A virtual private network (VPN) can add another effective form of security to data that moves from a remote client to a host network that can be located anywhere with a connection to the Internet.
A VPN uses a data tunnel to connect two points on a network through an encrypted channel. The endpoints can be a single network client and a network server, a pair of client computers or other devices, or the gateway to a pair of LANs. Data that passes through a public network such as the Internet is completely isolated from other network traffic. VPNs use login and password authentication to restrict access to authorized users; they encrypt the data to make it unintelligible to intruders who intercept the data; and they use data authentication to maintain the integrity of each data packet and to assure that all data originates with legitimate network clients.
Note
VPN functions occur at the IP or network layer of the ISO model. Therefore, they can operate on top of the Wi-Fi or other wireless protocols, which operate at the physical layer. VPNs can also pass data across a network connection that includes more than one physical medium (for example, a wireless link that passes data onward to a wired Ethernet network). In other words, a VPN is an end-to-end service; the data can use a wireless link, an Ethernet cable, an ordinary telephone line, or some combination of those and other transmission media.
In a traditional VPN, a remote user can log in to a distant LAN and obtain all the same network services that are available to local clients. VPNs are commonly used to extend corporate networks to branch offices and to connect users to the LAN from home or from off-site locations such as a client or customer's office.
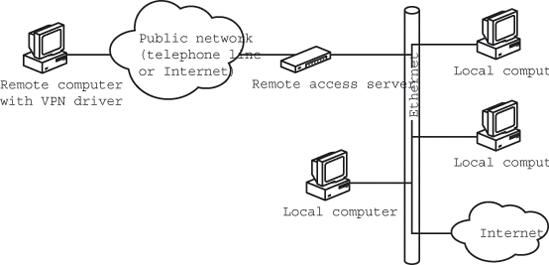
A connection through a VPN server looks to the rest of the network exactly like a client device connected directly to the LAN. The only difference is the data from the VPN passes through a VPN driver and a public network instead of moving directly from the network adapter to the LAN. Figure 13-3 shows a typical VPN connection to a remote network.
All of the same security benefits also apply to short-range VPNs that tunnel through a wireless link and longer-range VPNs that start on a wireless network and relay the data to a remote server. These are two different uses for a VPN: a local VPN that only extends across the wireless portion of a network between the client devices and the access point, and an extended network that carries VPN-encoded data beyond the access points to a VPN server through a public network, such as the Internet or a dial-up telephone connection. An extended network is a traditional VPN that happens to originate from a wireless network client. The same VPN can also support connections that don't include a wireless segment and logins from public wireless services, such as the ones at airports or coffee shops. This setup is conventional for a VPN.
Local, short-range VPNs are interesting to people who operate wireless networks because they add another layer of security to wireless links. Because the data moving between wireless clients and the network access point is encrypted (using an algorithm that is more secure than WPA encryption), it is unintelligible to any third party who might be monitoring the radio signal. Because the VPN server won't accept data links at the access point from wireless clients that are not using the correct VPN drivers and passwords, an intruder can't break into the network by associating a rogue client with the access point.
The goal of a wireless VPN is to protect the wireless link between the clients and the access point and to lock out unauthorized users. Therefore, the isolated and encrypted data can only move across a single room rather than over hundreds or thousands of miles. Of course, the access point might also relay VPN-encoded data onward through the Internet to a network host in another location.
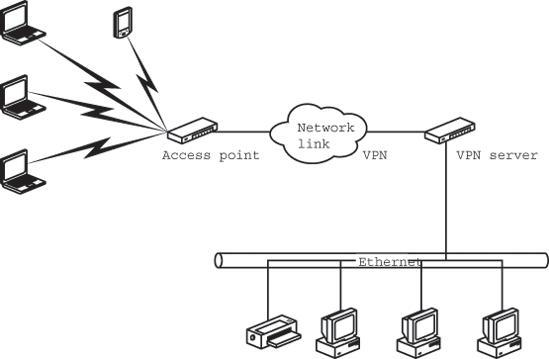
Figure 13-4 shows a wireless connection to a VPN. The VPN server is located between the wireless access point and the host LAN, so all of the packets that move through the wireless portion of the network are encoded. For clarity, the diagram shows the VPN server as a separate component, but the most practical way to add VPN security to a wireless LAN is to use a router or gateway that incorporates VPN support. VPN-enabled routers are available from several vendors, including Cisco, NETGEAR, and TRENDnet.
Figure 13-4. A VPN provides a secure connection between a wireless network and an Internet gateway or a local LAN.
A VPN moves data through one or more intermediate networks to a destination on another network. The VPN's tunneling client encapsulates the existing data packets or frames by adding a new header with the routing information that instructs the packets how to reach the VPN's endpoint. The transmission path through the intermediate networks is called a tunnel. At the other end of the tunnel, the VPN server removes the tunneling header and forwards the data to the destination specified by the next layer of headers. The exact form of the tunnel doesn't make any difference to the data because the data treats the tunnel as a point-to-point connection.
The tunneling headers can take several forms. The methods used most widely in VPNs are Point-to-Point Tunneling Protocol (PPTP), Layer Two Tunneling Protocol (L2TP), and IP Security (IPsec) mode. PPTP and L2TP can move data through IP, IPX, and NetBEUI networks; IPsec is limited to IP networks. Both the client and the server must use the same protocol.
In PPTP and L2TP, the client and server must configure the tunnel for each transmission before they begin to exchange data. The configuration parameters include the route through the intermediate network and the encryption and compression specifications. When the transmission is complete, the client and server terminate the connection and close the tunnel.
Unfortunately, several data security analysts have identified significant flaws in PPTP that allow intruders to break into a PPTP-based VPN and sniff passwords and then decode encryption, read data, or inflict damage to a network server. Therefore, PPTP headers are not secure and should not be used.
In an IPsec network link, the client and server must establish the tunnel through the intermediate networks in a separate transaction before they begin to exchange data.
Both L2TP and IPsec offer specific advantages and disadvantages, but they're both good enough to create a secure link between a wireless network client and an access point. The differences among the three are technical rather than practical. You can find an excellent explanation of the internal operation of all three protocols in Microsoft's white paper entitled "Virtual Private Networking in Windows 2000: An Overview," which is available online at http://technet.microsoft.com/en-us/library/bb742566.aspx (but remember that the flaws in PPTP networks were identified after that whitepaper was written).
A VPN server (or host) can be part of a Linux/Unix or Windows server, or it can be built into a stand-alone network router or gateway. If your network already uses a separate computer as a dedicated server, you can use that computer as the VPN server. A separate piece of hardware might be a better choice if your network does not already have a full-blown network server.
Dozens of VPN equipment makers offer routers, gateways, and other products that support one or more of the VPN protocols. Each of these products has a different feature set, so testing the specific combination of client and server that you intend to use on your own network before you commit to them is essential. The Virtual Private Network Consortium (VPNC) is moving toward a set of interoperability tests and certification standards (much like the Wi-Fi standards for wireless Ethernet equipment). The VPNC website (http://www.vpnc.org/) lists the products that have passed the interoperability tests, and the site also provides links to information sources for a long list of VPN products.
If you're committed to using a Windows server, you can use either L2TP or IPsec with Windows Server 2003 or Windows Server 2008; if your server runs the older Windows NT Server 4.0 or Windows 2000 Server software, you're limited to L2TP (or the seriously flawed PPTP). The server also requires two network interface cards: one connected to the wired LAN or the Internet gateway and the other connected to the wireless network. The interface card that is connected to the wireless port normally connects directly to the wireless access point's Ethernet port. The exact process of installing an L2TP host on a Windows server is slightly different in each version of Windows, but the general steps are the same. For specific information about configuring a particular operating system, consult the online Help screens and Microsoft's Resource Kit and other online documentation for your server's operating system. The following sections describe the configuration steps in general terms.
Note
For more information about deploying and using VPNs with Microsoft servers, see the Microsoft TechNet articles at http://technet.microsoft.com/en-us/network/bb545442.aspx.
- Configure the connection to the LAN.
The link to the LAN or other network is a dedicated connection through a network adapter. The network connection profile for this connection must include the IP address and subnet mask assigned to this connection and the default gateway address assigned to the network gateway.
- Configure the VPN connection.
The VPN connection is usually an Ethernet link to one or more access points. The connection profile on the server for the VPN connection must include the IP address and subnet mask assigned to this port and the addresses of the DNS and WINS name servers used by this network.
- Configure the remote-access server as a router.
The server must use either static routes or routing protocols that make each VPN client reachable from the wired network.
- Enable and configure the server for L2TP clients.
Windows uses Remote Access Service (RAS) and point-to-point protocol (PPP) to establish VPN connections. The Routing and Remote Access service enables RAS. A VPN connection requires the following RAS configuration options:
- Authentication method
Encrypted PPTP connections use the MS-CHAP or EAP-TLS authentication methods.
- Authentication provider
Either Windows 2000 security or an external RADIUS server can verify network clients.
- IP routing
IP routing and IP-based remote access must be active. If the wired network acts as a DHCP server for the wireless clients, DHCP must be active.
- Configure L2TP ports.
Set each L2TP port to accept remote access.
- Configure network filters.
Input and output filters keep the remote-access server from sending and receiving data that does not originate at a VPN client. These filters will reject data to or from unauthorized users, so those intruders will not be able to obtain an Internet connection (or a connection to the wired LAN) through the wireless network.
- Configure remote-access policies.
Set the remote-access permission for each VPN client to allow access to the RAS server. The port type must be set to the correct VPN protocol (for example, PPTP or L2TP), and the profile for each connection must include the type of encryption in use. Windows offers three encryption strength options:
- Basic
Uses a 40-bit encryption key
- Strong
Uses a 56-bit encryption key
- Strongest
Uses a 128-bit encryption key
All of the BSD variations (including FreeBSD, NetBSD, OpenBSD, and Mac OS X) include an IPsec VPN client and server as part of the release package.
Linux FreeS/WAN is the most popular implementation of IPsec for Linux. Go to http://www.freeswan.org/ for downloads, documentation, and access to the community of FreeS/WAN users.
OpenVPN is an SSL-based VPN solution for Linux, BSD, OS X, and Windows. OpenVPN is easy to configure and offers both routed VPN (traffic to specific destinations is sent through the VPN) and tunneled virtual interfaces (emulating a physical layer Ethernet device, which can pass non-IP traffic through the VPN). OpenVPN can be found at http://openvpn.net/.
If you're using a Linux firewall, you might want to consider VPN Masquerade. Linux uses the IP Masquerade function in the Linux kernel to share a single connection to the Internet among multiple clients. VPN Masquerade is the section of IP Masquerade that supports IPsec clients. The HOWTO for Linux VPN Masquerade is at http://tldp.org/HOWTO/VPNMasquerade-HOWTO.html.
A dedicated computer running Linux or one of the BSD versions of Unix can be an inexpensive VPN server. Or if you're using a Windows server for other purposes, a dedicated computer can also provide VPN support at little or no additional cost. But a full-size network server is often a bigger and more complicated solution to a relatively simple problem. They're not always the best choice. Many switches, routers, gateways, and firewall devices also include VPN support. Cisco, 3COM, Intel, and many other manufacturers make VPN products that are often easier to install and maintain than a separate computer.
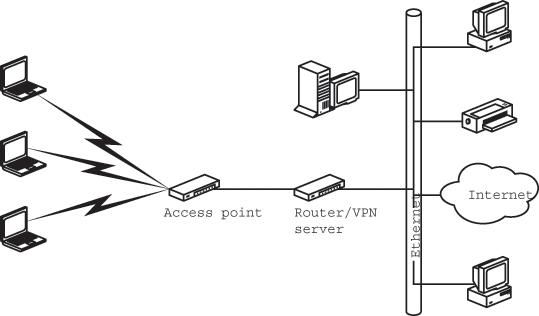
In a wireless network, the VPN server does not need all the same bells and whistles as a server in a larger corporate network. As Figure 13-5 shows, a router located between the wireless access point and the wired portion of an enterprise network can easily double as a VPN server. In a home network, the VPN server can operate between the access point and a DSL or cable modem.
Stand-alone VPN client hardware that sits between the computer and the network is also available, but this setup isn't as practical in a wireless network because the wireless network adapter is almost always plugged directly into the computer itself.
A wireless client connects to a VPN server through its wireless Ethernet link to the network access point, which the operating system sees as a LAN connection. To set up a VPN tunnel through that connection, you must install the tunneling protocol as a network service.
Windows XP and Vista include support for virtual private networks, but this support is not part of the default installation, so the first step in setting up a VPN client is to install the protocol.
In Windows XP and Windows Vista, a wizard makes the whole process easy. In XP, follow these steps to set up a VPN connection:
From the Control Panel, open Network Connections.
Double-click the New Connection Wizard icon.
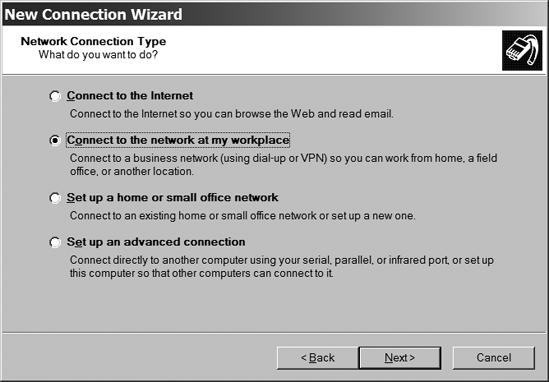
When the Network Connection Type window, shown in Figure 13-6, appears, select the Connect to the network at my workplace option and click the Next button.
Figure 13-6. The option for creating a VPN link specifies connecting to a workplace network, but this option also applies to a wireless VPN.
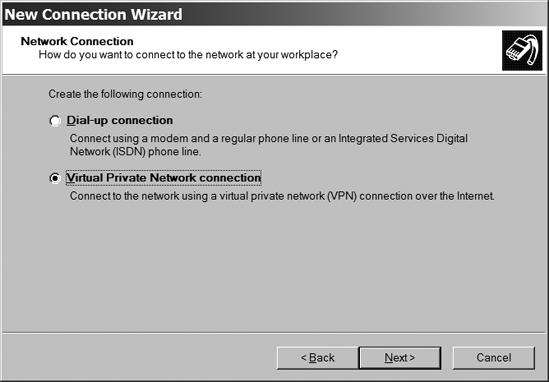
In the Network Connection window (shown in Figure 13-7), select the Virtual Private Network connection option and click the Next button.
In the Connection Name window, type a name for the wireless VPN connection. This name will appear on desktop shortcuts to this connection. Click the Next button.
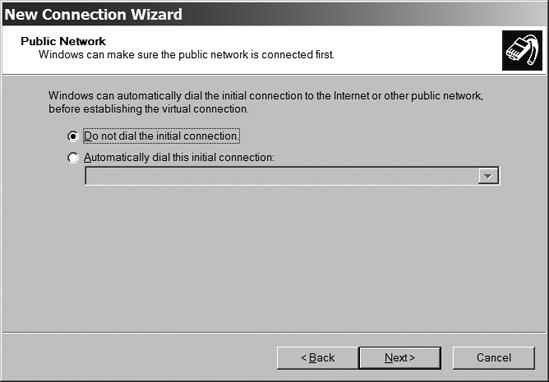
In the Public Network window (shown in Figure 13-8), select the Do not dial the initial connection option because you don't need to connect through a telephone line. Click the Next button.
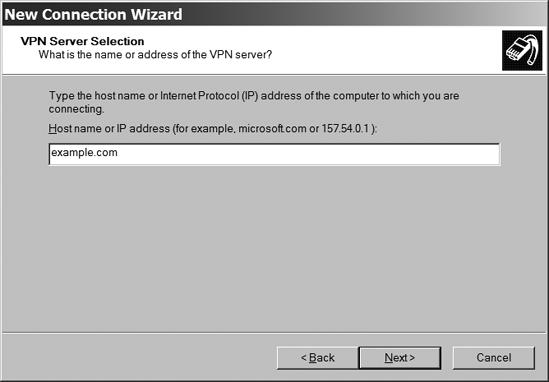
In the VPN Server Selection window, shown in Figure 13-9, type the host name or IP address of the VPN server.
Figure 13-9. The host name or IP address identifies the VPN server at the other end of the wireless link.
Click the Next button and then the Finish button to complete the wizard.
In Vista, follow these steps:
Open the Control Panel.
Select the Network and Sharing Center.
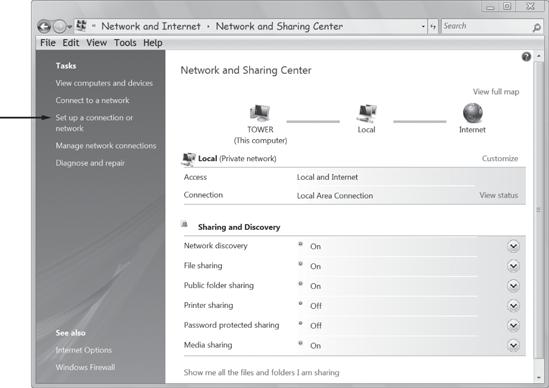
In the Tasks list on the left side of the Network and Sharing Center, shown in Figure 13-10, select the Set up a connection or network option. A Choose a Connection Option window will open.
Select the Connect to a workplace option and click the Next button. The wizard will ask if you want to use an existing connection.
Select the No, create a new connection option. The wizard will ask if you want to use a VPN or a dial-up connection.
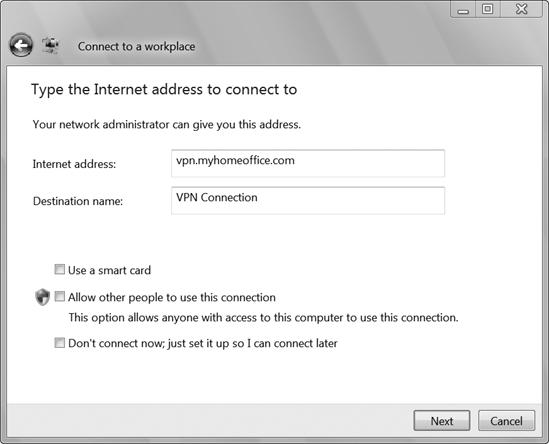
Select the Internet connection (VPN) option. The wizard will then ask for details in the screen shown in Figure 13-11.
Type the VPN server's address provided by the network manager in the Internet address field. This can be either a numeric address or a name.
Type the name you want to use on your own computer for this VPN connection in the Destination name field.
If you want to test the connection, click the Next button. If you don't want to connect, select the Don't connect now option and then click Next. The wizard will ask for your name and password.
Type the name and password you use for this VPN account. If you want your computer to automatically send your password, turn on the Remember this password option. Click the Create button to establish the VPN connection and close the wizard.
To create a shortcut to a VPN on your desktop in Windows, follow these steps:
In XP, open the Control Panel and select Network Connections. In Vista, open the Control Panel, select the Network and Sharing Center, and select Manage Network Connections from the Tasks list.
From the Network Connections window, right-click the icon or listing for the VPN and select Create Shortcut from the pop-up menu.
A pop-up window will ask if you want to place the shortcut on the desktop. Click the Yes button. A shortcut will now appear on the desktop.
Microsoft includes a client for L2TP connections with Internet Protocol security (IPsec) in Windows 2000, Windows XP, and Windows Vista. A similar client program for Windows 98, Windows Me, and Windows NT Workstation 4.0 is available for free download from http://download.microsoft.com/download/win98/Install/1.0/W9XNT4Me/EN-US/msl2tp.exe.
When the VPN connection profile is in place, it's easy to connect a Windows client to the host LAN or the Internet through the wireless VPN link: Just double-click the icon for the connection profile. Windows will ask for a login and password and then make the connection.
If you mostly use your wireless connection to connect to the Internet, you can make it the default connection, which will open whenever you run a network application such as a web browser or email client program. To make the VPN profile the default, follow these steps:
Open the Internet Properties window from the Control Panel.
Select the Connections tab.
In the Dial-Up Settings section, select the VPN connection profile from the list, and click the Set Default button.
Click the Settings button. In the Dial-Up Settings section, type your login and password on the VPN server.
Select the Dial whenever a network connection is not present option.
Windows XP and Windows Vista offer many VPN options that were not available in earlier versions of Windows. To set these options, follow these steps:
Choose the Network Connections window from the Control Panel. If you have a shortcut to your VPN connection on the desktop, you can skip this step.
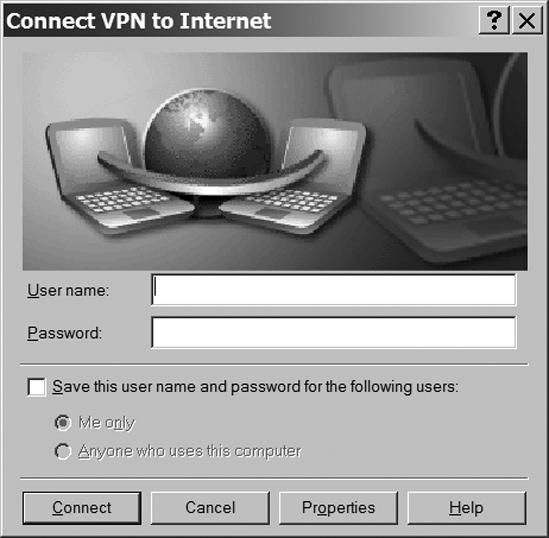
Double-click the VPN icon. A Connect VPN to Internet window, like the one in Figure 13-12, will appear.
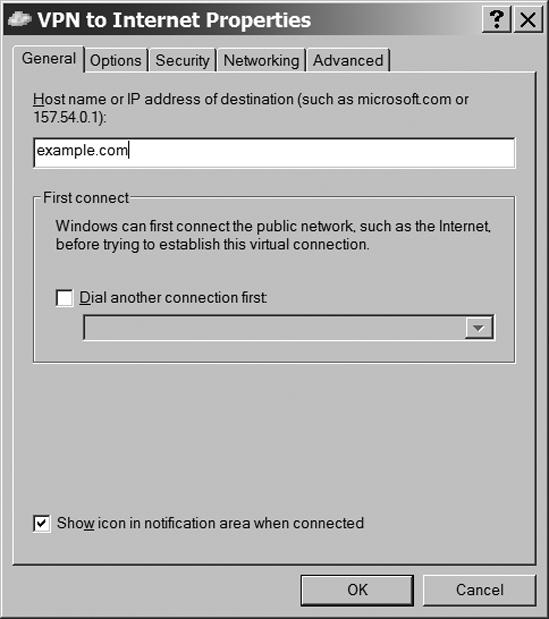
Click the Properties button. The Properties window for your VPN client will appear. Figure 13-13 shows the General tab of the VPN to Internet Properties window.
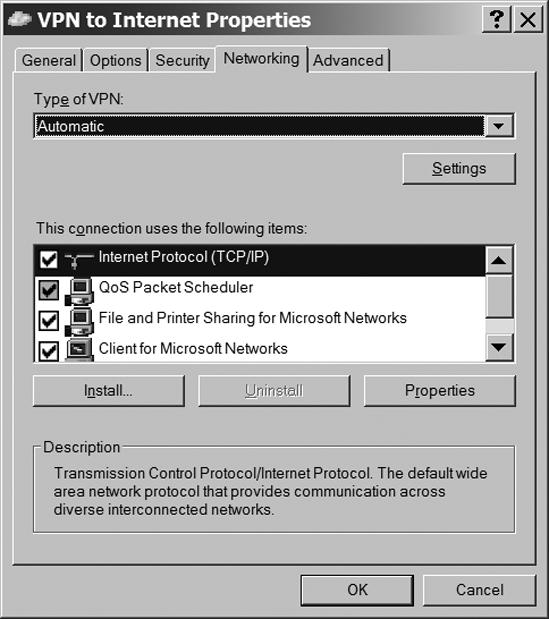
The IP address of the VPN server should already be visible in the Host name or IP address of destination field. The Dial another connection first option should be disabled. Click the Networking tab to view the dialog shown in Figure 13-14.
Select the type of VPN server your network will use from the Type of VPN menu. If you don't know the VPN type, select the Automatic option.
Select Internet Protocol (TCP/IP) or Internet Protocol Version 4 from the list of connection items, and click the Properties button to change the network settings, including the use of a DHCP server or manual settings for IP address and DNS.
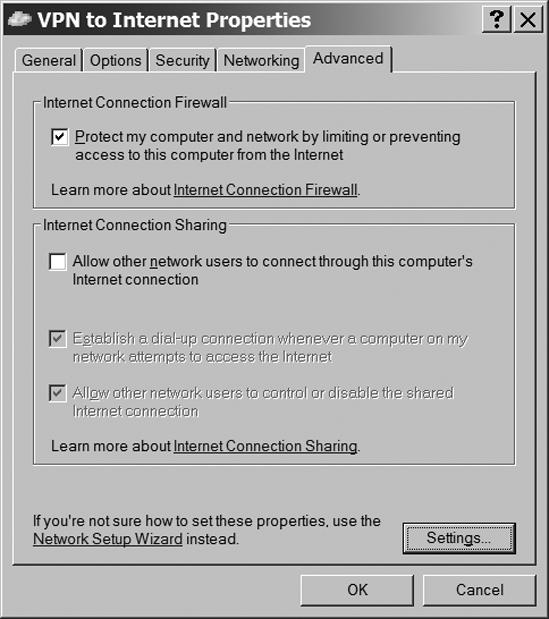
Click the Advanced tab to open the dialog shown in Figure 13-15. If your network is not already protected by a firewall, select the Internet Connection Firewall option. This will protect the wireless client from attacks coming through the Internet.
The Options and Security tabs in the VPN to Internet Properties window control connection options that normally don't change from the default settings. Network managers who want to change the security settings should instruct their users on how to configure these options to comply with the network's specific requirements.
Using a VPN client on a computer running Unix is more complicated than running a VPN from a Windows machine because the client is not integrated into the kernel. Therefore, you must find a client program that works with the version of Unix and the VPN protocol you're trying to use. No single program offers a universal VPN client, and some combinations, such as PPTP on BSD Unix versions, don't seem to exist at all.
Linux users, however, can choose from several IPsec implementations:
| FreeS/WAN http://www.freeswan.org/ |
| pipsec http://perso.enst.fr/~beyssac/pipsec |
| NIST Cerberus http://w3.antd.nist.gov/tools/cerberus/ |
IPsec is included in the OpenBSD distribution. You can find a tutorial that explains how to use it at http://tutorials.papamike.ca/pub/obsd_ipsec.html.
The IPsec implementation for FreeBSD is at http://www.r4k.net/ipsec/. For information about NetBSD IPsec, take a look at http://www.netbsd.org/Documentation/network/ipsec/.
OpenVPN (http://openvpn.net/) is an open source VPN that does not use IPSec. It can operate on Windows, Mac OS X, Linux, and Unix. It's designed for ease of use and security, even through noisy or otherwise unreliable networks.
When you connect your laptop to your corporate LAN through a public network at an airport or in a conference center, or if you're using a broadband wireless service, you can connect through that network to the Internet and onward to your corporate VPN server. Because you'll have to log in to the public network before you initiate the VPN connection, you should create a separate VPN via Public Network connection profile in addition to the one you use from your own office. The profile should point to your corporate VPN server, but it should not be your default connection.
To connect through a public network on a computer running Windows, follow these steps:
Turn on the computer with the wireless network adapter in place.
Use your wireless configuration utility to select the public network you want to use.
Start Internet Explorer, Netscape Navigator, or another web browser. You will see the public network's login screen.
If the computer doesn't do it automatically, type your account name and password. The public network will acknowledge your login.
Minimize the browser window and open the Network Connections window or find the VPN shortcut on your desktop.
Double-click the icon for your VPN via Public Network profile. The computer will connect through the Internet to your corporate LAN.
Type the login and password for your corporate network.
VPNs are an important part of many networks' security plans for off-site users. With just a few keystrokes or mouse clicks, you can establish access to your network resources from anywhere with an Internet connection. If any Internet technique can eliminate the apparent distance between you and your LAN, your office, and your colleagues without sacrificing security, a virtual private network is that technique.