Most computer network defense occurs at the border of the network, and often almost nothing is done internally. As the thinking goes, if you put in a firewall, you will be safe. Another way to look at this philosophy is to see it as a country with decent border control, but no cops inside. Bouncing off an internal host is equivalent to blackmailing someone already inside the network to carry out your requests. Security is mostly nonexistent at this point: the host/person is already trusted. Core Impact allows the attacker to perform tasks such as bouncing off a host and then continue attacking the network from within. To activate this feature, right-click on an already installed agent and select "Set as Source." From then on, all attacks/modules will originate from that specific host.
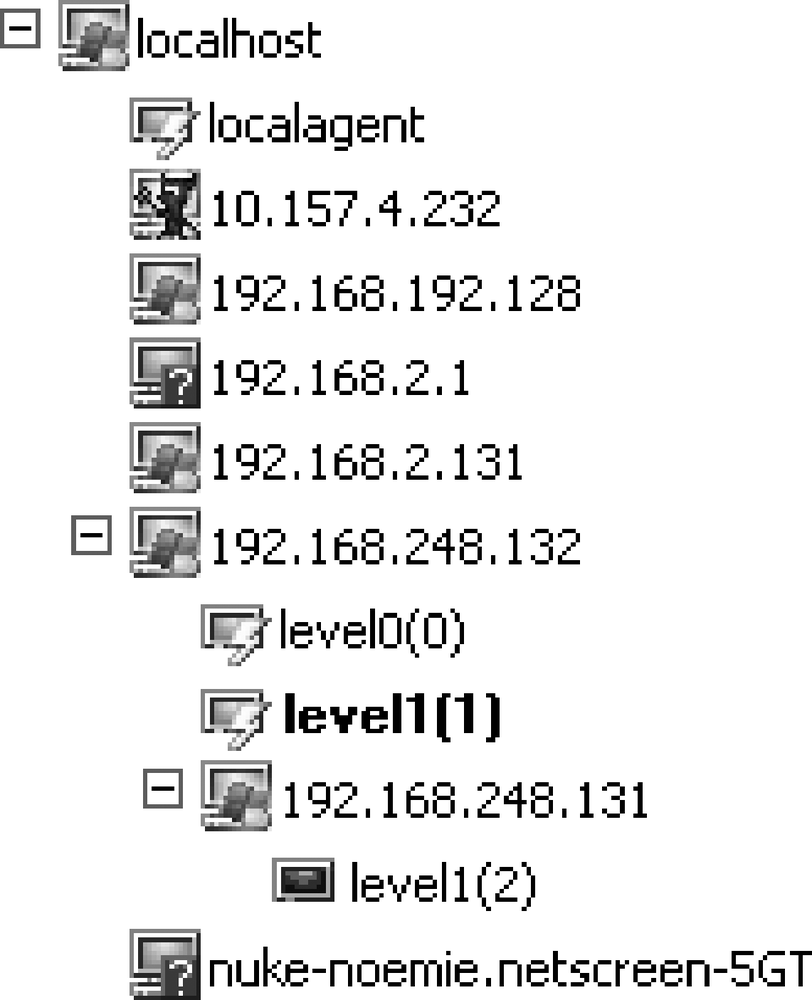
In Figure 9-7, you can see that the exploit runs from the host 192.168.248.132, since the Level 1 agent is now the active one (in bold); all attacks now occur as if the hacker host was 192.168.248.132.
Tip
The host tree in Figure 9-7 shows an example of an attack chain in which the local host can exploit 192.168.248.132 and use this host to attack 192.168.248.131 from within its subnet, as if the attack came from 192.168.248.132.