Take a look at your system. Is it running 50 different processes you know nothing about? If we take some random Windows XP install and run netstat -aon inside a CMD window, what might we see?
Active Connections Proto Local Address Foreign Address State PID TCP 192.168.1.81:1292 64.191.197.245:706 ESTABLISHED 2160 TCP 192.168.1.81:1863 192.168.1.1:5819 ESTABLISHED 3828 TCP 192.168.1.81:1894 70.109.139.219:52525 ESTABLISHED 3828 TCP 192.168.1.81:1919 192.168.1.1:5819 ESTABLISHED 3828 TCP 192.168.1.81:1967 24.8.195.195:30809 ESTABLISHED 3828 TCP 192.168.1.81:1971 81.93.108.73:46123 ESTABLISHED 3828 TCP 192.168.1.81:1972 75.134.131.167:16470 ESTABLISHED 3828 TCP 192.168.1.81:2031 84.190.103.54:6881 ESTABLISHED 3828 TCP 192.168.1.81:2054 82.131.196.41:6881 ESTABLISHED 3828 TCP 192.168.1.81:2072 82.152.170.220:34683 ESTABLISHED 3828 TCP 192.168.1.81:2078 172.182.28.215:64649 ESTABLISHED 3828 TCP 192.168.1.81:2080 213.143.75.160:59429 ESTABLISHED 3828 TCP 192.168.1.81:2090 85.17.40.43:80 SYN_SENT 3828 TCP 192.168.1.81:63011 24.5.211.82:4041 ESTABLISHED 3828 TCP 192.168.1.81:63011 24.67.137.89:1599 ESTABLISHED 3828 TCP 192.168.1.81:63011 24.118.225.33:63230 ESTABLISHED 3828 TCP 192.168.1.81:63011 24.169.228.109:2066 ESTABLISHED 3828 TCP 192.168.1.81:63011 24.222.25.43:56807 TIME_WAIT 0 TCP 192.168.1.81:63011 60.22.249.185:2875 ESTABLISHED 3828 TCP 192.168.1.81:63011 60.48.218.169:3446 TIME_WAIT 0 TCP 192.168.1.81:63011 60.48.218.169:3465 TIME_WAIT 0 TCP 192.168.1.81:63011 60.48.218.169:3482 TIME_WAIT 0 TCP 192.168.1.81:63011 60.48.218.169:3499 TIME_WAIT 0 TCP 192.168.1.81:63011 60.48.218.169:3516 TIME_WAIT TCP 192.168.1.81:63011 60.48.218.169:3538 TIME_WAIT 0 TCP 192.168.1.81:63011 60.52.118.86:63233 LAST_ACK 3828 TCP 192.168.1.81:63011 62.150.137.115:35847 ESTABLISHED 3828 TCP 192.168.37.10:139 0.0.0.0:0 LISTENING 4
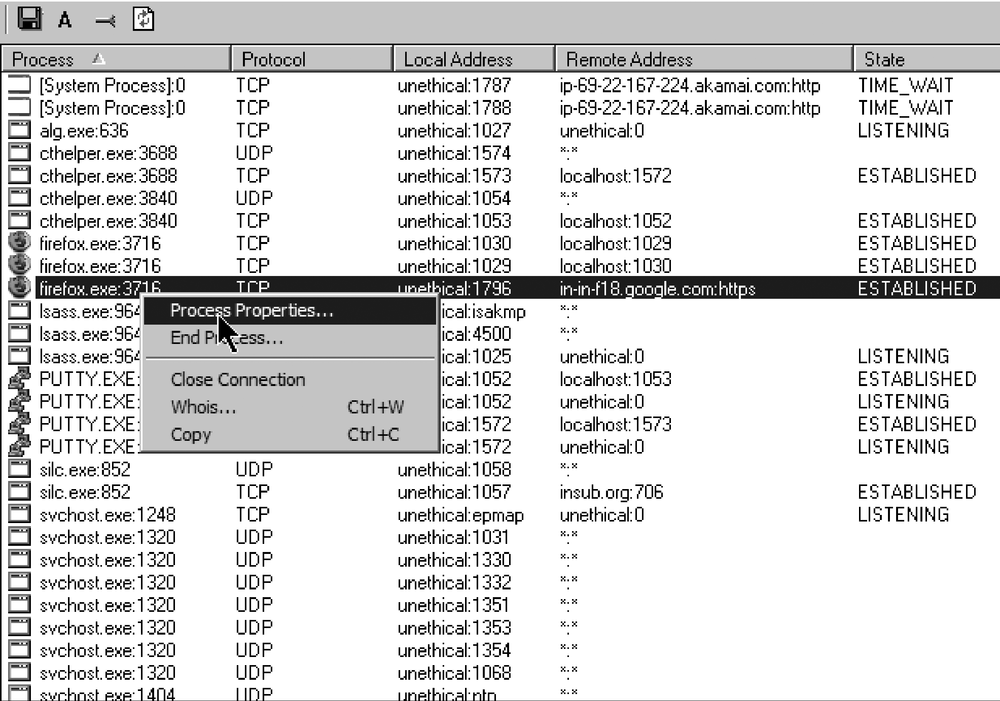
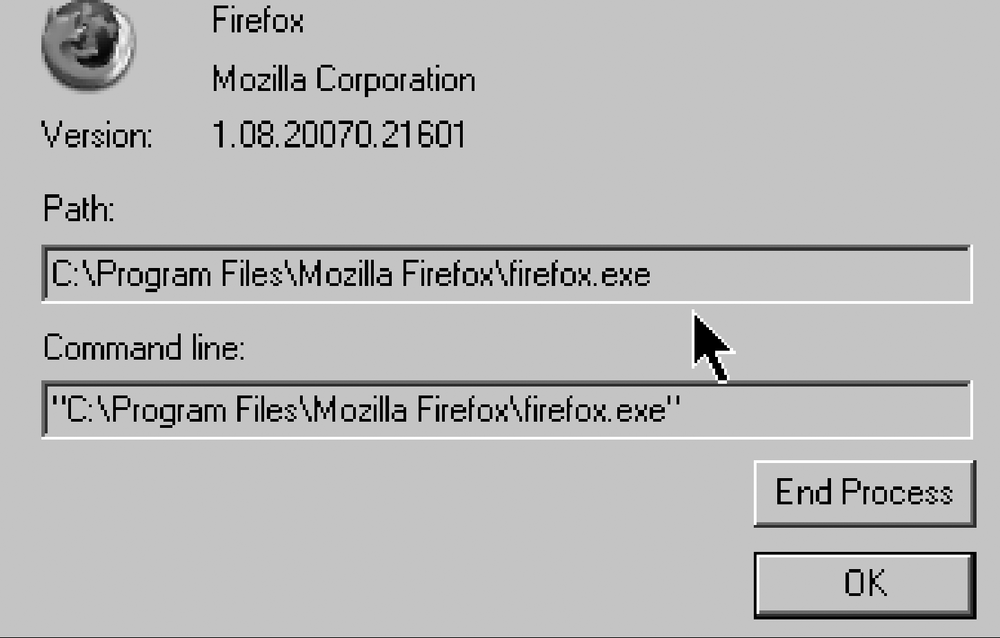
What is all this stuff? Why is it running and listening on all of these ports? If you want to get a quick view of what processes are using the network, pop open a CMD window and run netstat –aonbv. The –n disables DNS lookups (for speed), the –o shows the Parent Process ID, and the –b and the –v work in conjunction to show the name of the executable currently using the connection. GNU/Linux administrators should get in the habit of popping off netstat –aopl —numeric–hosts, which does the same thing, just with different letters. If the machine has been heavily compromised and is running a rootkit, don't expect netstat to show truthful data. Windows administrators can download a copy of TCPView, shown in Figure 14-2 and Figure 14-3, which is from the Sysinternals tool suite and available from Microsoft directly at http://www.microsoft.com/technet/sysinternals/utilities/tcpview.msapx. I really like this tool. It's like a combination of netstat and the Windows Task Manager, and it allows you to right-click on a process to either examine the properties or kill the process.
In this case, someone had taken control of the machine through an exposed MSRPC vulnerability and installed a VNC server, then installed a BitTorrent client as well as an SMTP relay to send some spam. Thankfully, the machine was a victim host running on a VMware virtual machine. We saved the compromised disk image for later analysis, restored a prior image from a backup, patched the vulnerability, and edited our firewall rules to block connections to MSRPC ports. Virtualization as a hardening technique is covered in Sandboxing with OS Virtualization.