9. THE MINECRAFT WARS
Every profession has its public faces—its doyens, deans, sages, gurus, old hands, éminences grises, international authorities, spokespeople for the field. These trusted professionals translate technical issues for the general public and offer sensible suggestions about how to resolve them. They are the go-to specialists whenever journalists need an expert opinion or a good quote. For cybersecurity, one of those specialists is Bruce Schneier.
Schneier looks just as our Representativeness Heuristic says he should: trim, medium height, with a full, well-groomed gray beard and perpetually balding hair tied into a long ponytail. Schneier is known for his flowery shirts and flattop taxicab hats. He is outspoken and unapologetic. Schneier invented the term security theater, arguing that the post-9/11 reforms to airline security only make us feel safer. In reality, they’ve made us less safe. According to Schneier, the purpose of x-raying your shoes is to convince you to get on the plane, not to stop terrorists from blowing it up.
On September 13, 2016, Schneier posted a disturbing entry titled “Someone Is Learning How to Take Down the Internet” on Lawfare, a blog widely read by the national security community. Schneier reported that, in the past year, there had been multiple attempts to probe the core infrastructure of the internet. These attacks were not indiscriminate. Rather, they were “precisely calibrated attacks designed to determine exactly how well these companies can defend themselves, and what would be required to take them down.” The post was a warning. When Bruce Schneier warns, the security industry listens.
Schneier noted that the easiest way to take down the internet would be a Distributed Denial of Service attack, known as a DDoS (pronounced Dee-dos). In a DDoS, the attacker attempts to shut down a computer service by exhausting its resources—available bandwidth, network connections, memory, storage space, or its central processing units. To exhaust these resources, attackers typically use a “botnet,” a collection of bots. A single botnet can have bots distributed over hundreds or millions of infected machines around the globe. The attacker controls the bots remotely. When the attacker issues orders to the botnet, the bots deluge the target with requests from across the internet. As the server responds to these fraudulent appeals, the process consumes resources allocated for processing legitimate requests. Imagine thousands of people calling your phone at the same time. Friends and family would not get through.
DDoSs were not new in 2016. Hackers associated with the Russian Federation had shut down most of Estonia’s websites for three weeks in 2007 using the same basic technique. But these attacks had not targeted core internet infrastructure. They did not go after internet service providers, the Domain Name System, or Tier 1 high-speed networks that comprise the “internet backbone.” Until now.
Because companies don’t like to announce cyberattacks and treat their occurrence as highly confidential, Schneier could not name names. But he reported that the past year had seen multiple strikes against the support systems of the internet, the unsung yeomen that run the global digital internetwork. Even worse, Schneier reported that these hacks had become more powerful. Botnets were sending floods of requests that were bigger and lasted longer than ever before. The attacks also appeared to be methodical. “One week, the attack would start at a particular level of attack and slowly ramp up before stopping. The next week, it would start at that higher point and continue. And so on, along those lines, as if the attacker were looking for the exact point of failure.”
Schneier did not suspect private individuals or groups. “It doesn’t seem like something an activist, criminal, or researcher would do.” Probing core infrastructure, however, is standard for nation-states. Intelligence agencies routinely delve deep into the technical guts of the internet for spying and information collection. The scale of the attacks also suggested actors with large budgets and immense capabilities. Schneier compared the testing to America’s Cold War practice of flying high-altitude planes to activate Soviet air defense systems and then map their capabilities. If nation-states were responsible, their raids would be illegal aggression. They would be starting a cyberwar.
Schneier was not alone in noticing the uptick in DDoS attacks. From April through June of 2016, Akamai, one of the largest DDoS mitigation providers, reported a 129 percent increase in such attacks compared to the same period in 2015. According to Kyle York, chief strategist for the internet infrastructure company Dyn, “It’s a total Wild, Wild West out there.”
Schneier did not have any advice to offer. If a nation-state attacked the core digital infrastructure with enough firepower, it would flatten the internet and cause a major global disruption. “What can we do about this? Nothing, really,” Schneier sighed. “But this is happening. And people should know.”
Confirmation came swiftly. On September 18, five days after Schneier’s post, a ferocious attack was launched against the French cloud computing provider OVH. At its height, the attack clocked in at 1.2 terabits (terabit = trillion bits) per second, via 152,000 internet-connected devices, including closed- circuit television cameras and personal video recorders. The botnet that targeted OVH was twenty times larger in volume than any of its rivals. These raging torrents knocked OVH, the largest cloud provider in Europe, off-line.
No one claimed credit, but the attack on OVH seemed to confirm Schneier’s hypothesis that someone, probably a nation-state, was testing core internet infrastructure. Who else had that kind of firepower and would stir up this kind of trouble?
At 8:00 p.m. EDT on Tuesday, September 20, another massive DDoS attack was launched, this time against a cybersecurity blog, Krebs on Security. In his long career specializing in cybercrime reporting, Brian Krebs has exposed numerous illicit enterprises, especially bank and credit card fraud operations out of Eastern Europe. Krebs has faced massive retaliation for the exposés he posts on his blog.
Because Krebs’s blog had been attacked so many times—his website was the target of 269 DDoS attacks between 2012 and 2016—the company Akamai offered its DDoS protection for free. But even Akamai—which runs the largest networks in the world—could barely handle the onslaught. Reports estimated that the attack threw an incredible 620 gigabits per second at Krebs’s site, orders of magnitude more than needed to take out a simple blog. Akamai claimed that the Krebs attack was twice as large as any other it had ever encountered. Though its defenses held, Akamai dropped Krebs as a customer, pleading that it could no longer afford to donate its services, even for journalists crusading against cybercrime.
October 21
At 7:07 a.m. on Friday, October 21, 2016, major websites including Twitter, Netflix, Spotify, Airbnb, Reddit, Etsy, SoundCloud, and The New York Times disappeared. The sites were still up and running—visitors just couldn’t find them. Not if they were on the East Coast of the United States, that is. By attacking the infrastructure that enabled millions of users to access these sites, the most extreme DDoS attack to date made them vanish.
Dyn is a company based in Manchester, New Hampshire, that provides Domain Name System (DNS) resolution services for much of the East Coast of the United States. DNS servers translate human-readable domain names (www.example.com) into computer-readable IP addresses (203.0.11.0), so that browsers can make sense of them. Just after seven in the morning, a DDoS attack took Dyn’s servers off-line; without them, users could not access websites by their domain names. It was as if all the telephone directories were stolen and no one could look up the numbers of people they wanted to call.
Just as Dyn managed to divert the early-morning barrage, a second wave began at 9:30 a.m. A third barrage slammed the company before noon, and a fourth pummeled it at 5:00 p.m. Each successive surge caused outages to spread farther west until much of web traffic in the United States was affected. “This was not your everyday DDoS attack,” Kyle York, Dyn’s chief strategist, noted. The salvos were heavier, longer, and more sophisticated.
The law enforcement and intelligence communities had no leads, but Schneier’s recent warning loomed large. Only a nation-state would have the means, motive, and opportunity to take down the internet in the United States. Especially concerning was the timing: the presidential vote was a fortnight away, scheduled to take place on November 8. Were the Russians preparing to take down the internet on Election Day? Thirty-one states and the District of Columbia allowed internet voting for the military overseas and for certain civilians. Alaska let any voter cast their choice over the internet. “A DDoS attack could certainly impact these votes and make a big difference in swing states,” said Dr. Barbara Simons, a member of the board of advisers to the Election Assistance Commission, the federal body that oversees voting technology standards.
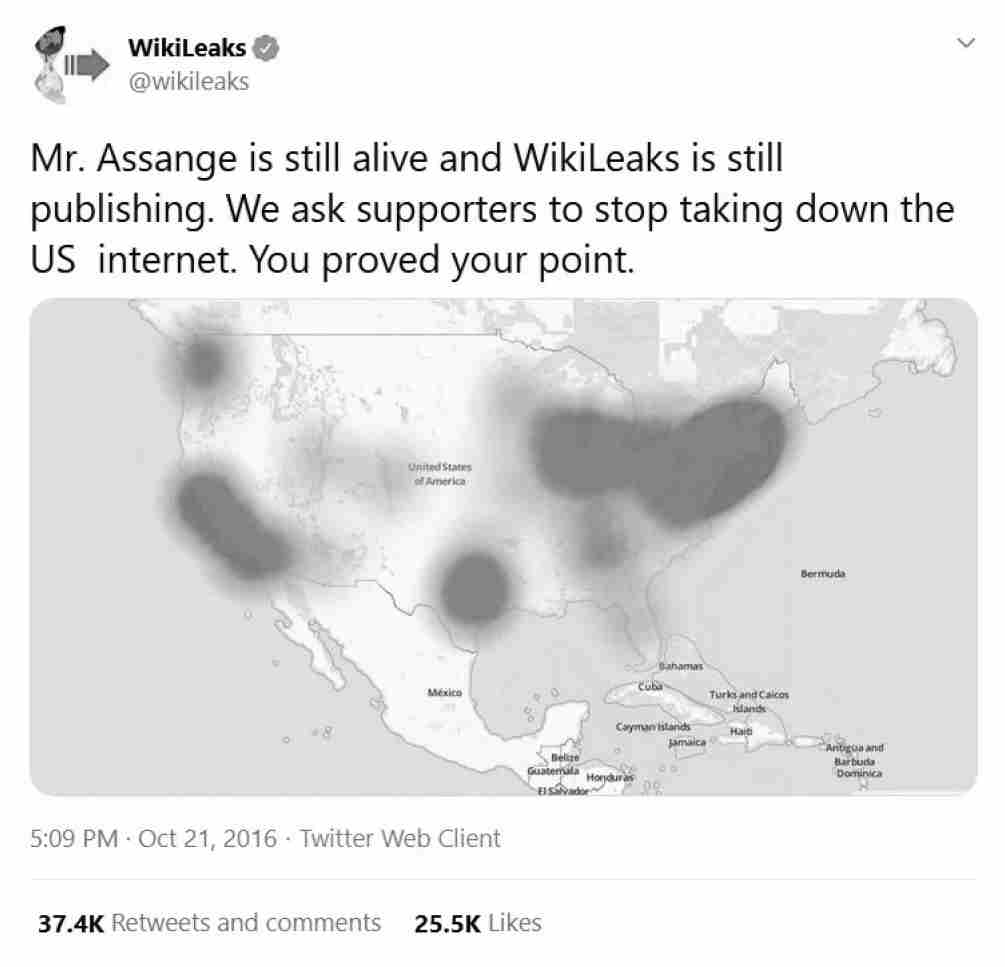
At 5:00 p.m., WikiLeaks posted an internet outage map on Twitter. Hacktivist groups such as Anonymous had claimed responsibility, saying that they were retaliating for Ecuador’s termination of Julian Assange’s internet connection. However, no evidence backed up their boasts, and no one believed that they had access to such ammunition.
Using red blotches to indicate affected areas, WikiLeaks’ map made it appear as though the internet in the United States had been fried to a crisp. The internet was still working, even though many popular websites were no longer reachable in the usual way. Service was down in the Northeast, the upper Midwest, Texas, California, and Washington State, the country’s centers of computer use. Since WikiLeaks had been affected by a similar DDoS attack a month earlier, its Twitter account assured the world, “Mr. Assange is still alive and WikiLeaks is still publishing”; it asked “supporters to stop taking down the US internet. You proved your point.”
Just two weeks earlier, the U.S. intelligence community had fingered Russian intelligence in the hack of the DNC. Some even suspected that WikiLeaks had actively been involved in the Guccifer 2.0 cover-up scheme. Were the pessimists right after all? Could WikiLeaks be covering again for the Russians, who were preparing to launch a cyberwar?
Attacking the University Registrar
First-year college students are understandably frustrated when they can’t get into popular upper-level electives. But they usually just gripe. Paras Jha was an exception.
Enraged that upper-class students were given priority to enroll in a computer-science elective at Rutgers University, Paras decided to crash the registration website so that no one could enroll. On Wednesday night, November 19, 2014, at 10:00 p.m. EST—as the registration period for first-year students in spring courses had just opened—Paras launched his first DDoS attack. He had assembled an army of forty thousand bots, primarily in Eastern Europe and China, and unleashed them on the Rutgers Central Authentication server. The botnet sent thousands of fraudulent requests to authenticate, overloading the server. Paras’s classmates could not get through to register for the next semester. Given its vulnerability to the DDoS attack, Rutgers decided to build up its defenses. The university invested $3 million to upgrade its systems, which it passed on to the students in a 2.3 percent tuition increase.
The next semester Paras tried again. He not only enjoyed the notoriety the first attack received, but was also desperate to delay his calculus exam. On March 4, 2015, he sent an anonymous email to the campus newspaper, The Daily Targum: “A while back you had an article that talked about the DDoS attacks on Rutgers. I’m the one who attacked the network … This might make quite an interesting story … I will be attacking the network once again at 8:15 pm EST.” The newspaper kept the email secret while alerting the police. Paras followed through on his threat, knocking the Rutgers network off-line at precisely 8:15 p.m.
On March 27, Paras unleashed another assault on Rutgers. This attack lasted four days and brought campus life to a standstill. Fifty thousand students, faculty, and staff had no computer access from campus. They could not log on to check course websites, university announcements, or email. Frustrated students did not know who was throttling their network, or why, but Paras was delighted. “He was laughing and bragging about how he was going to get a security guy at the school fired, and how they raised school fees because of him,” a friend later reported.
On April 29, Paras posted a message on the website Pastebin, popular with hackers for sending anonymous messages. “The Rutgers IT department is a joke,” he taunted, using the handle ogexfocus to conceal his identity. “This is the third time I have launched DDoS attacks against Rutgers, and every single time, the Rutgers infrastructure crumpled like a tin can under the heel of my boot.” Paras was furious that Rutgers chose Incapsula, a small cybersecurity firm based in Massachusetts, as their DDoS mitigation provider. He claimed that Rutgers chose the cheapest company. “Just to show you the poor quality of Incapsula’s network, I have gone ahead and decimated the Rutgers network (and parts of Incapsula), in the hopes that you will pick another provider that knows what they are doing.” Rutgers was paying Incapsula $133,000 a year for a product that did not work—or at least not against Paras’s powerful botnet.
Paras’s fourth attack on the Rutgers network, taking place during finals period, caused chaos and panic on campus. Since online materials were unavailable, deans and chairs pleaded with faculty not to give final exams, but to offer paper options instead.
Paras reveled in his ability to shut down a major state university. But his ultimate objective was to force it to abandon Incapsula. Paras had started his own DDoS mitigation service, ProTraf Solutions, and wanted Rutgers to pick ProTraf over Incapsula. And he wasn’t going to stop attacking his school until it switched.
Vertical Integration
In the hit NBC comedy 30 Rock, the corporate executive Jack Donaghy (played by Alec Baldwin) tries to explain to one of his head writers, Liz Lemon (played by Tina Fey), the economic concept of vertical integration: “Imagine that your favorite corn chip manufacturer also owned the number one diarrhea medication.”
Liz’s eyes light up. “That’d be great ’cause then they could put a little sample of medication in each bag.”
Jack can see that Liz does not fully appreciate the business logic. “Keep thinking.”
Liz turns the idea over in her mind as she works out the economics. “Except then they might be tempted to make the corn chips give you…”
Jack smiles. “Vertical integration.”
Although Donaghy called it “vertical integration,” lawyers have traditionally used another term: racketeering. In its strictest sense, a racket is a fraudulent scheme in which the racketeer creates a problem and forces the victim to pay for the solution. In a protection racket, for example, the local strongman threatens to torch neighborhood stores or beat up merchants if they do not pay for “protection”—the proverbial offer you can’t refuse.
Protection rackets tend to cover rival gangs, so that one payment to the strongman protects the merchant from others as well. Mobsters do not offer this umbrella protection out of gratitude or goodwill. Their aim is to freeze out competitors. If a rival racketeer tries to muscle in, the local boss will protect his turf. The local mobster aims to monopolize protection services and be the only provider.
When Donaghy described vertical integration to Lemon, she was shocked because his corn chip maker was running a scam—a diarrhea racket, if you will. It sold the medicine to cure the ailment it caused. “Wow, this should not be allowed to happen,” she gasped.
According to the famous sociologist Charles Tilly, it is allowed to happen. All the time. Tilly argued that European states arose by rulers imposing protection rackets on their subjects. In contrast to philosophical accounts like the social contract, where individuals freely trade their liberties for state protection, Tilly claimed that the state acquired its authority through extortion. By provoking wars with rival powers, European princes created threats to their subjects. Without protection, they would be open to attack from “enemy” forces. To remedy the situation, these very same princes offered their protection services to these individuals … for a price. That price is called a tax.
Taxes helped pay for armies that defended subjects. Subjects had incentives to pay these taxes because they wanted protection from the enemy (even when their protectors were provoking their enemies). Subjects had another motivation: if they didn’t pay their taxes, they were subject to harsh punishment. Like the local mobster, the state made offers its subjects could not refuse.
Taxes were not only used for protection; they were used to consolidate power over territory. States demilitarized the powerful feudal lords—confiscating their guns, disbanding their militias, razing their castles—and built up armies to take their place. The states asserted a monopoly over the use of force and prosecuted those who refused to acknowledge their supreme coercive authority—“making it criminal, unpopular and impractical for most of their citizens to bear arms.”
According to Tilly, the European state began as a protection racket, but did not remain one. When states succeeded in eliminating rivals in the Early Modern period, they switched from illegitimate racketeering to legitimate protection. European states no longer intentionally created threats. Instead, they pledged to destroy threats not of their own making.
Cyberspace is an ideal forum for rackets. Like poorly governed borderlands, cyberspace constitutes a vast power vacuum that gives raiders the opportunity to harass users. And it also provides the opportunity to sell their protection services to victims for a price.
By DDoS-ing Rutgers University, Paras Jha was running a protection racket. He was trying to force Rutgers to give up Incapsula and switch to his firm, ProTraf. When Rutgers stuck with its choice, Paras Jha set out to teach his university a painful and expensive lesson.
Minecraft
Paras Jha was born and raised in Fanwood, a leafy suburb in Central New Jersey. The oldest son of Anand and Vijaya Jha, Paras was different from the other children in the neighborhood. He lagged developmentally and found it difficult to make friends. Awkward and withdrawn, he was bullied by other children.
When Paras was in the third grade, a teacher recommended that he be evaluated for attention deficit hyperactivity disorder (ADHD). ADHD is an executive-function disability that decreases mental attention and increases impulsive behavior. Paras had many signs of ADHD. Despite being highly intelligent, he found school a challenge. He had trouble paying attention in class, following his teachers’ rules, and turning in assignments on time. Paras would focus only on those subjects that he found interesting. But when he focused, he was transfixed.
Paras’s mother, Vijaya, was disturbed by his teacher’s suggestion. She viewed a diagnosis of ADHD as meaning that her son was not destined for greatness. She wanted to believe that her oldest was the “quickest, fastest, and most intelligent son.” Unfortunately, ADHD in children is diagnosed through questionnaires filled out by parents and teachers. Because his mother intentionally answered the questions incorrectly, Paras was misdiagnosed. He did not receive the therapy, medicine, and accommodations that would have helped him.
As Paras progressed through elementary school, his struggles increased. Because he was so obviously intelligent, his teachers and parents attributed his lackluster performance to character flaws such as laziness and apathy. His perplexed parents pushed him even harder.
Paras sought refuge in computers. He taught himself how to code when he was twelve and was hooked. His parents happily indulged this passion, buying him a computer and providing him with unrestricted internet access. But their indulgence led Paras to isolate himself further, as he spent all of his time coding, gaming, and hanging out with his online friends. Vijaya was unhappy with her son’s burgeoning obsession. Anand, however, was pleased. He took pride in Paras’s programming prowess and hoped that coding would be his son’s ticket to success and affirmation. Anand even set up a website for his son to exhibit his work.
Paras was particularly drawn to the online game Minecraft. Minecraft is a video game in which players explore a world made out of pixelated blocks. Players mine these blocks for raw materials to build tools, furniture, houses, gardens, castles, even Turing Machines. The game supports single and multiplayer modes. In multiplayer mode, individuals can cooperate in teams or compete with others from all around the internet. The game is easily “modded”—that is, modifiable to generate new worlds with different rules and novel capabilities. Many players switch between Minecraft servers that host these modded games, usually for a fee.
Although Minecraft is a “blocky” video game with a cartoonish look—the characters’ hands do not even have fingers—it is wildly popular, especially with adolescent boys. Microsoft has sold over 200 million copies since buying the game in 2014 (current price: $26.99); on any given day 55 million users play it. The market for popular Minecraft servers is also lucrative—some hosting services make as much as $100,000 a month.
In ninth grade, Paras graduated from playing Minecraft to hosting servers. He wrote on his website about the satisfaction he felt “seeing others enjoy my work.” It was in hosting game servers, however, that he first encountered DDoS attacks. Because the competition between servers is so fierce, Minecraft administrators often hire DDoS services to knock rivals off-line. Others can buy DDoS tools on the web for as little as $15 or watch YouTube videos to learn how to launch these attacks themselves. By taking Minecraft servers off-line, attackers hope to poach their customers. “If you’re a player, and your favorite Minecraft server gets knocked off-line, you can switch to another server,” Robert Coelho, vice president of ProxyPipe, a San Francisco company specializing in defending Minecraft servers, explained. “But for the server operators, it’s all about maximizing the number of players and running a large, powerful server. The more players you can hold on the server, the more money you make. But if you go down, you start to lose Minecraft players very fast—maybe for good.” Paras’s servers were routinely targets of these attacks.
Coehlo had been friends with Paras when he started out. They stopped communicating, however, after Paras joined Hackforums.net, an online platform used by newbie hackers looking to trade tips and brag about their exploits. Hack Forums also ran a malware marketplace where hackers advertised their products and services. “He just kind of dropped off the face of the earth entirely,” Coelho said. “When he started going on Hack Forums, I didn’t know him anymore. He became a different person.” On these online forums, Paras fell in with a bad crowd. According to Coelho, Paras was a member of lelddos, a group of DDoSers who were active in 2014. Lelddos would taunt their victims before they took them off-line, usually posting their insults on Twitter. These hooligans specialized in attacks on Minecraft servers.
As Paras learned more sophisticated DDoS attacks, he also studied DDoS defense. As he became proficient in mitigating attacks on Minecraft servers, he decided to create ProTraf Solutions. “My experience in dealing with DDoS attacks led me to start a server hosting company focused on providing solutions to clients to mitigate such attacks,” he wrote on his personal website. The company’s website, protrafsolutions.com, noted that its team had been managing and administering game servers “ever since 2009.” In 2009, Paras was twelve, the year he learned how to code.
Paras’s obsession with Minecraft attack and defense, compounded by his untreated ADHD, led to an even greater retreat from family and school. His poor academic performance in high school frustrated and depressed him. His only solace was Japanese anime and the admiration he gained from the online community of Minecraft DDoS experts.
Paras’s struggles deteriorated into paralysis when he enrolled in Rutgers University studying for a BS in computer science. Without his mother’s help organizing his days, he was unable to regulate the normal demands of living on his own. He could not manage his sleep, schedule, or study. Paras was also acutely lonely. Aside from his roommate, he saw no one else. He did not attend parties, make new friends, or attend football games, which he hated but which dominated social life at Rutgers. Paras was so ashamed about his poor academic performance that he dared not tell his parents. By the end of his first year, he had been put on academic probation.
MalWar
Charles Tilly claimed that European states began as glorified protection rackets. But he made an even more shocking claim: the most celebrated features of the modern state—the rule of law, fair judicial systems, protection of property rights, efficient bureaucracies—were forged by the competition to win wars. As Tilly famously argued, “States make war and vice versa.”
To make war, Tilly pointed out, rulers need armies. But armies need money—lots and lots of money. Rulers, therefore, had to raise the vast sums to feed the maw of war in an age of gunpowder weapons and mass mobilizations. They needed wealthy subjects to tax, which required protecting property for subjects to safely invest and amass more capital. Rulers needed court systems to adjudicate disputes between these wealthy subjects and those seeking to become wealthy. And rulers needed bureaucracies to collect, count, and distribute taxes.
Tilly did not claim that this state building was deliberate. Rather, it was the result of competitive pressures, a political survival of the fittest. Weak state institutions could not produce and collect enough money to fund armies. These states’ armies lost wars more often against efficient states. Successful states conquered more territory, got larger, and collected more money; weaker states were conquered, lost territory, and saw their revenues dwindle.
The same Darwinian pressures that forged the modern state have also profoundly affected botnet malware. Like an army, the larger the botnet, the more powerful the collection of bots tends to be. Bot herders, therefore, fight over the same prize—not land, as in the case of traditional war, but vulnerable devices to infect. The malware for each side scans the internet for devices—laptops, consumer appliances, security cameras, virtual assistants, printers, doorbells, and so forth—and races to infect them. If one side discovers the other side’s malware on the device, it kills the process, deletes the competing program, and conscripts the device into its own botnet, another troop for its digital army. The more bots a side can capture, the larger the botnet it can assemble. And the larger the botnet, the more fraudulent requests it can launch and the more services it can deny. Malware that cannot raise large bot armies will therefore normally lose to malware that can.
Paras Jha would soon enter this fray. He would not start off small. He and his friends Josiah White and Dalton Norman would go after the kings of DDoS—a gang known as VDoS. VDoS was the leading provider of DDoS in the world. They had been providing these services for four years—an eternity in cybercrime. The decision to fight experienced cybercriminals may seem brave, but the trio were actually older than their rivals. The VDoS gang members had been only fourteen years old when they started to offer DDoS services from Israel in 2012. These nineteen-year-old American teenagers would be going to battle against two eighteen-year-old Israeli teenagers.
The war between these two teenage gangs would not only change the nature of malware. Their struggle for dominance in cyberspace would create a doomsday machine.
Crime as a Service
Not all Denial of Service attacks use botnets. In 2013, the Syrian Electronic Army (SEA)—the online propaganda arm of the brutal Bashar al-Assad regime—hacked into Melbourne IT, the registrar that sold the nytimes.com domain name to The New York Times. The SEA altered the DNS records so that nytimes.com pointed to SEA’s website instead. Because Melbourne IT contained the authoritative records for the Times’ website, the unauthorized changes quickly propagated around the world. When users typed in the normal New York Times domain name, they ended up at a murderous organization’s website.
Conversely, not all botnets launch Denial of Service attacks. Botnets are, after all, a collection of many hacked devices governed by the attacker remotely, and those bots can be used for many purposes. Originally, botnets were used for spam. The Viagra and Nigerian Prince emails that used to clutter inboxes were sent from thousands of geographically distributed zombie computers. In these cases, the attacker reaches out to their army of bots, commanding them to send tens of thousands of emails a day. In 2012, for example, the Russian Grum botnet sent over 18 billion spam emails a day from 120,000 infected computers, netting its botmaster $2.7 million over three years. Botnets are excellent spam infrastructure because it’s hard to defend against them. Networks usually use “block lists”: lists of addresses that they will not let in. To block a botnet, however, one would have to add the addresses of thousands of geographically disbursed servers to the list. That takes time and money.
Because the malware we have seen up till now—worms, viruses, vorms, and wiruses—could not work together, it was not useful for financially motivated crime. Botnet malware, on the other hand, is because the botnets it creates are controllable. Botmasters are capable of issuing orders to each bot, enabling them to collaborate. Indeed, botnet malware is the Swiss Army knife of cybercrime because botmasters can tell bots in their thrall to implant malware on vulnerable machines, send phishing emails, or engage in click fraud allowing botnets to profit from directing bots to click pay-per-click ads. Click fraud is especially lucrative, as Paras Jha would later discover. In 2018, the ZeroAccess botnet could earn $100,000 a day in click fraud. It commanded a million infected PCs spanning 198 countries, including the island nation of Kiribati and the Himalayan Kingdom of Bhutan.
Botnets are great DDoS weapons because they can be trained on a target. One day in February 2000, the hacker MafiaBoy knocked out Fifa.com, Amazon.com, Dell, E*TRADE, eBay, CNN, as well as Yahoo!, then the largest search engine on the internet. He overpowered these web servers by commandeering computers in forty-eight different universities and joining them together into a primitive botnet. When each sent requests to the same IP address at the same time, the collective weight of the requests crashed the website.
After taking so many major websites off-line, MafiaBoy was deemed a national security threat. President Clinton ordered a countrywide manhunt to find him. In April 2000, MafiaBoy was arrested and charged, and in January 2001 he pled guilty to fifty-eight charges of Denial of Service attacks. Law enforcement did not reveal MafiaBoy’s real name, as this national security threat was only fifteen years old. MafiaBoy later revealed himself to be Michael Calce. “You know I’m a pretty calm, collected, cool person,” Calce reported. “But when you have the president of the United States and attorney general basically calling you out and saying, ‘We’re going to find you’ … at that point I was a little bit worried.” Calce now works in the cybersecurity industry as a white hat—a good hacker, as opposed to a black hat, after serving five months in juvenile detention.
Both MafiaBoy and the VDoS crew were adolescent boys who crashed servers. But whereas MafiaBoy did it for the lulz, VDoS did it for the money. Indeed, these teenage Israeli kids were pioneering tech entrepreneurs. They helped launch a new form of cybercrime: DDoS as a service. DDoS as a service is a subscription-based model that gives subscribers access to a botnet to launch either a daily quota or unlimited attacks, depending on the price. DDoS providers are known as booter services or stressor services. They come with user-friendly websites that enable customers to choose the type of account, pay for subscriptions, check status of service, launch attacks, and receive tech support.
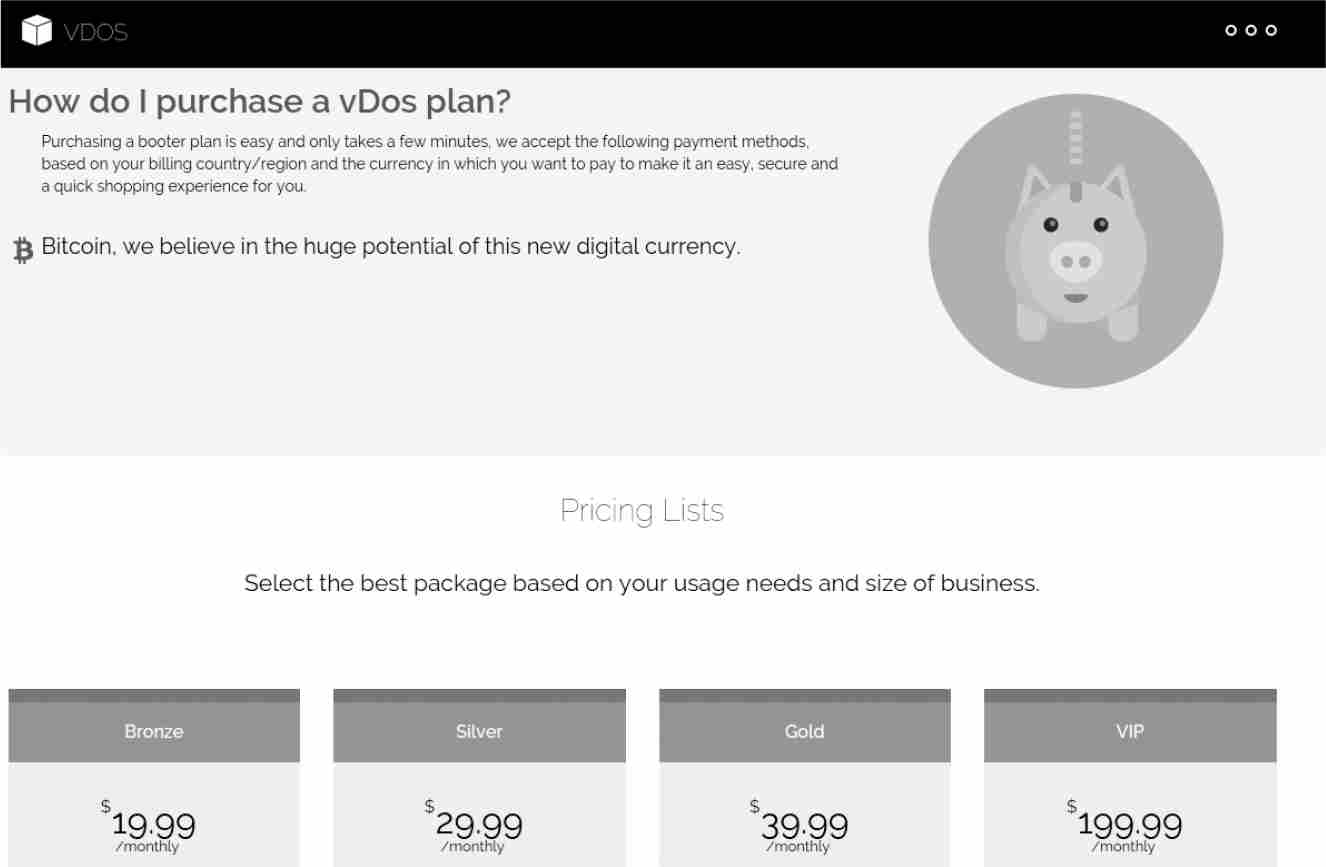
VDoS advertised their booter service on Hack Forums, the same site on which, according to Coelho, Paras Jha spent hours. On their website, www.vdos-s.com, VDoS offered the following subscription services: Bronze ($19.99/month), Silver ($29.99/month), Gold ($39.99/month), and VIP ($199.99/month) accounts. The higher the price, the more attack time and volume. At its peak in 2015, VDoS had 1,781 subscribers. The gang had a customer service department and, for a time, accepted PayPal. From 2014 to 2016, VDoS earned $597,862, and it launched 915,287 DDoS attacks in one year.
VDoS democratized DDoS. Even the most inexperienced user could subscribe to one of these accounts, type in a domain name, and attack its website. “The problem is that this kind of firepower is available to literally anyone willing to pay thirty dollars a month,” Allison Nixon, director of security research at business-risk-intelligence firm Flashpoint, explained. “Basically what this means is that you must have DDoS protection to participate on the internet. Otherwise, any angry young teenager is going to be able to take you off-line in a heartbeat.” Even booter services need DDoS protection. VDoS hired Cloudflare, one of the largest DDoS mitigation companies in the world.
DDoS as a service was following a trend in cybercrime known as “malware as a service.” Where users had once bought information about software vulnerabilities and tried to figure out how to exploit those vulnerabilities themselves, or had bought malicious software and tried to figure out how to install and execute it, they could now simply pay for the use of malware and hack with the click of a button, no technical knowledge required.
Because customers who use DDoS as a service are inexperienced, they are particularly vulnerable to scams. Fraudsters often advertise booter services on public discussion boards and accept orders and payment, but do not launch the promised attacks. Even VDoS, which did provide DDoS service, did so less aggressively than advertised. When tested by Flashpoint, VDoS botnet never hit the promised fifty gigabits/second maximum, ranging instead from six to fourteen gigabits/second.
The boards that advertise booter services, as Hack Forums once did, are accessible to anyone with a standard browser and internet connection. They exist on the Clear Web, not on the so-called Dark Web. To access sites on the Dark Web you must use a special network, known as Tor, typically using a special browser known as the Tor Browser. When a user tries to access a website on the Dark Web, the Tor Browser does not request web pages directly. It chooses three random sites—known as nodes—through which to route the request. The first node knows the original sender, but not the ultimate destination. The second node knows neither the original source nor the ultimate destination—it recognizes only the first node and the third node. The third node knows the ultimate destination, but not the original sender. In this way, the sender and receiver can communicate with each other without either knowing the other’s identity.
The Dark Web is doubly anonymous. No one but the website owner knows its IP address. No one but the visitor knows that they are accessing the website. The Dark Web, therefore, tends to be used by political dissidents and cybercriminals—anyone who needs total anonymity. The Dark Web is legal to browse, but many of its websites offer services that are illegal to use. (Fun fact: the U.S. Navy created the Dark Web in the mid-1990s to enable their intelligence agents to communicate confidentially.)
It might be surprising that DDoS providers could advertise on the Clear Web. After all, DDoS-ing another website is illegal everywhere. In the United States, one violates the Computer Fraud and Abuse Act if one “knowingly causes the transmission of a program, information, code, or command, and as a result of such conduct, intentionally causes damage without authorization,” where damage includes “any impairment to the … availability of data, a program, a system, or information.” To get around this, booter services have long argued they perform a legitimate “stressor” function, providing those who set up web pages a means to stress test websites. Indeed, booter services routinely include terms of service that prohibit attacks on unauthorized sites and disclaim all responsibility for any such attacks.
In theory, stressor sites play an important function. But only in theory. Private chats between VDoS and its customers indicated that they were not stressing their own websites. As a booter service provider admitted to Cambridge University researchers, “We do try to market these services towards a more legitimate user base, but we know where the money comes from.”
Poodle Corp
Paras dropped out of Rutgers in his sophomore year and, with his father’s encouragement, spent the next year focused on building ProTraf Solutions, his DDoS mitigation business. After launching four DDoS attacks his freshman year, he attacked Rutgers yet again in September 2015, still hoping that his former school would give up on Incapsula. The attacks had become so frustrating that an open letter circulated among students demanding a tuition refund—the $3 million they were spending on cybersecurity was not working. Still, Rutgers refused to budge.
ProTraf Solutions was failing. The company had a few small Minecraft clients, but Paras was having trouble keeping the lights on. He needed cash. In May 2016, Paras reached out to Josiah White. Josiah lived in Washington, Pennsylvania, went by the handles “lightspeed” and “thegenius,” and was a skilled malware coder. Like Paras, Josiah frequented Hack Forums. When he was fifteen, he developed major portions of Qbot, a botnet worm that at its height in 2014 had enslaved half a million computers. Qbot went by many different names—Bashlite, Gafgyt, Lizkebab, and Torlus. Malware vendors often change names of their products to make it appear that they are selling improved versions. Now eighteen, Josiah switched sides and worked with his friend Paras at ProTraf doing DDoS mitigation.
In an online chat, Paras hit up Josiah for money: “I hate to ask you this, but do you have anything? Any Bitcoins or something that can be cashed?” Josiah suggested instead that they create a DDoS service to make some money. Josiah knew someone who was upgrading his Qbot botnet due to increased demand for booter services. “An old friend wants to release v2 [version 2.0] of an old project and has people lined up to fill us up with btc [Bitcoin].” Paras replied, “Sounds ill ey gahl.” “eh kinda,” Josiah agreed.
Josiah declined the offer from his old friend and started working with Paras. They would take the Qbot malware, improve it, and build a bigger, more powerful DDoS botnet. Josiah told Paras in June 2016 that he believed they could make $10,000 to $15,000 a month.
Paras and Josiah partnered with Dalton Norman, also nineteen years old, hacker name Uber, hailing from Metairie, Louisiana. He specialized in finding vulnerabilities in consumer electronic devices. The trio turned into a well-oiled team: Dalton found the vulnerabilities, Josiah updated the botnet malware to exploit these vulnerabilities, and Paras wrote the C2—the Command and Control server—for controlling the botnet.
But the trio had competition. Two other DDoS gangs—LizardStresser and VDoS—decided to band together to built a giant botnet. The collaboration, known as Poodle Corp, was successful. The Poodle Corp botnet hit a record four hundred gigabits/second, almost four times higher than any previous botnet had achieved. They used their new weapon to attack banks in Brazil, U.S. government sites, and Minecraft servers. They achieved this firepower by hijacking 1,300 web-connected cameras. Because video is computationally intensive, tends to have good connectivity, and is rarely patched, a botnet that harnesses video has enormous cannons at its disposal.
While Poodle Corp was on the rise, Paras, Josiah, and Dalton worked on their new weapon. They also began to hunt for Poodle Corp’s C2 servers, which controlled Poodle Corp’s botnets, and would lodge abuse complaints against the companies that hosted them. Abuse complaints are often sent to hosting companies, alerting them to abusive behavior on their servers, such as distributing spam, trafficking in child-sex-abuse material, hosting click-fraud schemes, and engaging in software piracy. Paras knew how to draft a professional-looking abuse complaint because he ran a DDoS mitigation company and often lodged abuse complaints against companies hosting DDoS services. Administrators started to take Poodle Corp’s servers down, much to Poodle Corp’s surprise.
Mirai Nikki
By the beginning of August 2016, the trio had completed the first version of their botnet malware. Paras called the new code Mirai, after the anime series Mirai Nikki, about a lonely girl whose only friend, the God of Space and Time, gives her a diary (Japanese: nikki) about the future (Japanese: mirai). Paras began using the handle Anna-Senpai, which was also an anime reference—in particular to Anna Nishikinomiya, the main character in the series Shimoneta. She is best known as the anime character who bakes her boyfriend cookies using sexual fluids from her vagina (which she calls “love nectar”).
At 1:07 p.m. on July 10, 2016, posting as Anna-Senpai on Hack Forums, Paras declared war: “Just made this post to let you know that as of last night I will be killing qbots. Watch your botcount people.” Paras, Josiah, and Dalton were close to finishing their new botnet, and they were preparing to conquer, like European sovereigns in the early modern period. They eliminated rival botnets by having their bots use the Linux “kill” command to remove Qbots, including VDoS’s. They then sealed the devices by closing common ports so no other malware could get a toehold.
Paras also prepared the battlefield by launching a disinformation campaign. He opened fake accounts on Facebook and Reddit under a new name, OG_Richard_Stallman. Richard Stallman is the father of open-source software and the person whose account Robert Morris Jr. used to release his worm. Paras would use this handle when trying to extort money from particular DDoS victims (though he continued to use Anna-Senpai when posting on Hack Forums). Paras hoped to throw law enforcement off the trail by creating this imaginary hacker named OG_Richard_Stallman.
It is probably no coincidence that Paras’s false-flag operation coincided with Russian intelligence actions in the DNC hacks. On June 15, Fancy Bear created the Guccifer 2.0 persona on Twitter and Facebook to throw people off its track. It also created a fake website, DCLeaks.com, to disseminate the information. On July 6, Guccifer 2.0 used WikiLeaks to release the Clinton emails to a wider audience. While the FBI had never seen DDoSers use disinformation campaigns before, it made sense given the times. Disinformation was in the air.
When Mirai was released, it spread like wildfire. In its first twenty hours, it infected sixty-five thousand devices, doubling in size every seventy-six minutes. Andrew McGill from The Atlantic magazine set up a fake smart toaster—a so-called honeypot—in his house to see how long it would take Mirai to infect it. The result: forty-one minutes.
Last One Standing
Mirai had an unwitting ally. Up in Anchorage, Alaska, the FBI cyber unit was building a case against VDoS. The FBI was unaware of Mirai, or its war against Qbot. The agents did not regularly read online boards such as Hack Forums. They did not know that the target of their investigation was being decimated. The FBI also did not realize that Mirai was ready to step into the void.
The head investigator in Anchorage was Special Agent Elliott Peterson. A former marine, Peterson is a calm and self-assured agent with a buzz cut of red hair. After leaving the military, he entered the Bureau in the Pittsburgh field office, working on the GameOver ZeuS banking Trojan case. GameOver ZeuS is malware designed to set up botnets and steal credentials from those engaged in online banking. The malware was estimated to have infected close to a million Windows machines worldwide. Peterson noticed during the investigation that when cybercriminals used stolen credentials to steal money from victims, they would also DDoS the bank in question. By shutting down the bank’s network, the bank could not detect the fraudulent transactions and reverse them in time.
At the age of thirty-three, Peterson returned to his native state of Alaska to fight cybercrime. Alaska’s FBI unit is the smallest in the country, at the time having only forty-five agents. Peterson helped build their computer intrusion team with three other agents. As Marlin Ritzman, the special agent in charge of the FBI’s Anchorage Field Office, noted, Alaskans are particularly vulnerable to DDoS attacks. “Alaska’s uniquely positioned with our internet services—a lot of rural communities depend on the internet to reach the outside world. A Denial of Service attack could shut down communications to entire communities up here.”
On September 8, 2016, the Anchorage and New Haven cyber units teamed up and served a search warrant in Connecticut on the member of Poodle Corp who ran the C2 that controlled all their botnets. On the same day, the Israeli police arrested the VDoS founders in Israel. Suddenly, Poodle Corp was no more. More than a half dozen smaller booter services were using Poodle Corp’s infrastructure, and they went dark as well.
The Mirai group waited a couple of days to assess the battlefield. As far as they could tell, they were the only botnet left standing. And they were ready to use their new power.