Airpwn requires two types of configuration: command-line arguments that specify network interfaces and other options, and a configuration file that specifies the request/response data for injection. Once Airpwn is running, it sits quietly waiting for packets matching the configuration to arrive. When a matching packet arrives, it sends the configured response back to the client and continues to wait for more matching packets. Essentially, there are three stages to the process:
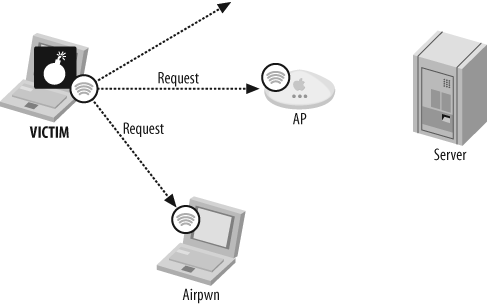
Figure 8-1 shows Stage 1, in which the victim client sends a request packet across the wireless network. That packet is received by both the access point (AP) and Airpwn.
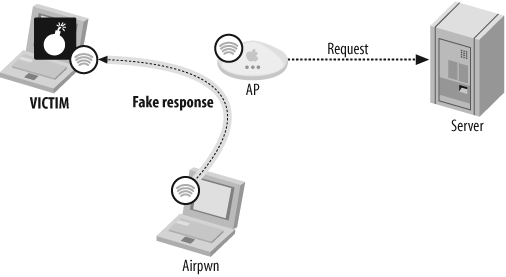
Figure 8-2 shows Stage 2, in which Airpwn sends a fake response back to the victim client. That response appears to be from the AP. Meanwhile, the AP forwards the request on to the server.
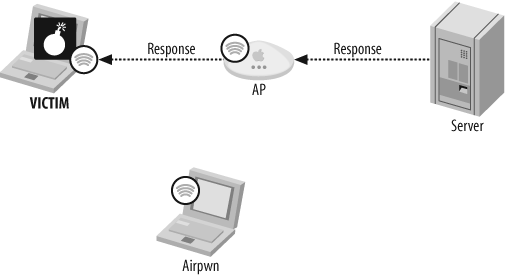
Figure 8-3 shows Stage 3, in which the server's response is returned and relayed to the client by the AP, but it's too late; the data provided by Airpwn has already been accepted, so the real response gets discarded.
Airpwn is not limited to a particular wireless network (ESSID); it works for all networks it is capable of seeing. However, it is limited to listening to one channel at a time. By default, Airpwn listens on the channel your wireless card is set to prior to running Airpwn. To change channels, you can type the channel number into the Airpwn session, and then press Enter.
Airpwn accepts the following command-line options:
-cconfiguration fileSpecifies the configuration file that contains the request/response data. The syntax of the configuration files is covered in Basic Airpwn Usage.
-ddriver nameInforms Airpwn of the wireless driver currently loaded for your wireless interface hardware. Airpwn uses the LORCON wireless library to interface with the hardware, so Airpwn supports any drivers that LORCON supports. To see the list of supported drivers, run Airpwn with the
-hoption.-Minterface nameSelects an interface for monitoring. The monitor interface is the one Airpwn sniffs looking for request patterns.
-Cinterface nameSelects an interface for sending control operations. Currently, the only control commands sent to the interface are channel change commands.
-Iinterface nameSelects an interface to use for packet injection. When a request pattern is matched from the monitoring interface, the response packet is sent out on this interface.
Airpwn allows you to specify the control, monitor, and injection interfaces separately because some wireless drivers do not allow monitoring and raw packet injection on the same interface. For example, the madwifi driver requires you to create a separate pseudointerface for packet injection that you cannot monitor on. If your driver allows you to monitor, control, and inject on the same interface, you can use the
-ioption to set all three interfaces to the same value.-iinterface nameSets the monitor, control, and injection interfaces to the same value. For example,
-i wifi0is equivalent to-M wifi0 -I wifi0 -C wifi0.-llogfileInstructs Airpwn to log data about injected content to the logfile specified. This provides a useful log of which IP addresses had data injected to them and when the injection occurred.
-ffilter expressionSets a BPF filter on the monitor interface. This can be used to limit pattern matches to specific IP addresses or TCP ports (or anything else a BPF filter lets you specify).
-kWEP keyAdds a WEP key to the list of keys with which Airpwn tries to decrypt encrypted packets. Multiple keys can be specified, and each is tried in turn. This allows Airpwn to work on multiple encrypted networks at once. To learn more about using Airpwn on WEP-encrypted networks, see Airpwn Configuration Files.
-mMTU in bytesSets the interface's maximum transmission unit (MTU) to a custom size for the injection interface. You need only to set this if you are injecting more data than will fit in a single frame (typically around 1,400 bytes).
Warning
Injecting more than one frame (for example, sending more than 1,400 bytes of response data) may not work well, depending on your wireless card and driver. In general, injecting a single frame of data is the most reliable way to use Airpwn.
-FInforms Airpwn that a Frame Check Sequence (FCS) is present at the end of WEP-encrypted frames. Airpwn cannot tell if an FCS is present or not, which can cause WEP decryption to fail. If you know you are providing the correct WEP key and Airpwn is not functioning properly, try setting or unsetting the
-Fflag.-vIncreases the verbosity setting. The more you specify the
-vflag, the more verbose the output becomes. Typing-vfour times, for example, prints out a message for every wireless packet seen by the monitor interface (this can be useful for verifying that Airpwn is seeing wireless packets).-hPrints out a help screen that includes a list of supported drivers.