It's Windows time. In general, rootkit tools on Windows are a bit more polished and technologically advanced than those available for Unix. The main reason is probably due to the fact that there are more rootkits and rootkit technology on Windows than Unix (although this gap is getting smaller). The tools covered in the following sections mostly fall into the category of syscall output differencing technology. Good sources of information already exist about anti-virus and signature technologies as well as for file integrity checking. As for call monitoring, in my experience, they have not proven to be very effective and are difficult for the average user.
Rootkit Revealer from Sysinternal (http://www.sysinternals.com) is a tool that processes the differential results between API calls. While this technique is efficient at detecting most Windows rootkits, it is not 100 percent foolproof. Rootkits that do not hide and use API-call filtering are not detected by Rootkit Revealer.
Rootkit Revealer's output involves a simple list of hidden files or registries. This list can contain false positives, especially in the case where a file/registry changed during the scan. To minimize these false positives, follow Sysinternal's recommendation and close all applications before starting the scan. It is also possible to manually double-check the existence of the files. If the file or registry is not hidden from normal APIs such as Windows Explorer or Regedit, it is probably a false positive.
IceSword (http://pjf.blogone.net) is a utility that uses low-level kernel access to enumerate running services, open ports, registry keys, hooks, and process/thread creation. Using this technique, IceSword is able to bypass most rootkit stealth technologies and discover their presence. In a sense, IceSword is like Rootkit Revealer, but is used manually and is much more flexible.
By default, IceSword highlights differences between the normal high-level API calls (usually hooked by a rootkit) and the counterpart low-level calls. It is also allowed to kill such processes, and enumerate their files and registry keys. As such there are two warnings I must point out.
Warning
Using IceSword for the kill process is dangerous and may cause the system to crash. Since IceSword works at kernel level, everything is possible for this utility; no security restrictions apply or are checked. Always be cautious when using this software. Using a kernel debugger in conjunction with IceSword is not recommended.
IceSword information is split into three parts; function, registry, and files. The Function submenu is the most versatile. Table 12-7 lists the capabilities available under the Function menu.
Table 12-7. Functionality of IceSword
Function | Description |
|---|---|
Process | Hidden processes are marked in red. This subwindow allows the user to kill processes and threads, unload DLLs, and access (e.g., read or write) the process memory. |
Port | Displays hidden ports of system-level backdoors, as long as the port is opened by a Windows system call. |
Kernel Module | Kernel Module consists of Core modules loaded by the system—for example, the drivers. |
Startup | Lists modules that are started during boot. |
Win32 Services | Under Services, lists all registers, whether hidden or not. Hidden services are shown in red. |
SPI | Lists the service provider interface. |
BHO | Lists Browser Helper Objects that are extensions for Internet Explorer. A Browser Helper Object is a DLL that allows developers to customize and control Internet Explorer. |
SSDT | SSDT stands for System Service Descriptor Table. If the SSDT was changed, then that particular entry is indicated in red by IceSword. |
Message Hooks | Lists all registered information hooks in the system using the |
Log Process Creation | Thread creation information is stored in Cycle Buffer. The thread information is recorded only if the IceSword application is running. This information could be used to find which processes and threads have been created by the Trojan backdoor. |
Log Process Termination | Normally logs processes terminated by another one. It does not record when a process terminates itself. |
System Check | Currently under development; an attempt to automatically discover rootkits using other functionalities of IceSword. |
The Registry submenu includes the current registry table from raw access and the possibility to modify it (e.g., add or delete). The File submenu includes the current files from raw access and the possibility to modify them (e.g., copy or delete).
Tip
Remember that all operations done inside IceSword are implemented as if the kernel would do it itself, so it is possible to perform very dangerous tasks.
Let's go through the basics of discovering and killing a rootkit with IceSword. As always, it is safer to format and reinstall than to remove the rootkit, but that is not always possible. Follow these steps:
After reboot, launch IceSword (double-click the icon).
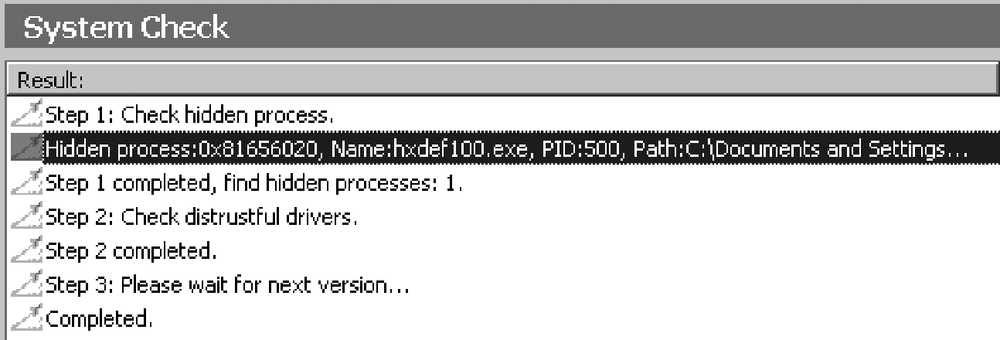
From the left pane, click "System check." See Figure 12-1. If the rootkit uses common features, this could be the last needed step to detect it.
If nothing is found, you can move to a more manual detection.
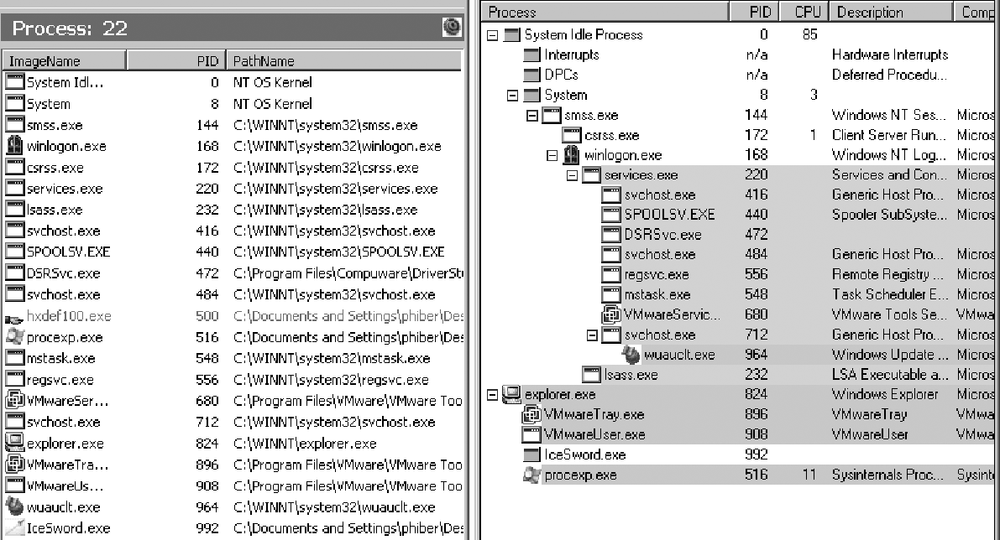
From the left pane, click on "process/services," as in Figure 12-2; at the same time, open ProcessExplorer (http://www.sysinternals.com) and compare the list of running processes. Processes present in IceSword but not in ProcessExplorer are usually hidden.
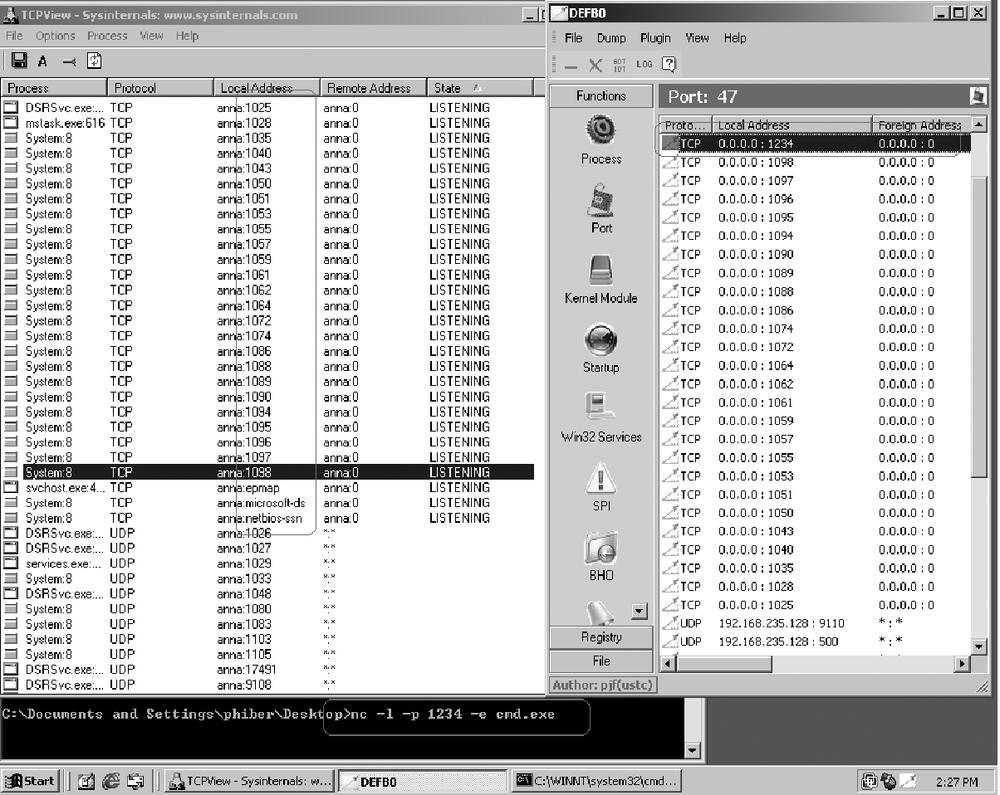
From the left pane, click on Ports; at the same time, open TcpView, as shown in Figure 12-3 (available from http://www.sysinternals.com) and compare the list of open ports. Ports present in IceSword but not in TcpView are usually hidden. It is possible for a rootkit to reuse already open ports, so the absence of open ports does not mean the absence of a remote backdoor.
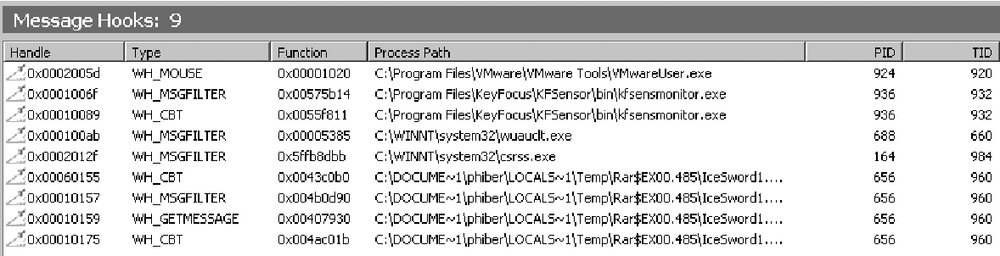
From the left pane, click on Hooks. As shown in Figure 12-4, this window gives the list of hooks. Look for any process or service that does an unusual hook for your current configuration. Saving this list from a base/clean install is a good idea.
From the left pane, click on Service Descriptor. As shown in Figure 12-5, this window gives the list of addresses. Look for any process or service that has an address that is unusual for your current configuration. Saving this list from a base/clean install will allow you to make comparisons to look for clues.
If the values in the current address do not match the values in the original address, this behavior is suspicious and should be looked at.
IceSword also provides a lot of other information about your system that could be used to pinpoint rootkit and abnormal behavior. Always try to differentiate the result provided by IceSword from the userspace-provided information to find what the rootkit is trying to hide.
If you feel comfortable enough and know exactly what infected your system, you may try to remove the rootkit files and startup configuration using the kill features in IceSword. IceSword allows the user to kill processes (hidden or not), stop services, and delete files and registry keys. It is best to thoroughly familiarize yourself with IceSword, rootkits, and performing backups before trying such a procedure.