer calling them the Red book, myself.
The Red book provides guidelines on how the concepts and guidelines from the Orange book can be applied to network environments. The guidelines within this book are as strict as the Orange book itself, but it is at least designed to work with networked environments.
The Orange and Red books were superseded in 2005 by the Common Criteria for IT Security Evaluation, also known as the Common Criteria (CC). This is an international standard (ISO 15408) for computer security which incorporates many of the requirements included in the Orange and Red books as well as the Information Technology Security Evaluation Criteria (ITSEC) European standard and Canadian Trusted Computer Product Evaluation Criteria (CTCPEC) from Canada. Using the CC, software and hardware can be certified at a variety of Evaluation Assurance Levels (EAL) similar to those available with the Orange and Red books. These levels range from EAL1 through EAL7. Using these criteria, Microsoft Windows Vista and Windows Server 2008 were graded as EAL1, the first level of certification.
With this information in mind, let’s move on to the access control models themselves.
The formal models of access control are theoretical applications of access control methods. These do not specify specific methods of controlling access but rather specific guidelines that should be followed. They work best with static environments and are difficult to implement within dynamic systems that are constantly changing such as those in most enterprise environments. The documentation on how these models are supposed to be implemented is very limited and does not give any specific examples.
However, the formal models do provide a good baseline to start from when designing access control systems. By ensuring that the guidelines within the formal model most closely related to your needs are followed, you ensure that you’ve got a strong foundation on which to build the rest of the access control system.
The Clark–Wilson formal model was written as a paper titled “A Comparison of Commercial and Military Computer Security Policies” for the IEEE Symposium on Research in Security and Privacy in 1987 and updated in 1989 by David D. Clark and David R. Wilson (http://theory.stanford.edu/~ninghui/courses/Fall03/papers/clark_wilson.pdf). This model is similar to Biba as it addresses integrity. The Clark–Wilson model is designed to not only address access to objects, but also to ensure integrity by specifying guidelines for processes which occur using the access control object.
One of the most important guidelines to come out of Clark–Wilson is that of segregation of duties or separation of duties. The principle of segregation of duty states no single person should perform a task from beginning to end but that the task should be divided among two or more people to prevent fraud by one person acting alone. This ensures the integrity of the access control object by securing the process used to create or modify the object.
David E. Bell and Len J. La Padula wrote the Bell–La Padula formal access control model in 1973 as a paper titled “Secure Computer Systems: Mathematical Foundations” for use in government and military applications (www.albany.edu/acc/courses/ia/classics/belllapadula1.pdf). This formal model specifies that all access control objects have a minimum security level assigned to it so that access control subjects with a security level lower than the security level of the objects are unable to access the object. Does this sound familiar? The Bell–La Padula formal model is what the mandatory access control (MAC) model is based on. MAC follows the guidelines of the Bell–La Padula formal model very closely, so if you understand MAC, you understand the Bell–La Padula formal model.
The Biba formal model was written as a paper titled “Integrity Considerations for Secure Computer Systems” by K.J. Biba in 1977 and is unique as it was the first formal model to address integrity. The Biba model bases its access control on levels of integrity. The Biba policy consists of three primary rules. The first rule specifies that a subject cannot access objects that have a lower level of integrity than the access control subject has. The second rule states that access control subjects cannot modify objects that have a higher level of integrity than their current integrity levels. The last rule specifies that an access control subject may not request services from subjects that have a higher integrity level.
Authentication is defined as a process through which specific information is proven and verified. It is through the process of authentication that any form of access information is verified to be true. In the physical world, this could be the keyway of a door lock verifying that the correct key has been inserted or that the correct fingerprint has been scanned. Authentication can occur with either the access control object or the access control subject and is controlled by the access control system. For example, when a user requests access to a file on a remote server, the access control system could require both the user and the remote server to be authenticated prior to allowing the user to access the file.
When you identify yourself to an access control system, you are effectively telling it who you are. This identification can come in a variety of forms and can be as simple as typing in your name or as complex as providing DNA for scanning purposes. We’ll cover identification in a little more detail later.
But just because you say you are someone doesn’t mean that you are telling the truth. The purpose of authentication is to ensure that the identity presented is accurate. Of course, the flip side of that is that the authentication process is responsible for ensuring that the person pretending to be you is found out before they are granted access to anything!
Authentication is basically the transfer of some form of information that proves that you are who you say you are. This can be in many different forms, but there are three basic types under which all the different forms of authentication fall.
 Something you know
Something you know
 Something you have
Something you have
 Something you are
Something you are
We will examine each of these and their advantages and disadvantages. In addition to these three primary types of authentication, there are also combinations of these types which are much more secure and difficult to crack. We will go through several of these combinations as well and discuss how they increase the overall security of the access control system.
The “something you know” authentication type basically relies on the access control subject to memorize and know specific facts that can be used to prove who they are. For example, this type of authentication includes passwords, personal identification numbers (PINs), facts about the subject’s life or family, code words, and so forth. All these require the subject to know a specific fact and respond with it when requested.
The most popular among these as it relates to IT security is a password. In a good access control system, passwords are required to gain access to any access control object. The advantage to passwords is that they are very common and easy to use. There are several different types of passwords and these are shown in Table 8.2.
For a password to be easy to remember, it must be something that the user can relate to and understand. Any combination of symbols, letters, and numbers will work for a password, but the more secure the password is in this manner, the easier it is for the user to forget. This leads to the problem where the user writes down his or her passwords. Going through a typical office building, more than 20 percent of the users will typically have their passwords written down somewhere in the vicinity of their computers. This is a major security problem and one that is battled at almost every office building in the world.
Based on this, the users typically choose their own password rather than having one randomly generated, and they generally make it a password that is easy for them to remember. Most users will use their birthdays, names, or favorite pet’s name, and so forth for their password as that makes it easy for them to remember. Unfortunately, this also makes their passwords fairly easy to guess.
A major disadvantage of password authentication comes into play after an intruder obtains the password in some manner. This type of authentication can be repudiated meaning that there is no proof that it is actually the password owner who is using the password. Using combinations of authentication types, which we will go over later in this section, typically solves this problem.
Because passwords are still something that must be used in current access control systems, there are several best practices that will help make the passwords as secure as possible. First, use words that are easy to remember (so it is not tempting to write them down) but are difficult to guess. In addition, replacing letters in the words with numbers or symbols will help by adding another layer of difficulty when trying to crack the password. Ensure that none of the following are used in the password:
Password Type |
Definition |
Cognitive |
Cognitive data that the user knows such as mother’s maiden name or favorite color |
Dynamic |
Passwords that change upon each consecutive login |
One Time |
Passwords that are only valid for a single use and are thereafter useless |
Passphrase |
A password based on a group of words or phrase |
Static |
A “normal” password which is only changed on request and remains the same otherwise |
 Names
Names
 Important dates
Important dates
 Phone numbers
Phone numbers
 Words (in any language) which could be found in a dictionary
Words (in any language) which could be found in a dictionary
 Simple words such as “password” or “computer”
Simple words such as “password” or “computer”
By following these recommendations, you will be able to create strong passwords that are difficult to crack and impossible to guess.
The “something you have” authentication type relies on some form of authentication that the access control subject physically has. This could be anything from a driver’s license to authenticate them as a valid driver of vehicles to an ATM card used to authenticate them to their bank. Several other examples of this type of authentication are as follows:
 Smart cards
Smart cards
 Proximity cards
Proximity cards
 Identification tokens
Identification tokens
 Keys
Keys
 Identification badges
Identification badges
 Passports
Passports
 Transponders
Transponders
All these are forms of identification that an access control subject would have to physically have available to be authenticated. They are also known as “physical tokens” because they represent a physical form of data which can be used for access control. If the access control subject doesn’t have the physical form of identification or token, they simply are not authenticated.
The security offered by this type of authentication has the disadvantage of being repudiated, similar to the “something you know” type of authentication. However, it does offer a few advantages. First of all, no one can guess or crack a physical form of identification. Second, since there is nothing to memorize, there is nothing for the user to write down and breach the security in this manner.
The disadvantage of this type of authentication is that the physical form of identification can be stolen. Because it can be repudiated, no one can prove that the person using it is actually the person who is authorized to do so. Also, some physical forms of authentication can be copied or cloned which can result with more than one person having a copy. Most secure physical forms of identification have controls in place which make them difficult to copy or clone, but with enough perseverance, it can be done.
The “something you are” authentication type is a relatively new type of authentication coming into the IT world. Although it has been around for several years, it is only now that this type of authentication is becoming affordable enough to be commonly implemented. This authentication type is known as biometrics and is based on the science of identifying people based on their physical characteristics.
The science of biometrics is based on the concept that while many people share common traits, there are certain traits that are unique to almost every individual on the planet. It is by detecting and measuring these traits that biometric authentication works. Some of these measurable traits that are commonly used for authentication are as follows:
 Fingerprints
Fingerprints
 Signatures
Signatures
 Eye characteristics
Eye characteristics
 Facial characteristics
Facial characteristics
 Voiceprints
Voiceprints
 DNA
DNA
All these traits are detectable, measurable, and generally unique to every individual. A biometric system is designed to scan for one or more of these traits and compare the measure of the trait being scanned against a database of prescanned measurements. By doing so, the biometric system is able to authenticate the access control subject if they are in the database of allowed subjects.
This system has many advantages over the other authentication types. No one can guess or crack a password, as there isn’t one. There is nothing that can be stolen or copied aside from actual body parts of the person being scanned. It is very difficult to duplicate any of the measured characteristics being used by the biometric system.
Biometric authentication does have some very serious disadvantages as well. The cost of biometrics is going down, but it is still the most expensive authentication type in use. The hardware and software necessary to provide accurate authentication is very expensive and difficult to maintain. In addition, as the biometric authentication is still relatively new to the field of information security, there are many learning curve problems to overcome with both the manufacturers and the administrators. An excellent example of this is the identification and response to false positives and false negatives. These are situations in which either the biometric scanner authenticates someone that should not have been or does not authenticate someone who should have been. Most administrators want to have a 0 percent false positive rate and the users want to have a 0 percent false negative rate. With most biometric hardware and software, this is an impossible goal so a middle ground must be met. This can be very difficult to do.
One of the greatest disadvantages to the biometric authentication type is that of privacy. Most people do not want to have information as private as their DNA sitting out in a computer database just so they can gain access to something. This is an understandable concern. In addition, with the facial characteristics recognition aspect of biometric authentication, there comes into play the possibility of your every movement or action being tracked remotely by camera. Many people consider this a paranoid point of view, but it is a valid privacy concern that many individuals have. These concerns must be addressed within any authentication type that is implemented. A good authentication type is completely useless if the end users refuse to make use of it.
Notes from the Field
The Dawn of Biometrics
We’re working in a very exciting time in the realm of information security. Biometric technology has been around for many years, but only now is it becoming reliable and affordable enough to be implemented as a common authentication method. Every few months, a new device comes out on the market using this technology to improve security. With this advanced technology in hand, we can do a great deal to increase system security while making obtaining access easier for our users.
The day is coming where a user will simply sit down at their desk and be identified by their smell and behavior through biometric devices. If the companies creating these devices can alleviate the privacy concerns that many people have about biometrics, there is no end to the uses of biometric technology.
These three basic types cover the main types of authentication. In addition, the three types of authentication can be combined to provide even greater security. These combinations are called factors of authentication. A two-factor authentication method would make use of two of the three types of authentication. Three-factor authentication uses all three types of authentication and is considered the strongest form of authentication.
Some examples of authentication type combinations are requiring that a PIN be entered in combination with a 6-digit code displayed on an authentication token or requiring a password, smart card, and fingerprint scan to enter a secure area. These combinations provide more security than any of the three authentication types can provide by themselves. By using these combinations, you can increase the security of an access control system and lower the risk caused by the disadvantages of the individual access control types.
There is a lot of confusion about the role identification plays in access control and how it differs from authentication. The Security+ exam requires that you understand identification and authentication as well as the differences between them.
Identification is basically the concept of saying that you are a specific access control subject. This process can be as simple as saying, “Hi, I’m Peaches Perry” or as complex as presenting a sample of your DNA for a biometric scan. Note that identification is just the act of presenting yourself as the access control subject, nothing more. It does not involve proving that you are who you say you are. That is where we get into authentication.
So the difference between identification and authentication is just proof. With identification, you are identifying yourself as a specific access control subject whereas with authentication, you take the next step and prove that you are the access control subject that you say you are. Both play an integral part in access control and you can’t have one without the other. However, they are two distinct terms that are not synonymous and the Security+ exam expects you to know that.
We have already covered some of the formal models used with access control, but there are concepts and derivatives of those formal models that require more in-depth analysis. In this section, we will be going over some of the key concepts associated with access control methods and models. Some of these directly relate to the formal models, so expect some repetition; however, the concepts themselves stand alone and can be implemented without implementing a full formal model.
The concept of implicit deny or deny by default is very common in the security industry. This concept basically says that if something is not explicitly allowed, it is denied. Most access control lists (ACLs) use this as the last processed rule to ensure that any access requests that fall outside the defined criteria are not allowed. In some cases, you have to manually add an implicit deny to the end of your access control list (ACL) in the event that this is not done automatically.
When specifying an implicit deny ACL, it may also be a good idea to log the incoming request. This will allow for future analysis to determine if additional ACL entries need to be defined to handle common requests which keep triggering the implicit deny rule. This log data can also be used as part of an intrusion detection/prevention system to find trends in the logged behavior to identify scans or intrusion attempts.
The first concept that we’ll go over is that of separation (or segregation) of duties. This is a very important security concept especially as it relates to fraud. We talked about this a little in the section covering the Clark–Wilson formal model. Separation of duties is the concept that no one person should handle a transaction from beginning to end. Instead, some parts of a transaction should be executed by one person, whereas other parts of the transaction should be executed by someone else entirely.
Let’s go over an example to illustrate why this is so important. Imagine an organizational structure at a small business such as a convenience store. Typically there will be a clerk who handles the day-to-day transactions at the register. There will also be a manager of some type who has different responsibilities. Some of the duties the clerk may be responsible for are stocking the shelves, selling products, and cleaning the store. The manager may be responsible for depositing the daily till into the bank, ordering products, and paying the clerk. With this separation of duties, each employee is responsible for specific tasks.
Now what if it were arranged differently? What if the clerk were responsible for all aspects of the purchasing transaction from beginning to end? They would order the products, stock them, sell them, and then deposit the money in the bank. That still isn’t a problem if the clerk is honest. However, if they’re not, there is no longer any protection against them stealing money, products, or both. The same argument could be made about the manager.
Separation of duties allows for a basic level of fraud prevention by providing some checks and balances organizationally. The same principle applies in many areas and is actually one of the basic tenets of the antitrust lawsuits, which are common for large organizations. When one entity controls too many portions of a transaction, there is increased risk that the transaction can be manipulated in the favor of the entity that has control over it. Separation of duties can help prevent this by establishing lines of segregation between elements of the transaction.
The principle of least privilege is very simple, but incredibly important. The concept here is to provide the lowest amount of access to an access control object necessary for the access control subject to perform their task. For example, if a developer needed to see log data on a system to troubleshoot a problem, you would grant them read-only access to the specific log files they need to see. You would not grant write access as this could allow them to remove log entries when they shouldn’t or overwrite the log file to hide the problem. You would also not grant access to files other than the log files as the other files may store data that the developer should not see.
This has the unfortunate side effect of causing the access control subject to have to go through the steps of requesting access to what they need every time their roles, or the tasks that they need to perform change. This is made more difficult by the fact that a typical end user may not know what they need access to in order to do their job. For example, they may request access to a specific file but not the directory containing other files that the first file is linked to.
This also applies to access across systems. For example, if you have a network printer set up and do not restrict access to the print resource, you can run into issues where large print jobs are mistakenly sent to the incorrect printer causing the actual users of that resource to be unable to use it. This basically means that by leaving access to the print resource unrestricted you have enabled a simple type of denial of service attack to be performed.
Consequently, there is often a balance struck here where the access control subject is granted access to the access control objects that they need now or may need in the foreseeable future. In general, you should always attempt to maintain the principle of least privilege by granting the access control subject the most appropriate access to the access control object possible.
Job rotation is the concept of personnel changing job roles at a scheduled time into a different role. There are several reasons behind this such as increasing education across the personnel, allowing for people to experience different parts of a company and how it functions, increased job satisfaction through change, and scheduled changes due to changes in leadership (terms in public offices). All these reasons lead to changing the job role for personnel and raise new security concerns because of it.
Going back to separation of duties, it might initially seem that job rotation violates this principle since personnel could be in roles which would allow them to perform a transaction end-to-end. What prevents this from being a concern is that each role in job rotation would only be held by a single individual at one time, not multiple roles at the same time. This adds more overhead from the access control perspective as the access control system must be able to handle shifts in job roles as well as ensuring that access permissions are changed rather than added to.
An example for this would be where a loan agent is scheduled to change roles as part of the company’s job rotation policy and take a position doing underwriting. When the agent prepares to change roles, they will probably put in an access request to be granted access to the files, systems, and privileges used by the underwriting group. If the person controlling the user’s access is not watchful, it could be possible that the additional underwriting access would be added to the user’s account without removing the loan agent access. This would inadvertently give the user permissions to both initiate a loan and approve it which would violate the principle of separation of duties.
It is important for you to be aware of job rotation and what its impacts to access control are. Be cognizant of how job rotation could lead to difficulties in ensuring that other security principles are adhered to. The Security+ exam expects you to understand these concepts and how they apply to access control.
MAC is based on sensitivity levels rather than ACLs on objects and is frequently used by government systems. In MAC, the security administrator gives every access control object and access control subject a sensitivity level and the object owner or system user cannot change this sensitivity level. Based on the sensitivity levels of the access control objects, the access control system decides how all data will be shared and the data are restricted to the access control subjects with the required matching sensitivity label. For example, if an object has a sensitivity label of top-secret, an access control subject with a label of secret will be unable to access the object.
The following example illustrates the level of control possible. When using MAC, if a file has a certain level of sensitivity (or context) set, the system will not allow certain users, programs, or administrators to perform operations on that file. Think of setting the file’s sensitivity higher than that of an e-mail program. You can read, write, and copy the file as desired, but without an access level of root, superuser, or administrator, you cannot e-mail the file to another system, because the e-mail program lacks clearance to manipulate the file’s level of access control. For example, this level of control is useful in the prevention of Trojan horse attacks, since you can set the access levels appropriately to each system process, thus severely limiting the ability of the Trojan horse to operate. The Trojan horse would have to have intimate knowledge of each of the levels of access defined on the system to compromise it or make the Trojan horse viable within it.
MAC is considered to be a more secure access control model than discretionary access control (DAC) as every subject and object must have a label assigned to it. This model ensures that if a subject is not authorized to access data with a specific sensitivity label, they will not be able to access it. This works well in a strictly defined hierarchy such as the military where subjects are simply not authorized to access any information that is above their level in the hierarchy.
Access control systems using MAC are able to gain an Orange Book B-level rating if the access control system meets all the criteria specified in the Orange book. Access control systems using DAC are unable to attain this level due to the additional security requirements which MAC fills.
The major disadvantage to MAC is that it is extremely difficult to implement. There is a great deal of administration involved, as every object must be assigned a sensitivity level by the administrator when it is created. It is also very difficult to program applications to work with MAC due to the way objects are created and used. For example, the guidelines for MAC require that any data or information with a sensitivity level higher than the object that the data are going to be placed in should be restricted from completing the operation. This logic is very difficult to work with when designing applications. In addition, whenever output is generated from the data in an object, the output media itself (print job, diskette, CD, and so forth) must be labeled with the same sensitivity level. This makes MAC very difficult to work with which is the primary reason that it is not implemented in most corporate environments. The total cost of ownership for MAC is not justified for most business purposes.
To review briefly, MAC is
 Nondiscretionary The control settings are hard-coded and not modifiable by the user or owner
Nondiscretionary The control settings are hard-coded and not modifiable by the user or owner
 Multilevel Control of access privileges is definable at multiple access levels
Multilevel Control of access privileges is definable at multiple access levels
 Label-based May be used to control access to objects in a database
Label-based May be used to control access to objects in a database
 Universally Applied Applied to all objects
Universally Applied Applied to all objects
The DAC model is the most common access control model in use. This model bases security on the identity of the access control subject. Every access control subject has specific permissions applied to it and based on these permissions has some level of authority.
This access control model is called discretionary because individual users or applications have the option of specifying access control requirements on specific access control objects that they own. In addition, the permission to change these access control requirements can also be delegated as a permission. As assigning access control permissions to the access control object is not mandatory, the access control model itself is considered discretionary. Basically, the owner of the access control object is allowed to decide how they want their data protected or shared.
Any system using DAC is considered Orange Book C-level at best. DAC is not eligible for A-level or B-level. The primary use of DAC is to keep specific access control objects restricted from users who are not authorized to access them. The system administrator or end user has complete control over how these permissions are assigned and can change them at will.
DAC allows for a distributed access control system to be used as the owner of the access control object has the ability to change the access control permission on objects without regard to a central authority. Also, centralized access control systems can be used with this as a single authoritative point of authorization with the permissions still being applied at the object level. The ability to use different types of access control systems with this model gives it a great deal of flexibility.
As previously mentioned, this is a very common access control model. It is used in UNIX, Windows, Novell NetWare, Linux, and many other network operating systems (NOSes). These systems use an ACL to set permissions on access control objects. These ACLs are basically a list of user IDs or groups with an associated permission level. Every access control object has an ACL, even if it is left at the default after the object is created. The operating systems vary in the way the permissions are defined in the ACL, but the Security+ exam is not vendor specific and does not require you to know how each operating system uses these. However, you are required to know the basic types of permissions that are defined. These are detailed in Table 8.3 along with a definition of what they mean.
EXAM WARNING While the Security+ exam is not vendor specific and takes a general perspective of information security, you do need to know how DAC works and that many common NOSes use DAC with ACLs as part of their access control security.
It is important to understand that DAC is assigned or controlled by the owner rather than being hard-coded into the system. DAC does not allow the fine level of control available with MAC but requires less coding and administration of individual files and resources.
To summarize, DAC is
 Discretionary Not hard-coded and not automatically applied by the OS/network operating system (NOS) or application
Discretionary Not hard-coded and not automatically applied by the OS/network operating system (NOS) or application
 Controllable Controlled by the owner of the object (file, folder, or other types)
Controllable Controlled by the owner of the object (file, folder, or other types)
 Transferable The owner may give control away
Transferable The owner may give control away
Almost all current NOSes allow administrators to define or set DAC settings. UNIX and Linux accomplish this either by way of a graphical user interface (GUI) or at a terminal window as the superuser creating changes to the settings using the chmod command. Windows operating systems set DAC values using Windows Explorer.
For this exercise, you will view the DAC settings in Windows Vista. To start, open Windows Explorer. Navigate to the %systemroot%\System32 folder (where %systemroot% is the folder Windows Vista is installed in). Highlight this folder’s name and select Properties. Select the Security tab; you should see a window as shown in Figure 8.2.
FIGURE 8.2
Viewing the DAC Settings on a Folder
Notice that the creator owner account is granted full control permission for this folder. Check the access settings for other users and groups that are defined on your machine. You should notice that the system has full control but that various other access settings are in place for different types of access permissions. Within the Windows OS, this is the area that allows you to control and modify the DAC settings for your resources.
Similar DAC settings are in place for all files and folders stored on New Technology File System (NTFS) partitions, as well as all objects that exist within Active Directory and all Registry keys.
A similar function is available in most other OSes. As mentioned, UNIX and Linux use the chmod process to control access through DAC. NetWare also has a file access system in place that is administered by the administrator (who has “Supervisor” rights).
RBAC can be described in different ways. The most familiar process is a comparison or illustration using the “groups” concept. In Windows, UNIX/Linux, and NetWare systems, the concept of groups is used to simplify the administration of access control permissions and settings. When creating the appropriate groupings, you have the ability to centralize the function of setting the access levels for various resources within the system. We have been taught that this is the way to simplify the general administration of resources within networks and local machines.
However, although the concept of RBAC is similar, it is not the exact same structure. With the use of groups, a general level of access based on a user or machine object grouping is created for the convenience of the administrator. However, when the group model is used, it does not allow for the true level of access that should be defined, and the entire membership of the group gets the same access. This can lead to unnecessary access being granted to some members of the group.
RBAC allows for a more granular and defined access level, without the generality that exists within the group environment. A role definition is developed and defined for each job in an organization, and access controls are based on that role. This allows for centralization of the access control function, with individuals or processes being classified into a role that is then allowed access to the network and to defined resources. This type of access control requires more development and cost but is superior to MAC in that it is flexible and able to be redefined more easily.
FIGURE 8.3
RBAC Inheritance
RBAC is easier to understand using an example. Assume that there is a user at a company whose role within the company requires access to specific shared resources on the network. Using groups, the user would be added to an existing group which has access to the resource and access would be granted. RBAC on the other hand would have you define the role of the user and then allow that specific role access to whatever resources are required. If the user gets a promotion and changes roles, changing their security permissions is as simple as assigning them to their new role. If they leave the company and are replaced, assigning the appropriate role to the new employee grants them access to exactly what they need to do their job without trying to determine all the appropriate groups that would be necessary without RBAC.
In addition, there is a hierarchy within RBAC whereby some roles can inherit permissions that are granted to another role. For an example, take a look at Figure 8.3.
Based on this illustration, you can see how roles can be inherited. In this example, the Office Assistant role has access to only the patient’s contact information. The Medical Doctor role has permission to view the patient’s medical records. However, since the Medical Doctor role inherits the permissions of the Office Assistant role, the patient’s contact information is accessible as well. The Medical Specialist has been explicitly granted access to all patient information and therefore has access not only to the contact information and medical records, but also anything else in the patient’s files.
In a good RBAC implementation, there is also the ability to block inheritance. There are instances where, for security reasons, you would want to limit privileges in the access control hierarchy. For example, in a banking situation, you would want to have someone in the Bank Teller role have access to balance out his or her register at the end of the day. In addition, you would want to have someone in the Floor Supervisor role to have access to verify that the teller’s balance matches the actual money shown in the final count. However, you really wouldn’t want the Floor Supervisor to be able to balance the register as well otherwise the organization would be open to fraud from a single person. This would be a violation of the principle of least privilege that we discussed earlier. You can combat this by blocking inheritance in the hierarchy.
TEST DAY TIP The best way to think of RBAC is to look at it like an organizational chart. Every person has a specific position and job function and the access control model mimics this organizational structure.
With RBAC, there is less administrative work than MAC as any objects created by a subject can be accessed by other subjects with the same role in the organization. This behavior can also be overridden in most access control systems using RBAC to increase security.
In summary, RBAC is
 Job Based The role is based on the functions performed by the user
Job Based The role is based on the functions performed by the user
 Highly Configurable Roles can be created and assigned as needed or as job functions change
Highly Configurable Roles can be created and assigned as needed or as job functions change
 More Flexible Than MAC MAC is based on very specific information, whereas RBAC is based on a user’s role in the company, which can vary greatly
More Flexible Than MAC MAC is based on very specific information, whereas RBAC is based on a user’s role in the company, which can vary greatly
 More Precise Than Groups RBAC allows the application of the principle of least privilege, granting the precise level of access required to perform a function
More Precise Than Groups RBAC allows the application of the principle of least privilege, granting the precise level of access required to perform a function
EXAM WARNING Be careful! RBAC has two different definitions in the Security+ exam. The first is defined as Role-Based Access Control. A second definition of RBAC that applies to control of (and access to) network devices is defined as Rule-Based Access Control. This consists of creating ACLs for those devices and configuring the rules for access to them.
When working with access control, it’s typically easiest to control access by groups of access control subjects instead of applying security on an individual level. These access control subjects would, of course, have to have some common factor which would allow them to be grouped together such as sharing a job role, working in the same department, or even being located in the same building. By applying access controls on groups of access control subjects, an administrator can make their job a little easier while still applying good security practices.
Because a company may have hundreds or thousands of users on a network or system, it would be an administrative nightmare to maintain access control over every single account. To make management easier, groups can be used to assemble user accounts together and define access control as a batch. For example, let’s say a network administrator wanted branch office managers to have the ability to backup data on servers and workstations in their individual locations. The administrator could modify the account of every manager, or add each of these accounts to a Backup Operators group, which has the necessary permissions to backup data. By modifying the access control of one group, the access of each account that is a member of that group would also be affected.
User accounts and groups may be local to a computer or server or have the ability to connect to servers on a network. This allows administrators to control what a user or group can do on a specific machine or on the network as a whole. This is particularly useful when they want users to have different levels of access on individual machines and the network.
Network OSes like Novell NetWare also have the ability to control access through roles. Roles are similar to groups, as they can be used to control the access of numerous users as a batch. If a number of users have a similar role in an organization, the administrator can associate them with a role created on the network OS. The role would have specific access to resources such as drive mappings or other privileges unique to this role. For example, department managers might have similar duties in an organization and wish to access a shared directory for storing data that all the managers would need. You could create a role and associate each of the manager’s accounts with this role. When the managers log-in, they would have the same access to the shared directory and any other privileges provided through the role.
EXAM WARNING Remember that users should only receive the minimum amount of access to perform their jobs. If users receive more than this, they can accidentally or intentionally cause damage to systems and data. This is especially true if users are added to administrator groups, which give them complete access and control over everything.
Security controls refer to the access control mechanisms that we put into place to mitigate security risks. There are three levels of security controls that are typically put into place:
 Preventative
Preventative
 Detective
Detective
 Corrective
Corrective
Each of these refers to the time frame around access control breaches. Preventative security controls are there to prevent a security breach. These would be the controls put into place to authenticate users or control their access to resources.
Detective security controls are intended to detect when a security breach happens and get details on the breach. This can be as simple as a log showing a failed log-on attempt due to an incorrect password or as complex as a network intrusion detection system. The key factor for this security control is all about detecting a problem.
The last level of security controls is corrective controls. These types of controls are put into place to fix a problem after it has occurred and has been detected. Going with the previous example, a corrective control for failed authentication attempts would be to lock an account to prevent further attempts until the lock is cleared. This could also be a network intrusion prevention system where not only are issues detected, but action is taken to stop the intrusion.
Implementing security controls is part of what every security professional does on a daily basis, but you need to be aware of this specific terminology for the Security+ exam. You should also be able to categorize different activities into the appropriate levels of security controls.
Despite the emphasis on group-based access permissions, a much higher level of security can be attained in all operating platforms by individually assigning access permissions. Administratively, however, it is difficult to justify the expense and time involved in tracking, creating, and verifying individual access permissions for thousands of users trying to access thousands of individual resources. RBAC is a method that can be used to accomplish the goal of achieving the status of least privileged access. It requires more design and effort to start the implementation but develops a much higher level of control than does the use of groups.
Good practice indicates that the default permissions allowed in most OS environments are designed for convenience, not security. For this reason, it is important to be diligent in removing and restructuring these permissions. Applying important security concepts such as the principle of least privilege to file resources can help to prevent users from gaining access to data that they should not have as well as ensuring the integrity of the data.
From the perspective of organization, some general guidelines can be used to group access to specific file resources together to aid in easier administration. Most functional areas in an organization need to share files within that functional area. Consequently, any file resources used in this shared area should be secured to provide access to those people in that area and only those people. For example, you wouldn’t want people in the human resource department to access files in the finance department.
Typically, there will also be a need to share some data across the entire organization or across specific business units. The same logic applies; grant access to those groups of file resources to the people who need it and deny access to those who don’t.
The organization of print resources is often forgotten from a security perspective. Print devices may not be considered critical to most organizations, but they are important and incorrectly applying access controls to print resources can cause problems. For example, if print resources are inadequately secured, they can be hijacked and used to obtain a great deal of information about an organization. In addition to external risks, internal problems can occur due to incorrectly secured or assigned print resources. Imagine the issues that could arise when the human resource department goes to print some salary information and the print job goes to the wrong printer.
Print resources can be organized by a few different criteria, again in the interest of making administration easier. Some of the most common methods are to organize based on physical location, functional area, or job role. Sometimes a combination of all three is used to provide for more precise access controls. Regardless of the grouping used to organize the application of security to print resources, you should be cognizant of the issues that can arise with poor security as it relates to print resources and be able to describe how to adequately secure and organize these access control objects.
Access control can be broken up into two primary methods, logical and physical. In this section, we will be going over logical access control methods and we’ll cover physical access control a little later. Logical access control involves applying access controls to logical entities such as data or the ability to perform a certain action on a computer. This differs from physical access control methods in that physical access control deals with limiting the ability to physically interact with an entity.
Logical access control involves a lot of the concepts that we’ve already gone over as well as a few others that we’ll discuss in detail. Most IT security professionals focus a great deal of time and effort around implementing security on logical entities so that it tends to be the primary focus of most security exams including the Security+ exam.
ACLs are lists of permissions associated with access control objects. Access control subjects are listed in the ACL as well as the level of permission that the subject is granted to the object. For example, an ACL for a file named “test.txt” could have the user ID “JEREMY” listed with an access level of “read” as well as a separate entry for “CHRISTINA” with an access level of “read/write.” This would give “JEREMY” the ability to read the file, but not write to it, whereas “CHRISTINA” could perform both actions.
This is all part of the DAC model as ACLs are enforced on a discretionary basis rather than being mandated by the operating system. As previously mentioned, MAC requires the definition of sensitivity levels on the access control subjects and objects to define the access level to be granted. ACLs make no use of sensitivity levels of the access control subjects and basically provide access in the exact manner defined through the rules laid out in the ACL. Another feature of ACLs is that it is possible to grant an ACL rule, which allows the access control subject to modify the ACL for the object.
ACLs can typically be associated with single files, full directories, disks, ports, or any other type of access control object based on the capabilities of the access control system. There is also typically an implicit deny associated with ACLs to prevent access from being granted to access control subjects when they fall outside the defined criteria.
Group policies are a feature of the Microsoft Active Directory technology that allows for logical access control based on groupings of access control subjects. The access control subjects are organized by site, organizational unit (OU), or domain. After you group the access control subjects, a Group Policy Object (GPO) can be defined. A GPO controls many elements of a user’s system access, including Registry settings, auditing, software installation, and Internet Explorer settings. This GPO is created as a template that can then be applied to the groups previously defined.
When a user is authenticated and granted access to a Windows workstation, the GPOs applicable to that user are pulled from the authenticating server and applied. In addition, the workstation will poll for new GPOs assigned to the user on a regular basis using a random delay between the ranges of 90 and 120 min. Any changes found between the previously applied GPOs and the new GPOs will be applied to the workstation at that time.
Windows Vista further expanded the functionality available with GPOs by allowing a more granular level of control over the system Registry using ADMX files. This newer format for performing Registry-level changes increases the flexibility and power of the GPOs for user workstations.
Domain policies are GPOs that are defined at the domain level within Microsoft Active Directory. GPOs, once defined, can be linked to Sites, Domains, or Organizational Units (OUs). The GPOs defined at each of these levels as well as locally are always applied in the following order:
1. Local
2. Site
3. Domain
4. OU
GPOs at each level are applied with each having the ability to overwrite the previous GPO unless forced otherwise. This allows for setting specific security policies such as password expiration and required password length at the domain level overriding conflicting settings at the local level.
Inheritance plays a very important role in the use of GPOs within Windows environments. While GPOs are applied in the order listed above, there are options available to make exceptions. These are the “Block Policy Inheritance” and “No Override/Enforced” options. “Block Policy Inheritance” prevents the GPOs at higher levels (such as Domains) from being inherited by lower levels. The “No Override” option has recently been renamed to “Enforce” and prevents lower levels from overriding higher level settings.
In the order of precedence, “Enforce” wins over “Block Inheritance.” This means that if you set up a GPO at the domain level requiring a 14-character password and have the “Enforce” parameter set, it cannot be overridden at the OU level with an eight-character password requirement.
Another form of logical access control is use of Time of Day restrictions. This is often used in the home environment to ensure that children are unable to use a computer outside their allowed hours, but it actually began in corporate environments. Similar to the way a time-lock safe works, time of day restrictions prevent specific applications or systems from being used outside of specific hours. Some situations where this can be useful would be to restrict the size of a print job allowed to be processed during working hours or to prevent a bank teller workstation from being accessed after the bank is closed.
Both these situations are valid, but from the security perspective, the second is probably more applicable. Time of day restrictions can also apply at the data level wherein you may want to ensure that a batch process can only access a file containing sensitive data after a process has run which masks elements of that data. Regardless of the reasoning, restricting access to logical entities to specific time frames can be useful to IT security personnel.
When you are dealing with access control, the most common task is granting access to access control objects. The second most common is removing access. This can be required due to a variety of reasons including account revocation, changes in roles, and account expiration.
Often it makes sense for an account to only be valid for a specific duration. For example, an account might only be active for a contractor for the duration of their contract. Or an account allowing remote system access might only be valid during the term of a support contract. In cases such as this, it is logical to specify a specific duration of validity to access that has been granted and automatically revoke that access when the duration expires. Of course, the option is always there to extend the expiration date if needed.
Logical tokens are basically strings of values that can be used in lieu of a password to gain access to access control subjects. This concept allows for systems external to the client and server to be responsible for authenticating the user and then to pass along a token indicating that the user has been authenticated to the system which then authorizes access to the access control object. This mechanism is familiar to most security professionals as it is the method used by Kerberos to authenticate users. Kerberos will be discussed in detail in the next chapter.
Most frequently, logical tokens are used to prevent passwords from being sent directly from an access control subject to the access control system. Instead, the password is sent to a third party and a token issued in return which takes the place of a password when the access control subject then uses the access control system.
When working with logical tokens, there are a few requirements that must be met in order for this mechanism to be effective. First, there must be a trusted third party who authenticates the access control subject and provides the token. This third party must be trusted by both the access control subject and the access control system responsible for the access control object(s) in question.
Next, there must be a method defined by the third party for creating tokens, which allows for the access control system being issued the token to validate its authenticity. This can be done by decrypting the token using a previously shared key, revalidating the token with the third-party system, or some other similar technique.
Lastly, there must be a set of policies in place that determine important things such as how long a token is valid and how it can be revoked. With these policies in place, there are rules defining the use of the tokens, and they can then be applied to improve the security of the processes associated with the logical tokens.
When people consider computer and network security, the focus revolves around accounts, passwords, file permissions, and software that limits and monitors access. However, even though a user’s account has been denied access to files on a server, what is to stop that user from opening files directly at the server instead? Worse yet, what is to prevent them from stealing the server’s hard disk? Issues like these are why physical security is so important to the protection of data and equipment.
Physical security involves protecting systems from bodily contact. It requires controlling access to hardware and software so that people are unable to damage devices and the data they contain. If people are unable to have physical access to systems, they will not be able to steal or damage equipment. Physical security also limits or prevents their ability to access data directly from a machine or create additional security threats by changing account or configuration settings.
Physical security also requires protecting systems from the environmental conditions within a business. Environmental conditions such as floods, fires, electrical storms, and other natural disasters can result in serious losses to a business. These conditions can also leave a business exposed to situations such as power outages, leakage of data due to poor shielding, and other potential threats. Without strong physical security in place, unauthorized persons can access information in a variety of ways. When designing physical security, the first step is to identify what needs to be protected and what it needs to be protected from. Inventories should be made of servers, workstations, network connectivity devices, and other equipment within an organization.
Not all equipment is at risk from the same threats. For example, a workstation at a receptionist’s desk is vulnerable to members of the public who may be able to view what is on the monitor or access data when the receptionist steps away. Equipment is also vulnerable to accidental or malicious damage, such as when a user or visitor accidentally knocks a computer off a desk or spills something on a keyboard. A server locked in the server room would not be subject to the same type of threats as the receptionist’s workstation, since access to the room is limited to members of the IT staff. Because the level of risk varies between assets and locations, risks must be evaluated for each individual device.
When designing security, it is important to strike a balance between the cost of security and the potential loss—you do not want to pay more for security than the equipment and data are worth. Servers are costly and may contain valuable data, so a higher level of security is needed to protect them. On the other hand, an old computer in the Human Resources department that is used for keyboarding tests given to prospective employees needs little or no protection.
When determining value, it is important to not only consider the actual cost of something, but how difficult it is to replace or what the cost to the organization’s credibility would be. Although certain data may be of relatively low cost value, it may still be important to a company and difficult to replace. For example, a writer may have the only copy of a book on his hard disk. Because it has not been published, the actual value of the book is minimal, and the cost of creating the book is limited to the time it took the writer to type the material. However, if the hard disk crashed and the book was lost, it would be difficult to replace the entire book. Even if the writer rewrote the book, it would be unlikely that the new version would be identical to the original. By determining the difficulty in replacing data, you are better able to determine its nonmonetary or potential value.
Losses to credibility are even more difficult to quantify. For example, imagine that a listing of 10 credit card numbers is stolen from your company. Assuming that only $500 in purchases went through on each card before they were deactivated for fraud, there would sum a total of $5,000 in losses. However, the loss to your company’s credibility would be immense if the loss were made public. Hundreds of current or potential customers may choose not to use your company due to a lack of trust. Consequently, all the potential transactions of those customers must be taken into account to determine the full impact of the loss.
Another point to remember is that equipment is often devalued yearly for tax purposes, making it seem that the equipment has no worth after a certain time period. If this is the only measurement of worth, security may be overlooked in certain areas, because the equipment does not seem to have any reasonable value. However, older systems may be vital to an organization, because they are used for important functions. For example, a small airport may use older systems for air traffic control such as takeoffs, landings, and flying patterns of aircraft. Because these older systems are essential to normal operations, they are more valuable than a new Web server that hosts a site with directions to the airport. When determining value, you must look at the importance of the equipment as well as its current monetary value.
When creating measures to protect systems, it is important to note that threats are not limited to people outside the company. One of the greatest challenges to physical security is protecting systems from people within an organization. Corporate theft is a major problem for businesses, because employees have easy access to equipment, data, and other assets. Because an employee’s job may require working with computers and other devices, there is also the possibility that equipment may be damaged accidentally or intentionally. Physical security must not only protect equipment and data from outside parties, but also those within a company.
A good way to protect servers and critical systems is to place them in a centralized location. Rather than keeping servers in closets throughout a building, it is common for organizations to keep servers, network connectivity devices, and critical systems in a single room. Equipment that cannot be stored in a centralized location should still be kept in secure locations. Servers, secondary routers, switches, and other equipment should be stored in cabinets, closets, or rooms that are locked, have limited access, are air-conditioned, and have other protective measures in place to safeguard equipment.
Test Day Tip
Reviewing Physical Security
Even if the physical security of a location is suitable when a server was installed, it may not be at a later date. In an office environment, people will move to different offices, renovations will be made to facilities, and equipment will be moved. Even though a server was initially placed in a secure location, the server could be moved or the location could become insecure as changes are made.
Unfortunately, many of the decision makers in a company may be unaware of the importance of physical security for network equipment and make changes without considering implications. In a large organization where much of the network administration is done remotely, IT staff may be unaware that such changes have even occurred. For example, in one organization, I saw numerous problems with physical security. During construction to a reception area, the server was moved from a closet behind the reception desk area to the center of an unlocked room. Another server closet became a catchall area and would be unlocked to allow people to store equipment, office supplies, and their coats and boots in the winter. When renovations occurred at another location, the server was moved to a closet in a washroom area. This would have been bad enough, except that it was later designated a public washroom, and employees who accessed the closet would occasionally forget to lock it. Perhaps even worse, when an architecture firm was hired to evaluate the facility problems and determine what was needed in a new or renovated facility, they appeared to ignore the specifications made by IT staff and forgot to include a server room and any locations for network equipment. This happened not just once, but twice.
The cold, hard fact is that (unless there’s a problem) few people care about the physical security of a server and other network equipment, so it is up to IT staff to perform reviews. Part of the indifference lies in advertising of “zero administration” and heightened security in operating systems (OSes), leading some people to believe that the need for network administration and physical security has lessened. Another contributing factor is that most people have computers and even home networks, so they consider themselves peers to the expertise of IT staff and feel they can effectively make these decisions that ultimately compromise security. To help with these problems, policies should also be created that include strict measures against those who compromise physical security.
However, while curbing these mindsets can be frustrating, the only people-problem that IT staff can immediately fix is with themselves. Because so much work can be done remotely, the physical presence of IT staff visiting an off-site location is generally minimal. If a server is moved, or the physical security of where it is located is compromised, IT staff won’t notice the problem until long after it has occurred. It is important for routine reviews to be made of assets like servers and other network equipment, inclusive to their locations in an organization, and whether they are physically secure.
Access lists are basically preauthorized lists of people who are allowed to enter an area. Think of it as similar to the list of celebrities that a bouncer will let in to a private party. Only the specific people on the list will be allowed entry. Just like most elements of access control, the visitor must first prove his/her identity using some form of identification to be allowed in assuming that they are not recognized by sight. This is not a very secure manner of controlling access to buildings as it is not a very complicated process to fabricate a false identification card. All a potential intruder would need to know is the name of someone who is likely to be on the list and fabricate an ID to match.
Access logs require anyone entering a secure area to sign in before entering. When visitors require entry, such as when consultants or vendor support staff need to perform work in a secure room, an employee of the firm must sign the person in. In doing so, the employee vouches for the credibility of the visitor and takes responsibility for this person’s actions. The access log also serves as a record of who entered certain areas of a building. Entries in the log can show the name of a visitor, the time this person entered and left a location, who signed them in, and the stated purpose of the visit.
Even after a visitor has been given access to an area, a member of the organization should accompany him/her whenever possible. Doing so ensures that the visitor stays in the areas where they are permitted. It also provides a measure of control to ensure that the visitor does not tamper with systems or data while they are there.
One of the easiest methods of securing equipment is the simplest: keep it behind a locked door. There are a variety of different locks that can be used. Some locks require metal keys to open them, much like those used to unlock the front door of a home. Other types may be programmed and have keypads requiring a PIN or card key to open them. With these more advanced locks, features may be available that allow logging of anyone who enters the area, which is useful for monitoring who entered a secure area at a particular time.
If unable to store servers or other equipment in a dedicated server room, consider storing them in a locked closet, rack, or cabinet. By locking the equipment up, employees and visitors to a site will not be able to access it without authorization.
If equipment is stored in a centralized server room or a locked closet, it is important that all sides of the room or closet are secure. Windows should be locked and alarmed, if possible, so that anyone climbing through will be stopped or detected. Air vents can also provide a route into a room, so any large vents should be bolted shut with grates. Even seemingly obscure routes should be blocked or secured. Intruders may be able to crawl into a room through the area between a false ceiling and the real ceiling or the space between a raised floor and the concrete beneath. Thus, walls surrounding the room should be extended to reach the real ceiling. Even walls may not provide real security, when you consider that someone could break through weak drywall to enter a “secure” area. If the need for security justifies the cost, vault rooms constructed of concrete, metal, or other materials that are difficult to penetrate can be built. In more common situations, the server room can be positioned beside other secure areas or in areas that use cinder blocks or bricks for walls. When designing a physical security plan, make sure that the walls, ceiling, and floor are secure.
TEST DAY TIP Remember that physical security includes all sides of a room, the walls, ceiling, and floor. Even if most of these are secure, leaving one side of the room insecure can provide an avenue of penetration. Looking at the room this way will also help to identify where security lapses exist and what security measures should be implemented.
ID badges are identification cards issued to individuals who need access to a specific location. These badges will often include a photograph of the individual as well as other identifying information such as their name or a badge number. They may also include a magnetic strip or a radio frequency identification (RFID) tag, which allows for storage of additional data or identification that the badge is genuine.
There may be policies in place at a company that requires ID badges to be worn at all times when on the premises. This is one manner of ensuring that only authorized individuals are onsite at the facility. Anyone without an ID badge could potentially be an intruder and quickly identified due to the lack of the identifying badge.
There are, of course, some challenges with relying solely on ID badges for security at a site. If the ID badges do not include a photo, they can easily be stolen and used by unauthorized personnel. In addition, there are logistics that must be considered when implementing an ID badge system such as ensuring that a process exists for visitors with no badge, handling of stolen or lost badges, and temporary badges for personnel who forget their badge. Badges with no magnetic strip or imbedded chip for identification can be easily forged, and even those with these features can be duplicated with a little effort.
That’s not to say that ID badges are a bad idea or should not be used. Just be aware that your physical access control mechanism should not rely on ID badges alone. You should always plan on having multiple layers of security around critical or confidential systems and information. ID badges may be one element of that security plan and should be considered any time that physical access to a premises is being restricted.
Door access systems have increased in complexity from simple locks to complex systems that perform elements of access control such as authentication and logging of entry/exit. With the increased complexity comes increased security as well as increased management needs. It is no longer a matter of just duplicating keys and handing them out. Management of door access systems now includes having to detail out how a person (access control subject) is going to identify himself/herself, how to authenticate them, and how to authorize their access to the room or building in question (access control object).
These door access systems come in two major types, stand-alone or centrally managed. Stand-alone door access systems typically have a small imbedded electronic system built into them which allows the administrator to set up all the rules of access control such as who has access to the door during which time periods. A stand-alone door access system is only concerned with the one door that it has to protect and does not share data with any other door access systems. As soon as you increase the number of door access systems to two or more, the complexity of managing these stand-alone systems becomes increasingly difficult. At that point, you must either manually maintain synchronization between the systems or set different rules for each (also manually).
The solution to this is to use a centralized door access system. With this type of system, a central computer is responsible for performing the access control necessary across multiple door access systems. This allows for simpler centralized administration of the door access systems but has its own drawbacks. In the event of a failure of the centralized system, it is possible that multiple door access systems will stop working correctly. Some systems work around this by maintaining a copy of the centralized server’s rules in the memory of each local door access system so that if the central system fails, they can continue functioning using the last update they received until the problem is corrected. This works well from the perspective of keeping things running, but can be a security problem as revoked IDs will still work on systems with cached data until they receive a new rule set from the central server.
Even with the most stringent physical security in place, there are ways of bypassing these methods and gaining access. One of the simplest methods is tailgating, or piggybacking, in which an unauthorized person follows an authorized person into a secure area. Regardless of whether a person has to use a key, PIN, card key, biometrics, or other methods to open a door and enter, all a second person needs to do is follow him or her through the door. Even if the first person notices the security breach, he may feel uncomfortable challenging the person who’s tailgating, and not bother asking the person to provide identification, get out, or go back and use his own key or access to enter.
Intruders piggybacking on another person’s access can be a real security challenge, because any existing security measures are rendered useless even though they’re functioning properly. It is especially common if the authorized person knows the tailgater, such as when management, a coworker, or others who are visually recognized are piggybacking. It’s common to see one person use a key card to enter a building and several others follow their way in. However, even in these cases, you cannot be 100 percent sure that one of them has been dismissed from the company, under a disciplinary action (such as suspension), or is a contractor whose contract has ended. Even if the person legitimately works for the company, allowing them to piggyback their way into a server room could result in equipment being knocked over, sensitive documents (such as administrator passwords) being seen, or other problems.
Human nature can cause significant problems for any security measures you put in place, and there is no easy way of dealing with it. Policies can be implemented that prohibit allowing anyone to enter an area unless they have used their own security access method (that is, key, access card, PIN, and so forth), with procedures on what to do if someone does sneak in behind a person (such as challenging the person to produce ID, notifying security personnel, and so forth). However, most employees are neither trained nor willing to confront or physically remove a person from the premises, so often, the policy may be ignored for personal safety reasons or because it is emotionally uncomfortable. After all, no one wants to ask their boss to get out of the building or room because they snuck in the door.
This makes education one of the best methods of combating the problem. Employees should be educated that tailgating is a security issue, that policies exist that make a person responsible for those permitted access, and that allowing an unauthorized person access could result in disciplinary actions (including termination of employment). Although this won’t completely eliminate tailgating, it will limit the number of people who attempt or allow security breaches.
A mantrap in a security context is basically a method used for physically trapping a person if they fail to be properly authenticated. It often takes the form of a small room with two doors. After gaining entry through the first door, there are specific criteria which must be met for the second door to open. The first of these is typically that the first door is closed. This prevents the person entering the mantrap from leaving if they fail to pass the other criteria necessary to enter the second door.
The other criteria are all based on the authentication mechanisms in use for the facility and can include entry of a code, biometric verification, physical recognition, or any combination of these. Failure to authenticate would lead to the person attempting to gain entry being stuck in the mantrap until released. Typically, some sort of alarm is associated with authentication failures so as to ensure that security personnel are aware that someone has been isolated in the mantrap.
Chaperoning someone who has been given clearance to an area is not always possible or desirable. For example, if you have hired an outside party to install equipment that is needed for Internet access, you may not want to stand beside the installer for an extended period of time. However, workers can be monitored in high security locations using video cameras to provide electronic surveillance. This provides a constant eye and allows for review of their actions if an incident occurs.
In this chapter, we looked at a number of topics covered in the access control domain of the Security+ exam. The objectives we have covered are all critical to your understanding of IT security in general and especially as they relate to this exam. By understanding each concept, you will have a strong foundation in the areas of network access that you will be tested on.
As we looked at access control, we found that there were three distinct parts of access control: access control objects, access control subjects, and access control systems. The combination of these three parts gives us access control. This access control can be implemented using a number of different access control models and can be graded by older criteria such as the Orange book or new criteria such as the CC. Among these models are the Clark–Wilson, Bell–La Padula, and Biba formal models.
We also talked about authentication models and how authentication works. Authentication differs from identification by the simple mechanism of proof. Presenting proof by one of the authentication types such as something you know, something you have, or something you are establishes that you are authenticating versus simply identifying yourself. Remember, of course, that each type of proof is considered a factor of authentication and can be combined to create a multifactor authentication type.
When going over access control methods and models, we covered some very important concepts that really apply to every task in the security industry. The ideas behind implicit denial, separation of duties, principle of least privilege, and job rotation all play a part in increasing security or reducing risks in a secure environment. We also talked about mandatory, discretionary, and role-based access control with a focus on how they differ. Each applies in its own place and this is something you should be highly aware of.
Access control is easiest to apply if the access control subjects or objects are organized in some way. This can be done using things like security groups for users or security controls around file and print resources. Any type of organization can decrease the administrative effort necessary to secure resources, but it should always be noted that if a grouping is too generic, it is difficult to get granular enough on the security permissions assigned to the groups. There must be a careful balance between ease of administration and granularity of control.
When going over logical access control methods, we discussed how ACLs work and how DACs such as ACLs differ from MAC. We also spent some time discussing some Microsoft Active Directory-specific features, specifically group and domain policies. Remember that there is a hierarchical order of application for GPOs, and naturally, there are exceptions to always keep in mind. Other types of logical access control methods include time of day restrictions, account expiration, and logical tokens. Each of these plays a role in access control and you should understand how each works.
Lastly, we went over the often forgotten part of IT security, physical access. There are different ways to justify the design and costs of physical security, but in general, the same rules apply to physical security as they do to any other security design. The cost isn’t just the amount of money stolen but the loss to credibility, loss of corporate secrets, and breach of trust to the company’s clients. To that end, using things such as access lists and logs, hardware locks, ID badges, door access systems, mantraps, and video surveillance can all help to increase the physical security of your site.
All these items that we’ve gone over have an effect on the access control that you as a security professional are responsible for. Always keep in mind the best practices that we’ve discussed, not only when taking the Security+ exam, but also in the real world. It is part of our role as security professionals to do everything we can to maintain the integrity, confidentiality, and availability of the systems that we are responsible for. Following best practices such as these and maintaining a secure environment is a big part of fulfilling that responsibility.
 Access control is comprised of access control subjects, objects, and systems.
Access control is comprised of access control subjects, objects, and systems.
 Some access control formal models include Clark–Wilson, Bell–La Padula, and Biba.
Some access control formal models include Clark–Wilson, Bell–La Padula, and Biba.
 Authentication means presenting proof in the form of something you know, something you have, or something you are (or a combination of these).
Authentication means presenting proof in the form of something you know, something you have, or something you are (or a combination of these).
 The difference between identification and authentication is that of proof.
The difference between identification and authentication is that of proof.
 Implicit deny, separation of duties, the principle of least privilege, and job rotation are all methods of access control that can improve security and reduce risk.
Implicit deny, separation of duties, the principle of least privilege, and job rotation are all methods of access control that can improve security and reduce risk.
 MAC is nondiscretionary, multilevel, label-based, and universally applied.
MAC is nondiscretionary, multilevel, label-based, and universally applied.
 DAC is discretionary, controllable, and transferable.
DAC is discretionary, controllable, and transferable.
 Role-based access control is job-based, highly configurable, more flexible than MAC, and more precise than groups.
Role-based access control is job-based, highly configurable, more flexible than MAC, and more precise than groups.
 Security groups are ways to organize access control subjects into logical groups to make security administration easier.
Security groups are ways to organize access control subjects into logical groups to make security administration easier.
 Security controls are access control mechanisms that mitigate security risks and can be preventative, detective, or corrective.
Security controls are access control mechanisms that mitigate security risks and can be preventative, detective, or corrective.
 Grouping of file and print resources (access control subjects) can also be done to ease the efforts of administration.
Grouping of file and print resources (access control subjects) can also be done to ease the efforts of administration.
 ACLs are part of DAC and list permissions for access control subjects.
ACLs are part of DAC and list permissions for access control subjects.
 Group policies and domain policies are elements of Microsoft Active Directory that allow for security rules to be enforced on access control subjects in a logical manner.
Group policies and domain policies are elements of Microsoft Active Directory that allow for security rules to be enforced on access control subjects in a logical manner.
 Other logical access controls include time of day restrictions, account expiration, and logical tokens.
Other logical access controls include time of day restrictions, account expiration, and logical tokens.
 Logical tokens are strings of values which are used in lieu of a password to gain access to access control objects.
Logical tokens are strings of values which are used in lieu of a password to gain access to access control objects.
 Physical security is very important but is very expensive often requiring cost justification based on loss estimations including loss of products, money, credibility, corporate secrets, and trust.
Physical security is very important but is very expensive often requiring cost justification based on loss estimations including loss of products, money, credibility, corporate secrets, and trust.
 Physical security should be continually reviewed to ensure that it is current and effective.
Physical security should be continually reviewed to ensure that it is current and effective.
 Access lists and logs, hardware locks, ID badges, door access systems, mantraps, and video surveillance are all elements of physical access security.
Access lists and logs, hardware locks, ID badges, door access systems, mantraps, and video surveillance are all elements of physical access security.
Q: What is the difference between access controls and authentication? They seem to be the same.
A: Access controls set the condition for opening the resource. This could be the time of day, where the connection originates, or any number of conditions. Authentication verifies that the entity requesting the access is verifiable and who the entity is claiming to be.
Q: I am implementing an access control system using biometrics. Is biometrics reliable enough to use or should I combine this with something else?
A: Biometric authentication is fairly reliable, but it is still best to combine this with some other form of identification from the user. It is typical in most biometric installations to use a combination of the biometric data and a password or PIN. This would give you a multifactor access control system.
Q: Why are password policies important in an access control system? It would be a lot easier to just tell the users to pick passwords that are difficult to guess.
A: Unfortunately, to maintain a secure system, you cannot rely on the users to know what a secure password is or use one. By implementing an access control policy, you ensure that passwords are more secure and improve the overall security of the access control system.
Q: When working with accounts, at what point should the account be deleted?
A: Accounts should only be deleted if there are no data associated with the a ccount that needs to be retained, no database records are tied to the account, and there is no need for a new person to fill the position previously occupied by the original user. Typically, it is best to just disable accounts, but deletions can and should be done occasionally based on these criteria.
Q: I ran a test against my access control system using a dictionary/brute force password cracker and most of the passwords were compromised within a few minutes. What should I do?
A: You need to change your access control policy to require more secure passwords. For the passwords to be compromised that quickly, the passwords had to be very simple or contain common words. Implementing a better access control policy can help alleviate this risk.
Q: The idea of RBACs seems very complicated. Wouldn’t it be easier just to use groups?
A: Easier, yes. More secure, no! RBACs allow much finer control over which users get access. This is backward from the conventional teaching that had us use the groups to ease administrative effort.
Q: When using DAC, what is the best way to apply permissions so that data are protected but users can still perform their job functions?
A: Always use the principle of least privilege. Apply the permissions at the lowest level in the directory hierarchy possible and allow the users to access the data at that point. It is always a good idea to restrict access to the minimum necessary to do a job.
Q: When separating duties, shouldn’t a manager have access to do anything their employee can do?
A: In some cases, yes, when the roles permit it. In other cases, no. If the employee has the responsibility of entering a transaction, and the manager has the responsibility of approving it, the manager should probably not be able to enter the transaction. This prevents a single person from performing an entire transaction from start to finish, which can reduce the possibility of fraud. It does make things more complex from a business perspective, but depending on the criticality of the tasks can mitigate a lot of risk.
Q: Why isn’t MAC used more frequently than DAC if it’s more secure?
A: Mainly because it’s very difficult to design and administer. When using MAC, sensitivity levels must be assigned to every access control object with similar labels on every access control subject. This makes a system very secure if implemented correctly, but takes a lot of time and effort to administer. In most cases, the administration and implementation costs are considered to be more than the value of the additional security.
Q: Putting file and print resources into groups seems to make them a lot easier to manage. Is this a good idea?
A: It often makes sense to group certain file and print resources together. In some cases, you can group all printers on a floor together and simply allow all users on that floor to have access to that group. Where you run into trouble is when you then have to change that due to specific requirements. For example, if there is one group on the floor who purchased a color laser printer and they don’t want other users printing there due to the cost of supplies, you now have to change your security to group those users together and isolate access to that printer to those users. This type of thing happens a lot, but there is still benefit to be found in grouping resources because it really does cut down on the amount of administrative overhead versus managing each object individually.
Q: When defining an ACL, why should I include an implicit deny at the end? Won’t the DAC using the ACL do that automatically?
A: Most DAC systems do an implicit deny by default, but it is not guaranteed. It is always best to add the implicit deny just to be 100 percent certain that requests falling outside the rules in the ACL are denied. This also makes the ACL more clear to others who look over it in the future to troubleshoot problems.
Q: When working with domain policies, why is the local policy applied before any other policy?
A: There are multiple reasons for this. One is so that there can be a default policy set applied if the system is unable to access the network to get GPOs. Another is so that changes to the local security policy can be overridden by GPOs defined by the administrator in the event that they have been changed by the user to be less restrictive.
Q: When using logical tokens, what prevents a token from being hijacked and used by an unauthorized user?
A: This is typically a part of the design of the access control system using logical tokens. In most cases, tokens only have a short time to live and it is difficult to replay them before they expire. In others, a sequence number is incorporated into the token and if the tokens are sent with the wrong sequence number they fail. The mechanisms differ based on the access control system, but there should always be some sort of mechanism to prevent token reply. This is, of course, something you should ensure before using a token-based system.
Q: If access logs are being kept for a facility, should those be made available to the IT security personnel?
A: This depends on the circumstances and the policies of the company. In most organizations, the IT security group is responsible for gathering information in the event of a security breach. This may or may not include physical access logs. Often, there is a facilities group that has the same charge in the physical security realm and each group may individually supply data to a legal group or auditor who processes it.
Q: I don’t understand why IT security professionals should care about physical security. Isn’t that someone else’s job?
A: In a lot of cases, yes, someone else is responsible for physical security. But consider a situation where IT assets or data are stolen due to a breach in physical security. If the group who handles the physical security was not properly advised or informed about what asset or data were being stored in that location, it could be considered a failure on the IT security side. Our role is to protect the systems and data that we’re responsible for and that protection should extend outside the logical realm when necessary.
1. When you are using DAC systems with ACLs, what permission or privilege gives users the ability to read and write to an access control object?
A. Write
B. Create
C. Execute
D. Modify
2. When you are using MAC, how is permission to access control objects controlled after a user has been authenticated?
A. By ACLs
B. By sensitivity levels
C. By identification
D. By user role
3. How does role-based access control differ from DAC?
A. Role-based access control requires that permissions be configured on every object and DAC does not
B. Role-based access control uses the ID of the user to help determine permissions to objects and DAC does not
C. Role-based access control uses the position of the user in the organization structure to determine permissions for objects and DAC does not
D. Role-based access control requires that every object have a sensitivity label and DAC requires that every object have an ACL
4. The Bell–La Padula formal model for access control is most similar to which access control model?
A. DAC
B. MAC
C. Role-Based Access Control
D. Clark–Wilson Access Control
5. The Clark–Wilson formal access control model specifies a very important guideline related to account administration. What is this guideline and what does it mean?
A. Principle of least privilege Grant all the rights and permissions necessary to an account, but no more than what is needed.
B. Account administration Work hand-in-hand with the human resources or personnel office of the company to ensure that accounts can be authorized and created when employees are hired and immediately destroyed when they are dismissed.
C. Segregation of duties No single person should perform a task from beginning to end, but the task should be divided among two or more people to prevent fraud by one person acting alone.
D. Access control Provide access control subjects the ability to work with access control objects in a controlled manner.
6. When you are performing account administration, the principle of least privilege is an important guideline to apply. Why is this principle so important?
A. Applying the principle of least privilege ensures that permissions are broken up based on job functions which can prevent fraud
B. Applying the principle of least privilege ensures that an access control policy is in place which can increase security by requiring frequent password changes
C. Applying the principle of least privilege ensures that users are guaranteed a minimum level of access to the access control objects that they need to work with which provides assurance in the form of availability
D. Applying the principle of least privilege ensures that users do not have more permission to an access control object than is necessary which can prevent users from accessing more than they should
7. When you are administering access control objects in a MAC system, what is an important part of an administrator’s duty?
A. Declassifying data when necessary
B. Removing ACLs when necessary
C. Deleting inactive accounts regularly
D. Replacing expired access control tokens when necessary
8. You have been brought in as a security consultant for a programming team working on a new operating system designed strictly for use in secure government environments. Part of your role is to help define the security requirements for the operating system and to instruct the programmers in the best security methods to use for specific functions of the operating system. What method of access control is most appropriate for implementation as it relates to the security of the operating system itself?
A. MAC
B. DAC
C. RBAC
D. All of the above
9. You are designing the access control methodology for a company implementing an entirely new IT infrastructure. This company has several hundred employees, each with a specific job function. The company wants their access control methodology to be as secure as possible due to recent compromises within their previous infrastructure. Which access control methodology would you use and why?
A. RBAC because it is job-based and more flexible than MAC
B. RBAC because it is user-based and easier to administer
C. Groups because they are job-based and very precise
D. Groups because they are highly configurable and more flexible than MAC
10. You have been brought in to analyze the overall security strength of a banking organization. As part of your analysis, you work with the existing security administrator to see what issues she has to deal with on a daily basis. She receives a help desk ticket stating that a teller issued a credit to his own account then authorized the credit so that he was able to prevent bouncing a check. According to the human resources department who called in the ticket, he said that he planned on removing the credit later after he got paid. The security administrator made a change to the security policies around one of the following areas. If she analyzed the issue correctly, which area did she change the policy for?
A. System logging to capture events similar to this in the future
B. Separation of duties to prevent a teller from issuing and authorizing a credit
C. System scanning to test other areas of the software for vulnerabilities similar to this
D. Log analysis to ensure that future events like this are flagged for follow-up.
11. Both identification and authentication play a role in access control. When analyzing a security infrastructure, you are tasked with documenting which elements of their security fall into identification versus authentication. Which option below correctly identifies these elements?
A. Identification: ID Badge, PIN, User ID
B. Identification: Fingerprint, User ID, Password
C. Authentication: Password, PIN, Visual ID Verification
D. Authentication: PIN, Fingerprint, Password
12. You are consulting for a small organization which does retail services. As part of your role, you must outline a security infrastructure and justify its cost to executives. Your biggest concern is around the lack of security in their point of sale system. Because credit cards are used for transactions in the point of sale system and it can be easily compromised, how would you justify the cost of an upgrade to executives?
A. Note the merits of the new system including how much faster it can process transactions, how much easier it is to integrate with other systems, and its support for faster hardware
B. Show what can happen with a real-time demonstration of how easily their current system can be compromised
C. Present the merits of enterprise security and design a full enterprise architecture with appropriate intrusion, detection, and access controls to work around the limitations of the existing point of sale system
D. Present an analysis of the pros and cons of upgrading including the potential cost of lost credibility in the event that the existing system is compromised
13. You are working on an existing Windows Active Directory implementation. A problem has been identified where users are able to keep their passwords for 90 days instead of the company mandated 30-day policy. You’ve looked at the GPO defined at the domain level and the password expiration is set for 30 days. What could be the problem?
A. A policy at the OU level is setting the expiration for 90 days
B. A policy at the site level is setting the expiration for 90 days
C. A policy at the local level is setting the expiration for 90 days
D. A policy at the domain level is set for “Enforce”
14. When implementing a security infrastructure in an organization, you are tasked with designing their ACLs. Specifically, you must define how some firewall rules are set up. What principle or method would you want to make sure to include in your design?
A. Separation of duties
B. Principle of least privilege
C. Implicit deny
D. Block inheritance
15. You are working with an access control mechanism which uses logical tokens to validate user access requests. When a user presents his ID and token to the secured resource, he is granted access, but it is read-only rather than the read-write access he was expecting. Where should you look first for the cause?
A. Have the user confirm that he is using the right password
B. Ensure that the third-party authentication service is working properly
C. Check the security permissions on the access control object
D. Check to see if the token has been revoked
1. D
2. B
3. C
4. B
5. C
6. D
7. A
8. A
9. A
10. B
11. C
12. D
13. A
14. C
15. C