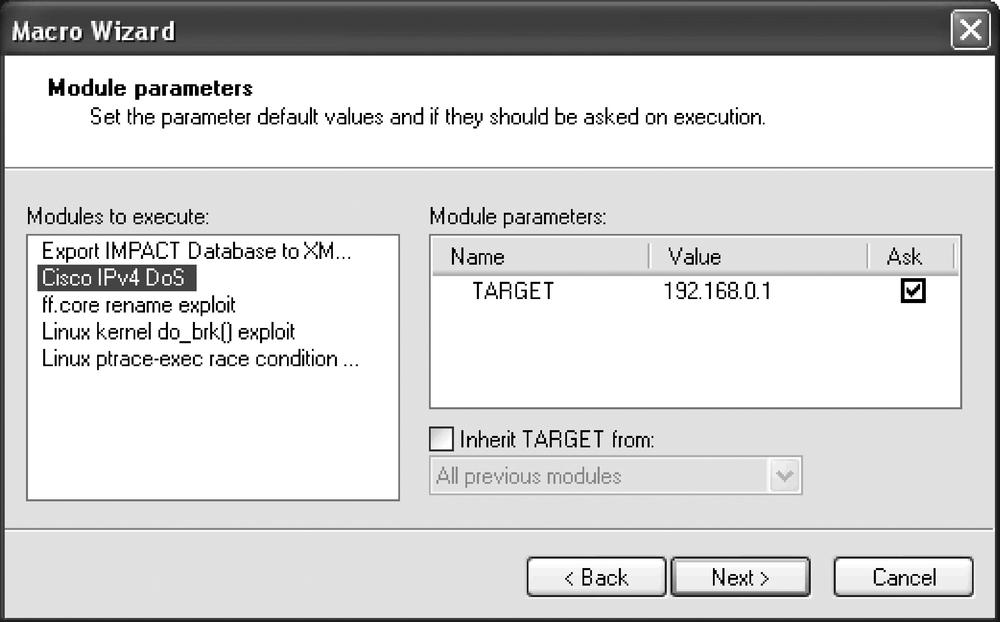
To run automated repetitive tasks, Core Impact provides a macro language and a Wizard to help you develop macro scripts. Figure 9-5 shows the Macro Wizard, which allows you to consolidate sequences of repetitive tasks into one task. Those tasks can include discovery, scans, tests for one specific vulnerability, post intrusions, root kit uploads, installs, and agent cleanup. The Macro Wizard also allows you to use information discovered in previous modules to pass the information to the new macro.
Since all submodules in Core Impact are written in Python, modifications and improvements are easy to achieve with a little knowledge of Python. The following code is a snippet of Python code that could be used as a macro. Since Python provides full language modification, adding logic is easy to implement with a little basic programming:
try:
OSDetectbyDCERPCEndpointMapper1 =
ModuleManager.getModuleEntity("OS Detect by
DCE-RPC Endpoint Mapper")
# Choosing which module to run
self.setInstance(OSDetectbyDCERPCEndpointMapper1)
OSDetectbyDCERPCEndpointMapper1.set_parameters(self.getParameters( ).
get( "OS Detect by DCE-RPC Endpoint Mapper", {}
))
#Getting the list of targets from previous modules
targets = self.getCommittedEntities( )
if len(targets) == 0: # if no target
raise Exception("No entities/hosts discovered")
OSDetectbyDCERPCEndpointMapper1.set_target_list( getEntityNa
mes(targets) ) #setting the list of target for this module.
self.getAgent( ).run(OSDetectbyDCERPCEndpointMapper1,
[(modulecb.Event.POST_COMMIT,
self.ourCBHandler)] )#Running the module.
self.commitChild( )
except Exception, e: # Exception handler
self.logHi( 'Error running module: OS Detect by DCE-RPC Endpoint Mapper')
self.logHi( 'Exception: %s' % str(e) )
#raiseA successful exploitation with Core Impact ends with the installation of an agent Level 0 on the target host. Once an agent is installed, several different tasks can be performed. The first consists of information gathering on the local side. It is important to know as much as possible about the host on which you are running. For local information gathering, Core Impact has a multitude of modules that provides functionality equivalent to the ps command, a screenshot grabber, audio capture (Windows only), password retrieval, and key logger. The information gathered can be very useful for performing deeper attacks, including the installation of a Level 1 agent or even a full rootkit.
Being able to gather a lot of information locally can provide insight about the anti-virus software and backup solutions being used. This information can be very helpful when you want to install a persistent kernel rootkit that cannot be detected by the other network's anti-virus solution and that does not affect its backup system. Being able to keep your tracks hidden even after exploitation is important so that "administrators" won't try to fix the system, which would remove the links created by your chain of attack and break your entry point to a subsection of the network.
Since most services do not run in the kernel or as root on Unix-based systems, your newly installed agent will only have the rights of the process it just exploited. To bypass this restriction, you can use local exploits or other means (e.g., password sniffing) that will allow you to install an agent with greater privileges. The privilege escalation needed to install a Level 1 agent can be preformed automatically if the exploited process belongs to root or system; otherwise, you need to run some escalation before installing a Level 1 agent.
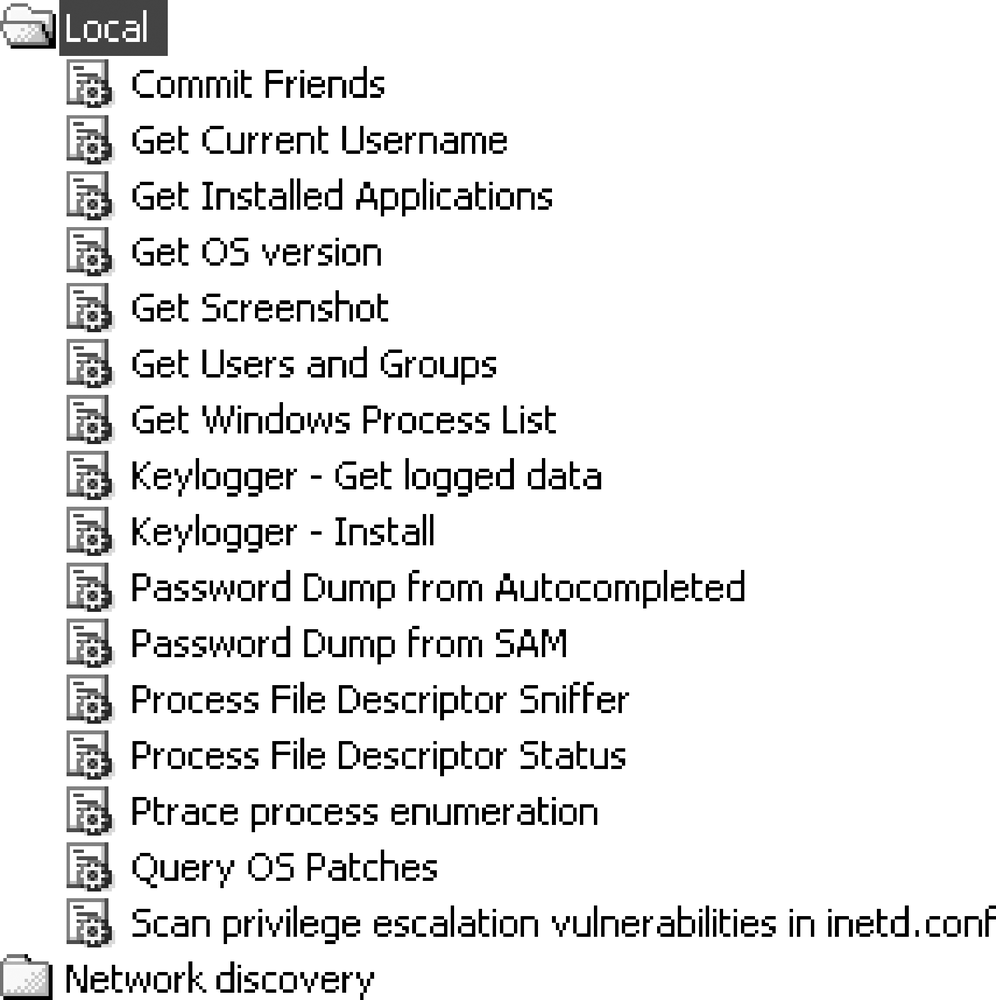
Figure 9-6 shows some of the possible tasks a local agent can perform; for example, discovering the exact version of the OS, grabbing the password file, getting lists of running processes, retrieving a list of users, and capturing screenshots.
Once installed, a Level 0 agent provides a mini-shell. Here are the commands currently available with the mini-shell:
cd [proxied_directory] lcd [local_directory] pwd cat proxied_filename rm proxied_filename cp src_proxied_filename dst_proxied_filename mv src_proxied_filename dst_proxied_filename get src_proxied_filename put src_local_filename ls [-l] id hostname execute remote_filename [arguments ....] exit help
While the functionality provided by the mini-shell is minimal, everything you need to perform deeper exploitation is included, such as the ability to install a full-blown remote administration solution and a rootkit.