There is a wide array of malicious software ( malware) available that is designed to damage your computer, take control of systems, or gather personal information. Here are some types of malware, although these examples in no way cover all the possible varieties that malicious people create:
- Virus
A virus is a self-replicating program that inserts copies of itself in other computer programs (usually executables) or documents (for example, office documents with macros). Viruses often use email to spread across a network. Polymorphic viruses modify themselves each time, making them harder detect. Bombs are viruses that start acting on a given date (time bomb ) or with a given action by the user (logic bomb ).
- Worm
A worm is similar to a virus, but worms use vulnerabilities in networking to spread (for example, Slammer exploited a vulnerability in the Microsoft SQL Server, and Sasser exploited a vulnerability in Microsoft Active Directory).
- Trojan/Backdoor/RAT
A Trojan, backdoor, or Remote Administration Tool (RAT) allows unauthorized persons to take partial or complete control of an infected system. Unlike viruses or worms, they cannot replicate themselves. They often lie inside programs downloaded from obscure web sites or from peer-to-peer networks.
- Spyware
The term spyware includes a wide range of software aimed at spying on the user. Spyware usually does not replicate itself, but it can download other spyware to your computer. Spyware is becoming the most common threat today. Some types of spyware are as follows:
- Adware
This is the most common, but also least harmful type of spyware. It displays pop-ups with advertising. It often spies on your web searches and checks the URLs you are visiting to target the advertisement.
- Browser hijacker
Browser hijackers infect your web browser and redirect you to different web sites, change your home page and/or other settings, and add a toolbar to your window.
- Key logger
Key loggers are looking for any data they can steal from the user—for example, login, passwords, credit card numbers, Social Security numbers, and any other personal information. They do this by recording all the key strokes you make and then sending the data back to their home source.
- Miscellaneous
Malicious programmers do not lack imagination, and some of their creations are not easy to catalog. Some malware switches the dial-up phone number for your Internet provider to an over-charged number or simply uses your dial-up modem to call expensive services. Others encrypt your important files and ask you for money to get them back.
The symptoms of a malware infection can be very different and are sometimes difficult to detect. When you receive a new pop up every time you click on a link, you are obviously infected by spyware; but you could spend weeks or months using your computer without knowing that it is being used as a spam relay or to attack other systems. An infected system is not always slower and does not necessarily crash more often.
It is necessary to have software to protect your computer against all these malicious programs. Nothing is worse than being a network security expert and having your own laptop infected! To combat new types of malware, anti-virus programs have evolved to offer a protection against all these types of threats, including spyware. One day, a friend asked me to look at his computer, which was not working correctly. While he was reading his emails, I noticed a scam that was very well designed. I asked him to click on the link to check whether the fake web site was as good as the email. Unfortunately, it was not just a scam. The page contained spyware installed through the latest vulnerability in WMF images. Unfortunately, his computer did not run any anti-virus or anti-spyware software. In less than a minute, the screen was covered by advertising.
Windows is the most targeted operating system. It is the most popular OS, and a lot of users log in as Administrator, which mean that any program running can basically do anything it wants on the computer. But this does not mean that other operating systems are more secure. We have seen an increase of attacks against Mac OS X, and Apple has released a lot of security updates for serious vulnerabilities in their software.
Attacking and owning computers is becoming a business. Spammers use them to relay advertising emails. People rent farms of zombie PCs to launch attacks at a larger scale. Protecting your computer against such threats is not an option for paranoid users.
Symantec is one of the most popular anti-virus vendors, and its Norton Antivirus software comes with several modules to detect viruses, spyware, worms, etc. The default options are adequate for most users; however, the following discusses some settings that you might want to change to further protect your system. (All functionality, settings, and menu items are based on Norton Antivirus 2006.)
Once you have installed an anti-virus program, the first thing to do is to test your installation. Nothing is worse than the false feeling of having secured your environment when your anti-virus program is actually not working. Using a file called Eicar is the best way to test your anti-virus program. It is a test file that is detected by virtually all anti—virus software. You can download Eicar at http://eicar.org/anti_virus_test_file.htm. The test file is available in four formats:
- eicar.com
The .com files are executables on Windows.
- eicar.com.txt
Text files are often not scanned for viruses since they are never executed. You can check whether your anti-virus program is scanning all the files, regardless of the extension.
- eicar_com.zip
This is a compressed archive containing eicar.com. It is used to verify that the anti-virus program is checking all the files inside archives.
- eicarcom2.zip
This is a compressed archive that contains another compressed archive with eicar.com inside. The anti-virus should decompress the archives recursively.
Use Eicar to check all the different anti-virus detection methods, which include:
- Browser integration
Norton Antivirus can be integrated with Internet Explorer and Firefox. If you click on the link to download any of the Eicar test files, the anti-virus program should prevent you from saving the file to your hard drive. The default options allow some formats to pass through (see the section "Configuration Tuning," next), so you can tune your Norton Antivirus installation. Note that when you click on eicar.com.txt, your browser displays the file content instead of trying to download it, which prevents Norton from scanning it. But if you try to download the file by selecting "Save Page as" in your browser, Norton Antivirus prevents you from downloading the file.
- On-access scanning
To test this function, disable Norton Antivirus temporarily (right-click on the Norton Antivirus icon in the system tray) so you can download the four files. After the files are downloaded, re-enable the program and try to open the files. The Norton Antivirus stops you from opening them because it scans all the files that the user or other programs try to open (this is on-access scanning, which Norton calls Auto-Protect).
- Email integration
To test this function, try to attach each Eicar file to an email to verify that the anti-virus program is checking outbound emails. Perform the same function with inbound emails, first by disabling the anti-virus program, and then sending an email with an Eicar test file to yourself, and finally re-enabling the anti-virus program. The incoming emails should be detected by the anti-virus program. Alternatively, you can use the free service at http://www.webmail.us/support/anti-virus to send the Eicar file to your email address.
- Instant messenger integration
To test this function, try to send the Eicar files through instant messaging software (MSN, AIM, etc.). Perform the same function with inbound file transfers by sending an Eicar test file to yourself. Use the same procedure as in the last paragraph.
The last feature to check is LiveUpdate. It is critical to keep your virus definition database and your software up to date. You need to check for updates daily, preferably up to three to five times. If your virus definition is outdated, you are not protected as new threats are discovered everyday. Norton Antivirus comes with a one-year subscription to LiveUpdate. Perform a LiveUpdate to make sure your software can update itself automatically.
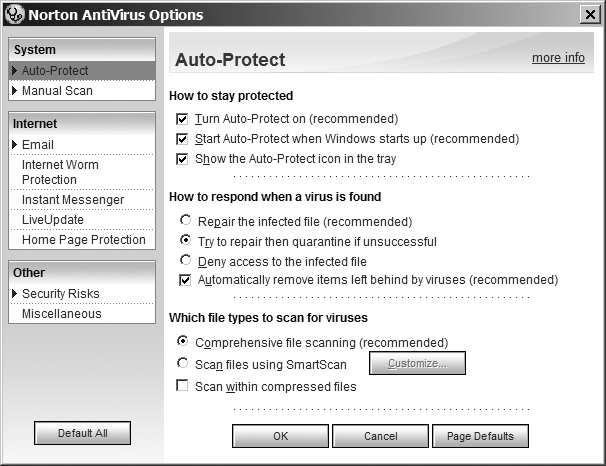
Auto-Protect is the most important feature for detecting viruses and is shown in Figure 16-1. When enabled, the program scans every file that is opened for execution or for reading. If you find your computer slows down after installing Norton Antivirus, you can disable the browser, email, and instant messenger integrations. The attachments are scanned when any application opens the file. However, leaving these features enabled is recommended, as it helps you to identify the virus source quickly. It also prevents nonscanned files from being shared with other persons who may not have an anti-virus program.
If some of the Eicar tests fail, the default configuration needs to be tweaked to provide better protection.
By default, "Scan within compressed files" is disabled for performance reasons. However, if any program decompresses an archive and opens one of the files, Auto-Protect scans the decompressed files. You can enable this feature by selecting the "Scan within compressed files" radio button under the heading "Which file types to scan for viruses" on the Auto-Protect screen. In the same section, you can enable Smartscan to scan specific file extensions and to save resources on your system.
Warning
Remember that viruses and malware in general can be found in other documents besides executables; e.g., images (there are known exploits for JPEG, animated icons, Windows Media File, and others), Microsoft Office documents (they use macros), and drivers, to name a few.
It is possible to turn off individual rules for Internet Worm Protection to avoid false positives. A false positive is a case when the software reports a legitimate file or network traffic as a threat. For example, the program Install Shield has occasionally been falsely reported as a virus by anti-virus software. Internet worm and Trojan signatures can also trigger false positives if you have a network service running on a port used by known Trojans or worms.
The Internet Worm Protection includes a very powerful but hard to manage Program Control feature. Norton Antivirus can warn you when a program is trying to access the network. It can find adware, key loggers, and worms, but it requires a deep knowledge of your operating system and all the legitimate software installed to determine whether a given executable has the right to access the network. Users often do not take the time to verify all alerts; they allow all executables to reach the network without carefully checking legitimacy to keep their program running correctly. You can add programs you trust to Program Control.
Internet Worm Protection also provides a firewall that can replace the default Windows Firewall in the Windows Security Center of Microsoft Windows XP with Service Pack 2. You should check Chapter 13 for good firewall policies. By default, the firewall allows all outbound and inbound connections from the local network and blocks four inbound connections from Internet for three common targets of network attacks: Server Message Block (SMB), End-Point Mapper (EPMAP), and Universal Plug and Play (UPnP). The default policy is very loose and should be tightened (see Chapter 13) to secure the computer.
Home Page Protection is an interesting feature. A lot of spyware, especially adware, attempts to change your home page. Norton Antivirus can detect attempts to overwrite your browser settings. When you open your browser or click on the Home Page icon, Norton Antivirus warns you that the location of the home page has changed and asks whether you want to keep the new address. This is usually a sign that your computer is infected with spyware. However, you also receive a warning if you change your home page manually, or if you authorize a program to change the default home page.
To configure the software and virus database updates, click on LiveUpdate in Norton Protection Center, and then click on Options. Choosing Express Mode allows all updates to be done automatically without interfering with your work, as opposed to Interactive Mode. The default update frequency is 240 minutes (six updates a day if the computer is running 24/7).
Finally, you might want to change the default actions accessible from Security Risks. To do so, double-click Actions in the Security Risks section and select "Ask me what to do" to prevent Norton Antivirus from deleting files in case of false positives. It is better to quarantine the files than to delete them, so that you can recover them later if they are found to be noninfected files.