CHAPTER 6
So You Want to Be a Pen Tester?
Penetration testing is an exciting and challenging field. However, many aspiring penetration testers don’t know where to start. For example, you might be wondering: How do I enter the field? Once I’m an established practitioner, how do I get to the next level and really refine my tradecraft? How can I begin to work for myself? How can I provide as much value as possible to the entities that have put their trust in me? You should strive to try to be the best in the world at what you do because the pursuit of excellence is a noble thing. If penetration testing is your chosen field, this chapter will guide you through the development and refinement of your pen-testing career.
This chapter covers material intended to provide a career roadmap for aspiring penetration testers. The chapter also provides a model for existing practitioners who wish to become industry experts in penetration testing. We’ll discuss what you can do to optimize your efforts, improve your skill set, and reduce the risk of working as a pen tester. We’ll cover training and degree programs, hacking games, and Capture the Flag (CTF) competitions, as well as give you an idea of the resources available to you to refine your tradecraft. With a little study, a little practice, and a little guidance, you’ll find that developing from a novice to an expert is an achievable goal.
In this chapter, we discuss the following topics:
• The journey from novice to expert Pen tester ethos, pen tester taxonomy, practice resources, training, degrees, professional organizations, conferences, and so on.
• Pen tester tradecraft Liability reduction, operational risk reduction, insurance, managing and executing a pen-testing project, reporting efficiencies, and so on.
The Journey from Novice to Expert
To become a master in any field, a combination of adeptness, passion, commitment to practice, and resiliency is needed. The challenge of developing from a novice to an expert is eased with study, practice, mentorship, and the understanding that neither success nor failure is permanent. A rewarding career as an ethical hacker means that you will fail (many times), learn from your mistakes, and then master the skill—only to then find the industry evolving to present you with your next challenge. The cycle is relentless and wonderful.
Pen Tester Ethos
Curiosity of spirit is the heart of the pen tester ethos. An ethical hacker strives to understand the systems in play and acts to subvert them—to not use them as they were intended, but to use them in novel ways. To hack a system is to understand it, to turn a system’s nature against itself, to challenge the common way. Ethical hackers reinvent and transform systems when they make them act in unintended ways. Curiosity is not a sin or a crime—nor is knowledge. In fact, knowledge applied ethically, and with the intent of doing good, is one of the most powerful weapons we have against those who mean to harm us. We aim to understand the attack vectors that the bad guys would use against us and to use that knowledge to prevent attacks.
Ethical hacking is still misunderstood by many, evoking fear and curiosity alike. The heavy prosecution of early hackers and a general fear of those who possess that skill set has led to a culture where ethical hackers have a heavy focus on fighting injustices, preserving our rights and freedoms, and pushing back when privacy is put at risk. The tumultuous history between security researchers and the courts have led to the hacker community building close alliances with organizations like the Electronic Frontier Foundation (EFF) and the American Civil Liberties Union (ACLU). The often-cited Hacker’s Manifesto gives us insight into the anger, frustration, and rebelliousness of the early hacking community. The Hacker’s Manifesto also touches on aspects of the pen tester ethos that promote equality, justice, and an inclusiveness not seen in other industries or communities.

NOTE See the “For Further Reading” section at the end of the chapter for pointers to the websites, organizations, and sources mentioned in this chapter.
Pen Tester Taxonomy
As we discuss curiosity, the trait that all hackers have in common, it’s important to discuss the differences among us as well. There is no shortage of areas a pen tester can specialize in. Although there are exceptionally talented individuals among us who have many areas of expertise, most pen testers specialize in only a few areas. When beginning a pen-testing career, it’s important to play to your strengths.
Penetration testers who have a software development background may focus more on exploit development and manipulating code. Those who have specialized in physical security in past military careers may have more of a specialty in bypassing locks or manipulating cameras and doors. Those with engineering backgrounds may be more apt to work with embedded device testing. Many pen testers have a broad focus, using their experience in IT operations to specialize in hacking the enterprise. Those who have experience working on supervisory control and data acquisition (SCADA) systems tend to focus on pen testing of industrial control systems (ICSs) simply because they have a basic understanding to expand upon. The goal is to acknowledge the experience that you have and learn to build on that knowledge.
The Future of Hacking
As different technology becomes available to the masses, like software-defined radio (SDR), or new technology is developed, like artificial intelligence (AI) and machine learning systems, we’ll see pen testers develop specialties in assessing and mitigating their attack vectors. Almost any “smart” device of the future will need to be understood, assessed, and have its vulnerabilities remediated. Currently, biomedical device manufacturers are beginning to understand the importance of securing their devices. I imagine a future where advanced nanotechnology-based medical technology is ubiquitous and pen testers are researching how to prevent and detect attack vectors. Technology that today seems like science fiction will become tomorrow’s reality. Technological advancements of the future will require smart penetration testers and security researchers who are up to the challenge of securing these advancements. I look forward to seeing what we come up with.
Know the Tech
Technology is going to continue to advance, becoming more complex and connected. The skills needed to assess the attack vectors of future technology will evolve as technology evolves. Ethical hackers must possess the aptitude to solve complex problems, as well as the curiosity and work ethic needed to keep up with emerging technology. The best pen testers have a diverse skill set that’s complemented by several specialties. A critical aspect of developing into an expert penetration tester is learning how to code. That is why Chapter 2 provides you with some information on programing survival skills.
At the most basic level, a pen tester should understand the technology they are assessing. Understanding basic technical information related to your target is necessary. If you are working with embedded hardware or Internet of Things (IOT) devices, an understanding of system engineering and embedded Java would be beneficial. If you are assessing the perimeter security of a company that provides cloud services, then understanding the programing language used to create the applications and database technology is a good starting point. Penetration testers working on assessing an enterprise would benefit from understanding the operations systems, applications, and networking technology in use. For example, if you are testing an environment centered around AS400 systems, then it’s important to understand the nuance of the technology and how it differs from other technology.
Know What Good Looks Like
In addition to understanding the technology you are assessing, it’s important to have a solid fundamental understanding of security operations and best practices. Knowing what “good security” looks like for a certain device or technology will allow you to properly remediate issues that are discovered. For this reason, Chapter 8 focuses on next-generation security operations.
Understanding how attacks are performed is one aspect of cybersecurity. However, the true intent of a pen tester is to be able to protect an organization by understanding how to detect and, when possible, prevent the attacks they can perform. An ethical hacker who lacks the knowledge to remediate the vulnerabilities they discover is missing an important perspective. For this reason, we’ve included information about defensive security controls in Chapter 8.
Knowing what good looks like can take many forms. One of the most valuable resources a new pen tester can have is finding a seasoned professional to mentor them. Mentors don’t have to be people you know well or even interact with in person. The ethical hacking community has always put a premium value on knowledge transfer. Many ethical hackers provide valuable information on Twitter, via blogs and articles, and in various books available on the subject. Novice pen testers would benefit from reading Penetration Testing: A Hands-On Introduction to Hacking, by Georgia Weidman (No Starch Press, 2014). It is a beginner’s guide that takes you through the basics, like setting up a virtual machine and learning what a man page is. The book then expands into topics like antivirus evasion and smartphone pen testing. Another excellent resource is the many Hacking Exposed books that have been released. The Hacking Exposed books (also published by McGraw-Hill Professional) have a variety of focuses, including mobile, wireless, and industrial control systems.
Pen Tester Training
Many training options are available that will help you develop the skill set needed to become a great pen tester. Each year Black Hat offers a variety of training options at its well-known conferences; the SANS Institute offers many onsite and remote training options; and Offensive Security offers some well-respected options as well. Numerous penetration-testing certifications exist that vary in difficulty and quality, so getting training from an industry-recognized source is important. Courses from the SANS Institute that prepare you for the Global Information Assurance Certification (GIAC) Certified Penetration Tester (GPEN) exam are a good starting point. However, Offensive Security’s family of certifications, beginning with the Offensive Security Certified Professionals (OSCP), are widely recognized as the cream of the crop of pen-testing certifications. During the OSCP exam, you are given access to a lab and 24 hours to demonstrate your hacking skills. Your ability to successfully execute attacks and write a professional report are what earn you an OSCP certification.
Other penetration-testing certifications include the E-Council’s Certified Ethical Hacking (CEH) certification. However, unless a certification requires you to demonstrate your hacking abilities in a lab, quite frankly, I would take it for what it is—a valuable resource that teaches you the vocabulary and process of hacking without mandating that you demonstrate your hacking skills or ability to write a pen test report. There’s certainly value to any knowledge acquired via certifications like the GPEN and CEH that don’t require you to demonstrate your ability at the keyboard. Those certifications are certainly valuable to the industry and to pen testers alike, but it’s important to know the difference between the approaches taken by different certifications to choose what’s most valuable to you in your career right now. It may be best to learn the “lay of the land” with a traditional certification and then expand to OSCP-style certifications once you’ve established confidence in your abilities on a keyboard.
Practice
Some of the best training doesn’t occur in the classroom or in training sessions; it occurs on the job or in a home lab. Nothing beats real work experience when it comes to ethical hacking. Penetration-testing skills are best refined at your keyboard. The vast amount of resources available include many companies offering labs to practice hacking. These resources make it much easier today to develop pen-testing skills.
Virtual technology, including intentionally vulnerable virtual machines like Metasploitable, and other resources exist that can allow you to build entire environments for testing purposes with a fraction of the work previously required. Vulnhub.com, an industry gem, allows you access to many vulnerable systems built to allow ethical hackers a way to practice (see Figure 6-1). The resources available on vulnhub.com allow for easier skill acquisition than in the past.
Figure 6-1 Vulnhub.com is a wonderful resource of vulnerable virtual machines and virtual environments designed to give pen testers hands-on experience.
The ethical hacking community truly has its own culture. Pen testing is not only a career choice, it’s a hobby. Many pen testers spend their free time, evenings, and weekends attending security conferences and participating in CTF events, hackathons, and other hacking competitions. CTF events can come in many forms. Some events are based on the traditional CTF structure, where two opposing teams try to penetrate each other’s CTF environment and “get the flag” while simultaneously trying to harden and protect their own environment against the other team’s attacks. Notable events for beginners include “Joes vs. Pros” competitions where beginners, with some coaching and mentorship, compete against professional penetration testers. CTF events can also be Jeopardy-style tournaments, where ethical hackers compete individually to solve puzzles to reveal the “flag.” For those ethical hackers who live in small towns and might not have easy access to in-person CTF events, a multitude of online CTF events exists. Notable websites like CTF365.com and CTFtime.org (shown Figure 6-2) are valuable resources for those who want to refine their skills at home.
Figure 6-2 CTFTime.org provides an avenue for virtual Capture the Flag competitions so that anyone, anywhere can participate in a CTF event.
There are also skill-building games designed to teach and develop hacking skills, starting at the novice level. OverTheWire.org, pictured in Figure 6-3, offers war games at a variety of levels. The war game Bandit is an especially valuable resource for beginners.
Figure 6-3 OverTheWire.org’s offering of war games
The Internet is full of resources for an ethical hacker to practice on to refine their skills. You should consider participating in the SANS Institute’s NetWars or using the OSCP labs, even if you aren’t taking the certification test or already have it. Also, the Arizona Cyber Warfare Range, a nonprofit, is an excellent resource, along with many of the university-backed and private cyber ranges in existence. As always, be mindful of your activities and research sites before participating in their games. Enjoy the resources that exist now—previous generations of pen testers didn’t have these types of resources available to them.
Degree Programs
Although there are many ways to acquire a refined pen-testing skill set, formal education via college or university will always be the most comprehensive way. The comprehensive nature of a cybersecurity, computer science, or engineering degree cannot be underestimated when striving to shore up knowledge gaps. The National Security Agency (NSA) and Department of Homeland Security (DHS) jointly sponsor two programs: the National Centers of Academic Excellence in Cyber Defense and the National Centers of Academic Excellence in Cyber Operations. The goal of these programs is to broaden the pool of skilled workers capable of supporting a cybersecure nation. Well-known and respected universities such as Carnegie Mellon and the Naval Postgraduate School are among the NSA’s Centers of Academic Excellence.
Alternatives to a traditional degree program also exist. For example, Harvard University created the Harvard Extension School, which allows students to take courses without first having to be admitted into Harvard University. If a student excels in three courses at the Harvard Extension School, they qualify for admission into a degree program. The CS50 course, an introduction to computer science at Harvard, is a particularly good place to start. This creates a path for anyone to take courses at Harvard, and those who do well may pursue a degree from one the most respected universities in the country. Other well-respected universities like the Massachusetts Institute of Technology make their courses available online for free, and Stanford University offers up to 100 free online courses to make their classes accessible to the masses.
On the other hand, a multitude of innovative higher learning institutions are offering accredited programs to facilitate cybersecurity degrees based on work experience, aptitude, and industry certifications. This newer approach to traditional education combines traditional degree programs with programs that allow adults to receive college credit for their technical industry certifications or to test out of classes by demonstrating their on-the-job knowledge. This approach works well for the “hands-on” nature of ethical hacking skills. Newer competency-based schools such as Western Governors University are attempting to shift the paradigm in education and redefine higher education with new, and somewhat controversial, approaches to online degree programs. Most of the technical classes lead to an industry certification, providing immediate value to a working professional’s career.
Knowledge Transfer
One of the best sources of information about penetration testing comes from other security professionals in the community. An endless number of videos can be found online that span most aspects of penetration testing. For example, videos of talks at cybersecurity conferences are regularly released online. Videos of talks at the Black Hat and DEF CON security conferences are useful even to those who were able to attend the conference in person, because no one is ever able to see all of the talks. Irongeek.com’s repository, which contains DerbyCon and ShmooCon content, might also be useful. For international readers, ZeroNights and SyScan conference content may be of particular interest.
Unlike in many other industries, the cybersecurity community treats the acquisition of skills more like a hobby than a chore. The amount of community groups focused on the development of new pen testers shows that our community is remarkably committed to sharing knowledge and building an inclusive culture for newcomers. Sites like SecurityTube.net have been used for years to share knowledge.
An active pen-testing community is a necessity because new attack techniques are introduced all the time. Malicious actors and security researchers reveal new attack vectors regularly. The security community is constantly working to develop security controls to remediate the current issues pen testers take advantage of. This means that the best pen testers stay abreast of offensive and defensive security techniques. They understand that while some issues persist, new attack vectors, devices, and technologies are constantly being revealed. Professional organizations like Information Systems Security Association (ISSA) and InfraGard also help with an ethical hacker’s ongoing development, and Infosec-conferences.com has useful information about conferences that can be attended.
Pen Tester Tradecraft
So far we’ve discussed building a good foundation as a penetration tester. Let’s now take the perspective that you’d like to use your ethical hacking skills professionally, for profit or for charity. Let’s suppose you’ve gotten some experience as a professional pen tester and now want to take on more responsibility. Perhaps you even want to start your own small operation with the goal of ensuring that your team can scale to handle just one large project at a time. You’re no longer a lone wolf, so you have to learn to collaborate now. In this section, we won’t cover the basics of starting a small business, but we will cover specific things to consider if you decide to start a pen-testing business.
Personal Liability
Choosing ethical hacking as a career is a fun yet gutsy move. Therefore, it’s best to think through the inevitable risks you’ll face in your chosen path. Performing a risk assessment for your small pen-testing business will be similar to risk assessments you may have been exposed to in the past. You need to consider the threats to your business, understand the vulnerabilities, and try to reduce your risk to a level that is acceptable to you.
Business Structure
When starting any business, you should structure it to reduce your personal liability as the owner. Consider creating a limited liability company (LLC) or incorporating and creating an S corp. When either of these business structures is properly implemented, it can shield your personal assets as the owner from lawsuits stemming from the business. Because penetration testing is a well-paying field, it’s best to set aside some funds to work with a lawyer and accountant to ensure you understand the nuances and limitations of operating an S corp or LLC.
Insurance
You should purchase insurance for many reasons. First and foremost, it’s important to protect your business since you’ll be investing your time and money into it. Also, you’ll often find that your business partners and clients have set minimum thresholds for the insurance types and coverage required for vendors to do business with them. You’ll want to speak to an insurance broker to guide you through the process, and the information provided is only a general recommendation intended to aid your conversations with your insurance broker. You may want to consider purchasing several types of insurance. General liability is recommended to protect your business as a whole. Technology errors and omissions (E&O) provides critical coverage in case you “make a mistake or miss something.” If you can get it, you should also consider cyberinsurance. Security companies are valuable targets for attackers, and cyberinsurance helps to protect your organization if it’s the victim of an attack.
Reducing Operational Risk
It’s always a good idea to run a criminal background check for anyone who has access to sensitive information in any environment. The ethical hacking field has more potential for “bad apples” than other fields. The responsibility is yours to ensure that your team members are ethical hackers and have the judgment and maturity to not put your clients at risk. Make sure you are performing criminal background checks that include both local and national database searches. Do a meticulous job checking references, verifying degree programs, and verifying past military experience. Sit down and take the time to talk to potential team members. Listen for conflicting statements and inaccuracies. I’m shocked to see how many resumes are fabricated and how often I encounter “stolen valor,” a false claim of past military experience.
Create a strategy for securely operating within your technical environment. You should have technical, administrative, and physical security policies and technical security controls in place to protect your client’s data. Even small teams need well-thought-out procedures in order to stay organized, reduce risk, and increase efficacy.
Being the Trusted Advisor
Your clients are depending on you to be their trusted advisor. You have the responsibility of making good recommendations to them. Often clients will have budget constraints and will ask for assessments that don’t meet their regulatory requirements or that are just too small to provide true value to them. You must be wary of giving clients a false sense of security. Take the time to ensure you have a good understanding of what’s going on in the organization. The ultimate responsibility for making good decisions related to penetration testing belongs to the organization’s leaders. However, they’ll rely on your input and recommendations to steer them in the right direction.
Penetration tests are performed for the greater good. Testing activities are often detailed, arduous, and require a good amount of effort and resolve. You aren’t doing this for your health, after all—you are doing it to protect the assets you’ve been entrusted with. To provide as much value as possible, you need to understand and define the appropriate nature, duration, frequency, and scope of your work. Most importantly, you must tie all your efforts back to the business impact and focus on what your assessment results mean to the organization.
An overview of the pen-testing process was provided in Chapter 1. This chapter expands on those topics and aligns them to provide as much value as possible to an organization. This means selecting the correct methodology and tools and refining your choices until you find solutions that make you the best pen tester you can be.
At an absolute minimum, an organization should perform an enterprise penetration test once per year. Having a penetration test once a year is often insufficient for most organizations. However, when we take into consideration that most systems change and are updated frequently and that new attacks appear all the time, it’s often necessary to perform a penetration test more than once a year. Many compliance requirements, such as PCI and HIPAA, require a penetration test only once a year or after significant changes are made to the environment. The trouble with such vague requirements is that it is often hard to define what meets the threshold to count as a “significant change,” and they don’t take into consideration the uniqueness of each environment. An organization whose security program is in its infancy might not benefit from frequent penetration testing. It may only need to have an initial test done to determine its likely attack vectors and then focus on building a robust security program before having another test performed. Annual penetration tests are often performed by an external entity, thus allowing for more objectivity in testing.
Frequent penetration testing is recommended for most environments that have an established security program and a dynamic environment. Conducting quarterly or monthly testing allows for faster identification and remediation of exploitable cybersecurity issues. It also allows for a greater focus on certain areas of the environment or security program, and the tests can be tailored to align with the organization’s goals. For example, the first quarter can be dedicated to internal penetration testing, the second quarter to web application testing, the third quarter to testing the organization’s security response and incident response capabilities, and the fourth quarter can focus on social engineering. Large entities with disparate locations can focus on a different location each quarter (or more frequently, if needed). When quarterly penetration tests are performed by internal staff, it is often necessary to have an annual penetration test performed by a third party to ensure objectivity is maintained.
Many entities that grow through acquisitions will have penetration testing built into their merger and acquisition (M&A) process. Penetration testing that occurs prior to an acquisition can help set the price of an entity. Many preacquisition penetration tests reveal issues that can cost millions of dollars to resolve. Testing activities that occur after a purchase can help an organization understand the amount of risk it has acquired and to formulate a plan to address it. Using a penetration test to address risk that must be managed during the integration of disparate networks “post-merger” can provide a valuable perspective to an organization.
Entities with mature security programs understand that the risk information provided by a penetration test is valuable and needed on an ongoing basis. Some organizations with a mature security program work penetration-testing and security assessment activities into their change management program, requiring that potential risk due to compromise or unauthorized access be addressed before new deployments can gain approval to be deployed into the production environment. Mature organizations that develop software often have implemented Secure Software Development Lifecycle (SSDLC) processes that require penetration testing to ensure that risk to the organization’s environment and software is limited. Long-term red or purple team exercises can last six months to a year and allow an organization to test its incident response capabilities in greater detail. These long-term assessments often involve regular meetings and monthly or quarterly out-briefs to provide input to the organization.
When you’re pen-testing a product, it is best to include time in the schedule to fix any issues identified prior to the launch of the product. High- or critical-level vulnerabilities can often delay the release of a product when time is allocated for testing, but not for remediation of the issues the test revealed. Product penetration tests should also be performed when significant updates are released.
Managing a Pen Test
Managing a penetration test is like managing other technical projects. You can reduce the risk to the project’s success via proper planning and good communication. Some of the basics of a pen test were covered in the “Emulating the Attack” section of Chapter 1. The content provided in this chapter assumes that you understand the basics now and want to learn ways to improve your processes and optimize your efforts.
Organizing a Pen Test
White or gray box assessments begin with some knowledge or full knowledge of the environment. You’ll need a “data call” to gather the information about the technical environment. It’s best to prepare a question set ahead of time or use one of the many checklists available on the Internet. Gather information about personnel, IP address ranges, out-of-scope systems and networks, technical details of particular systems and targets, active security controls the client has in place, and so on. If phishing attacks are in scope, try to perform some early reconnaissance and submit a list of e-mail targets for approval ahead of time. The question set will vary depending on what you’re assessing, but it’s best to get into the habit of communicating early and often.
Briefly mentioned in Chapter 1 is the importance that all parties understand the scope of the assessment. A detailed statement of work (SOW) helps to ensure there are no misunderstandings. Always have a clear description of the nature and scope of the assessment in your paperwork; whether you call it a contract, proposal, statement of work, or scoping paper, it’s best to define the scope in writing in a document that your client will sign. If your assessment has a physical security component, be sure to get a signed “Get Out of Jail Free Card” or authorization letter. The letter should be used to defuse potentially hostile situations in case your client’s security guards or staff encounter or detain anyone on the pen test team. The letter should state that a penetration test is occurring and that the members of the assessment team, listed in the letter by name, are authorized to perform testing activities. The authorization letter should have a contact number for the security guards to call, usually the head of physical security or cybersecurity at the client’s company.
You’ll likely have a scheduling phone call and a detailed kick-off meeting. Use the kick-off meeting to confirm the scope and focus of the assessment and to discuss fragile systems. You should also talk through the methodology, step by step. It’s best to discuss the ideas you have in mind for any phishing campaigns and try to get preapproval. Review the schedule and logistics, and be sure to define client milestones so your client knows what you’ll need from them and when you’ll need it. Logistical issues you may need to cover include getting a small conference room or office to work out of, discussing access to network ports and internal VLANs, and obtaining physical access badges and parking passes. You may want to request working out of a room with a door that locks at night so you can leave equipment at the client site during the internal phase of the pen test.
Also, for most short-term penetration tests, you’ll want to avoid “cat-and-mouse” scenarios where your client is actively blocking and trying to defend against your attacks. Some assessments are intended to allow a defensive security team to actively protect the network and thus “practice” those skills. Regardless of the type of assessment, it’s necessary to have detailed discussions about the “rules of engagement.” When discussing the rules of engagement, you’ll want to talk about the client’s “active defenses” (security controls in place that can slow down or stop an attack). Be sure to always give a client credit in their report for the security controls they have in place.
One of the best methodologies I’ve seen used to address “active defenses” is simple. If a control is stopping you from moving forward during your pen test, just ask the client to allow you to bypass it. Then you can continue with your testing until you’re sure you’ve provided value to the client, testing each security layer. Afterward—and this is crucial—go back and work to bypass that original control you had trouble with. Many security controls can be bypassed one way or the other, time permitting.
Another aspect of the rules of engagement is determining the best course of action for the IT help desk to take if a user calls in and reports something related to the pen test. Usually, it’s best to disclose the fact that a pen test is occurring to the fewest number of people possible, and often the IT help desk is not aware that an assessment is occurring at the beginning of the test. After all, the IT help desk is a frequent target during a pen test. However, this is always a balancing act, and the IT help desk will frequently get “read in” during that assessment so they can appropriately respond to user inquiries and reports. Ideally, the IT help desk will begin to execute triage procedures when an event is reported, and the pen test team can begin to gauge the client’s response.
As simple as it seems, be sure to exchange contact information with your client and their team. You may need to call your client outside of business hours, so be sure to get mobile phone numbers and know who the best person to call is after hours. You might decide to call your client after hours for a variety of reasons. Occasionally, a penetration tester will encounter indictors of compromise (IOC) in the client’s environment, indicating that the client has an active breach occurring. Also, sometimes a critical vulnerability is discovered on the client’s perimeter, and it’s best to not wait until the next morning to disclose this fact to your client.
You’ll need to e-mail different types of sensitive information during a penetration test. It’s best to ensure you have a secure e-mail system in place that includes encryption and multifactor authentication. Make sure it provides your client a secure way to send and receive information. This way, when they are sending you information about their personnel or environment, or when you are sending them their pen test report, an established and secure communication channel can be used.
Executing a Pen Test
There are so many pen-testing tools and techniques that it’s impossible to cover them all. We cover more specific information on hacking methodologies in the next couple of chapters. Because in this chapter we are discussing the pen tester tradecraft, let’s talk about some ideas that can help you work effectively and present yourself in a more refined manner while executing a pen test.
There’s always value in collaborating with others and taking advantage of their skills and experience. A variety of pen-testing collaboration tools make it easy to take a team approach. While executing a penetration test with a team, consider using a collaboration tool like Armitage with Cobalt Strike or Faraday. These tools allow for a team approach so that team members can stay in sync, and they add visualization features that facilitate team work.
Accountability is important. Ensure your team members are accountable for their actions by enabling logging on their tools and devices. Occasionally, a client environment may experience a technical problem during your pen test and the client will want to know if it was caused by your testing activities. If logging is properly enabled on your software and testing infrastructure devices, you’ll be able to confirm precisely who was working on what testing activities and when.
One of the most arduous parts of a penetration test is writing the report. Reports can often be 60 pages or more in length. A great report will have an executive summary, a variety of diagrams, a summary of findings, and a section with in-depth information about each finding. Each finding should have evidence and remediation guidance. Also, it’s always nice to give credit where credit is due. Add a section to your report that describes the client’s current security controls so that the client’s efforts are recognized.
Now let’s talk about report generation and supporting processes and technologies. Each day leading up to the pen test and throughout the assessment, you’ll learn information about the client. Be sure to document the things you learn as “findings” and “good findings.” If an attack was successful, you may have a “finding” for your report. If the attack wasn’t successful, then stop to ask yourself, “What prevented the attack from working? What made it difficult? Is there anything I can give the client credit for?” Then record those thoughts as “good findings.” Add information and findings to your report on an ongoing basis. Jot down details while the information is fresh in your mind. End each day by recording and reviewing your findings. You can make writing the final report a less arduous task by reporting as you go.
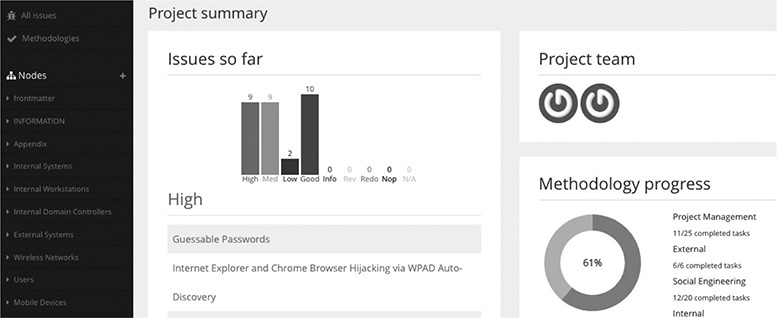
Also, pen test reporting technology exists that we as technologists can put to good use. Pen test reporting tools integrate or include databases so that you can create a findings repository. You’ll find that many of your clients have similar findings, and it’s not efficient to write the same findings repeatedly. Therefore, every time you have a new finding, be sure to sanitize it and put it in your findings database. This way, the next time you must write a new finding, you can see if some existing verbiage can be used from previous findings. Several great pen test reporting tools are available, including the tried-and-true Dradis, shown in Figure 6-4. Dradis allows you to create report templates and pull information from findings you’ve entered into VulnDB, the findings database. Whatever tool you decide to use, be sure it allows you to assign a risk rating to your findings.
Figure 6-4 Dradis integrates with VulnDB, allows you to categorize your pen test findings, and offers project management features to help you track overall progress.
Finally, guide your clients through any “close-out” activities at the end of your pen test. Ensure you tell them what computers they’ll need to reboot. If you created any accounts, be sure to tell the client so they can delete those accounts. Also, discuss any changes made to the environment so that they can be appropriately reviewed or disabled. You need to establish a data retention period as well. Your clients are much better off if you only retain data about their environment for a limited amount of time. Therefore, be sure to talk your clients through your retention and destruction policies.
Summary
In this chapter, we discussed a wide range of topics intended to help you continue down the path to becoming an expert pen tester. This entire book is designed to give you guidance through the many activities that will help you become an advanced pen tester. We discussed the pen tester ethos and gave a nod to our history with a mention of the Hacker’s Manifesto. Many different paths can lead a person to becoming a pen tester. We covered a variety of resources that will help you practice your skills and keep them fresh, including training, formal education, and hacking games.
After discussing ways to refine your pen-testing skills, we discussed how to refine your tradecraft. Guidance was provided about starting a small operation to allow you to profit from your abilities. We discussed reducing your legal liability while optimizing your efforts. The benefits gained from working with others using collaboration and reporting tools cannot be overstated. We also discussed the responsibilities that come with being a pen tester or running a small pen-testing operation. These include screening your team, organizing your efforts, maintaining accountability for your actions, and logging everything. The responsibility that comes with being a trusted advisor means that you should always strive to make ethical recommendations that are in your client’s best interest.
For Further Reading
American Civil Liberties Union (ACLU) https://www.aclu.org/
Arizona Cyber Warfare Range http://azcwr.org/
Armitage www.fastandeasyhacking.com/
Black Hat www.blackhat.com/
Cobalt Strike https://www.cobaltstrike.com/
CTF Time https://ctftime.org/
CTF365 https://ctf365.com/
DEF CON https://www.defcon.org/
DerbyCon https://www.derbycon.com/
Dradis https://dradisframework.com/ce/
E-Council’s Certified Ethical Hacking (CEH) https://www.eccouncil.org/programs/certified-ethical-hacker-ceh/
Electronic Frontier Foundation (EFF) www.eff.org
Faraday https://www.faradaysec.com/
GIAC GPEN www.giac.org/certification/penetration-tester-gpen
Hackers Manifesto – Phrack.org, January 8, 1986 http://phrack.org/issues/7/3.html
Hacking Exposed https://www.mhprofessional.com/9780071780285-usa-hacking-exposed-7-grou
Harvard Extension School https://www.extension.harvard.edu/
Information Systems Security Association (ISSA) www.issa.org/
Infosec Conferences https://infosec-conferences.com/
InfraGard https://www.infragard.org/
Irongeek www.irongeek.com/
Massachusetts Institute of Technology Open Courseware https://ocw.mit.edu/index.htm
National Centers of Academic Excellence in Cyber Operations https://www.nsa.gov/resources/educators/centers-academic-excellence/cyber-operations/
NSA – National Centers of Academic Excellence in Cyber Defense https://www.nsa.gov/resources/educators/centers-academic-excellence/cyber-defense/
Offensive Security Certified Professional https://www.offensive-security.com/information-security-certifications/oscp-offensive-security-certified-professional/
Offensive Security https://www.offensive-security.com/
OverTheWire: Wargames http://overthewire.org/wargames/
Penetration Testing: A Hands-On Introduction to Hacking (Georgia Weidman) No Starch Press, 2014
SANS NetWars https://www.sans.org/netwars
SecurityTube.net https://www.securitytube.net/
ShmooCon http://shmoocon.org/
Stanford University Online http://online.stanford.edu/about
SyScan https://www.syscan360.org/en/
The SANS Institute https://www.sans.org/
Vulnhub https://www.vulnhub.com/
Western Governors University https://www.wgu.edu/
ZeroNights https://2017.zeronights.org/