Chapter 9
Address Resolution
Objectives
Upon completion of this chapter, you will be able to answer the following questions:
What are the roles of the MAC address and the IP address?
What is the purpose of ARP?
What is the operation of IPv6 neighbor discovery?
Key Terms
This chapter uses the following key terms. You can find the definitions in the glossary at the end of the book.
Introduction (9.0)
Hosts and routers both create routing tables to ensure that they can send and receive data across networks. So how does this information get created in a routing table? As a network administrator, you could enter these MAC and IP addresses manually. But that would take a lot of time, and the likelihood of making a few mistakes is great. Are you thinking that there must be some way that this could be done automatically, by the hosts and routers themselves? Of course, you are correct! Even though this address resolution process is automatic, you must understand how it works because you may have to troubleshoot a problem or, worse, your network could be attacked by a threat actor. Are you ready to learn about address resolution? This chapter mentions several very good videos to help explain the concepts, as well as three Packet Tracer activities to cement your understanding. Why wait?
MAC and IP (9.1)
This section discusses the differences between Layer 2 data link addresses, such as Ethernet MAC addresses, and Layer 3 network address, such as IP addresses.
Destination on Same Network (9.1.1)
Sometimes a host must send a message, but it only knows the IP address of the destination device. The host needs to know the MAC address of that device, but how can it be discovered? This is where address resolution becomes critical.
There are two primary addresses assigned to a device on an Ethernet LAN:
Physical address (the MAC address): This address is used for NIC-to-NIC communications on the same Ethernet network.
Logical address (the IP address): This address is used to send a packet from the source device to the destination device. The destination IP address may be on the same IP network as the source, or it may be on a remote network.
Layer 2 physical addresses (that is, Ethernet MAC addresses) are used to deliver a data link frame with an encapsulated IP packet from one NIC to another NIC on the same network. If the destination IP address is on the same network, the destination MAC address will be that of the destination device.
In Figure 9-1, PC1 wants to send a packet to PC2. The figure displays the Layer 2 destination and source MAC addresses and the Layer 3 IPv4 addressing that would be included in the packet sent from PC1.
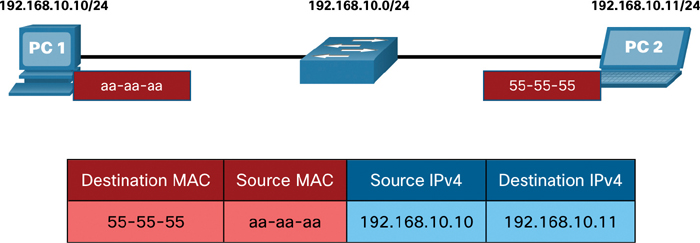
Figure 9-1 Addressing of Hosts on the Same Network
The Layer 2 Ethernet frame contains the following:
Destination MAC address: This is the simplified MAC address of PC2, 55-55-55.
Source MAC address: This is the simplified MAC address of the Ethernet NIC on PC1, aa-aa-aa.
The Layer 3 IP packet contains the following:
Source IPv4 address: This is the IPv4 address of PC1, 192.168.10.10.
Destination IPv4 address: This is the IPv4 address of PC2, 192.168.10.11.
Destination on Remote Network (9.1.2)
When the destination IP address (IPv4 or IPv6) is on a remote network, the destination MAC address is the address of the host default gateway (that is, the router interface).
In Figure 9-2, PC1 wants to send a packet to PC2. PC2 is located on a remote network. Because the destination IPv4 address is not on the same local network as PC1, the destination MAC address is that of the local default gateway on the router.
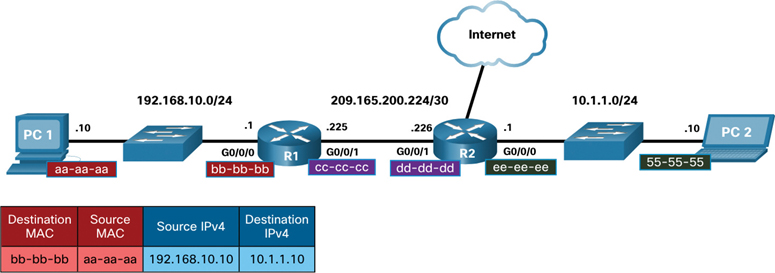
Figure 9-2 Remote Network Example: PC1 to R1
Routers examine the destination IPv4 address to determine the best path for forwarding the IPv4 packet. When a router receives the Ethernet frame, it de-encapsulates the Layer 2 information. Using the destination IPv4 address, it determines the next hop device and then encapsulates the IPv4 packet in a new data link frame for the outgoing interface.
R1 can now encapsulate the packet with new Layer 2 address information, as shown in Figure 9-3.
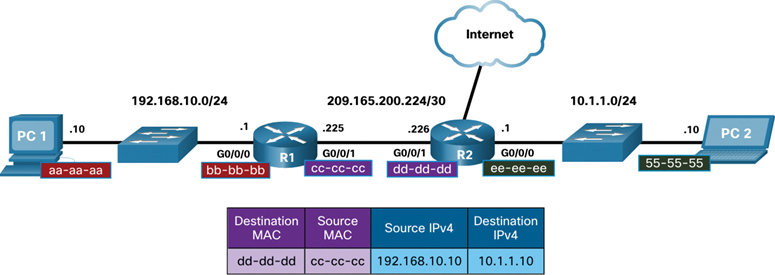
Figure 9-3 Remote Network Example: R1 to R2
The new destination MAC address would be the address of the R2 G0/0/1 interface, and the new source MAC address would be that of the R1 G0/0/1 interface.
Along each link in a path, an IP packet is encapsulated in a frame. The frame is specific to the data link technology that is associated with that link, such as Ethernet. If the next hop device is the final destination, the destination MAC address is the address of the device’s Ethernet NIC, as shown in Figure 9-4.
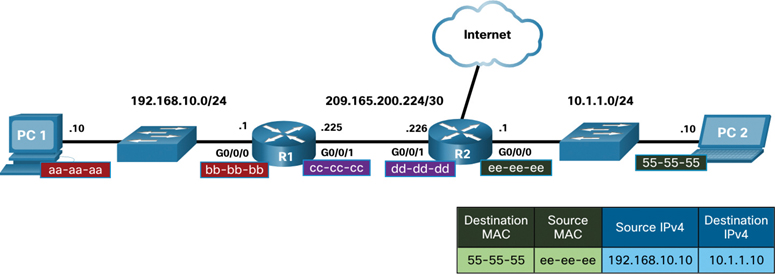
Figure 9-4 Remote Network Example: R2 to PC2
How are the IP addresses of the IP packets in a data flow associated with the MAC addresses on each link along the path to the destination? For IPv4 packets, this is done through a process called Address Resolution Protocol (ARP). For IPv6 packets, the process is ICMPv6 Neighbor Discovery (ND).
Packet Tracer—Identify MAC and IP Addresses (9.1.3)

In this Packet Tracer activity, you will complete the following objectives:
Gather PDU Information for Local Network Communication
Gather PDU Information for Remote Network Communication
This activity is optimized for viewing PDUs. The devices are already configured. You will gather PDU information in simulation mode and answer a series of questions about the data you collect.
Check Your Understanding—MAC and IP (9.1.4)

Refer to the online course to complete this activity.
ARP (9.2)
This section discusses the relationship between MAC addresses and IPv4 addresses, as well as how Address Resolution Protocol (ARP) is used to map these two addresses.
ARP Overview (9.2.1)
If your network is using the IPv4 communications protocol, Address Resolution Protocol (ARP) is what you need in order to map IPv4 addresses to MAC addresses. This section explains how ARP works.
Every IP device on an Ethernet network has a unique Ethernet MAC address. When a device sends an Ethernet Layer 2 frame, it contains these two addresses:
Destination MAC address: The Ethernet MAC address of the destination device on the same local network segment. If the destination host is on another network, then the destination address in the frame would be the address of the default gateway (that is, router).
Source MAC address: The MAC address of the Ethernet NIC on the source host.
Figure 9-5 illustrates the problem when sending a frame to another host on the same segment on an IPv4 network.
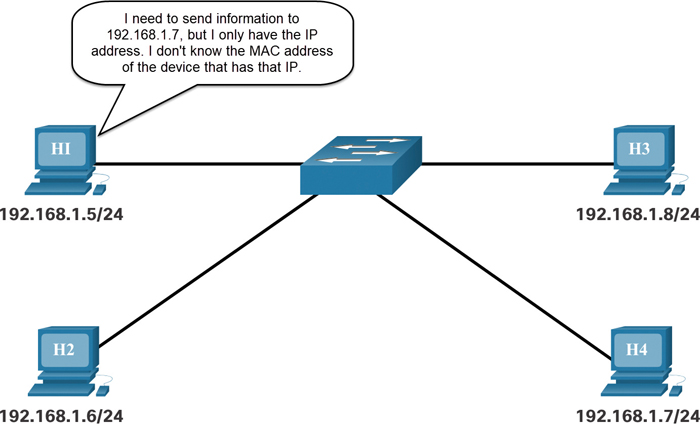
Figure 9-5 A Host Does Not Know the MAC Address for a Destination
To send a packet to another host on the same local IPv4 network, a host must know the IPv4 address and the MAC address of the destination device. Device destination IPv4 addresses are either known or resolved by device name. However, MAC addresses must be discovered.
A device uses ARP to determine the destination MAC address of a local device when it knows its IPv4 address.
ARP provides two basic functions:
Resolving IPv4 addresses to MAC addresses
Maintaining a table of IPv4-to-MAC address mappings
ARP Functions (9.2.2)
When a packet is sent to the data link layer to be encapsulated into an Ethernet frame, the device refers to a table in its memory to find the MAC address that is mapped to the IPv4 address. This table, which is stored temporarily in RAM, is called the ARP table or the ARP cache.
The sending device searches its ARP table for a destination IPv4 address and a corresponding MAC address. Then:
If the packet’s destination IPv4 address is on the same network as the source IPv4 address, the device searches the ARP table for the destination IPv4 address.
If the destination IPv4 address is on a different network from the source IPv4 address, the device searches the ARP table for the IPv4 address of the default gateway.
In both cases, the search is for an IPv4 address and a corresponding MAC address for the device.
Each entry, or row, of the ARP table binds an IPv4 address with a MAC address. We call the relationship between the two values a map. The map simply enables you to locate an IPv4 address in the table and discover the corresponding MAC address. The ARP table temporarily saves (caches) the mapping for the devices on the LAN.
If the device locates the IPv4 address, its corresponding MAC address is used as the destination MAC address in the frame. If no entry is found, the device sends an ARP request, as shown in Figure 9-6.
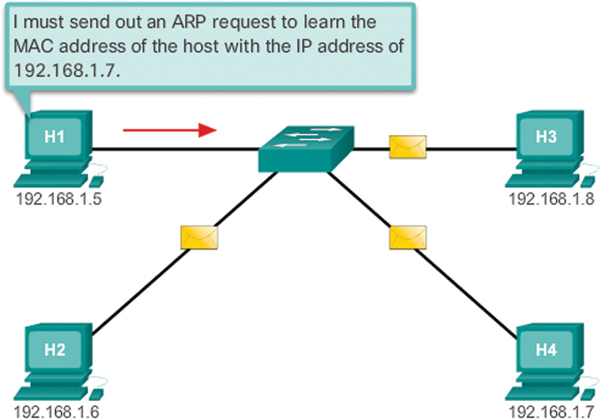
Figure 9-6 H1 Sends a Broadcast ARP Request
The destination responds with an ARP reply, as shown in Figure 9-7.
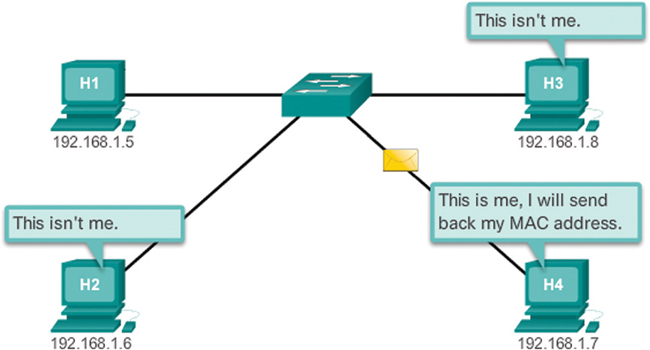
Figure 9-7 H4 Sends a Unicast ARP Reply
Video—ARP Request (9.2.3)

An ARP request is sent when a device needs to determine the MAC address that is associated with an IPv4 address, and it does not have an entry for the IPv4 address in its ARP table.
ARP messages are encapsulated directly within an Ethernet frame. There is no IPv4 header. An ARP request is encapsulated in an Ethernet frame using the following header fields:
Destination MAC Address: This is a broadcast address FF-FF-FF-FF-FF-FF, which requires all Ethernet NICs on the LAN to accept and process the ARP request.
Source MAC Address: This is the MAC address of the sender of the ARP request.
Type: ARP messages have a Type field setting of 0x806. This informs the receiving NIC that the data portion of the frame needs to be passed to the ARP process.
Because ARP requests are broadcasts, a switch floods them out all ports except for the receiving port. All Ethernet NICs on the LAN process broadcasts and must deliver the ARP request to the device’s operating system for processing. Every device must process the ARP request to see if the target IPv4 address matches its own. A router does not forward broadcasts out other interfaces.
Only one device on a LAN has an IPv4 address that matches the target IPv4 address in the ARP request. All other devices do not reply.
Refer to the online course to view this video.
Video—ARP Operation—ARP Reply (9.2.4)

Only the device with the target IPv4 address associated with the ARP request responds with an ARP reply. The ARP reply is encapsulated in an Ethernet frame using the following header fields:
Destination MAC Address: This is the MAC address of the sender of the ARP request.
Source MAC Address: This is the MAC address of the sender of the ARP reply.
Type: ARP messages have a Type field setting of 0x806. This informs the receiving NIC that the data portion of the frame needs to be passed to the ARP process.
Only the device that originally sent an ARP request receives a unicast ARP reply. After the ARP reply is received, the device adds the IPv4 address and the corresponding MAC address to its ARP table. Packets destined for that IPv4 address can then be encapsulated in frames using the corresponding MAC address.
If no device responds to an ARP request, the packet is dropped because a frame cannot be created.
Entries in the ARP table are timestamped. If a device does not receive a frame from a particular device before the timestamp expires, the entry for this device is removed from the ARP table.
In addition, static map entries can be entered in an ARP table, but this is rarely done. Static ARP table entries do not expire over time and must be manually removed.
Note: Whereas IPv4 uses ARP, IPv6 uses a similar process, known as ICMPv6 Neighbor Discovery (ND). IPv6 uses neighbor solicitation and neighbor advertisement messages, which are similar to IPv4 ARP requests and ARP replies.
Refer to the online course to view this video.
Video—ARP Role in Remote Communications (9.2.5)

When the destination IPv4 address is not on the same network as the source IPv4 address, the source device needs to send the frame to its default gateway. This is the interface of the local router. Whenever a source device has a packet with an IPv4 address on another network, it encapsulates that packet in a frame, using the destination MAC address of the router.
The IPv4 address of the default gateway is stored in the IPv4 configuration of the hosts. When a host creates a packet for a destination, it compares the destination IPv4 address and its own IPv4 address to determine if the two IPv4 addresses are located on the same Layer 3 network. If the destination host is not on its same network, the source checks its ARP table for an entry with the IPv4 address of the default gateway. If there is not an entry in the ARP table, the source uses the ARP process to determine the MAC address of the default gateway.
Refer to the online course to view this video.
Removing Entries from an ARP Table (9.2.6)
For each device, an ARP cache timer removes ARP entries that have not been used for a specified period of time. The times differ depending on the operating system of the device. For example, newer Windows operating systems store ARP table entries for 15 to 45 seconds, as illustrated in Figure 9-8.
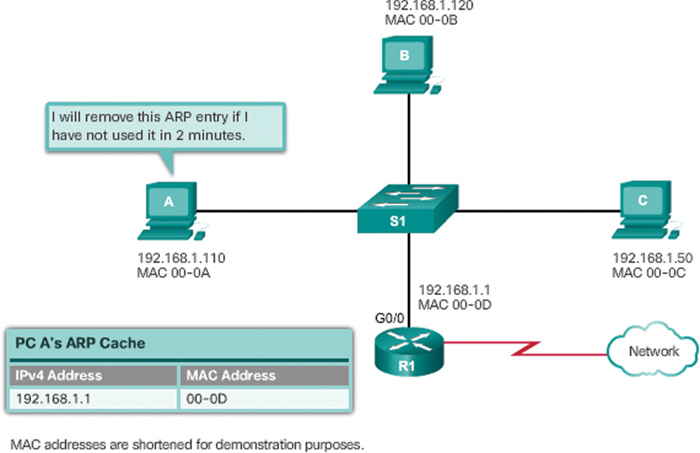
Figure 9-8 Removing MAC-to-IP Address Mappings
Commands may also be used to manually remove some or all of the entries in the ARP table. After an entry has been removed, the process for sending an ARP request and receiving an ARP reply must occur again in order to once again enter the map in the ARP table.
ARP Tables on Networking Devices (9.2.7)
On a Cisco router, the show ip arp command is used to display the ARP table, as shown in Example 9-1.
Example 9-1 Cisco Router ARP Table
R1# show ip arp Protocol Address Age (min) Hardware Addr Type Interface Internet 192.168.10.1 - a0e0.af0d.e140 ARPA GigabitEthernet0/0/0 Internet 209.165.200.225 - a0e0.af0d.e141 ARPA GigabitEthernet0/0/1 Internet 209.165.200.226 1 a03d.6fe1.9d91 ARPA GigabitEthernet0/0/1 R1#
On a Windows 10 PC, the arp -a command is used to display the ARP table, as shown in Example 9-2.
Example 9-2 Windows 10 PC ARP Table
C:\Users\PC> arp -a Interface: 192.168.1.124 --- 0x10 Internet Address Physical Address Type 192.168.1.1 c8-d7-19-cc-a0-86 dynamic 192.168.1.101 08-3e-0c-f5-f7-77 dynamic 192.168.1.110 08-3e-0c-f5-f7-56 dynamic 192.168.1.112 ac-b3-13-4a-bd-d0 dynamic 192.168.1.117 08-3e-0c-f5-f7-5c dynamic 192.168.1.126 24-77-03-45-5d-c4 dynamic 192.168.1.146 94-57-a5-0c-5b-02 dynamic 192.168.1.255 ff-ff-ff-ff-ff-ff static 224.0.0.22 01-00-5e-00-00-16 static 224.0.0.251 01-00-5e-00-00-fb static 239.255.255.250 01-00-5e-7f-ff-fa static 255.255.255.255 ff-ff-ff-ff-ff-ff static C:\Users\PC>
ARP Issues—ARP Broadcasts and ARP Spoofing (9.2.8)
As a broadcast frame, an ARP request is received and processed by every device on the local network. On a typical business network, these broadcasts would probably have minimal impact on network performance. However, if a large number of devices were to be powered up and all start accessing network services at the same time, there could be some reduction in performance for a short period of time, as shown in Figure 9-9. After the devices send out the initial ARP broadcasts and have learned the necessary MAC addresses, any impact on the network will be minimized.
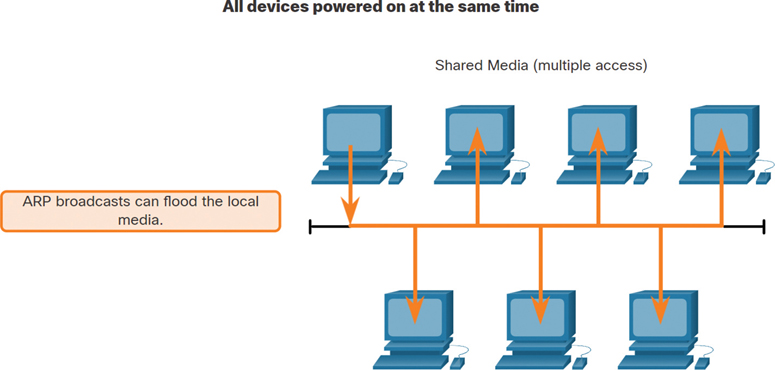
Figure 9-9 ARP Broadcasts Flooding a Network
In some cases, the use of ARP can lead to a potential security risk. A threat actor can use ARP spoofing to perform an ARP poisoning attack. This is a technique used by a threat actor to reply to an ARP request for an IPv4 address belonging to another device, such as the default gateway, as shown in Figure 9-10. The threat actor sends an ARP reply with its own MAC address. The receiver of the ARP reply adds the wrong MAC address to its ARP table and sends these packets to the threat actor.

Figure 9-10 Threat Actor Spoofing an ARP Reply
Enterprise-level switches can use mitigation techniques such as dynamic ARP inspection (DAI). DAI is beyond the scope of this course.
Packet Tracer—Examine the ARP Table (9.2.9)

In this Packet Tracer activity, you will complete the following objectives:
Examine an ARP Request
Examine a Switch MAC Address Table
Examine the ARP Process in Remote Communications
This activity is optimized for viewing PDUs. The devices are already configured. You will gather PDU information in simulation mode and answer a series of questions about the data you collect.
Check Your Understanding—ARP (9.2.10)

Refer to the online course to complete this activity.
IPv6 Neighbor Discovery (9.3)
This section discusses the relationship between MAC addresses and IPv6 addresses and how the Neighbor Discovery (ND) protocol is used to map the two addresses.
Video—IPv6 Neighbor Discovery (9.3.1)

If your network is using the IPv6 communications protocol, the Neighbor Discovery protocol (ND) is what matches IPv6 addresses to MAC addresses. This section explains how ND works.
Refer to the online course to view this video.
IPv6 Neighbor Discovery Messages (9.3.2)
IPv6 Neighbor Discovery protocol is sometimes referred to as ND or NDP. In this book, we refer to it as ND. ND provides address resolution, router discovery, and redirection services for IPv6 using ICMPv6. ICMPv6 ND uses five ICMPv6 messages to perform these services:
Neighbor Solicitation messages
Neighbor Advertisement messages
Router Solicitation messages
Router Advertisement messages
Redirect message
Neighbor Solicitation and Neighbor Advertisement messages are used for device-to-device messaging such as address resolution (similar to ARP for IPv4). Devices include both host computers and routers, as shown in Figure 9-11.
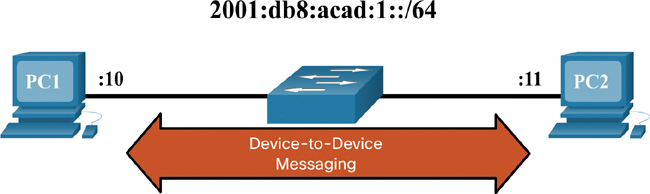
Figure 9-11 Device-to-Device Messaging
Router Solicitation and Router Advertisement messages are for messaging between devices and routers. Router discovery is typically used for dynamic address allocation and stateless address autoconfiguration (SLAAC).
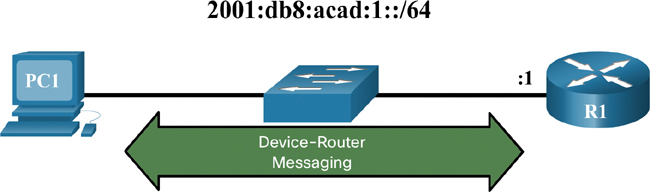
Figure 9-12 Device–Router Messaging
Note
The fifth ICMPv6 ND message is a redirect message that is used for better next hop selection. This is beyond the scope of this book.
IPv6 ND is defined in IETF RFC 4861.
IPv6 Neighbor Discovery—Address Resolution (9.3.3)
Much as with ARP for IPv4, IPv6 devices use IPv6 ND to determine the MAC address of a device that has a known IPv6 address.
ICMPv6 Neighbor Solicitation and Neighbor Advertisement messages are used for MAC address resolution. This is similar to ARP requests and ARP replies used by ARP for IPv4. For example, say that PC1 wants to ping PC2 at IPv6 address 2001:db8:acad::11. To determine the MAC address for the known IPv6 address, PC1 sends an ICMPv6 Neighbor Solicitation message, as illustrated in Figure 9-13.
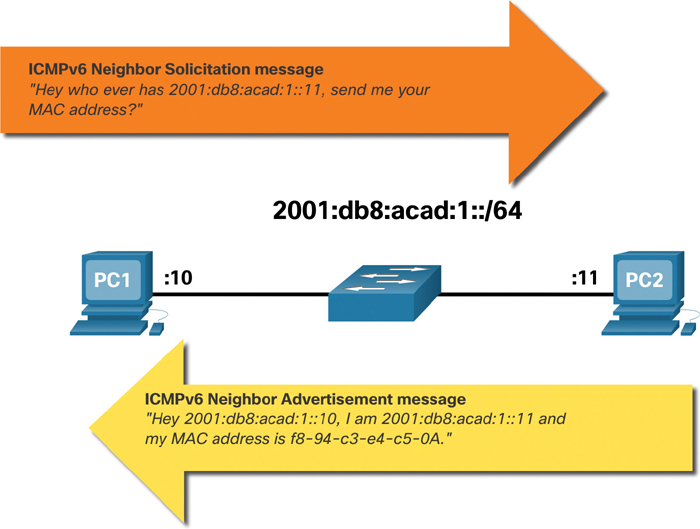
Figure 9-13 IPv6 Neighbor Discovery Process
ICMPv6 Neighbor Solicitation messages are sent using special Ethernet and IPv6 multicast addresses. This allows the Ethernet NIC of the receiving device to determine whether the Neighbor Solicitation message is for itself without having to send it to the operating system for processing.
PC2 replies to the request with an ICMPv6 Neighbor Advertisement message, which includes its MAC address.
Packet Tracer—IPv6 Neighbor Discovery (9.3.4)

For a device to communicate with another device, the MAC address of the destination device must be known. With IPv6, a process called Neighbor Discovery is responsible for determining the destination MAC address. In this activity, you will gather PDU information in simulation mode to better understand the process. There is no Packet Tracer scoring for this activity.
Refer to the online course to complete this activity.
Check Your Understanding—Neighbor Discovery (9.3.5)

Refer to the online course to complete this activity.
Summary (9.4)
The following is a summary of the topics in the chapter and their corresponding online modules.
MAC and IP
Layer 2 physical addresses (that is, Ethernet MAC addresses) are used to deliver the data link frame with the encapsulated IP packet from one NIC to another NIC on the same network. If the destination IP address is on the same network, the destination MAC address is the address of the destination device. When the destination IP address (IPv4 or IPv6) is on a remote network, the destination MAC address is the address of the host default gateway (that is, the router interface). Along each link in a path, an IP packet is encapsulated in a frame. The frame is specific to the data link technology associated with that link, such as Ethernet. If the next hop device is the final destination, the destination MAC address is the address of the device’s Ethernet NIC. How are the IP addresses of the IP packets in a data flow associated with the MAC addresses on each link along the path to the destination? For IPv4 packets, this association is done through a process called ARP. For IPv6 packets, the process is ICMPv6 ND.
ARP
Every IP device on an Ethernet network has a unique Ethernet MAC address. When a device sends an Ethernet Layer 2 frame, it contains two addresses: destination MAC address and source MAC address. A device uses ARP to determine the destination MAC address of a local device when it knows its IPv4 address. ARP provides two basic functions: resolving IPv4 addresses to MAC addresses and maintaining a table of IPv4-to-MAC address mappings. The ARP request is encapsulated in an Ethernet frame using header information about the source and destination MAC addresses and type. Only one device on a LAN has an IPv4 address that matches the target IPv4 address in the ARP request. All other devices do not reply. An ARP reply contains the same header fields as a request. Only the device that originally sent the ARP request receives the unicast ARP reply. After the ARP reply is received, the device adds the IPv4 address and the corresponding MAC address to its ARP table. When the destination IPv4 address is not on the same network as the source IPv4 address, the source device needs to send the frame to its default gateway. This is the interface of the local router. For each device, an ARP cache timer removes ARP entries that have not been used for a specified period of time. Commands may also be used to manually remove some or all of the entries in the ARP table. As a broadcast frame, an ARP request is received and processed by every device on the local network, which could cause the network to slow down. A threat actor can use ARP spoofing to perform an ARP poisoning attack.
Neighbor Discovery
IPv6 does not use ARP; rather, it uses the ND protocol to resolve MAC addresses. ND provides address resolution, router discovery, and redirection services for IPv6 using ICMPv6. ICMPv6 ND uses five ICMPv6 messages to perform these services: Neighbor Solicitation, Neighbor Advertisement, Router Solicitation, Router Advertisement, and Redirect. Much as with ARP for IPv4, IPv6 devices use IPv6 ND to resolve the MAC address of a device to a known IPv6 address.
Practice
The following activities provide practice with the topics introduced in this chapter. The lab is available in the companion Introduction to Networks Labs & Study Guide (CCNAv7) (ISBN 9780136634454). The Packet Tracer activity instructions are also provided in the Labs & Study Guide. The PKA files are available in the online course.
Packet Tracer Activities

Packet Tracer 9.1.3: Identify MAC and IP Addresses
Packet Tracer 9.2.9: Examine the ARP Table
Packet Tracer 9.3.4: IPv6 Neighbor Discovery
Check Your Understanding Questions
Complete all the review questions listed here to test your understanding of the topics and concepts in this chapter. The appendix “Answers to ‘Check Your Understanding’ Questions” lists the answers.
1. When a host has an IPv4 packet sent to a host on a remote network, what address is requested in the ARP request?
the IPv4 address of the destination host
the IPv4 address of the default gateway
the MAC address of the default gateway, the router interface closest to the sending host
the MAC address of the switch port that connects to the sending host
2. How does the ARP process use an IPv4 address?
to determine the MAC address of the remote destination host
to determine the MAC address of a device on the same network
to determine the amount of time a packet takes when traveling from source to destination
to determine the network number based on the number of bits in the IP address
3. Which of the following does the ARP table in a switch map together?
Layer 3 address to a Layer 2 address
Layer 3 address to a Layer 4 address
Layer 4 address to a Layer 2 address
Layer 2 address to a Layer 4 address
4. What is one function of the ARP protocol?
obtaining an IPv4 address automatically
mapping a domain name to its IPv4 address
resolving an IPv4 address to a MAC address
maintaining a table of domain names with their resolved IPv4 addresses
5. Which router component holds the routing table, ARP cache, and running configuration file?
RAM
Flash
NVRAM
ROM
6. What type of information is contained in an ARP table?
switch ports associated with destination MAC addresses
domain name-to-IPv4 address mappings
routes to reach destination networks
IPv4 address-to-MAC address mappings
7. A cybersecurity analyst believes an attacker is spoofing the MAC address of the default gateway to perform a man-in-the-middle attack. Which command should the analyst use to view the MAC address a host is using to reach the default gateway?
ipconfig /all
route print
netstat -r
arp -a
8. What is a function of ARP?
resolving known MAC addresses to unknown IPv4 addresses
resolving known port addresses to unknown MAC addresses
resolving known MAC addresses to unknown port addresses
resolving known IPv4 addresses to unknown MAC addresses
9. What is the purpose of ARP in an IPv4 network?
to forward data onward based on the destination IP address
to obtain a specific MAC address when an IP address is known
to forward data onward based on the destination MAC address
to build the MAC address table in a switch from the information this gathered
10. Which action does a Layer 2 switch take when it receives a Layer 2 broadcast frame?
It drops the frame.
It forwards the frame out all ports except the port on which it received the frame.
It forwards the frame out all ports that are registered to forward broadcasts.
It forwards the frame out all ports.
11. Which destination MAC address is used in an ARP request?
0.0.0.0
255.255.255.255
FFFF.FFFF.FFFF
127.0.0.1
01-00-5E-00-AA-23
12. What is the destination MAC address of an ICMPv6 Neighbor Solicitation message?
multicast
unicast
broadcast
anycast
13. What does a Layer 2 switch do when the destination MAC address of a received frame is not in the MAC table?
It initiates an ARP request.
It broadcasts the frame out all ports on the switch.
It notifies the sending host that the frame cannot be delivered.
It forwards the frame out all ports except the port on which the frame was received.
14. Which two ICMPv6 messages are used during the Ethernet MAC address resolution process? (Choose two.)
Router Solicitation
Router Advertisement
Neighbor Solicitation
Neighbor Advertisement
Echo Request