Chapter 2
Investigative Process Models
Abstract
Over the years, there have been several different process model methodologies developed in an effort to group the common digital forensic activities into recognizable phases. From the existing process models, commonalities have been identified leading to the proposal of a new process model.
Keywords
Gathering; Model; Preparation; Presentation; ProcessingThis chapter analyzes different digital forensic process models used to support investigative workflows. You will learn about the phases contained within each process model, the uniqueness and commonalities of tasks performed, and its application toward digital forensic.
Introduction
From what was discussed in chapter “Understanding Digital Forensics,” we know that digital forensics is the application of forensic science to law and is built on the extensive common body of proven scientific principles, methodologies, or techniques that can be applied to any phase of the investigative workflow.
As early as 1984, law enforcement agencies began developing processes and procedures to use as part of their computer forensic investigations. This eventually led to the realization that, as a result of bypassing, switching, or not following correct processes, the digital investigation would result in missed, incomplete, or inadmissible evidence. Since then, several authors have attempted to develop and propose digital forensic process models to address either a specific need, such as law enforcement, or with a generalized scope with the intention that it could be adopted universally.
Existing Process Models
There have been several digital forensic process models developed over many years to address either a specific need, such as law enforcement, or with a generalized scope with the intention that the process model could be adopted universally. While there might be some process models absent from the table below, Table 2.1 contains a chronological list of process models including a unique identifier, the author(s), the publication year, and the number of phases included in the model. It is important to note that inclusion of the process models in the table does not suggest that these are better or recommended over other models that were not included.
Every digital forensic process model noted in the table below was developed with distinct characteristics and with the purpose of addressing a need within the digital forensic investigative workflow. There are, however, no criteria for stipulating which of the identified process models is the one and only right way for conducting a digital forensic investigation.
Table 2.1
Digital Forensic Process Models
| ID | Name | Author(s) | Year | Phases |
| M01 | Computer Forensic Investigative Process | Pollitt | 1995 | 4 |
| M02 | Computer Forensic Process Model | U.S. Department of Justice | 2001 | 4 |
| M03 | Digital Forensic Research Workshop Investigative Model (Generic Investigation Process) | Palmer | 2001 | 6 |
| M04 | Scientific Crime Scene Investigation Model | Lee et al. | 2001 | 4 |
| M05 | Abstract Model of the Digital Forensic Procedures | Reith et al. | 2002 | 9 |
| M06 | Integrated Digital Investigation Process | Carrier and Spafford | 2003 | 5 |
| M07 | End to End Digital Investigation | Stephenson | 2003 | 9 |
| M08 | Enhanced Integrated Digital Investigation Process | Baryamureeba and Tushabe | 2004 | 5 |
| M09 | Extended Model of Cyber Crime Investigation | Ciardhuáin | 2004 | 13 |
| M10 | A hierarchical, Objective-Based Framework for the Digital Investigations Process | Beebe and Clark | 2004 | 6 |
| M11 | Event-Based Digital Forensic Investigation Framework | Carrier and Spafford | 2004 | 5 |
| M12 | Four Step Forensic Process | Kent et al. | 2006 | 4 |
| M13 | Framework for a Digital Forensic Investigation | Kohn et al. | 2006 | 3 |
| M14 | Computer Forensic Field Triage Process Model | Rogers et al. | 2006 | 12 |
| M15 | FORZA—Digital forensics investigation framework | Ieong | 2006 | 6 |
| M16 | Common Process Model for Incident and Computer Forensics | Freiling and Schwittay | 2007 | 3 |
| M17 | Dual Data Analysis Process | Bem and Huebner | 2007 | 4 |
| M18 | Digital Forensic Model based on Malaysian Investigation Process | Perumal | 2009 | 7 |
| M19 | Generic Framework for Network Forensics | Pilli et al. | 2010 | 9 |
| M20 | Generic Computer Forensic Investigation Model | Yusoff | 2011 | 5 |
| M21 | Systematic Digital Forensic Investigation Model | Agarwal et al. | 2011 | 11 |

Depending on the purpose of why the process model was developed, such as law enforcement, there are advantages and disadvantages depending on the investigative scenario, such as, being too rigid, linear, or generalized. Appendix A: Process Models, further dissect the digital forensic process models identified in the table above to understand the tasks performed in phases and better understand the uniqueness and commonalities with investigative workflow phases. Despite the differences noted among these process models, there are still significant commonalities in how some phases are used across multiple process models. These similarities confirm that while the process models address different investigative requirements, the underlying forensic science principles, methodologies, and techniques are applied consistently throughout.
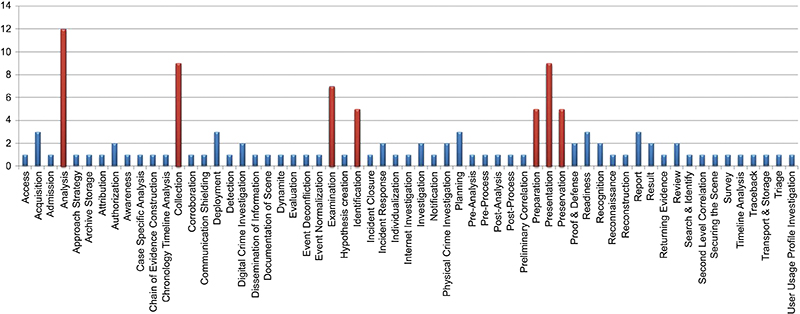
As illustrated in Figure 2.1, we can get a better sense of how some phases are frequently used across multiple digital forensic process models. Without getting caught up on the subtle differences in naming convention, it is quite apparent that there is an opportunity to consolidate all phases identified throughout each process model into these common phases. Of special note, highlighted in the figure below are seven phases that have the highest frequency of reoccurrence:
• Preparation includes activities to ensure equipment and personnel are prepared.
• Identification involves detection of an incident or event.
• Collection of relevant data using approved techniques.
• Preservation establishes proper evidence gathering and chain of custody.
• Examination evaluates digital evidence to reveal data and reduce volumes.
• Analysis examining the context and content of digital evidence to determine relevancy.
• Presentation includes preparing reporting documentation.
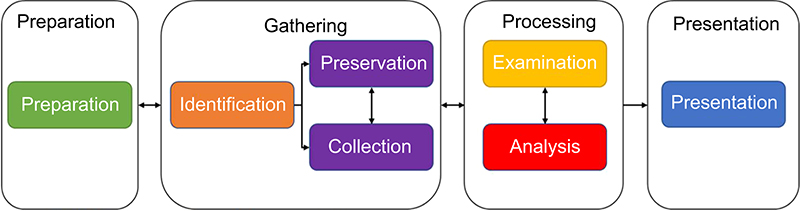
Process models developed to support the digital forensic investigative workflow are focused on establishing the activities and tasks performed throughout to ensure that processes are not bypassed, switched, or not followed. As outlined above, there are seven common phases of a digital forensic investigation workflow: preparation, identification, collection, preservation, examination, analysis, and presentation. From the descriptions of each of these phases, we see that there are further commonalities between them that allow for further consolidation of these phases into higher level grouping of workflow categories:
• Preparation includes activities to ensure administrative, technical, and physical provisions are in place.
• Gathering involves following proven techniques to identify, collect, and preserve evidence.
• Processing reveals data and reduces volumes based on the contextual and content relevancy.
• Presentation includes preparing reporting documentation.
Illustrated in Figure 2.2, the seven phases have been placed into higher level groupings based on the commonalities of when they are performed during the investigative workflow. The interrelationships between these higher level groupings common phases are illustrated in the order of how they are performed in an investigative workflow; noting the bidirectional interactions between specific phases.
Digital Forensic Readiness Model
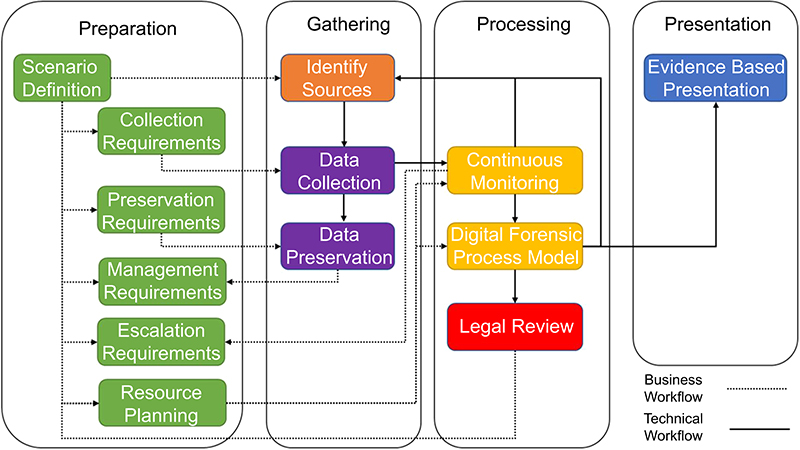
A process model developed to support digital forensic readiness is somewhat different than a process model developed for the digital forensic investigative workflow. Unlike the digital forensic investigative workflow, digital forensic readiness is not a linear process where activities and steps are executed sequentially and there are established “start/end” criteria.
A process model for digital forensic readiness consists of activities and steps within a circular and redundant hierarchy. Initiation of the digital forensic readiness process model can originate from any activity or steps and can subsequently lead to any other phase. The digital forensic readiness process model must establish administrative, technical, and physical foundations to effectively support the activities and tasks performed in all phases of the digital forensic process model by:
• maximizing the potential use of digital evidence.
• minimizing the cost(s) of digital forensic investigations.
• minimizing the interference disruption of business processes.
• preserving and improving the information security posture.
High-level groupings of a digital forensic readiness process model follow the same naming convention as the digital forensic process model. Figure 2.3 illustrates the activities and steps that make up the digital forensic readiness process model. Within this process model, there is a combination of sequential steps within each phase as well as redundant workflows that are dependent on the nature of the investigation at hand. This digital forensic process model serves as the basis for the detailed topics addressed in Section B of this book.
Summary
Digital forensics science has long established itself as a discipline that adheres to consistent, repeatable, and defensible processes. Although there have been several models developed to meet the different needs of how digital forensics practices, they are all homogenous in the design methodology. Following a process methodology that is ambiguous to context of its implementation, the digital forensic community adopts a common model as the basis for conducting consistent, repeatable, and defensible processes.