| TCP/IP |
 |
In 1973, the U.S. Defense Advanced Research Projects Agency (DARPA) first proposed TCP/IP as a standard for connecting various existing networks so that they could exchange information. One aim was to develop a common standard to replace the growing number of proprietary and incompatible networks that were emerging. The work undertaken as part of the DARPA project eventually led to the development of the TCP/IP protocol suite and the Internet as we know it today. In the early days of networking, many protocols competed for market share. Microsoft networks used NetBIOS/NetBEUI, for example, and NetWare networks used IPX/SPX. Today, everybody uses TCP/IP.
 |
The TCP/IP Protocol Suite |
TCP/IP is made up of a number of protocols that work together to make it the most popular protocol in networking today. Each protocol in the TCP/IP protocol suite performs a specific role; this section identifies some of the popular ones.
Application Protocols
Application-level protocols are responsible for initiating some sort of request (on the client) or answering that request (on the server). When you surf the Internet, for example, you use an application (a web browser) that sends a request to a web server for a specific page. This communication happens across TCP/IP using an Application-layer protocol known as Hypertext Transfer Protocol (HTTP).
Port Numbers
A TCP/IP client computer initiates contact with a server computer and uses specific values, called port numbers, to request a particular kind of service. Servers listen on ports that correspond to the services they offer. A web browser, for example, contacts a server at the destination port number 80; the web server listens to port 80 so it knows that the client wants a webpage.
The use of port numbers enables servers to provide more than one type of service. One of the servers in my office, for example, handles internal webpages for essential company policies. It also acts as a file server and a print server. Finally, it handles our lunchtime gaming needs by running as a Counter-Strike or Unreal Tournament server. Clients request each of these different services using different port numbers.
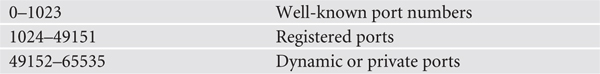
Clearly defined port numbers exist for every popular, or well-known, TCP/IP application. A port number is a 16-bit value between 0 and 65535. Port numbers from 0 to 1023 are called well-known port numbers and are reserved for specific TCP/IP applications. (No TCP or UDP application can use the reserved port 0.)
Exam Tip
TCP/IP port numbers between 0 and 1023 are the well-known port numbers. You’ll find them at every party.
Destination and Source Port Numbers The client uses a destination port number to request a service. To communicate back and establish a session with the client, the server uses a port number specified by the client. The web client, in essence, says, “Hey, server! I’m requesting on port 80. You can reach me through my port 50002.” In this example, port 50002 is the source port number. Port numbers that devices allocate on the fly for a source port number are also called ephemeral ports.
Registered and Dynamic Port Numbers The port numbers from 1024 to 49151 are called registered ports. Less-common TCP/IP applications can register their ports with the Internet Assigned Numbers Authority (IANA). Unlike well-known ports, anyone can use these port numbers for their servers or for ephemeral numbers on clients. Most operating systems steer away (or are in the process of steering away) from using these port numbers for ephemeral ports, opting instead for the dynamic/private port numbers. Here’s the full list of ports:
Sockets
Each computer on each side of a session must keep track of the status of the communication. In TCP/IP, the session information (a combination of the IP address and port number) stored in RAM is called a socket or endpoint. When discussing the information each computer stores about the connection between two computers’ TCP/IP applications, the term to use is socket pairs or endpoints. A session or connection refers to the connection in general, rather than anything specific to TCP/IP. Many people still use the term session, however. Here’s a summary of the terms used:
• Terms for the connection information stored on a single computer—socket or endpoint
• Terms for the connection information stored on two computers about the same connection—socket pairs or endpoints
• Terms for the whole interconnection—connection or session
As two computers begin to communicate, they store the information about the session—the endpoints—so they know where to send and receive data. At any given point in time, your computer probably has a large number of communications going on. If you want to know who your computer is communicating with, you need to see this list of endpoints. Windows, Linux, and Mac OS X come with netstat, the universal “show me the endpoint” utility. The netstat utility works at the command line, so open one up and type netstat –n to see something like this:
Travel Advisory
Even though almost all operating systems use netstat, there are subtle differences in options and output among the different versions.
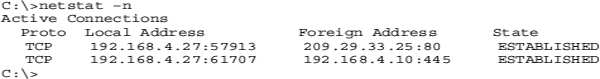
When you run netstat –n on atypical computer, you’ll see many more than just two connections! The preceding example is simplified for purposes of discussing the details. It shows two connections: My computer’s IP address is 192.168.4.27. The top connection is an open webpage (port 80) on a server at 209.29.33.25. The second connection is an open Windows Network browser (port 445) on my file server (192.168.4.10). Looking on my Windows desktop, you would certainly see at least these two windows open (Figure 5.1).
FIGURE 5.1 Two open windows
Both connections require open ports on my computer. These show up under the Local Address column. Ephemeral port 57913 is open for the web browser; port 61707 is open for the network browser.
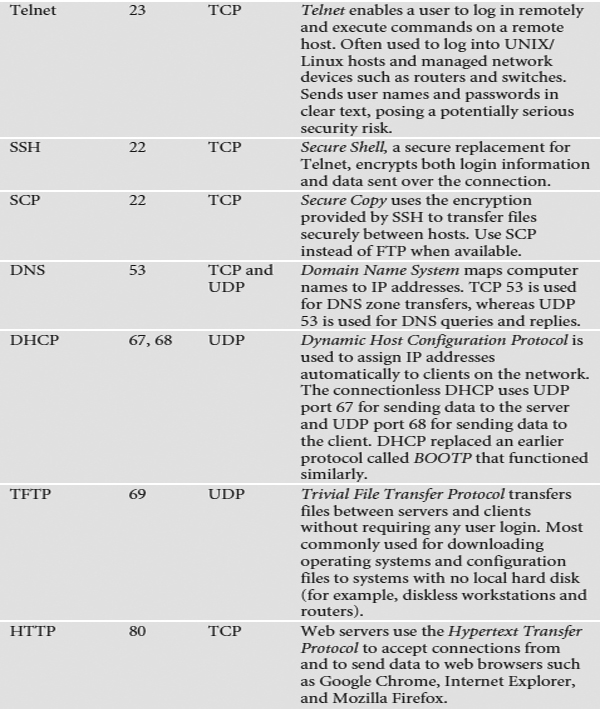
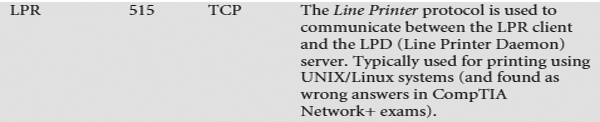
List of Application Protocols
Here are some examples of popular Application-level protocols and the port number(s) they use by default. And yes, you need to memorize the port numbers for the CompTIA Network+ exam.
Compound Application Protocols
Some common Application-layer protocols use multiple protocols to accomplish their tasks. HTTPS and VoIP provide good examples.
HTTP over Secure Sockets Layer (SSL) provides an encrypted connection between a web server and a web client. Most web browsers display a closed padlock to indicate a secure connection. HTTPS provides the basic fabric for e-commerce on the Internet. Although the protocol name still refers to SSL, current HTTPS implementations use Transport Layer Security (TLS), an improved cryptographic protocol. HTTPS uses TCP port 443.
Exam Tip
TLS is up to version 1.2 as of this writing.
Voice over IP (VoIP) enables users to make phone calls over an IP network, such as the Internet. The user uses special VoIP boxes that support telephones that connect to the IP network instead of requiring the user to use a PC. VoIP uses a number of different protocols, two of which you must know for the CompTIA Network+ exam. The Session Initiation Protocol (SIP) establishes and takes down the communication channel for VoIP. The Real-time Transport Protocol (RTP) delivers the voice across the connection after it has been established.
SIP uses either TCP or UDP ports 5060 and/or 5061. RTP has no fixed port number, though many implementations use UDP ports 5004 and 5005.
Transport Protocols
When an application sends out a request, the request needs to be specified as either a connection-oriented request or a connectionless request, as you’ll recall from Chapter 1. Two protocols handle the Transport-layer traffic in TCP/IP networks: TCP and UDP.
TCP
The Transmission Control Protocol (TCP) enables connection-oriented communication in networks that use the TCP/IP protocol suite. TCP is, by far, the most common type of session on a typical TCP/IP network. Figure 5.2 shows two computers. One computer (Server) runs a web server and the other (Client) runs a web browser. When you enter a computer’s address in the browser running on Client, it sends a single packet with the SYN (synchronize) flag activated to the web server. If Server gets that packet, it returns a single packet with SYN, ACK (synchronize, acknowledge) flags active. Client then sends Server a single packet with an active ACK flag and immediately requests that Server begin sending the webpage. This process is called the TCP three-way handshake.
FIGURE 5.2 A connection-oriented session starting
Once Server finishes sending the webpage, it sends a FIN, ACK (finished, acknowledge) packet. Client responds with an ACK (acknowledge) packet and then sends its own FIN, ACK packet. The server then responds with an ACK; now both parties consider the session closed (Figure 5.3).
FIGURE 5.3 A connection-oriented session ending
Most TCP/IP applications use TCP because connection-oriented sessions are designed to check for errors. If a receiving computer detects a missing packet, it just asks for a repeat as needed.
Figure 5.4 shows a simplified TCP header. Notice the source port and the destination port, part of the TCP segment or UDP datagram encapsulated in the packet.
Ports aren’t the only items of interest in the TCP header. The header also contains these fields:
• Sequence number This value is used to assemble/disassemble data.
• ACK number This value tracks the readiness of the two communicating systems to send/receive data.
• Flags These individual bits give both sides detailed information about the state of the connection.
• Checksum The checksum checks the TCP header for errors.
UDP
User Datagram Protocol (UDP) runs a distant second place to TCP in terms of the number of applications that use it, but that doesn’t mean UDP is not important. UDP is perfect for the types of sessions that don’t require the overhead of all that connection-oriented stuff.
Exam Tip
Be sure that you know the difference between TCP and UDP when preparing for the CompTIA Network+ exam.
A UDP datagram doesn’t possess any of the extras you see in TCP to make sure the data is received intact (Figure 5.5). UDP works best when you have a lot of data that doesn’t need to be perfect or when the systems are so close to each other that the chances of a problem occurring are too small to bother worrying about. A few dropped frames on a Voice over IP call, for example, won’t make much difference in the communication between two people. So there’s a good reason to use UDP: it’s smoking fast compared to TCP.
Exam Tip
Data gets chopped up into chunks at the Transport layer. The chunks are called segments with TCP and datagrams with UDP.
Internet Protocols
Internet-layer protocols handle addressing in a TCP/IP network. They help devices determine whether an intended recipient is local or remote.
Internet Protocol
The Internet Protocol (IP) is responsible for the addressing and routing of data to the remote system. Addressing means that IP is responsible for some sort of addressing scheme used to identify each system on the network (or Internet) and for determining how to use that address to route the data to the destination. The addressing scheme that IP uses is known as an IP address. The IP address is a unique number assigned to your system that looks something like this: 192.168.1.10.
The full IP packet has 14 different fields. As you would expect, the destination and source IP addresses are part of the Network/Internet layer. Other fields include version, header length, and more. Dissecting the entire set of fields isn’t important, but here are a few descriptions just to whet your appetite:
• Version The version (Ver) field defines the IP address type: 4 for IPv4, 6 for IPv6.
• Header Length The total size of the IP portion of the packet in words (32 bits) is displayed in the header length field.
• Differentiated Services Code Point (DSCP) The DSCP field contains data used by bandwidth-sensitive applications like Voice over IP. (Network techs with long memories will note that this field used to be called the Type of Service field.)
• Time to Live Routers on the Internet are not perfect and sometimes create loops. The Time to Live (TTL) field prevents an IP packet from indefinitely spinning through the Internet by using a counter that decrements by one every time a packet goes through a router. This number cannot start higher than 255; many applications start at 128.
• Protocol In the vast majority of cases, the protocol field is either TCP or UDP.
FIGURE 5.6 Simplified IP header
An entire section is devoted to IP addressing later in this chapter, so I will leave the rest of our discussion on IP for that section.
Internet Control Message Protocol (ICMP)
Sometimes applications are so simple that they’re always connectionless and never need more than a single packet. The Internet Control Message Protocol (ICMP) works at layer 3 to deliver connectionless packets. ICMP handles mundane issues such as disconnect messages (host unreachable) that applications use to let the other side of a session know what’s happening. ICMP is used for informational and error reporting.
TCP/IP users rarely start a program that uses ICMP. For the most part, ICMP features are called automatically by applications as needed without you ever knowing. There is one very famous program that runs under ICMP, however: the venerable Ping utility. Run Ping from a command prompt to query if a host is reachable. Ping will show the round trip time (RTT)—some call this the real transfer time—for the ICMP packet, usually in seconds. If Ping can’t find the host, the packet will time out and Ping will show you that information, too.
 |
IPv4 Addressing |
TCP/IP networks have long used the Internet Protocol version 4 (IPv4) protocol for addressing. (See “IPv6 Addressing” later in this chapter for a discussion about the protocol poised to replace IPv4.)
IPv4 addresses originally followed rigid blocks, called classes. Today’s IPv4 addresses don’t use classes, but are doled out under a different set of rules. Let’s look at classic IPv4 addressing first, and then turn to modern IPv4 usage.
Local Lingo
IPv4 Most writers drop the version number when discussing IP addressing. The assumption is that if there’s no version number listed, it must be IPv4.
When installing TCP/IP on a system, techs need to configure three settings:
• IP address A unique value that represents a node on a TCP/IP network.
• Subnet mask A value used to help devices distinguish the host’s network.
• Default gateway The IP address of the router interface for your network. The router is responsible for sending data off your network if needed.
IP Addresses
The most common type of IP address consists of a 32-bit value. Here’s an example:
11000000101010000000010000000010
Whoa! IP addresses are just strings of 32 binary digits? Yes, they are, but to make IP addresses easier for humans to use, the 32-bit binary value is broken down into four groups of eight, separated by periods, or dots, like this:
11000000.10101000.00000100.00000010
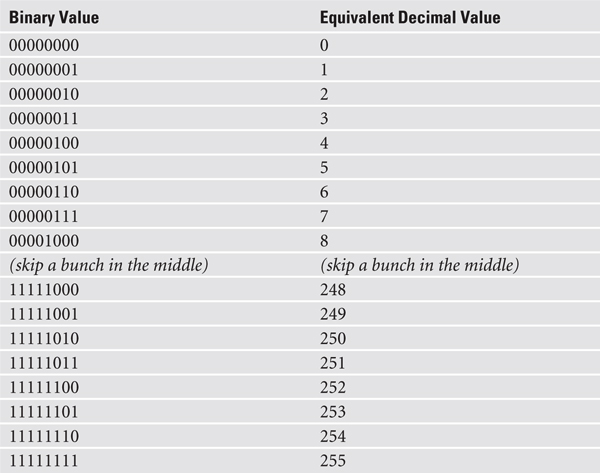
Each of these 8-bit values—called an octet—is, in turn, converted into a decimal number between 0 and 255.
If you took every possible combination of eight binary values and placed them in a spreadsheet, it would look something like the list in the left column. The right column shows the same list with a decimal value assigned to each.
Converted, the original value of 11000000.10101000.00000100.00000010 is displayed as 192.168.4.2 in IPv4’s dotted decimal notation (also referred to as the dotted octet numbering system). Note that dotted decimal is simply a shorthand way for people to discuss and configure the binary IP addresses computers use.
Travel Advisory
When you type an IP address into a computer, the computer ignores the periods and immediately converts the decimal numbers into binary. People need dotted decimal notation, but computers do not.
People who work on TCP/IP networks must know how to convert dotted decimal to binary and back. You can convert easily using any operating system’s calculator. Every OS has a calculator (UNIX/Linux systems have about 100 different ones to choose from) that has a scientific or programmer mode like the one shown in Figure 5.7.
FIGURE 5.7 Mac OS X Calculator in Programmer mode
To convert from decimal to binary, just go to decimal view, type in the value, and then switch to binary view to get the result. To convert to decimal, just go into binary view, enter the binary value, and switch to decimal view to get the result.
Figure 5.8 shows the result of Windows 7’s Calculator converting the decimal value 47 into binary. Notice the result is 101111—the leading two zeroes do not appear. When you work with IP addresses, you must always have eight digits, so just add two more to the left to get 00101111.
FIGURE 5.8 Converting decimal to binary with Windows 7’s Calculator
Travel Advisory
Using a calculator utility to convert to and from binary/decimal is a critical skill for a network tech. Later on you’ll do this again, but by hand!
Just as every MAC address must be unique on a network, every IP address must be unique as well. For logical addressing to work, no two computers on the same network may have the same IP address. In a small network running TCP/IP, every computer has both an IP address and a MAC address (Figure 5.9).
FIGURE 5.9 A small network with both IP and MAC addresses
Every GUI operating system comes with graphical and command-line utilities to display a system’s IP address and MAC address. Figure 5.10 shows a Mac OS X system’s Network utility. Note the MAC address (00:14:51:65:84:a1) and the IP address (192.168.4.57).
FIGURE 5.10 Macintosh OS X Network utility
You can use the command-line utility ipconfig to display the IP and MAC addresses. Run ipconfig /all to see the results shown in Figure 5.11.
FIGURE 5.11 The results from running ipconfig /all
In UNIX/Linux/Mac OS X, you can run the very similar ifconfig command. Figure 5.12, for example, shows the result of running ifconfig ("“eth0” is the NIC) in Ubuntu.
FIGURE 5.12 Results from running ifconfig in Ubuntu
Exam Tip
Make sure you know that ipconfig and ifconfig provide a tremendous amount of information regarding a system’s TCP/IP settings.
IP Addresses in Action
Both LANs and WANs use IP addresses. This can create problems in some circumstances, such as when a computer needs to send data both to computers in its own network and to computers in other networks. How can this be accomplished?
To make all this work, IP must do three things:
• Create some way to use IP addresses so that each LAN has its own identification.
• Interconnect all of the LANs using routers and give those routers some way to use the network identification to send packets to the right network.
• Give each computer on the network some way to recognize if a packet is for the LAN or for a computer on the WAN so it knows how to handle the packet.
Network IDs
To differentiate LANs from one another, each computer on a single LAN must share a very similar IP address. Some parts of the IP address will match all the others on the LAN. Figure 5.13 shows a LAN where all of the computers share the first three numbers of the IP address, with only the last number being unique on each system.
FIGURE 5.13 IP addresses for a LAN
In this example, every computer has an IP address of 202.120.10.x. That means the network ID is 202.120.10.0. The x part of the IP address is the host ID. Combine the network ID (after dropping the ending 0) with the host ID to get an individual system’s IP address. No individual computer can have an IP address that matches the network ID.
Interconnecting
To organize all those individual LANs into a larger network, every TCP/IP LAN that wants to connect to another TCP/IP LAN must have a router connection. There is no exception to this critical rule. A router, therefore, needs an IP address on all the LANs that it serves (Figure 5.14) so it can correctly route packets.
FIGURE 5.14 LAN with router
That router is known as the default gateway. When configuring a client to access the network beyond the router, you use the IP address for the default gateway. Most network administrators give the LAN-side NIC on the default gateway the lowest host address in the network, usually the host ID of 1.
Routers use network IDs to determine network traffic. Figure 5.15 shows a diagram for a small, two-NIC router similar to the ones you see in many homes. Note that one port (202.120.10.1) connects to the LAN and the other port connects to the Internet service provider’s network (14.23.54.223). Built into this router is a routing table, the actual instructions that tell the router what to do with incoming packets and where to send them.
FIGURE 5.15 Router diagram
Travel Assistance
Routing tables are covered in more detail in Chapter 6.
Now let’s add in the LAN and the Internet (Figure 5.16). (The LAN, of course, connects via a switch to the router.) When discussing networks in terms of network IDs, by the way, especially with illustrations in books, the common practice is to draw circles around stylized networks. Here, you should concentrate on the IDs—not the specifics of the networks.
FIGURE 5.16 LAN, router, and the Internet
Network IDs are very flexible, as long as no two interconnected networks share the same network ID. If you wished, you could change the network ID of the 202.120.10.0 network to 202.155.5.0, or 202.21.8.0, just as long as you can guarantee no other LAN on the WAN shares the same network ID. On the Internet, powerful governing bodies carefully allocate network IDs to ensure no two LANs share the same network ID. I’ll talk more about how this works later in the chapter.
So far you’ve only seen examples of network IDs where the last value is zero. This is common for small networks, but it creates a limitation. With a network ID of 202.120.10.0, for example, a network is limited to IP addresses from 202.120.10.1 to 202.120.10.254. (202.120.10.255 is a broadcast address used to talk to every computer on the LAN.) This provides only 254 IP addresses: enough for a small network, but many organizations need many more IP addresses. No worries! You can simply use a network ID with more zeroes, such as 170.45.0.0 (for a total of 65,534 hosts) or even 12.0.0.0 (for around 16.7 million hosts).
Network IDs enable you to connect multiple LANs into a WAN. Routers then connect everything together, using routing tables to keep track of which packets go where. So that takes care of the second task: interconnecting the LANs using routers and giving those routers a way to send packets to the right network.
Now that you know how IP addressing works with LANs and WANs, let’s turn to how IP enables each computer on a network to recognize if a packet is going to a computer on the LAN or to a computer on the WAN. The secret to this is something called the subnet mask.
Subnet Mask
Picture this scenario. Three friends sit at their computers—Computers A, B, and C—and want to communicate with each other. Figure 5.17 illustrates the situation. You can tell from the drawing that Computers A and B are in the same LAN, whereas Computer C is on a completely different LAN. The IP addressing scheme can handle this communication, so let’s see how it works.
FIGURE 5.17 The three amigos, separated by walls or miles
The process to get a packet to a local computer is very different from the process to get a packet to a faraway computer. If one computer wants to send a packet to a local computer, it must send a broadcast to get the other computer’s MAC address. (It’s easy to forget about the MAC address, but remember that the network uses Ethernet and must have the MAC address to get the frame that encapsulates the packet to the other computer.) If the packet is for some computer on a faraway network, the sending computer must send the packet to the default gateway (Figure 5.18).
FIGURE 5.18 Sending a packet remotely
In the scenario illustrated in Figure 5.17, Computer A wants to send a packet to Computer B. Computer B is on the same LAN as Computer A, but that begs a question: How does Computer A know this? Every TCP/IP computer needs a tool to tell the sending computer whether the destination IP address is local or long distance. This tool is the subnet mask.
A subnet mask is nothing more than a string of ones followed by some number of zeroes, always totaling exactly 32 bits, typed into every TCP/IP host. Here’s an example of a typical subnet mask:
11111111.11111111.11111111.00000000
Convert each octet into decimal (use a calculator):
255.255.255.0
When you line up an IP address with a corresponding subnet mask in binary, the portion of the IP address that aligns with the ones of the subnet mask is the network ID portion of the IP address. The portion that aligns with the zeroes is the host ID. With simple IP addresses, you can see this with dotted decimal, but you’ll want to see this in binary for a true understanding of how the computers work.
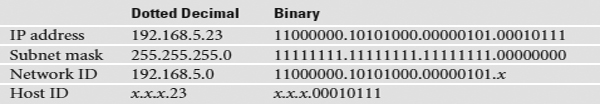
The IP address 192.168.5.23 has a subnet mask of 255.255.255.0. Convert both numbers to binary and then compare the full IP address to the ones and zeroes of the subnet mask:
Before a computer sends out any data, it first compares the destination IP address to its own IP address using the subnet mask. If the destination IP address matches the computer’s IP wherever there’s a one in the subnet mask, then the sending computer knows the destination is local. The network IDs match.
If even one bit of the destination IP address where the ones are on the subnet mask is different, then the sending computer knows it’s a long-distance call. The network IDs do not match.
Travel Advisory
The explanation about comparing an IP address to a subnet mask simplifies the process, leaving out how the computer uses its routing table to accomplish the goal. We’ll get to routing and routing tables in Chapter 6. For now, stick with the concept of the node using the subnet mask to determine the network ID.
Exam Tip
At this point, you should memorize that 0 = 00000000 and 255 = 11111111. You’ll find knowing this very helpful throughout the rest of the book.
Let’s head over to Computer A and see how the subnet mask works. Computer A’s IP address is 192.168.5.23. Convert that into binary:
11000000.10101000.00000101.00010111
Let’s say Computer A wants to send a packet to Computer B. Computer A’s subnet mask is 255.255.255.0. Computer B’s IP address is 192.168.5.45. Convert this address to binary:
11000000.10101000.00000101.00101101
Computer A compares its IP address to Computer B’s IP address using the subnet mask, as shown in Figure 5.19. For clarity, I’ve added a line to show you where the ones end and the zeroes begin in the subnet mask. Computers certainly don’t need the line!
FIGURE 5.19 Comparing addresses
A-ha! Computer A’s and Computer B’s network IDs match! It’s a local call. Knowing this, Computer A can now send out an ARP request, which is a broadcast, as shown in Figure 5.20, to determine Computer B’s MAC address. The Address Resolution Protocol (ARP) is how nodes in a TCP/IP network figure out the destination MAC address based on the destination IP address.
FIGURE 5.20 Sending an ARP
The addressing for the ARP frame looks like Figure 5.21. Note that Computer A’s IP address and MAC address are included.
FIGURE 5.21 Simplified ARP frame
Computer B responds to the ARP by sending Computer A an ARP reply (Figure 5.22). Once Computer A has Computer B’s MAC address, it starts sending packets.
FIGURE 5.22 Computer B responds
Exam Tip
The long-dead Reverse Address Resolution Protocol (RARP) was used to get a layer-3 address when the computer’s MAC address was known, thus, the reverse of an ARP. You’ll see this sometimes as an incorrect answer on the CompTIA Network+ exam.
But what happens when Computer A wants to send a packet to Computer C? First, Computer A compares Computer C’s IP address to its own using the subnet mask (Figure 5.23). It sees that the IP addresses do not match in the ones part of the subnet mask—meaning the network IDs don’t match; therefore, this is a long-distance call.
FIGURE 5.23 Comparing addresses again
Whenever a computer wants to send to an IP address on another LAN, it knows to send the packet to the default gateway. It still sends out an ARP, but this time to the default gateway (Figure 5.24). Once Computer A gets the default gateway’s MAC address, it then begins to send packets with the destination MAC address of the default gateway in the frame, but with the destination IP address of the actual remote destination in the packet.
FIGURE 5.24 Sending an ARP to the gateway
Subnet masks are represented in dotted decimal like IP addresses—just remember that both are really 32-bit binary numbers. All of the following (shown in both binary and dotted decimal formats) can be subnet masks:
11111111111111111111111100000000 = 255.255.255.0
11111111111111110000000000000000 = 255.255.0.0
11111111000000000000000000000000 = 255.0.0.0
Most network folks represent subnet masks using special shorthand: a forward slash (/) character followed by a number equal to the number of ones in the subnet mask. Here are a few examples:
11111111111111111111111100000000 = /24 (24 ones)
11111111111111110000000000000000 = /16 (16 ones)
11111111000000000000000000000000 = /8 (8 ones)
An IP address followed by the / and number tells you the IP address and the subnet mask in one statement. For example, 201.23.45.123/24 is an IP address of 201.23.45.123 with a subnet mask of 255.255.255.0. Similarly, 184.222.4.36/16 is an IP address of 184.222.4.36 with a subnet mask of 255.255.0.0.
Fortunately, computers do all of this subnet filtering automatically. Network administrators need only to enter the correct IP address and subnet mask when they first set up their systems, and the rest happens without any human intervention.
Exam Tip
By definition, all computers on the same network have the same subnet mask and network ID.
Class IDs
To support the dispersion of IP addresses, and to make sure that no organizations used duplicate IP addresses on the Internet, IANA was formed to track and disperse IP addresses to those who need them. Initially handled by a single person (the famous Jon Postel) until 1998, IANA has grown dramatically and now oversees a number of Regional Internet Registries (RIRs) that parcel out IP addresses to large ISPs and major corporations. The RIR for North America is called the American Registry for Internet Numbers (ARIN). The vast majority of end users get their IP addresses from their respective ISPs. IANA passes out IP addresses in contiguous chunks called class licenses, which are outlined in the following table:
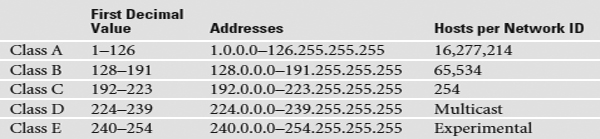
Travel Advisory
127.0.0.0 Careful readers might have picked up on the missing range of numbers in this list: 127.0.0.0–127.255.255.255. These numbers are used for loopback testing, running diagnostics on a local computer. Any number in this range automatically maps to 127.0.0.1, also called the loopback, the local machine, or simply home.
A typical Class A license, for example, has a network ID that starts between 1 and 126; hosts on that network have only the first octet in common, with any numbers for the other three octets. Having three octets to use for hosts means you have an enormous number of possible hosts—over 16 million different number combinations. The subnet mask for Class A licenses is 255.0.0.0, which means you have 24 bits for host IDs.
Do you remember binary math? 224 = 16,277,216. Because the host can’t use all zeroes or all ones (those are reserved for the network ID and broadcast IP, respectively), you subtract two from the final number to get the available host IDs.
Travel Assistance
The Internet Corporation for Assigned Names and Numbers (ICANN) manages the IANA. See www.icann.org for more details.
A Class B license, with a subnet mask of 255.255.0.0, uses the first two octets to define the network ID. This leaves two octets to define host IDs, which means each Class B network ID can have up to 65,534 different hosts.
A Class C license uses the first three octets to define only the network ID. All hosts in network 192.168.35.0, for example, would have all three first numbers in common. Only the last octet defines the host IDs, which leaves only 254 possible unique addresses. The subnet mask for Class C licenses is 255.255.255.0.
Multicast class licenses are used for one-to-many communication, such as in streaming video conferencing. There are three types of ways to send a packet: a broadcast, which is where every computer on the LAN hears the message; a unicast, where one computer sends a message directly to another user; and a multicast, where a single computer sends a packet to a group of interested computers. Multicast is often used when routers talk to each other.
Experimental addresses are reserved and never used except for occasional experimental reasons. These were originally called reserved addresses.
Exam Tip
Make sure you memorize the IP class licenses! You should be able to look at any IP address and know its class license. Here’s a trick to help: The first binary octet of a Class A address always begins with a 0 (0xxxxxxx); for Class B, it begins with a 10 (10xxxxxx); for Class C, with 110 (110xxxxx); for Class D, with 1110 (1110xxxx); and for Class E, it begins with 1111 (1111 xxxx).
Private vs Public IP Addresses
Lots of folks use TCP/IP in networks that either aren’t connected to the Internet or want to hide their computers from the rest of Internet. Certain groups of IP addresses, known as private IP addresses, are available to help in these situations. All routers destroy private IP addresses. Those addresses can never be used on the Internet, making them a handy way to hide systems. Anyone can use these private IP addresses, but they’re useless for systems that need to access the Internet—unless you use the mysterious and powerful NAT, which I’ll discuss in the next chapter. (Bet you’re dying to learn about NAT now!) For the moment, however, let’s just look at the ranges of addresses that are designated as private IP addresses:
• 10.0.0.0 through 10.255.255.255 (1 Class A license)
• 172.16.0.0 through 172.31.255.255 (16 Class B licenses)
• 192.168.0.0 through 192.168.255.255 (256 Class C licenses)
All other Class A, B, and C IP addresses are public IP addresses, meaning they are routable and usable on the Internet.
Exam Tip
Make sure you can quickly tell the difference between a private and a public IP address for the CompTIA Network+ exam.
Need for Changes
IP class licenses worked well for the first few years of the Internet, but quickly ran into trouble due to the fact that they didn’t quite fit for everyone. Early on, IANA gave away IP class licenses rather generously—perhaps too generously. Over time, unallocated IP addresses became scarce. In addition, the IP class licenses concept didn’t scale well. If an organization needed 2,000 IP addresses, for example, it either had to take a single Class B license (wasting 63,000 addresses) or eight Class C licenses. As a result, a new method of generating blocks of IP addresses, called Classless Inter-Domain Routing (CIDR), was developed.
 |
CIDR and Subnetting |
CIDR is based on a concept called subnetting: taking a single network ID and chopping it up into multiple smaller subnets. CIDR and subnetting are virtually the same thing. Subnetting is done by an organization—the organization is given a block of addresses and then breaks the single block of addresses into multiple subnets. CIDR is done by an ISP—the ISP is given a block of addresses, subnets the block into multiple subnets, and then passes out the smaller individual subnets to customers. Subnetting and CIDR have been around for quite a long time now and are a critical part of all but the smallest TCP/IP networks. Let’s first discuss subnetting and then visit CIDR.
Subnetting
Subnetting enables a much more efficient use of IP addresses compared to class licenses. It also enables you to separate a network for security (separating a bank of public access computers from your more private computers) and for bandwidth control (separating a heavily used LAN from one that’s not so heavily used).
Exam Tip
You need to know how to subnet to pass the CompTIA Network+ exam.
The cornerstone to subnetting lies in the subnet mask. You take an existing /8, /16, or /24 subnet and extend the subnet mask by adding more ones by taking away the corresponding number of zeroes. For example, let’s say you have an Internet café with about 50 computers, 40 of which are for public use and 10 of which are used in the back office for accounting and such (Figure 5.25). Your network ID is 192.168.4.0/24. You want to prevent people using the public systems from accessing your private machines, so you decide to create subnets. You also have wireless Internet and want to separate wireless clients (never more than 10) on their own subnet.
FIGURE 5.25 Layout of the network
You need to keep two things in mind about subnetting. First, start with the given subnet mask and add more ones to the right until you have the number of subnets you need. Second, forget the dots. They no longer define the subnets.
Never try to subnet without first converting to binary. Too many techs are what I call “victims of the dots.” They are so used to working only with class licenses that they forget there’s more to subnets than just /8, /16, and /24 networks. There is no reason network IDs must end on the dots. The computers, at least, think it’s perfectly fine to have subnets that end at points between the periods, such as /26, /27, or even /22. The trick here is to stop thinking about network IDs and subnet masks just in their dotted decimal format and instead return to thinking of them as binary numbers.
Exam Tip
Some authors will drop the trailing zeros when using CIDR notation. I always do this when teaching because it’s faster to write. So you might see a network ID like 192.168.4/24. The last octet of zero is implied by the /24. Either way works.
Let’s begin subnetting the café’s network of 192.168.4/24. Start by changing a zero to a one on the subnet mask so the /24 becomes a /25 subnet:
11111111111111111111111110000000
Calculating Hosts
Before going even one step further, you need to answer this question: On a /24 network, how many hosts can you have? Well, if you used dotted decimal notation, you might say
192.168.4.1 to 192.168.4.254 = 254 hosts
But do this from the binary instead. In a /24 network, you have eight zeroes that can be the host ID:
00000001 to 11111110 = 254
There’s a simple piece of math here: 2x – 2, where x represents the number of zeroes in the subnet mask:
28 – 2 = 254
If you remember this simple formula, you can always determine the number of hosts for a given subnet. This is critical! Memorize this!
If you have a /26 subnet mask on your network, what is the maximum number of hosts you can have on that network?
1. Because a subnet mask always has 32 digits, a /26 subnet means you have 6 zeroes left after the 26 ones.
2. 26 – 2 = 62 total hosts.
Excellent! Knowing how to determine the number of hosts for a particular subnet mask will help you tremendously in a moment.
Your First Subnet
Let’s now make a subnet. All subnetting begins with a single network ID. In this scenario, you need to convert the 192.168.4/24 network ID for the café into three network IDs: one for the public computers, one for the private computers, and one for the wireless clients.
Travel Advisory
You cannot subnet without using binary!
The primary tool for subnetting is the existing subnet mask. Write it out in binary. Place a line at the end of the ones, as shown in Figure 5.26.
FIGURE 5.26 Step 1 in subnetting
Now draw a second line one digit to the right, as shown in Figure 5.27. You’ve now separated the subnet mask into three areas that I call (from left to right) the default subnet mask (DSM), the network ID extension (NE), and the hosts (H). These are not industry terms so you won’t see them on the CompTIA Network+ exam, but they’re a handy Mike Trick that makes the process of subnetting a lot easier.
FIGURE 5.27 Organizing the subnet mask
You now have a /25 subnet mask. At this point, most people first learning how to subnet start to freak out. They’re challenged by the idea that a subnet mask of /25 isn’t going to fit into one of the three pretty subnets of 255.0.0.0, 255.255.0.0, or 255.255.255.0. They think, “That can’t be right! Subnet masks are made out of only 255s and 0s.” That’s not correct. A subnet mask is a string of ones followed by a string of zeroes. People only convert it into dotted decimal to enter things into computers. So convert /25 into dotted decimal. First write out 25 ones, followed by seven zeroes. (Remember, subnet masks are always 32 binary digits long.)
11111111111111111111111110000000
Insert the periods in between every eight digits:
11111111.11111111.11111111.10000000
Then convert them to dotted decimal:
255.255.255.128
Get used to the idea of subnet masks that use more than 255s and 0s. Here are some examples of perfectly legitimate subnet masks. Try converting these to binary to see for yourself.
255.255.255.224
255.255.128.0
255.248.0.0
Calculating Subnets
When you subnet a network ID, you need to follow the rules and conventions dictated by the good folks who developed TCP/IP to ensure that your new subnets can interact properly with each other and with larger networks. All you need to remember for subnetting is this: start with a beginning subnet mask and extend the subnet extension until you have the number of subnets you need. The formula for determining how many subnets you create is 2y, where y is the number of bits you add to the subnet mask.
Figure 5.28 shows a starting subnet of 255.255.255.0. If you move the network ID extension over one, it’s only a single digit: 21.
FIGURE 5.28 Organizing the subnet mask
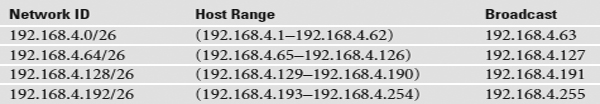
That single digit is only a zero or a one, which gives you two subnets. You have only one problem—the café needs three subnets, not just two! So let’s take the original /24 and subnet it down to /26. Extending the network ID by two digits creates four new network IDs, 22 = 4. To see each of these network IDs, first convert the original network ID—192.168.4.0—into binary. Then add the four different network ID extensions to the end, as shown in Figure 5.29.
FIGURE 5.29 Creating the new network IDs
Figure 5.30 shows a sampling of the IP addresses for each of the four new network IDs.
FIGURE 5.30 New network ID address ranges
Now convert these four network IDs back to dotted decimal:
The host ranges start with the first address available after the network ID. The first one is obvious, because the network ID ends with 0 in the fourth octet, so the first host would have a 1 in the fourth octet. The last number available in the host range is one number before the start of the next network ID, because the last available address on the subnet is the broadcast address.
Congratulations! You’ve just taken a single network ID, 192.168.4.0/24, and subnetted it into four new network IDs! Figure 5.31 shows how you can use these new network IDs in a network.
FIGURE 5.31 Three networks using the new network IDs
You may notice that the café only needs three subnets, but you created four—you’re wasting one. Because subnets are created by powers of two, you will often create more subnets than you need—welcome to subnetting.
Travel Advisory
In terms of the café example, the unused network ID sets them up for scalability. If the café grows to need another subnet, it’s already there for them to use without messing with the existing subnets.
 |
IPv6 Addressing |
The word is out (actually, it has been for some time)—the Internet’s running out of spare 32-bit IP addresses. What is the Internet to do? Simple—use bigger addresses. But is that possible while making everything backward-compatible with the existing address scheme? Sure it is; here’s IP version 6.
It sounds easy, but it has taken many years to perfect a replacement for the 32-bit IP addressing scheme.
With a 128-bit address range, IPv6 supports a mind-blowing 340,282,366,920,938,463,463,374,607,431,768,211,456 addresses, which equates to approximately 665,570,793,348,866,943,898,599 addresses per square meter of the surface of the planet Earth.
IPv6 is in use today on parts of the Internet, but it’s not having much impact on the desktop (yet). The new addressing scheme was designed to slide in place of IPv4 relatively seamlessly, and parts of the Internet infrastructure are being upgraded all the time without us noticing. IPv6 will address two major issues that plague IPv4: a shortage of addresses and the increasing complexity of routing information.
Exam Tip
For the CompTIA Network+ exam, you will need to know and identify an IPv6 address along with some basics about the IPv6 address schemes. You don’t need to memorize the long numbers mentioned earlier—they’re just there out of interest and to give you some sense of what “128-bit addressing” means.
IPv6 Addresses
An IPv6 address is a 128-bit address displayed in hexadecimal format and not the dotted decimal notation that is used by IPv4. The IPv6 address is divided into eight 16-bit groups that are separated by a colon (:). Many techs call these groups hextets, although that’s not an official name. The following is an example of an IPv6 address:
65b3:b834:45a3:0000:0000:762e:0270:5224
An IPv6 address is not case-sensitive, and you do not need to place leading zeros at the beginning of the address when referencing a system that has leading zeros at the beginning. You can also replace consecutive zeros with double colons (::) when referencing an address that has a group of zeros in the address. For example, the loopback address in IPv6 is 0:0:0:0:0:0:0:1 and can be shorted to ::1, with the :: replacing all the consecutive zeros at the beginning of the address. This process is known as compressing zeros.
Exam Tip
You need to know that IPv6 uses a 128-bit address space. You may also be asked to identify the IPv6 loopback address: 0:0:0:0:0:0:0:1.
IPv6 uses three types of addresses: unicast, multicast, and anycast:
• Unicast Used for one-to-one communication.
• Multicast Used to send data to a group of systems.
• Anycast Applied to a group of systems providing a service. Clients that send data to the anycast address could have the data sent to any of the systems that are part of the anycast address.
To make life more complicated, you should be familiar with different types of unicast addresses for the CompTIA Network+ exam: global unicast, site-local unicast, and link-local unicast addresses handle different types of unicast traffic. Following is a quick breakdown of each of the different types of unicast addresses:
• Global unicast A public IPv6 address that is routable on the Internet. The address assigned to the host must be unique on the Internet. This address type is equivalent to a public IP address with IPv4.
• Site-local unicast A private address for the IPv6 protocol; the address always starts with FEC0. Assigning a site-local address to a system is equivalent to using a private address in IPv4, such as 10.0.0.0. The site-local address cannot be used to communicate off the local site or network and is not reachable by other sites or systems on the Internet.
• Link-local unicast An address that’s automatically assigned to the system and is used to communicate only with other nodes on the link. Link-local addresses always start with FE80. This address type is equivalent to an APIPA address with IPv4.
Exam Tip
You should be familiar with two of the reserved addresses in IPv6: the loopback address, which is 0:0:0:0:0:0:0:1 (or ::1), and the address for a system with no address specified: 0:0:0:0:0:0:0:0 (or ::).
IPv6 Protocols
Not only has the address scheme changed with IPv6, but so have the protocols that exist in the IPv6 protocol suite. ICMPv6 provides a great example.
ICMPv6
The ICMPv6 protocol is responsible for error and status information as in IPv4, but it has been changed. ICMPv6 uses codes, while ICMPv4 used types and codes. For ICMPv6, each code indicates the type of message. Codes from 0 to 127 are used by error messages, while codes 128 to 255 are for information messages. For example, the echo request message is code 128 with ICMPv6, and the echo reply message is code 129.
ICMPv6 has expanded on its features from the ICMPv4 days. You should be familiar with the following two features of the ICMPv6 protocol:
• Multicast Listener Discovery (MLD) Replaces the multicast protocol in IPv4 known as Internet Group Management Protocol (IGMP) and is used for multicast communication.
• Neighboring Discovery (ND) Replaces ARP from the IPv4 days by performing the same function, but it’s also responsible for neighboring router discovery, automatic address assignment, and duplicate address detection, to name a few features.
IPv6 has been totally redesigned and offers many additional new features, but for the CompTIA Network+ exam, you need to know only the basics.
 |
Domain Name System |
TCP/IP networks use Domain Name System (DNS) servers to translate IP addresses into names that humans can better handle and remember. DNS has a set of rules for names and rules for name resolution that enable computers to communicate over networks large and small.
DNS uses a hierarchical naming scheme. When a device wants to know the IP address for a device somewhere else in a network, it queries the local DNS server. The DNS server on a local network knows all the names and IP addresses for local computers. If the LAN connects to other LANs, the DNS server will know the IP address for a DNS server higher up the chain. That way, if a local computer needs to find the IP address for a remote computer, the DNS server doesn’t have to know it. It simply forwards the DNS request up to the next higher DNS server. This continues until resolution occurs (Figure 5.32).
FIGURE 5.32 A host’s DNS server resolves an FQDN using a hierarchy of DNS servers.
The top-dog DNS server is actually a bunch of powerful computers dispersed around the world. They work as a team and are known collectively as the DNS root servers (or simply as the DNS root). The Internet name of this computer team is “.”—that’s right, just “dot.” Sure, it’s weird, but it’s quick to type, and they had to start somewhere.
DNS root has the complete definitive name resolution table, but most name resolution work is delegated to other DNS servers. Just below the DNS root in the hierarchy is a set of DNS servers—called the top-level domain servers—that handle what are known as the top-level domain (TLD) names. These are the famous com, org, net, edu, gov, mil, and int names (although many TLDs have been added since 2001). The top-level DNS servers delegate to thousands of second-level DNS servers; these servers handle the millions of names, like totalsem.com and whitehouse.gov, that have been created within each of the top-level domains.
Exam Tip
The original top-level domain names were com, org, net, edu, gov, mil, and int.
A complete DNS name, including the host name and all of its domains (in order), is called a fully qualified domain name (FQDN), and it’s written with the root on the far right, followed by the names of the domains (in order) added to the left of the root, and the host name on the far left.
A typical DNS name for a web server, such as www.google.com, for example, has three components:
• .com refers to the root domain.
• .google refers to the google subdomain of the root domain.
• www refers to the specific computer (or cluster of computers, in this case).
The www.google.com FQDN maps directly to an IP address. DNS servers at the .com level certainly know the IP address for the google.com DNS server; the google.com DNS server knows the IP address for the www host.
FQDNs work at the local level too, by the way, even in networks that don’t connect to the Internet. My office LAN is totalhome, with no .com or anything. So to access my file server, my employees and I type //fs7.totalhome in Network and the file server opens up. I’m using Internet FQDNs for the primary example of how DNS works because that’s what most people are used to seeing.
Although this process might sound a bit complex, it works very well and provides a great deal of flexibility. Prior to the existence of DNS, every computer that wanted to use domain names had to have a local file—called a HOSTS file—that contained a table of IP addresses and their associated names. This file was stored on every system’s hard disk. Because the HOSTS file changed on a daily basis, network techs had to keep downloading updates from the Internet! You can still use a HOSTS file today if you just have a small number of computers on a local network, but DNS is the way to go for bigger networks. A simple HOSTS file would look something like this:
127.0.0.1 localhost
Notice that the name localhost appears in the HOSTS file as an alias for the loopback address 127.0.0.1.
Exam Tip
Most DNS servers support a feature known as Dynamic DNS (DDNS), which means that client systems can automatically register their own records in DNS upon bootup using DHCP (see the DHCP section below). This is a popular feature with Windows DNS servers. You could add a special option to the DHCP server, which is generally called the DNS suffix. The DNS suffix helps clients access network resources more efficiently.
DNS Records
A DNS server maintains a database of information about the domain names it knows, separating them according to type, using different records. For example, an A record maps a hostname to its IPv4 address. An AAAA record does the same for a hostname in an IPv6 network.
Local Lingo
MX, CNAME, PTR Other, less common DNS record types are MX, used by SMTP servers to determine where to send mail; CNAME, which maps aliases to IP addresses; and PTR, which is used in reverse lookups. My computer’s name is mikespc.totalhome, but people in my office can ping mike.totalhome and reach the same physical computer. MX stands for Mail eXchanger; CNAME is short for canonical name; PTR is short for pointer.
DHCP
With so many settings (IP address, subnet mask, default gateway, DNS servers) to specify, the typical TCP/IP network administrator can spend days properly configuring each host manually. For troubleshooting purposes, you sometimes must put in all these settings manually, what we call static configuration, because the settings only change when you manually make the changes.
Fortunately, TCP/IP provides a protocol that takes much of the drudgery out of TCP/IP configuration: DHCP.
Travel Advisory
IPv6 uses DHCPv6 as its DHCP protocol, while the DHCP protocol that came with IPv4 is known as DHCPv4.
Dynamic Host Configuration Protocol (DHCP) servers distribute IP addresses and additional IP settings to machines on the network. Once a computer is configured to use DHCP, we call it a DHCP client. When a DHCP client boots up, it automatically sends out a special DHCP Discover packet using the broadcast address. This DHCP Discover message asks, “Are there any DHCP servers out there?” (See Figure 5.33.) What follows is a series of back-and-forth broadcasts.
FIGURE 5.33 Computer sending out a DHCP Discover message
The DHCP server responds to DHCP Discover requests with a DHCP Offer. The DHCP server is configured to pass out IP addresses from a range (called a DHCP scope) and a subnet mask (Figure 5.34). It also passes out other information, known generically as options, that cover an outrageously large number of choices, such as your default gateway, DNS server, Network Time server, and so on.
FIGURE 5.34 DHCP server main screen
Exam Tip
DHCP servers can be set up to reserve addresses for specific machines through what’s called, appropriately, DHCP reservations. You use these for servers inside your network, for example, so if you had to change their IP addresses for some reason, you could do it from a central location. The other option is to use static IPs, but then you’d need to log into each server to change the IP addresses.
Figure 5.35 shows the configuration screen from the popular DHCP Server that comes with Windows Server 2008. Note the single scope. Figure 5.36 shows the same DHCP Server tool, in this case, detailing the options screen.
FIGURE 5.35 DHCP Server configuration screen
FIGURE 5.36 DHCP Server options screen
The DHCP client sends out a DHCP Request—a poor name choice, as it is really accepting the offer. The DHCP server then sends a DHCP Acknowledge and lists the MAC address as well as the IP information given to the DHCP client in a database (Figure 5.37).
FIGURE 5.37 DHCP request and DHCP acknowledge
The acceptance from the DHCP client of the DHCP server’s data is called a DHCP lease. A DHCP lease is set for a fixed amount of time, generally five to eight days. Near the end of the lease time, the DHCP client simply makes another DHCP Discover message. The DHCP server looks at the MAC address information and, unless another computer has taken the lease, always gives the DHCP client the same IP information, including the same IP address.
Living with DHCP
DHCP is very convenient and, as such, very popular. It’s so popular that you’ll very rarely see a user’s computer on any network using static addressing.
You should know how to deal with the problems that arise with DHCP. The single biggest issue is when a DHCP client tries to get a DHCP address and fails. You’ll know when this happens because the operating system will post some form of error telling you there’s a problem (Figure 5.38) and the DHCP client will have a rather strange address in the 169.254/16 network ID.
FIGURE 5.38 DHCP error in Windows 7
This special IP address is generated by Automatic Private IP Addressing (APIPA). All DHCP clients are designed to generate an APIPA address automatically if they do not receive a response to a DHCP Discover message. The client only generates the last two octets of an APIPA address. This at least allows the dynamic clients on a single network to continue to communicate with each other because they are on the same network ID.
 Objective 5.01: The TCP/IP Protocol Suite The TCP/IP suite is made up of a number of protocols that work together to make it the most popular protocol in networking today. Application-level protocols use port numbers to initiate some sort of request (on the client) and answer that request (on the server). TCP and UDP operate at the Transport layer, packaging data into segments and datagrams, and sending those to the IP for encapsulation into IP packets.
Objective 5.01: The TCP/IP Protocol Suite The TCP/IP suite is made up of a number of protocols that work together to make it the most popular protocol in networking today. Application-level protocols use port numbers to initiate some sort of request (on the client) and answer that request (on the server). TCP and UDP operate at the Transport layer, packaging data into segments and datagrams, and sending those to the IP for encapsulation into IP packets. Objective 5.02: IPv4 Addressing The original IP addressing scheme (IPv4) uses a 32-bit address to identify a host address and its network address based on a series of addressing schemes known as IP classes. The associated subnet mask identifies where the boundary between the network and host address lies and also allows us to change this boundary if we wish.
Objective 5.02: IPv4 Addressing The original IP addressing scheme (IPv4) uses a 32-bit address to identify a host address and its network address based on a series of addressing schemes known as IP classes. The associated subnet mask identifies where the boundary between the network and host address lies and also allows us to change this boundary if we wish. Objective 5.03: CIDR and Subnetting CIDR did away with typical class IDs. Altering the default subnet mask enables you to subdivide a network ID into smaller sections, called subnets. Subnetting can help with general network management and also traffic management.
Objective 5.03: CIDR and Subnetting CIDR did away with typical class IDs. Altering the default subnet mask enables you to subdivide a network ID into smaller sections, called subnets. Subnetting can help with general network management and also traffic management. Objective 5.04: IPv6 Addressing IPv6 uses a 128-bit addressing scheme to provide (in effect) a limitless supply of IP addresses, and it is needed because the 32-bit address range of IPv4 is running out of spare addresses. Parts of the Internet are already using IPv6, but it is not generally in use at the desktop yet. Be sure that you can identify an IPv6 address, and know that the loopback address is 0:0:0:0:0:0:0:1 or (::1) and that an unspecified address shows as 0:0:0:0:0:0:0:0 (or ::).
Objective 5.04: IPv6 Addressing IPv6 uses a 128-bit addressing scheme to provide (in effect) a limitless supply of IP addresses, and it is needed because the 32-bit address range of IPv4 is running out of spare addresses. Parts of the Internet are already using IPv6, but it is not generally in use at the desktop yet. Be sure that you can identify an IPv6 address, and know that the loopback address is 0:0:0:0:0:0:0:1 or (::1) and that an unspecified address shows as 0:0:0:0:0:0:0:0 (or ::). Objective 5.05: Domain Name System Although it’s easier for humans to refer to computer systems using computer names or fully qualified domain names (such as www.totalsem.com), communication between two systems can take place only if the target machine’s IP address is known. TCP/IP environments use a database system called DNS (Domain Name System) to resolve IP addresses from fully qualified domain names, such as www.totalsem.com. DNS uses a hierarchical structure, with separate servers (or groups of servers) managing the resolution of various parts of a domain name. Use DHCP for automatic setup of hosts on a network, so you don’t have to provide the IP address, subnet mask, and so on manually.
Objective 5.05: Domain Name System Although it’s easier for humans to refer to computer systems using computer names or fully qualified domain names (such as www.totalsem.com), communication between two systems can take place only if the target machine’s IP address is known. TCP/IP environments use a database system called DNS (Domain Name System) to resolve IP addresses from fully qualified domain names, such as www.totalsem.com. DNS uses a hierarchical structure, with separate servers (or groups of servers) managing the resolution of various parts of a domain name. Use DHCP for automatic setup of hosts on a network, so you don’t have to provide the IP address, subnet mask, and so on manually.REVIEW QUESTIONS
1. Which of the following does not represent an IPv6 address?
A. 2001:0db8:3c4d:0015:0000:0000:abcd:ef12
B. 0:0:0:0:0:0:0:1
C. 255.255.0.0
D. ::1
2. Which of the following is a valid class B host address?
A. 147.28.0.0
B. 192.168.14.50
C. 12.12.12.12
D. 128.14.255.0
3. What is the minimum number of data bits required for subnet addressing to allow a total of five subnets to be created?
4. What port number does Telnet use?
5. Which of the following protocols provides TCP/IP name resolution?
A. DHCP
B. SNMP
C. Telnet
D. DNS
6. Which protocol provides automatic host IP address assignment?
A. DHCP
B. DNS
C. NetBIOS
D. BOOTR
7. Which protocol enables connectionless communication?
A. DNS
B. DHCP
C. TCP
D. UDP
8. What port number is used to connect to a DNS server?
9. A user calls and says his IP address is 169.154.50.12. What kind of address does he have?
A. APIPA
B. DHCP
C. DNS
D. Loopback
10. Which of the following is a valid class A address?
A. 10.256.128.12
B. 120.255.128.12
C. 169.154.128.12
D. 192.168.1.12
REVIEW ANSWERS
1. C 255.255.0.0 is an IPv4 class B subnet mask address. All other choices are valid IPv6 addresses.
2. D 128.14.255.0 is a valid class B address. Although choice A is a class B address, it is an invalid host address of all zeroes (x.x.0.0).
3. C Three bits allow a total of six subnets to be created, giving scope for the five we want to create. Two bits (choice B) would allow only two subnets.
4. B Telnet uses port 23.
5. D DNS provides name resolution. DHCP dynamically dishes out IP addresses and other important information to clients. SNMP is for network management, and Telnet provides terminal emulation functionality.
6. A DHCP, Dynamic Host Configuration Protocol, provides automatic host IP address assignment.
7. D UDP enables connectionless communication.
8. C DNS uses UDP and TCP port 53.
9. A The poor guy’s computer can’t reach a DHCP server and thus has a default APIPA address.
10. B Both A and B start in the right address range (first octet between 1 and 126), but the second octet in choice A contains an invalid number, because 255 is the highest number in an IPv4 octet.







































 Objective 5.01: The TCP/IP Protocol Suite The TCP/IP suite is made up of a number of protocols that work together to make it the most popular protocol in networking today. Application-level protocols use port numbers to initiate some sort of request (on the client) and answer that request (on the server). TCP and UDP operate at the Transport layer, packaging data into segments and datagrams, and sending those to the IP for encapsulation into IP packets.
Objective 5.01: The TCP/IP Protocol Suite The TCP/IP suite is made up of a number of protocols that work together to make it the most popular protocol in networking today. Application-level protocols use port numbers to initiate some sort of request (on the client) and answer that request (on the server). TCP and UDP operate at the Transport layer, packaging data into segments and datagrams, and sending those to the IP for encapsulation into IP packets. Objective 5.02: IPv4 Addressing The original IP addressing scheme (IPv4) uses a 32-bit address to identify a host address and its network address based on a series of addressing schemes known as IP classes. The associated subnet mask identifies where the boundary between the network and host address lies and also allows us to change this boundary if we wish.
Objective 5.02: IPv4 Addressing The original IP addressing scheme (IPv4) uses a 32-bit address to identify a host address and its network address based on a series of addressing schemes known as IP classes. The associated subnet mask identifies where the boundary between the network and host address lies and also allows us to change this boundary if we wish. Objective 5.03: CIDR and Subnetting CIDR did away with typical class IDs. Altering the default subnet mask enables you to subdivide a network ID into smaller sections, called subnets. Subnetting can help with general network management and also traffic management.
Objective 5.03: CIDR and Subnetting CIDR did away with typical class IDs. Altering the default subnet mask enables you to subdivide a network ID into smaller sections, called subnets. Subnetting can help with general network management and also traffic management. Objective 5.04: IPv6 Addressing IPv6 uses a 128-bit addressing scheme to provide (in effect) a limitless supply of IP addresses, and it is needed because the 32-bit address range of IPv4 is running out of spare addresses. Parts of the Internet are already using IPv6, but it is not generally in use at the desktop yet. Be sure that you can identify an IPv6 address, and know that the loopback address is 0:0:0:0:0:0:0:1 or (::1) and that an unspecified address shows as 0:0:0:0:0:0:0:0 (or ::).
Objective 5.04: IPv6 Addressing IPv6 uses a 128-bit addressing scheme to provide (in effect) a limitless supply of IP addresses, and it is needed because the 32-bit address range of IPv4 is running out of spare addresses. Parts of the Internet are already using IPv6, but it is not generally in use at the desktop yet. Be sure that you can identify an IPv6 address, and know that the loopback address is 0:0:0:0:0:0:0:1 or (::1) and that an unspecified address shows as 0:0:0:0:0:0:0:0 (or ::). Objective 5.05: Domain Name System Although it’s easier for humans to refer to computer systems using computer names or fully qualified domain names (such as www.totalsem.com), communication between two systems can take place only if the target machine’s IP address is known. TCP/IP environments use a database system called DNS (Domain Name System) to resolve IP addresses from fully qualified domain names, such as www.totalsem.com. DNS uses a hierarchical structure, with separate servers (or groups of servers) managing the resolution of various parts of a domain name. Use DHCP for automatic setup of hosts on a network, so you don’t have to provide the IP address, subnet mask, and so on manually.
Objective 5.05: Domain Name System Although it’s easier for humans to refer to computer systems using computer names or fully qualified domain names (such as www.totalsem.com), communication between two systems can take place only if the target machine’s IP address is known. TCP/IP environments use a database system called DNS (Domain Name System) to resolve IP addresses from fully qualified domain names, such as www.totalsem.com. DNS uses a hierarchical structure, with separate servers (or groups of servers) managing the resolution of various parts of a domain name. Use DHCP for automatic setup of hosts on a network, so you don’t have to provide the IP address, subnet mask, and so on manually.