Chapter 5
Cybercriminal Activities in Dark Net
Introduction
There are lots of cybercrime activities that take place on the dark net. It has offered a breeding ground for many cybercriminals, and the results of these are slowly being witnessed. Cyberattacks are increasingly becoming more effective and also more challenging for authorities to trace where data and money stolen by cybercriminals disappear to. This is because of the structuring of the underground economy on dark nets. There are different types of actors in an attack, and each of these has been specializing and advancing their techniques. The actors responsible for creating exploits and malware have become better at it. Those that deal with money muling have also become quicker and better at ensuring that the proceeds from attacks are less traceable. When the efforts from the different actors that form a cyberattack today are combined, the end result is an advanced attack that is difficult to stop and equally challenging to investigate. This chapter will mainly focus on familiarizing you with the categories of cybercrimes, the cybercrime activities that take place on the dark net, and the new value chains that have made cyber attackers to be more effective. It will cover this in the following topics:
-
Cybercrime and its categories
-
Cybercriminal activities through the dark net
-
Data exfiltration
-
Monetization of cybercrime
-
Malware-as-a-service and money laundering.
Cybercrime and Its Categories
The commonly used definition of cybercrime is a crime that involves the use of a computer and/or a network for illegal reasons. These could include fraud, identity theft, or copyright violation among other reasons. Cybercrime has been happening on the surface net for a long time. However, the increasing popularity of the dark net has given cybercriminals a more secure space that they can operate from. The main challenge that cybercriminals seek to avoid is trails of their criminal activities leading back to them. This is because if they are traced, they can be arrested and face criminal charges and probably serve long sentences. The dark net provides an almost ideal platform for cybercriminals to carry out their activities. There are several categories of cybercrimes, and these are as listed below.
Computer Fraud
This involves the misrepresentation of facts to cause someone to do or to refrain from doing something, thus leading to a loss. It is a popular type of cybercrime and has seen many people and organizations fall victim. Computer fraud involves the falsification of data through either entry of falsified data or the entry of unauthorized instructions. It may also involve the alteration, destruction, suppression, or theft of online transactions. Lastly, it may also involve the manipulation or deletion of stored data. There has been an increase in these types of illegal activities which have translated to millions of dollars lost annually. The following are the most reported computer fraud incidents by both individuals and organizations.
Business Email Compromise
This is a high-profile scam that is generally targeted at businesses. The scam is ideal when the business has partners in foreign countries to whom funds are regularly electronically sent. The scam begins with the compromise of a business email account of a high-ranking organizational employee. When the email has been compromised and is in the hands of the attackers, they will study the type of communication that the executive employee handles. In most cases, they will send an email to the accounts or finance department requesting the next payments for certain companies to be paid through new overseas bank accounts. With this instruction, hackers can create a cash cow where employees will periodically send huge amounts of money as payments to their foreign suppliers or business partners while the amounts go to hackers (Figure 5.1).
An example of such an attack was on a company called Ubiquiti Networks. Hackers created a spoofed email account of a high-ranking staff member and instructed the accountants to be sending payments to suppliers through new overseas bank accounts. By the time that the scam was realized, the company had lost close to $44 million. It is, therefore, an elaborate scam that is currently in use by hackers and has been proven to be effective (Figure 5.2).
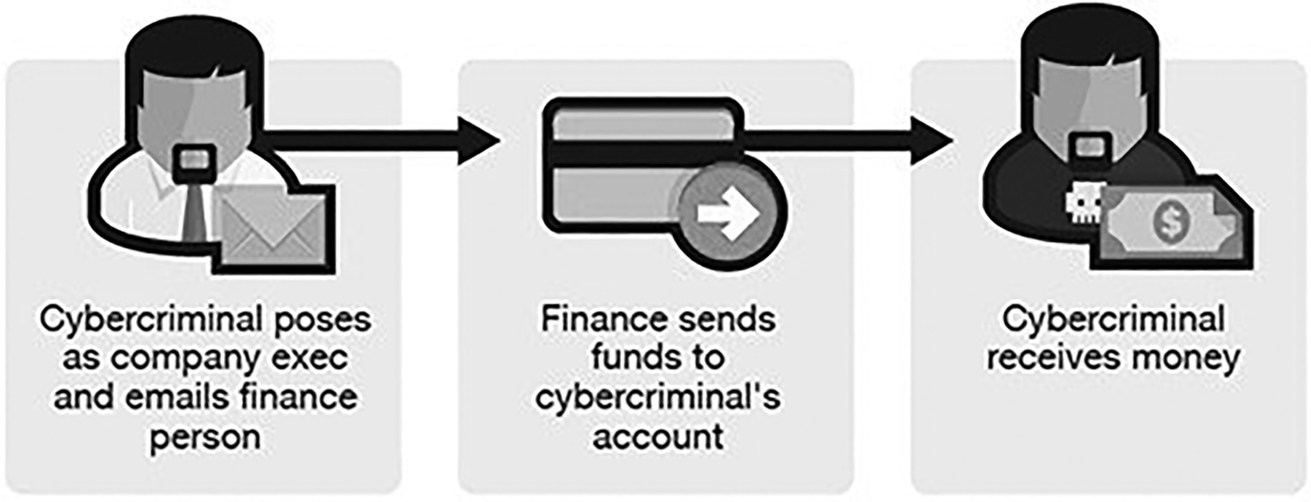
Figure 5.1 A depiction of the BEC (Business Email Compromise) attack.
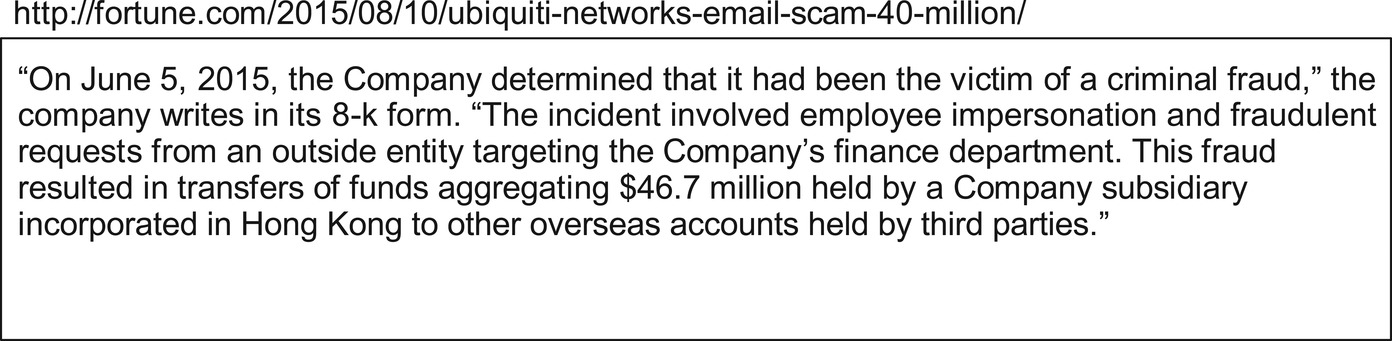
Figure 5.2 Ubiquiti networks attack brief. (http://fortune.com/2015/08/10/ubiquiti-networks-email-scam-40-million/.)
Data Breach
This is another common type of computer fraud. It is where data is leaked or spilled from a purportedly secure storage. Sensitive information ends up in the hands of hackers who either release it publically or use it as ransom to get paid a certain amount. One of the biggest data breaches for a renowned company is that of the email provider company called Yahoo. Yahoo has repeatedly been a victim of data breach where it is reported that hackers have had access to sensitive information about millions of Yahoo’s users. Surprisingly, the attack has not occurred once to the company hinting that the hackers may be working closely with an insider or have been on Yahoo’s systems for a significant period of time. Another significantly big hack was that of Republican National Committee’s (RNC) voter data in the United States. RNC was compromised and the data of over 200 million Americans breached by the attackers. This was as a result of data being stored insecurely on Amazon S3 bucket. Uber has also been a victim of a data breach though the managers handled the incident quite loosely. It is reported that a hacker was able to breach the company and steal data of 57 million users. Some executives paid the hacker a significant amount of money to silence the hacker. In the end, this attempt to conceal the hacker rather than to deal with it came into the limelight and some executive employees were fired. The US White House has already banned the use of Kaspersky products on government computers after the popular antivirus maker was caught up within the traps of computer fraud. Kaspersky has been reported to have been hacked by Russian hackers to help them pull out data from a laptop owned by a contractor to the NSA that was using the antivirus. In this specialized attack, the hackers are said to have used the program’s ability to access any file on a computer’s hard drive to steal. This attacker showed the extent to which insecurity had gone to if an antivirus program could be used for data breaches. Another data breach that involved an unlikely perpetrator was that reported by WikiLeaks. According to the popular expose network, the US CIA had a database of exploits that it could use to track Windows users (Figure 5.3).

From all these attacks, it can be noted that there has been an increase in sophistication and effectiveness. One would think that big companies such as Yahoo would be invincible by attackers since they must have state-of-the-art security systems guarding their networks. However, it has been proven by hackers that data breaches can affect anyone and there are very many ways for them to conduct the breaches. This makes data breaches one of the most feared types of cybercrime and can affect just about anyone.

Figure 5.3 An article on top data breaches of 2017.
Denial of Service
Denial-of-service (DoS) attacks are considered part of computer fraud since they are done to purposefully suppress or prevent normal processes or transactions, thereby leading to losses. DoS attacks involve the interruption of access to systems or networks due to an overwhelming amount of illegitimate requests being sent to servers. This type of an attack has become one of the most feared by organizations since it comes unannounced and is hard to stop once it has started. The main culprits behind the attack are botnets which have recruited thousands of devices that send huge amounts of requests to organizational servers. In 2016, an unlikely victim of distributed denial of service (DDoS) was a domain name resolving company called Dyn. The attack was executed by a botnet of 100,000 devices that continuously sent requests to the company at an estimated rate of 1 Tbps. The attack was a bold one since it was targeted at a company that directly influences internet performance since it is responsible for translating domain names into IP addresses (Figure 5.4).

Figure 5.4 Depiction of a DoS attack.
With the attack on Dyn, several websites could not be accessed since their names were not able to be resolved. The attack served as a wakeup call to all other companies that had looked down upon the capabilities of determined attackers. Another DDoS attacker was against an investigative reporter called Brian Krebs whose website was taken down by a massive attack that peaked at 620 Gbps effectively putting the site offline. The significance of this attack was the sheer amount of force that was used against the investigative reporter. The attack was attributed to a Mirai botnet which had scanned devices connected to the web and infected thousands of them with malware to force them to participate in DDoS attacks. Lastly, for 2016 attacks, there was a wave of DDoS attacks against Russian banks whereby a botnet of approximately 24,000 computers was reported to be behind the attack. The attacks were targeted at five banks, and the attacks lasted over 2 days. However, it is reported that the attacking botnet was not able to take the websites offline. In 2017, there was a reported 915 increase in DDoS attacks. This was due to the increased adoption of Internet of Things (IoT) devices. IoT devices have been plagued with insufficient security, thus making them ideal targets for hackers wishing to get very many devices to recruit to their botnets. The attack on many organizations has been in an effort to either take them offline or to distract the organizations while a data breach takes place (Figure 5.5).

Figure 5.5 Reports on DDoS prevalence. (https://techrepublic.com/article/ddos-attacks-increased-91-in-2017-thanks-to-iot/.)
Email Account Compromise
This is quite similar to the discussed business email compromise. However, this type of an attack is not constrained to businesses only. It can be targeted at the general public and even to people that least expect to be targeted. Compromised email accounts belonging to professionals are used and the aim is to manipulate other people into sending money or sensitive information to the attackers. Individuals working in financial institutions, real estate, and law brokerage firms are likely targets by the attackers for the purpose of obtaining the email accounts. The attackers will pretend to be the professionals and continue on to engage with clients and request for payments or some favors. The accounts are compromised through password guessing or through social engineering techniques. The hacker can use the compromised email to target clients, friends, and relatives or perform transactions under the pretense of being the real owners of the account.
Malware
The malware was exhaustively covered in Chapter 4 where it was said to be malicious software that is broadly categorized into three classes: viruses, worms, and Trojans. These programs are created to alter, manipulate, or destroy systems and data. Some types of malware, especially the ones that are considered to be exploits, are used to open an avenue for attacks. Malware has increasingly been used at the core of most cybercrime activities. Malware can easily be installed onto unsecured devices and then be used to commit other crimes such as data theft. There are malware that automatically download onto a device once the user visits a certain page. It is difficult for the user to tell when his or her device has been infected without an antivirus program. Malware can not only steal data but can maintain an open communication channel between the hackers and the victim machine. The hackers can monitor everything that a user does for a long period before executing their attacks. In the previous chapter, there was a highlight on the new value chains of the underground malware economy. There was a particular value chain whereby when attackers were targeting businesses and financial institutions, they would compromise the machines and keep monitoring the infected devices for long. Once they were familiar with the systems that the targets were using, they would proceed to execute the last bit of the attack. This is the bit where they would use the systems on the infected devices to do either authorize transactions to their accounts or to create transactions to transfer money to their accounts.
Phishing
This is a form of computer fraud that involves the use of emails to manipulate people into sending money or sensitive information to cybercriminals. The normal phishing attack is hardly targeted at specific people since the same phishing email is sent to multiple recipients. The most common pattern of such attack is the claim by the sender to be from a legitimate company, and certain information or credentials are required from the recipient. Another variation of phishing attacks is where the recipients are deceived of having won lotteries or some competitions and they are required to give some information or part with a certain amount to claim their prize. A more advanced form of phishing is spear phishing which is quite different from normal phishing by the fact that the email is highly customized according to the recipient. The attacker will have some foreknowledge about the recipient and thus will know exactly where to target them. For instance, an attacker could create an email resembling that of the HR of a company and then use the email to manipulate the target into giving out their tax information or their sensitive information. It will not appear as inappropriate for the HR to request some personal information and so the target will most likely send it over. Phishing has been advancing with time and has incorporated technology into it. Whereas traditional phishing emails featured grammatical errors, spelling mistakes, and obviously faked emails, a new set of attackers has come up. These attackers create high-quality emails. There are tools that can clone websites, and all the attacker has to do is to play around with the domain name they will use to host the fake website. The attacker can then send a phishing email to the target informing them that there is a problem with their account with a certain company and they need to log in to solve the problem by clicking on a provided link. Upon clicking the link, the target will be directed to the clone website and will be prompted to log in using a similar interface as is on the legitimate website. When the target logs into the account, the credentials are sent to the attackers and the target will be taken round in circles being told to provide more personal information to authenticate himself or herself into the account (Figure 5.6).
Phishing has been a very effective attack of late with attackers duping many people with the new techniques that they are using. There have been PayPal phishing attacks where users are told that their PayPal accounts have a problem that needs to be resolved and thus they are required to immediately log in to through a provided link. The link would go to a cloned site, provide the targets with the normal PayPal login page and then they would enter their credentials. After doing so and submitting the information, the cloned website would take the user through a series of steps where they would continually be requested to give out a bit more of personal information. At the end of the attack, the target would have given out so much information such that they would be at the mercy of the attackers. PayPal acknowledged the attack and sent emails to all its users on how to prevent themselves from falling victim. Another successful wave of phishing attacks took place in the 2017 tax-filing season for US citizens. Hackers used the opportunity where people were in a rush to complete filing their taxes to defraud them. They would create emails purported to be from the Internal Revenue Service (IRS) requiring the recipients to either send out information or to send out some monies. The ring of phishers was, later on, tracked to India and the mastermind arrested. This was after Americans had lost millions of dollars to them. The same attack can be replicated just about anywhere else in the world using the same techniques and technologies that the attackers used.

Figure 5.6 A depiction of phishing.
The effectiveness of phishing attacks has definitely been noted by hackers. They are therefore capitalizing on this technique of reaching a large number of people but using minimal resources. There have been many other attacks just as effective as the two described above. In Qatar, it was estimated that 1 of each 25 citizens had been hit by over 93,000 phishing attempts in just 3 months of 2017. In Czech, there was a fake campaign purporting to be by the country’s postal service. The fake campaign urged people to download an app for their postal services. However, they were downloading a malicious app that turned out to steal their banking information. In the same year, companies in over 50 countries were fooled into downloading a pdf file on energy solutions. The pdf file had a malware injected into it and would infect any device that it was opened in. Amazon has seen the same fate as PayPal after hackers sent phishing emails claiming that there were some items on discount on the e-commerce site. When they clicked on items in the email, they would proceed to log into a clone site, but when they clicked on the discounted products, they would be told that the items were no longer available. However, the information that they would have already given the hackers would be used to attack them in future. There were very many other phishing attempts sent to organizational employees. From a security survey done to a sample of organizations worldwide, it was estimated that 75% of all organizations had received phishing emails in 2017. This estimate shows that phishing is making a great come back and they were increasingly becoming successful. Moreover, the survey showed that the impacts of phishing were malware infections, compromised accounts, and data loss.
Ransomware
This is a unique type of malware that uses cryptography for illegal purposes. Once the malware has infected a device, it will encrypt the files in the computer effectively making it unusable. One will not be able to open any file or program that is encrypted. This, therefore, affects the availability of the infected machine for any task. Ransomware are commonly distributed through phishing. End users get emails with malicious attachments, and when they open them, their computers get infected. Some types of ransomware will go on to infect all the other computers in the network that they are in. They can rapidly encrypt files, and therefore, users hardly have a chance to stop the attack once it starts. After the encryption process, the malware will display a warning that the computer has been encrypted and the victim needs to pay a certain amount in order for a decryption key to be provided, thus allowing the victim to locally decrypt the computer. In some cases, the attackers will give the victim a program that can do the decryption. Payment is mostly sent via Bitcoin to make it harder to trace.
The year 2017 saw quite a number of ransomware attacks, some of which were felt worldwide proving that many people are still to grasp the new reality of cybercrime. It is becoming indiscriminate and very effective. The biggest attack of the year was WannaCry, a ransomware that has ever since been tied to North Korea. The ransomware claimed victims in over 150 countries, thus receiving a lot of publicity. For each encrypted machine, the hackers would demand a ransom of $300 in Bitcoin. There were reportedly 150,000 reported cases all over the world within a short span of days. It was confirmed that the ransomware was so effective since it targeted an exploit called EternalBlue in Microsoft. The exploit had been patched 2 months earlier, but there were quite a number of people that had not updated their computers. EternalBlue is said to be among the exploits in possession of the National Security Agency; thus, the agency received condemnation after the attack. It is only after a static analysis of WannaCry’s code that a weakness was revealed leading to the shutdown of the whole attack. However, it was already too late for the thousands of already encrypted machines. In unfortunate circumstances, the ransomware-encrypted computers in hospitals used to offer critical services. Not only did this lead to the unavailability of such computers, there were a number of deaths due to the stoppage of the services that those computers were offering.
NotPetya
This ransomware was reported almost a month after WannaCry. It started off by affecting power companies in both the Netherlands and Ukraine. Britain and Spain, later on, reported similar incidents of the ransomware. In a few days, NotPetya had spread to over 100 countries. The ransomware encrypted the MBR (Master Boot Record) thus was a level deeper than WannaCry. However, the ransomware still used the EternalBlue exploited that WannaCry used. NotPetya was named so to prevent people from confusing it with a much less prolific ransomware called Petya. The real impact of the ransomware was felt by the corporates, some of which reported $300 million in losses.
BadRabbit
It was a less successful ransomware that claimed hundreds of companies in Russia and Ukraine as victims. Some of these victims included Russia media outlets, a metro system used by Kiev, and an airport. There were scarce reports of the malware in South Korea, United States, and Poland. The BadRabbit malware did not exploit vulnerabilities in the Microsoft Windows OS like both WannaCry and Petya. Once the malware encrypted the computers, it demanded a ransom of 0.5 Bitcoin.
Locky
This was a malware that was first discovered in February 2016 but has ever since been going dark and resurfacing. It has been identified to rely on botnets that spew out multiple spam emails for its distribution. Particularly, it has been associated with Necurs. In August 2017, it was distributed through 23 million emails within a day. The emails had been written exciting subjects such as pictures and the body had downloadable attachments. The attachments were zipped and contained a Visual Basic Script. This is the script that would activate the ransomware once opened.
Cyberterrorism
A new type of terrorism that governments all over the world are having to face is cyberterrorism. There has been growing concern on agencies such as the FBI on the increased level of terrorism both on the surface web and the dark net. Cyberterrorists are a group of attackers that intimidate or coerce governments and organizations into adhering to the terrorists’ propaganda through computer attacks. It, therefore, becomes terrorism targeted at computers and committed through computers or networks. The list is long of what can be considered as cyberterrorism. If a blogger publishes an article and spreads it on social media claiming that there are bombs planted at certain places and will be exploded on a certain day, this can be regarded as cyberterrorism. Terrorism propaganda spread through social media platforms aimed at causing distress to the citizens of a particular country is also cyberterrorism. Hacking government websites with the aim of causing fear or to demonstrate power and subversion of a country is also cyberterrorism.
Countries have increasingly digitized some of their systems. There are countries that rely on smart grids for electricity. In other countries or major cities, there are a lot more digitized basic services. Industries such as those that produce power from nuclear reactors also rely on information systems to keep going. However, there is a threat in that cyberterrorists can target these critical infrastructures through the computer systems used to control them. The United States and Israel are accused of taking down Iran’s nuclear plant using a malware called Stuxnet. The malware infected the computers that had systems to control the nuclear reaction process and caused the plant to self-destruct. Investigations after the attack pointed out that it must have been state-sponsored.
This type of an attack can be replicated but by a more barbaric actor such as the Islamic State or Al Qaeda. With a large-enough team of experienced hackers, these terrorist groups could bring entire cities to their knees by interrupting the provision of sensitive services such as electricity and water. Fortunately, the famous terrorist groups lack members that have such skillset. Most of them prefer physical combat rather than a cyber-based one. There have only been isolated cases ever since Stuxnet to show deliberate cyberterrorism attempts. For instance, there were attacks on Ukraine’s energy provider systems which led to blackouts. The United States has also been a victim once when a researcher took control of traffic systems merely by exploiting a vulnerability in the system used to control the lights. There have been a few other attacks that can be categorized as cyberterrorism in different countries.
One of the countries that have faced a full-scale attack that crippled all online services was Estonia. In 2007, Estonia was targeted with a DDoS attack that led to the shutdown of the internet. The country crept back to the dark days without any access to infrastructure dependent on the internet such as online banking, phone carrier networks, and online access to government services. The culprit was suspected to be Russia since the two countries had been in dispute after the removal of a Soviet statue in Tallinn. The attack on Estonia highlighted the increasing dependence of states on technology and thus their vulnerability to cyberterrorism.
Based on the few highlighted incidents, the number of cyberterrorism attacks is still low. However, it might not remain so in the next few years. The cyberspace is soon going to be the frontline where terrorism will be fought. The adoption of the IoT in many industries and infrastructure is on the rise. They are a necessary convenience for many. However, these devices are particularly vulnerable to attackers. Many of the available devices have been made without appropriate or adequate security controls; thus, they are vulnerable to many cyberattacks. Cyberterrorists might begin targeting infrastructure or industries that have integrated IoT in their processes. The lack of members of terrorist groups that have expertise in hacking is no longer an assurance that these groups cannot commit such attacks. The underground malware market has given an opportunity to hire skilled professionals that could be instructed to sabotage computer systems and networks in a certain country for political reasons. There are already pointers that terrorists will be headed in that direction in the future. One of key Jihad proponents, Mohammad Bin Ahmad wrote a piece on the ways that one could participate in Jihad. One of the ways was through disrupting western states by attacking their websites and other resources.
Globally, there are already preparations to deal with this type of threat. There are already formed institutions to aid in preventing cyberterrorism. The United States has already formed joint task forces in its military that are responsible for preventing and also responding to any cyberterrorism incidents. North Atlantic Treaty Organization (NATO) has a cyber defense unit that also responds to cyberterrorism attacks in member countries. South Korea, being considered as a hyper-connected society, is among the countries at the highest risk of cyberattacks. This is because the country’s cutting-edge technology, though fascinating, is said to be weak in regards to its security. The country has already suffered some attacks that have proven this. The country has increasingly put efforts at securing critical organizations such as is National Intelligence Agency. China has a controversial defense unit called the Blue Army that is said to be purposefully for cyber defense thus can also handle cases of cyberterrorism. The Blue Army is controversial because it has also been associated with penetrating the systems used by other governments hence being a threat to other governments. More countries are recognizing the threat that is cyberterrorism and are mounting defenses for such attacks.
Cyber Extortion
This is a new type of threat where organizational servers are threatened with incessant DoS attacks if the organization does not pay a certain amount to hackers. The hackers assure that if the demanded amount is paid, they will not attack the servers. In another version of the attack, the hackers attack the servers with repeated DoS attacks just to prove their abilities and then request the organization to pay a certain amount for the attack to stop. Corporates have been facing this type of cyberattack, and they have mostly agreed to pay instead of watching as their systems and networks are crippled by the attackers. The FBI said that there are approximately 20 reported cases in a month but many go unreported especially by corporates that want to save face and also not to expose their vulnerabilities to the public.
Cyberwarfare
This is a politically motivated war between groups, states, or countries that is fought in the cyberspace. The states attack each other’s computer systems and networks for the purpose of disrupting normal activities in organizations, industrial espionage, and also to obtain data that can be used for strategic military purposes. Cyberwarfare can take several forms. It could be in the form of malware spread to government institutions, infrastructure, or organizations in a certain country. The aim of the malware will be to take down normal operations, key infrastructure, and even military systems. The Stuxnet attack against Iran’s nuclear facility was an act of cyberwarfare if the culprits could be positively confirmed to be the United States and Israel. Another form of cyberwarfare is the execution of DoS attacks on government computing systems or key industries in a given country with the purpose of preventing the legitimate users from accessing such systems. DoS attacks could cripple operations that are transacted or processed online. Some DoS attacks are so strong that they can shut off the entire internet connectivity of a country as is the case with Estonia. Hacking and theft of data on key government institutions and a country’s industries are also considered to be a form of cyberwarfare. Many countries have accused Russia, China, and North Korea of hacking units in their governments or funded by governments to hack and steal data from foreign countries. Even though many cases have not been proven, there is tension being created and an actual cyberwarfare might take place in the near future. Countries have been arming themselves for such attacks too. Lastly, ransomware can be used in cyberwarfare where a country could target key government institutions with spam containing ransomware. The ransomware could encrypt computers used for vital services, thereby making them unavailable.
The motives of cyberwarfare are many, but they are aimed at attacking countries through their critical infrastructure or their key industries and institutions. Most countries are at the risk of falling victim to cyberwarfare attacks due to the increasingly inevitable need to automate services and to stay connected to the internet. Even with secured systems, there are specialist hackers that can be paid by enemy countries to find weaknesses in a country’s systems so that they can be exploited. Key infrastructure are the most common targets. For instance, if an attack is made on a nation’s power distribution network, there would be widespread blackouts. Sensitive services that rely on electricity to run would be brought to a halt. Some countries use hydroelectric power plants to generate power while others rely on nuclear reactors. When these plants are attacked, the production of electricity in the country could be affected. Systems used to control hydroelectric power plants could be attacked and the controls manipulated to cause flooding.
Computer systems used by government agencies and institutions could also be attacked. The data stored in these systems could be stolen and used by enemy states for political reasons. Identities of secret agents, spies, and even a government’s secrets could be put into the public domain. The systems could also be made unusable by ransomware. Communication channels can be hacked to prevent further communication between government agencies or officials. Messages exchanged on the communication channels could be stolen and sensitive information could be obtained from them. Hacks to sensitive institutions could lead to the release of personal data the citizens of a country. Lastly, military databases could be attacked by enemy states to expose troop locations, the equipment they have, and the types of weapons they are using. Communication channels used to give orders to the military could be infiltrated to give the enemy state access to a backdoor to all communications.
Cybercriminal Activities through the Dark Net
Chapter 2 highlighted most of the cybercriminal activates that are carried out on the dark net. This section will just recap some of these activities.
Drugs
The sale of drugs is done in many dark net markets. The sellers list their products on some of the dark net markets. Buyers pay via Bitcoin and have their drug shipped to them. Since there are hardly any regulations, buyers rely on sellers that are proven to be reliable. Some websites will have a trust score that is updated by the buyers based on their experiences with different sellers. However, legal agencies have been taking down most markets. If previous patterns were anything to go by, new markets are being formed to absorb the demand from the sellers and buyers that used the markets that have been taken down.
Human Trafficking, Sex Trade, and Pornography
There was a time when 17% of all the dark net sites on Tor were adult websites. These sites provided access to porn but also to human trafficking and sex trade. Even though it might seem that sex trade and human trafficking are a thing of the past, in 2014, there were reports of 2.5 million people trafficked through the dark net and surface web. This means that the illegal business of selling humans might still be ongoing on the dark net. This has prompted US Defense Advanced Research Projects Agency (DARPA) to create a program called Memex that can search the dark net and follow up on possible human traffic activities being carried out on the dark net.
Child pornography was a disturbing issue on the dark net that showed the depths of human degradation. However, almost all the dark net sites that had been offering child porn were taken down by the FBI and their founders tracked down. Many sites on the dark net also prohibited the listing of child pornography material on their markets. For instance, among the things that were banned from Silk Road 2.0 was child porn. It is fortunate that there are hardly any sites left offering this type of obscene content.
Weapons

Figure 5.7 Weapon on sale on the dark net.
There are sites on the dark net that have been used for the purpose of buying and selling weapons. The weapons include guns, explosives, and their ammunition. These sites are a threat to security since the weapons are sold to many people that have malicious intentions. Terrorists have used the dark net to acquire weapons and use them in attacks. Terror activities such as the Paris attacks were carried out using weapons that were bought on the dark net. The Charlie Hebdo attack led to 130 deaths and 350 injuries. The weapons were military grade and they still landed in the hands of ISIS terrorists. Weapons are in plenty and not so expensive on these underground markets on Tor. There has been a notable increase in demand for deadlier weapons by terrorists. They are willing to pay more to get the coveted military equipment that outperforms their normal arsenal. Self-radicalized individuals are also getting access to weapons without much of a hustle through these markets (Figure 5.7).
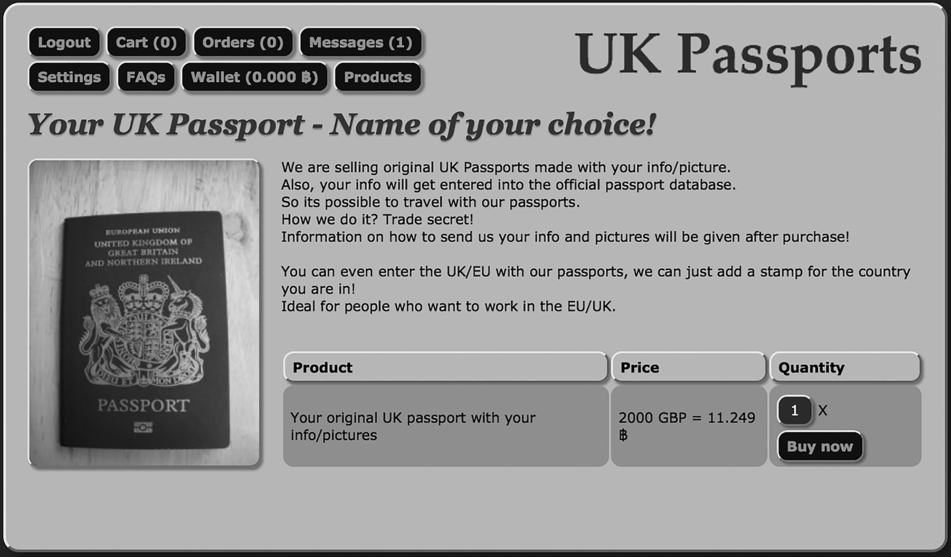
Figure 5.8 UK passport on sale on the dark net.
Fake Documents
For a few hundreds of dollars, one can get fake citizenship. This is done through the issuing of fake passports. Alongside the fake passports are fake driving licenses. The fake documents are offered to immigrants, terrorists, and people that wish to leave or enter the country without putting their real identities at risk. Some of the offered passports are high quality and hardly can a layman tell apart the fake from the real passports. There is an excellent delivery network for these documents such that people can get them from their own countries if they wish to use the documents as they enter foreign countries (Figure 5.8).
ATM PIN Pad Skimmers and ATM Malware
There are reports of ATM fraud where users complain that their accounts have been withdrawn shortly after using ATM machines. One of the ways attackers use to get money out of other people’s ATM cards is through ATM PIN pad skimmers. These can be fit on ATM machines to enable the attackers to collect data keyed in by the users of the machines. Even though banks might catch up with the perpetrators of the crime after some time, money will already have been stolen. ATM PIN pad skimmers are sold on the dark net markets to criminals.
ATM malware are malicious programs that are used to illegally withdraw money from ATM machines. The malware can be installed by third parties inside ATM computers. The attackers will then be able to send instructions to the ATM machines to cash out their cassettes. The money will be emptied to the waiting hands of the attackers.
Counterfeit Currency
The dark net has markets that people can find counterfeit currency of high quality. This currency can be used to do normal transactions in stores, restaurants, or other business premises without the owners knowing that they are receiving illegitimate currency. Such currency can lead to lots of losses especially to small businesses that lack the tools to check for the authenticity of currency. Even then, there are some sellers of the counterfeit currency that assure that the currency can pass the common UV light test.
Data Dumps
There are markets on the dark net where one can buy data dumps of stolen data. The data could include personal information such as names, age, physical address, phone number, email address, and login credentials to some websites. Some data dumps contain encrypted data, and it is the burden of the buyer to find out how they can decrypt it. The data dumps are sold according to the value of the data contained and size.
Exploit Kits
Cybercriminals can buy exploit kits that they can use for attacks on the dark net. Exploit kits have been sold on the dark net for a long period now. They have a regular demand since not many cybercriminals are good at programming, and thus, they cannot write their own exploits. Exploit writers are the ones that study different systems, find vulnerabilities, and then create exploits that can be used against these systems.
Fake Websites
Modern phishing attacks are advanced and have many things that can trick cautious users into falling into the traps. There are lots of efforts being put in modern-day phishing attacks to make them more believable. Traditional phishing emails only relied on the content to trick users into performing some actions. However, today’s phishing emails do not just rely on content, they rely on trust. They try to make targets believe that they have actually been sent by legitimate people. They give their targets links to login to the purported companies that the emails claim to be sent from. The links will open identical sites to the legitimate one. Every part of the website will look real and the target will not have doubts about the legitimacy of the site that they are on. This is because there are dark net markets selling cloned copies of commonly used websites that are relevant for hacks. They have cloned online banking websites, cloned government institutions websites, and many other fake but high-quality clone websites (Figure 5.9).
Data Exfiltration
There are very many attacks today that are aimed at stealing data rather than money. In some cases, data is more valuable than money and is also less risky to steal. When one steals money, there could be money trails left behind that could be used to track them. Data is, however, easier to handle. Data exfiltration is the process of transferring data from a storage medium to another. In the world of cybercrime, it refers to the theft process of data where hackers copy data from compromised servers to their own storage devices. Data exfiltration occurs at the last stages of an attack where a hacker has already been able to gain access to a network and then to storage servers in the network. A number of companies have had this befall them. Yahoo was a victim when records belonging to approximately 2 billion people were stolen. Most exfiltration attempts end with the placement of the data on dark net markets for sale. Here, there are markets that allow sellers to list data dumps where interested parties can buy. The data is mostly bought by advertising companies and other hackers. Advertising companies will use the data to profile users and send advertisements to them through any available communication media. Cybercriminals will use the data to conduct further attacks against the people whose personal information is in the stolen data. They could, for instance, use it to send spear phishing emails to these people. With the available information, they will be able to craft more convincing emails to trap the targets.

Figure 5.9 A news article on the Charlie Hebdo attack. (http://time.com/how-europes-terrorists-get-their-guns/.)
There are some exfiltration attempts where the hackers end up with encrypted data. There are two options when this happens. The first option is for the hackers to sell the data for cheap on the dark net and make the meager profits they can from the sale. The second option is to try and decrypt the data. Sometimes, decryption attempts work, especially for weak encryption algorithms. It was reported that hackers initially stole user data from Yahoo in encrypted formats. However, the encryption algorithm that was used was MD5 which is in the least of weak encryption algorithms. After several attempts, hackers were able to decrypt the data and thus get access to information on over 2 billion user accounts. Therefore, even if data exfiltration ends in a seemingly useless data that has been encrypted, attackers will still try to decrypt it.
There is a new security measure where organizations can hire professionals to scout through the surface and dark net to search for stolen data. This is done after the organizations have confirmed that they were hacked and data stolen from them. These can find such data and begin investigations into the culprits responsible for putting the stolen data online. There are also services that have made it easier for organizations to monitor data leaks. One of these is PwnedList.com. The service continually searches for new data posted on the dark web and indexes it. One can tell whether organizational data has been stolen by running a sample search using PwnedList, and if there are any hits, the organization will know that its data has been listed on the dark net. It can then follow up with authorities and try to find the culprits behind that. An alternative to PwnedList is Hold Security. Hold Security offers a similar service where it scans the dark webs for data and indexes it. The index can then be searched against by a company to determine whether its stolen data has been listed on the dark web. However, the challenge for these services is that when stolen data is posted on the dark net, it is normally for sale. Also, hackers will not display a whole data set. They may only describe the type of data that they are selling.
Monetization of Cybercrime
At the initial stages of hacking, the motivation was hardly financial. It was just a way of proving that one could do certain things. Moreover, most attacks involved the use of scripts either copy-pasted from the internet or simple software available on some forums. It was hardly a financial undertaking and the motives were only to cause problems and become famous. With time, however, hackers started to improve and with that, they wanted to leverage their skills for financial incentives. At that time, there was not a proven way to make them become elite out of cybercrime. Therefore, they started creating a market for hacking services and tools which could be monetized.
In 2006, the first exploit kits surfaced on Russian markets on the dark web. They marked a beginning of the monetization of cybercrime. More kits were listed on the underground markets. Some came with more features such as a graphical user interface that one would use to launch an attack from. These kits got buyers who sold them to crime groups that would find targets to exploit. At that time, the same exploit kit would be used over and over against different targets. Therefore, a hacker only needed to buy the kit once. However, it is no longer viable to use the same exploit many times today due to the nature of the cybersecurity products available. Once they determine a threat signature, the same threat can hardly be used again to attack secured systems.
Hackers have, however, come up with more techniques to generate revenue from cybercrime. These are as follows.
Extortion
The first option is through extortion. Extortion has gained popularity as a common money mincing technique since the victims hardly have a walk around ransomware have been used to encrypt computer devices, thus requiring users to pay a certain amount to get their files decrypted. Traditionally, such an attack would only be for fun and the threat actors would hardly request anything from the victims. Today, ransomware attacks are spanning the whole continent, and the attackers are requesting significant amounts as ransom. For instance, the WannaCry ransomware used to demand for $300 to be paid in Bitcoin within a week. If the amount was not paid within that time, the price would go up to $600. If the victim never paid, the computer would be encrypted permanently. There have been similarly high charges from other malware, some that have gone as high as demand for 0.5 Bitcoin. To add seriousness to their threats, some ransomware display warning messages claiming to be from the FBI. They mostly say that one’s computer has been locked due to either accessing illegal content or downloading pirated content. The ransom amount is said to be the fine, and there is always a stern warning that the failure to pay the stated amount could lead to the permanent lock of their computers or even arrests (Figure 5.10).

Figure 5.10 A depiction of extortion.
Phishing
Another monetization method of cybercrime is through phishing. The new techniques used in phishing have seen victims lose millions of dollars to hackers through fake messages. The traditional phishing attacks were a bit easy to tell since they did not feature the use of much technology. There was the widespread phishing email of the Nigerian prince. The email required a user to assist a Nigerian Prince to get inherited a fortune, and in the end, the assistance would be highly rewarded. When one opted to offer the assistance, they would be told to pay some clearance charges to facilitate the transfer of the money. However, the charges would seemingly never end because after paying a certain amount, there would be another request to pay more. It is only until too late that one would realize that it was a con game. Many people, however, came to know of this and avoided it. However, phishing has been advancing and now features well-laid traps to get people to give out money and their personal information to hackers. During the tax season in the United States, there is a group of phishers that comes up and starts sending messages to US citizens that they are required to pay some fines and penalties since they failed to file their returns in the right way. These emails are formatted with the font colors and styles of the real IRS that processes tax filings. Sometimes, they can even recreate the IRS website so appear to be more authentic. Similarly, PayPal phishers are on the rise, and they have been using an effective way of getting login credentials that they can use to hack users’ accounts and steal their money. The PayPal phishers craft an email that features the same styling and layout as the real ones from PayPal. They then explain that one’s account has been limited due to certain reasons. As per PayPal terms, when an account is limited, it cannot be withdrawn from or money deposited to till the limitation is removed. It is therefore plausible that a user will want to resolve the limitation within the shortest time. The phishers have clone sites that look and feel like the normal PayPal site. The site is used to harvest a user’s login credentials and personal information.
Adverts
Another type of monetization of cybercrime is through adverts. There are cybercriminals that get revenue from forcefully showing adverts to users. They infect many computing devices with adware. The adware will be displaying adverts in pop-ups. This might not be so harmful, but it is annoying to users since their browsing activities keep on getting interrupted by the adverts. The cybercriminals depend on payments from advertising companies either through the impressions the ad received or the number of clicks the ad got (Figure 5.11).

Figure 5.11 A depiction of ad pop-ups.
Theft of Login Details
There is an underground market for cybercriminals that has buyers willing to pay for stolen login information. The login credentials could be for online banks, social media websites, email accounts, or just normal websites. There is malware that is purposefully used for stealing credentials. Since many users store login credentials on their browsers, the malware automatically downloads onto a user’s machine when certain websites are visited. The malware will steal the stored login information and send it back to the attackers. These logins could be used for extortion or direct theft through money withdrawal.
Premium Rate SMSs
This was a threat that surfaced on both Android and iOS play stores. Malicious apps that claimed to offer certain functionalities were found to be sending messages to premium rate numbers. The effect was that phone users would lose a lot of money without knowing that their apps were the culprits. This led to major improvements in Android and iOS. Android became more strict on the permissions that apps requested to have when installed. Both the platforms also instituted thorough checks on the apps that had been published in their app markets. However, there still are premium rate SMS attacks that are taking place. This is being carried out through surveys. Users are instructed to give out their numbers during surveys and send a certain code that they receive on their phones. When they send back the code, they are charged at premium rates.
Banking malware—a few years back, there were concerns over key loggers capturing the username–password combination one used to log into websites. There then came to the concerns of login information being sniffed from packets when entered into unsecured websites. Currently, there are Trojans that can infect phones and computers and record incoming messages and record one’s screen. These can harvest a lot of information that can be used by hackers to get access to one’s account.
Malware-as-a-Service and Money Laundering
Malware-as-a-service is one of the new value chains that attackers are using in their underground economies. Here, an attacker does not go through the trouble of creating a malware. Malware can be rented or bought from other specialists in the dark net. The following are some of the specialists in the malware-as-a-service delivery module (Figure 5.12).
Exploit Writers
These are the hackers that discover new vulnerabilities in systems and then create exploits for them. Exploits will be targeted at one or several vulnerabilities in a system. For example, EternalBlue was an exploit written to target a vulnerability in Windows. The exploit has been used repeatedly in ransomware attacks such as WannaCry and NotPetya. When exploit writers create an exploit, they will sell it to other cybercriminals that do not have the coding expertise to make exploits. An exploit writer may never come to the frontline of an attack since they make their money through the sale or renting of the exploits. Exploits are sold differently based on their complexity and effectiveness. The most expensive category of exploits are zero-day exploits. These are exploits that target vulnerabilities that system owners have not yet detected. Therefore, their effectiveness is high. Stuxnet is said to have used a number of zero-day exploits. This added to the speculation that the attack was state-sponsored. Several zero-day exploits would be too expensive for the common cybercriminals to waste in a single attack that did not attract any financial rewards. There are other low-quality exploits which fetch less on black markets but can still be harmful to a target.

Figure 5.12 A depiction of malware-as-a-service. Malware is bought by the cybercriminal from the cloud and then used to infect different devices.
Bot Herders
There has been an increase in the number and sophistication of DDoS attackers. Big companies have fallen victim to these attacks, temporarily being put offline by the overwhelming number of illegitimate requests send to their servers. The infrastructure for conducting these types of attacks is sold on the dark net. There are specialist hackers whose sole purpose is to recruit computers to botnets. They infect zombie computers with a client version of a malware allowing them to control the activities of the infected computer. Bot herders maintain a program that allows all the zombie computers to be directed to send illegitimate traffic to certain addresses (Figure 5.13).
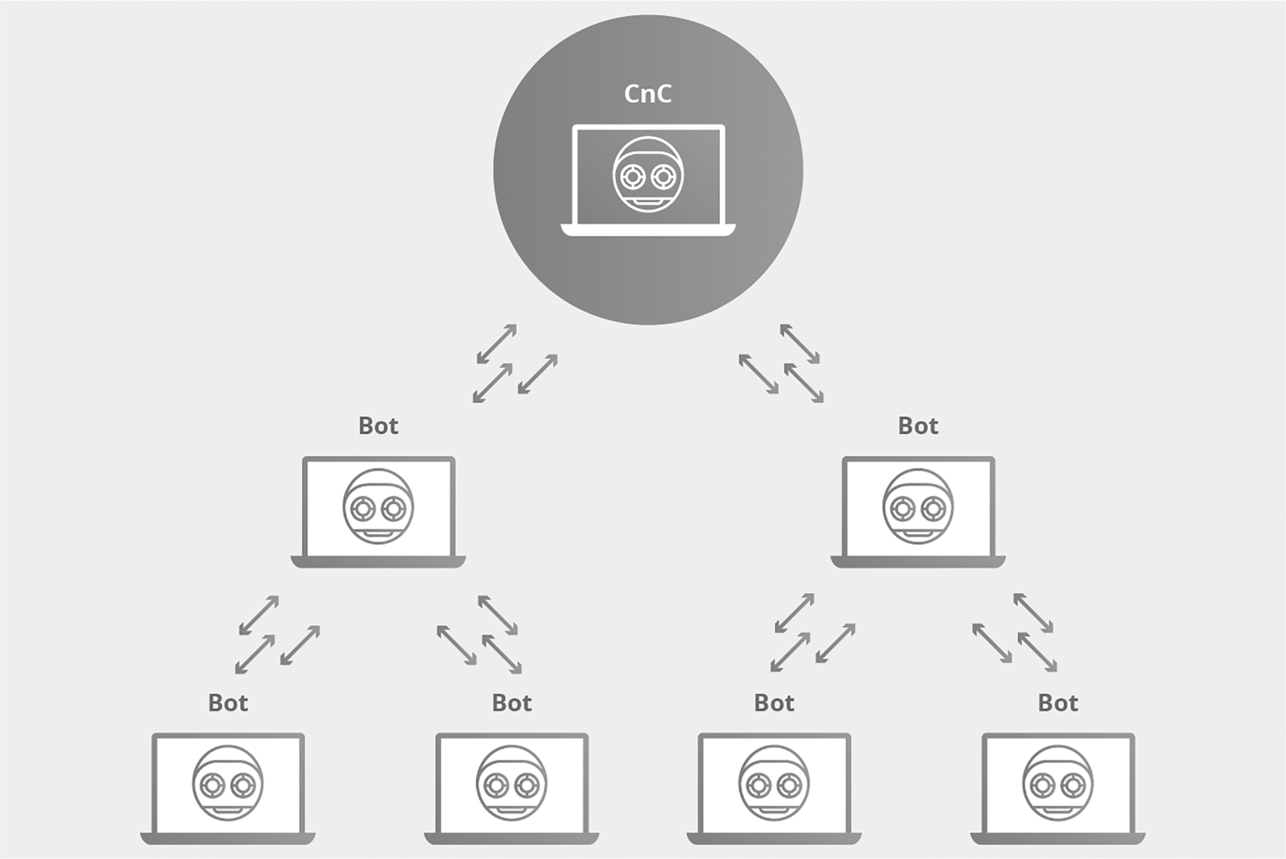
Figure 5.13 A botnet setup.
Malware Writers
Viruses, worms, and Trojans are coded by malware writers. These writers have the expertise of compromising browsers, operating systems, file systems, and networks. Malware writers can code different behaviors into malware to prevent their easy detection. They can also make them polymorphic hence can assume different behaviors. This makes it hard for them to be detected. Malware writers are always in a constant competition with antivirus systems. Since antivirus systems will index malware signatures rendering the malware no longer usable, malware writers have to keep releasing new variants of the malicious programs. Malware are sold on the dark net markets.
Money Laundering
When cybercriminals make money, they try as much as possible to reduce the traceability of the money. Money transfer leaves trails, and these can be used by law enforcement agencies to arrest the cybercriminals. To prevent this from happening, there are specialists on the dark net that offer money-muling services. Money mules arguably play the most important role in the cybercrime chain. A cybercriminal cannot go to a bank account to cash out money that they have stolen from a victim. It is the money mule that will facilitate the movement of the money from where it is deposited by the hackers to cleansing platforms and then to the hackers. The cleansing services are those that make trails leading to the money disappear or at least difficult to trace. Cryptocurrencies are commonly used and a money mule may convert the stolen money back and forth from one cryptocurrency to another. The money mules can also buy products with the money and resale them to get clean money that can be given to the cybercriminals. This is why it is normally hard for money stolen by cybercriminals to be recovered. The money mules will be waiting for the cybercriminals to give them the go ahead to cleanse the money once it enters into bank accounts or Bitcoin address (Figure 5.14).

Figure 5.14 Money laundering.
Summary of the Chapter
This chapter has discussed the cybercriminal activities on the dark net. It has first given the categories of cybercrime. The first category is that of computer fraud. Under this category are data breaches, DoS attacks, business email compromise, email account compromise, phishing, and ransomware. The second category that the chapter has looked at is cyberterrorism. Here, it has highlighted the increasing threat of critical services and infrastructure being taken down by terrorists through hacking. An explanation has been given on how different countries have prepared themselves to this threat. According to the current reports, there have not been many cyberterrorism incidents, but the chapter explains why countries need to prepare themselves for a future with such kinds of attacks. The next category of cybercriminal activities is cyber extortion. The paper has highlighted that there are attackers extorting money from organizations by threatening to hack them or attack them with DDoS. Lastly, the paper has looked into the category of cyberwarfare. Based on the research, there have been multiple confrontations between nations on the cyberspace, thus showing clear signs that a cyberwarfare is not far from happening. The isolated confrontations discussed feature China, Russia, and North Korea as perpetrators of attacks that could easily translate to cyberwarfare. These attacks range from shutting down the internet of other countries to industrial espionage and election meddling. The chapter has also gone through the cybercriminal activities that have been taking place through the dark net. These were highlights of the exhaustive list provided in Chapter 3 where most of the attacks were covered. Data exfiltration was discussed, and there was an explanation of what happens when huge chunks of data are finally stolen from companies. An example was given of how data from Yahoo was stolen, and even though it was initially encrypted, the hackers were able to decrypt it due to the use of a weak encryption algorithm. The chapter has delved into the monetization of cybercrime. A brief history has been given on how monetization of cybercrime began. The chapter has then looked at the current techniques of monetizing cybercrime. The discussion has looked at exploit kits, extortion, adverts, theft of login details, premium rate SMSs, and banking malware. Lastly, the chapter has looked at two important components of today’s cybercrime market: malware-as-a-service and money laundering. Since not all cybercriminals are programmers, they have been relying on the services of experts to make the malware that they will use in attacks. Money laundering services offered by money mules have also been discussed. The techniques that are used by the money mules to eliminate trails behind the illegal proceeds of cybercrime have been highlighted.
Questions
-
Explain the business email compromise attack.
-
Give three categories of cybercrime.
-
Explain the difference between cyberterrorism and cyberwarfare.
-
What are premium rate SMSs?
-
Who are exploit writers?
-
Who are bot herders?
-
What do money mules do?
Further Reading
The following are resources that can be used to gain more knowledge on this chapter: