Core Impact is a suite of automated penetration-testing tools. Its biggest advantage is its user friendliness. It allows most network administrators to perform basic penetration-testing tasks without needing to code in assembly language or even compile an exploit. It is truly the drag-and-drop of network exploitation. Core Impact also provides a good exploitation framework, but due to its GUI interface, it does lack some of the flexibility found in similar tools. In some cases, the GUI and hardware requirements of Core Impact become its biggest weakness. Core Impact is based on an agent technology (agent being a program install on a system you compromised). This allows deep penetration of network and good control of the target either for local tasks or for attacking other targets from an already compromised host.
Tip
A covert way to perform a penetration test with an exploit framework could involve putting all your tools on a PDA, installing the PDA in the target network, and using that PDA as your attack platform. This is sometimes a very good way to bypass the first line of defense. However, these kinds of attacks are hard to achieve with GUI-only tools such as Core Impact, since you need a full PC rather than a PDA to run these tools. However, other GUI-driven tools (such as Immunitysec CANVAS) can be modified to run reliably on a PDA.
Core Impact's GUI is divided into six windows by default, containing the information pertinent to penetration testing. The GUI uses drag-and-drop; to run an exploit, you can just drop it over a host or a network. The GUI window is shown in Figure 9-1.
The default window is divided into several sections:
- Current inventory of known systems
Shows a list of known systems or subnetworks. If Core Impact identifies too many hosts from the same subnet, it aggregates them to show a network node.
- History of completed modules
Shows a list of modules that have already been run. This list is useful to reports the sequence of events that occur during the test.
- Log and debug windows for the current module
Allows you to check that execution occurred as planned. This is very useful when writing new exploits.
- Current system properties
Provides information about a specific host from the inventory. You can also use this window to change the properties of a host (OS version, open port, note, and users).
- Quick information about the current module
Supplies information about the module you are going to run: functions, limitations, possible tweaks, and effects on the system.
By default, Core Impact expects to be connected directly to the network. If you are running behind a NAT gateway, the only way to get Core Impact working for the callback is to set the parameters in the console (Open Tools → Options → Nat). If the values are not properly set, the agent won't be able to reach the callback address.
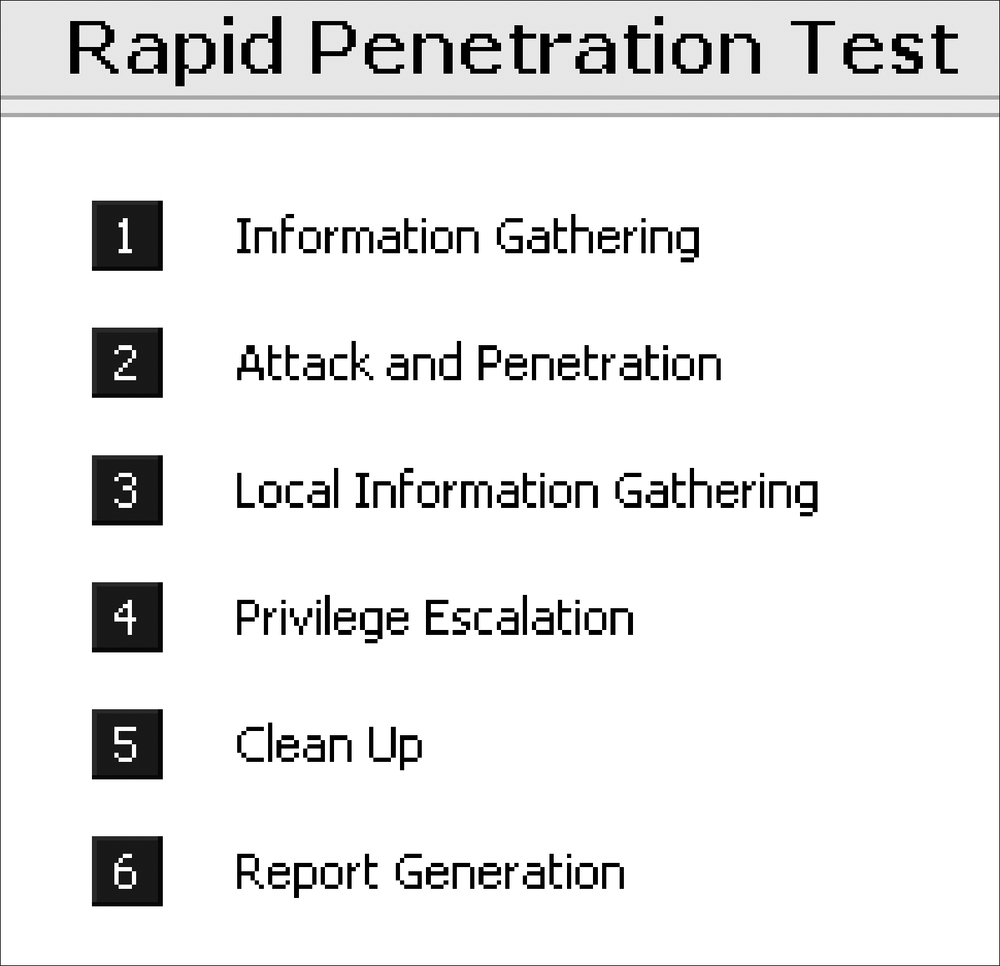
Core Impact allows you to do automatic network penetration testing (the program calls it Rapid Penetration Testing, or RPT). This method of attacking the network, while easy and wizard-based, is also very noisy on the network and not necessarily complete. Figure 9-2 shows the basic steps for penetration testing. Each step is wizard-based and uses the information acquired from the previous step. As you might imagine, the steps need to be performed in numerical order; however, steps one through four can be repeated multiple times to ensure the full depth of the target network is reached. Before repeating these steps, be sure to set the wanted agent (the compromised system) as source.
While the Rapid Penetration Testing is an easy way to perform a network assessment, it cannot replace an experienced penetration tester. RPT provides a quick demonstration of Core Impact's power and user friendliness, but it should not be used while defeating a defense system during real penetration testing, when the goal is to leave as little trace as possible. This automated system is not very covert and will trigger most defense systems.
Another issue that turns up when using RPT is that you can easily end up rooting more systems than necessary for the penetration test, putting your network stability in jeopardy; even if most exploits are stable, a single error can cause a denial of service of one or even multiple systems, potentially bringing down the whole network. While this might seen like a normal thing to happen during a penetration test, most CSOs and CEOs do not see it that way and do not always consider downtime for shoring up security a valid compromise.
RPT can also lull you into a sense of overconfidence; if you run the RPT module and find nothing on your network, that doesn't necessarily mean your network is safe. The way Core Impact is designed, a single misinterpretation of information can disable multiple exploits. For example, if a host is identified as Windows 2003 but it's really Windows 2000, you need to run a different set of exploits, and the penetration testing results will not be accurate.
Core Impact is a wonderful tool, but as with any tool, the hands that use it are still very important. Modules such as RPT allow a network administrator with a basic understanding of security to perform simple penetration testing; however, Core Impact in the right hands can accomplish much more.