In IT in the early 1990s, just about every LAN used 10baseT hubs. The ones that did not were still using 10base2 with BNC coax connectors, and you had to restart all the hosts if you wanted to add a new machine to the network. Hubs brought us a great amount of flexibility by allowing us to add hosts dynamically with less downtime. As the number of hosts and network interface speeds increased, the total bandwidth exceeded the capability for a single hub, and we all started upgrading our LANs to Ethernet switches.
The basic problem of capturing packets on a switched network, as opposed to a hub, is that the Ethernet frames are not copied to every port on the switch. For example, if host A is plugged into switch port 1 and needs to talk to host B on port 2, the switch sets up a temporary electrical connection between port 1 and port 2. Once the switch creates the connection, the network conversation is relatively private. The switch does this by maintaining a list of which hosts are plugged into which switch ports and uses their MAC addresses to uniquely identify them.
One way to listen to a network conversation is to falsely identify yourself to the other computers on the network and convince them that you are the machine to which they wish to talk. This technique is referred to as ARP spoofing (also known as ARP poisoning) and is the method ettercap and arpspoof use.
You can get ettercap at (http://ettercap.sourceforge.net) and arpspoof (part of the dsniff package) at http://monkey.org/˜dugsong/dsniff.
The command-line switches for ettercap are well documented in the included manual page, so I will simply point out some of the ones I use the most. I tend to run ettercap on a command line as opposed to using the curses or GTK+ interface because I like to script my tools as much as possible, as well as redirect output to other programs, such as perl scripts or the old reliable sed, grep, and awk. I will occasionally show the GTK+ or curses interfaces to highlight some functionality when necessary.
When run at the command line in text mode, ettercap places the default interface into promiscuous mode and shows you packet data for all packets it sees. Use the -q option in conjunction with the -T (text mode) option to quiet things down:
[lou@duodenum] ettercap -TqNow ettercap displays only status messages and help text.
To quickly sniff all hosts within your subnet, use the following command:
[lou@duodenum] ettercap -T -M arp:remote //You should see something similar to:
ettercap NG-0.7.3 copyright 2001-2004 ALoR & NaGA Listening on eth1... (Ethernet) eth1 -> 00:0A:5E:02:3B:B3 10.0.0.3 255.255.255.0 Privileges dropped to UID 65534 GID 65534... 28 plugins 39 protocol dissectors 53 ports monitored 7587 mac vendor fingerprint 1698 tcp OS fingerprint 2183 known services Randomizing 255 hosts for scanning... Scanning the whole netmask for 255 hosts... 2 hosts added to the hosts list... ARP poisoning victims: GROUP 1 : ANY (all the hosts in the list) GROUP 2 : ANY (all the hosts in the list) Starting Unified sniffing... Text only Interface activated... Hit 'h' for inline help
The -M option sets the man-in-the-middle (MITM) mode. Other MITM options (other than arp) include icmp, dhcp, and port. Some of the other MITM modes are covered later in this chapter.
One of the best parts of running ettercap on a subnet is that you receive a list of machines and you get it fast. Running a host scan with an ancient Pentium 3 on a 100 Mbit network, you can expect to scan a class C subnet in about seven seconds.
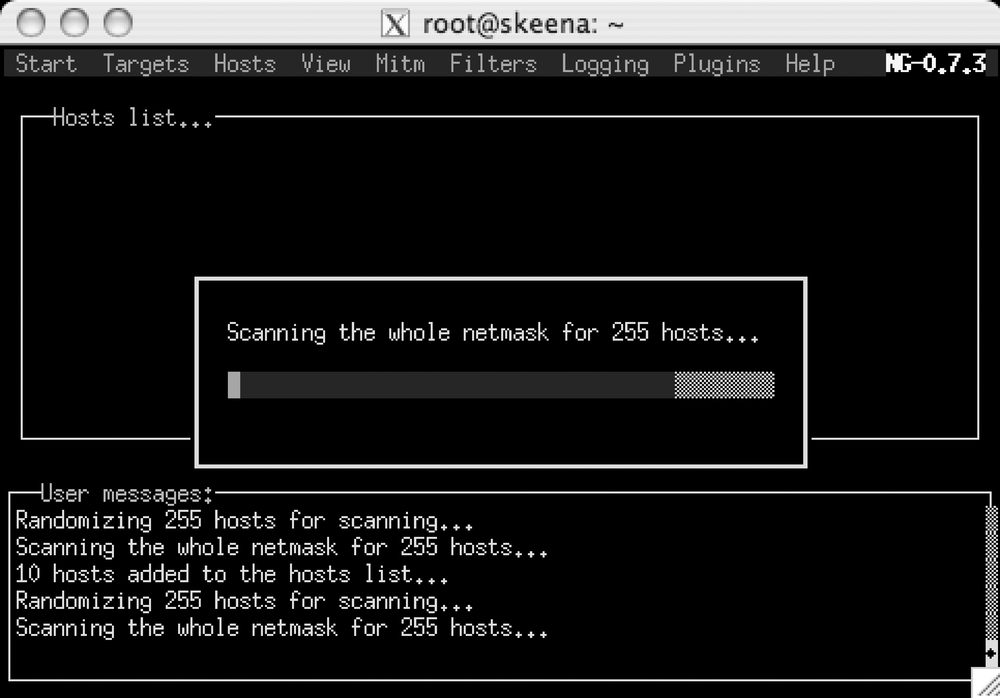
If you are running ettercap in curses mode, you can start a scan either by using the menu or through the keyboard shortcut Ctrl-S, as shown in Figure 4-1.
A host scan floods the network with ARP packets and inserts your sniffer's MAC address as the destination MAC for all traffic. Many networks have some kind of ARP monitoring enabled, but surprisingly, many do not—maybe because network administrators that run monitoring tools such as snort are constantly deluged with false-positives and they eventually stop looking. Because a lot of common network misconfigurations can cause the occasional short-lived ARP storm, too many administrators stop considering it a threat.
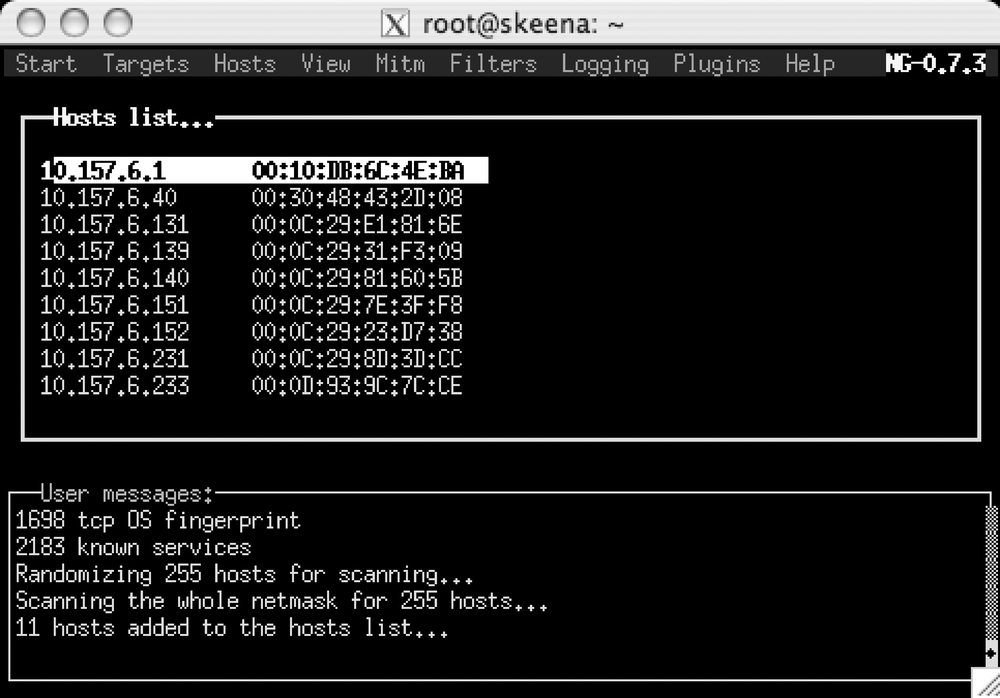
Once the host scan is complete, press the H key to display the results, including the MAC addresses, as shown in Figure Figure 4-2.
Now, to poison the ARP caches of all the listed hosts, set the man-in-the-middle mode to ARP by selecting Mitm → Arp poisoning. If the keyboard focus is on one of the other windows, tap the Tab key until the menu bar is highlighted. Figure 4-2 shows that the host list has the current focus.
arpspoof is much simpler than ettercap to redirect packets. The syntax is:
[lou@duodenum] arpspoof [ -i<interface>] [ -t<target>]intercepted-host
Specifying the interface is optional; the default is used if the option is omitted. If the target option is omitted, then all hosts on the LAN are fooled into thinking the sniffer is the intercepted host. Some people believe that the intercepted host should be the default gateway, but in my experience, some of the most interesting traffic (and cleartext passwords, by the way) can be found inside the LAN itself, going from host to host.
arpspoof uses the same ARP Reply technique as ettercap does, but one crucial difference between the programs is that arpspoof does not handle any packet forwarding, so if you forget to turn on IP forwarding in your kernel or use some other method of forwarding packets, the connections you sniff are half-duplex.