The effectiveness of your Snort sensor greatly depends on factors such as the rules that are loaded and what network traffic is available. Snort can only work on traffic that its interface sees, a kind of what you see is what you get. To ensure optimal information from the sensor, it is very important to plan ahead and find where this sensor should be placed and with what kind of rules.
Snort can be used in many different scenarios. Those scenarios include, but are not limited to, the ones discussed in the following sections. A simple network topology is used as an example to illustrate what the different implementations are and what interesting types of practices can be performed from each of these different positions within a network.
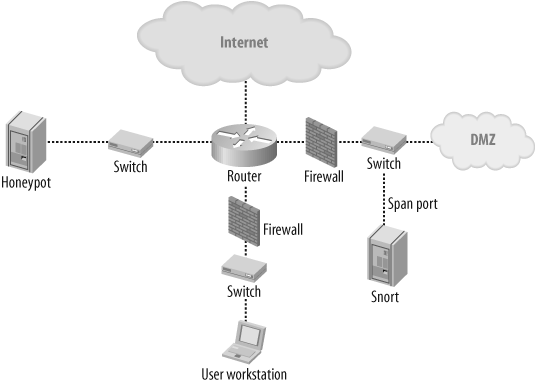
For network intrusion detection, Snort is usually positioned to monitor systems that face the Internet. Systems such as mail servers or web servers that are placed in the demilitarized zone (DMZ) are the primary target. Using the span port of the DMZ to monitor all traffic in this zone is a good choice. As for the rules base, you are interested in attacks that can happen to open services, and also in monitoring uncommon communications between servers (which can indicate a breach inside this zone). There is no need to apply all the signatures to this sensor, only those of interest per service, or even per Internet-facing application. Also, since you should be behind a firewall, all LAN attacks, port scans, and uncommon communication within the zone should be logged for further analysis. A typical topology might look like the one in Figure 19-3.
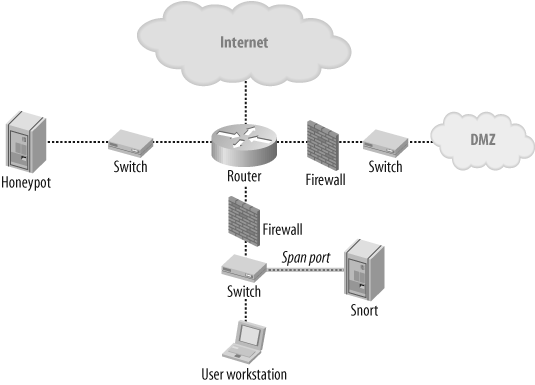
As a user-monitoring device, Snort is best positioned to monitor outgoing communication from the users. Using the span port of the last switch before the router/firewall/gateway to monitor all traffic in this zone is usually a good choice. As for the rules base, what you are looking for are patterns that can lead you to unauthorized use of the corporate network. It might be P2P networks, chat applications, nonbusiness related web sites, or vast media downloading. These rules are not intended to protect as much as monitor the behavior of the employees. However, web-based attacks affecting multiple browsers is becoming a more popular attack vector, so it might also be a good idea to monitor web server responses for attacks targeting browsers, by using this setup. The signatures of interest are those that monitor the user and server-to-client attacks. A typical topology for user monitoring might look like the one in Figure 19-4.
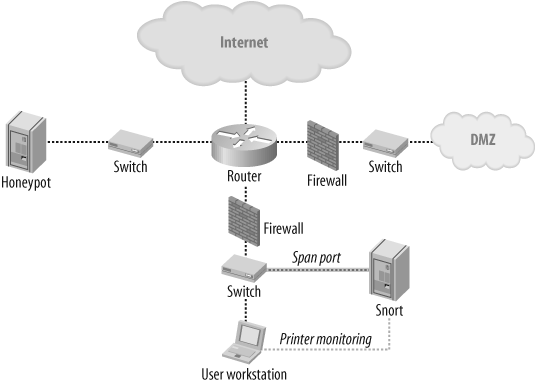
As an information leak detection device, Snort is usually positioned to monitor internal communication within the LAN by using the span port of the main switch to monitor traffic. The primary target is traffic leaving the network as well as traffic directed to printers. As for the rules base, you are interested in patterns that can lead to the use of unauthorized corporate network traffic, such as emails sent outside, blogging, or printing of protected documents. The rules are not intended to protect as much as monitor the behavior of the network user. A typical topology could look like the topology shown in Figure 19-5.