
Figure 3.1
The door that led to the Equinix Internet Peering Point on the outskirts of Washington, DC. Image © 2011 Jason Farman.
On the Invisible Infrastructure of Mobile Networks
For several years now, I have been using locative media to “check in” to locations I visit. When I arrive to a location, I will turn on my phone, load the Foursquare app, click the “Check In” button, wait until the phone returns a list of possible locations that are near my GPS coordinates, and check in. For my own purposes, I find this practice to be a useful tool for journaling. Returning to the locations I checked in to over the past year unveils the intimate connection between space and practice, between the place and the meaning of the place, and between a location and the embodied production of that location.
One recent check-in on Foursquare stands out for me because it dramatically transformed the way that I think about locative media. On October 27, 2011, I visited a major site for the Internet on the outskirts of Washington, DC: the Equinix Data Center. This “Internet peering point” serves as one of the key places for Internet traffic on the East Coast of the United States since most of the data that moves in and out of this part of the country goes through this facility at some point. Along with most other major companies that do business in the United States, Foursquare houses their database here (run through Amazon’s Cloud servers). I was able to tour the facility with my graduate students. We touched base with our tour guide on the phone that day and were asked to meet him at a nondescript door. “Since there are no signs for the facility—for security reasons—you’ll pull to the end of the warehouse area and look for the only door with a handle,” he said (see Figure 3.1), Andrew Blum, in his journey to uncover the material reality of the Internet, faced a similar challenge when visiting Equinix while writing his book, Tubes: A Journey to the Center of the Internet. He writes,
When I showed up, I had trouble finding the door. Equinix had grown to fill six single-story buildings at the time I visited; by early 2012, four more had been added, totaling more than seven hundred thousand square feet—about the size of a twenty-story office building—all tightly arranged around a narrow parking lot. I saw no proper entrance to speak of and no signs, only blank steel doors that looked like fire exits.
(Blum 2012, 90)

Figure 3.1
The door that led to the Equinix Internet Peering Point on the outskirts of Washington, DC. Image © 2011 Jason Farman.
He goes on to note that, according to David Morgan, the director of operations at this site, this kind of confusion is the goal of the design of Equinix: “customers are reassured by the anonymity of the place” (Blum 2012, 90).
The “door to the Internet” led to a room that was only as big as a mediumsized elevator. Brian, our tour guide, placed his hand on a biometric scanner and punched in his passcode in order to open the doors into the next room. This led us to the security area, where we showed our identification and were given visitor badges. Brian scanned his hand on another biometric scanner, punched in his passcode, and led us to the waiting area, which had a conference room where we were told about the history and current practices of this Equinix facility. He led us to the next set of doors, which was the entrance to the data center. Once he scanned his hand and entered his passcode one last time, we walked into a frigid, dark and extremely loud environment. Here, there were long stretches of aisles in all directions, bounded by black steel cages housing servers stacked to the ceiling (see Figure 3.2). These servers run nonstop, twenty-four hours a day, and produce so much heat that one of the primary concerns for these facilities is keeping the electricity running to the air conditioning system that keeps everything cool.1 Thus, upon entering the data center, I could barely hear Brian talk above the noise of cold air blasting down onto the front faces of the server racks. Above my head, running down the center of each aisle, was a yellow tray that held the fiber-optic cables running to and from each server. Along these cables, data was flowing around the world at speeds so incredibly fast that it was difficult for me to comprehend.

Figure 3.2
The inside of the Equinix Internet Peering Point in Ashburn, Virginia. Behind the cages are the servers that are run by major companies like Amazon, EA Games, Verizon and Google. The yellow trays along the aisles hold the fiber-optic cables running between these server cages. © 2011 Equinix, Inc. All rights reserved. The Equinix logo is a trademark of Equinix, Inc.
It was here that I pulled out my mobile phone, loaded up Foursquare, and checked in to the Equinix data center over a 3G network. Knowing that Foursquare’s databases were housed somewhere at this facility—located on servers behind one of these cages—I began to wonder about the flows that my information took. What information pathways were necessary in order for me to be “located” and to broadcast my location to my network of friends on Foursquare? What does the infrastructure behind locative media and mobility actually look like?

Figure 3.3
The base of the cell tower that my phone connected with near the Equinix Peering Point, showing the wired infrastructure that my data flowed through. Image © 2013 Jason Farman.
Tracing the flows of my locative data turned out to be an enlightening endeavor. Combining research on the ways that the mobile Internet works with physically walking around and locating cell towers and antennas, I discovered that as my mobile device sent out its signal from the Equinix building, it connected (through a line-of-sight link) with my carrier’s nearest cell antenna through what is termed an “air interface.” Since I was in an area with enough coverage, my signal connected directly to a cell tower that was linked in with the technology that routes my request through the fiber-optic (or sometimes copper) cables that connect to the Internet (called a “backhaul”). As soon as my signal connected with this cell tower, the rest of the pathway was not wireless; instead, the journey to Foursquare’s database took place entirely through the material, hard-wired, tangible infrastructure of the mobile Internet. The signal ran down the wires of the cell tower (see Figure 3.3), connected into the fiber optics of the Internet infrastructure, and took various routes from the cell tower to the larger cellular network that directs the data packets that are sent from a phone. After being directed by my carrier’s network, the packets of data sent from my phone came shooting right back to my location—the Equinix data center—in order to access Foursquare’s database. It is quite possible that the request made by my mobile device traveled on the fiber-optic cables directly over my head in the data center where I was standing as this request went down into one of the cages and pulled the relevant data from the server. Here, using the GPS coordinates delivered to the server by my mobile device, Foursquare was able to pull up a list of nearby locations. It then sent that information back along the fiber-optic cables, back out to the cellular network, up the cell tower lines, and back out to the antennas, eventually landing right back on my mobile device.
When tracing the flow of my data, it struck me how circuitous the pathway was to send and receive information. Even more striking was the fact that much of the journey of my data took place across a very static/fixed infrastructure. In fact, much of what we consider to be “mobile” media is generated through very nonmobile technologies such as the cell tower and fiber-optic cable.
The largest take-away for me gained by tracing the flows of my mobile and locative data—with which this chapter will be most concerned—is that most of these interactions took place at a level that was far beyond my awareness. I tend to imagine that locative media begin and end at the level of the interface; however, this sentiment couldn’t be further from the truth. The vast majority of locative media takes place well beneath the level of the interface, with technologies communicating with technologies in ways that exceed my own sense perceptions. Therefore, as we continue to theorize location-aware technologies, especially as they impact the practices of embodied space, social interaction and site-specificity, we need to look beyond the human-to-human connectivity to take into consideration both the human-to-technology and the vital technology-to-technology interactions that take place beyond the realm of the perceptible. Ultimately, what is gained from such an inquiry is a necessary insertion of objects into our understanding of the production of space and of the ability for embodied people to truly engage a political practice of difference. My sense of embodied identity is not simply gained through social interactions with other humans; instead, it is continually constituted by what I term a “sensory-inscribed” engagement with people, objects, social and cultural structures, protocols and the spaces produced through the interactions among these things.
Ultimately, to argue for this mode of embodiment, it becomes apparent that many of these interactions are not visible to us. They tend to recede into the background of our practices with locative technologies. In fact, many of these technologies are designed to withdraw from view (if they are designed well, according to the designers). Thus, as I try to unveil the role that objects play in the practice of location-aware technologies, my hope is to push on the categories of “visible” and “invisible” to trouble the ways that these concepts are implemented in the design and everyday practices of mobile and locative media.
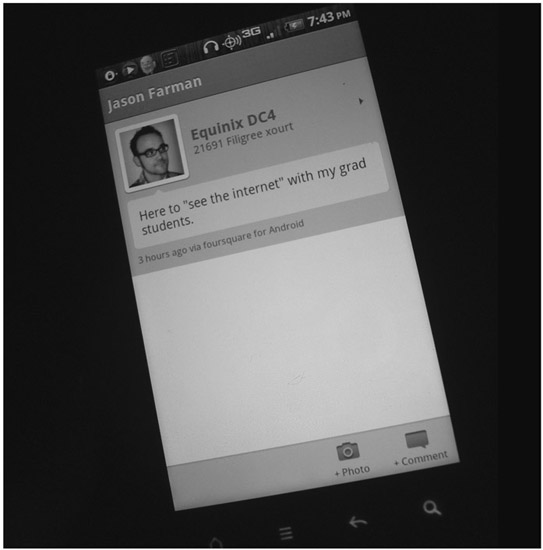
Figure 3.4
An image of my check-in to Equinix on Foursquare, which broadcasted my location, activity and companions to those in my network. Image © 2011 Jason Farman.
When I checked in to the Equinix facility, I attached a brief note to my check-in saying, “Here to ‘see the internet’ with my grad students” (see Figure 3.4). This note, along with my location, was broadcast to those in my network on Foursquare. So, if any of my seventy-eight friends and colleagues happened to load Foursquare that evening—or if any of them had push notifications enabled on their devices that would automatically send my message to the screens of their mobile devices—they would have known that I was visiting this site with my small group of graduate students from the University of Maryland. This seems to be the most obvious audience for locative media and, in fact, most scholarship on locative media tends to focus on it as an extension of social media sites like Facebook by bringing it out onto the streets and into the everyday movements of these networks of people. For me, as I mentioned at the beginning of this chapter, my primary use of Foursquare is as a kind of spatial journal to log my movements throughout a given day. So, my network was not my primary audience; instead, I thought of myself as the audience of this message, which I received exactly one year later on email in a message that read: “Your check-ins from one year ago today.” This service, now called Time Hop (though once cleverly called 4SquareAndSevenYearsAgo), sends reminders to users of Foursquare (and other services like Facebook and Twitter) of what they were doing a year ago on this day.
Yet, my check-in to Equinix forced me to ask: who is the primary audience of locative media? Could it possibly be the objects that are interacting and exchanging information with each other beyond the realm of my human awareness? When I loaded my phone to check in, I was searching for a 3G signal and searching for my location from Foursquare’s database. Simultaneously, my phone was searching for the nearest antenna and backhaul, which searched for the correct IP address in order to connect to right fiber-optic line leading down the long yellow tray that ran above my head and down into a cage in the data center, connecting to the exact server that held the information that corresponded to my GPS coordinates. Here, machines are talking to machines. There is an entire network of connectivity that encircles this one act of “checking in,” and I am just one node in that network, and while I might have been the initiator of this particular request (“Foursquare, please locate me and log my visit to this location”), my phone was already engaging this network of technological objects long before I made the request. My phone is able to navigate handoffs between various network “cells”—hopping from antenna to antenna to maintain a seamless connection so I never have to drop a call or receive an error message on a website I’m browsing. My phone is also tracking my movements, often without me giving it permission to do so (which has, in recent years, caused major controversies). It connects with GPS satellites—those celestial objects constantly orbiting the earth and only visible to me at night when they look like extremely slow shooting stars—three at a time in order to triangulate my position. My phone runs constant checks on my email, on my text messages, my voicemails, messages to me on Twitter, and a host of other services I have set up to run in the background while I go about my day. This is all happening right now as my phone sits at the bottom of my pocket.
Such interactions broaden our understanding of what constitutes an “audience” and extends Alice Rayner’s theorization of what an audience is for a performance studies perspective. She writes that the term audience is “a model for intersubjective relations as opposed to a model for a unified community; to view the audience, that is, as a ‘boundary condition’ in the act of understanding another and, as a result, of understanding the constitution and contradictions of its own differences” (Rayner 1993, 6). The audience is not a coherent, unified entity based on collective experience and empathy; instead, the audience exists as a practice of imagined collectivity between listeners that simultaneously offer feedback, between those in a constantly evolving context that have affective/effective impact on/by the messages being sent and received.
When this begins to truly sink in, I realize how small my Foursquare request was and that I am not the primary audience for locative media. I am only one audience member among many, including my phone, the cell antennas, the cell tower, the fiber-optic cables, the servers, data talking to data, machines talking to machines, signals communicating to infrastructure. There are a whole host of communicative objects that are connecting and serve as the “audience” of locative data. This shifts the entire focus of locative media in fairly radical ways. Instead of being this solipsistic interface for the oversharing of banal information (e.g., “To all of my friends: I am currently at the corner gas station filling up my car.”), locative media highlight the site-specific interactions among human agents and the informational objects that are weaving themselves into the fabric of our everyday lives.
The role these informational objects play in the practice of locative media initially rubbed against the grain of my theorizations of embodied space in a mobile media age. As I worked to define “interface” in an early draft of my book, Mobile Interface Theory: Embodied Space and Locative Media, I wrote that the interface is “constituted as a larger set of social relations” and is the nexus of these relationships. Therefore, the mobile phone, in and of itself, is not an interface (I still hold this to be true). Only when the mobile phone serves as the nexus of relationships and interactions does it become an interface. I draw here largely from Johanna Drucker’s arguments when she writes, “What is an interface? If we think of interface as a thing, an entity, a fixed or determined structure that supports certain activities, it tends to reify in the same way a book does in traditional description. But we know that a codex book is not a thing but a structured set of codes that support or provoke an interpretation that is itself performative” (Drucker 2011, 8). However, my attempts to think beyond the “thingness” of the mobile-phone-as-interface (and instead think of the interface as the nexus of relationships) led me down an ill-reasoned path. In this early draft of my book, I went on to say, “The mobile device, on its own, is nothing but a beautifully designed paperweight.” For me, as I worked to theorize embodied space as something that is produced through practice, the mobile phone sitting on my desk seemed to not engage these practices because I was not directly interacting with it. Once I began to see beyond this narrow box of human-computer interaction and practice, the device’s engagement with its own practices, its own audiences, its own content opened up an entire realm vital to my theorizations of the production of space.
My theorization of embodiment is founded on the ideas in phenomenology, especially the work of Maurice Merleau-Ponty. This mode of inquiry prioritizes an experience of the world gained through the body and through the senses. It takes up experiences, sense perception, the body’s role in knowledge production and the philosophies of being as its main objects of study. It is focused on subjectivity and embraces the limited perspectives of human perception as the main window through which we understand the world. By inserting mobile objects—the materiality that serves as the foundation of locative media—into a phenomenological approach to understanding embodied interaction, we begin to see some of possible limits to phenomenology (limits, I will argue, that don’t accurately characterize the phenomenological approach of those like Merleau-Ponty and Martin Heidegger).
In a 1946 presentation of his work to the Société francaise de philosophie, Merleau-Ponty was challenged to defend his work against the idea that phenomenology was solipsistic and always must come back to the individual’s perspective on the world. During the question and answer session of his presentation, another philosopher of the time, Emile Bréhier, lobbed a complaint against Merleau-Ponty and his phenomenological approach. His complaint is one that would thereafter be echoed multiple times by other detractors of phenomenology: “When you speak of the perception of the other, this other does not even exist, according to you, except in relation to us and in his relations with us. This is not the other as I perceive him immediately; it certainly is not an ethical other; it is not this person who suffices to himself. It is someone I posit outside myself at the same time I posit objects” (Merleau-Ponty 1964, 28).
Indeed, phenomenology, as with the main object of study for this chapter—locative media—can be seen as giving an overemphasis to the individual rather than the community or others that are able to exist beyond our realm of understanding. This kind of “immanence” of the individual comes at the cost for any existence of “transcendence” of the other. As Jack Reynolds puts it, referencing Emmanuel Levinas’s concern with this approach to being in the world, “phenomenology hence ensures that the other can be considered only on the condition of surrendering his or her difference” (Reynolds 2004, 125).
Michael Yeo phrases the problem of immanence and transcendence by asking, “How is it possible to experience the other as other—as really transcendent—given that I cannot but experience her in relation to my own immanent frame of reference?” (1992, 38). However, any theorization of difference requires the ability for us to engage transcendence, for a recognition that not all things exist on the plane of immanence, but instead can exist beyond our understanding and realm of experience. People need to be able to exceed their individual understandings and frames of reference in order for there to be any sense of knowledge, surprise and cross-cultural exchange. As Reynolds argues, “Not only can interactions with the other involve us in a renewed appreciation of their alterity (i.e., the ways in which they elude us), but the other is equally importantly that which allows us to surprise ourselves, and move beyond the various horizons and expectations that govern our daily lives” (2004, 128). Within this framework of alterity, we must include objects. Objects have to be considered as often exceeding our realm of understanding (and thus existing on the horizon of transcendence).
The flow of my mobile data offers an important example of this: most people, including myself prior to this investigation, typically engage the mobile Internet without any sense of awareness about the larger network of objects that make such connectivity possible. Though these objects and their interactions with one another often exceed our realm of human perception, they nonetheless shape the sense of self via location-aware technologies. We still deeply understand our sense of space even though we may not be aware of the informational objects that help produce that sense of space. For a sensory-inscribed phenomenology of embodiment, which stakes a claim in the continued value of phenomenology for analyzing our sense of being in the world, transcendence is always at the forefront of what it means to be human in a technological world. This transcendence, however, takes place on many phenomenological levels. The phenomenology of sensory-inscription, as produced simultaneously through the senses and through various cultural inscriptions, takes into account the distinction that cognitive scientists have made between cognitive awareness and the cognitive unconscious. There are things that we gather through human sense perception that we’re aware of: I turn on my phone, load Foursquare, compare its results to where I think I am, check in and finally compare my position in the world with my friends and colleagues. These are actions of which I am conscious. My awareness of these various levels of mediation involved in the ways space is produced ultimately results in an embodied sense of proprioception (i.e., of knowing where my body fits as it moves out into the world, of knowing the spatial relationships that constitute my place in this locale). However, there is much beneath the surface of human perception that is still vital to this sensory-inscribed experience of space. This takes place at the level of the “cognitive unconscious.” Many of the aspects of life and the uses of our emerging technologies require our ability to either filter out excess information in order to focus or, alternatively, to simply not be aware of certain aspects of our lives and surroundings (both biologically, such as not knowing how many times you’ve blinked in the last five minutes, and socially, such as not knowing the name of the person at the Foxconn factory who put the screen on your iPhone).
While much of our experience of location-awareness through our technologies does engage the cognitive unconscious, it is often designed to do so. For many designers of mobile devices and mobile applications, a good design is one that is not noticeable. If done well, it should recede into the background of your everyday life. Designers dating back to at least Mark Weiser’s work on ubiquitous computing have sought to design for invisibility or what Jay David Bolter and Richard Grusin have called the immediacy of the interfaceless-interface (Bolter and Grusin 1999, 23). As Weiser argues, “The most profound technologies are those that disappear. They weave themselves into the fabric of everyday life until they are indistinguishable from it” (Weiser 1991, 66). This is what Heidegger calls “readiness-to-hand,” and what philosophers in the field of Object-Oriented Ontology (OOO) like Graham Harman term “tool-being.”2 The tool, in its essence as a tool (its tool-being), is invisible to us. Only when the tool stops working (and, for Harman, no longer exists in its essence as the tool it once was) do we actually notice the tool. This move from ready-to-hand to present-at hand is the move from invisibility to visibility.
The categories of “ready-to-hand” and “present-at-hand” are rarely clear cut and distinct from one another. Emerging mobile devices are representative of the bleed-over between these categories. While designers and theorists of ubiquitous computing, like Weiser, hope to achieve a design that so intimately weaves itself into the fabric of our everyday lives that we rarely notice it as a distinct interface from “the interface of everyday life” (Farman 2012, 86–87), there is also a cultural desire for our devices to engage in this kind of seamless integration and be a visible object of significance. The device’s immediacy should be obtained while allowing for the device to still function as a status symbol, a technological fetish object and a signifier of a person’s brand loyalties. The fluctuation between these levels of invisibility and visibility are a result of the power structures (such as capitalism) that are invested in maintaining various levels of visibility and invisibility and the cultural desires that are founded on such structures.
For mobile and locative media, an analysis of the relationship between visibility and invisibility is a productive one, and one of the best examples is seen in the attempts to camouflage cell phone towers (and their resulting hypervisibility). I see this daily as I drive to work, making the thirty-five-minute commute to College Park, Maryland. As I drive through the northern part of the town of Silver Spring, at the corner of Bonifant Road and Layhill Road, there is a brick building with cell antennas perched on the top. These antennas are covered with a faux-brick veneer in order to make them blend in with the building. Driving another few minutes east on Bonifant, there is an extremely large tree standing in a field, twice as large as any other tree in the area. Even from a distance, it is apparent that this is a cell tower disguised to look like an evergreen tree (Figure 3.5).3 As I turn south onto New Hampshire, I see an interesting contrast between a huge cell tower on the busy intersection of Randolf Road and New Hampshire that stands high above the ground without any attempt to disguise it, and a cell tower further down New Hampshire, which blends into a church steeple near Adelphi Road.

Figure 3.5
A cell tower disguised as an evergreen tree in Silver Spring, Maryland. Image © 2012 Jason Farman.
This attempt to make the infrastructure of mobile technologies invisible is, in large part, one of the only recourses a community has as a response to the excessive visibility of these towers. As Ted Kane and Rick Miller note, the Telecommunications Act of 1996 essentially removed local oversight about where cell towers could be placed, thus “local governments are limited to regulation based on community planning standards, largely imposing some form of visual control” (Kane and Miller 2008, 152).
These methods of visual control, however, almost always make the infrastructure more pronounced and more visible. The attempts at disguise only draw our eye to the towers rather than allowing them to blend in. In thinking of an object-oriented approach to the study of these towers, this invisibility-made-visible led me to ask, “Who do these attempts at invisibility address?” Since mobile technologies work on line of sight (the signal from your mobile phone must connect with an antenna based on a direct, visible connection) the height of the evergreen cell tower in Silver Spring, Maryland, is designed to be visible to mobile devices in the area. The technologies work because they are visible to one another. However, the invisibility of the tower—the attempt to camouflage it as a tree—is done for the human users and inhabitants of this region.
While those addressed by this visible/invisible divide might seem obvious, the political consequences are significant. As Lisa Parks notes, the attempts to make our technologies invisible, as profoundly seen in the attempts at disguising cell towers, highlight a cultural desire to remove particular technological objects from view and, thus, to remove the political consequences of having those objects play a vital role in the ways that we practice space, identity and community creation. She writes,
Perhaps the ultimate irony of the antenna tree is that it actually exposes more than it hides and in this sense can be thought of as a site for generating further public knowledge about the materiality of wireless and other network systems. We are socialized to know so little about the infrastructures that surround us, even though many of us use mobile phones each day. Would our experience of mobile telephony change if we knew more about the architectures of signal distribution? It is difficult to say, but we certainly would have a different relation to the technology if we understood it as something more elaborate and expansive than something that rings in our purse or vibrates in our pocket.
(Parks 2009, n.p.)
The move to make our mobile objects and infrastructures invisible is to deny the “vibrant matter” of things and the essential part they play in the ways that we think about being human in this pervasive computing age. This resonates with Jane Bennett’s concerns when she writes, “How would political responses to public problems change were we to take seriously the vitality of (nonhuman) bodies? By ‘vitality’ I mean the capacity of things—edibles, commodities, storms, metals—not only to impede or block the will and designs of humans but also to act as quasi agents or forces with trajectories, propensities, or tendencies of their own” (Bennett 2010, viii). She goes on to argue that things like patterns of consumption would change “if we faced not litter, rubbish, trash, or ‘the recycling,’ but an accumulating pile of lively and potentially dangerous matter” (Bennett 2010, viii).
What would be the consequences of approaching mobile infrastructure in a similar way? Would advocating for a “vibrant materiality” of our mobile devices and infrastructures have an impact on things like consumption and purchasing patterns? On the ways we understand and legislate labor in the digital age? By inserting these vibrant objects into our understanding of locative experiences through mobile media, our phenomenological engagement with the world requires us to address the need for otherness and alterity: not only is locative media about connecting with one another, but it is about connecting with the various information objects around us, the spaces in which those objects exist, the labor that produces these devices and infrastructures and, ultimately, about objects connecting with objects. Objects like the cell tower and the data center are extreme versions of otherness, communicating and interacting with each other in ways that far exceed my realm of understanding. Yet, the ways we make these things invisible very likely is derived not from a stance of seeking the transcendence of others, but instead from a stance that seeks immanence of the self, that seeks to place the individual far above any of the networked social connections that are responsible for the constitution of the self.
Realizing the various objects that make something as simple as a locative application like Foursquare work has been illuminating for me. I see my mobile phone differently. I see the landscape around me differently, constantly noticing cell towers, antennas and networked infrastructures of all kinds, and while most of these things still remain outside of the realm of full visibility—for some things, like data transfer speeds across a fiber-optic cable or the signal emitting from my mobile device, I will never be able to fully grasp on a sensory level—I believe the push toward increased levels of visibility with our mobile tools and infrastructure is ultimately vital to our understanding of identity and difference broadly. The push to make our objects disappear ends up mirroring our push to make otherness disappear, and, ultimately, as we continue to engage in cultural analysis and theory, this kind of difference plays a central role. As those modes of inquiry continue to grow, they will need to include objects as a central object of study. For through the study of objects like emerging locative and pervasive computing tools, we can begin to locate the essential relationship between humans and objects, and between visibility and alterity.
A shorter version of this chapter first appeared in The Routledge Handbook of Mobilities, edited by Peter Adey, David Bissell, Kevin Hannam, Peter Merriman and Mimi Sheller (New York: Routledge, 2014), 233–242.
1. Brian noted that in the event of a major power outage (e.g., in a natural disaster or a “terrorist attack”), the gasoline to keep generators running would first be rationed out to area hospitals; second in line would be Equinix. The need to keep the Internet running is prioritized as a central to national safety in such circumstances.
2. See Graham Harman, Tool-Being: Heidegger and the Metaphysics of Objects (Chicago: Open Court, 2002). Harman, as well as Ian Bogost in his book Alien Phenomenology, Or, What it’s Like to be a Thing (Minneapolis: University of Minnesota Press, 2012) argue for an “object-oriented ontology” that extends the theorizations of those like Bruno Latour and actor-network theory by arguing for “things” that can be theorized even outside of the network. Bogost’s approach finds limitations in actor-network theory since “entities are de-emphasized in favor of their couplings and decouplings.”
3. Interestingly, since it is “evergreen” and surrounded by mostly deciduous trees, there are a remarkable number of birds living in this cell-tower-made-tree because it offers year-round shelter.
Bennett, Jane. Vibrant matter: A Political Ecology of Things. Durham: Duke University Press, 2010.
Blum, Andrew. Tubes: A Journey to the Center of the Internet. New York: Ecco, 2012.
Bolter, David, and Richard Grusin. Remediation. Cambridge, MA: MIT Press, 1999.
Drucker, Johanna. “Humanities Approaches to Interface Theory.” Culture Machine. no. 12 (2011): 1–20.
Farman, Jason. Mobile interface theory: Embodied space and locative media. New York: Routledge, 2012.
Kane, Ted, and Rick Miller. “Cell Structure: Mobile Phones.” In The Infrastructural City: Networked Ecologies in Los Angeles, edited by Kazys Varnelis. New York: Actar, 2008.
Kihlstrom, John F. “The Cognitive Unconscious.” Science. no. 237 (1987): 1445–1453.
Merleau-Ponty, Maurice. The Primacy of Perception. Evanston: Northwestern University Press, 1964.
Parks, Lisa. “Around the Antenna Tree: The Politics of Infrastructural Visibility.” Flow. no. 8 (2009). Accessed February 1, 2014. http://flowtv.org/2009/03/around-the-antenna-tree-the-politics-of-infrastructural-visibilitylisa-parks-uc-santa-barbara/
Rayner, Alice. “The Audience: Subjectivity, Community and the Ethics of Listening.” Journal of Dramatic Theory and Criticism. no. 2 (1993): 3–24.
Reynolds, Jack. Merleau-Ponty and Derrida. Athens: Ohio University Press, 2004.
Weiser, Mark. “The Computer for the 21st Century.” Scientific American (September 1991): 66–75.
Yeo, Michael. “Perceiving/Reading the Other: Ethical Dimensions.” In Merleau-Ponty, Hermenutics, and Postmodernism, edited by Thomas W. Busch and Shaun Gallagher, 37–52. Albany: State University of New York Press, 1992.