Wireless networks are not secure. They are safe enough for many users most of the time, but it's just not possible to make a network that uses radio to exchange data absolutely private.
Wireless networks are a trade-off between security and convenience. The obvious benefits of a wireless network connection—fast and easy access to the network from a portable computer or an isolated location—come at a cost. For most users, the convenience of wireless operation outweighs the possible security threats. But just as you lock the doors of your car when you park it on the street, you should take similar steps to protect your network and your data.
The simple truth is that a wireless network uses radio signals with a well-defined set of characteristics, so somebody who wants to dedicate enough time and effort to monitoring those signals can probably find a way to intercept and read the data contained in them. If you send confidential information through a wireless link, an eavesdropper can copy them. Credit card numbers, account passwords, and other personal information are all vulnerable.
An entire catalog of tools for cracking Wi-Fi encryption methods is easy to find on the Internet. Although 3G broadband and WiMAX networks might be more secure than Wi-Fi (primarily because capturing data from them is more difficult), and WPA encryption is better than WEP encryption, no wireless security is perfect. Encryption and other security methods can make data a little more difficult to steal, but these methods don't provide complete protection against a really dedicated snoop. As any police officer will tell you, locks are great for keeping out honest people, but serious thieves know how to get past them.
To make things even more dangerous, many network managers and home wireless users leave the doors and windows to their networks wide open to intruders by failing to use encryption and the other security features that are built into every Wi-Fi access point and network node. "Drive-by logins" to unprotected private networks are possible in many urban and suburban business districts and in a surprising number of residential neighborhoods.
Most people have gotten the message about using encryption on their home and office networks, but too many of them are still using the older WEP encryption system rather than the much more secure WPA method. The technical support people at one major telephone company, Qwest, were still advising their DSL customers to use WEP encryption as late as mid-2007.
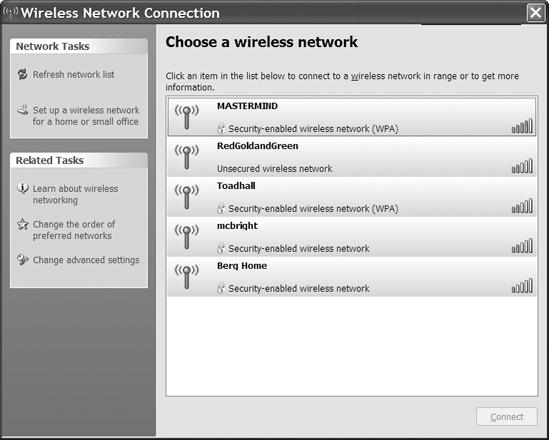
If you're located in a city center or a suburb, you can probably see this for yourself. When you use your Wi-Fi control program to scan the networks in your neighborhood, you will probably see a list of nearby networks in addition to your own access point. The control program will also tell you what kind of encryption (if any) each network is using. In the example shown in Figure 13-16, one network (RedGoldandGreen) is wide open, and four others are encrypted; two of the encrypted networks use WPA, and the two that are listed as "security-enabled" without an encryption type use WEP.
Figure 13-16. Four of the networks in this neighborhood require an encryption key before they will connect.
Do the math: Your access point can reach 150 feet or more in all directions, so the signal probably extends beyond your own property lines (or the walls of your apartment or office). A network device in the building next door or across the street can probably detect your network. If you don't take some precautions to prevent it, your neighbor, or somebody using a laptop or PDA inside a car parked on the street, can log in to your LAN, steal files from your servers, and tie up your Internet connection with streaming videos, multiplayer games, or worse.
It's important to understand that we're talking about two different kinds of security threats. The first is the danger of an outsider connecting to your network without your knowledge or permission; the second is the possibility that a dedicated eavesdropper can steal or modify data as you send and receive it. Each represents a different potential problem, and each requires a different approach to prevention and protection. While it's certainly true that none of the encryption tools currently available can provide complete protection, they can make life more difficult for most casual intruders. And as long as the tools are out there, you might as well use them.
An unsecured wireless network presents many opportunities to an attacker. Not only are the network crackers able to monitor any data that moves through the network, but they might also be able to modify that data. If, for example, your web browser has a vulnerability, an attacker can replace images as you view them with an image that exploits that vulnerability and installs a Trojan horse program on your computer, allowing the attacker to steal data stored on the computer, even if you never sent that data over the wireless network. This type of attack might be relatively rare (casual snoopers are unlikely to take the time to snoop around on the chance you have something interesting), but it still presents a real risk.
Also, many popular websites encrypt the login page with SSL encryption via HTTPS, but they don't encrypt subsequent pages to reduce the drain on processing power—your password might be secure, but any email you read via the web mail interface might not be, and attackers might be able to steal the cookie (a unique piece of data passed with web data) that identifies your login and open your mailbox directly.
As the operator of a Wi-Fi network, what can you do to keep outsiders out? You can employ a few techniques that can discourage them. First, you can accept the fact that wireless networks are not completely secure and use the built-in network security features to slow down would-be intruders; second, you can supplement your wireless router's built-in tools with a hardware or software firewall (or both) to isolate the wireless network; and third, you can use additional encryption such as a VPN to secure traffic to the network.
The security features of the early Wi-Fi protocols (WEP encryption) were not adequate to protect data. The wireless equivalent privacy (WEP) protocol had several serious flaws: The basic encryption method (the RC4 algorithm) was known to have weaknesses in certain applications, all users had to know the key, and no secure mechanisms for distributing new keys existed. Most of these shortcomings were acknowledged and dismissed as being outside the scope of providing the same protection that a user on a standard wired network would receive, but in fact, they meant that wireless equivalent privacy was little better than no protection at all. Recent attacks (such as those performed by the aircrack-ptw tool) have further undermined WEP because these tools have often been able to disclose an encryption key in a matter of minutes by analyzing a limited amount of traffic. With these developments, WEP should be treated more as a "do not disturb" sign than as a real means of protection.
The WPA and WPA2 standards attempt to fix the shortcomings of WEP, but they only work when all of the users of your network have modern cards and drivers. Most, if not all, network interfaces made in the last few years support WPA or WPA2.
For most of us, the more serious danger is not that people will eavesdrop on our messages but that they will create their own connection to your network and either read files stored on computers on the LAN or use your broadband connection to the Internet without your knowledge.
However, business networks must take extra precautions to protect their (and their customers') data. Several high-profile compromises of customer credit card data in major store chains have been traced to inadequate network protection.
Maintaining control of your network and keeping it secure is essential. "Wi-Fi Security" in Wi-Fi Security includes a list of specific actions you can use to keep intruders out of your wireless network.
The security tools in the Wi-Fi specifications aren't perfect, but they're better than nothing. Even if you choose not to use them, it's essential to understand what they are and how they work, if only to turn them off.
Every wireless network has a name. In a network with just one access point, the name is the basic service set ID (BSSID). When the network has more than one access point, the name becomes the extended service set ID (ESSID), but your computer's control program displays both types in the same list. The generic designation for all network names is the service set ID (SSID), which is the term you will see most often in wireless access point and client configuration utility programs.
When you configure the access points for a network, you must specify the SSID for that network. Every access point and network client in a network must use the same SSID. When a network client detects two or more access points with the same SSID, it assumes that they are all part of the same network (even if the access points are operating on different radio channels), and the client associates with the access point that provides the strongest or cleanest signal. If that signal deteriorates due to interference or fading, the client will try to shift to another access point on what it thinks is the same network. This transfer is called a handoff.
If two different networks with overlapping signals have the same name, a client will assume that they're both part of a single network, and it might try to perform a handoff from one network to the other. From the user's point of view, this misdirected handoff will look like the network has completely dropped its connection. Therefore, every wireless network that could possibly overlap with another network must have a unique SSID.
The exceptions to the unique SSID rule are public and community networks that only provide access to the Internet but not to other computers or other devices on a LAN. Those networks often have a common SSID, so subscribers can detect and connect to them from more than one location. In other words, if you have an Internet access account at your local coffee shop, you might find and use exactly the same SSID when you visit another shop owned by the same company.
A network's SSID provides a very limited form of access control because it's necessary to specify the SSID when you set up a wireless connection. The SSID option in an access point is always a text field that will accept any name you care to assign, but many network configuration programs (including the wireless network tools in Windows XP and those supplied with several major brands of network adapters) automatically detect and display the SSIDs of every active network within their signal range.
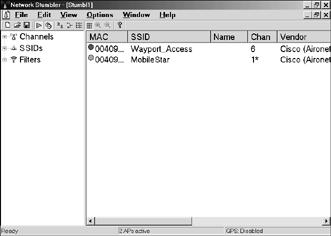
It's not always necessary to know the SSID of a network before you try to connect; the configuration utility (or a network monitor or sniffer program like Network Stumbler) will show you the names of every nearby network in a list or a menu (the exceptions are networks in which the broadcast SSID feature has been turned off). For example, Figure 13-17 shows the result of a Network Stumbler scan at Seattle-Tacoma Airport, where Wayport served the passenger terminal and MobileStar provided coverage in the American Airlines VIP club.
Warning
Every access point comes with a default SSID setting and password. These defaults are well known and documented within the community of network snoops (run a web search for default SSID to find several lists). Obviously, the defaults should never be used in any active network. Make sure you change the access point's administrative login and password while you're at it.
Figure 13-17. Network Stumbler and many configuration utilities display the SSIDs of every nearby wireless network.
Normally, most Wi-Fi access points send out beacon signals that broadcast the network's SSID. When a network adapter performs a radio scan, it detects those beacon signals and displays a list of nearby SSIDs in its control program. However, you can disable the SSID broadcast so the network doesn't show up on most control program scans. To connect a computer to a network whose name is not visible, you must instruct your control program to search for the SSID.
A nonbroadcast SSID is not completely invisible. A sniffer program (such as Network Stumbler) can still detect it and display the SSID, and every time a user connects to the network, the network adapter sends the SSID in a packet that can be easily sniffed. Disabling the SSID broadcast might, in some cases, make it easier for an attacker to later attack the laptop of one of your users (this is a more serious issue for businesses or corporate network administrators than for people running home networks). Because the laptop cannot know if the hidden network is available, it must constantly probe for the network, announcing its presence and giving an attacker much of the information needed to spoof the hidden network. Because a hidden network must be in a laptop's Preferred Networks list, the laptop will automatically connect to the spoofed network.
WEP encryption is an option in every Wi-Fi system, so it's important to know how it works, even if you choose not to use it. As the name suggests, the original intent of the wired equivalent privacy (WEP) protocol was to provide a level of security on wireless networks that was comparable to the security of a wired network. That was the goal, but a network that depends on WEP encryption is almost as vulnerable to intrusion as a network with no protection at all. WEP will keep out the casual snoops (and your freeloading neighbors, if they're not particularly adept at cracking encryption), but WEP is not particularly effective against a dedicated intruder. The more recent WPA encryption is always the better choice.
WEP encryption is intended to serve three functions: It prevents unauthorized access to the network; it performs an integrity check on each packet; and it protects the data from eavesdroppers. WEP uses a secret encryption key to encode data packets before a network client or an access point transmits them, and it uses the same key to decode packets after it receives them. The original standard used shared authentication, in which the access point sends a challenge packet that a client must encrypt with the proper WEP key and send back. However, this opens a significant vulnerability by allowing a snooper to watch both parts of the exchange and derive the key.
The "open" authentication method, which should be used by any network using WEP (not that any network should use WEP), simply discards packets that cannot be decrypted by the network's WEP key. Therefore, the WEP settings must be exactly the same on every access point and client adapter in the network. This sounds simple enough, but it can get confusing because manufacturers use different methods to identify the size and format of a WEP key. The functions don't change from one brand to another, but identical settings don't always have identical descriptions.
A WEP key can have either 64 bits or 128 bits. Although 128-bit keys are more difficult to crack (but they are still pretty insecure), they also increase the amount of time needed to transmit each packet. However, confusion arises because a 40-bit WEP key is the same as a 64-bit WEP key, and a 104-bit key is the same as a 128-bit key. The standard 64-bit WEP key is a string that includes an internally generated 24-bit initialization vector and a 40-bit secret key assigned by the network manager. Some manufacturers' specifications and configuration programs call this 64-bit encryption, but others describe it as 40-bit encryption. Either way, the encryption scheme is the same, so an adapter that uses 40-bit encryption is fully compatible with an access point or another adapter that uses 64-bit encryption.
Many network adapters and access points also include a strong encryption option that uses a 128-bit key. Devices that support strong encryption are downward compatible with 64-bit encryption, but compatibility is not automatic, so all of the devices on a mixed network of 128-bit and 64-bit devices will operate at 64 bits. If your access point and all of your adapters accept 128-bit encryption, use a 128-bit key. But if you want your network to be compatible with adapters and access points that only recognize 64-bit encryption, set the entire network to use 64-bit keys.
In practice, the choice of 64- or 128-bit WEP encryption doesn't make much difference. Tools are easily available that can crack both types, although cracking a 128-bit key might take a bit longer.
The length of the key is not the only confusing thing about setting WEP encryption. Some programs request the key as a string of ASCII characters, but many others want the key in hexadecimal (hex) numbers. Still others can generate the key from an optional passphrase.
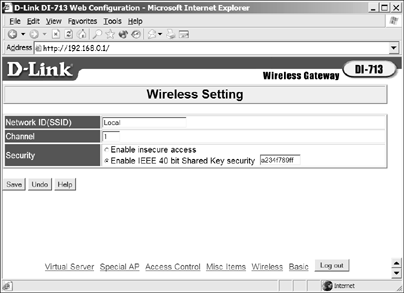
Each ASCII character has 8 bits, so a 40-bit (or 64-bit) WEP key contains 5 characters, and a 104-bit (or 128-bit) key has 13 characters. In hex, each character uses 4 bits, so a 40-bit key has 10 hex characters, and a 128-bit key has 26 characters. In Figure 13-18, the Wireless Setting screen for a D-Link access point, the 40-bit Shared Key Security field uses hex characters, so it has space for 10 characters. The D-Link program runs all 10 characters together in a single string, but some others split them into 5 sets of 2 digits or 2 sets of 5. The key looks the same to the computer either way, but copying the string when it's broken apart is easier.
A passphrase is a string of text that the adapters and access points automatically convert to a string of hex characters. Because humans can generally remember actual words or phrases more easily than hex gibberish, a passphrase can be easier to distribute than a hex string. However, a passphrase is only useful when all the adapters and access points in a network come from the same manufacturer.
Like just about everything else in a Wi-Fi configuration utility, the names of the encryption options are not consistent from one program to the next. Some programs use a straightforward set of options such as "enable WEP (or WPA) encryption," but others use technical language taken from the formal 802.11 specification.
Some access points also offer a shared key authentication option that uses encryption when a network client has the key but uses unencrypted data with other network nodes.
Setting up a mixed network becomes more complicated when some network nodes use hex only and others require ASCII keys. If that's the situation on your network, you will want to follow these rules for setting the encryption keys:
Convert all your ASCII keys to hex. If a configuration program demands an ASCII key, enter the characters 0x (zero followed by lowercase letter x), followed by the hex string. If you're using Apple's AirPort software, you'll have to enter a dollar sign ($) at the beginning of a hex key.
Make sure all your encryption keys have exactly the right number of characters.
If all else fails, read the security sections of the manuals for your network adapters and access points. It's possible that one or more of the devices in your network might have some obscure proprietary feature that you don't know about.
WPA encryption was developed as a partial solution to the security problems that make WEP encryption less than totally secure. WPA is much safer than WEP, but cracking WPA is still possible.
WPA is more secure because it uses a method called Temporal Key Integrity Protocol (TKIP) to automatically change the encryption key after a specified period of time or after the system exchanges a specific number of packets. Because WPA changes the key frequently, it's a lot more difficult for a cracker to gather enough information to decipher its encryption code.
In large networks, WPA uses an authentication server to verify the identity of each network user. The server uses Remote Authentication Dial-in User Service (RADIUS) and Extensible Authentication Protocol (EAP) to exchange encryption keys with the computers and other devices that are connected to the wireless network.
In home networks and smaller business networks that don't have a server, a method called pre-shared key (PSK) mode uses a passphrase stored in the access point in place of the authentication server. To connect to the network, users must enter the same passphrase on their computer or other network device (or set their device to automatically enter the passphrase). When you set up WPA encryption, you must specify whether the network uses a server or PSK mode.
Any access point and network adapter that supports 802.11g or 802.11n should also recognize WPA encryption. If you're using an older 802.11b or 802.11a access point, you might be able to add WPA encryption by installing the latest version of firmware and drivers. Look in the support or downloads section of the manufacturer's website for free upgrade instructions and software.
A WPA-PSK passphrase can be a string of either 8 to 63 ASCII characters or 64 hexadecimal digits. The passphrase that you enter into a network device must be exactly the same as the one stored in the access point. Obviously, typing 64 digits correctly is not something that you want to do frequently, so the ASCII alternative is the better choice for most users. For optimal security, the ASCII passphrase you assign to your network should be a random mixture of at least 20 characters including letters (capitals and lowercase), numbers, and punctuation marks.
A PSK network uses the passphrase to set up the initial connection between a client (such as a computer or PDA) and the access point. After the connection is in place, the TKIP assigns new encryption keys to every packet or group of packets. The PSK combines with your network SSID to calculate the final key value. Choosing a unique SSID and a strong passphrase is important.
Attackers can build large tables of SSID and PSK pairs for common network names and dictionary words, performing weeks of calculation once with the payoff of nearly instantly determining the key of any network that matches that pair of values. Choosing strong passphrases and unique SSIDs can mitigate this attack.
When you set up a new network, the security section of the access point's configuration software will ask if you want to use encryption, and if so, whether you want WEP or WPA encryption. Unless you're planning to run an open access network, you should choose WPA.
In many cases, the access point will offer two or more types of WPA encryption. If your network includes a RADIUS server, choose EAP. If the network has no encryption server, use the WPA-TKIP option.
For a network user, providing a WPA key is just as easy as providing a WEP key. Most network adapters made in the last couple of years automatically recognize the type of encryption embedded in each Wi-Fi signal that they detect, so the control program might ask for an encryption key without specifying whether it's a WEP key or a WPA key.
It was probably inevitable that somebody would take the added security features in WPA encryption as a challenge and develop a WPA cracking tool.
Several such tools are out there, so WPA does not provide the impenetrable protection that some of its proponents might want you to believe. In particular, programs called coWPAtty and Aircrack-ng both use dictionary attacks on WPA-TKIP networks to try thousands or millions of possible keys until they find the correct one. Fortunately, neither of these programs nor any of the others aimed at cracking WPA encryption are easy to use, and cracking a network can take a lot of time, so successful attacks on WPA are not particularly common. This technique takes time because the programs can only try about 50 different encryption keys per second, but eventually they will find the right passphrase and connect to the target network. Because each additional letter, number, or other character in a key increases the key's complexity, a long key takes much longer to crack than a short one. However, a commercial product called Elcomsoft Distributed Password Recovery uses graphics processors on video cards to "break Wi-Fi encryption up to 100 times faster than by using CPU only," so even a relatively long key is not that secure.
Completely protecting yourself against attacks might not be possible or practical, but a long passphrase that includes random numbers and punctuation marks is still a better choice than a string of words or numbers alone. In other words, something like hdt%mzx33wolf$fgilxxq&#smedbxor is a better passphrase than nostarchpressbooks. But the only truly secure way to use Wi-Fi is to combine it with VPN encryption.
Most access points include an option that permits the network manager to restrict access to a specific list of client adapters. If a network device with a MAC address that does not appear on the list of authorized users tries to connect, the access point will not accept the request to associate with the network. This option can keep intruders from connecting to a wireless LAN, but it forces the network administrator to keep a complete list of users' adapters and their MAC address. Every time a new user wants to join the network, and every time an established user swaps adapters or gets a new laptop, PDA, or other device with a built-in adapter, the network manager must add one more MAC address to the list. This task is probably manageable in a home or small office network, but it could be a major undertaking for a larger corporate or campus-wide system, if it's practical at all.
MAC authentication does not provide unbreakable protection against unauthorized users because a determined cracker could monitor radio signals from approved users, intercept their adapters' MAC addresses, and load an approved address onto a different adapter. But combined with encryption and other security tools, authentication adds one more impediment in the path of a network cracker.
Every access point configuration utility uses a different format for its access lists. The manual and online documentation supplied with your access point should provide detailed instructions for creating and maintaining an access control list.
The Wi-Fi standards do not specify a maximum size for an access point's access control list, so the numbers are all over the map. Some access points limit the list to a few dozen entries, but others, such as the Proxim Harmony AP Controller, will support as many as 10,000 separate addresses. Still others accept an effectively unlimited number. If you plan to use a list of addresses to control access to your network, make sure your access point will work with a large enough list to support all of your users, with enough expansion space for future growth. As a rule of thumb, the access point should accept at least twice as many MAC addresses as the number of users on your network today.
Some access points also include a MAC address exclusion feature that allows the network manager to block one or more MAC addresses from access to the network.