Several software programs can gather and display useful information when you're trying to understand what's happening inside your network. These programs are available as free or trial downloads, so you don't incur a cost when testing them.
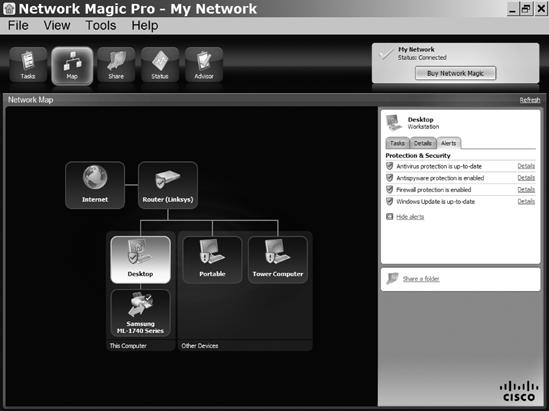
Network Magic (http://www.networkmagic.com/) provides a graphic display of the devices connected to a LAN, as shown in Figure 17-2, and a central control point for adding new network devices or changing the existing network configuration. It can also perform some basic troubleshooting tests and automatic repairs.
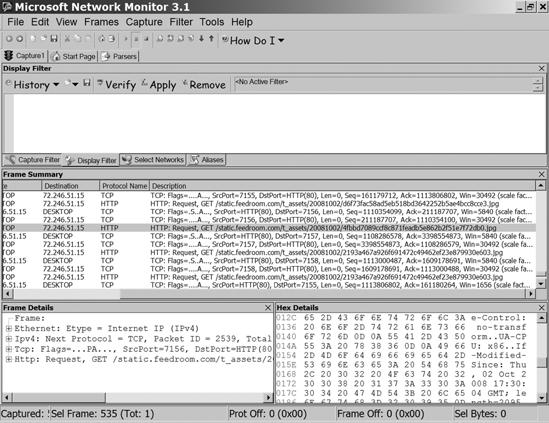
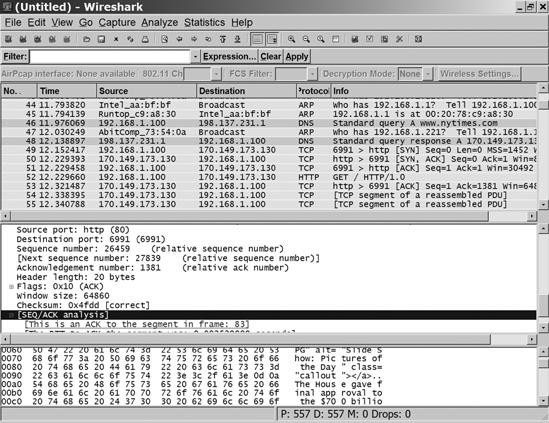
Microsoft Network Monitor (go to http://www.microsoft.com/downloads/ and search for Network Monitor) and Wireshark (http://www.wireshark.org/) are free protocol analyzers that capture and display data as it moves through your network. In other words, they grab each block of data (a frame) as it passes in or out of your computer, and they display the contents of the frame along with detailed information about the form and structure of each frame. Figure 17-3 shows a data capture in Network Monitor, and Figure 17-4 shows a Wireshark screen. The two programs capture the same data stream, but they handle and display it differently. The programs are available at no cost, so you might want to install both of them. Protocol analyzers are also known as network sniffers.
Most of this data display looks like hexadecimal gibberish, but it contains the actual text of messages, conversations, and other transactions, along with all the commands and status messages that move through the network. Most of the time, you can allow your computer and the network plumbing to handle the data in background. But when something goes wrong, the data captured by a protocol analyzer can help you identify what's causing the problem.
For example, if the amount of incoming or outgoing traffic moving through your network increases, the network may be sending or receiving many requests every second. This could be a hacker's denial of service attack, or a computer that has innocently latched itself into an endless program loop. Either way, you will want to identify the source and take action to make it stop. When this happened to me, I used Wireshark to find the numeric IP address of the computer that was originating the bogus messages and a whois program to identify that computer's owner; then I sent an email explaining the problem and asking them to fix it. The data stream stopped within an hour.
A network sniffer can also identify a device within your own network that becomes infected or has some other problem that interferes with proper operation. By running the sniffer program on more than one computer, or even inserting a sniffer at a router, a modem connection, or other interface point, you can often isolate the source of a problem.
You won't use a protocol analyzer very often, which is probably okay, because it's a complex and tedious process. But when you need to know what's moving through your network, an analyzer can give you information that you won't find anywhere else.