Chapter 1
Networking Today
Objectives
Upon completion of this chapter, you will be able to answer the following questions:
How do networks affect our daily lives?
How are host and network devices used?
What are network representations, and how are they used in network topologies?
What are the characteristics of common types of networks?
How do LANs and WANs interconnect to the internet?
What are the four basic requirements of a reliable network?
How do trends such as BYOD, online collaboration, video, and cloud computing change the way we interact?
What are some basic security threats and solutions for all networks?
What employment opportunities are available in the networking field?
Key Terms
This chapter uses the following key terms. You can find the definitions in the glossary at the end of the book.
small office and home office (SOHO) networks page 12
local-area networks (LANs) page 13
wide-area networks (WANs) page 13
internet service provider (ISP) page 17
digital subscriber line (DSL) page 18
dialup telephone connection page 19
converged data network page 21
fault-tolerant network page 24
quality of service (QoS) page 25
Introduction (1.0)
Congratulations! This chapter starts you on your path to a successful career in information technology by giving you a foundational understanding of the creation, operation, and maintenance of networks. As a bonus, you get to dive into networking simulations using Packet Tracer. We promise you will really enjoy it!
Networks Affect Our Lives (1.1)
Networks are all around us. They provide us with a way to communicate and share information and resources with individuals in the same location or around the world. Networks require an extensive array of technologies and procedures that can readily adapt to varying conditions and requirements.
Networks Connect Us (1.1.1)
Among all of the essentials for human existence, the need to interact with others ranks just below our need to sustain life. Communication is almost as important to us as our reliance on air, water, food, and shelter.
In today’s world, through the use of networks, we are connected as never before. People with ideas can communicate instantly with others to make those ideas reality. News events and discoveries are known worldwide in seconds. Individuals can even connect and play games with friends physically separated by oceans and continents.
Video—The Cisco Networking Academy Learning Experience (1.1.2)

World changers aren’t born. They are made. Since 1997 Cisco Networking Academy has been working toward a single goal: educating and building the skills of the next generation of talent required for the digital economy. Refer to the online course to view this video.
No Boundaries (1.1.3)
Advancements in networking technologies are perhaps the most significant changes in the world today. They are helping to create a world in which national borders, geographic distances, and physical limitations become less relevant and present ever-diminishing obstacles.
The internet has changed the manner in which our social, commercial, political, and personal interactions occur. The immediate nature of communications over the internet encourages the creation of global communities. Global communities allow for social interaction that is independent of location or time zone.
The creation of online communities for the exchange of ideas and information has the potential to increase productivity opportunities around the globe.
The cloud lets us store documents and pictures and access them anywhere, anytime. So whether we are on a train, in a park, or standing on top of a mountain, we can seamlessly access our cloud-stored data and applications on any device.
Network Components (1.2)
Many different components are required to enable a network to provide services and resources. These various components work together to ensure that resources are delivered in an efficient manner to those requiring the services.
Host Roles (1.2.1)
If you want to be part of a global online community, your computer, tablet, or smartphone must first be connected to a network. That network must be connected to the internet. This section discusses the parts of a network. See if you recognize these components in your own home or school network!
Any computer that is connected to a network and that participates directly in network communication is classified as a host. Hosts can be called end devices. Some hosts are also called clients. However, the term host specifically refers to a device on a network that is assigned a number for communication purposes. This number, which identifies the host within the particular network, is called the Internet Protocol (IP) address. An IP address identifies the host and the network to which the host is attached.
Servers are computers with software that allows them to provide information, such as email or web pages, to other end devices on the network. Each service requires separate server software. For example, a server requires web server software in order to provide web services to the network. A computer with server software can simultaneously provide services to many different clients.
As mentioned earlier, a client is a type of host. Clients have software for requesting and displaying the information obtained from the server, as shown in Figure 1-1.
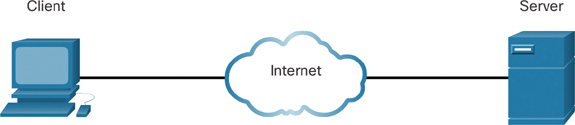
Figure 1-1 A Client and a Server
An example of client software is a web browser, such as Chrome or Firefox. A single computer can also run multiple types of client software. For example, a user can check email and view a web page while instant messaging and listening to an audio stream. Table 1-1 lists three common types of server software.
Table 1-1 Common Server Software
Software Type |
Description |
An email server runs email server software. Clients use mail client software, such as Microsoft Outlook, to access email on the server. |
|
Web |
A web server runs web server software. Clients use browser software, such as Windows Internet Explorer, to access web pages on the server. |
File |
A file server stores corporate and user files in a central location. The client devices access these files with client software such as Windows File Explorer. |
Peer-to-Peer (1.2.2)
Client and server software usually run on separate computers, but it is also possible for one computer to be used for both roles at the same time. In small businesses and homes, many computers function as both servers and clients on the network. This type of network, called a peer-to-peer network, is shown in Figure 1-2.
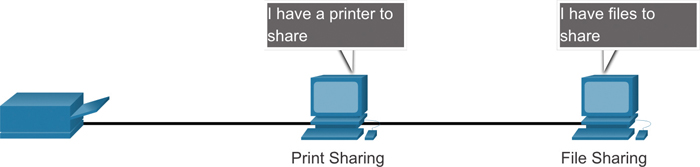
Figure 1-2 Peer-to-Peer Network
Table 1-2 outlines the advantages and disadvantages of peer-to-peer networking.
Table 1-2 Peer-to-Peer Networking Advantages and Disadvantages
Advantages |
Disadvantages |
Easy to set up |
No centralized administration |
Less complex |
Not as secure |
Lower cost because network devices and dedicated servers may not be required |
Not scalable |
Can be used for simple tasks such as transferring files and sharing printers |
All devices may act as both clients and servers, which can slow their performance |
End Devices (1.2.3)
The network devices that people are most familiar with are end devices. To distinguish one end device from another, each end device on a network has an address. When an end device initiates communication, it uses the address of the destination end device to specify where to deliver the message.
An end device is either the source or destination of a message transmitted over the network, as shown in Figure 1-3.
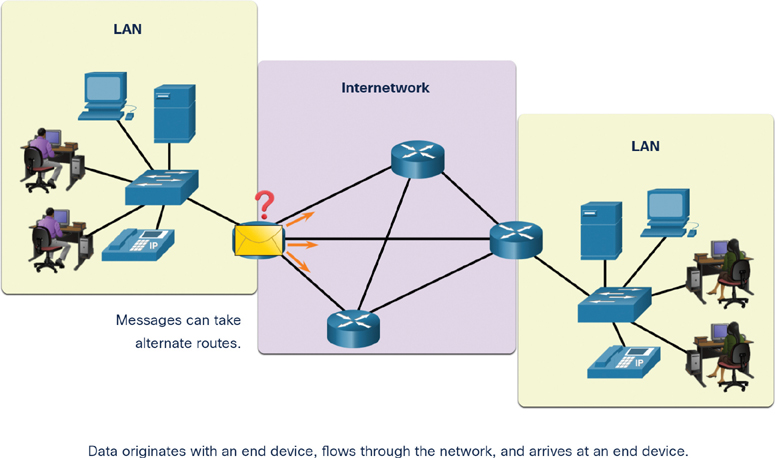
Figure 1-3 Data Flow Through a Network
Intermediary Devices (1.2.4)
Intermediary devices connect individual end devices to a network. They can connect multiple individual networks to form an internetwork. These intermediary devices provide connectivity and ensure that data flows across the network.
Intermediary devices use the destination end device address, in conjunction with information about the network interconnections, to determine the path that messages should take through the network. Figure 1-4 shows examples of the most common intermediary devices.
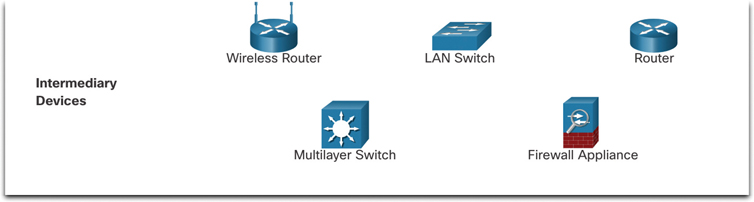
Figure 1-4 Intermediary Devices
Intermediary network devices perform some or all of these functions:
Regenerate and retransmit communication signals
Maintain information about what pathways exist through the network and internetwork
Notify other devices about errors and communication failures
Direct data along alternate pathways when there is a link failure
Classify and direct messages according to priorities
Permit or deny the flow of data, based on security settings
Note
Figure 1-4 does not show any legacy Ethernet hubs. An Ethernet hub is also known as a multiport repeater. Repeaters regenerate and retransmit communication signals. Notice that every intermediary device performs the function of a repeater.
Network Media (1.2.5)
Communication transmits across a network on media. The media provide the channel over which a message travels from source to destination.
Modern networks primarily use three types of media to interconnect devices, as shown in Figure 1-5:
Metal wires within cables: Data is encoded into electrical impulses.
Glass or plastic fibers within cables (fiber-optic cable): Data is encoded into pulses of light.
Wireless transmission: Data is encoded via modulation of specific frequencies of electromagnetic waves.
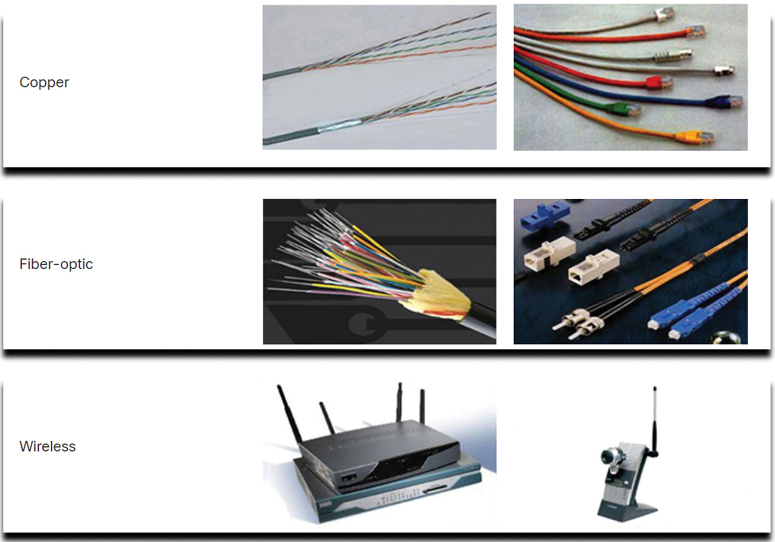
Figure 1-5 Network Media
Different types of network media have different features and benefits. Not all network media have the same characteristics, and they are not all appropriate for the same purpose.
Check Your Understanding—Network Components (1.2.6)

Refer to the online course to complete this activity.
Network Representations and Topologies (1.3)
A network’s infrastructure is documented using commonly used symbols to represent devices and different types of diagrams to represent the interconnection of these devices in the network. Understanding these symbols and diagrams is an important aspect of understanding network communications.
Network Representations (1.3.1)
Network architects and administrators must be able to show what their networks look like. They need to be able to easily see which components connect to other components, where they are located, and how they are connected. Diagrams of networks often use symbols, like those shown in Figure 1-6, to represent the different devices and connections in a network.

Figure 1-6 Network Symbols for Topology Diagrams
A diagram provides an easy way to understand how devices connect in a network. This type of “picture” of a network is known as a topology diagram. The ability to recognize the logical representations of the physical networking components is critical to being able to visualize the organization and operation of a network.
In addition to these representations, specialized terminology is used to describe how each of these devices and media connect to each other:
Network interface card (NIC): A NIC physically connects an end device to a network.
Physical port: A port is a connector or an outlet on a networking device where a medium connects to an end device or another networking device.
Interface: An interface is a specialized port on a networking device that connects to a network. Because routers connect networks, the ports on a router are referred to as network interfaces.
Note
Often, the terms port and interface are used interchangeably.
Topology Diagrams (1.3.2)
Topology diagrams are mandatory documentation for anyone working with a network. Such a diagram provides a visual map of how the network is connected. There are two types of topology diagrams: physical and logical.
Physical Topology Diagrams
A physical topology diagram illustrates the physical locations of intermediary devices and cable installation, as shown in Figure 1-7. You can see that the rooms in which these devices are located are labeled in this physical topology.
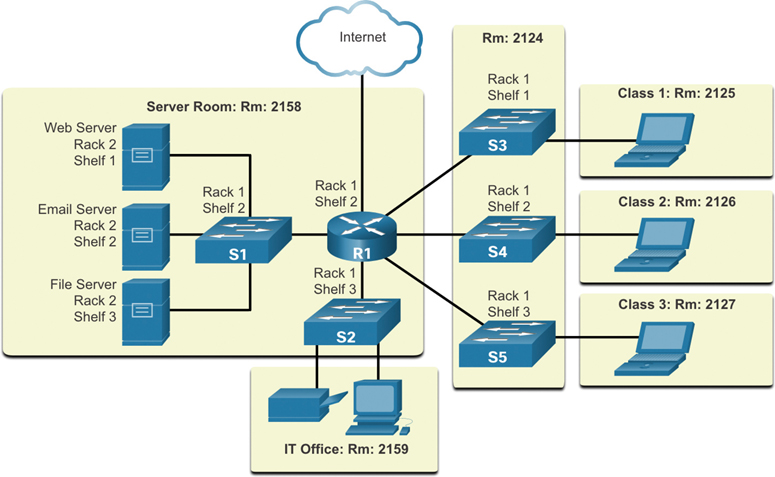
Figure 1-7 Physical Topology Example
Logical Topology Diagrams
A logical topology diagram illustrates devices, ports, and the addressing scheme of a network, as shown in Figure 1-8. You can see which end devices are connected to which intermediary devices and what media are being used.
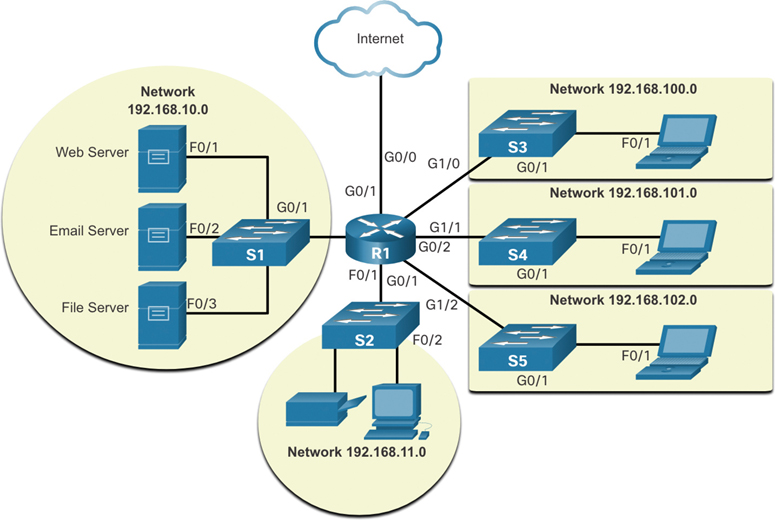
Figure 1-8 Logical Topology Example
The topologies shown in physical and logical diagrams are appropriate for your level of understanding at this point in the course. Search the internet for “network topology diagrams” to see some more complex examples. If you add the word “Cisco” to your search phrase, you will find many topologies using icons that are similar to what you have seen in these figures.
Check Your Understanding—Network Representations and Topologies (1.3.3)

Refer to the online course to complete this activity.
Common Types of Networks (1.4)
Networks can be categorized in various ways, including by size, by location, or by function. No matter the type of network being discussed, the underlying principles apply to all types of networks.
Networks of Many Sizes (1.4.1)
Now that you are familiar with the components that make up networks and their representations in physical and logical topologies, you are ready to learn about the many different types of networks.
Networks come in all sizes. They range from simple networks consisting of two computers to networks connecting millions of devices.
Simple home networks let you share resources, such as printers, documents, pictures, and music, among a few local end devices.
Small office and home office (SOHO) networks allow people to work from home or a remote office. Many self-employed workers use these types of networks to advertise and sell products, order supplies, and communicate with customers.
Businesses and large organizations use networks to provide consolidation, storage, and access to information on network servers. Networks provide email, instant messaging, and collaboration among employees. Many organizations use a network connection to the internet to provide products and services to customers.
The internet is the largest network in existence. In fact, the term internet means a “network of networks.” The internet is a collection of interconnected private and public networks.
In small businesses and homes, many computers function as both servers and clients on the network. This type of network is called a peer-to-peer network. There are networks of varying sizes that can be categorized in various ways, including the following:
Small home networks: Small home networks connect a few computers to each other and to the internet.
SOHO networks: A SOHO network allows computers in a home office or a remote office to connect to a corporate network or access centralized, shared resources.
Medium to large networks: Medium to large networks, such as those used by corporations and schools, can have many locations with hundreds or thousands of interconnected hosts.
Worldwide networks: The internet is a network of networks that connects hundreds of millions of computers worldwide.
LANs and WANs (1.4.2)
Network infrastructures vary greatly in terms of
Size of the area covered
Number of users connected
Number and types of services available
Area of responsibility
The two most common types of network infrastructures are local-area networks (LANs) and wide-area networks (WANs). A LAN is a network infrastructure that provides access to users and end devices in a small geographic area. A LAN is typically used in a department within an enterprise, a home, or a small business network. A WAN is a network infrastructure that provides access to other networks over a wide geographic area, which is typically owned and managed by a larger corporation or a telecommunications service provider. Figure 1-9 shows LANs connected to a WAN.
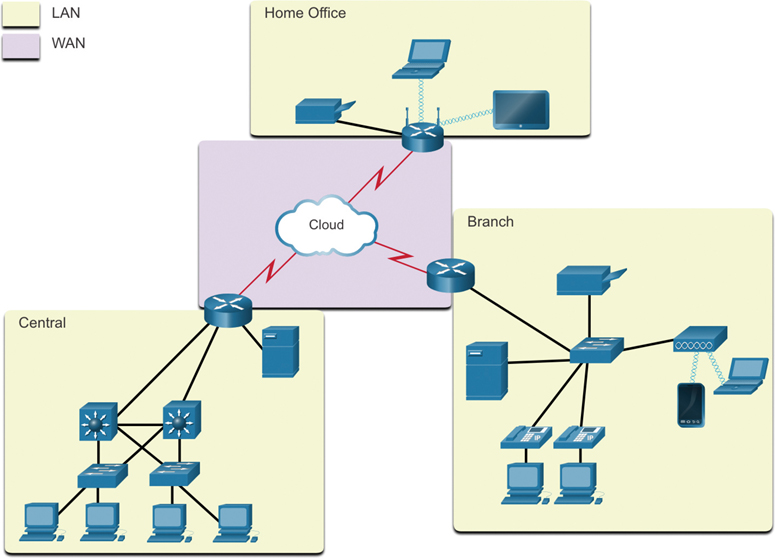
Figure 1-9 Example of Connected LANs and WANs
LANs
A LAN is a network infrastructure that spans a small geographic area. LANs have specific characteristics:
LANs interconnect end devices in a limited area such as a home, school, office building, or campus.
A LAN is usually administered by a single organization or individual. Administrative control is enforced at the network level and governs the security and access control policies.
LANs provide high-speed bandwidth to internal end devices and intermediary devices, as shown Figure 1-10.
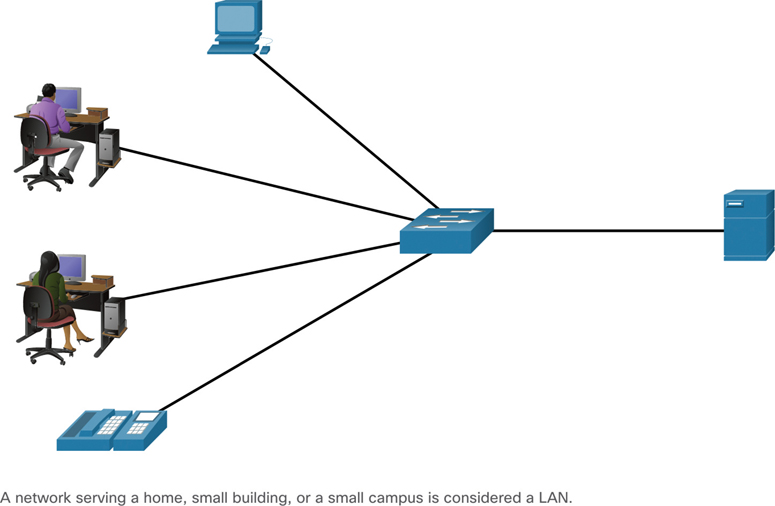
Figure 1-10 Example of a LAN
WANs
Figure 1-11 shows a WAN that interconnects two LANs. A WAN is a network infrastructure that spans a wide geographic area. WANs are typically managed by service providers (SPs) or internet service providers (ISPs).
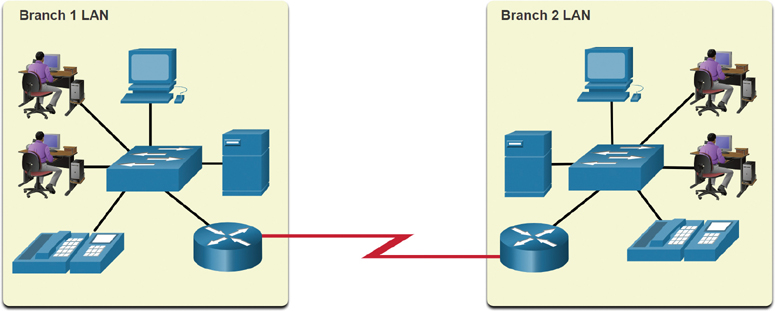
Figure 1-11 Example of a WAN Link
WANs have specific characteristics:
WANs interconnect LANs over wide geographic areas such as between cities, states, provinces, countries, or continents.
WANs are usually administered by multiple service providers.
WANs typically provide slower-speed links between LANs.
The Internet (1.4.3)
The internet is a worldwide collection of interconnected networks (internetworks, or internet for short). Figure 1-12 shows one way to view the internet as a collection of interconnected LANs and WANs.
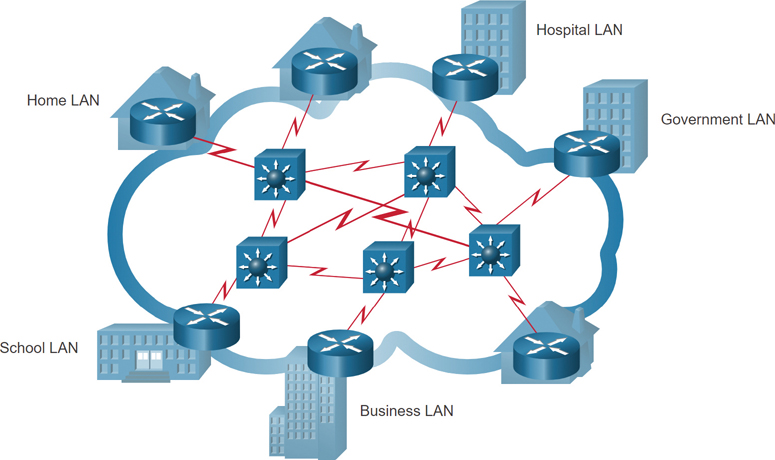
Figure 1-12 Example of a View of the Internet
Some of the LAN examples in Figure 1-12 are connected to each other through a WAN connection. WANs are then connected to each other. The WAN connection lines (which look like lightning bolts) represent the varieties of ways we connect networks. WANs can connect through copper wires, fiber-optic cables, and wireless transmissions (not shown).
The internet is not owned by any individual or group. Ensuring effective communication across this diverse infrastructure requires the application of consistent and commonly recognized technologies and standards as well as the cooperation of many network administration agencies. Organizations have been developed to help maintain the structure and standardization of internet protocols and processes. These organizations include the Internet Engineering Task Force (IETF), Internet Corporation for Assigned Names and Numbers (ICANN), and the Internet Architecture Board (IAB), among many others.
Intranets and Extranets (1.4.4)
Two other terms are similar to the term internet: intranet and extranet.
The term intranet is often used to refer to a private connection of LANs and WANs that belongs to an organization. An intranet is designed to be accessible only by the organization’s members, employees, or others with authorization.
An organization may use an extranet to provide secure and safe access to individuals who work for a different organization but require access to the organization’s data. Here are some examples of extranets:
A company that is providing access to outside suppliers and contractors
A hospital that is providing a booking system to doctors so they can make appointments for their patients
A local education office that is providing budget and personnel information to the schools in its district
Figure 1-13 illustrates the levels of access that different groups have to a company intranet, a company extranet, and the internet.
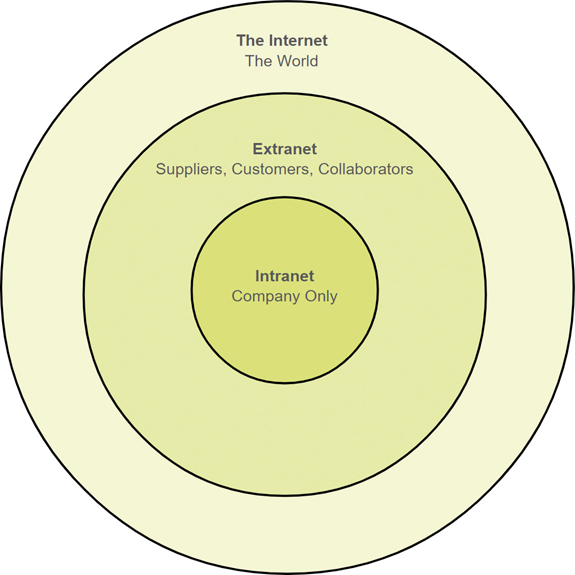
Figure 1-13 Levels of Access from Intranet to Internet
Check Your Understanding—Common Types of Networks (1.4.5)

Refer to the online course to complete this activity.
Internet Connections (1.5)
End devices such as computers and smartphones connect to a network in a variety of ways, using both wired and wireless means. These same types of connections are used to interconnect intermediary devices.
Internet Access Technologies (1.5.1)
Now you have a basic understanding of what makes up a network and the different types of networks. How do you actually connect users and organizations to the internet? As you may already know, there are many different ways to do this.
Home users, remote workers, and small offices typically require a connection to an internet service provider (ISP) to access the internet. Connection options vary greatly between ISPs and in different geographic locations. However, popular choices include broadband cable, broadband digital subscriber line (DSL), wireless WANs, and mobile services.
Organizations usually need access to other corporate sites as well as the internet. Fast connections are required to support business services such as IP phones, video conferencing, and data center storage. ISPs offer business-class interconnections. Popular business-class services include business DSL, leased lines, and Metro Ethernet.
Home and Small Office Internet Connections (1.5.2)
Figure 1-14 illustrates common connection options for small office and home office users:
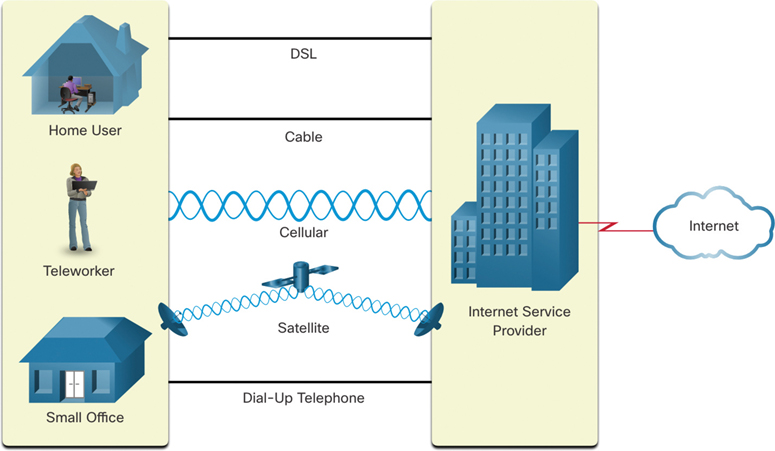
Figure 1-14 Small Office and Home Office Connection Options
Cable connection: With this type of connection, typically offered by cable television service providers, the internet data signal transmits on the same cable that delivers cable television. This connection type provides a high-bandwidth, high-availability, and an always-on connection to the internet.
Digital subscriber line (DSL): DSL provides high bandwidth, high availability, and an always-on connection to the internet. DSL runs over a telephone line. In general, small office and home office users connect using asymmetrical DSL (ADSL), which means that the download speed is faster than the upload speed.
Cellular connection: Cellular internet access uses a cellphone network to connect. Wherever you can get a cellular signal, you can get cellular internet access. Performance is limited by the capabilities of the phone or other device and the cell tower to which it is connected.
Satellite connection: The availability of satellite internet access is a benefit in areas that would otherwise have no internet connectivity at all. A satellite dish must have a clear line of sight to the satellite.
Dialup telephone connection: This is an inexpensive option that uses any phone line and a modem. The low bandwidth provided by a dialup modem connection is not sufficient for large data transfers, although it is useful for mobile access while traveling.
The choice of connection varies depending on geographic location and service provider availability.
Businesses Internet Connections (1.5.3)
Corporate connection options differ from home user options. Businesses may require higher bandwidth, dedicated bandwidth, and managed services. Connection options that are available differ depending on the type of service providers located nearby.
Figure 1-15 illustrates common connection options for businesses:
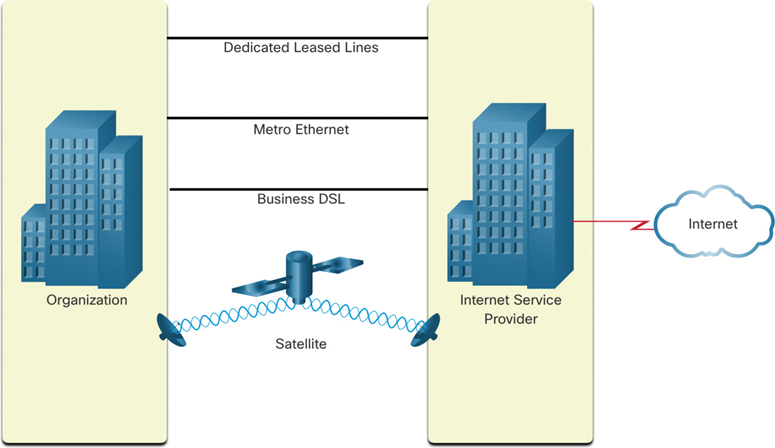
Figure 1-15 Business Connection Options
Dedicated leased lines: Leased lines are reserved circuits within a service provider’s network that connect geographically separated offices for private voice and/or data networking. The circuits are rented at a monthly or yearly rate.
Metro Ethernet: This is sometimes known as Ethernet WAN. In this chapter, we will refer to it as Metro Ethernet. Metro Ethernet can be used to extend LAN access technology into the WAN. Ethernet is a LAN technology you will learn about in a later chapter.
Business DSL: Business DSL is available in various formats. A popular choice is symmetric DSL (SDSL), which is similar to the consumer version of DSL but provides uploads and downloads at the same high speeds.
Satellite: Satellite service can provide a connection when a wired solution is not available.
The choice of connection varies depending on geographic location and service provider availability.
The Converging Network (1.5.4)
Consider a school built 30 years ago. Back then, some classrooms were cabled for the data network, telephone network, and video network for televisions. These separate networks could not communicate with each other. Each network used different technologies to carry communication signals. Each network had its own set of rules and standards to ensure successful communication. Multiple services ran on multiple networks, as shown in Figure 1-16.
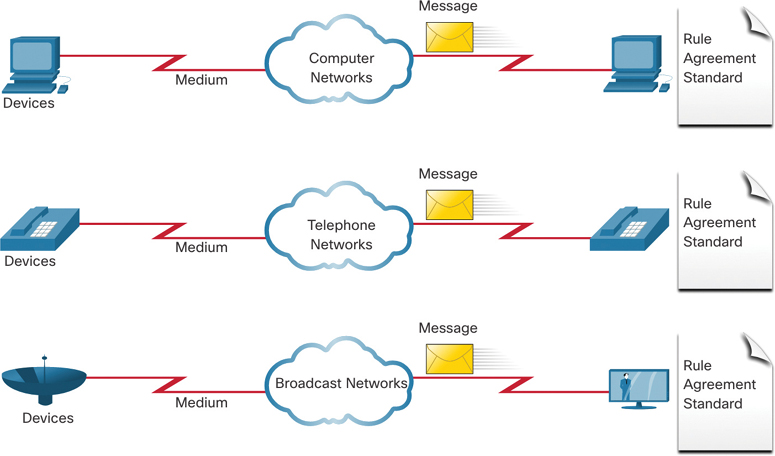
Figure 1-16 Traditional Networks
Today, separate data, telephone, and video networks have converged. Unlike dedicated networks, converged networks are capable of delivering data, voice, and video between many different types of devices over the same network infrastructure. This network infrastructure uses the same set of rules, agreements, and implementation standards. Converged data networks carry multiple services on one network, as shown in Figure 1-17.
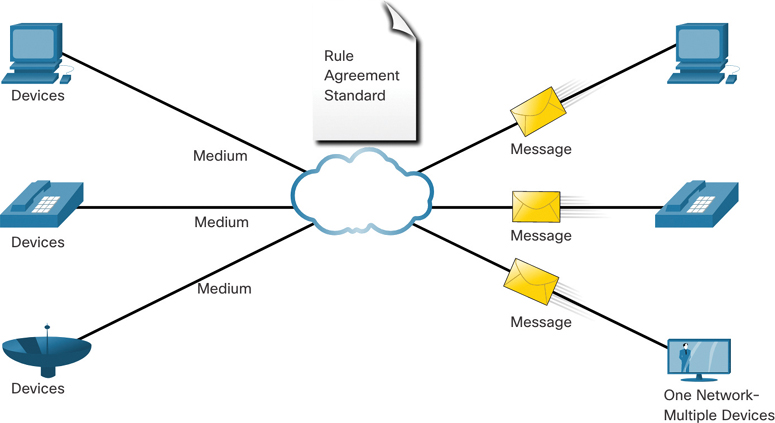
Figure 1-17 Converged Network
Video—Download and Install Packet Tracer (1.5.5)

This video shows you how to download and install Packet Tracer, which you can use to simulate the creation and testing of networks on your computer. Packet Tracer is a fun, take-home, flexible software program that will give you the opportunity to use the network representations and theories that you have just learned to build network models and explore relatively complex LANs and WANs.
Students commonly use Packet Tracer to
Prepare for a certification exam
Practice what they learn in networking courses
Sharpen their skills for a job interview
Examine the impact of adding new technologies into existing network designs
Build their skills for jobs in the Internet of Things
Compete in global design challenges (such as at the 2017 PT 7 Design Challenge on Facebook)
Packet Tracer is an essential learning tool used in many Cisco Networking Academy courses.
To obtain and install a copy of Cisco Packet Tracer, follow these steps:

Step 1. Log in to your Cisco Networking Academy “I’m Learning” page.
Step 2. Select Resources.
Step 3. Select Download Packet Tracer.
Step 4. Select the version of Packet Tracer you require.
Step 5. Save the file to your computer.
Step 6. Launch the Packet Tracer installation program.
Refer to the online course to view this video.
Video—Getting Started in Cisco Packet Tracer (1.5.6)

Packet Tracer is a tool that allows you to simulate real networks. It provides three main features:
You can add devices and connect them via cables or wirelessly
You can select, delete, inspect, label, and group components within a network
You can manage a network by opening an existing/sample network, saving your current network, and modifying your user profile or preferences
If you have used any program such as a word processor or spreadsheet, you are already familiar with the File menu commands located in the top menu bar. The Open, Save, Save As, and Exit commands work as they would for any program, but there are two commands that are special to Packet Tracer:
The Open Samples command displays a directory of prebuilt examples of features and configurations for various network and Internet of Things devices included within Packet Tracer.
The Exit and Logout command removes the registration information for this copy of Packet Tracer and requires the next user of this copy of Packet Tracer to go through the login procedure again.
Refer to the online course to view this video.
Packet Tracer—Network Representation (1.5.7)

In this activity, you will explore how Packet Tracer serves as a modeling tool for network representations.
Reliable Networks (1.6)
A network is a platform for distributing a wide range of services to end users in a reliable, efficient, and secure manner.
Network Architecture (1.6.1)
Have you ever been busy working online only to have “the internet go down”? As you know by now, the internet did not go down, but it is possible to lose your connection to it—and that can be very frustrating. With so many people in the world relying on network access to work and learn, it is imperative that networks be reliable. In this context, reliability means more than your connection to the internet. This section focuses on the four aspects of network reliability.
The role of networks has changed. What was once a data-only network is now a system that enables connections between people, devices, and information in a media-rich, converged network environment. For networks to function efficiently and grow in this type of environment, networks must be built on a standard network architecture.
Networks also support a wide range of applications and services. They must operate over the many different types of cables and devices that make up the physical infrastructure. The term network architecture, in this context, refers to the technologies that support the infrastructure and the programmed services and rules, or protocols, that move data across the network.
As networks evolve, there are four basic characteristics that network architects must address to meet user expectations:
Fault tolerance
Scalability
Quality of service (QoS)
Security
Fault Tolerance (1.6.2)
A fault-tolerant network is a network that limits the number of devices affected by a failure. It is built to allow quick recovery when a failure occurs. These networks depend on multiple paths between the source and destination of a message. If one path fails, the messages are instantly sent over a different link. Having multiple paths to a destination is known as redundancy.
Implementing a packet-switched network is one way to provide redundancy. Packet switching splits traffic into packets that are routed over a shared network. A single message, such as an email or a video stream, is broken into multiple message blocks, called packets. Each packet has the necessary addressing information of the source and destination of the message. The routers within the network switch the packets based on the condition of the network at that moment. This means that all the packets in a single message could take very different paths to the same destination. In Figure 1-18, the user is unaware and unaffected by the router that is dynamically changing the route when a link fails.
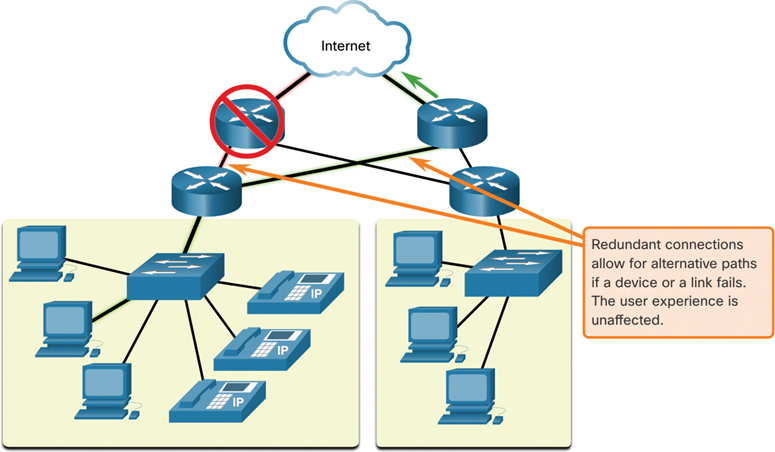
Figure 1-18 Fault-Tolerant Design
Scalability (1.6.3)
A scalable network expands quickly to support new users and applications. It does this without degrading the performance of services that are being accessed by existing users. Figure 1-19 shows how a new network is easily added to an existing network. These networks are scalable because the designers have followed accepted standards and protocols. Because of these standards and protocols, software and hardware vendors can focus on improving products and services without having to design a new set of rules for operating within the network.
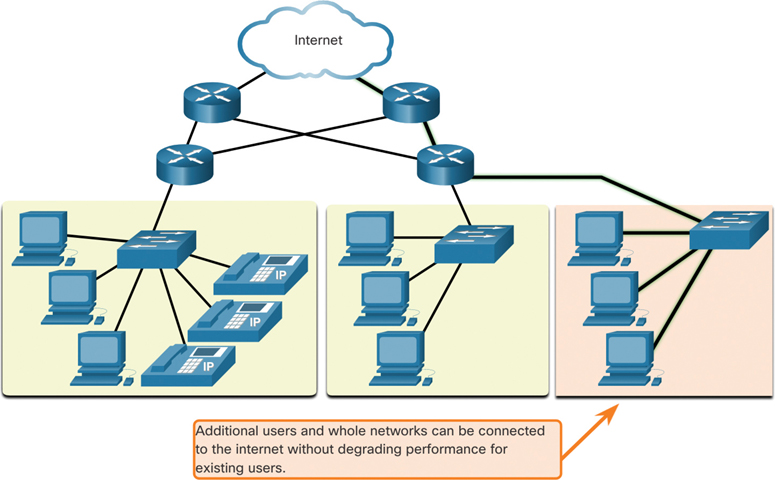
Figure 1-19 Scalable Design
Quality of Service (1.6.4)
Quality of service (QoS) is an increasing requirement in networks today. New applications available to users over networks, such as voice and live video transmissions, create higher expectations for the quality of the delivered services. Have you ever tried to watch a video and experienced constant breaks and pauses? As data, voice, and video content continue to converge onto the same network, QoS becomes a primary mechanism for managing congestion and ensuring reliable delivery of content to all users.
Congestion occurs when the demand for bandwidth exceeds the amount available. Network bandwidth is measured in the number of bits that can be transmitted in a single second, or bits per second (bps). When simultaneous communications are attempted across a network, the demand for network bandwidth can exceed its availability, creating network congestion.
When the volume of traffic is greater than what can be transported across the network, devices hold the packets in memory until resources become available to transmit them. In Figure 1-20, one user is requesting a web page, and another is on a phone call. With a QoS policy in place, the router can manage the flow of data and voice traffic and give priority to voice communication if the network experiences congestion.

Figure 1-20 QoS Design
Network Security (1.6.5)
The network infrastructure, the services, and the data contained on network-attached devices are crucial personal and business assets. Network administrators must address two types of network security concerns: network infrastructure security and information security.
Securing the network infrastructure involves physically securing devices that provide network connectivity and preventing unauthorized access to the management software that resides on them, as shown in Figure 1-21.
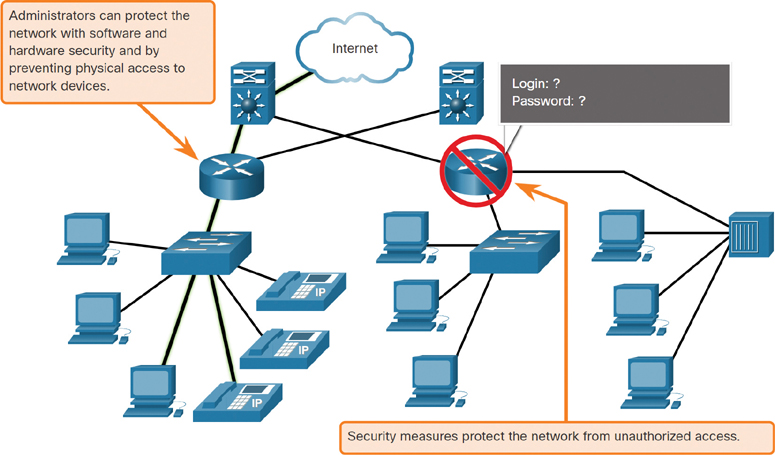
Figure 1-21 Security Design
Network administrators must also protect the information contained within the packets being transmitted over the network, as well as the information stored on network-attached devices. In order to achieve the goals of network security, there are three primary requirements:
Confidentiality: Data confidentiality means that only the intended and authorized recipients can access and read data.
Integrity: Data integrity assures users that the information has not been altered in transmission, from origin to destination.
Availability: Data availability assures users of timely and reliable access to data services for authorized users.
Check Your Understanding—Reliable Networks (1.6.6)

Refer to the online course to complete this activity.
Network Trends (1.7)
The network environment continues to evolve, providing new experiences and opportunities for end users. The network is now capable of delivering services and applications in a manner that was once only a dream.
Recent Trends (1.7.1)
You know a lot about networks now, including what they are made of, how they connect us, and what is needed to keep them reliable. But networks, like everything else, continue to change. You, as a NetAcad student, need to know about a few trends in networking.
As new technologies and end-user devices come to market, businesses and consumers must continue to adjust to the ever-changing network environment. Several networking trends affect organizations and consumers:
Bring your own device (BYOD)
Online collaboration
Video communications
Cloud computing
Bring Your Own Device (BYOD) (1.7.2)
The concept of any device, for any content, in any manner is a major global trend that requires significant changes to the way we use devices and safely connect them to networks. Bring your own device (BYOD) gives end users the freedom to use personal tools to access information and communicate across a business or campus network. With the growth of consumer devices and the related drop in cost, employees and students may have advanced computing and networking devices for personal use. These include laptops, notebooks, tablets, smartphones, and e-readers. Such devices may be purchased by the company or school, purchased by the individual, or both.
BYOD refers to any device, with any ownership, used anywhere.
Online Collaboration (1.7.3)
Individuals want to connect to a network not only for access to data applications but also to collaborate with one another. Collaboration is defined as “the act of working with another or others on a joint project.” Collaboration tools, such as Cisco Webex (see Figure 1-22), enable employees, students, teachers, customers, and partners to instantly connect, interact, and achieve their objectives.

Figure 1-22 Cisco Webex Interface
Collaboration is a critical and strategic priority that organizations are using to remain competitive. Collaboration is also a priority in education. Students need to collaborate to assist each other in learning, to develop the team skills used in the workforce, and to work together on team-based projects.
Cisco Webex Teams is a multifunctional collaboration tool that lets you send instant messages to one or more people, post images, and post videos and links. Each team “space” maintains a history of everything that is posted there.
Video Communications (1.7.4)
Another facet of networking that is critical to a communication and collaboration effort is video. Video is used for communication, collaboration, and entertainment. Video calls can be made to and from anyone with an internet connection, regardless of where they are located.
Video conferencing is a powerful tool for communicating with others, both locally and globally. Video is becoming a critical requirement for effective collaboration as organizations extend across geographic and cultural boundaries.
Video—Cisco Webex for Huddles (1.7.5)

Refer to the online course to view this video.
Cloud Computing (1.7.6)
Cloud computing is one of the ways that we access and store data. Cloud computing allows us to store personal files—even back up an entire drive—on servers over the internet. Applications such as word processing and photo editing can be accessed using the cloud.
For businesses, cloud computing extends the capabilities of IT without requiring investment in new infrastructure, training for new personnel, or licensing of new software. These services are available on demand and delivered economically to any device that is anywhere in the world without compromising security or function.
Cloud computing is possible because of data centers. Data centers are facilities used to house computer systems and associated components. A data center can occupy one room of a building, one or more floors, or an entire warehouse-sized building. Data centers are typically very expensive to build and maintain. For this reason, only large organizations use privately built data centers to house their data and provide services to users. Smaller organizations that cannot afford to maintain their own private data centers can reduce the overall cost of ownership by leasing server and storage services from a larger data center organization in the cloud.
For security, reliability, and fault tolerance, cloud providers often store data in distributed data centers. Instead of storing all the data of a person or an organization in one data center, it is stored in multiple data centers in different locations.
As described in Table 1-3, there are four primary types of clouds: public clouds, private clouds, hybrid clouds, and community clouds.
Table 1-3 Cloud Types
Cloud Type |
Description |
Public |
Cloud-based applications and services offered in a public cloud are made available to the general population. Services may be free or offered on a pay-per-use model, such as paying for online storage. A public cloud uses the internet to provide services. |
Private |
Cloud-based applications and services offered in a private cloud are intended for a specific organization or entity, such as a government. A private cloud can be set up using the organization’s private network, although this can be expensive to build and maintain. A private cloud can also be managed by an outside organization with strict access security. |
Hybrid |
A hybrid cloud is made up of two or more clouds (for example, part private and part public), where each part remains a distinct object but the two are connected using a single architecture. Individuals on a hybrid cloud would be able to have degrees of access to various services based on user access rights. |
Community |
A community cloud is created for exclusive use by specific entities or organizations. The differences between public clouds and community clouds are the functional needs that have been customized for the community. For example, healthcare organizations must remain compliant with policies and laws (such as HIPAA) that require special authentication and confidentiality. Community clouds are used by multiple organizations that have similar needs and concerns. A community cloud is similar to a public cloud environment but with set levels of security, privacy, and even regulatory compliance, as in a private cloud. |
Technology Trends in the Home (1.7.7)
Networking trends are not only affecting the way we communicate at work and at school but also changing many aspects of the home. The newest home trends include smart home technology.
Smart home technology is being integrated into everyday appliances, which can connect with other devices to make the appliances more “smart,” or automated. For example, you could prepare food and place it in the oven for cooking prior to leaving the house for the day. You would program your smart oven for the food you want it to cook, and the oven would be connected to your calendar of events so that it could determine what time you should be available to eat and adjust start times and length of cooking accordingly. It could even adjust cooking times and temperatures based on changes in schedule. In addition, a smartphone or tablet connection would let you connect to the oven directly to make any desired adjustments. When the food is ready, the oven could send an alert message to you (or someone you specify) to indicate that the food is done.
Smart home technology is being developed for all rooms in a house. Smart home technology will become more common as home networking and high-speed internet technology expand.
Powerline Networking (1.7.8)
Powerline networking for home networks uses existing electrical wiring to connect devices, as shown in Figure 1-23.
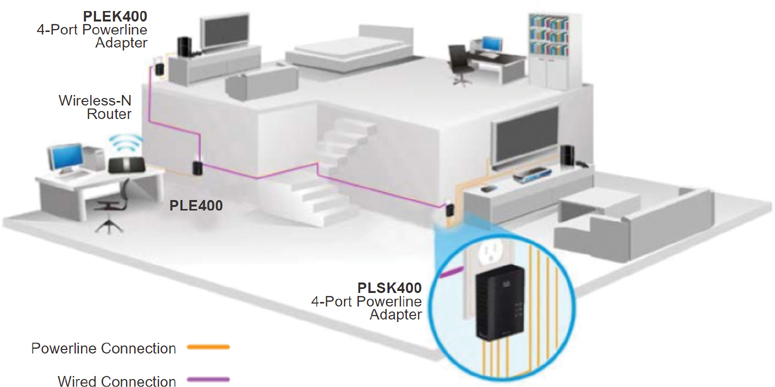
Figure 1-23 Powerline Networking Adapters
Using a standard powerline adapter, devices can connect to the LAN wherever there is an electrical outlet. No data cables need to be installed, and little to no additional electricity is used. Using the same wiring that delivers electricity, powerline networking sends data on certain frequencies.
Powerline networking is especially useful when wireless access points cannot reach all the devices in the home. Powerline networking is not a substitute for dedicated cabling in data networks. However, it is an alternative when data network cables or wireless communications are not possible or effective.
Wireless Broadband (1.7.9)
In many areas where cable and DSL are not available, wireless may be used to connect to the internet.
Wireless Internet Service Providers
A wireless internet service provider (WISP) is an ISP that connects subscribers to a designated access point or hotspot using wireless technologies similar to those found in home wireless local-area networks (WLANs). WISPs are most commonly found in rural environments where DSL or cable services are not available.
Although a separate transmission tower may be installed for the antenna, typically the antenna is attached to an existing elevated structure, such as a water tower or a radio tower. A small dish or antenna is installed on the subscriber’s roof, in range of the WISP transmitter. The subscriber’s access unit is connected to the wired network inside the home. From the perspective of the home user, the setup is not much different from that of DSL or cable service. The main difference is that the connection from the home to the ISP is wireless instead of a physical cable.
Wireless Broadband Service
Another wireless solution for homes and small businesses is wireless broadband. This solution uses the same cellular technology as a smartphone. An antenna is installed outside the house, providing either wireless or wired connectivity for devices in the home. In many areas, home wireless broadband is competing directly with DSL and cable services.
Check Your Understanding—Network Trends (1.7.10)

Refer to the online course to complete this activity.
Network Security (1.8)
Security is a critical component in designing, implementing, and maintaining networks. Network engineers and administrators must always consider security risks and employ the proper mitigation methods before deploying any type of network service.
Security Threats (1.8.1)
You have, no doubt, heard or read news stories about a company network being breached, giving threat actors access to the personal information of thousands of customers. Network security is always going to be a top priority of administrators.
Network security is an integral part of computer networking, regardless of whether the network is a home network with a single connection to the internet or a corporate network with thousands of users. Network security must consider the environment, as well as the tools and requirements of the network. It must be able to secure data while still allowing for the quality of service that users expect of the network.
Securing a network involves using protocols, technologies, devices, tools, and techniques to protect data and mitigate threats. Threat vectors may be external or internal. Many external network security threats today originate from the internet.
There are several common external threats to networks:
Viruses, worms, and Trojan horses: These contain malicious software or code running on a user device.
Spyware and adware: These types of software are installed on a user’s device to secretly collect information about the user.
Zero-day attacks: Also called zero-hour attacks, these attacks occur on the first day that a vulnerability becomes known.
Threat actor attacks: In these attacks, malicious persons attack user devices or network resources.
Denial-of-service attacks: These attacks slow or crash applications and processes on a network device.
Data interception and theft: This type of attack involves capturing private information from an organization’s network.
Identity theft: This type of attack involves stealing the login credentials of a user in order to access private data.
It is important to consider internal threats. Many studies have shown that the most common data breaches are related to internal network users. Such breaches may be attributed to lost or stolen devices, accidental misuse by employees, or even malicious employees. BYOD strategies make corporate data especially vulnerable. Therefore, when developing a security policy, it is important to address both external and internal security threats, as shown in Figure 1-24.
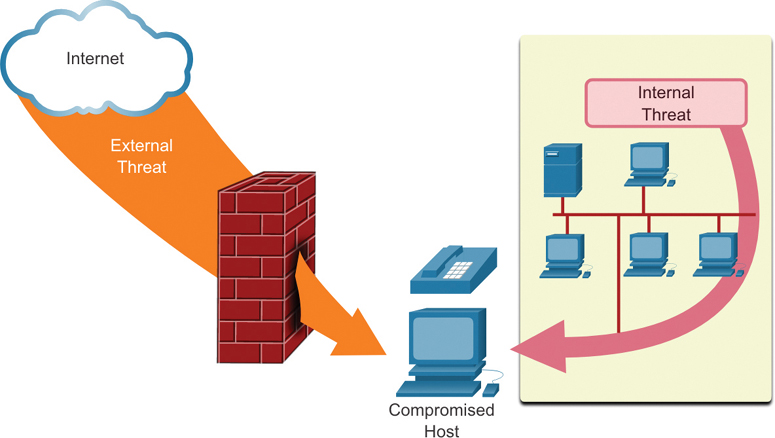
Figure 1-24 External and Internal Threats
Security Solutions (1.8.2)
No single solution can protect a network from the variety of threats that exist. For this reason, security should be implemented in multiple layers, using more than one security solution. If one security component fails to identify and protect a network, others may succeed.
A home network security implementation is usually rather basic. Typically, you implement it on the end devices, as well as at the point of connection to the internet. You may even be able to rely on contracted services from the ISP.
These are the basic security components for a home or small office network:
Antivirus and antispyware: These applications help to protect end devices from becoming infected with malicious software.
Firewall filtering: Firewall filtering blocks unauthorized access into and out of the network. This may include a host-based firewall system that prevents unauthorized access to the end device or a basic filtering service on the home router to prevent unauthorized access from the outside world into the network.
In contrast, the network security implementation for a corporate network usually consists of many components built into the network to monitor and filter traffic. Ideally, all components work together to minimize maintenance and improve security. Larger networks and corporate networks use antivirus, antispyware, and firewall filtering, and they also have additional security requirements:
Dedicated firewall systems: These provide more advanced firewall capabilities that can filter large amounts of traffic with more granularity.
Access control lists (ACL): ACLs further filter access and traffic forwarding based on IP addresses and applications.
Intrusion prevention systems (IPS): These systems identify fast-spreading threats, such as zero-day or zero-hour attacks.
Virtual private networks (VPN): These networks provide secure access into an organization for remote workers.
Network security requirements must consider the environment as well as the various applications and computing requirements. Both home and business environments must be able to secure their data while still allowing for the quality of service that users expect of each technology. In addition, any security solution that is implemented must be adaptable to the growing needs of the network and changing trends.
The study of network security threats and mitigation techniques starts with a clear understanding of the underlying switching and routing infrastructure used to organize network services.
Check Your Understanding—Network Security (1.8.3)

Refer to the online course to complete this activity.
The IT Professional (1.9)
The role of an IT professional is constantly evolving. An IT professional is always learning in an ever-changing environment.
CCNA (1.9.1)
As a NetAcad student, you may already have a career in IT, or you may be educating yourself to prepare for your career. In either case, it is good to know about the skills needed for the various jobs that are available in IT.
Network engineers are more vital today than ever before, and their roles and required skills are constantly evolving. The Cisco Certified Network Associate (CCNA) certification demonstrates that you have knowledge of foundational technologies and ensures that you stay relevant with the skills needed for the adoption of next-generation technologies.
The requirements of the CCNA for networking engineers have been consolidated and updated to three courses and one exam covering the fundamental topics for all network technologies. This new CCNA focuses on IP foundation and security topics, along with wireless, virtualization, automation, and network programmability.
Cisco offers new DevNet certifications at the associate, specialist, and professional levels to validate your software development skills.
In addition, you can obtain specialist certifications (such as Cisco Enterprise Advanced Infrastructure Specialist certification) to validate your skills in line with your job role and interests.
You can start where you want. There are no prerequisites to start earning your associate-, specialist-, professional-, or expert-level certifications. Continuing education credits for recertification and ongoing development are now available for CCNA certification.
Networking Jobs (1.9.2)
Your CCNA certification will prepare you for a variety of jobs in today’s market. At www.netacad.com you can click the Careers menu and then select Employment opportunities. You can find employment opportunities where you live by using the Talent Bridge Matching Engine. Use this new program to search for jobs with Cisco and Cisco partners and distributors seeking Cisco Networking Academy students and alumni.
You can also search for IT jobs using online search engines such as Indeed, Glassdoor, and Monster. Use search terms such as IT, network administrator, network architect, and computer systems administrator. You can also search using the term Cisco CCNA.
Lab—Research IT and Networking Job Opportunities (1.9.3)

In this lab, you will complete the following objectives: Part 1: Research Job Opportunities; Part 2: Reflect on Research.
Summary (1.10)
The following is a summary of the topics in the chapter and their corresponding online modules.
Networks Affect Our Lives
In today’s world, through the use of networks, we are connected as never before. People with ideas can communicate instantly with others to make those ideas reality. The creation of online communities for the exchange of ideas and information has the potential to increase productivity opportunities around the globe. The cloud enables us to store documents and pictures and access them anywhere, anytime.
Network Components
All computers that are connected to networks and participate directly in network communication are classified as hosts. Hosts can be called end devices, and some hosts are also called clients. Many computers function as servers and clients on a network called a peer-to-peer network. An end device is either the source or destination of a message transmitted over a network. Intermediary devices connect the individual end devices to the network and can connect multiple individual networks to form an internetwork. Intermediary devices use the destination end device address, in conjunction with information about the network interconnections, to determine the path that messages should take through the network. The media provide the channel over which the message travels from source to destination.
Network Representations and Topologies
Diagrams of networks often use symbols to represent the different devices and connections that make up a network. A topology diagram provides an easy way to understand how devices connect in a large network. A physical topology diagram illustrates the physical locations of intermediary devices and cable installation. A logical topology diagram illustrates devices, ports, and the addressing scheme of a network.
Common Types of Networks
A small home network connects a few computers to each other and to the internet. A small office/home office (SOHO) network allows computers in a home office or a remote office to connect to a corporate network or access centralized shared resources. Medium to large networks, such as those used by corporations and schools, can have many locations with hundreds or thousands of interconnected hosts. The internet is a network of networks that connects hundreds of millions of computers worldwide. The two most common network infrastructures are local-area networks (LANs), and wide-area networks (WANs). A LAN is a network infrastructure that spans a small geographic area. A WAN is a network infrastructure that spans a wide geographic area. An intranet is a private connection of LANs and WANs that belongs to an organization. An organization may use an extranet to provide secure and safe access to individuals who work for a different organization but require access to the organization’s data.
Internet Connections
SOHO internet connections include cable, DSL, cellular, satellite, and dialup telephone. Business internet connections include dedicated leased lines, Metro Ethernet, business DSL, and satellite. The choice of connection varies depending on geographic location and service provider availability. Traditional separate networks used different technologies, rules, and standards. Converged networks deliver data, voice, and video between many different types of devices over the same network infrastructure. This network infrastructure uses the same set of rules, agreements, and implementation standards. Packet Tracer is a flexible software program that lets you use network representations and theories to build network models and explore relatively complex LANs and WANs.
Reliable Networks
The term network architecture refers to the technologies that support the infrastructure and the programmed services and rules, or protocols, that move data across a network. As networks evolve, we have learned that there are four basic characteristics that network architects must address to meet user expectations: fault tolerance, scalability, quality of service (QoS), and security. A fault-tolerant network limits the number of devices affected by a failure. Redundancy means having multiple paths to a destination. A scalable network expands quickly to support new users and applications. Networks are scalable because the designers follow accepted standards and protocols. QoS is a primary mechanism for managing congestion and ensuring reliable delivery of content to users. Network administrators must address two types of network security concerns: network infrastructure security and information security. To achieve the goals of network security, there are three primary requirements: confidentiality, integrity, and availability.
Network Trends
Several recent networking trends affect organizations and consumers: bring your own device (BYOD), online collaboration, video communications, and cloud computing. BYOD refers to any device, with any ownership, used anywhere. Collaboration tools such as Cisco WebEx enable employees, students, teachers, customers, and partners to instantly connect, interact, and achieve their objectives. Video is used for communication, collaboration, and entertainment. Video calls can be made to and from anyone with an internet connection, regardless of where they are located. Cloud computing allows us to store personal files—even back up an entire drive—on servers over the internet. Applications such as word processing and photo editing can be accessed using the cloud. There are four primary types of clouds: public clouds, private clouds, hybrid clouds, and custom clouds. Smart home technology is being developed for all rooms in a house. Smart home technology will become more common as home networking and high-speed internet technology expand. Using the same wiring that delivers electricity, powerline networking sends data on certain frequencies. A wireless internet service provider (WISP) is an ISP that connects subscribers to a designated access point or hotspot using wireless technologies similar to those found in home wireless local-area networks (WLANs).
Network Security
There are several common external threats to networks:
Viruses, worms, and Trojan horses
Spyware and adware
Zero-day attacks
Threat actor attacks
Denial-of-service attacks
Data interception and theft
Identity theft
These are the basic security components for a home or small office network:
Antivirus and antispyware
Firewall filtering
Larger networks and corporate networks use antivirus, antispyware, and firewall filtering, and they also have additional security requirements:
Dedicated firewall systems
Access control lists (ACL)
Intrusion prevention systems (IPS)
Virtual private networks (VPN)
The IT Professional
The Cisco Certified Network Associate (CCNA) certification demonstrates that you have knowledge of foundational technologies and ensures that you stay relevant with skills needed for the adoption of next-generation technologies. Your CCNA certification will prepare you for a variety of jobs in today’s market. At www.netacad.com you can click the Careers menu and then select Employment opportunities. You can find employment opportunities where you live by using the Talent Bridge Matching Engine to search for jobs with Cisco as well as Cisco partners and distributors seeking Cisco Networking Academy students and alumni.
Practice
The following activities provide practice with the topics introduced in this chapter. The lab is available in the companion Introduction to Networks Labs & Study Guide (CCNAv7) (ISBN 9780136634454). The Packet Tracer activity instructions are also provided in the Labs & Study Guide. The PKA files are available in the online course.
Lab

Lab 1.9.3: Research IT and Networking Job Opportunities
Packet Tracer Activity

Packet Tracer 1.5.7: Network Representation
Check Your Understanding Questions
Complete all the review questions listed here to test your understanding of the topics and concepts in this chapter. The appendix “Answers to ‘Check Your Understanding’ Questions” lists the answers.
1. During a routine inspection, a technician discovered that software that was installed on a computer was secretly collecting data about websites that were visited by users of the computer. Which type of threat is affecting this computer?
DoS attack
identity theft
spyware
zero-day attack
2. Which term refers to a network that provides secure access to the corporate offices for suppliers, customers, and collaborators?
internet
intranet
extranet
extended net
3. A large corporation has modified its network to allow users to access network resources from their personal laptops and smartphones. Which networking trend does this describe?
cloud computing
online collaboration
bring your own device
video conferencing
4. What is an ISP?
It is a standards body that develops cabling and wiring standards for networking.
It is a protocol that establishes how computers in a local network communicate.
It is an organization that enables individuals and businesses to connect to the internet.
It is a networking device that combines the functionality of several different networking devices in one.
5. For which of the following would the use of a WISP be recommended?
an internet café in a city
a farm in a rural area without wired broadband access
any home with multiple wireless devices
an apartment in a building with cable access to the internet
6. What characteristic of a network enables it to quickly grow to support new users and applications without impacting the performance of the service being delivered to existing users?
reliability
scalability
quality of service
accessibility
7. A college is building a new dormitory on its campus. Workers are digging in the ground to install a new water pipe for the dormitory. A worker accidentally damages a fiber-optic cable that connects two of the existing dormitories to the campus data center. Although the cable has been cut, students in the dormitories experience only a very short interruption of network services. What characteristic of the network is described here?
quality of service
scalability
security
fault tolerance
integrity
8. What are two characteristics of a scalable network? (Choose two.)
easily overloaded with increased traffic
grows in size without impacting existing users
is not as reliable as a small network
suitable for modular devices that allow for expansion
offers limited number of applications
9. Which device performs the function of determining the path that messages should take through internetworks?
a router
a firewall
a web server
a DSL modem
10. Which two internet connection options do not require that physical cables be run to a building? (Choose two.)
DSL
cellular
satellite
dialup
dedicated leased line
11. What type of network must a home user access in order to do online shopping?
an intranet
the internet
an extranet
a local area network
12. How does BYOD change the way businesses implement networks?
BYOD requires organizations to purchase laptops rather than desktops.
BYOD users are responsible for their own network security, thus reducing the need for organizational security policies.
BYOD devices are more expensive than devices that are purchased by an organization.
BYOD provides flexibility in where and how users can access network resources.
13. An employee wants to access the network of an organization remotely, in the safest possible way. What network feature would allow an employee to gain secure remote access to a company network?
ACL
IPS
VPN
BYOD
14. What is the internet?
It is a network based on Ethernet technology.
It provides network access for mobile devices.
It provides connections through interconnected global networks.
It is a private network for an organization with LAN and WAN connections.
15. What are two functions of end devices on a network? (Choose two.)
They originate the data that flows through the network.
They direct data over alternate paths in the event of a link failure.
They filter the flow of data to enhance security.
They are the interface between humans and the communications network.
They provide the channel over which the network message travels.