Let's create a no-frills backdoor to acquaint you with configuring both the client and server and some of the pitfalls involved in that process. Once you get a feel for it, we'll present some more advanced techniques later in the chapter.
First you need the latest BO2k package. At the time of this writing, I am using the bo2k_1-1-3.zip package from http://www.bo2k.com. For the time being, we are not interested in any of the plug-ins available there. Unzip the archive to a location of your choosing. We are interested in three files:
- bo2k.exe
The unconfigured server. Running this (after configuration) would infect the host with the backdoor. (If it is set it up to be particularly insidious, be careful—it could be tricky to remove.)
- bo2kcfg.exe
The server configuration utility does exactly that—it configures the server.
- bo2kgui.exe
The backdoor's client. Only the Windows version is included in this package, but there are clients for other platforms available.
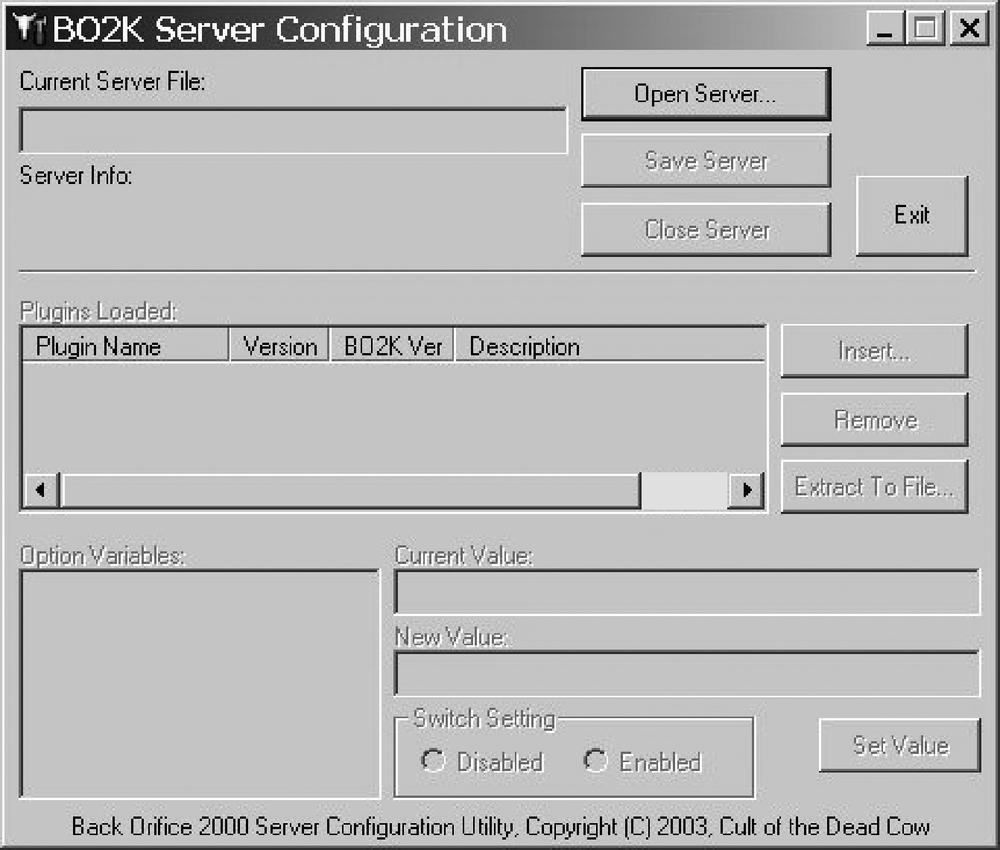
Use bo2kcfg.exe to load and configure the server. Upon running, a simple GUI displays the BO2k Server Configuration window shown in Figure 11-6.
The interface of the configuration window can best be examined if you split it into thirds horizontally. In the top third, you can load, unload, or save your current server configuration. In the middle, you can manage the plug-ins to be used by the loaded server. And in bottom third, you can cite specific server and plug-in variable management.
Tip
Now is a great time to make a copy of the fresh bo2k.exe server and rename it to something more fitting to the intended backdoor's purpose. When saving the configured server, you are not presented with the option to save to another file. Changes are made to the currently loaded server binary.
Clicking the Open Server button displays an open file dialog that you can select bo2k.exe or the copy of it that you just made. Once loaded, you can begin to manage plug-ins and server-side variables.
Now that our plug-in box and buttons are enabled, you can really customize the server. Even the most basic functionality in BO2k comes from plug-ins. This is really fantastic because it allows you to upgrade core components (e.g., the protocol or authentication) when something better or newer comes out, or if you find something more suitable to the backdoor's application.
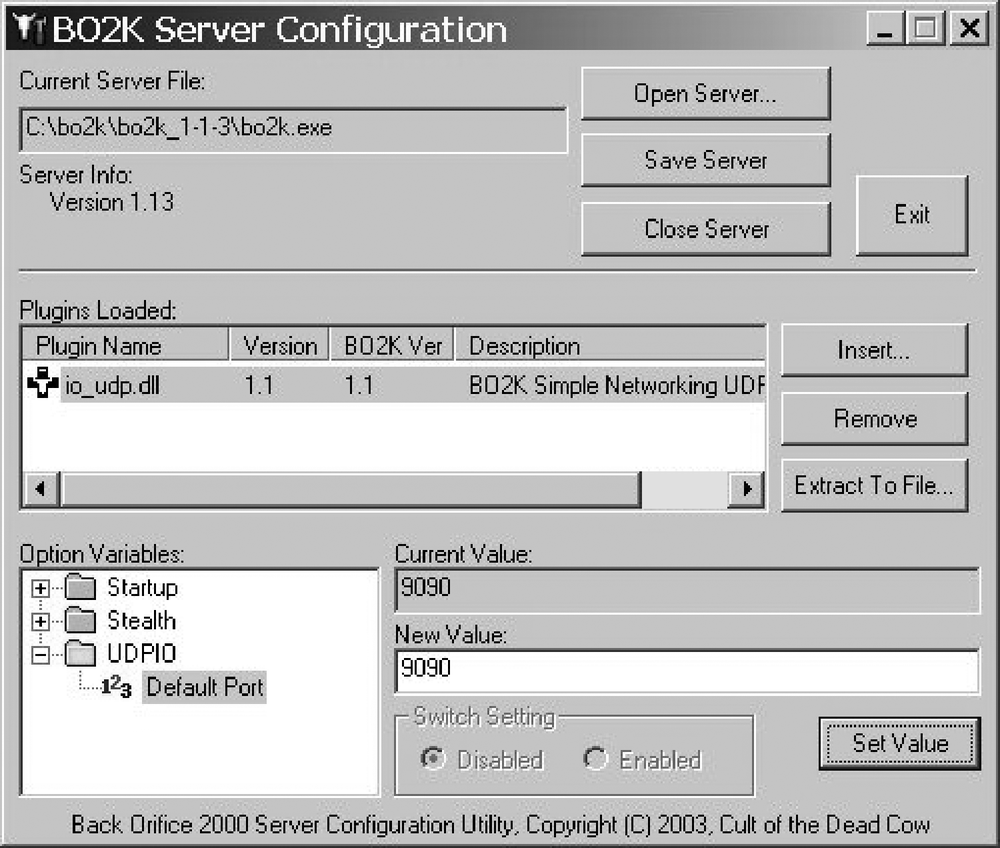
Clicking on the Insert . . . button displays a File Open dialog that allows you to choose a plug-in to load. In the default directory configuration (you may choose to change where you add your own plug-ins later), the plug-ins are loosely organized by type under the plug-ins subdirectory as shown in Figure 11-7. Navigate to plug-ins\io, select io_udp.dll, and click Open.
Tip
Make note of the cyan folder that appears in the Option Variables window after you inserted the io_udp.dll plug-in. This means that the plug-in you loaded contains variables that may need to be changed for it to function properly.
The Extract To File . . . button shown in the middle third of the dialog (Figure 11-7) deserves some special mention. It allows you to extract a plug-in that you might not have the original source for. Surely you can see the possibilities for this. Should you happen upon a system, with a BO2k backdoor already running on it, that just happens to have some neat custom plug-ins you have never seen before, this button makes filching them nice and easy.
With the creation of the UDPIO folder in the Option Variables field, you can now begin setting variables. Expand the cyan UDPIO folder to display the Default Port variable. Default Port, which takes a string, is one of two types of variables in BO2k. The other type takes a Boolean value that can be changed by clicking one of the radio buttons in the Switch Setting box.
Tip
The Set Value button to the right of the Switch Setting box need only apply when changing String values. Boolean variables are updated immediately.
Select Default Port and the value text boxes to the right of the Option Variables box become active (as they are in Figure 11-7). To update its value from the displayed Current Value, enter the new value into the New Value box and click the Set Value button.
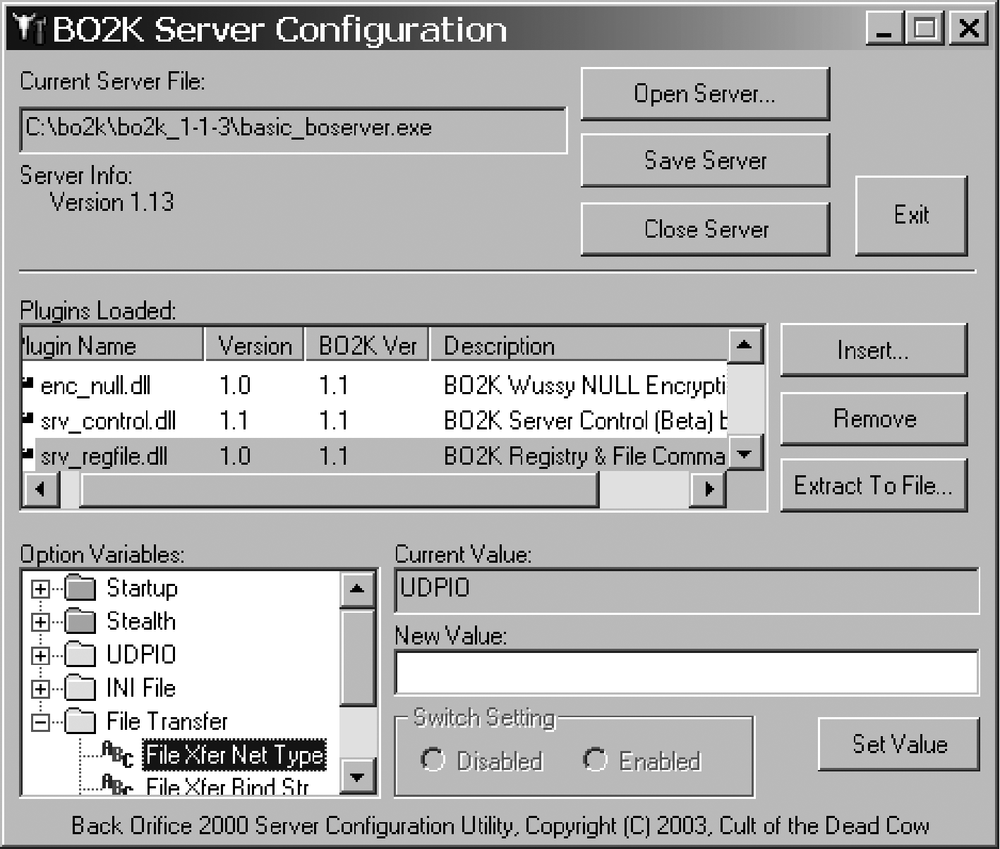
There is a set of absolute minimum requirements that must be met for the server to run. Three different types of plug-ins must be loaded, and a couple of related variables, native to the server, must be configured appropriately: an IO plug-in, an Authentication plug-in, and an Encryption plug-in. Control plug-ins, although not required for a minimum configuration, are also important. Figure 11-8 shows a fully loaded BO2K server, with the entire minimum configuration done.
For the server to be capable of any remote communication, an IO module must be loaded. This module and its associated variables are used to control parameters such as network protocol and port. The io_udp.dll plug-in does this and is found in plugins\io. Some additional variables must be configured:
- Default Port
The Default Port tells the UDPIO module what port to listen on.
- Init Cmd Net Type
Expand the Startup folder to modify this variable. This is where the server looks to figure out what IO module to use during startup. In this example, set its value to
UDPIO.- Init Cmd Bind Str
Expand the Startup folder to modify this variable. This variable must have its value set to match the Default Port value of the IO module that you selected. In this example, use
9090.
The downloaded BO2k package includes only a null plug-in to satisfy the encryption requirement. Now is the time to insert the enc_null.dll plug-in found in plugins\enc. (Later in this chapter, I cover using one of the much better encryption plug-ins available for BO2k.)
- Init Cmd Encryption
Expand the Startup folder to modify this variable. This should be set to the name of the encryption plug-in that you chose to use. Since you are using a null plug-in for this configuration, you can leave the value set to
NULL.
As with encryption, insert the supplied null plug-in. It is auth_null.dll, found under plugins\auth. (Although there aren't any auth plug-ins listed on the web site as of this writing, there are bound to be some eventually.)
- Init Cmd Auth
Expand the Startup folder to modify this variable. This should be set to the name of the Authentication that you use, which at this point can always be left to
NULLorNULLAUTH.
The server-side control plug-ins are not really part of the minimum configuration, but they deserve a quick mention here. The three previously mentioned plug-ins get us talking to the backdoor, but without any sort of control. Plug-ins aid our ability to do anything on the machine running the backdoor. The control plug-ins that are part of the BO2k core package are located in the plugins/srv directory. To make our very basic backdoor just a bit more useable, add some functionality by inserting these two plug-ins:
- srv_control.dll
Offers some basic backdoor control features, such as restarting the server or plug-in management.
- srv_regfile.dll
Allows full control over the registry and many very useful filesystem related utilities, including file transfer. srv_regfile.dll has several associated variables that may be tweaked to modify the behavior of the file transfer functions. See Figure 11-8.
Warning
Remember that all of the Init Cmd variables are set in accordance to the plug-ins that you have loaded. Discrepancies here will cause your backdoor to silently fail. Since it is designed as a backdoor, it will not throw errors like a legitimate application would in order to tell you when it is not functioning.
Before you finish, examine all of the variables and make sure that all of the features you are interested in are enabled. Some of the variables in the Stealth folder might be worth checking out. When messing around with new features or plug-ins, you should keep most of the stealth features disabled so that you can easily kill the server process, make changes, and then restart it. That gets tricky if the Hide Process and Insidious Mode variables are enabled.
Tip
Remember to save your server before closing the application! You are not prompted to do it upon exit.
Now that the server is configured, the client needs to be set up with some matching settings (see Figure 11-7). Then we have a fully functional backdoor.