There is no miracle tool to catch phishing emails, but rather a set of tools that can catch phishing web sites at different levels.
Phishing can be caught by Bayesian filters. They often require you to "update your information" because "your account has been disabled," phrases that are not often seen in legitimate email. However, some phishing emails have the same text as legitimate emails, only the links are forged.
SpamAssassin contains tests in /usr/share/spamassassin/20_uri_tests.cf to check URLs contained in email. For example, NUMERIC_CHECK_ADDR and NORMAL_HTTP_TO_IP look for an IP address in a URL, which is very common in phishing. Other tests look at ways to hide the real domain name.
The ClamAV daily and main databases contains more than 900 definitions of phishing email. These signatures contain "phishing" in their name; for example, HTML.Phishing.Bank-527. These signatures apply to the email body, not on the attachments. The Procmail rules used previously to run ClamAV must be modified to not check the presence of the attachment:
CLAMAV= 'clamdscan --no-summary --stdout -'
:0 fwh
* CLAMAV ?? : \/.*Phishing.* FOUND
| formail -I "X-ClamAV: $MATCH" -I"Subject: *** Phishing ***"It is possible to only use the phishing signatures with ClamAV. main.cvd and daily.cvd must be unpacked (see the section "MD5 Signatures" earlier in this chapter) to extract all phishing signatures to a new directory. This can be done with this script:
#!/bin/sh
for SIGNATURE in 'grep -i phishing *';
do
echo 'echo $SIGNATURE|cut -d: -f2,3,4,5'>> /usr/share/clamav-phishing/'echo $SIG
NATURE|cut -d: -f1';
done;The -d /usr/share/clamav-phishing option can be used to load the new databases.
Some phishing emails slip through the email filtering systems. The next line of defense is a toolbar installed on the web browser of each client that warns the user when he is about to display the fraudulent web site. Both Firefox and Microsoft Internet Explorer have support for such toolbars, including the Google Toolbar, Netcraft Anti-Phishing Toolbar, TrustWatch Toolbar, and SpoofStick.
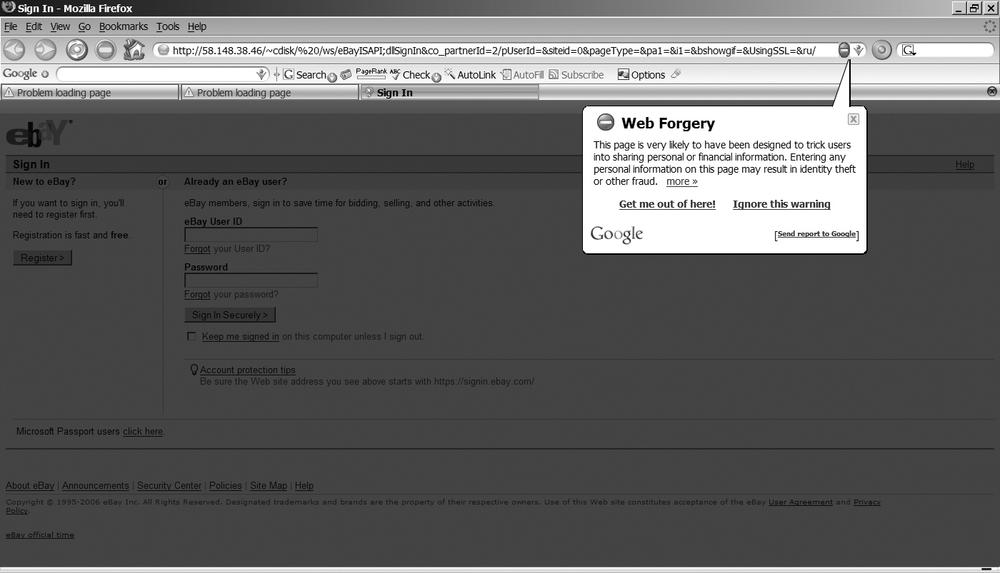
The Google Toolbar (http://toolbar.google.com/) and the Netcraft Anti-Phishing Toolbar (http://toolbar.netcraft.com/) have a dynamic list of phishing web sites, as shown in Figure 16-5. Users can also report fraudulent web sites.
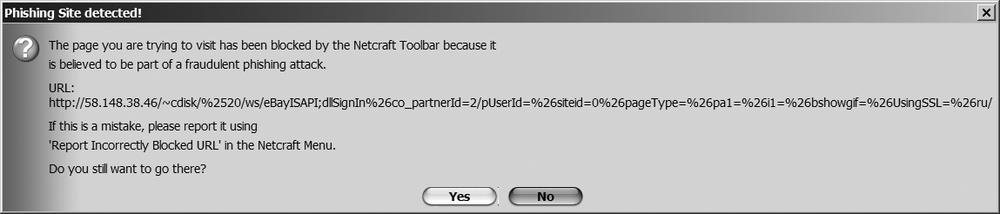
The Google Toolbar displays a warning after the page is loaded. If the web site contains exploits, the attacks are not prevented by this toolbar. Netcraft displays a warning before the page is loaded, as shown in Figure 16-6.
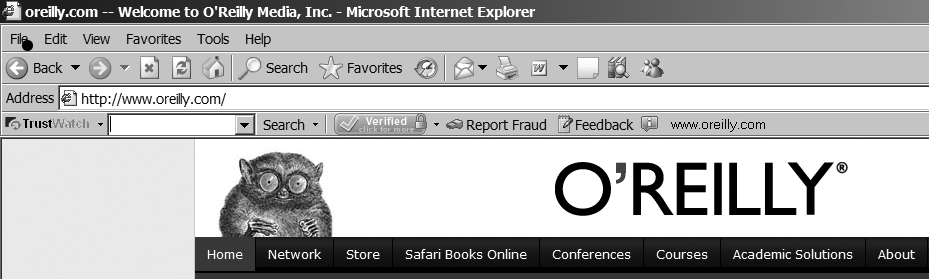
The TrustWatch Toolbar (http://toolbar.trustwatch.com/) behaves like a whitelist, whereas the two previous are blacklists of phishing web sites. Trustwatch displays the Verified icon for known legitimate sites, as in Figure 16-7.
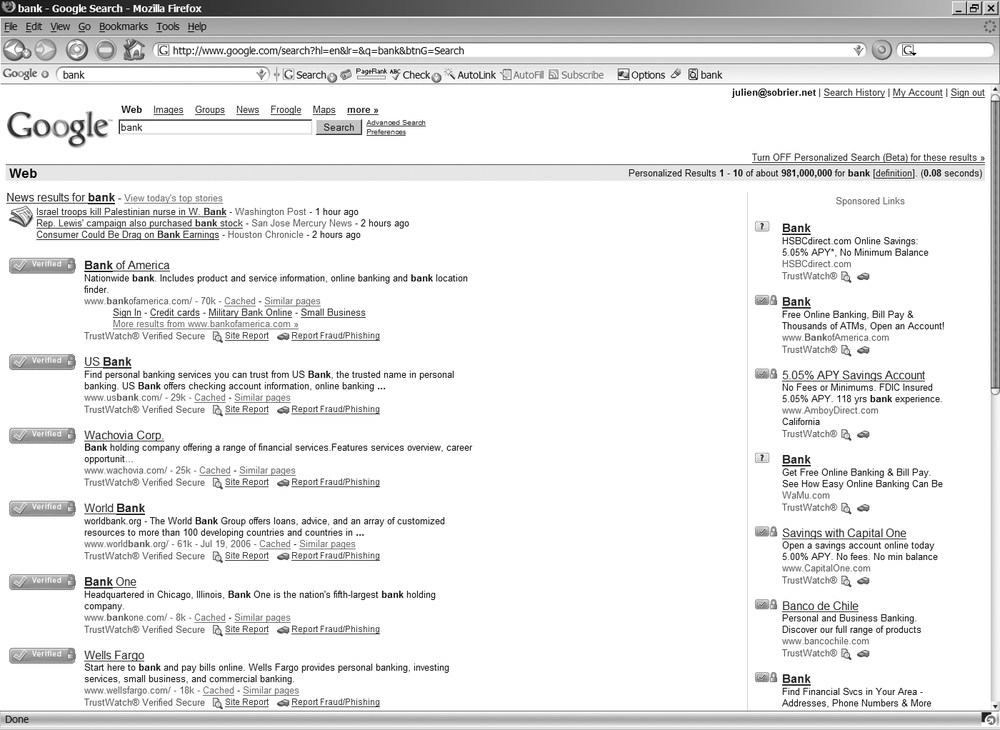
Figure 16-8 shows that this icon is also displayed on the search results of major search engines such as Google, MSN, and Yahoo!.
SpoofStick (http://www.spoofstick.com/) has a different approach. Phishing web sites often use different techniques to hide the actual domain name. Spoofstick displays clearly the hostname the user is browsing, as shown in Figure 16-9.
These anti-phishing toolbars can help protect you from threats coming from unknown web sites, and are a worthwhile addition to your Internet security toolbox.