Secure/Multipurpose Internet Mail Extensions (S/MIME) offers an alternative to OpenPGP to encrypt and sign emails. It is easier to use then GPG or PGP, but it is also restricted to emails. A trusted third party replaces the Web of Trust, and the keys are embedded in an X.509 certificate.
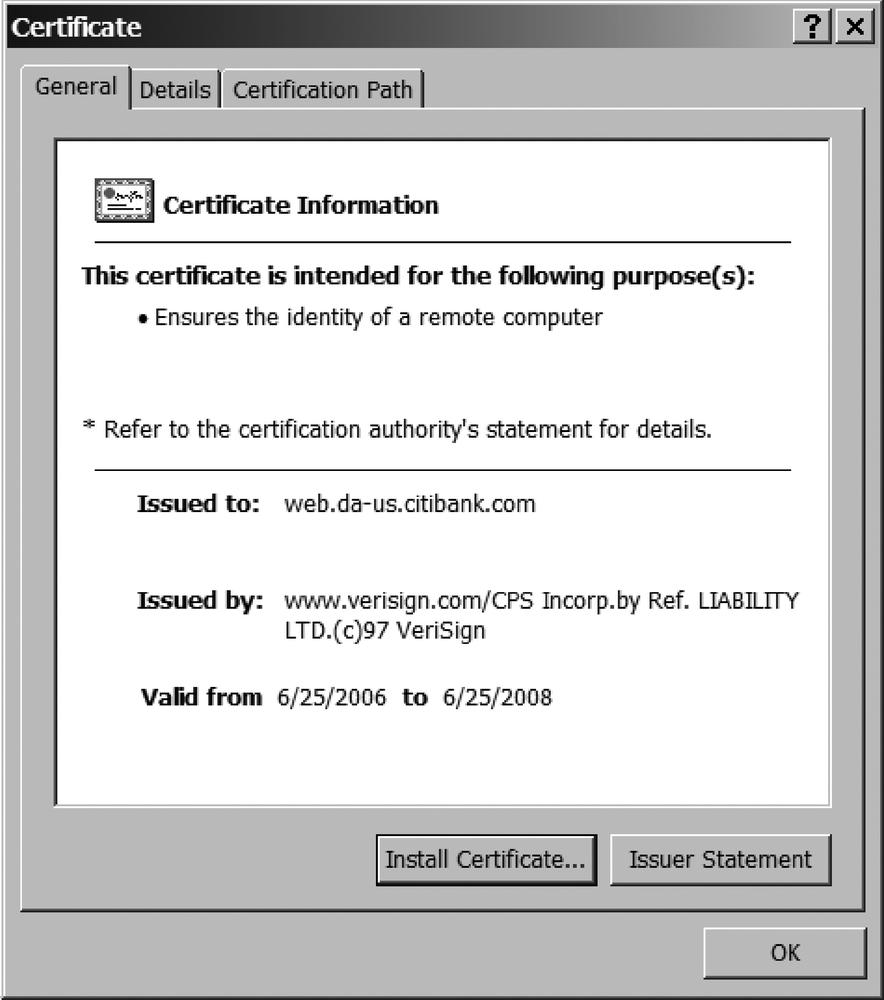
When browsing on secured sites, such as banking sites, the communication is encrypted with HTTPS and an X.509 certificate is associated with the domain and subdomain browsed. Certificates linked to domain names let users confirm they are browsing a legitimate web site, not a fake or a copy. The certificates are delivered by a Certificate Authority (CA) that acts as a trusted third party. By default, web browsers ship with certificates issued by established trusted CAs; for example, VeriSign. If the certificate is not issued by one of these trusted CAs, it displays a warning asking if this third party should be trusted.
Figure 15-16 shows an example of an X.509 certificate issued by VeriSign to Citibank that certifies that I was browsing the legitimate Citibank web site.
Tip
Web browsers ship with a default list of trusted Certificate Authorities. In Internet Explorer, this list can be found under Tools → Internet Options → Content → Certificate → Trusted Root Certification Authorities.
In Firefox, the same list is available under Tools → Options → View Certificates → Authorities.
S/MIME is included in standard Microsoft Outlook, Apple Mail, Lotus Notes, BlackBerry email client, and Mozilla Thunderbird. No additional software plug-ins are required for these email clients.
The use of a Public Key Infrastructure (PKI) makes it easier to use. The email client automatically displays a warning message if the certificate used to sign or encrypt the email is not signed by a trusted certificate authority.
Like with GPG, a signature is created with the sender's public key embedded in his own certificate. Encryption is done with the recipient's certificate.
Tip
S/MIME was designed to be used for email only, but it is possible to encrypt or sign regular files with the gpgsm tool; gpgsm accepts similar options to GPG.
It is possible to create a self-signed certificate. However, you should remember that it defeats the purpose of the PKI, since the same entity cannot be both a trusted third party and the certificate owner.
VeriSign is the most popular and most trusted Certificate Authority. But acquiring a certificate from VeriSign or from most of the trusted CAs has a cost—commonly, several thousands of dollars for a time-limited certificate. However, a couple of CAs now offer free X.509 certificates. It is highly recommended to choose a free CA that is already trusted by the most popular email clients. Some of the free CAs trusted by default are:
- Comodo (http://www.comodogroup.com/)
Offers free email certificates for personal use only. The key length is limited to 1024 bytes. It is trusted by virtually all email clients.
- CAcert (http://www.cacert.org/)
Not trusted in most applications. If you want your identity to be included in your certificate, you must verify it with his notary-based Web of Trust.
- Thawte (https://www.thawte.com/)
Thawte certificates are trusted by most email software. Thawte was acquired by VeriSign in 2000. You must prove your identity to one of his local notaries within his Web of Trust in order to include your name in your certificate.
Both Thawte and CAcert offer two levels of certificates. The first level validates only that the email address is valid. This does not certify that the owner of the email is who he pretends to be.
Certificates including your identity must be verified physically. A customer could get her identity checked by having it verified at the CA's company. However, this is not scalable and not everyone can afford a trip to South Africa just to get her identity checked by a Thawte employee. Thawte and CAcert have created a Web of Trust, similar to GPG's Web of Trust, to certify the identity of their users.
Users can become notaries for CAcert or Thawte after their identities are verified by capitalizing points. You get points every time your ID is verified by the companies themselves, a trusted third party such as an official registered notary, or by other Thawte/CAcert notaries. Once a user has enough points, his identity is added to the certificate. The certificate certifies both the email address and the identity of the owner.
S/MIME is easier to use than GPG, is supported by more clients, and is free. With a trusted third party, there is no problem in verifying the key's authenticity. All the trust is placed in one entity.
However, it is not as widely used as GPG. The main reason is historical. S/MIME first supported only weak encryption protocols. This has long been fixed, and it offers the same level of security as GPG; however, it still has a bad image in many people's mind.
The second drawback of S/MIME is that it is designed for email. You must use GPG and another set of keys to sign or encrypt files, so you may as well use GPG for both functions.
Another inconvenient, although minor, problem with S/MIME is that there is no clear warning when the certificate misses the owner's identity and lists only an email address. Each certificate should be verified manually.