Running a specific exploit in Core Impact against a machine is as simple as a drag-and-drop operation. All you have to do is verify that Core Impact has completely identified the relevant OS, version, and advance features. The OS version is very important; Core Impact uses that information to craft the needed exploit with a good return address.
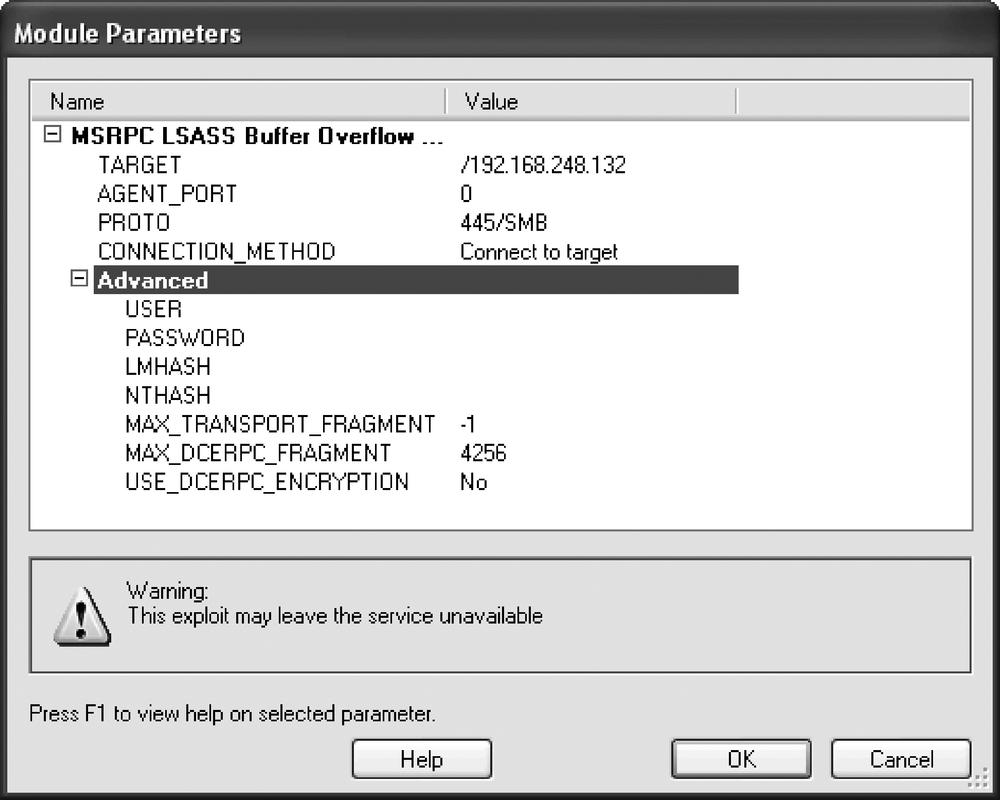
Figure 9-4 shows some of the options available when launching an exploit. The Advanced sections allow the user to set account information, fragmentation, and encryption. Adding such information is optional, but it can improve the exploit success rate.
By default, Core Impact tries to help the user by limiting the available exploits, so only the ones affecting the relevant platforms are available. However, due to the statistical nature of the identification process, Core Impact sometimes wrongly identifies a host. It is possible to remove this feature and drop all modules, whatever the platforms. To do so, go to Tools → Options → Views → Entity, and then select the checkbox "Allow dropping module over unsupported platforms." This allows you to search for any module.
By making all modules available, you run the danger of choosing an ineffective exploit. When you run an exploit over unsupported platforms, there is the risk that the exploit will not perform as planned by the software. For example, if only a small rebase is done between two versions of a similar exploit (i.e., each intended for a different OS version), it is possible that the exploit can become a denial of service instead, or just simply do nothing.
The module-selecting feature is especially useful when you are only interested in a sample of what a typical attack could look like; for instance, allowing you to recreate the communication of an attack without a proper reconnaissance phase, which would require having the exact vulnerable setup.