8
Halo
Instrument Everything, Change the Game
Several years ago, we wrote Code Halos to outline how any “noun”—any person, place, or thing—actually has both a physical self and a virtual self. Once instrumented and tracked, an invisible halo of code emerges around the object, and this “digital twin” often provides more insight and value than the actual physical item itself.
This is how, having never met you as a consumer in person, Amazon and Netflix know your tastes in literature and movies better than your family and friends do. These halos are central to how the FANG vendors can build such personal and valuable customer relationships.
In the time since we wrote that book, winning with data has since gone mainstream, and leveraging Code Halos has become a strategic imperative for nearly every type of business. The race is on to win through instrumentation, and established companies are changing the rules of competition across many industries, including:
- Industrial machinery: Bosch, John Deere, Caterpillar, General Electric, Siemens, Boeing, and Airbus, with combined revenues approaching $500 billion annually, view halo-based competition as central to their strategies, as they are all now instrumenting their machines as a default. Whereas these firms until recently competed on only physical aspects—the quality, price/performance, and safety of their products—they are now focused on the value of the virtual.
- Athletic apparel: Nike, Adidas, and Under Armour are all looking at annual growth rates of more than 15% between 2015 and 2020—with Under Armour aiming to double in size during that time—based on the power of instrumented shoes and clothing.1 In the process, these companies are transitioning from new-age cobblers to health information platforms.
- Automobiles: Toyota, BMW, Ford, GM, Mercedes-Benz, and Tesla are investing a combined $6 billion in digitization capabilities, primarily focusing on revolutionizing the automobile through instrumentation. Doing so will redefine not just the car but also car ownership and driving itself.
- Insurance: Progressive, Allstate, and Travelers are leading the charge in telematics devices, as the instrumentation of cars, homes, and buildings promises to transform customer relationships along with actuarial science itself through real-time asset monitoring. The traditional insurance model, based on static and one-to-many customer engagements, is soon to become context based, situational, and one-to-one.
There is now no limitation, technical or financial, for connecting anything to the Internet and then infusing it with the brilliance of a system of intelligence.
The question now is: What to do about it.
Every “Thing” Is Now a Code Generator
The cost of instrumenting everything is now too low, and the potential value too high, to avoid. As we noted in Code Halos:
[Winners in the digital economy] have mastered the ability to create and manage the Code Halos surrounding their customers, products, services, and entire organizations to establish new thresholds of performance. In wrapping those widgets with digits, they have created highly personalized customer experiences, products, and services that deliver not just utility but also insight and meaning at unassailable levels of efficiency.2
Boeing's Digital Airline, Philips's connected lighting systems, and Toyota's smart cars are all examples of these ideas being applied in the enterprise context. In each case, business leaders are turning their key products into code generators, thus creating the raw materials (data) for the digital economy. Algorithms and AI, integrated into systems of intelligence, convert that data into valuable insights that drive business outcomes.
With all this activity, the failure to take action at this point and turn “things” into code generators could almost be considered corporate malpractice. To get started, here are some key tactics to making this work in your world.
Three New Rules of Competition
After helping hundreds of clients learn how to compete on code over the past few years, we have identified three key principles for success:
- Instrumentation is no longer elective; it is now core curriculum. Code Halos began in the media and entertainment markets, but they don't end there. As recently as 2013, many thought the digital movement would be isolated to a handful of industries and would not expand into nearly every industry you can name, as it has done.
- Code is more valuable than things. The value of code can often meet or exceed the value of any physical device. Many view this as “turning water into wine,” as traditional products are transformed into platforms that seal customer relationships. A running shoe of old is the data platform of today, and the virtual has as much or even more value than the physical.
- Never turn them off. Instrumenting every “thing” also means making it continually connected to the Internet. Value can't grow exponentially when engagement is an episodic, once-in-a-while thing. Connections with data need to be always-on.
For a specific example of how these three principles are playing out in the market, let's take a look at a health insurer in Johannesburg, South Africa.
Become a “Know-It-All”
Why instrument everything and build solutions around information? Because doing so sets you on the path to being a “Know-It-All” business. With sensors and instrumentation, it's now possible to collect and analyze information about everything, to know everything about everything.
Before the advent of the Know-It-All business, the answers to many questions (e.g., real-time equipment status of an in-flight plane, the immediate impact of an economic event, a student's real-time performance on a particular assignment) were often simply guesses and would take time to figure out.
Earlier we introduced a few examples of this. To determine how a particular plane engine is performing in-flight, for example, the maintenance crew at Heathrow would collect some post-flight information and sort of have an idea of the metrics of the flight, but much of their perspective would be based on hunches and educated guesses, and would be available eight hours after the flight had landed.
To determine how an interest rate change in New Zealand would impact state-issued bonds in California, the traders at your local broker would check their Excel spreadsheets with complex equations showing the relationship between x and y, or a and b. But ask about the impact of x on b and ask them for it now, and the phone line would probably go quiet.
When asked how Johnny did on today's lesson in differential calculus, a teacher in a traditional school would probably have some sense of how the student was performing on a semester-to-semester basis, but he or she wouldn't know for sure whether Johnny really understood the difference between his local maxima or minima at this very moment.
Let's look at how General Electric (GE), one of the most venerable industrial brands in the world, is adopting this model to get more from its machines.
Know Your Back Office Too!
In a Know-It-All business everything can be known, should be known, and must be known. The new rules of business are based on knowing and knowing more than your competitors do. Get this right: know and win. Get this wrong: guess and lose.
As of now, using data and devices to upgrade consumer experiences is nothing new. The big work ahead is applying the same philosophy to other vital, but maybe less high-profile, aspects of enterprise work. This Know-It-All mindset is already springing to life in some common enterprise back-office processes:
- Human resource management: Google leverages instrumentation internally to optimize its people management by analyzing the formal, informal, and personal information its employees generate throughout the day. Google tries to know all of its roughly 57,000 employees in much more detail than is typical in a large enterprise and works to personalize career trajectories for its entire staff. Laszlo Bock, senior advisor at Google and former senior vice president of people operations (or human resources) at the company, points to the positive economic impact this approach generates: better recruitment, retention, and job satisfaction rates (all with an associated financial implication) than found at competitors. The Code Halos around its people allow Google to apply the same type of rigor to its people-based decisions as it does to its engineering decisions. Microsoft's $26 billion acquisition of LinkedIn in June 2016 is premised on a similar idea—of harvesting the data around people to inject the same type of collaboration and “social selling” that is common online into how big businesses run these types of processes.
- Supply chain management: The concept of building Code Halos around “things” is finding its way into global supply chains, helping manufacturers and retailers answer a growing number of questions from customers about the provenance of the goods and services they buy, such as “Where was this shirt made, and are the people who made it being treated fairly?” The shoe manufacturer Toms, as an example, uses a software product called Sourcemap to create transparency within its products’ journeys from factories around the world to stores in the United States and Europe. Customers can access information on factory conditions where the shoe was made and can track the progress of the shoes they buy through sensor enablement within the end-to-end supply chain, including raw materials, manufacturing equipment, and shipping containers.
- Smart automobiles and fleet management: Automobiles are fast becoming the next computing platform; according to industry estimates, the average car already has 100 sensors on board and projections suggest this number will double by 2020. As such, every car is a rolling generator, sharing data that allows manufacturers, insurers, and others to know about the health and performance of each and every individual car in highly personalized detail. Offerings such as Hum from Verizon—priced at $10 per month—are attempting to put the “mass” into this “mass personalization.” A car owner using the service can know in real time about the health of the car's engine, upcoming road conditions (what exactly is the next best action?), precisely where he or she parked (or where the car is if it's been stolen), as well as a whole range of other information. Soon, we predict this type of plug-in device will be embedded in every new car (even those that retail at budget prices). The technology is also finding its way into fleets of company cars and trucks, providing organizations with far more granular insight into shipping route performance, trip optimization, and overall fleet maintenance, than has ever been available before.
What to Do on Monday? Capitalize on Code
The case studies we've presented share a basic element: people just got started. Instead of spending months outlining grand strategies in attempts to determine every possible end state, competitor move, and customer value proposition, and then outlining detailed plans for getting there, instrumentation winners simply started by putting a chip in a machine and seeing what happened. With this as a guiding philosophy, here are some tactics you should adopt and adapt to your business.
Buy an Extra-Large Box of Chips
We've shown that getting your new raw material is the first step to building effective systems of intelligence. So, first things first; start by ordering chips with everything (well, sensors, actually). There are many types of sensor and instrumentation devices, such as RFID sensors, accelerometers, proximity sensors, motion sensors, and so on. These small, often inexpensive devices can be placed on any physical thing and can generate data (i.e., about what that thing is, its physical location, etc.) and then transmit data to a reader. RFID chips, for example, are already widely used to track goods within supply chains, manage inventory management, and verify personal information in a range of applications, such as passports, access management, and contactless payment. You may even have found one opening this book!
Soon, sensors will be embedded within most if not all physical things in the world, and even within people. In fact, over 10,000 people have chips implanted under their skin already (and millions more use medical devices that are sensor-enabled).6 Seemingly the stuff of Hollywood and/or nightmares, human chip implants are a frontier of science that is still in its infancy but may in time seem commonplace.
Regardless of the specific sensor type (or the creepiness factor of people getting chipped like a pampered pet), the point is that instrumentation is an important building block of introducing AI and the new machines into your organization.
Simply saying “buy chips” is a bit hyperbolic, but we're making an important point: You and your team should view sensors as essentially free and ubiquitous, and apply them liberally.
Find a Squad of Data Scientists
Once your instrumentation initiatives are in flight, you will soon notice how much data is being generated. Of course, as we examined in Chapter 5, this raw data—this raw material—is useless unless you can do something with it. This is where data scientists come into the picture. Called, perhaps a bit wishfully, the “sexiest job of the 21st century,” the data scientist's role is to find business meaning in all the data that instrumentation creates.7
In our recent research, however, big data and analytics were named the number-one hard-to-find competency, not just now but also for the next three years.8 While many respondents plan to form cross-functional teams (60%) or recruit staff (58%) to fill the gap, many others (56%) plan to increase their use of contractors and sourcing providers. Whichever you choose, the important thing—so important that it may mean the difference between success or failure—is getting access to smart people to help you pull business insight from rapidly filling lakes of data.
Everything you do to build systems of intelligence hinges on your organization's ability to use the new raw material of the machine age. Without the talent to do this, every step we outline within this book is moot. Recruit, retrain, contract, acqui-hire, beg, steal, or borrow.9 The future of your work depends on it.
Build a Halo Business Model
Information begets value, but not without a little help. As we said before, the real key is to simply get started, but at some point you need to show a material ROI.
Virtually every solution we've looked at during the past several years shares the same pattern. Someone had a really rough but interesting idea, and they just started. Even though solutions are different, in all the cases we've investigated, once a business begins to compete with code, the business model emerges.
This may sound easier said than done, but it's happening every day, and it all boils down to establishing the logical link between insight and value. The best advice we ever heard about this is to keep it simple and follow the money.
A large industrial player is now able to commit to very specific savings targets for its customers. A medical-device company now has lower maintenance costs and a streamlined new product development process. Managers of each of these real-world scenarios know that their solutions create real value, and in each case they found a way to monetize that value.
Redesign Your Customer Experiences
Code Halos initially emerged in the world of “consumerized” IT. The members of what we call the Trillion Dollar Club (Google, Amazon, Apple, Facebook, Netflix, and Pandora)10 were all primarily business-to-consumer, not business-to-business, technology companies. The Web 2.0 movement of the early 2000s led the way in making applications and technology-based services easy on the eye, easy to use, engaging, youthful, and fun, in contrast to “big business” technology, which was (and to a large extent still is) difficult to use and less concerned with making things intuitive and visually attractive.
The Trillion Dollar Club, along with many other companies and organizations (e.g., the social news aggregator Reddit, Twitter, Mashable, microblogging platform Tumblr, room booking app Hotel Tonight), realized that to generate (and keep) users, they needed to simplify the complexity of using technology and compete in markets that increasingly overlapped with the fashion and entertainment industries.
The company that first brought all these trends together was, of course, Apple. Apple realized that the design of a device or an experience—how it looked, how it felt, how it was used, how it was experienced, what feelings and sensations it generated in its user—was no longer something briefly considered by marketers long after engineers had done the real work; it was absolutely central to the entire end-to-end process of creating, manufacturing, and selling the device or service.
The success of this philosophy speaks for itself. The beauty of Apple products and the Apple experience has made it the most financially successful company in the history of business. Though “beauty” is an odd, ephemeral, subjective, seemingly non-quantifiable thing, good design has turned out to be the biggest generator of wealth in history. Even the coldest, hardest-hearted, most cynical accountant has to be impressed by that.
The lesson from Apple is that making “things” beautiful is not an esoteric exercise for those with nothing better to do; rather, it is the highest priority on your to-do list. Every example of a successful machine highlighted in this book has a design-thinking approach at its core. Narrative Science, Palantir, New Classrooms, and all the other companies offering systems of intelligence understand that technology for technology's sake is no longer a winning formula.
To build winning machines, you need to have this obsession too. Good design is not a nice-to-have; it's an impossible-without, in every aspect of your business. If you're not involving designers from the very beginning of product and services development, you're trying to win a fight with one hand tied behind your back. You're playing an old game when there's a new game in town.
Keep Away from the Dark Side
Once people understand the idea of competing with code, their minds start ticking through the worst-case scenarios of how corporations and governments and hackers can use information provided directly or indirectly (via the metadata of our online activity) to scam, trick, or simply rob us blind. This is the “dark side of the halo.”
The thinking behind these dark thoughts is not hard to decipher. The day-to-day news is full of horror stories that show we truly are living in a “world without secrets,” as Gartner analyst Richard Hunter put it.11 In just the past few years, we've seen a raft of high-profile examples of hacking, including the following:12
- Anthem: 80 million records of current and former customers of the U.S. health insurer were reportedly exposed.
- Ashley Madison: 32 million customer accounts of this infamous dating site were accessed.
- Central Intelligence Agency Director John Brennan: His personal e-mail account was broken into and details were shared online.
- The U.S. Government's Office of Personnel Management: 21 million people's records were hacked, including the fingerprints of 5.6 million federal employees.
- Sony Pictures: 47,000 Social Security numbers of employees and contractors were stolen, and e-mails between executives discussing the production and launch of the film The Interview were made public.13
- Democratic National Committee (DNC): 20,000 e-mails from top officials were placed on WikiLeaks.14
- Yahoo: 500 million customer accounts were hacked.15
Not surprisingly, legislators are increasingly focused on wading into these fast-moving and complex waters. The European Union passed a new law—General Data Protection Regulation—in the spring of 2016, encoding the notion of a “right to be forgotten.”16 In the United States, the Federal Bureau of Investigation was facing a Supreme Court showdown over its request that Apple provide information from the iPhone of the San Bernardino shooter until the agency managed to crack into the phone without Apple's assistance.17
All this activity and anxiety notwithstanding, the dark side of the halo still shows no sign of dampening people's enthusiasm for the bright side of the halo. We still continue to vote with our fingers. In the second quarter of 2016, Facebook had 1.7 billion active users per month, up from 1 billion in 2012.18 At the time of writing, Amazon's market capitalization (around $400 billion) has raced past Walmart's (just over $200 billion), surpassing it for the first time in 2015.19 Google became the most valuable company on Earth in February 2016.20 It's clear that—collectively—we place connection, convenience, and insight far above these hacking risks. This is good news for business, because it means we are all getting used to the idea that bad things will happen, but we still expect companies to take sufficient steps to keep us safe because treating data well is the foundation of trust, as shown in Figure 8.2. There are no easy answers, but fortunately, early winners provide some ideas on the rules of the road.
- Don't be creepy. The business economics of trust and security are now clear. In our research, we've found that 50% of consumers are ready to pay a premium to do business with companies they trust, and 57% will walk away from companies that have lost their trust (see Figure 8.2).21 Being very clear about what data you are collecting, why you are collecting it, and what you'll do with it are the first steps to gaining customer trust. Companies have gotten into trouble when they've tried to draw conclusions based on information in a way that leaves customers feeling invaded. We've all felt this when we see an ad for something shortly after a Google search or find our Facebook feed leaking into our ad feed. It doesn't feel right, and more than that, we now know this is shaping brand perceptions.
- Give your customers a delete button. A growing number of companies have realized that allowing customers to easily opt out of an information-sharing relationship is a healthy way of giving agency back to all of us, and this helps avoid creating those creepy feelings. Make the delete button easy to find. Hiding it at the end of a labyrinth isn't going to help you win trust points. People give companies data with an implied or explicit contract, and part of the contract is that we should all be able to walk away with our data. If someone wants out, make sure she can find the exit door easily.
- Show me you know me. As data exchanged becomes increasingly informative, companies are able to draw more personal conclusions about each of us. Companies may know if we are prone to driving drunk, have an illness, are getting ready to have a baby, tend to be altruistic, lean to the left or the right politically, and so forth. If a customer asks, “What do you know about me?” you have an obligation to share that information back. Even if no one ever asks, you should be ready to be transparent about the kinds of insights you can draw, based on the information you have.
- Shine a light on the “give-to-get” equation. Commerce means exchanging value for goods and services, and that doesn't change in a digital economy. Now, however, what's changing hands (or servers) is data. Consumers (or companies) are sharing information for value. We call this the give-to-get relationship. To maintain trust, companies must be explicit about the data being collected and the value being delivered in exchange.
- Hard-code self-control. As we noted in Code Halos, “Self-regulation by organizations will be a critical element of success.” Virtually every major enterprise has loads of content and mountains of policies related to security, privacy, and regulatory compliance. These are decidedly not going away, but they are also insufficient for managing a new economy built on the value of data. In addition, people who will have access to this data will make mistakes. On rare occasions, there may even be a bad actor seeking access to your data for personal gain. What we've learned from forward-thinking companies succeeding in the digital economy is that we need to hard-code self-control. This doesn't mean wrapping yourselves with a protective layer of lawyers and un-implementable processes. It does mean that someone's job should be focused on worrying about data protection, risk exposure, and managing your company's new relationship with data. Because technology outpaces policy, laws and regulations will never catch up. There are no turnkey solutions to risk management, but appointing a chief digital risk officer or amending an existing role to recognize and manage your new risks and responsibilities related to code is a good first step.
- Breaches will happen, but they are not a death sentence. Security breaches are now expected, so you should get ready to absorb and manage the inevitable hacks. The targets of the biggest macro-hacks— JMPC, the U.S. Office of Personnel Management, Target, among others—paid a steep price, but virtually all are still open for business.22 Learn from them: prepare for the dark side of digital, but don't conclude that one adverse event will bring down the company.
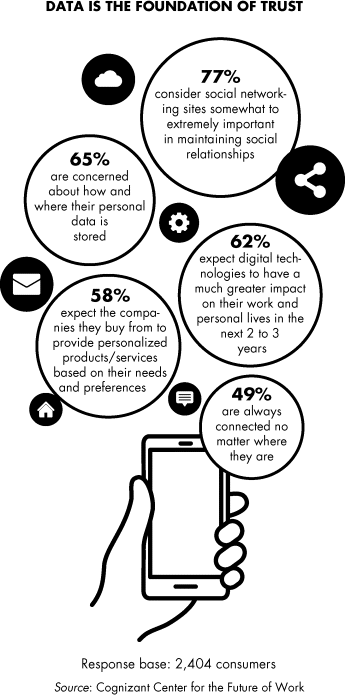
Figure 8.2 Data Is the Foundation of Trust
Monetize Your Data
Given that data is the raw material for the Fourth Industrial Revolution, it's perhaps no surprise that some companies are now leveraging this proprietary asset by selling it on the market, creating entirely new revenue streams (at enormous margin) that simply didn't exist only a few years ago.
Comcast, for example, has a data “lake” (more like a small sea, actually), full of information on consumers' media consumption habits. This includes data not only on set-top box media but, in many cases, on our browsing habits and more. Comcast is now offering access to its code for a price, because it recognizes that this data is a treasure trove of insight for many other companies.23
Iora Health, another company attempting to disrupt the currently dysfunctional U.S. health care system (like TriZetto), is offering a new commercial model based on patient health outcomes, community health coaches, and data management. So far, it's working. By increasing patient engagement, Iora has seen a 35% to 40% reduction in hospitalizations and a 12% to 15% drop in health care costs.24 In both of these cases, organizations are focusing on data-rich processes and applying new technologies and business models to generate value by monetizing data and accessing much larger markets. You should be doing this too.
Digits over Widgets: The Next Age of Business and Technology
Competing with code is now becoming the default model for our modern economy. Instrumenting everything, accessing data scientists and other big data/analytics talent, and avoiding the dark side of the halo are all tactics you must adopt to get started. Fortunes will be won and lost depending on your organization's ability to leverage the upsides of the halo and mitigate its downsides.
In Chapter 7, we showed how automation will be used to cut costs from virtually every business function. That cash must be used to bring Code Halo solutions to life. Winning with data is the number-one competitive game in nearly every industry. Companies that fail to embrace this strategy are destined to come face-to-face with their own extinction event.
Next, we'll explore how systems of intelligence can allow us to be better than we are—smarter, more efficient, more engaged—in short, “enhanced.”