Chapter 2. Manage Devices and Data
The MD-100 Windows 10 exam focuses on how to manage devices within an enterprise environment, such as a Microsoft 365 subscription. Once you have installed or upgraded devices with Windows 10, you need to understand how to join devices to Azure Active Directory.
Users need to access data stored on file servers, NAS drives, and on other PCs. Also, you need to know how to manage and protect data by using file-and folder-level data protection. You’ll be expected to know how to configure Windows security and use Windows Defender Firewall to safeguard Windows 10.
Skills covered in this chapter:
Skill 2.1: Manage local users, local groups, and devices
In this skill, you will review how to manage local users and local groups on Windows 10 devices. If you have experience of an earlier version of Windows, you might be familiar with configuring local users and local groups as these operations are largely unchanged. Before you use Windows 10 on a device, you must sign in with the credentials for a user account. In an enterprise environment, the device and the user are often used to provide, control, and audit access to resources. Groups may be used for simplifying administration, allowing entities to share a common function or role or require the same set of privileges. You need to understand how local users, local groups, and devices form a key component in Windows security.
Manage local users
A user account is required to log on to a Windows 10 computer, and to secure the device, it should have a password. You need to understand the default user accounts that are created automatically when you install Windows 10 and how to create new user accounts so that users can log on to machines and access resources. In this skill, you will focus on local accounts that are created and operate only on the local device.
Configure local accounts
Local accounts, as the name suggests, exist in the local accounts database on your Windows 10 device; they can only be granted access to local resources and, where granted, exercise administrative rights and privileges on the local computer.
When you first install Windows 10, you are prompted to sign in using a Microsoft account or Work Account, such as a Microsoft 365 account that is connected to Azure Active Directory. If neither of these options are available or are suitable to your requirements, you can choose an offline account and create a local account to sign in. Thereafter, you can create additional local user accounts as your needs dictate.
Default accounts
In Windows 10, there are three default local user accounts on the computer in the trusted identity store. This store is a local list of users and groups and is stored as the Security Accounts Manager (SAM) database in the registry. The three accounts are the Administrator account, Default Account, and Guest account.
The default Administrator account cannot be deleted or locked out, but it can be renamed or disabled. When the default administrator account is enabled, it requires a strong password. Another local account called the HelpAssistant account is created and enabled when a Windows Remote Assistance session is run. The HelpAssistant account provides limited access to the computer to the person who provides remote assistance. The HelpAssistant account is automatically deleted if there are no Remote Assistance requests pending.
When you install Windows 10 using a local account, you can create additional user accounts and give these accounts any name that is valid. To be valid, the username
Must be from 1 to 20 characters
Must be unique among all the other user and group names stored on the computer
Cannot contain any of the following characters: / \ [ ] : ; | = , + ? < > “ ” @
Cannot consist exclusively of periods or spaces
The initial user account created at installation is a member of the local Administrators group and therefore can perform any local management task on the device. You can view the installed accounts, including the default accounts, by using the Computer Management console, as shown in Figure 2-1. If you cannot find the Local Users And Groups section within Computer Management, then you are probably running Windows 10 Home Edition, which does not have the Local Users And Groups Microsoft Management Console (MMC) snap-in.
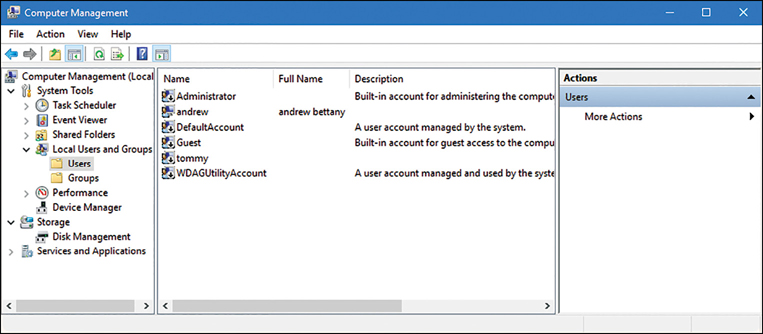
You can also use the net user command-line tool and the get-wmiobject -class win32_useraccount Windows PowerShell cmdlet to list the local user accounts on a device.
![]() Exam Tip
Exam Tip
In Windows 10 Home edition, you must use the User Accounts applet in Control Panel, and you cannot create or manage groups as the Local Users And Groups Console snap-in is not present.
Managing local user accounts
You can manage local user accounts by using Computer Management (except with Windows 10 Home edition), Control Panel, the Settings app, and Windows PowerShell.
Using Computer Management
To manage user accounts by using Computer Management, right-click Start and then click Computer Management. Expand the Local Users And Groups node and then click Users. To create a new user, right-click the Users node and click New User.
In the New User dialog box, configure the following properties, as shown in Figure 2-2, and then click Create.

User Name
Full Name
Password
User Must Change Password At Next Logon
User Cannot Change Password
Password Never Expires
Account Is Disabled
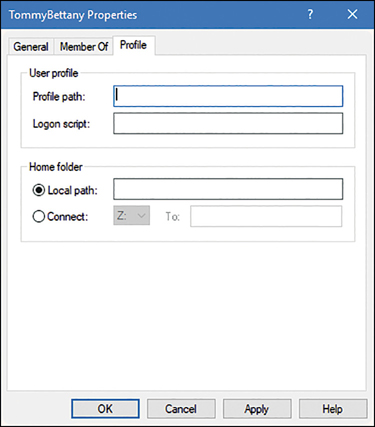
After you have added the new user account, you can modify more advanced properties by double-clicking the user account. On the General tab, you can change the user’s full name and description and password-related options. On the Member Of tab, you can add the user to groups or remove the user from groups. The Profile tab, shown in Figure 2-3, enables you to modify the following properties:
Profile Path This is the path to the location of a user’s desktop profile. The profile stores the user’s desktop settings, such as color scheme, desktop wallpaper, and app settings (including the settings stored for the user in the registry). By default, each user who signs in has a profile folder created automatically in the C:\Users\Username folder. You can define another location here, and you can use a Universal Naming Convention (UNC) name in the form of \\Server\Share\Folder.
Logon Script This is the name of a logon script that processes each time a user signs in. Typically, this will be a .bat or .cmd file. You might place commands to map network drives or load apps in this script file. It is not usual to assign logon scripts in this way. Instead, Group Policy Objects (GPOs) are used to assign logon and startup scripts for domain user accounts.
Home Folder This is a personal storage area where users can save their personal documents. By default, users are assigned subfolders within the C:\Users\Username folder for this purpose. However, you can use either of the following two properties to specify an alternate location:
Local Path A local file system path for storage of the user’s personal files. This is entered in the format of a local drive and folder path.
Connect A network location mapped to the specified drive letter. This is entered in the format of a UNC name.
Using Control Panel
You can manage user accounts from Control Panel by opening Control Panel, clicking User Accounts, and then clicking User Accounts again. From here, you can:
Make Changes To My Account In PC Settings Launches the Settings app to enable you to make user account changes.
Change Your Account Type Enables you to switch between Standard and Administrator account types.
Manage Another Account Enables you to manage other user accounts on this computer.
Change User Account Control Settings Launches the User Account Control Settings dialog box from Control Panel.
If you are an administrator and you select another local user, you can perform these tasks:
Change The Account Name Enables you to change your account name.
Change The Password You can change the password for the user and provide a password hint.
Change Your Account Type Enables you to switch between Standard and Administrator account types.
Delete The Account Allows you to delete the user account and optionally any files associated with their account.
Manage Another Account Enables you to manage other user accounts on this computer.
You cannot add new accounts from the Control Panel. If you want to add a new local account, use Computer Management, Windows PowerShell, or click the Add A New User In PC Settings link to open the Family And Other Users section of the Settings app.
Using the Settings App
The preferred way to manage local accounts in Windows 10 is by using the Settings app. From Settings, click Accounts. As shown in Figure 2-4, on the Your Info tab, you can modify your account settings, including:
Sign In With A Microsoft Account Instead You can sign out and sign in using a Microsoft account.
Create Your Picture You can browse for an image or take a selfie if your device has a webcam.
Create A Microsoft Account You can create a new Microsoft account using this option.
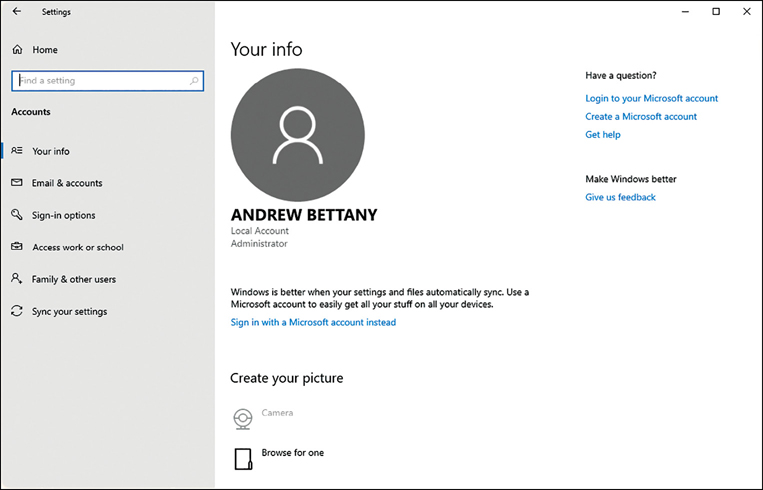
If you need to add a new local user account, click the Family & Other Users section and then click Add Someone Else To This PC.
Windows 10 requires you to then enter that person’s email address, typically the address they use to sign in to Office 365, OneDrive, Skype, Xbox, or Outlook.com.
If you do not have the recipient’s email address, you can still add a local account by using the following procedure:
In the Settings app, click Accounts.
On the Family & Other Users tab, under Other Users, click Add Someone Else To This PC.
In the How Will This Person Sign In dialog box, click I Don’t Have This Person’s Sign-In Information.
In the Create Account dialog box, click Add A User Without A Microsoft Account.
On the Create An Account For This PC page, type the user name, type a new password twice, provide answers to the three security questions, and then click Next to create the local account.
The account is listed under Other Users.
Using Windows Powershell
You can view local user accounts using Windows PowerShell, but to add or modify local accounts, you will need to run the cmdlets with elevated privileges.
You can use the following cmdlets to manage local user accounts.
Get-LocalUser Gets local user accounts
New-LocalUser Creates a local user account
Remove-LocalUser Deletes local user accounts
Rename-LocalUser Renames a local user account
Disable-LocalUser Disables a local user account
Enable-LocalUser Enables a local user account
Set-LocalUser Modifies a local user account
For example, to add a new local user account called User 03 with a password, run the following cmdlets.
$Password = Read-Host -AsSecureString <<Enter Password>> New-LocalUser "User03" -Password $Password -FullName "Third User" -Description "User 3 "
Need More Review? Local Accounts Cmdlets
To review further details about using Windows PowerShell to manage local accounts, refer to the Microsoft PowerShell reference at https://docs.microsoft.com/powershell/module/microsoft.powershell.localaccounts/?view=powershell-5.1
Manage local groups
There are a number of built-in groups with Windows 10, which provide an easy way for users to be granted the same permissions and rights as other group members. Assigning permissions to groups is usually more efficient than applying them to individual users.
You use the Computer Management console, or if you are an administrator, you can create a custom Microsoft Management Console (MMC) and add the Local Users And Groups Snap-in as shown in Figure 2-5 to create and manage local groups.
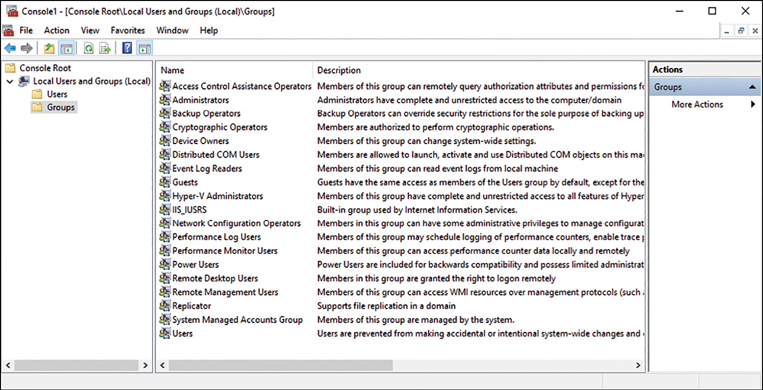
In Figure 2-5, you can see the default built-in local groups (such as Administrators and Device Owners) and a description for each. These built-in groups already have the necessary permissions associated to them to accomplish specific tasks.
If you select the Users or Administrators groups, you should see members that you recognize. Administrators have complete and unrestricted access to the computer, whereas users are unable to make accidental or intentional system-wide changes, but they can run most applications that have already been installed on a device.
Built-In Local Groups
You can add your own groups, change group membership, rename groups, and delete groups. It is best practice to use the built-in groups wherever possible because these already have the appropriate permissions and are familiar to other administrators. Some of the built-in local groups are special groups that Windows 10 system requires (and cannot be managed).
Some of the following local groups that are created on Windows 10 devices together with their uses are shown in Table 2-1.
Table 2-1 Built-in Local Groups
Local Group |
Description |
|---|---|
Access Control Assistance Operators |
Members of this group can remotely query authorization attributes and permissions for resources on the computer. |
Administrators |
The Administrators group has full permissions and privileges on a Windows 10 device. Members can manage all the objects on the computer. The Administrator and initial user accounts are members of the Administrators local group. |
Backup Operators |
Backup Operators group members have permissions to back up and restore the file system regardless of any NTFS permissions. Backup Operators can access the file system only through the Backup utility. |
Cryptographic Operators |
The Cryptographic Operators group has access to perform cryptographic operations on the computer. |
Device Owners |
Members of this group can change system-wide settings to the computer. |
Distributed COM Users |
The Distributed COM Users group can launch and run Distributed COM objects on the computer. |
Event Log Readers |
Event Log Readers group members can read the event log on the local computer. |
Guests |
The Guests group has very limited access to the computer. In most cases, administrators disable guest access because guest access can pose a potential security risk; instead, most administrators prefer to create specific users. By default, the Guest user account is a member of the Guests local group. |
Hyper-V Administrators |
Members of this group have complete and unrestricted access to all features of Hyper-V if this feature has been installed. |
IIS_IUSRS |
The IIS_IUSRS group is used by Internet Information Services (IIS). By default, the NT AUTHORITY\IUSR user account, used by IIS, is a member of the IIS_IUSRS group. |
Network Configuration Operators |
Members of the Network Configuration Operators group can manage the computer’s network configuration. |
Performance Log Users |
The Performance Log Users group can access and schedule logging of performance counters and create and manage trace counters on a device. |
Performance Monitor Users |
The Performance Monitor Users group can access and view performance counter information on a device. Members of this group can access performance counters both locally and remotely. |
Power Users |
The Power Users group is included in Windows 10 for backward compatibility only. Power Users was a group used on computers running Windows XP and granted members limited administrative rights. |
Remote Desktop Users |
The Remote Desktop Users group members can log on remotely using the Remote Desktop service. |
Remote Management Users |
Members of this group can access WMI resources over management protocols (such as WS-Management via the Windows Remote Management service). This applies only to WMI namespaces that grant access to the user. |
Replicator |
The Replicator group supports directory replication, which is a feature used by domain controllers. |
System Managed Accounts Group |
Members of this group are managed by the system. |
Users |
The Users group is used for end users who require very limited system access. On a fresh copy of Windows 10, members of the Users group are unable to compromise the operating system or program files. By default, all users who have been created on a device, except Guest users, are members of the Users local group. |
In Table 2-1, you saw that Administrators group members have full permissions and privileges on a Windows 10 device. A member of the Administrators local group can perform the following tasks:
Access any data on the computer
Assign and manage user rights
Backup and restore all data
Configure audit policies
Configure password policies
Configure services
Create administrative accounts
Create administrative shares
Increase and manage disk quotas
Install and configure hardware device drivers
Install applications that modify the Windows system files
Install the operating system
Install Windows updates, service packs, and hot fixes
Manage disk properties, including formatting hard drives
Manage security logs
Modify groups and accounts that have been created by other users
Modify system wide environment variables
Perform a system restore
Re-enable locked-out and disabled user accounts
Remotely access the Registry
Remotely shut down the system
Stop or start any service
Upgrade the operating system
Create and Delete Groups
Only members of the Administrators group can manage users and groups. When creating a new group, the group name is required to be unique on the local computer and cannot be the same as a local username that exists on the computer.
You should make the group name descriptive, and wherever possible, you should include a description of the new group’s function. Group names can have up to 256 characters in length and include alphanumeric characters including spaces, but the backslash (\) character is not allowed.
To create a new group, follow these steps:
Right-click Start and select Computer Management.
Open the Local Users And Groups console.
Right-click the Groups folder and select New Group from the context menu.
In the New Group dialog box, enter the group name. (Optionally, you can enter a description for this group.)
To add group members, click the Add button.
In the Select Users dialog box, type the username then click OK.
In the New Group dialog box, you will see that the user has been added to the group.
To create the new group, click the Create button.
To delete a group from the Local Users And Groups console in Computer Management, right-click the group name and choose Delete from the context menu. You will see a warning that deleting a group cannot be undone, and you should click the Yes button to confirm the deletion of the group.
When a group is deleted, all permissions assignments that have been specified for the group will be lost.
Special Identity Groups
There are a number of special identity groups (sometimes known as special groups) that are used by the system or by administrators to allocate to resources. Membership in special groups is automatic, based on criteria, and you cannot manage special groups through the Local Users And Groups console. Table 2-2 describes the special identity groups that are built in to Windows 10.
Table 2-2 Built-in Special Identity Groups
Special Identity Group |
Description |
|---|---|
Anonymous Logon |
When a user accesses the computer through an anonymous logon, such as via special accounts created for anonymous access to Windows 10 services, they become members of the Anonymous Logon group. |
Authenticated Users |
This is a useful group because it includes all users who access Windows 10 using a valid username and password. |
Batch |
This group includes users who log on as a batch job operator to run a batch job. |
Creator Owner |
The creator owner is the account that created or took ownership of an object, such as a file, folder, printer, or print job. Members of the Creator Owner group have special administrator-level permissions to the resources over which they have ownership. |
Dialup |
This group includes users who log on to the network from a dial-up connection. |
Everyone |
This group includes anyone who accesses the computer. This includes all users, including Guest accounts and all users that are within a domain or trusted domains. Members of the Anonymous Logon group are not included as a part of the Everyone group. |
Interactive |
This group includes all users who use the computer’s resources locally and those who are not using the computer’s resources remotely via a network connection. |
Network |
This group includes users who access the computer’s resources over a network connection. |
Service |
This group includes users who log on as a user account that is used to run a service. |
System |
When Windows 10 needs to access internal functions, it can perform actions as a system user. The process being accessed by the operating system becomes a member of the System group. |
Terminal Server User |
This group includes users who log on through Terminal Server applications. |
Manage devices in directories
Microsoft has designed Windows 10 to be managed using cloud-based tools such as Microsoft Intune and Microsoft 365 Device Management. As more businesses migrate away from traditional on-premises domain environments to the cloud, you will need to understand how to configure devices to register them in Azure Active Directory.
In this section, you will learn how to register a device so that it can be managed by a work or school using cloud-based services. You will see how to enable device registration and the process of joining devices to Azure Active Directory.
Understand Device Management
Once devices are managed by Azure Active Directory (Azure AD), you can you ensure that your users are accessing your corporate resources from devices that meet your standards for security and compliance. To protect devices and resources using Azure AD, users must be allowed to have their Windows 10 devices managed by Azure AD.
Azure AD is a cloud-based identity authentication and authorization service that enables your users to enjoy the benefits of single sign-on (SSO) for cloud-based applications, such as Office 365. Users can easily join their devices to your organization’s Azure AD once you have enabled device joining in the Azure Active Directory Admin Center.
When joining devices to an on-premises domain environment, the types of devices that you can join to the domain are quite restrictive; devices, for example, must be running a supported operating system. This means that any users that have devices running Windows 10 Home editions cannot join the company’s on-premises domain. However, Azure AD is less restrictive in this respect; you can add to Azure AD almost any tablet, laptop, smartphone, and desktop computer running a variety of platforms. When you enable users to add their devices to Azure AD, you will manage their enrolled devices by using a mobile device management solution, such as Microsoft Intune, which allows you to manage and provision your users’ devices.
Devices can be managed by Azure AD using two methods:
Joining a device to Azure AD
Registering a device to Azure AD
Azure Ad–Joined Device
Joining a Windows 10 device to Azure AD is similar to registering a device with Azure AD, but it allows enhanced management capabilities. Once a device has been joined to Azure AD, the local state of a device changes to allow your users to sign in to the device using the work or school account instead of a personal account.
An enterprise will typically join its work-owned devices to Azure AD to allow for cloud-based management of the devices and to grant access to corporate apps and resources.
Bulk joining of devices to Azure AD and Windows AutoPilot deployment are outside the scope of the MD-100 Windows 10 exam, though you should expect to find these topics covered in the MD-101 Managing Modern Desktops exam.
Organizations of any size can deploy Azure AD Join. Azure AD Join works well in a cloud-only (no on-premises infrastructure) environment. When Azure AD Join is implemented in a hybrid environment, users gain access to both cloud and on-premises apps and resources.
Azure AD–joined devices allow your users to access the following benefits:
Single-Sign-On (SSO) Allows users simplified access to Azure managed SaaS apps, services, and work resources.
Enterprise-compliant roaming User settings can be roamed across joined devices using their Azure AD–joined devices (without the need to sign in using a Microsoft account).
Access to Microsoft Store for Business Users can access a Microsoft Store populated with apps chosen by your organization.
Windows Hello Devices can be secured using the enterprise features of Windows Hello.
Restriction of access Devices will only be able to access apps that meet the organizational compliance policy.
Seamless access to on-premises resources Hybrid Azure AD–joined devices can access on-premises resources when connected to the domain network.
Organizations that already have Office 365 or other SaaS apps integrated with Azure AD have the necessary components in place to have devices managed in Azure AD instead of being managed in Active Directory.
Azure Ad–Registered Devices
Once a device is registered into management, it is known to Azure AD, and information relating to the device is stored in Azure AD. Effectively, the device is given an identity with Azure AD. You can create conditional access rules to determine whether access to resources from your devices will be granted.
Azure AD–registered devices allow users to use personally owned devices to access your organization’s resources in a controlled manner. Azure AD supports Bring Your Own Device (BYOD) scenarios for multiple types of devices, including Windows 10, iOS, Android, and macOS.
With an Azure AD–registered device, the user will gain access to resources using a work or school Azure AD account at the time they access the resources. All corporate data and apps will be kept separate from the personal data and apps on the device. If the personal computer, tablet, or phone that is registered with Azure AD does not meet your corporate standards for security and compliance—for example, if a device is not running a supported version of the operating system, or it has been jail broken—then the access to the resource will be denied.
Device Registration enables you to facilitate a single sign-on (SSO) experience for users, removing the need for them to repeatedly enter credentials to access resources.
The main reasons to implement Device Registration are
To enable access to corporate resources from nondomain-joined or personally owned devices
To enable SSO for specific apps and/or resources managed by Azure AD
After you enable Device Registration, users can register and enroll their devices in your organizational tenant. After they have enrolled their devices
Enrolled devices are associated with a specific user account in Azure AD.
A device object is created in Azure AD to represent the physical device and its associated user account.
A user certificate is installed on the user’s device.
Configure Device Management
Device management requires configuration to ensure that when your users attempt device registration, the process will not fail. By default, the setting is enabled, and it allows all Windows 10 devices that present valid credentials to be managed by your Azure AD.
The Azure portal provides a cloud-based location to manage your devices. To allow registration of devices into Azure AD follow these steps:
Sign in as an administrator to the Azure portal at https://portal.azure.com.
On the left navigation bar, click Azure Active Directory.
In the Manage section, click Devices.
Click Device Settings.
On the Device Settings blade, ensure that the Users May Join Devices To Azure AD setting is configured to All, as shown in Figure 2-6. If you choose Selected, then click the Selected link and choose the users who can join Azure AD. You can select both individual users and groups of users.
![A screenshot shows the Azure Active Directory Admin Center page with three sections. The left section shows a list of items: Dashboard, All services, Azure Active Directory, Users, and Enterprise Applications. The middle section shows a Manage heading with options for All Devices, Device Settings (selected), and Enterprise State Roaming. Below, sections for Activity and Troubleshooting are shown. In the right pane, Users May Join Devices To Azure AD shows the following options: All (selected), Selected, and None. Below this is another option for Additional Local Administrators On Azure AD[nd]Joined Devices. Two options are available: Selected and None (selected).](Images/02fig06.jpg)
Figure 2-6 Enabling Azure AD join Click Save.
Within the Azure AD portal, you can fine-tune the process of registering and joining devices by configuring the device settings as listed in Table 2-3.
Table 2-3 Azure AD device configuration settings
Device Setting |
Description |
|---|---|
Users May Join Devices To Azure AD |
The default is All. The Selected option allows you to select users who can join Windows 10 devices to Azure AD. |
Additional Local Administrators On Azure AD Joined Devices |
You can select the users who are granted local administrator rights on a device and added to the Device Administrators role in Azure AD. By default, global administrators in Azure AD and device owners are granted local administrator rights. Requires an Azure AD Premium P1 or P2 license. |
Users May Register Their Devices With Azure AD |
Required to allow devices to be registered with Azure AD by users. Options include:
|
Require Multi-Factor Auth To Join Devices |
Choose whether users are required to use multifactor authentication to join their devices to Azure AD. The default setting is No. This setting is only applicable to Azure AD Join on Windows 10 and BYOD registration for Windows 10, iOS, and Android. |
Maximum Number Of Devices |
By default, all users can have a maximum of 20 devices in Azure AD. Once this quota is reached, they are not be able to add additional devices until one or more of the existing devices are removed. The device quota is across both Azure AD–joined and Azure AD–registered devices. |
Users May Sync Settings And App Data Across Devices |
By default, this setting is set to NONE, but you can enable this for specific users or groups. The ALL setting allows all the user’s settings and app data to sync across their Windows 10 devices. Requires Azure AD Premium P1 or a P2 license. |
![]() Exam Tip
Exam Tip
Each device must be able locate the Internet to allow you to authenticate using your Azure AD credentials. If a device cannot locate the cloud-based identity service, then there will be a problem accessing resources managed by Azure AD.
Device Management Tasks
Once devices have been registered or joined to Azure AD, they appear in the list within the All Devices section of the Azure Active Directory Admin Center. Devices managed by another management authority, such as Microsoft Intune, are also listed.
To locate a device, you can search using the device name or device ID. Once you have located a device, you can perform additional device management tasks including:
Update devices—You can enable or disable devices. You need to be a global administrator in Azure AD to perform this task, which prevents a device from being able to authenticate with Azure AD and thus, prevents the device from accessing any Azure AD resources.
Delete devices—When a device is retired, or it no longer requires access to your corporate resources, it should be deleted in Azure AD. Deleting a device requires you to be a to be a global administrator in Azure AD or an Intune administrator. Once deleted, all details stored in Azure AD relating to the device— for example, BitLocker keys for Windows devices—are removed. If a device is managed elsewhere, such as in Microsoft Intune, you should ensure that the device has been wiped before deleting the device in Azure AD.
View device ID Each device has a unique device ID that can be used to search for the device; the unique device ID can be used as a reference if you need to use PowerShell during a troubleshooting task.
View device BitLocker key Windows devices managed by Azure AD can have their BitLocker recovery keys stored in Azure AD. You can access this key if the encrypted drive needs to be recovered. To view or copy the BitLocker keys, you need to be either the owner of the device or have one of the following roles assigned: Global Administrator, Helpdesk Administrator, Security Administrator, Security Reader, or Intune Service Administrator.
Note Use Powershell to Back up the Bitlocker Recovery Key to Azure Ad
For Azure AD–joined computers, the BitLocker recovery password should be stored in Azure AD. You can use the PowerShell cmdlets Add-BitLockerKeyProtector, Get-BitLockerVolume, and BackupToAAD-BitLockerKeyProtector to add a recovery password and back it up to Azure AD before enabling BitLocker.
Connect devices to Azure AD
Once the pre-requisites have been configured to allow device registration service to take place, you are able to connect devices to Azure AD.
There are three ways to connect a Windows 10 device to Azure AD as follows:
Join a new Windows 10 device to Azure AD
Join an existing Windows 10 device to Azure AD
Register a Windows 10 device to Azure AD
In this section, you will learn the steps required for each method of connecting Windows 10 to Azure AD.
Join a New Windows 10 Device to Azure ad
In this method, we will take a new Windows 10 device and join the device to Azure AD during the first-run experience. The device could have been previously prepared using an enterprise deployment method, or it could have been distributed by the original equipment manufacturer (OEM) directly to your employees.
If the device is running either Windows 10 Professional or Windows 10 Enterprise, the first-run experience will present the setup process for company-owned devices.
Note Joining a Device to Active Directory During the First-Run Experience
Joining an on-premises Active Directory domain is supported in Windows 10 during the Windows out-of-box experience. If you need to join a computer to an AD domain, during setup, you should choose the option to Set Up For An Organization and then select the Domain Join Instead link. You then need to set up the device with a local account, then join the domain from the Settings app on your computer. For the MD-100 Windows 10 exam, you should expect that devices will be cloud- or hybrid cloud–enabled.
To join a new Windows 10 device to Azure AD during the first-run experience, use the following steps:
Start the new device and allow the setup process.
On the Let’s Start With Region. Is This Correct? page, select the regional setting that you need and click Yes.
On the Is This The Right Keyboard Layout? page, select the keyboard layout settings and click Yes.
On the Want To Add A Second Keyboard Layout? page, add a layout or select Skip.
The computer should automatically connect to the Internet, but it if it does not, you will be presented with the Let’s Connect You To A Network page where you can select a network connection.
On the How Would You Like To Set Up? Page, choose Set Up For An Organization and click Next.
On the Sign In With Microsoft page, enter your Organization or school account and password and click Next.
On the Do More Across Devices With Activity History page, choose whether to enable the Timeline feature.
On the Do More With Your Voice page, choose whether to enable the Speech Recognition feature and click Accept.
On the Let Microsoft And Apps Use Your Location page, choose whether to enable the location-based features and click Accept.
On the Find My Device page, choose whether to enable the Find My Device feature and click Accept.
On the Send Diagnostic Data To Microsoft page, choose Full or Basic diagnostic data transfers and click Accept.
On the Improve Inking & Typing page, choose Yes or No and click Accept.
On the Get Tailored Experiences With Diagnostic Data page, choose Yes or No and click Accept.
On the Let Apps Use Advertising ID settings page, choose the privacy settings that you require and click Accept.
Depending on organizational settings, your users might be prompted to set up Windows Hello. By default, they will be prompted to set up a PIN. When prompted to set up a PIN, click Set Up PIN.
On the More Information Required page, click Next, provide the additional security verification information, and click Next again.
You should now be automatically signed in to the device, joined to your organization or school Azure AD tenant, and presented with the desktop.
Join an Existing Windows 10 Device to Azure ad
In this method, we will take an existing Windows 10 device and join it to Azure AD. You can join a Windows 10 device to Azure AD at any time. Use the following procedure to join the device:
Open the Settings app and then click Accounts.
In Accounts, click the Access Work Or School tab.
Click Connect.
On The Set Up A Work Or Education Account page, under Alternative Actions, click Join This Device To Azure Active Directory, as shown in Figure 2-7.

Figure 2-7 Joining a device to Azure AD On The Let’s Get You Signed In page, enter your Work or Education username and click Next.
On the Enter Password page, enter your password and click Sign In.
On the Make Sure This Is Your Organization page, confirm that the details on screen are correct and click Join.
On the You’re All Set! page, click Done.
To verify that your device is connected to your organization or school, your Azure AD email address will be listed under the Connect button indicating that it is connected to Azure AD.
If you have access to the Azure Active Directory portal, then you can validate that the device is joined to Azure AD by following these steps:
Sign in as an administrator to the Azure portal at https://portal.azure.com.
On the left navigation bar, click Azure Active Directory.
In the Manage section, click Devices > All Devices.
Verify that the device is listed as shown in Figure 2-8.
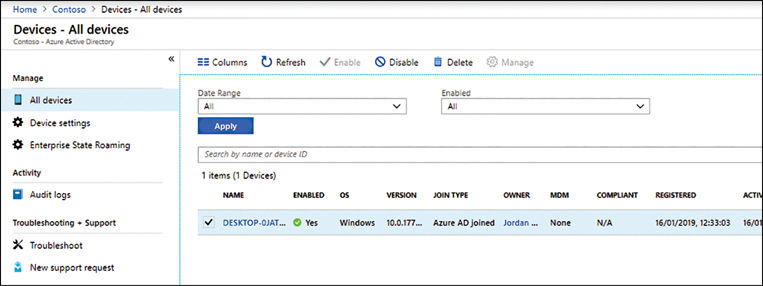
Figure 2-8 Viewing All devices in Azure AD
Register Devices to Azure Ad
You connect a Windows 10 device to Azure Active Directory using the Add Work or School Account feature found in the Settings app. Device registration is used to allow devices to be known by both Azure AD and MDM solutions.
In this method, we will take an existing Windows 10 device and register it to Azure AD. Use the following procedure to register the device:
Open the Settings app and then click Accounts.
In Accounts, click the Access Work Or School tab.
Click Connect.
On The Set Up A Work Or Education Account page, enter your work or education email address, click Next, and complete the wizard.
To verify that a device is registered to your organization or school Azure AD tenant, users can use these steps:
Open the Settings app and then click Accounts.
In Accounts, click the Access Work Or School tab.
On the Access Work Or School page, verify that your organization or school Azure AD email address is listed under the Connect button.
Note Register Byo Devices to Azure Ad
You can register a personally owned device with Azure AD using the Set Up A Work Or Education Account wizard. Personal devices are then known to Azure AD but are not fully managed by the organization.
Enroll devices into Microsoft 365
Microsoft 365 is a bundled subscription including Office 365, Windows 10, and Enterprise Mobility + Security. Microsoft 365 comes in three primary bundles:
Microsoft 365 Business For small- and medium-sized organizations up to 300 users
Microsoft 365 Enterprise For organizations of any size
Microsoft 365 Education For educational establishments
With Microsoft 365, you use Azure Active Directory for your identity and authentication requirements, and you can (and should) enroll Windows 10 into device management, so that your users can gain access to corporate resources. Once devices are joined to your Microsoft 365 tenant, Windows 10 becomes fully integrated with the cloud-based services offered by Office 365 and Enterprise Mobility + Security. Microsoft 365 supports other platforms including Android and iOS, which can also be managed as mobile devices. However, only Windows 10 devices can be joined to Azure AD.
Note Microsoft 365 Business Does not Include Windows 10
The Microsoft 365 Business subscription includes Office 365 Business and Enterprise Mobility + Security, but it does not include Windows 10. However, the Microsoft 365 Business subscription does allow businesses to upgrade their existing Windows 7 Professional, Windows 8 Pro, or Windows 8.1 Pro devices to Windows 10 Pro. Windows 10 Pro is then provided with a Windows 10 Business license, which enables businesses to use the set of cloud-services and device management capabilities included with Microsoft 365 Business.
Enroll Devices into Microsoft 365 Business
When you enroll Windows devices into Microsoft 365 Business, they must be running Windows 10 Pro, version 1703 (Creators Update) or later. If you have any Windows devices running Windows 7 Professional, Windows 8 Pro, or Windows 8.1 Pro, the Microsoft 365 Business subscription entitles you to upgrade them to Windows 10 Pro.
Microsoft 365 Business includes a set of device-management capabilities powered by Microsoft Intune. Microsoft 365 Business offers organizations a simplified management console that provides access to a limited number of device management tasks, including
Deploy Windows with Autopilot
Remove company data
Factory reset
Manage Office deployment
To enroll a brand-new device running Windows 10 Pro into Microsoft 365 Business, known as a “user-driven enrollment”, follow these steps:
Go through Windows 10 device setup until you get to the How Would You Like To Set Up? Page, as shown in Figure 2-9.

Figure 2-9 Windows 10 device setup Choose Set Up For An Organization and then enter your username and password for your Microsoft 365 Business subscription (the new user account not the tenant admin account).
Complete the remainder of the Windows 10 device setup.
The device will be registered and joined to your organization’s Azure AD, and you will be presented with the desktop.
You can verify the device is connected to Azure AD by opening the Settings app and clicking Accounts.
On the Your Info page, click Access Work Or School.
You should see that the device is Connected to your organization. Click your organization name to expose the Info and Disconnect buttons.
Click Info to see that your device is managed by your organization and to view your device sync status.
To verify that the device has been granted a Windows 10 Business license, click the Home icon, click System, and then click About.
Within Windows specifications, the Windows 10 Edition shows Windows 10 Business, as shown in Figure 2-10.
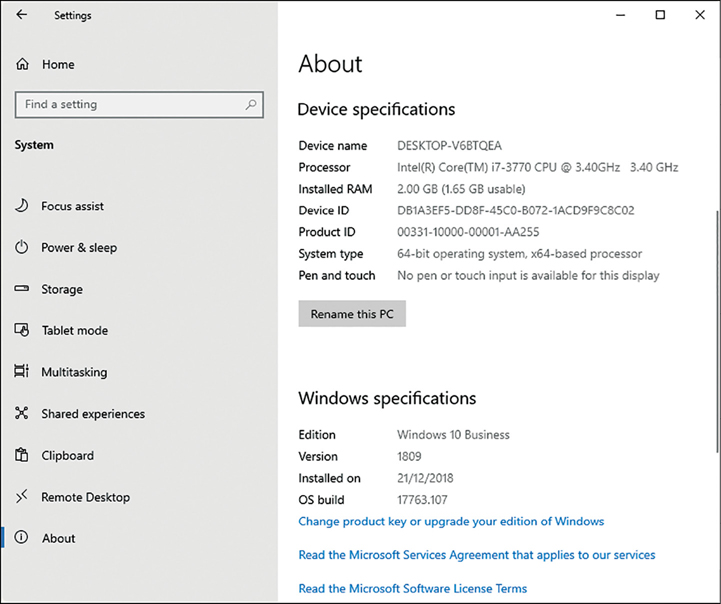
Figure 2-10 Windows 10 device setup
Although there is no link to Microsoft Intune within the Microsoft 365 Business Admin Center, the subscription includes the use of the full Intune capabilities for iOS, Android, MacOS, and other cross-platform device management. To access the Microsoft Intune console in Microsoft Azure, launch a browser and sign in with your Microsoft 365 Business credentials at https://portal.azure.com.
Follow these steps to access Intune App Protection in the Azure portal and view the app protection settings for managed Windows 10, Android, and iOS devices.
Sign into the Microsoft 365 Device Management portal at https://devicemanagement.microsoft.com with your Microsoft 365 Business admin credentials.
In the left navigation bar, select Client Apps.
In the Client Apps blade, select App Protection Policies.
You can now select Create Policy from the menu and configure App Protection Policies.
Enroll Devices into Microsoft 365 Enterprise
Microsoft 365 Enterprise plans can be chosen by larger organizations with more than 300 users or businesses of any size that require access to the increased levels of compliance and security management over Microsoft 365 Business.
When enrolling devices into Microsoft 365 Enterprise, those devices must be running Windows 10 Enterprise, version 1703 (Creators Update) or later. Devices running an earlier version of Windows can be upgraded to Windows 10 Enterprise as part of the Microsoft 365 Enterprise licensing.
Users can perform an Azure AD join using the user-driven enrollment method shown in the previous section to enroll their devices into management. Enrollment can happen during the Out-of-Box Experience (OOBE) or after a Windows profile has already been set up. To enroll a device once a user has already set up a Windows user profile, follow the steps outlined in the “Join a new Windows 10 device to Azure AD” section of this skill.
If you want to enroll a large number of devices in an enterprise scenario, you can use the Device Enrollment Manager (DEM) account in Microsoft Intune. The DEM is a special account in Microsoft Intune that allows you to enroll up to a maximum of 1,000 devices. (By default, standard users can manage and enroll up to five devices.) For security reasons, the DEM user should not also be an Intune administrator. Each enrolled device will require a single Intune license, but the DEM user does not require an Intune license.
By default, there is no device enrollment account user present in Microsoft Intune. You can create a device enrollment account by performing the following steps:
Sign into the Microsoft 365 Device Management portal at https://devicemanagement.microsoft.com with your Microsoft 365 Enterprise admin credentials.
In the left navigation bar, select Device Enrollment, and then under Manage, choose Device Enrollment Managers.
Select Add.
On the Add User blade, enter the username for the DEM user and select Add. The user is promoted to the DEM role.
Close the Add User blade.
The list of Device Enrollment Managers now contains the new user, as shown in Figure 2-11.
![A screenshot shows the Microsoft 365 device management page, which includes three sections. On the leftmost pane is a list of items, including Dashboard, All Services, Device Enrollment, and Device Compliance. The center pane is titled Device Enrollment[md]Device Enrollment Managers, and a list of options is shown under the Manage heading. (Device Enrollment Managers is selected.) In the right pane, two users and their respective email addresses are shown.](Images/02fig11.jpg)
Figure 2-11 List of Device Enrollment Managers
More Info Enroll Devices Using Device Enrollment Manager
For more information on the DEM in Microsoft Intune, including example scenarios and limitations of devices that are enrolled with a DEM account, visit https://docs.microsoft.com/intune/device-enrollment-manager-enroll.
View and manage devices in Microsoft 365
Microsoft 365 Business subscription administrators can manage their enrolled devices directly from the Microsoft 365 Business Admin Center Home screen using the Enroll Devices tile, as shown in Figure 2-12. Also, enrolled devices can be managed in the Microsoft 365 Device Management portal.

On the Microsoft 365 Business Admin portal Home screen, both the Device Enrollment link on the Enroll Devices tile and the Device Management option (under Admin Centers) will open the standalone Microsoft 365 Device Management portal. This portal can also be accessed at https://devicemanagement.microsoft.com.
Note Microsoft 365 Admin Portal Preview
At the time of writing, the Microsoft 365 Admin portal is available in a preview mode. This provides administrators with a portal with a new, cleaner look and feel. The Preview On toggle to swap between the old Admin Center and Preview Admin Center is located in the top-right corner of the Admin Center home page, as shown in Figure 2-12.
You can perform the following device-related actions on devices from within the Devices section on the navigation bar.
AutoPilot Including adding new devices to be deployed with the Windows Autopilot service and managing Windows Autopilot profiles that can be applied to devices.
Policies Including managing existing policies and assigning policies to groups. Add new application policies to Android, iOS, and Windows 10 devices, and add new device configuration polices to Windows 10 devices.
Manage Including view device details, Factory Reset, Remove Company Data, and Remove Device.
Organizations with a Microsoft 365 Enterprise subscription cannot view or manage devices from the Microsoft 365 Enterprise Admin Center and will need to use the following locations:
Azure Active Directory https://aad.portal.azure.com
Intune in the Azure portal https://portal.azure.com
Microsoft 365 Device Management https://devicemanagement.microsoft.com
From these views, you can manage and interact with the devices enrolled into your Azure AD tenant, including retiring or wiping a device. Also, you can perform remote tasks, such as retiring, wiping, or restarting the device, as shown in Figure 2-13.
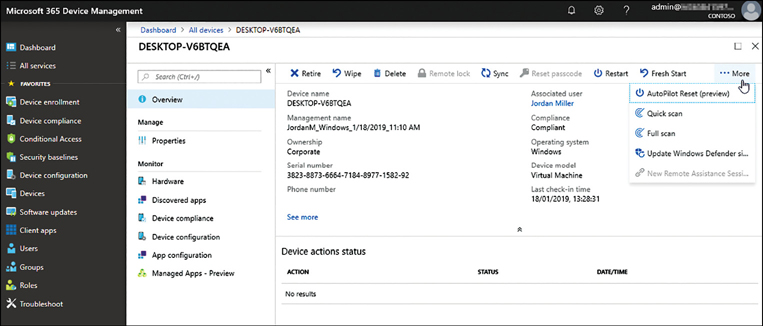
Skill 2.2: Configure data access and protection
Being able to access your data from anywhere is a key feature of Windows 10, whether in a small workgroup, in a large enterprise across a LAN, or when mobile using the Internet. This skill discusses multiple methods of sharing configuration and setting access permissions on the share so that you are in control of who can see or edit the data. You review how to troubleshoot data access issues and stay informed of your usage status when using a metered connection.
Configure NTFS permissions
Most users are familiar with using the File Explorer tool to view and manage files and folders. When administrating shared files and folders over a network, File Explorer is still the primary tool to configure file- and folder-level permissions. Although permissions have been part of NTFS and earlier versions of Windows, you need to ensure that you are familiar with NTFS and the changes offered in Windows 10.
Understand NTFS
NTFS is the native file system Windows 10 uses, which is widely used across most Windows operating systems. It offers you the ability to protect and secure folders and files through file- and folder-level security permissions to control access. NTFS offers the following characteristics:
File-level compression
Per-user volume quotas
Symbolic links and junction points
Volume sizes up to 256 TB
Support for large volumes—up to 232-1 files per volume
Maximum implemented file size is 256 TB minus 64 KB or 281,474,976,645,120 bytes
Support for extended-length paths
Support for long file names, with backward compatibility
Enterprise-level file and folder encryption
Support for BitLocker Drive Encryption
Metadata transactional logging to ensure that file structure can be repaired
Limited self-healing capabilities
Use File Explorer to manage files and folders
The most common tool used to manage files and folders is File Explorer, which is located on the taskbar and on the Start screen. Typical functions provided through File Explorer include:
Creating new folders and files
Viewing and accessing files and folders
Searching for files and information contained in files
Managing properties of files and folders
Previewing contents or thumbnails of files and folders
The Quick Access area is new in Windows 10 and appears at the uppermost left area of the File Explorer navigation pane; it includes pinned shortcuts for frequently used files and folders including the Desktop, Downloads, Documents, Pictures, and Music. As you browse and access files in other folders on your computer, folder shortcuts for these items appear in the right navigation pane under Frequent Folders or Recent Files. You can modify the behavior of Quick Access by right-clicking Quick Access and selecting Options, as shown in Figure 2-14.

On a shared computer, you might want to clear the check boxes for Show Recently Used Files In Quick Access and Show Frequently Used Folders In Quick Access.
Set file and folder permissions
Volumes formatted using either NTFS or the newer ReFS enable you to configure file and folder permissions. NTFS permissions are robust, reliable, and effective, and they enable you to configure granular permissions on both files and folders that determine how individual users and groups can use the objects.
The creator of the resource, such as a file or folder, is automatically assigned the special status of creator-owner, and the creator can grant or deny permissions to it. Administrators and anyone given the Full Control permission also can modify permissions for that file or folder.
Note Refs Creation Ability
With the Windows 10 Fall Creators Update (Windows 10 version 1709), the ability to format a disk with ReFS was removed, except for Windows 10 Enterprise and Windows 10 Pro for Workstations editions. All Windows 10 clients will only be able to read/write ReFS disks.
To modify permissions to a file or folder, access the Security tab in the object’s properties, as shown in Figure 2-15.

If a user leaves the organization or the account is deleted, an Administrator can take ownership of the files and folders to modify permissions by changing the Owner principal found in the Advanced settings in Properties.
If you have the permission to modify the security settings in the access control list (ACL), you can add or remove users or groups and then grant or deny a specific permission level. In organizations, you assign permissions to groups rather than to multiple users because this minimizes administrative effort.
Review the acronyms relating to objects that you might use when applying security permissions, as shown in Table 2-4.
Table 2-4 Security Permission acronyms
Name |
Acronym |
Description |
|---|---|---|
Access control list |
ACL |
A list of trustees (users and groups) with permissions for the object. |
Access control entry |
ACE |
Identifies specific permissions granted to a user or group. Each ACE identifies the trustee and specifies the access rights allowed, denied, or audited for that trustee. |
Discretionary access control list |
DACL |
Specifies which trustees are allowed or denied access to an object. |
System access control list |
SACL |
Specifies which users and groups will be audited when they perform actions, such as creating, modifying, or deleting objects. |
When configuring permissions for files and folders, you can configure basic or advanced permissions. Unless you are seeking a very fine degree of control to a resource, you typically work with basic permissions and assign them to groups and users, as shown in Table 2-5.
Table 2-5 Basic file and folder permissions for NTFS and ReFS
File Permission |
Description |
|---|---|
Full Control |
Complete authority and control of all file or folder permissions. |
Modify |
Ability to read a file, write changes to it, and modify permissions. |
Read & Execute |
Ability to see folder content, read files and attributes, and start programs. |
Read |
Ability to read a file but not make any changes to it. |
Write |
Ability to change folder or file content and create new files. |
Special Permissions |
Indication of whether additional advanced permissions have been configured for the file or folder. |
Note Basic and Advanced Permissions
If you are familiar with older versions of Windows, you might notice that Windows 10 uses the modern naming for permissions as follows: Standard Permissions has been changed to Basic Permissions, and Special Permissions has been changed to Advanced Permissions.
Basic permissions are easier to manage and document. Under the hood, a basic permission is made from a combination of individual advanced special permissions. Consider that permissions for folders can have a different effect on files, as described in Table 2-6.
Table 2-6 Basic NTFS file and folder permissions
Basic Permission |
Description: When Applied to a Folder |
Description: When Applied to a File |
|---|---|---|
Full Control |
Permits reading, writing, changing, and deletion of files and subfolders. Allows the modification of permissions on folders. |
Permits reading, writing, changing, and deletion of the file. Allows modification of permissions on files. |
Modify |
Permits reading, writing, changing, and deletion of files and subfolders. Does not allow changes to permissions on folders. |
Permits reading, writing, changing, and deletion of the file. Does not allow changes to the permissions on files. |
Read & Execute |
Allows the content of the folder to be accessed and executed. |
Allows the file to be accessed and executed (run). |
List Folder Contents |
Allows the contents of the folder to be viewed. |
Does not apply to files. |
Read |
Allows content to be read. |
Allows access to the contents. Does not allow files to be executed. |
Write |
Allows addition of files and subfolders to the folder. |
Allows a user to modify but not delete a file. |
Behind the basic permissions is a matrix of 13 advanced permissions that can also be applied to files and folders. Each basic permission is a collection of one or more advanced permissions, as shown in Table 2-7.
Table 2-7 Basic and advanced permissions
Advanced Permission |
Full Control |
Modify |
Read & Execute |
List Folder Contents |
Read |
Write |
|---|---|---|---|---|---|---|
Traverse Folder/ Execute File |
X |
X |
X |
X |
|
|
List Folder/Read Data |
X |
X |
X |
X |
X |
|
Read Attributes |
X |
X |
X |
X |
X |
|
Read Extended Attributes |
X |
X |
X |
X |
X |
|
Create Files/Write Data |
X |
X |
|
|
|
X |
Create Folders/Append Data |
X |
X |
|
|
|
X |
Write Attributes |
X |
X |
|
|
|
X |
Write Extended Attributes |
X |
X |
|
|
|
X |
Delete Subfolders And Files |
X |
|
|
|
|
|
Delete |
X |
X |
|
|
|
|
Read Permissions |
X |
X |
X |
X |
X |
X |
Change Permissions |
X |
|
|
|
|
|
Take Ownership |
X |
|
|
|
|
|
It is recommended to use basic permissions unless there is a clear requirement for setting advanced permissions; otherwise, they can become complex and difficult to troubleshoot. If you do use the advanced permissions, it is best practice to document any modifications so that you can review the configuration and, if necessary, reverse the settings.
Many inexperienced users who configure NTFS permissions can complicate the settings on files by setting advanced permissions (frequently using deny permissions) and setting permissions for individual users instead of setting permissions for groups. There is a strict canonical order or hierarchy of how Deny and Allow permissions can interoperate, and the general rule is that a Deny setting prevents an Allow setting.
![]() Exam Tip
Exam Tip
Remember the principle of least administration when applying NTFS or ReFS permissions. If you want to prevent a user or group from having any access to a resource, you could set no permissions. If neither Allow nor Deny permission is explicitly configured or inherited on a resource, users are prevented from accessing the file or folder.
Review Table 2-8 to understand the relationship between Deny and Allow settings and how the behavior changes, depending on how the setting is applied.
Table 2-8 Allow and Deny NTFS permissions
Permission Type |
Description |
Check Box Status |
|---|---|---|
Explicit Deny |
The user is denied the permission on the file or folder. |
The check box is selected. |
Explicit Allow |
The user is allowed the permission on the file or folder. |
The check box is selected. |
Inherited Deny |
Deny permission is applied to the file or subfolder by permissions given to the parent folder. |
The check box is dimmed but selected. |
Not configured |
When no permissions are assigned, the user has no permission to access the file or folder. |
The check box is cleared. |
Inherited Allow |
Allow permission is applied to the file or subfolder by permissions given to the parent folder. |
The check box is dimmed but selected. |
Note When Allow Overrides Deny
When applying permissions to groups and allowing inheritance, sometimes one group has an explicit Allow setting, and another group has an inherited Deny setting. If a user is a member of both groups, the Allow setting will override the implicit Deny.
Although most administrators will use File Explorer to set individual ACLs for files and folders, you can also use Windows PowerShell or the ICACLS command-line utility.
Windows PowerShell offers two cmdlets that you can use to manage file and folder permissions: Get-Acl and Set-Acl. For additional information and examples of how to use these cmdlets, type Get-Help Get-Acl, or Get-Help Set-Acl.
ICACLS enables you to configure and view permissions on files and folders on a local computer. Some of the most common ICACLS parameters and permission masks are shown in Table 2-9.
Table 2-9 Common ICACLS parameters and permission masks
Parameter/ Permission Mask |
Description |
|---|---|
/grant |
Grants specific user access rights. Permissions replace previously granted explicit permissions. |
/deny |
Explicitly denies specified user access rights. An explicit Deny ACE is added for the stated permissions, and the same permissions in any explicit grant are removed. |
/reset |
Replaces ACLs with default inherited ACLs for all matching files. |
F |
Full access. |
M |
Modify access. |
RX |
Read and execute access. |
R |
Read-only access. |
W |
Write-only access. |
(OI) |
Object inherit. |
(NP) |
Do not propagate inherit. |
To grant a permission, use the /grant switch, as the following example on an existing file called My New Files within the C:\Working Folder shows.
Open File Explorer.
Navigate to the folder on which you want to set permissions.
Click File and then click Open Windows PowerShell As Administrator.
Type the following command.
Icacls 'My new files.rtf' /grant 'Demo:(OI)(M)'
Type Icacls ’My new files.rtf’ to view the permissions.
Need More Review? Icacls
This Microsoft resource provides additional information for you to review relating to ICACLS. Visit https://docs.microsoft.com/windows-server/administration/windows-commands/icacls.
Understand NTFS inheritance
Setting NTFS permissions on hundreds of files and folders would take a long time, especially if each setting were configured manually. Fortunately, you don’t need to because, by default, NTFS and ReFS security permissions are inherited from their parent folder. In this way, permissions will “flow” from top to bottom and follow the folder hierarchy. By default, inheritance is enabled because this facilitates more efficient administration. NTFS enables you to disable inheritance from flowing from a parent folder to the child.
You can review the inheritance status of a file or folder in File Explorer by following these steps.
Open File Explorer.
Navigate to the folder whose inheritance settings you want to review.
Right-click the file or folder, and choose Properties > Advanced.
On the Permissions tab, review the permission entries and notice the Inherited From column, as shown in Figure 2-16.
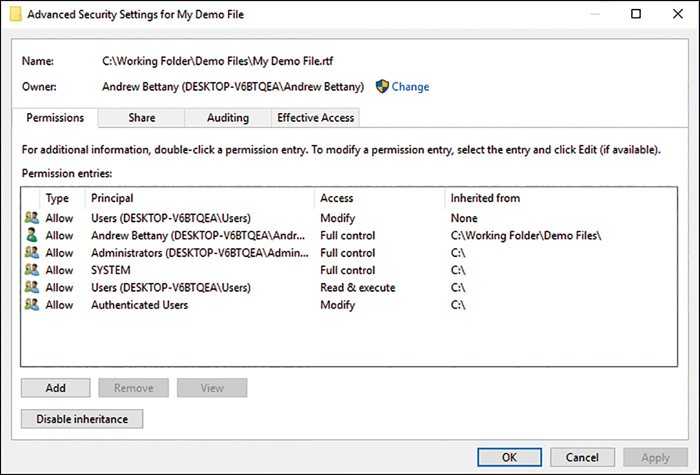
Figure 2-16 NTFS inheritance
Figure 2-16 shows a Disable Inheritance button. If you select this button, you are presented with two choices as shown in Figure 2-17.
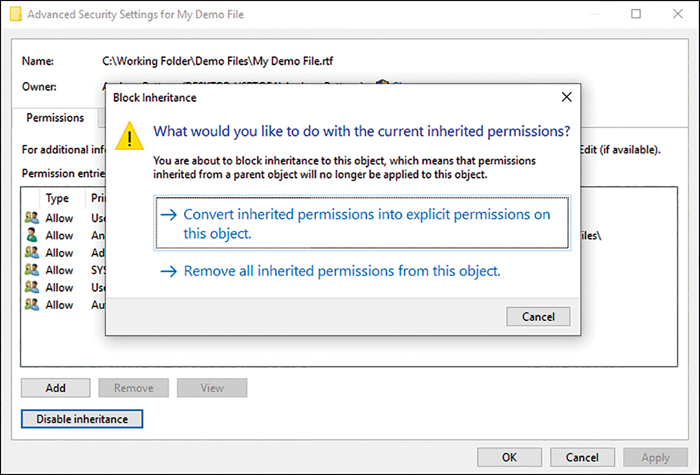
In the Block Inheritance dialog box, there are two options, as follows:
Convert Inherited Permissions Into Explicit Permissions On This Object Prevents inherited permissions from being able to “flow” from top folders to the subfolders. Current inherited permissions are changed by the system from implicit permissions to explicit permissions. This can result in hundreds or thousands of inherited permissions being changed into explicit permissions.
Remove All Inherited Permissions From This Object Removes all permissions and gives you a folder structure with no permissions set. Care needs to be taken with this option because it is very easy to remove all access—even system access—to the file structure.
The option to convert inherited permissions to explicit permissions on this object stops inheritance from flowing from the parent folders and changes the permissions on all child items from implicit permissions to explicit permissions. You can then modify the permissions.
If you choose the second option, Remove All Inherited Permissions From This Object, you completely remove all permissions. This provides you with a folder structure with no permissions at all.
Both options are powerful and can have far reaching effects. Best practice recommends employing inheritance wherever possible, to ease administration. You should also document and test your outline folder structure before it becomes too large. A big change on a small structure is simple to put in place, whereas modifying a large, established file structure could be cumbersome.
Understanding move, copy, and permissions inheritance
When you need to move or copy a folder from one location to another, you need to understand how NTFS will perform the task with respect to how permissions on the resource are modified. Table 2-10 shows the behavior that NTFS adopts when copying files from one folder to another folder, and between partitions.
Table 2-10 Resultant effect of moving or copying NTFS files
Action |
Effect |
|---|---|
Copy or Move a file or folder to a different volume |
Inherits the permissions from the destination (new location) folder. |
Copy or Move a file or folder within the same NTFS volume |
Inherits the permissions from the new parent folder, and explicitly assigned permissions are retained and merged with the inherited permissions. |
Copy a file or folder to a non-NTFS volume |
The copy of the folder or file loses all permissions. |
Note What Happens When You Move a Ntfs-Protected File to a Fat Volume?
If you’re moving a file or folder from NTFS to a non-NTFS partition, such as a FAT volume, all NTFS file and folder permissions will be lost because FAT does not support NTFS file and folder permissions. Only Creator Owners and users with the Modify permission (and administrators) can perform this task because they have permission to move files and folders. When moving files to a FAT volume, the process involves saving the object onto the new file system, losing the original NTFS permissions in the process, and then deleting the original object.
When you copy a file or folder within the same volume or between volumes, the user must have Read permission for the source folder and Write permission for the destination folder.
When you move a file or folder within the same volume or between volumes, you need to have both Write permission for the destination folder as well as Modify permission for the source file or folder. This is because Windows 10 will move the resources (Write) and then delete (Modify) the resources from the source folder once it has completed the copy to the destination folder.
View Effective Access
You might be required to calculate the access that a user has to a resource. Within the Advanced options of an object’s Security settings, you will find the Effective Access tab (previously called Effective Permissions) as shown in Figure 2-18. When setting permissions in a corporate environment you should verify that NTFS permissions are applied correctly and use the Effective Access feature to ensure that the results are as expected.
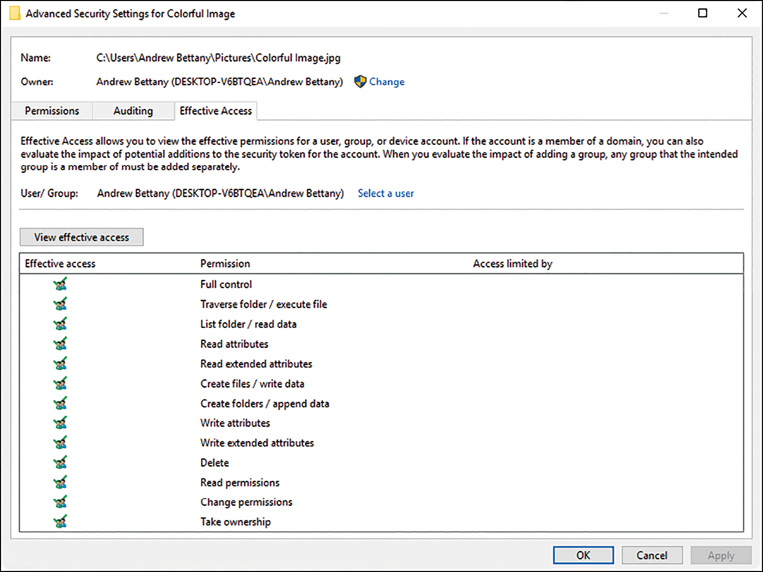
For example, for a resource, if you assign a user the Read permission and assign the Modify permission to a group that the same user is a member of, the effective access permissions are a combination of the Read permission and Modify permission, which is Modify permission.
When you combine permissions that include Deny permissions, NTFS will evaluate the Deny permissions before the Allow permissions that are set on the same resource with explicit Deny taking precedence over all Allow permissions.
If Deny and Allow permissions are set at different levels within a folder structure, or nested within each other—for example, if Deny is set at the top-level folder and an Allow permission is set at its subfolder—Allow can take precedence and override Deny because the Allow permission is explicit and not implicit.
When assigning permissions to several groups, remember that the security settings have a cumulative effect; you should review the effective permissions obtained for the user by following these steps.
Open Windows Explorer.
Navigate to the file or folder whose effective permissions you want to view.
Right-click the file or folder, click Properties, and click the Security tab.
Click Advanced and then click the Effective Access tab.
Next to the User/Group, click Select A User.
On the Select User Or Group dialog box, click in the Enter The Object Name To Select (Examples) box, enter the name of a user or group, and then click OK.
Click View Effective Access.
You should now see the detailed effective permissions of the user or group for that file or folder.
Be careful when using the Effective Access tool and reviewing permissions on folders that you own since the permissions given to the Creator Owner of the object are not taken into account.
Take ownership of resources
It is possible to remove access to a particular user or group on an object, such as a folder. Sometimes, this happens accidentally when configuring permissions, but typically, it will happen when the user who originally created the resource leaves the organization and the resource is then said to be “orphaned.”
In the Advanced Security Settings dialog box for an object, you will find the Effective Access tab and at the top of this screen, as shown in Figure 2-18, is an option to change the object owner. So long as you have administrative privileges, you can take ownership of the object and allocate it to another user or group. You can reset the permissions of all the folders, files and subfolders using the command-line tool icacls <file name> /reset, using an elevated command prompt.
Resolve NTFS permission issues
The type of security that can be configured on Windows 10 is determined by the file system in place. NTFS is the default underlying file system and it offers several security options, but you may also encounter removable drives or legacy systems that use FAT16, FAT32, or exFAT, which offer less security.
It has been several years since NTFS was established as the default file system of choice for all recent Windows client and server operating systems. NTFS file permissions offer administrators a very powerful tool for granting, controlling, auditing, and denying access to resources. Unlike share-level permissions, NTFS operates at the file level, which means NTFS permissions are applicable to resources shared over a network or accessed locally.
When troubleshooting resource access issues, you need to determine the following:
Is the file system in NTFS?
Are the files and folders being accessed locally or over the network?
It is easy to test if the file system is using NTFS by checking to see if there is a security tab on the volume on which the resource resides, as shown in Figure 2-19. The Security tab relates to NTFS permissions.

NTFS permissions can be complex and sometimes difficult to manage, especially for a junior or inexperienced administrator. Often the most challenging environment is one in which a newly hired administrator must adopt an enterprise, which has an existing problematic NTFS permission infrastructure in place that has very little documentation. Required small changes can sometimes have unintended consequences, which pose security risks. The role of the system administrator is to optimize data security, and to make sure that data is accessible to the right users. If users are denied access to files to which they have rights or given access to privileged files, it is a major problem that needs immediate remediation.
Note New Versus Legacy Folder Structure
Sometimes when adopting an existing NTFS permission infrastructure, it is better to design and recreate the file and folder permission structure rather than adopt a legacy environment.
NTFS permissions are cumulative, which means a user may have been given various group memberships as well as explicit permissions to resources that they are able to access. If a user has not been given any implicit or explicit permissions, they will not have access. If a combination of permissions for a resource has been set, you’ll need to calculate the cumulative effect of all permissions.
Faced with an issue resulting from lack of access or over privilege, you need to start troubleshooting the problem by determining the effective permissions for the files or folders in question. Establish the scope. For example, who does this problem affect, and is it confined to a single user or a group of users? Establishing the effective permissions will allow you to quickly determine permissions that apply and provide you with a starting point.
User-effective permissions are based on the total of all permissions that they have been granted or denied. Take special care to look for any Deny permissions because these are infrequently set. However, when Deny permissions are set, they are very powerful because any explicit Deny permission will have precedence over Allow entries.
![]() Exam Tip
Exam Tip
The Sharing tab shown in Figure 2-20 will only be visible if you are viewing the effective permissions for a shared folder.
Real World Document All Changes
The best practice when configuring NTFS permissions is to document a plan for how the NTFS permissions will be applied to the predefined users, groups, and folders. Ensure that all new users, groups, and folders are created according to the plan, and then apply NTFS permissions to this structure. Once the NTFS plan has been created, repeat for the Share permissions. Once permissions have been configured, continue to the testing phase where you perform tests for selected users to establish whether their effective access to resources matches the intended objectives of the plan. Over time, your NTFS change log will extremely useful when troubleshooting NTFS access issues.
Configure shared permissions
Data is often shared in an organization, perhaps within a team for project work or between you and your boss. You must know how this can be achieved in Windows 10 within a networked environment, whether that is at home or in a larger workplace network. You must be able to manage shared files and printers.
File and printer sharing is disabled by default, and it is automatically turned on when you share the first folder on a Windows 10 device. If you want to configure this setting manually, you can do so in the advanced sharing settings in the Network And Sharing Center in Control Panel.
Another consideration is that when sharing is enabled, the Windows Defender Firewall is automatically configured to allow users to access shares on a computer in the network. This is a potential security risk. Although the firewall settings are configured automatically when you first share a folder, they are not returned to their default status even if you remove all shared folders.
Configure folder shares
When you share a folder, other users can connect to the shared folder and its contents across the network. Shared folders available on the network are no different from normal folders, and they can contain applications, corporate data, or private data. Be careful when creating a network share, to ensure that you do not accidentally provide access to a user or group of users who should not have access. By default, everyone on the network is given read access to the share, although you can change this setting.
Normally, a shared folder is located on a file server, but in a small network environment, the sharing can be located on a Windows 10–based computer or network-attached storage (NAS) device. When choosing the device or server, the resources should be available whenever the users need them and, often, this means the server is always on.
By providing a central location for shared folders to reside on, you enable the following features.
Simplification of management
User familiarity
Ease in backing up data
Consistent location and availability
When a user tries to use resources accessed on a shared folder, the access permissions are determined by taking into consideration both the share permission and the NTFS security permissions. The most restrictive set of permissions prevail to the user.
Ensure that you do not create shared folders where the share permissions (SMB) become the primary access security mechanism. They are more restrictive than the NTFS permissions because users gaining access to the resource locally or by logging on through Remote Desktop would completely bypass SMB permissions. It is therefore essential for NTFS permissions to be configured independently to protect the resource.
To allow access to a locally stored folder across a network, first share the folder. Files contained in folders are also shared, but files cannot be specifically shared independently, except from within a user profile.
Server Message Block
Shares are provided by the Server Message Block (SMB) application-layer network protocol and not by NTFS. You can see what version of SMB your Windows 10 operating system is using by following these steps.
Sign in to your computer by using an administrative user account.
Open File Explorer and navigate to a shared or mapped folder on the network so that the shared files are visible in the right navigation pane.
On the File Explorer menu, click File and then click Open Windows PowerShell As Administrator.
Accept UAC if prompted.
Type the Windows PowerShell cmdlet Get-SmbConnection.
Windows PowerShell should report the SMB version (dialect) in use, as shown in Figure 2-20.
Figure 2-20 Windows 10 SMB version
Need More Review? Smb 3.0 Overview
This Microsoft resource, although focused on Windows Server 2016 and SMB 3.0, is useful to obtain more information relating to the benefits of using the latest version of SMB compared to previous versions. Visit https://docs.microsoft.com/windows-server/storage/file-server/file-server-smb-overview.
Configure Network Discovery
The network discovery feature was introduced in Windows Vista and uses a new layer 2-level protocol called Link Layer Topology Discovery (LLTD). It allows Windows to identify other devices present on the local subnet and, when possible, establish the quality of service (QoS) bandwidth capabilities of the network.
Knowing what is on the network increases the communication between devices. One downside of this increased awareness capability is that the firewall security settings are slightly relaxed. This means that not only does your computer see other network computers and devices, it also becomes discoverable on the network by other Windows clients.
![]() Exam Tip
Exam Tip
Administrators working in a domain environment can manage the settings of the two network discovery settings, LLTD Mapper (LLTDIO) and Responder (RSPNDR), in Group Policy settings. The Group Policy settings can be found here: Computer Configuration\Policies \Administrative Templates\Network\Link Layer Topology Discovery.
Network discovery is tightly linked to network location profiles and to Windows Defender Firewall configuration. As we have seen, by default, network discovery is enabled for devices connecting to networks that are assigned the Domain or Private network location profile, but network discovery is disabled on public networks.
To change network discovery settings, from the Network And Sharing Center, click Change Advanced Sharing Settings. As shown in Figure 2-21, you can then configure network discovery for each network location profile.

Create a Share by Using the Shared Folders Snap-In
You can create and manage file shares centrally on your computer by using the Shared Folders snap-in, which can be loaded into an empty Microsoft Management Console (MMC), or the snap-in found in Computer Management.
When you create a new share in the Shared Folders snap-in, the Create A Shared Folder Wizard appears and guides you through specifying the folder path, share name, description, and other settings, as shown in Figure 2-22.
By default, the share name will be the same as the folder name, and permissions for the share are set at read-only access for the Everyone group, but you can choose other options or full customization by completing the underlying Share Permissions discretionary access control list (DACL) page.
The Shared Folders snap-in enables you to view existing shares and modify their properties, including settings such as offline file status, share permissions, and even the NTFS security permissions.
![]() Exam Tip
Exam Tip
To launch the Create A Shared Folder Wizard directly from a command prompt, use Shrpubw.exe.
Share Folders by Using File Explorer
There are multiple methods of sharing a folder using File Explorer including
Use the Share With option, found on the Share tab on the ribbon bar (also called Network File And Folder Sharing).
Select Advanced Security from the Share tab on the ribbon bar.
Use the Sharing tab in the Properties dialog box.
Use the Give Access To context menu by right-clicking a folder to be shared.
All the methods present you with slightly different GUIs and wizards from which to choose the sharing options. Although they all result in sharing folders that can be accessed across the network, the main difference between each method is the speed and simplicity that some offer the novice.
In practice, most home users and small businesses prefer to use the sharing wizards found on the ribbon bar, but more experienced users seek the advanced level of control that can be gained through the Sharing tab in the Properties dialog box.
![]() Exam Tip
Exam Tip
Review the options for configuring shares and pay attention to the limitations of the wizard-based methods. The wizards configure the file system permissions automatically, based on the limited choices they present.
The Share tab in File Explorer enables you to launch the File Sharing Wizard and provides the same functionality as the Share With shortcut menu. Next to this is Advanced Security, which enables you to fine-tune the sharing beyond the limitations of the File Sharing Wizard.
When you configure basic sharing permissions, you have one of two simplified options.
Read Users and groups can open but cannot modify or delete files.
Read/Write Users and groups can open, modify, or delete a file and modify permissions.
After you create a share, all users see the share name over the network. Only users who have at least the Read permission can view its content.
Note Administrators Can Share Files and Folders
To share a file or folder across the network in Windows 10, you must be a member of the Administrators group or provide UAC credentials for an administrator.
Share Folders from the Command Prompt
The command prompt enables you to share a folder by using the net share command. To create a simple share, you would use the following example.
net share MyShareName=c:\Temp\Data /remark:"Temp Work Area"
This command shares the C:\Temp\Data folder with the share name MyShareName and includes a description of Temp Work Area.
You must have administrative privileges to create a shared folder by using Net Share.
Review the additional command-line options that you can use with Net Share, as shown in Table 2-11.
Table 2-11 Net Share command-line options
Option |
Description |
|---|---|
/Grant:user permission |
Enables you to specify Read, Change, or Full Share permissions for the specified user |
/Users:number |
Enables you to limit the number of users who can connect to the share concurrently (default and maximum for Windows 10 is 20 users) |
/Remark:“text” |
Enables you to add a description to the share |
/Cache:option |
Enables you to specify the offline files caching options for the share |
sharename /Delete |
Enables you to remove an existing share |
Note Sharing Caution
The Net Share command will not create a folder and share it. You can only share folders that already exist on the computer.
Share Folders by Using Windows Powershell
If you need to script the creation of shares, Windows PowerShell is the most appropriate choice and provides several cmdlets that enable you to manage shares in Windows 10. Windows PowerShell offers more in both scope and functionality than Net Share and will continue to expand in the future.
An example command for creating a share is:
New-SmbShare -Name MyShareName -Path c:\Temp\Data
Other Windows PowerShell cmdlets used in the administration of shares are shown in Table 2-12.
Table 2-12 Windows PowerShell Share cmdlets
Cmdlet |
Description |
|---|---|
Get-SmbShare |
Lists the existing shares on the computer |
Get-SmbShareAccess |
Lists the access control list of the SMB share |
New-SmbShare |
Creates a new SMB share |
Set-SmbShare |
Modifies the properties for an existing share |
Remove-SmbShare |
Deletes an existing share |
Grant-SmbShareAccess |
Sets the share permissions on an existing share |
Get-SmbShareAccess |
Lists the current share permissions for a share |
Note Multiple Shares
Sometimes you might want to provide different groups access to the same shared resources. You can share the same folder multiple times and use a different share name and share permission settings for each instance. Each group should only be able to access the share that they have permission for.
Share Files by Using File Explorer
Files typically cannot be shared without first sharing the parent folder. In Windows 10, files that reside in the user profile, such as Documents, Downloads, and Pictures folders, can be shared. To do this, follow these steps.
Sign in to your computer using an administrative user account.
Open File Explorer and navigate to the user profile.
Right-click a file, such as Pictures, in the user’s profile.
Select Give Access To Specific People, as shown in Figure 2-23.

Figure 2-23 Share, using the sharing wizard In the Choose People To Share With dialog box, type a user or group and click Add.
Set Permission Level to Read or Read/Write and click Share.
Note that you are sharing. The File Sharing Wizard completes, and the files are shared.
Optionally, you can use the links in the File Sharing Wizard to send someone the links to the shares.
Click Done.
You can also share a file using the Share icon on the Share ribbon bar. Select the file or multiple files and then click Share on the ribbon bar, as shown in Figure 2-24.
The Share option is also available within other apps including Microsoft Edge. The set of targets, including contacts and other apps will depend on which apps are installed on your device and offer a simplified method of sharing files quickly and with minimum effort.
Configure shared folders permissions
Permissions that are set on the share determine the level of access a user has to the files in the share. They can be set on FAT or later file systems. When you use the NTFS file system, be careful not to restrict access at the share level, because this might affect the effective permissions. You can configure the permissions when you share a folder and set a level that the user or group will have when they connect to the folder through the share across the network.
Sharing permissions have three options:
Read Users and groups can view the files, but they cannot modify or delete them.
Change Users and groups can open, modify, delete, and create content, but they cannot modify file or folder permissions; the Change permission incorporates all Read permissions.
Full Users and groups can perform all actions, including modifying the permissions; the Full permission incorporates all Change permissions.
Unlike in earlier versions of Windows, there is no longer a visual icon or indicator in File Explorer to distinguish whether a folder is shared. All shared folders on your device appear in the Shared Folders node of the Computer Management console. You can also view the shared folders that exist on your device by using the Get-SmbShare Windows PowerShell cmdlet or by typing net view \\localhost /all at the command prompt.
After a user has found the share in File Explorer, they can access the files directly. Another common way that users can connect to a shared folder over the network is by using the shares Universal Naming Convention (UNC) address. UNC addresses contain two backward slashes (\\) followed by the name of the computer that is sharing the folder and the shared folder name; for example, the UNC name for the Marketing shared folder on the LON-DC1 computer in the Fabrikam.com domain would be:
\\LON-CL1.Fabrikam.com\Marketing
Troubleshoot Share Permission Issues
Share permissions can cause many problems when troubleshooting access to files and folders. You need to remember that Share permissions work together with NTFS permissions and that the most restrictive permission will apply. Another common cause of confusion is that Share permissions only affect shared resources over the network.
If your file system is configured with FAT or FAT32, there is no option to configure NTFS permissions. If no Security tab is available in the resource Properties dialog box, we know that it cannot be formatted with NTFS, and the file system is likely to be FAT/FAT32, as shown in Figure 2-25.

If you need to confirm the file system in use, you can view the properties of the drive by following these steps:
Open File Explorer and right-click the drive that is under review.
Select Properties.
On the General tab, view the File System.
Click OK to close the dialog box.
Combine Ntfs and Share Permissions
Within a corporate environment, administrators share files over the network, using Share permissions. If the volume is formatted with NTFS, there are likely to be NTFS permissions configured on the shared file as well. To fully understand the effects of these two sets of permissions, you will need to combine them.
When combining share and NTFS permissions, restricting access to resources across the network can be easy. By accepting the default share permissions, you provide standard users with read-only access even if NTFS permissions are less restrictive.
Unfortunately, there is no wizard to diagnose which restrictions are in effect, but you can use the Effective Permissions feature in NTFS to determine the permissions being applied to a specific user or group (Principal).
NTFS is all about rules, and they are applied thoroughly by the file system. Wrongly applied settings, often combined with default inheritance, can instantly spread an incorrectly configured setting across hundreds of files. Unlike most computer operations, there is no undo option.
When troubleshooting access, always look for the most restrictive permission that has been set and evaluate whether this is being applied. If necessary, you can view the effective permissions. If the most restrictive permission is not being applied when the resource is being accessed, you need to determine the problem. Some other permission must be overlapping and affecting the resource; perhaps the user is a member of the Administrators group or another group that has full control permissions? You can also test what permissions are effective both at the local access level as well as when accessing the resource over the network share.
Often, the cause of many permission-based issues when troubleshooting file and folder access is that the Share permissions being applied on the share are too restrictive. It is preferable to use the more powerful NTFS permissions because these will always be effective, regardless of how they are accessed (over the network share or locally).
Reset Share and Ntfs Permissions
If you simply cannot decipher which NTFS settings are creating the problems, or if the problems are too complex or widespread, you can try to reset the file and folder permissions by using the ICACLS command-line utility.
This is especially useful if you get locked out of files and folders because of incorrect or deleted NTFS permissions.
To reset permissions using ICACLS, follow these steps.
Sign in to your computer using an administrator user account.
Open File Explorer and navigate to the folder that is giving you the problems.
On the File Explorer menu, click File > Open Windows PowerShell As Administrator.
Accept the UAC prompt, if prompted.
Type icacls * /RESET /T /C /Q.
The process of resetting files and folders to their default settings is very quick. After the original operating system defaults have been applied, you can configure the desired settings.
Skill 2.3: Configure devices by using local policies
In this section, you review how the Windows 10 registry can be used to configure computer settings that may not be available within the Settings app or Control Panel.
Group Policy is a key technology designed to help manage and control how users use Windows 10–based computers. Local Group Policy is the local implementation of these policies and you need to understand how to configure local settings on your computer using polices.
Finally, in this skill, you will review how to troubleshoot group policies on a computer to identify what policies are effective and how to resolve issues. Some of the tools used to fix policy issues on a local computer can be directly applied to domain joined devices, and this knowledge is valuable if you must apply the same type of settings to thousands of computers in a domain environment.
Configure Local Registry
All settings within Windows 10 are ultimately stored in the Windows Registry. This is a database that contains details of all Windows settings, installed software, device drivers, and much more. Without the registry, Windows would not work.
Every reference to working the registry always stipulates that you should take great care when working with or editing the registry. An incorrect registry change can prevent your system from booting and can result in you needing to completely reinstall the operating system. You should always take care and create a system backup before editing the registry.
Understanding the registry structure
The registry is a database that is split into multiple separate files known as hives, together with associated log and other support files.
You can find the registry files located in the %systemroot%\System32\Config\ though you will need to be an administrator to access this folder. Within this system folder, you should find several binary format “files” that the registry uses:
SAM (Security Accounts Manager used to store local passwords)
SECURITY
SOFTWARE
SYSTEM
DEFAULT
USERDIFF (used only for Windows upgrades)
In addition to the system files the user-specific settings are stored within the user profile and are loaded into system memory when a user signs in. These registry files are located in the following locations:
%userprofile%\ntuser.dat
%userprofile%\AppData\Local\Microsoft\Windows\UsrClass.dat
Other notable registry files include the Boot Configuration Data (BCD) store which stores its own file on the boot drive. The local services are located in %SystemRoot%\ ServiceProfiles\LocalService and network services are stored in %SystemRoot%\ServiceProfiles\NetworkService.
The vast majority of changes to the hive files are made automatically by Windows whenever you install an application, or change a setting or configuration by using the Settings app or Control Panel.
The main hives, or subtrees which store settings for Windows 10 are shown in Table 2-13.
Table 2-13 Registry Hives
Hive |
Description |
|---|---|
HKEY_CLASSES_ROOT |
This hive relates to file association information relating to applications installed in the device. For example, it defines that the application for .docx files is Microsoft Word. This hive contains application information from derived from the settings that are stored in the HKEY_LOCAL_MACHINE\Software\Classes and HKEY_CURRENT_USER\Software\Classes hives. |
HKEY_CURRENT_USER |
This hive contains information for the signed-in user. Personalized settings such as background image, Windows color scheme, and font settings are stored in this hive. |
HKEY_LOCAL_MACHINE |
This hive stores computer-related configuration settings. |
HKEY_USERS |
This hive contains user-related configuration settings for all users who have signed in locally to the computer, including the currently signed-in user. The HKEY_CURRENT_USER hive is a subkey of HKEY_USERS. Edits to this hive will affect the user settings for the currently signed-in user. |
HKEY_CURRENT_CONFIG |
This hive contains current hardware profile information for the local computer. |
Should you need to make a manual change, create a new entry, or modify an existing registry entry, these will typically take place in the following two hives:
HKEY_LOCAL_MACHINE
HKEY_CURRENT_USER
The primary tool for managing and editing the registry is the built-in registry editor.
Within the hives, settings containing values are stored in subtrees, keys and subkeys. The hierarchical nature of the registry makes it easy to locate a registry value. An example of a key, subkeys, and value would be
Computer\HKEY_CURRENT_USER\Control Panel\Mouse
This key holds many subkeys, which Windows uses to store settings for the mouse.
The mouse settings can be modified in the registry, as shown in Figure 2-26, or by using the Mouse item within the Control Panel. If you enable mouse pointer trails in the Control Panel, the registry subkey for MouseTrails is modified to have a value of 7.
Values are stored within each key and subkey that are used to configure the operating system. There are several value types which are used to store information such as numerical data, text, and variables such as file paths. Often a value is empty or not defined as shown in the (Default) subkey in Figure 2-26. Table 2-14 lists more common types of registry values.
Table 2-14 Registry Value Types
Value Type |
Data Type |
Description |
|---|---|---|
REG_BINARY |
Binary |
Raw binary data. Values are normally displayed in hexadecimal format. Hardware information is often stored in these values. |
REG_DWORD |
DWORD |
4-byte numbers (a 32-bit integer). Device-driver and service-related values are stored in these values. |
REG_SZ |
String |
A fixed-length text string. Most of the values listed in the \HKEY_CURRENT_USER\Control Panel\Mouse keys are REG_SZ values. |
REG_EXPAND_SZ |
Expandable string |
A variable length text string. Windows uses REG_EXPAND_SZ values to contain variables, such as file system paths. |
REG_MULTI_SZ |
Multiple strings |
Multiple string values. These values are typically used when multiple values are required. |
Understanding the Registry Editor
The built-in Registry Editor (Regedit.exe) allows you to view, search, and modify the registry’s contents. Some of the common tasks that administrators can perform using the Registry Editor tool include
Search the registry for a value, value name, subkey, or key
Create, delete, and modify keys, subkeys, and values
Import entries into the registry from an external (.REG) file
Export entries from the registry into an external (.REG) file
Back up the entire registry
Manage the HKEY_LOCAL_MACHINE and HKEY_USERS registry hives on a remote computer
You can also import registry keys and values directly into the registry using a text file with the .REG extension.
All .REG files will use the following syntax for Registry Editor to understand them:
Windows Registry Editor Version 5.00 [<Hive name>\<Key name>\<Subkey name>] "Value name"=<Value type>:<Value data>
Because .reg files are associated with the registry, executing a .REG file will merge it with—or import it to—the local Windows Registry. The contents of the .REG file will add, delete, or modify one or more keys or values in the registry. Depending on the changes contained within the .REG file, you might need to restart your computer after the changes have been made.
You can also use the import option on the file menu within the Registry Editor to import the settings, or you can use the command line with a script similar to the following example:
regedit /s C:\\Registry\\regsetting.reg \> nul
Using PowerShell to manage registry settings
The registry can be accessed directly using Windows PowerShell. The registry provider within PowerShell displays the registry like a file system, displaying the keys and subkeys as subfolders within a registry hive.
Windows PowerShell uses the abbreviated form of the hive nomenclature where the HKEY_LOCAL_MACHINE hive becomes HKLM and HKEY_LOCAL_USER becomes HKLU.
To view the registry using Windows PowerShell, open an elevated Windows PowerShell command prompt and then type the following, pressing Enter after each line.
Get-ChildItem -Path hklm: Dir
You can also obtain a richer output by using this PowerShell command:
Get-Childitem -ErrorAction SilentlyContinue | Format-Table Name, SubKeyCount, ValueCount -AutoSize
To create a new registry key, you can first use the Set-Location cmdlet to change to the appropriate registry subtree and key as shown here:
Set-Location "HKCU:\Software"
Alternatively, you can use the full path to the registry key in the cmdlet as follows:
New-Item -Path HKCU:\Software -Name "Demonstration" –Force
Use the following cmdlet to assign the new registry key a value of “demo”:
Set-Item -Path HKCU:\Software\Demonstration -Value "demo"
To validate that the key value has been stored correctly, view the key in the registry, or type:
Get-Item -Path HKCU:\Software\Demonstration
Implement local policy
Local Security Policy allows you to configure various security policies on a local computer. The computer may or may not be domain joined. When used in a domain-based environment, local policies can be used to affect all computers in the domain. Only the Windows 10 Pro, Enterprise, and Education editions provide access to the Local Security Policy console. For Windows 10 Home edition, the settings and rights are predefined and unchangeable.
With Local Security Policy, you create rules so that you can manage users’ computers. You can apply configuration settings that can affect a single device when deployed using the Local Group Policy Editor. When settings are configured using Group Policy within a domain environment, the settings can be deployed from one to thousands of targeted devices. When a policy has been configured, standard users cannot modify a managed policy setting.
Local Security Policy is a subset of the Local Group Policy Object Editor (gpedit.msc). You can also see the same settings by using the dedicated tool called Local Security Policy Editor, as shown in Figure 2-27. To launch the tool, follow these instructions:
Log onto Windows 10 with administrative privileges.
Click Start and search for Secpol.msc.
Click the Secpol.msc link to open the Local Security Policy Editor.
Expand both Account Policies and Local Policies.

Within Local Security Policy, you can find the following sections:
Account Policies These include local account Password Policy and Account Lockout Policy. These allow you to configure the device password history, maximum and minimum password age, password complexity, and password length. You can also configure what action will be taken when a user enters an incorrect password during logon.
Local Policies These include Audit Policy, User Rights Assignment, and Security Options, and they allow you to enable/disable auditing, configure user rights (including the ability to log on locally to the device), access the computer from the network, and have the right to shut down the system. In this section, you will also find settings to configure many security settings, such as interactive logon settings, User Account Control settings, and shutdown settings.
Windows Defender Firewall with Advanced Security These are used to configure the local firewall settings.
Network List Manager Policies These enable you to configure whether users can configure new network properties, including the network name, location, and icon.
Public Key Policies These allow you to configure settings for Certificate Auto- Enrollment and the Encrypting File System (EFS) Data Recovery Agents.
Software Restrictions Policies These are used to identify and control which applications can run on the local computer.
Application Control Policies These are used to configure AppLocker.
IP Security Policies on Local Computer These allow you to create, manage, and assign Internet Protocol Security (IPsec) policies.
Advanced Audit Policy Configuration These allow you to provide additional fine tuning and control when using audit policies.
Configuring a password policy
On a local device, if you want to ensure that all users use secure passwords and that the passwords are changed after a set number of days, you can configure a password policy as follows:
Log onto Windows 10 with administrative privileges.
Click Start and search for Secpol.msc.
Click the Secpol.msc link to open the Local Security Policy Editor.
Expand Account Policies and click Password Policy.
Double-click Enforce Password History. You can now enter a value that represents the number of unique new passwords that a user account must have used before an old password can be reused.
Enter 5 and click OK to set this policy.
Double-click Maximum Password Age. The default setting is 42, which allows a user can use their password over a 42-day period before they are forced to change it. The best practice is to have passwords expire every 30 to 90 days.
Enter 90 and click OK.
Double-click Minimum Password Age. The default setting is 0 days, which allows users to change their passwords whenever they like. A setting of 14 days prevents users from changing their password in rapid succession to bypass the password history setting.
Enter 14 and click OK.
Double-click Minimum Password Length. The default is set to 0 characters. A setting of 8 would require that a password must be at least 8 characters long.
Enter 8 and click OK.
Double-click Password Must Meet Complexity Requirements. This setting is disabled by default. Once set to enabled, all passwords need to be complex.
Double-click Store Passwords Using Reversible Encryption. The default is disabled. If you enable this policy, all passwords are stored in a way that all applications are able access the password, which also makes them vulnerable to hackers to access.
Close the Local Security Policy editor.
The changes relating to local passwords become effective immediately once the policy is configured. Users with existing passwords can continue to use them until they need to be changed. The next time a user changes his or her password, the new password will need to conform with the settings in the Password Policy.
Note Password Must Meet Complexity Requirements
When the Password Must Meet Complexity Requirements policy is enabled, passwords must meet the following minimum requirements:
Must not contain the user’s account name or parts of the user’s full name that exceed two consecutive characters
Must be at least six characters in length
Must contain characters from three of the following four categories:
English uppercase characters (A through Z)
English lowercase characters (A through Z)
Base 10 digits (0 through 9)
Nonalphabetic characters (for example, !, $, #, %)
Complexity requirements are enforced when passwords are changed or created.
Configuring an account lockout policy
When you implement a strong password policy, it is recommended that you also configure account lockout policy, which helps to protect accounts from password-cracking tools, which can attempt thousands of different passwords every hour in the hope that they succeed. Within a local environment, even an employee can try to guess a password to gain access to a system.
This brute-force attack on a system cannot be prevented. However, you can implement measures within the Account Lockout Policy that monitor incorrect attempts to log in to a local device. If a brute-force attack is suspected (for example, five incorrect passwords are entered in quick succession), then the account can be locked for a period of time.
To define that lockout policy, use the following steps:
Log onto Windows 10 with administrative privileges.
Click Start and search for Secpol.msc.
Click the Secpol.msc link to open the Local Security Policy Editor.
Expand Account Policies and click Account Lockout Policy.
Double-click Account Lockout Threshold, enter 3, and click OK.
When the Account Lockout Threshold has been set, Windows suggests two other settings:
Account Lockout Duration This setting specifies how long, in minutes, the user account will remain locked once the threshold has been reached.
Reset Account Lockout Counter After This setting specifies how long, in minutes, before the count of incorrect passwords entered is set back to zero.
Leave these settings as recommended and click OK.
Configuring local policy
Local policies are used to control users once they have logged on and gained access to a system. You can configure policies that implement auditing, specify user rights, and set security options.
Audit Policy
Audit policies are used to track specified user actions on a device. These actions are recorded as a success or failure, such as accessing a file or being blocked from printing a document. Auditing is costly because system resources are required to constantly monitor a system and record actions to the audit logs. Audit settings can generate many log items, and this may impede a computer’s performance. Therefore, you should use auditing on selective actions and turn off the feature when it is no longer required.
Auditing allows you to create a history of specific tasks and actions, such as file access (Audit Object Access policy), user account deletion (Audit Account Management) or successful logon attempts (Audit Account Logon Events). Often, auditing is used to identify security violations that arise; security violations could include, for example, when users attempt to access system management tasks or files within File Explorer for which they do not have permission. In this example, failed attempts to access resources will be logged in the audit log, with details of the user account, time, and details of the resources for which access was denied because of insufficient privileges.
Configuring audit policy involves three components:
Enable auditing within Local Policies for success or failure (or both) for specific events or actions.
For object access, such as file system files and folders, enable auditing on the objects to be audited.
Use Event Viewer to view the results of the audit in the security log.
To view the various settings that can be configured using audit policy, view the audit policy options in Table 2-15.
Table 2-15 Audit policy options
Policy Description |
Description |
|---|---|
Audit Account Logon Events |
Tracks user logon activity on his local device or to a domain (if domain auditing is enabled). |
Audit Account Management |
Tracks user and group account management including creation, deletion, and password changes. |
Audit Directory Service Access |
Tracks access to Active Directory objects by a user within a domain. |
Audit Logon Events |
Audits events related to local account activity, such as running a logon script, accessing a member server, or a device that uses a local account to generate a logon event. |
Audit Object Access |
Enables auditing of access to the file system and registry objects, including files, folders, printers, hives, and values. |
Audit Policy Change |
Tracks any changes to user rights assignment policies, audit policies, or trust policies, such as assigning, removal, creation, changing, starting, or stopping policies. |
Audit Privilege Use |
Tracks each instance of when a user exercises a user right that has been assigned to her user account. |
Audit Process Tracking |
Tracks events whenever a program is activated, a new process is created or exited, or if a user attempts to install a service. |
Audit System Events |
Tracks system events, such as when a user shuts down or restarts his computer and when an event occurs that affects either the system security or the security log. |
To configure an audit policy to monitor account logon events, use these steps:
Log onto Windows 10 with administrative privileges.
Click Start and search for Secpol.msc.
Click the Secpol.msc link to open the Local Security Policy Editor.
Expand Local Policies and click Audit Policy.
Double click the Audit Account Logon Events policy and check the Success and Failure boxes.
Click OK.
Log off the device and attempt to log back on as an Administrator, but use an incorrect password. Allow the logon to fail.
Log on as an administrator using the correct password.
Click Start and search for Event Viewer.
Click the Event Viewer app to open the Event Viewer.
Expand Windows Logs and select the Security log.
You should see the audited events listed with an Event ID of 4776 and a Task Category of Credential Validation, as shown in Figure 2-28.
Figure 2-28 Review audited events within the Security Log
User Rights Assignment
The user rights policies are used to determine what rights a user or group of users have on a device. Often, there is confusion between rights and permissions, and you should be clear that user rights, or privileges, apply to the system and relate to activities or tasks that the user can perform.
Some of the activities that you can grant to a user include:
Add Workstations To Domain
Allow Log On Locally
Allow Log On Through Remote Desktop Services
Back Up Files And Directories
Change The System Time
Deny Log On Locally
Shut Down The System
Take Ownership Of Files Or Other Objects
To configure a user to have the right to perform a backup of a device, use the following steps:
Log onto Windows 10 with administrative privileges.
Click Start and search for Secpol.msc.
Click the Secpol.msc link to open the Local Security Policy Editor.
Expand Local Policies and click User Rights Assignment.
Double-click the user right Back Up Files And Directories.
Click the Add User Or Group button. The Select Users Or Groups dialog box appears.
Type the name of the user or group to which you want to grant the right or click the Advanced button and then select Find Now. Select the user or group of users within the list.
Click OK.
Click OK in the Select Users Or Groups dialog box.
In the Back Up Files And Directories Properties dialog box, click OK.
Note User Rights Assignment
A user may be given a right that could contradict any existing permissions. For example, if when a user is given the right to Back Up Files And Directories, the user can back up files and folders even if the user does not have specific NTFS-level permissions to the files or folders.
Remember, a right authorizes a user to perform specific actions on a device, such as logging on to a computer interactively or backing up files and directories on a system. Before leaving this section, you should review the list of user rights policies, which can be found within the User Rights Assignment node of the Local Policies.
Security Options
The Security Options section of the local policies includes many options, which are used to allow or restrict activities on the device.
Some of the activities that you can configure with Security Options include:
Accounts Block Microsoft Accounts
Interactive Logon Do Not Require CTRL+ALT+DEL
Interactive Logon Don’t Display Username At Sign-In
User Account Control Admin Approval Mode For Built-In Administrator Account
Nearly all the several dozen settings have their default settings set to Not Defined. Once configured, a setting can be have the following statuses:
Enabled or Disabled
Text entry (For example, a user account name, or a system path.)
Value (For example, the number of previous logons to cache for when a domain controller is not available.)
One area of the Security Options that you should pay attention to are the User Account Control (UAC) settings. We will cover UAC in detail in the next skill, but you should note that you can configure UAC using policy settings in this area of Local Policy.
![]() Exam Tip
Exam Tip
For the exam, you should know how to set local group policies and understand the purpose of account policies and local policies. Work through the examples showing how to configure password policies and account lockout policies. Review the various audit policies, user rights assignments, and security options that are available.
Troubleshoot group policies on devices
Diving deep into Group Policy would double the size of this book, but you should understand how to perform basic troubleshooting of Group Policies on Windows 10 devices.
Generally, when we refer to Group Policy, we are referring to Group Policy Objects (GPO) containing GPO settings that are created by IT administrators and pushed over the network to affect devices within a domain environment. Local policy, or Local Group Policy, refers to policy settings that are locally administered and configured.
Whatever the source of a GPO setting or group policy, sometimes, these can fail to apply. There can be many reasons for these failures, including incorrect GPO settings, poor network connection, or failure of the Group Policy Client service.
Troubleshooting Tools
You can use many tools to investigate GPO-related issues, including the Resultant Set of Policy (RSoP.msc) tool within the GUI and Group Policy Result (GPResult) from the command line.
Connection Issues
There are several preliminary troubleshooting areas that you should verify before proceeding to use the specialist GPO tools. These relate to the essential services, network connection, and time synchronization.
Group Policy Client Service Before troubleshooting group policy, you should verify the status of the required services for GPO. Check that the Group Policy Client service has the status of Running or Automatic within the Services utility.
Network Connection Verify the network connection and configuration. This can be achieved by running the Network Adapter troubleshooter within the Settings app to find and fix issues automatically. Without a reliable network connection, your device will not be able to connect to the domain controller and obtain group policy.
Time The device time needs to be within five minutes of the time on the server. If there is more than a five-minute time difference, then problems with Active Directory synchronization can occur, which can then affect GPO delivery.
Resultant Set of Policy Tool
The Resultant Set of Policy (RSoP) tool is a diagnostic tool that is used to check and troubleshoot group policy settings. RSoP is built into Windows 10 and can be used to view the policies being applied to users and devices, and it can identify where the policy settings are coming from. It can also be used to simulate GPO settings for planning purposes.
There are two modes in which RsoP can be run: Logging Mode and Planning Mode.
Logging Mode Generates a report on policy settings for users and computers and is used to verify and troubleshoot group policy settings.
Planning Mode Used for “what if” scenarios, such as: If a user or computer is moved to a different Active Directory AD group, will they still receive the expected GPOs?
To run RSoP to determine computer and user policy settings, perform these steps:
Log onto Windows 10 with administrative privileges.
Click Start and type rsop.msc.
Click the rsop.msc link to open the Resultant Set of Policy tool.
RSoP will run and generate a report for the user and computer policy settings.
Review the policy settings that have been applied to the system by any Group Policy Objects that are in effect.
To verify that the policies that you have linked are being applied, you should compare the system results to those that are expected.
To simulate GPO policy settings, you can use the planning mode of the Resultant Set Of Policy tool. You would open the RSoP tool from Microsoft Management Console and add the Resultant Set Of Policy snap-in, follow the wizard, and select Generate Rsop Data while in Planning Mode.
Gpresult
The GPResult command line tool provides a powerful method of verifying what group policy objects are applied to a user or computer. The tool creates a report that displays what GPOs have been applied to a system and separates the results into the user and computer settings.
Follow these steps to display all GPOs that have been applied to a system:
Log on to Windows 10 with administrative privileges.
Right-click Start and select Windows PowerShell (Admin).
Confirm the User Account Control warning, if prompted.
Type gpresult /r and press Enter. You should see the RSoP data for your logged-in user and device.
The output of the gpresult /r command will display information, including:
The applied GPOs name(s)
Order of GPO application
GPO details and the last time group policy was applied
Domain and domain functional level
Which domain controller issued the GPO
Network speed link threshold
Which security groups the user and computer are a member of
Details of GPO filtering
You can fine tune the report to select only the user or computer GPOs by limiting the command scope as follows:
If you don’t want to see both User and Computer GPOs, then you can use the scope option to specify a user or computer.
To display GPOs applied to a specific user:
gpresult /r /scope:user
To display GPOs applied to a specific computer:
gpresult /r /scope:computer
To display GPOs applied on a remote computer, you can use the command:
gpresult /s Laptop123 /r
To generate an HTML report of the GPResult, as shown in Figure 2-29, you can use the command:
gpresult /h c:\GPOreport.html
Figure 2-29 Generate an HTML report using GPResult
Skill 2.4: Manage Windows security
In this section, you review how to keep Windows 10 secure by using features built into Windows. Devices and users need to be protected while online, and they rely on the built-in defense features, which provide resilience against ever-increasing threats.
You will review the Windows Security features and options that help maintain your device’s health and manage threat-protection settings.
You will also review how to use User Account Control (UAC) to help you control administrative privilege elevation in Windows 10 to reduce security risks.
Windows Defender Firewall provides a significant security barrier that helps isolate and protect Windows from external threats, and you will need to understand how to configure and maintain the firewall.
Finally, as a method of protecting data, you need to understand the various encryption methods available with Windows 10 and when to use encrypting file system and BitLocker.
Configure Windows Security
The Windows Security feature is an app accessible from within the Settings app that provides a single portal for users to control and view their device security, health, and online safety. The Windows Security section within the Settings app, as shown in Figure 2-30, contains an overview of the status of Windows security features, as well as links to other settings and support.

The Windows Security page in the Settings app provides a status report covering seven areas of security.
Virus & Threat Protection Monitor threats to your device, run scans, and get updates to help detect the latest threats.
Account Protection Access sign-in options and account settings, including features such as Windows Hello and Dynamic Lock.
Firewall & Network Protection Manage firewall settings and monitor network and Internet connections.
App & Browser Control Review and update settings for Windows Defender SmartScreen and configure exploit protection settings.
Device Security Review built-in security options that use virtualization-based security to help protect your device from attacks by malicious software.
Device Performance & Health View the status information about your device’s performance health.
Family Options Use features, such as Parental controls, that allow you to keep track of your kids’ online activity.
From the summary portal, you can review the color-coded status icons, which indicate the level of safety of the system:
Green The device is sufficiently protected, and there aren’t any recommended actions.
Yellow There is a safety recommendation that should be reviewed.
Red This is a warning indicating that something needs immediate attention.
From within the Settings app, you can launch the individual security elements, or launch the standalone Windows Security app by clicking the Open Windows Security button, shown previously in Figure 2-30.
Note Windows Defender Security Center
In previous versions of Windows 10, Windows Security is called Windows Defender Security Center.
When a Windows Security item requires action from the user, such as to update the virus and threat protection definitions, the shield icon within the notification area of the taskbar will show a red cross to indicate action is required.
The Windows Security app collects the status from each of the included security features and allows you to perform some configuration. As updates are collated by the Windows Security app, they will also trigger notifications through the Action Center.
It is possible to customize the view of the Settings app. Administrators can add support information about your organization in a contact card to the Windows Security app, as shown in Figure 2-31, and admins can hide entire sections of the app by using Group Policy. Hidden sections will not appear on the home page of the Windows Security app, and its icon will not be shown on the navigation bar on the side of the app.
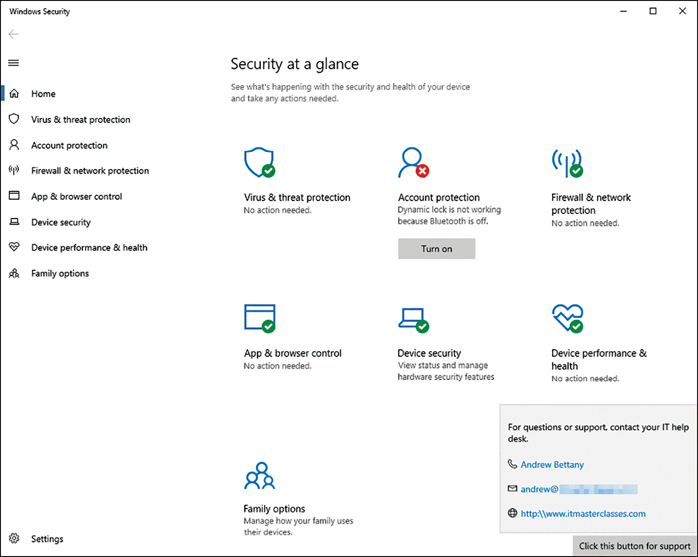
Need More Review? the Windows Security App
To review further details about configuring the Windows Security app, refer to the Microsoft website at https://docs.microsoft.com/windows/security/threat-protection/windows-defender-security-center/windows-defender-security-center.
Configure User Account Control
Once a user has gained access to the operating system following successful sign-on, the Windows 10 feature called User Account Control (UAC) prevents unauthorized changes to the system.
Systems that suffer from malware attacks can easily be compromised if the malware can effectively use administrative access and wreak havoc on the system. This creates extra work for the help desk, increases support costs, and reduces productivity. UAC has been very successful in preventing users and malware from using administrative credentials to harm a system.
With Windows 10, administrators no longer have “always on” full access to the system. Rather than enabling administrators to implement system-wide changes, UAC presents administrators with a challenge pop-up prompt to force them to confirm their actions. Similarly, a standard user who attempts to change system settings will receive a UAC prompt, which requires administrative credentials to be provided. If the proper admin credentials are not provided, the user is denied the ability to make the requested changes.
Since the introduction of UAC in Microsoft Vista, Microsoft has fine-tuned the UAC process with the aim of making the use of UAC less frustrating for all users by reducing the number of application and system tasks that require elevation.
UAC offers various layers of protection, with the UAC prompt being the most visible to the user. The following features complement UAC:
File and Registry Redirection
Installer Detection
UAC prompt
ActiveX Installer Service
Secure Desktop
Application Information Service
Note Access Denied
For UAC to function properly, the Application Information Service component must be running. If this service is stopped or disabled, applications that require administrative access will not be able to request UAC elevation and therefore will not launch, resulting in Access Denied errors.
Standard users
Except for administrators, all users are standard users with few privileges and limited ability to make changes to the system, such as installing software or modifying the date and time. Standard user accounts are described as “operating with least privilege.” The list of system tasks that a standard user can perform include:
Change the desktop background and modify display settings
View firewall settings
Change the time zone
Add a printer
Change their own user account password
Configure accessibility options
Configure power options
Connect to a wireless or LAN connection
Install drivers, either from Windows Update or those that are supplied with Windows 10
Install updates by using Windows Update
Use Remote Desktop to connect to another computer
Pair and configure a Bluetooth device with the device
Perform other troubleshooting, network diagnostic, and repair tasks
Play CD/DVD media
Restore own files from File History
View most settings, although the elevated permissions will be required when attempting to change Windows settings
UAC prevents you from making unauthorized or hidden (possibly malware-initiated) changes to your system that require administrator-level permissions. A UAC elevation prompt is displayed to notify you, as follows:
Prompt For Consent This is displayed to administrators in Admin Approval Mode whenever an administrative task is requested. Click Yes to continue if you consent.
Prompt For Credentials This is displayed if you are a standard user attempting to perform an administrative task. An administrator needs to enter her password into the UAC prompt to continue.
When an administrator provides permissions to a standard user via a UAC prompt, the permissions are only temporarily operative, and the permissions are returned to a standard user level once the isolated task has finished.
Standard users can become frustrated when they are presented with the UAC prompt, and Microsoft has reduced the frequency and necessity for elevation. Following are some common scenarios wherein a standard user would be prompted by UAC to provide administrative privileges. You will see that they are not necessarily daily tasks for most users:
Add or remove a user account
Browse to another user’s directory
Change user account types
Change Windows Defender Firewall settings
Configure Windows Update settings
Install a driver for a device not included in Windows or Windows Update
Install ActiveX controls
Install or uninstall applications
Modify UAC settings
Move or copy files to the Program Files or Windows folders
Restore system backup files
Schedule Automated Tasks
Administrative users
Administrative users need to be limited to authorized personnel within the organization. In addition to the ability to perform all tasks that a standard user can perform, they also have the following far-reaching permissions:
Read/Write/Change permissions for all resources
All Windows permissions
From this, it looks like administrators have considerable power, which can potentially be hijacked by malware. Thankfully, by default, administrators are still challenged with the UAC prompt, which pops up when they perform a task that requires administrative permissions. However, they are not required to re-enter their administrative credentials. This is known as Admin Approval Mode.
A user who signs on to a system with administrative permissions will be granted two tokens:
The first token enables him or her to operate as a standard user.
The second token can be used when the administrator performs a task that requires administrative permissions.
Just as with the standard user, after the task is completed using elevated status, the account reverts to a standard-user privilege.
Note Turning off Uac is not Recommended
UAC helps prevent malware from damaging PCs and should not be turned off. If UAC is turned off, all Universal Windows Platform apps will stop working.
Types of elevation prompts
UAC has four types of dialog boxes, as shown in Table 2-16. The Description column explains how users need to respond to the prompt.
Table 2-16 UAC elevation prompts
Type of Elevation Prompt |
Description |
|---|---|
A Windows 10 setting or feature needs your permission to start. |
This item has a valid digital signature that verifies that Microsoft is the publisher of this item, and it is usually safe to use the application. |
A non-Windows 10 application needs your permission to start. |
This application has a valid digital signature, and it is usually safe to use the application. |
An application with an unknown publisher needs your permission to start. |
This application does not have a valid digital signature from its publisher. Use extra caution and verify that the application is safe before using. Search the Internet for the program’s name to determine whether it is a known trustworthy application or malware. |
You have been blocked by your system administrator from running this application. |
This application has been blocked because it is known to be untrusted. To run this application, you need to contact your system administrator to remove the restriction, if appropriate. |
Within large organizations, nearly all users will be configured to sign in to their computer with a standard user account. On a managed system that has been provisioned and deployed by the IT department, standard user accounts should have little need to contact the help desk regarding UAC issues. They can browse the Internet, send email, and use applications without an administrator account. Home users and small businesses that lack a centralized IT resource to provision and manage their devices are often found to use administrative user accounts.
As with previous versions of Windows, an administrator can determine when the UAC feature will notify you if changes are attempted on your computer.
To configure UAC, use the following procedure.
Log onto Windows 10 with administrative privileges.
Click Start and type UAC.
Click Change User Account Control Settings to be shown the User Account Control Settings screen where you can adjust the UAC settings, as shown in Figure 2-32.
Figure 2-32 Changing User Account Control Settings
You need to review the information on this dialog box by moving the slider to each position in order to determine how the UAC feature will behave with each setting. The default is Notify Me Only When Applications Try To Make Changes To My Computer.
Table 2-17 shows the four settings that enable customization of the elevation prompt experience.
Table 2-17 User Account Control Settings
Prompt |
Description |
|---|---|
Never notify |
UAC prompting is disabled. |
Notify me only when applications try to make changes to my computer (do not dim my desktop) |
When an application makes a change, a UAC prompt appears. However, if the user makes a change to system settings, the UAC prompt is not displayed. The desktop does not dim. |
Notify me only when applications try to make changes to my computer (default) |
When an application makes a change, a UAC prompt appears. However, if the user makes a change to system settings, the UAC prompt is not displayed. Secure desktop feature is active. |
Always notify |
The user is always prompted when changes are made to the computer by applications or by the user. |
The settings enable changes to the UAC prompting behavior only, and do not elevate the status of the underlying user account.
Need More Review? User Account Control
To review further details about configuring UAC, refer to the Microsoft website at https://docs.microsoft.com/windows/security/identity-protection/user-account-control/user-account-control-overview.
In addition to the UAC settings within the GUI, there are many more UAC security settings that can be configured via Group Policy. These can be found here: Computer Configuration\Windows Settings\Security Settings\Local Policies\Security Options.
![]() Exam Tip
Exam Tip
You need to take time to review the UAC settings configurable by Group Policy, with attention to the settings that feature Admin Approval Mode.
Secure Desktop
When UAC prompts the user for consent or elevated credentials, it first switches to a feature called Secure Desktop, which focuses only on the UAC prompt. In addition, Secure Desktop prevents other applications (including malware) from interacting with the user or influencing the user response to the UAC prompt.
While it is possible for malware to generate a screen that imitates the look of Secure Desktop (and even re-create the visual UAC prompt), it is not possible for malware to actually provide UAC with the correct credentials. If a system was infected with malware, it could try to bypass the UAC security setting—using a bogus credential prompt to harvest usernames and passwords from unsuspecting users—and then use these credentials on genuine UAC prompts. Therefore, it is important that administrators are vigilant against potential malware attacks, and all devices are set to ensure that their malware protection is configured to automatically update.
Note Uac Integration With the Antimalware Scan Interface
The Antimalware Scan Interface (AMSI) allows Windows applications and services to integrate with antimalware products on a device. If the AMSI detects malware behind the UAC elevation request, the admin privilege is blocked.
Configure Windows Defender Firewall
After you connect a computer to a network, you might expose the computer to security risks. To mitigate these possible risks, you can implement several network security features in Windows 10, including Windows Defender Firewall.
Windows Defender Firewall blocks or allows network traffic based on the properties of that traffic. You can configure how Windows Defender Firewall controls the flow of network traffic by using configurable rules. In addition to blocking or allowing network traffic, Windows Defender Firewall can filter traffic, implement authentication and apply encryption to this filtered traffic.
The way in which you configure Windows Defender Firewall and your network location profiles can have a significant effect on file and printer sharing, and it can affect the discoverability of your device on connected networks.
Configure Firewall and Network Protection
Within the Windows Security app is the Firewall and Network Protection page. This page provides a unified interface for accessing firewall and network protection features, and consolidates several firewall-related components that are found within the Windows Defender Firewall in the Control Panel.
To access the Firewall and Network Protection page as shown in Figure 2-33, open Windows Security, and on the Home tab, click Firewall & Network Protection.
On the Firewall & network protection page, you can view the current Windows Defender Firewall status and access links to enable you to configure firewall behavior. Much of the functionality is duplicated between the Firewall & Network Protection page and Windows Defender Firewall. You can choose to perform the configuration and monitoring task outlined in this chapter using either tool. Eventually, the Windows Defender Firewall located within the Control Panel will be deprecated.
Configure Windows Defender Firewall
Windows Defender Firewall is a software-based firewall built into Windows 10 that creates a virtual barrier between a computer and the network to which it is connected. Windows Defender Firewall protects the computer from unwanted incoming traffic and protects the network from unwanted outgoing traffic.
To access the Windows Defender Firewall, click Start, type Firewall, and then click Windows Defender Firewall.
A firewall allows specific types of data to enter and exit the computer while blocking other data; settings are configured by default (but they can be changed). This type of protection is called filtering. The filters are generally based on IP addresses, ports, and protocols. A description for each filter type includes:
IP addresses are assigned to every computer and network resource connected directly to the network. The firewall can block or allow traffic based on an IP address of a resource (or a scope of addresses).
Port numbers identify the application that is running on the computer. For example
Port 21 is associated with the File Transfer Protocol (FTP).
Port 25 is associated with Simple Mail Transfer Protocol (SMTP).
Port 53 is associated with DNS.
Port 80 is associated with Hypertext Transfer Protocol (HTTP).
Port 443 is associated with HTTPS (HTTP Secure).
Protocols are used to define the type of packet being sent or received. Common protocols are TCP, Telnet, FTP, HTTP, Post Office Protocol 3 (POP3), Internet Message Access Protocol (IMAP), HTTPS, and User Datagram Protocol (UDP). (You should be familiar with the most common protocols before taking the exam.)
Although there are many rules already configured for the firewall, you can create your own inbound and outbound rules based on ports, protocols, programs, and more to configure the firewall to suit your exact needs.
Monitor the Windows Defender Firewall
You can monitor the state of the Windows Defender Firewall from either the Firewall & Network Protection area or the Windows Defender Firewall. It’s easy to tell from here if the firewall is on or off and which is the active network.
To make basic changes to the state of the firewall within the Firewall & Network Protection area, select the network and choose to turn the Windows Defender Firewall on or off. On the left pane of Windows Defender Firewall, click Turn Windows Defender Firewall On Or Off. From there, you can change settings for both private and public networks. There are two options for each:
Turn On Windows Defender Firewall (selected by default)
Block All Incoming Connections, Including Those In The List Of Allowed Apps
Notify Me When Windows Defender Firewall Blocks A New App (selected by default)
Turn Off Windows Defender Firewall (not recommended)
You can also use the links on the page to allow an app or feature through the firewall and the links to the advanced settings options.
Allow an app through the Windows Defender Firewall
Some data generated with and by specific apps is already allowed to pass through the Windows Defender Firewall. You can see the list of which apps are allowed by clicking Allow An App Or Feature Through Windows Defender Firewall in the left pane of the Windows Defender Firewall window in Control Panel. As you scroll through the list, you’ll see many apps (some you recognize and some you don’t), including Candy Crush Saga, Cortana, Groove Music, and of course, Microsoft Edge.
You can modify which firewall profile apps can use by clicking the Change Settings button and providing administrator approval to the UAC prompt. The list will be editable. You will notice from the list that not all apps listed are enabled by default, including Windows Media Player Netlogon Service, Windows Remote Management, and Remote Shutdown. The list of apps and settings may vary depending upon your existing configurations.
If you don’t see the app you want to allow or block, click Allow Another App. You can then browse to the app executable and select the app from the list of applications in the Add An App dialog box, as shown Figure 2-34. You can configure the app to allow or stop it from communicating through the appropriate network profile by selecting the network type option in the dialog box. For existing apps, you can choose the network profile within the Allow An App Or Feature Through Windows Defender Firewall dialog box. There are two checkbox options for each app: Private and Public.
You can also configure Windows Defender Firewall by using either the command line tool Netsh.exe or by using Windows PowerShell. For example, to configure an app exception in Windows Defender Firewall with Netsh.exe, run the following command.
netsh firewall add allowedprogram C:\Program Files (x86)\MyApp\MyApp.exe "My Application" ENABLE
Need More Review? Using Netsh.Exe to Configure Windows Defender Firewall
To find out more about controlling Windows Defender Firewall with Netsh.exe, refer to the Microsoft Support website at https://support.microsoft.com/kb/947709.
There are a significant number of Windows PowerShell cmdlets that you can use to configure and control Windows Defender Firewall. For example, to allow a new app through the firewall, you can use the following command.
New-NetFirewallRule -DisplayName "Allow MyApp" -Direction Inbound -Program "C:\Program Files (x86)\MyApp\MyApp.exe" -RemoteAddress LocalSubnet -Action Allow
Need More Review? Using Windows Powershell to Configure Windows Defender Firewall
To find out more about controlling Windows Defender Firewall with Windows PowerShell, refer to the Microsoft Support website at https://docs.microsoft.com/en-us/powershell/module/netsecurity/?view=win10-ps.
Configure Windows Defender Firewall with Advanced Security
Although you can configure a few options in the main Windows Defender Firewall window, you can perform more advanced firewall configurations by using the Windows Defender Firewall With Advanced Security management console snap-in, as shown in Figure 2-35. To access the snap-in, from Windows Defender Firewall, click the Advanced Settings link on the Firewall & Network Protection page within Windows Security or from the Windows Defender Firewall.
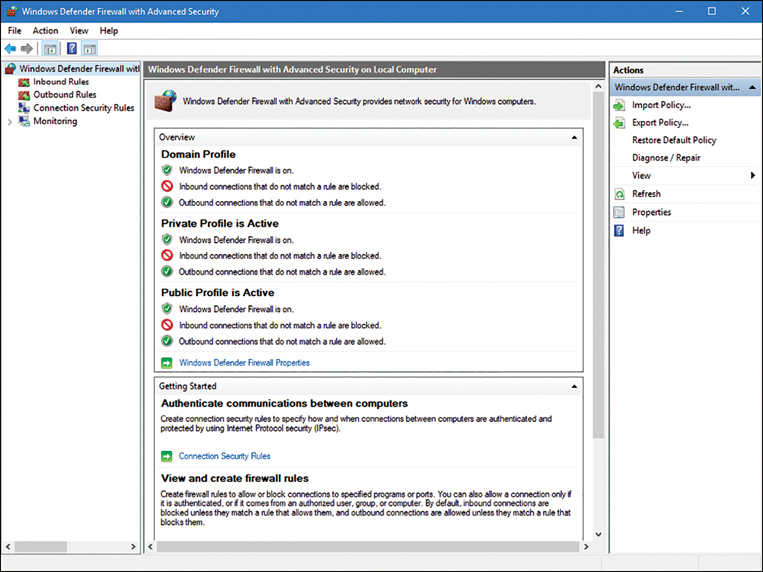
The Windows Defender Firewall With Advanced Security configuration is presented differently. Traffic flow is controlled by rules, and there is a Monitoring node for viewing the current status and behavior of configured rules.
Once opened, there are several options and terms with which you need to be familiar.
In the left pane, your selection determines which items appear in the middle and right panes.
Inbound Rules Lists all configured inbound rules and enables you to double-click any item in the list and reconfigure it as desired. Some app rules are predefined and can’t be modified, although they can be disabled. Explore the other nodes as time allows. You can also right-click Inbound Rules in the left pane and create your own custom rule. Rule types include Program, Port, Predefined, and Custom. They are detailed later in this section.
Outbound Rules Offers the same options as Inbound Rules, but these apply to outgoing data. You can also right-click Outbound Rules in the left pane and create your own custom rule.
Connection Security Rules Connection security rules establish how computers must authenticate before any data can be sent. IP Security (IPsec) standards define how data is secured while it is in transit over a TCP/IP network, and you can require a connection to use this type of authentication before computers can send data. You’ll learn more about connection security rules in the next section.
Monitoring Offers information about the active firewall status, state, and general settings for both the private and public profile types.
In the right pane, you’ll see the options that correspond to your selection in the left pane.
Import/Export/Restore/Diagnose/Repair Policies Enables you to manage the settings you’ve configured for your firewall. Polices use the WFW extension.
New Rules Enables you to start the applicable Rule Wizard to create a new rule. You can also do this from the Action menu.
Filter By Enables you to filter rules by Domain Profile, Private Profile, or Public Profile. You can also filter by state: Enabled or Disabled. Use this to narrow the rules listed to only those you want to view.
View Enables you to customize how and what you view in the middle pane of the Windows Defender Firewall With Advanced Security window.
When you opt to create your own inbound or outbound rule, you can choose from four rule types. A wizard walks you through the process, and the process changes depending on the type of rule you want to create. The rules are as follows:
Program A program rule sets firewall behavior for a specific program you choose or for all programs that match the rule properties you set. You can’t control apps, but you can configure traditional EXE. Once you’ve selected the program for which to create the rule, you can allow the connection, allow the connection only if the connection is secure and has been authenticated using IPsec, or block the connection. You can also choose the profiles to which the rule will be applied (domain, private, or public) and name the rule.
Port A port rule sets firewall behavior for TCP and UDP port types and specifies which ports are allowed or blocked. You can apply the rule to all ports or only ports you specify. As with other rules, you can allow the connection, allow the connection only if the connection is secured with IPsec, or block the connection. You can also choose the profiles to which the rule will be applied (domain, private, public) and name the rule.
More Info Connectivity and Security
When you create inbound and outbound rules and when you opt to allow the connection only if the connection is secured by authenticating the connection with IPsec, the connection will be secured using the settings in the IPsec properties and applicable rules in the Connection Security Rules node. The next section covers how to create connection security rules.
Predefined This sets firewall behavior for a program or service that you select from a list of rules that are already defined by Windows.
Custom This is a rule you create from scratch, defining every aspect of the rule. Use this if the first three rule types don’t offer the kind of rule you need.
![]() Exam Tip
Exam Tip
You might encounter questions regarding how to create a rule on the exam. Therefore, you should spend a few minutes working through the wizard a few times, selecting different rule types each time, to become familiar with the process.
With Windows Defender Firewall With Advanced Security selected in the left pane and using the Overview section of the middle pane, click the Windows Defender Firewall Properties link to see the dialog box shown in Figure 2-36. From here, you can make changes to the firewall and the profiles, even if you aren’t connected to the type of network you want to configure.
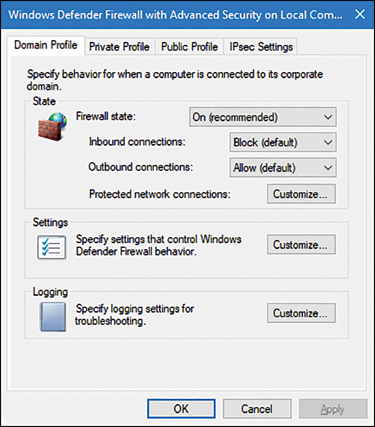
In Figure 2-36, the Domain Profile tab is selected. If you want, you can configure the firewall to be turned off when connected to a domain network. Additionally, you can strengthen the settings for the Public Profile and customize settings for the Private Profile. Finally, you can customize IPsec defaults, exemptions, and tunnel authorization on the IPsec Settings tab. Make sure to explore all areas of this dialog box and research any terms with which you are not familiar.
Configure connection security rules with IPsec
By default, Windows 10 does not always encrypt or authenticate communications between computers (there are exceptions). However, you can use Windows Defender Firewall With Advanced Security connection security rules to apply authentication and encryption to network traffic in your organization.
You can use IPsec network data encryption to ensure confidentiality, integrity, and authentication in data transport across channels that are not secure. Though its original purpose was to secure traffic across public networks, many organizations have chosen to implement IPsec to address perceived weaknesses in their own private networks that might be susceptible to exploitation.
If you implement IPsec properly, it provides a private channel for sending and exchanging potentially sensitive or vulnerable data, whether it is email, FTP traffic, news feeds, partner and supply-chain data, medical records, or any other type of TCP/IP-based data. IPsec provides the following functionality:
Offers mutual authentication before and during communications
Forces both parties to identify themselves during the communication process
Enables confidentiality through IP traffic encryption and digital-packet authentication
Connection security rules are used to force authentication between two peer computers before they can establish a connection and transmit secure information. To secure traffic with IPsec using a connection security rule, you must allow the traffic through the firewall by creating a firewall rule. Connection security rules do not apply to programs and services. Instead, they apply only between the computers that are the two endpoints.
![]() Exam Tip
Exam Tip
Connection security rules specify how and when authentication occurs, but they do not allow those connections. To allow a connection, you must create an inbound or outbound rule. During the inbound or outbound rule creation, you choose the required conditions for the connection, including requiring that the connections have been authenticated by using IPsec. When you do, connections will be secured using the settings in the IPsec properties and rules in the Connection Security Rule node.
Windows Defender Firewall with Advanced Security uses IPsec to enforce the following configurable rules:
Isolation An isolation rule isolates computers by restricting connections based on credentials, such as domain membership or health status. Isolation rules allow you to implement an isolation strategy for servers or domains.
Authentication Exemption You can use an authentication exemption to designate connections that do not require authentication. You can designate computers by a specific IP address, an IP address range, a subnet, or a predefined group, such as a gateway.
Server-To-Server This type of rule usually protects connections between servers. When you create the rule, you specify the network endpoints between which communications are protected. You then designate requirements and the authentication that you want to use.
Tunnel This rule allows you to protect connections between gateway computers. It is typically used when you are connecting across the Internet between two security gateways.
Custom There might be situations in which you cannot configure the authentication rules that you need by using the rules available in the New Connection Security Rule Wizard. However, you can use a custom rule to authenticate connections between two endpoints.
Need More Review? Layering Security Using Windows Defender Firewall with Advanced Security
To find out more about using and configuring Windows Defender Firewall with Advanced Security refer to the Microsoft website at https://docs.microsoft.com/windows/security/threat-protection/windows-firewall/windows-firewall-with-advanced-security.
Creating Firewall rules
To create a rule, from within the Windows Defender Firewall With Advanced Security management console, first select the appropriate node and then click New Rule from the Actions pane. You can then complete the wizard to create your rule. As an example, to create a new inbound rule to enable network traffic for a program, perform the following procedure.
Click Inbound Rules and then click New Rule in the Action pane.
On the Rule Type page, click Program and then click Next.
On the Program page, click This Program Path, browse and select the program executable, and then click Next.
On the Action page, choose Allow The Connection and click Next.
On the Profile page, select which network location profiles are affected by the rule and click Next.
Provide a name and description for your rule and click Finish.
![]() Exam Tip
Exam Tip
To configure port-based or custom rules properly, you might need to know about the TCP and UDP ports that common networking apps use. For further information, visit the following website at https://www.iana.org/assignments/service-names-port-numbers/service-names-port-numbers.xhtml.
In addition to using the Windows Defender Firewall With Advanced Security management console, you can also use the following Windows PowerShell cmdlets to configure and manage firewall settings and rules.
Get-NetFirewallRule Displays a list of available firewall rules
Enable-NetFirewallRule Enables an existing firewall rule
Disable-NetFirewallRule Disables an existing firewall rule
New-NetFirewallRule Creates a new firewall rule
Set-NetFirewallRule Configures the properties of an existing firewall rule
Need More Review? Using Windows Powershell to Configure Windows Defender Firewall with Advanced Security
To find out more about controlling Windows Defender Firewall with Advanced Security Administration with Windows PowerShell, refer to the Microsoft website at https://docs.microsoft.com/en-us/windows/security/threat-protection/windows-firewall/windows-firewall-with-advanced-security-administration-with-windows-powershell.
Implement Encryption
There are two encryption technologies available for Windows 10 devices: Encrypting File System (EFS) and BitLocker. Both tools are available for use on all Windows 10 editions except for Windows 10 Home. While both technologies offer robust methods of encryption, you need to understand how to implement each method as well as the use case for each, so that you can decide the most appropriate tool to use in a given scenario. Just because BitLocker is more modern, you should not assume it is better or worse than EFS. Both provide Windows 10 users with very strong encryption.
Implement Encrypting File System
The built-in Encrypting File System (EFS) is a very powerful method of restricting access to files within a NTFS environment. Although EFS has been available since Windows 2000, very few organizations routinely implement file- and folder-level encryption. Most organizations requiring encryption will choose to use BitLocker Drive Encryption, which encrypts complete drives.
Where EFS is utilized, most issues reported to the help desk relating to EFS often result from an over-enthusiastic member of staff encrypting some of their own files. By default, they have permission to encrypt their own files because they have the Creator Owner special identity.
The best way to ensure that EFS is not inadvertently used, potentially causing problems later, is to implement some or all the following measures:
Stand-alone computers that are not domain-joined should backup their encryption keys to ensure they can be used for recovery purposes later.
Explain the (strict) usage criteria of EFS in the staff handbook / policy.
Train IT staff on the use of EFS and the potential implications of unauthorized usage.
Plan and document where EFS will be applied and who will apply it.
Sufficient restrictions placed across the domain to prevent unauthorized use of EFS.
Implementation of an EFS Data Recovery Agent (DRA) so that if EFS is misused, then an Administrator within the organization can recover any encrypted files.
Implement employee-leaving procedures and scan for encrypted files to ensure all encrypted files are decrypted or ownership transferred.
Disable, rather than delete, user accounts for a fixed time period in case the user account needs to be reactivated in order to remove EFS from corporate resources.
It’s necessary to ensure that selected users and members of IT departments appreciate that EFS is an extremely secure method of protecting files and often, this level of protection is not necessary. Only the original file owner who applied the encryption can access the file and remove the encryption.
If an organization does not have a DRA in place, one needs to be created as soon as possible. Doing so will enable subsequent files encrypted with EFS to be decrypted by the DRA, if needed.
The process for creating a DRA certificate in Windows 10 for a device that is not domain joined can be performed using this procedure:
Open a PowerShell window, or a command prompt window. (This does not require administrative privilege.)
Navigate to the location where you want to store your DRA certificate.
Type cipher /r: file name and press Enter.
Provide a password to protect the DRA certificate. (This can be null.)
To install the DRA so that a user can use it, follow these steps:
Sign in with the user credentials of the user for whom you want to create access to the DRA.
In the search box, type secpol.msc and press Enter.
In the left pane of Local Security Policy, double-click Public Key Policies, right-click Encrypting File System, and then click Add Data Recovery Agent.
In the Add Recovery Agent Wizard, click Next.
Browse to the location of the DRA recovery certificate. (It will have a .cer file extension.)
Select the certificate, and then click Open.
When you are asked if you want to install the certificate, click Yes > Next > Finish.
In the right pane of Local Security Policy, scroll across and note that the Intended Purposes for the certificate is File Recovery.
Open a Command Prompt window, type gpupdate, and press Enter to update Group Policy.
Once the DRA has been created, all EFS encrypted files can be recovered by the DRA.
The encrypted files that are already encrypted are not automatically updated when a DRA is created. Existing encrypted files cannot be recovered by the DRA unless they are opened and closed by the resource owner, which causes the DRA to update the file. To update all encrypted files on a local drive, you can type cipher.exe /u in an elevated command prompt on the system containing the encrypted files.
Encrypt Files and Folders by Using Encrypting File System
When used with a Data Recovery Agent (DRA), Encrypting File System (EFS) is a very secure method to protect sensitive data by encrypting files and folders. Because EFS was first introduced in Windows 2000, EFS often suffers from being dismissed as being old or obsolete. Many people pass over EFS in favor of BitLocker Drive Encryption or BitLocker To Go. Don’t be fooled, though. EFS offers functionality that BitLocker does not, and despite EFS having been available for many years, it still offers an incredibly secure method of enterprise-grade encryption.
It is important to use EFS and a DRA together. Without a DRA available within your organization, you may never regain access to an EFS-encrypted resource. The DRA will help to recover data if the encryption key is deleted or if the machine has been lost or compromised.
EFS offers encryption at a file and folder level, and it cannot be used to encrypt an entire hard disk. Instead, you would use BitLocker (covered later in this section) to encrypt an entire drive. Users can encrypt any file or folder they have created on an NTFS-formatted hard disk by right-clicking the resource and selecting Properties from the context menu that appears. In the Advanced Attributes dialog box (shown in Figure 2-37) select the option to Encrypt Contents To Secure Data.
Encryption should not be used without prior planning and establishing some safeguards to secure the encryption keys that are used. EFS protects data from unauthorized access, and it is especially effective as a last line of defense from attacks, such as physical theft.
EFS uses Windows Public Key Infrastructure (PKI) and a fast encryption algorithm to protect files. The public and private keys generated during encryption ensure that only the user account that encrypted the file can decrypt it. Encrypted data can be decrypted only if the user’s personal encryption certificate is available, which is generated through the private key. Unless exported by the user, this key cannot be used by anyone else, and EFS prevents any access to the data. EFS will prevent attempts to copy or move encrypted data by anyone except users who have the proper credentials. If the user deletes his account or leaves the company, any encrypted resources will not be accessible, which could lead to data being lost. The only way to prevent data loss is to ensure that a DRA has previously been created, so that an administrator can use the DRA to decrypt the resource.
Here are some key points you need to learn about EFS:
The process of encryption and decryption happens behind the scenes and is not visible to users.
Encryption occurs when you close files; decryption occurs when you open them.
EFS is available only on NTFS volumes.
EFS keys aren’t assigned to a computer; they are assigned to a specific user.
If a hacker gains access to the user’s PC while he is signed in, they will be able to access and open EFS-protected files.
The file owner can move or copy an EFS-protected file.
You can’t use EFS and compression together. It’s one or the other.
If the file owner moves an EFS-protected file to a volume that does not support EFS (such as FAT32), the file will be decrypted.
Encrypted files and folders are no longer colored green in File Explorer; now they include a padlock icon on each file, as shown in Figure 2-38.
EFS uses Advanced Encryption Standard (AES), which uses a 256-bit key algorithm, which is a very credible industry standard of encryption.
EFS is only available on Windows 10 Pro, Enterprise, and Education editions.
By default, any user can use EFS to encrypt any file of which they have ownership. Unless company policy requires EFS, you should consider disabling EFS within Group Policy until a DRA is created.
It is very important that a DRA is in place before EFS is enabled. Without a DRA, even an administrator is unable to recover EFS-protected files and folders. For the exam, you need to be able to configure a DRA using the command-line tool Cipher.exe.
Once you have created a DRA, you should update the encryption of each currently encrypted file to have the new DRA applied by using cipher /u. You can continue to encrypt your files and folders within File Explorer using the Encrypt Contents To Secure Data option shown later in Figure 2-38.
Note Dra and Efs: the Sequence is Important
Only encrypted files that are created after the DRA has been created can be recovered using the DRA.
Perform Backup and Recovery of Efs-Protected Files
Built into Windows is a wizard for users who want to use EFS to create a file encryption certificate and key and back up these files. After you first encrypt files or folders, you will see the EFS pop-up notification in the notification area of the desktop asking you to back up your encryption key.
You can use the following steps to start the wizard and complete the process to configure an EFS certificate.
Open Control Panel and select User Accounts.
Click Manage Your File Encryption Certificates to open the Encrypting File System Wizard.
Click Next. The wizard asks for your file encryption certificate; you can select your existing certificate, or you can create a new certificate.
Click Create A New Certificate, and then click Next.
On the Create A Certificate page, select Make A New Self-Signed Certificate And Store It On My Computer and click Next.
Provide a backup location and password and click Next.
On the Update Your Previously Encrypted Files page, select All Logical Drives and click Next.
On the Your Encrypted Files Have Been Updated page, click Close.
In addition to the Cipher.exe command-line tool, you can also use the Certificates MMC (CertMgr.msc) to manage or back up your personal EFS certificate. You can also import your certificates to a new computer that doesn’t already contain your certificate. In the event of your certificate being lost, perhaps due to a failed computer or corrupted profile, you can import the DRA certificate onto a new computer, which would allow recovery of the encrypted files.
To import your EFS certificate into your personal certificate store via the Certificate Import Wizard, you should follow these steps:
Open Certificates MMC, by typing CertMgr.msc into the search box, and then press Enter.
Select the Personal folder.
Click Action > All Tasks > Import.
Work through the Certificate Import Wizard to import the .pfx certificate.
Need More Review? Cipher.Exe
For more information about Cipher.exe, refer to https://docs.microsoft.com/windows-server/administration/windows-commands/cipher.
Some of the most common parameters used with the Cipher.exe command include:
/c Displays information about an encrypted file
/d Decrypts specified files and directories
/s:<directory> Performs the specified operation on all subdirectories in the specified directory
/u Updates all encrypted files on the local drives (useful if you need to update previously encrypted files with a new recovery certificate)
/u /n Finds all encrypted files on a local drive
/? Displays help
/x Backs up the EFS certificate and keys to the specified file name
/r:<FileName> Generates an EFS recovery agent key and certificate, based on the user account, then writes them to a .pfx file (Personal Information Exchange file, which contains a certificate and private key) and a .cer file (Security Certificate file, which contains only the certificate)
After you have encrypted your first file or folder, Windows 10 will prompt you to make a backup of the EFS certificate and key, as shown in Figure 2-38. This reminder will appear in the notification area and it will re-appear on a regular basis until you back up the EFS certificate and key or choose to Never Back Up the files. You need to ensure you do take a backup and store this safely in a separate location from that of the files.
Troubleshoot Encrypting File System
When users report that they are unable to use EFS to encrypt files, you need to verify that all the four statements are correct:
A recovery agent policy has been defined, which prevents the use of EFS unless a DRA has been created.
The file volume is NTFS; EFS is only supported on NTFS.
The file is not compressed. NTFS allows files to be encrypted or compressed, not both.
You have Write access to the file. You need to be able to save the encrypted file.
Other examples of help desk EFS issues include the following scenarios and possible answers:
I can’t open files I have encrypted Only users with the correct EFS certificate and private key for the file can open EFS-protected files. Has the user account been deleted/recreated since the file was created? Use a DRA to recover the file and have the user encrypt the file again.
Will I get a warning that I will lose the EFS protection on my file when I copy my file to a FAT32 USB drive? There is no warning if the user has the necessary NTFS permissions to move or copy the file, and then Windows will carry out the operation without error or warning. Encrypted data copied to a drive not formatted with NTFS will lose the EFS protection.
I saved a file that is protected using Windows Information Protection (WIP) to a FAT32 USB drive. The file looks like it is encrypted using EFS. Is this correct? WIP is supported in Windows 10 to protect files. Protected files look and behave like EFS files, but they do not use EFS. The file is an encrypted PFILE that stores the Enterprise Data Protection metadata, which can be stored on a FAT32 drive.
I can’t open an EFS file after upgrading from a previous version of Windows You can still recover the files by importing the EFS certificate and key from your old computer into your new computer.
My anti-virus check program runs but I get “Access Denied” error messages An anti-virus check program can only read your encrypted files. If the device is a shared computer and other users have encrypted files on the hard disk, the anti-virus tool will not be able to access these files. Other users need to perform a virus check for files by signing in on the device.
Configure BitLocker
BitLocker Drive Encryption enables you to encrypt an entire hard disk, which can be the Windows operating system drive or a data drive. Only the Windows 10 Pro, Enterprise, and Education editions support BitLocker in both x86 and x64-bit varieties. During the encryption process, BitLocker Drive Encryption will configure the drive that contains the operating system to have a system partition and an operating system partition.
![]() Exam Tip
Exam Tip
Two partitions are required to run BitLocker because pre-startup authentication and system integrity confirmation must occur on a separate partition from the drive that is encrypted.
If these partitions are not present the process will automatically modify the partitions as required.
![]() Exam Tip
Exam Tip
You can enable BitLocker before you deploy the operating system. When you do, you can opt to encrypt used disk space only or encrypt the entire drive.
Many modern computers now ship with a Trusted Platform Module (TPM), which is a microchip that is used to securely store cryptographic information, such as the encryption keys that BitLocker uses. BitLocker supports versions 1.2 and 2.0 of the TPM specification, and information contained on the TPM is more secure from external software attacks and physical theft. If a device has been tampered with—for instance, a hard drive has been removed from the original computer—BitLocker will prevent the drive from being unlocked. BitLocker will seek remediation from the user by entering BitLocker recovery mode and requiring the user to enter a 48-digit recovery key. While a TPM is the most secure option, BitLocker technology can also be used on devices without a TPM by configuring a GPO to require that BitLocker obtains the required cryptographic information from a USB flash drive. This information must be presented to unlock the volume.
More Info Overview of Bitlocker Device Encryption in Windows 10
For more information about Windows BitLocker, visit https://docs.microsoft.com/en-us/windows/security/information-protection/bitlocker/bitlocker-device-encryption-overview-windows-10.
When configuring BitLocker, you must consider the following:
The requirements for hardware and software This includes TPM versions, BIOS configuration, firmware requirements, drive size, and so on.
How to tell if your computer has a TPM An administrator might opt to type TPM.msc into Search and click Enter. An end user might opt to access Control Panel, All Items, open BitLocker Drive Encryption, and see if he can turn on BitLocker. If a TPM isn’t found, you’ll have to configure the Group Policy setting called Require Additional Authentication At Startup, which is located in Computer Configuration\Administrative Templates\Windows Components\BitLocker Drive Encryption\Operating System Drives. You need to enable this policy and then select the Allow BitLocker Without a Compatible TPM check box.
What credentials are required to configure BitLocker? Only Administrators can manage fixed data drives, but Standard users can manage removable data drives. (The latter can be disabled in Group Policy.) Standard users can also change the PIN or password on operating system drives to which they have access via BitLocker.
How to automate BitLocker deployment in an enterprise One way is to use the command-line tool Manage-bde.exe. Manage-bde command-line tools you might use in your own work are detailed later in this section. There are other ways to automate BitLocker deployment in an enterprise, including using Windows Management Instrumentation (WMI) and Windows PowerShell cmdlets.
The reasons why BitLocker might start in recovery mode Reasons include disabling the TPM, making changes to the TPM firmware, making changes to the master boot record, and faults on the drive, motherboard, or TPM.
How to manage recovery keys Recovery keys let you access a computer in the event that BitLocker doesn’t permit access. There are many ways to store these keys for fixed drives, including saving them to a folder or your Microsoft account online, printing them, and storing the keys on multiple USB drives.
Note Using Bitlocker Without Tpm
You can only enable BitLocker on an operating system drive without a compatible TPM if the BIOS or UEFI firmware can read from a USB flash drive in the boot environment. This is because BitLocker requires a startup key. If you do this, though, you won’t be able to take advantage of the pre-startup system integrity verification or multifactor authentication.
Understand Bitlocker Key Protectors
BitLocker offers users several protection options. Administrators can choose which type of protection users should adopt to unlock a BitLocker-encrypted drive. BitLocker supports multifactor authentication for operating system drives, allowing you to require additional authentication, such as adding a smart card or a USB drive with a startup key on it or requiring a PIN on start up. These are called key protectors.
BitLocker offers multiple key protectors that can be used to unlock a protected system. These are as follows:
TPM + startup PIN + startup key This is the most secure combination. The encryption key is stored on the TPM chip. The user might find this option cumbersome because it requires multiple authentication tasks.
TPM + startup key The encryption key is stored on the TPM chip. The user needs to insert a USB flash drive that contains a startup key.
TPM + startup PIN The encryption key is stored on the TPM chip. The user needs to enter a PIN to unlock the device.
Startup key only The user needs to insert a USB flash drive with the startup key on it. The device doesn’t need to have a TPM chip. The BIOS must support access to the USB flash drive before the operating system loads.
TPM only The encryption key is stored on the TPM chip, and no user action is required.
With all the BitLocker authentication methods, the drive is encrypted until unlocked. When the BitLocker encrypted drive is in recovery mode, you can also unlock the drive by using either the recovery password or recovery key.
Recovery password This is a 48-digit number typed on a regular keyboard, or by using the function keys (F1–F10) to input the numbers.
Recovery key This is an encryption key created when BitLocker is first employed and is used for recovering data encrypted on a BitLocker volume. Often, the encryption key is stored on removable media.
Because the TPM chip together with BitLocker protects the hard drive, administrators can also configure BitLocker to operate without additional unlock steps; provided the device (and TPM) recognize the drive, then it will be unlocked.
With BitLocker enabled, the drive is no longer susceptible to data theft. On a system that is not encrypted, simply removing the drive from the PC, and attaching it as a slave to another PC allows the data to be read, which bypasses all NTFS security.
![]() Exam Tip
Exam Tip
Administrators can fine-tune within Group Policy the settings for BitLocker, and you would do well to review the available GPOs in detail because they are likely to appear on the exam. Review the GPOs located in Computer Configuration\Policies\Administrative Templates\Windows Components\BitLocker Drive Encryption.
Enable Bitlocker Without a Tpm
By default, a modern Windows device such as a Surface Pro will contain a TPM, and BitLocker Drive Encryption will be already enabled when shipped. When the user signs onto the device for the first time with a Microsoft account, the recovery key is saved to their Microsoft account.
If a TPM isn’t found, click Cancel on the BitLocker Drive Encryption, and follow the displayed instructions to configure the Require Additional Authentication At Startup GPO located in Computer Configuration\Administrative Templates\Windows Components\BitLocker Drive Encryption\Operating System Drives. Enable this GPO and select the Allow BitLocker Without A Compatible TPM check box, as shown in Figure 2-39.

Note Bitlocker is More Secure With a Tpm
Although BitLocker is fully supported and can be enabled on a Windows 10 device without a TPM present, you should fully understand that the most secure implementation of BitLocker is with a TPM present. The TPM also provides pre-operating system startup system integrity verification, which will not take place otherwise. Additionally, if you store the decryption key on a USB flash drive, you should protect the key with a PIN.
A new GPO is included with Windows 10 and can be found at Computer Configuration\Policies\ Administrative Templates\Windows Components\BitLocker Drive Encryption\Operating System Drives\Configure Pre-boot Recovery Message And URL. This GPO enables administrators to configure a custom recovery message and to replace the existing URL that is displayed on the pre-boot recovery screen when the operating system drive is locked. This allows administrators to provide information to the user, such as help desk support contact information.
Configure Bitlocker
To use BitLocker to encrypt the operating system drive on a supported Windows 10 device, the drive must be formatted as NTFS. Perform these steps to encrypt the drive using BitLocker:
Launch Control Panel, click System and Security, and then click BitLocker Drive Encryption.
Select the operating system drive and click Turn On BitLocker. (If you receive an error that the device can use a TPM chip, either enable the TPM within the BIOS or Unified Extensible Firmware Interface (UEFI) settings or enable the Require Additional Authentication At Startup Group Policy setting, which is referred to earlier in this section.)
On the BitLocker Drive Encryption Setup page, click Next.
On the Preparing Your Drive for BitLocker page, if prompted, click Next. (If your system has a Windows Recovery Environment, this will need to be manually enabled and moved to the system drive after the drive is encrypted.)
If you are presented a warning message regarding the Windows Recovery Environment, click Next.
Choose how to unlock your drive at startup. (Enter A Password is used in this example.)
Enter the password, re-enter to confirm and then click Next.
On the How Do You Want To Back Up Your Recovery Key page, select one of the options, then click Next and back up your key. (Optionally, you can choose to back up the key in a secondary location.)
On the Choose How Much Of Your Drive To Encrypt page, select to encrypt either the used disk space or the entire drive and click Next.
On the Choose Which Encryption Mode To Use page, select either the newest encryption mode or the compatible mode and click Next.
On the Are You Ready To Encrypt This Drive page, chose to allow the option BitLocker system check to take place (default), or deselect the option and then click Continue.
Restart the PC, enter the BitLocker password and allow the drive to be encrypted in the background.
In the taskbar notification area, there should be an icon indicating that BitLocker Drive Encryption is in progress.
Note Bitlocker is Immediately Enforced
When BitLocker Drive Encryption starts to encrypt the device, the drive is protected, and it will require unlocking during startup, even if the encryption process has not fully completed encrypting every file.
From within the BitLocker Drive Encryption page in the Control Panel, you can review the BitLocker status and perform additional tasks, including suspending protection, backing up your recovery key, changing the BitLocker password, removing the password, and turning off BitLocker.
Note Used Disk Space Only
An improvement to BitLocker enables administrators to choose whether to encrypt only the used disk space or encrypt the entire drive during the initial deployment of Windows. Choosing the first option significantly reduces the time to deploy and requires less administrative effort, though purists will tell you this is slightly less secure.
Configure Bitlocker Using Command-Line Tools
Administrators can also manage BitLocker Drive Encryption using the command-line tool Manage-bde.exe or by using the Command Prompt, PowerShell, and WMI. Managing recovery keys is discussed later.
There are many parameters that can be used with Manage-bde to manage BitLocker, as listed in Table 2-18.
Table 2-18 Manage-bde command line tool parameters
Parameter |
Description |
|---|---|
Manage-bde -status |
Provides information about all drives on the computer, regardless of whether they are BitLocker-protected. |
Manage-bde -on |
This encrypts the drive and turns on BitLocker. Use the UsedSpaceOnly switch to set the encryption mode to Used Space Only encryption. |
Manage-bde -off |
This decrypts the drive and turns off BitLocker. All key protectors are removed when decryption is complete. |
Manage-bde -pause & Manage-bde -resume |
Use with a drive letter to pause or resume encryption or decryption. |
Manage-bde -lock & manage-bde -unlock |
Use with a drive letter to lock and unlock access to BitLocker-protected data. |
Manage-bde -autounlock |
Manages automatic unlocking of a data drive. |
Manage-bde -protectors |
Manages protection methods for the encryption key. |
Manage-bde -changepassword |
Modifies the password for a data drive. |
Manage-bde -changepin |
Modifies the PIN for an operating system drive. |
Manage-bde - forcerecovery |
Forces a BitLocker-protected drive into recovery mode on restart. |
Manage-bde -changekey |
Modifies the startup key for an operating system drive. |
Manage-bde -WipeFreeSpace |
Wipes the free space on a drive. |
Manage-bde -help or -h |
Displays complete Help at the command prompt. |
More Info Manage-Bde Command-Line Tool
More information on using the manage-bde command-line tool is available in this article at https://docs.microsoft.com/windows-server/administration/windows-commands/manage-bde.
Windows 10 offers built-in support for BitLocker PowerShell cmdlets, as listed in Table 2-19. You can also use Get-help <BitLocker cmdlet>, such as Get-Help Enable-BitLocker -examples.
Table 2-19 BitLocker PowerShell cmdlets
Cmdlet |
Description |
|---|---|
Add-BitLockerKeyProtector |
Adds a key protector for a BitLocker volume |
Backup-BitLockerKeyProtector |
Saves a key protector for a BitLocker volume in Active Directory Domain Services (AD DS) |
Clear-BitLockerAutoUnlock |
Removes BitLocker automatic unlocking keys |
Disable-BitLocker |
Disables BitLocker encryption for a volume |
Disable-BitLockerAutoUnlock |
Disables automatic unlocking for a BitLocker volume |
Enable-BitLocker |
Enables encryption for a BitLocker volume |
Enable-BitLockerAutoUnlock |
Enables automatic unlocking for a BitLocker volume |
Get-BitLockerVolume |
Gets information about volumes that BitLocker can protect |
Lock-BitLocker |
Prevents access to encrypted data on a BitLocker volume |
Remove-BitLockerKeyProtector |
Removes a key protector for a BitLocker volume |
Resume-BitLocker |
Restores BitLocker encryption for the specified volume |
Suspend-BitLocker |
Suspends BitLocker encryption for the specified volume |
Unlock-BitLocker |
Restores access to data on a BitLocker volume |
Note Powershell Help
You may need to use the update-help cmdlet to allow PowerShell to display the most current help files and examples, which may assist your understanding.
More Info Configure Bitlocker Using Powershell Cmdlets
For more information about how to configure BitLocker using PowerShell cmdlets, visit this reference article at https://docs.microsoft.com/powershell/module/bitlocker/?view=win10-ps.
Using PowerShell, you can obtain very detailed information from systems, including status, key protectors used, encryption method, and type. If you run the Get-BitLockerVolume | format-list cmdlet to provide information about an encrypted drive without first unlocking the drive, the amount of information obtained will be restricted.
Upgrade a Bitlocker-Enabled Computer
BitLocker is designed to protect your computer from pre-boot changes, such as updating the BIOS or UEFI. If you upgrade your computer, for example, with a BIOS firmware upgrade, this can cause the TPM to perceive it is under attack. In order to prevent Windows 10 from entering BitLocker recovery mode, it’s recommended that some precautions are taken while upgrading a BitLocker-enabled computer. Prior to updating the BIOS, you should carry out the following steps:
Temporarily suspend BitLocker by opening the BitLocker Drive Encryption in Control Panel and selecting Suspend Protection on the operating system drive, which places it in disabled mode.
Upgrade the system or the BIOS.
BitLocker protection will be automatically turned back on following a reboot, but if this default behavior has been modified, you should turn BitLocker on again by opening BitLocker Drive Encryption in Control Panel and select Resume Protection on the operating system drive.
Forcing BitLocker into disabled mode keeps the data encrypted, with the volume master key encrypted with a clear key. The availability of this unencrypted key disables the data protection that BitLocker offers, but it ensures that the subsequent computer startup will succeed without further user input. After the BIOS upgrade, BitLocker is re-enabled so that the unencrypted key is erased from the disk and BitLocker protection is functional again. The encryption key will be resealed with the new key that has been regenerated to incorporate new values of the measured components that may have changed during the system upgrade.
Note Throughout Suspension, Data is Encrypted
Although BitLocker is suspended, the drive remains encrypted and all new data written to the disk is still encrypted. Suspension prevents BitLocker from validating system integrity at startup and is a security risk; therefore, the protection status should be resumed at the earliest opportunity.
Move a Bitlocker-Encrypted Drive to Another Computer
Moving a BitLocker-encrypted drive to another BitLocker-enabled computer requires that you turn off BitLocker temporarily (by using the Suspend Protection option). After the move is complete, you need to re-enable BitLocker, which will then resume BitLocker protection.
The PowerShell command for suspending BitLocker encryption on the system drive is:
Suspend-BitLocker -MountPoint "C:"
Sometimes a system change can cause the BitLocker system integrity check on the operating system drive to fail. This prevents the TPM from releasing the BitLocker key to decrypt the protected operating system drive and requires the user to enter recovery mode. Examples of system changes that can result in a BitLocker system integrity check failure include:
Moving the BitLocker-protected drive to a new computer
Installing a new motherboard with a new TPM
Turning off, disabling, or clearing the TPM
Making changes to any boot configuration settings
Making changes to the BIOS, UEFI firmware, master boot record, boot sector, boot manager, option ROM, or other early boot components or boot configuration data
When Windows 10 upgrades itself from one version to another, such as 1803 to 1809, there should be no issues with BitLocker because the system will automatically perform the suspend and resume actions during the process.
Configure Startup Key Storage and Recovery Options
You know that without access to the encryption key contained in the TPM or stored in the startup key, you are unable to unlock a BitLocker-encrypted drive.
You should ensure that you’re familiar with BitLocker-related terminology:
Recovery password and recovery key When you first configure BitLocker, it will create a recovery key and prompt you to store it safely. You’ll need to provide this recovery key if the TPM is unable to validate that the drive hasn’t been tampered with or if the startup key, password, or PIN have not been supplied during boot time.
Password A password or passphrase is created to protect fixed, removable, and operating system drives with or without a TPM. The password length can be set in Group Policy and can consist of eight to 255 characters.
PIN When you use a TPM, you can configure BitLocker with a PIN that the user must type during the initial startup of the device to allow Windows 10 to start. The PIN can consist of between 4 to 20 digits, and the length can be set in the Configure Minimum PIN Length For Startup Group Policy setting.
Enhanced PIN This enables administrators to force the use of a complex PIN, just like a password or passphrase (including spaces), by configuring the Allow Enhanced PINs For Startup GPO setting. This policy is applied when you turn on BitLocker and is configurable only for operating system drives.
Startup key This is stored on a USB flash drive and can be used with or without a TPM. To use this method of unlock, the USB flash drive must be inserted every time the computer starts. The USB flash drive can be formatted by using NTFS, FAT, or FAT32.
TPM Lockout By default, TPM 2.0 will lock the user out for two hours whenever the TPM is under attack. (TPM 1.2 lockout duration varies by manufacturer.)
Configure Bitlocker to Go
A portable version of BitLocker, BitLocker To Go, is aimed at protecting removable USB devices and uses the same technology as BitLocker Drive Encryption, but it does not require use of a TPM. BitLocker To Go can protect flash drives, Secure Digital (SD) cards, and removable hard disks formatted with NTFS, FAT16, FAT32, or exFat file systems. BitLocker To Go is available for users with Windows 10 Pro, Windows 10 Enterprise, or Windows 10 Education.
To create a BitLocker To Go drive, follow these steps:
Insert a removable drive.
Open Windows Explorer (though it may open automatically).
Right-click the removeable drive and select Turn BitLocker On.
After the BitLocker Drive Encryption wizard initializes, choose how to unlock the drive and click Next.
On the How Do You Want To Back Up Your Recovery Key? Page, choose an option and then once the password is saved, click Next.
On the Choose How Much Of Your Drive To Encrypt page, select to encrypt either the used disk space or the entire drive and click Next.
On the Choose Which Encryption Mode To Use page, select either the newest encryption mode or the compatible mode and click Next.
On the Are You Ready To Encrypt This Drive page, click Start Encrypting.
The encryption process will commence. Once complete, you can close the wizard.
If the option to encrypt the drive is not available, you need to check to ensure you are using a supported version of Windows and that the feature has not been disabled by Group Policy.
Once a removable drive has been encrypted, each time you insert the removable drive into a device, you will need to unlock it with one of the following methods:
A recovery password or passphrase. (This complexity can be set within Group Policy.)
A smart card.
Always auto-unlock this device on this PC.
The last option is very useful for users who frequently use removable drives because it reduces the likelihood of frustration of entering the password every time they use their removable drives. If the removable drive is used on other devices once the user unlocks the removable drive, it can also be configured to auto-unlock if required.
Standard users can turn on, turn off, or change configurations of BitLocker on removable data drives. They are also able to change their own password for encrypted drives via BitLocker Drive Encryption in Control Panel. However, if a user loses or forgets the password for the data or removable drive, you need to have access to the BitLocker recovery key to recover the data and unlock the drive.
![]() Exam Tip
Exam Tip
It is important to remember that a TPM is not required for BitLocker To Go. The encryption keys are secured using a password or passphrase or smart card, and not by a TPM.
The following GPOs are available within the BitLocker To Go settings found at Computer Configuration\Policies\Administrative Templates\Windows Components\BitLocker Drive Encryption\Removable Data Drives:
Control use of BitLocker on removable drives.
Configure use of smart cards on removable data drives.
Deny Write access to removable drives not protected by BitLocker.
Configure use of hardware-based encryption for removable data drives.
Enforce drive-encryption type on removable data drives.
Allow access to BitLocker-protected removable data drives from earlier versions of Windows.
Configure use of passwords for removable data drives.
Choose how BitLocker-protected removable data drives can be recovered.
Users of Windows 10 Home cannot encrypt removable data drives, but they can access BitLocker To Go enabled data drives and have read-only access to the data, if they provide the correct recovery password, passphrase, or smart card.
Understand Bitlocker and Bitlocker to go Data Recovery
You need to support users who have devices that will not boot into Windows because of BitLocker-related issues during boot time. There are several situations in which BitLocker will enter into BitLocker recovery mode because of a perceived threat to the system, such as one of the following:
Repeatedly failing to provide the startup password.
Changing the startup boot order to boot another drive in advance of the hard drive.
Changing the NTFS partition table, such as creating, deleting, or resizing a primary partition.
Entering the PIN incorrectly too many times so that the anti-hammering logic of the TPM is activated.
Turning off, disabling, deactivating, or clearing the TPM.
Upgrading critical early startup components, such as a BIOS or UEFI firmware upgrade, causing the related boot measurements to change.
Adding or removing hardware (for example, inserting a new motherboard or video card into the computer).
You can also force a BitLocker-protected device into recovery mode by pressing the F8 or F10 key during the boot process.
More Info Bitlocker Recovery Guide
The following article provides a useful list of examples of specific events that will cause BitLocker to enter recovery mode when attempting to start the operating system drive at https://docs.microsoft.com/windows/device-security/bitlocker/bitlocker-recovery-guide-plan.
When the device has entered the BitLocker recovery mode, you need to recover the drive by using one of these methods:
Supply the 48-digit recovery password.
Allow a domain administrator to obtain the recovery password from Active Directory, which may or may not use Microsoft BitLocker Administration and Monitoring (MBAM) Tool version 2.0. MBAM is included in the Microsoft Desktop Optimization Pack (MDOP) for Microsoft Software Assurance.
Allow an administrator to obtain the recovery password from Azure Active Directory.
Run a script to reset the password, using PowerShell or VBScript, which uses the key package.
For standalone and small-business users, the BitLocker recovery key is stored in the user’s Microsoft account at https://onedrive.live.com/recoverykey. You will need to use the keyboard number or function keys to enter the number to unlock the drive. Once the operating system has started, users can then re-create a new startup key; otherwise, the BitLocker recovery mode will remain in place.
For corporate users, there are several settings that can be configured in Group Policy that will define the recovery methods that require Windows to save BitLocker recovery information to Active Directory. The GPOs found in the subfolders of Computer Configuration\Administrative Templates\Windows Components\BitLocker Drive Encryption are as follows:
Choose how BitLocker-protected operating system drives can be recovered
Choose how BitLocker-protected fixed drives can be recovered
Choose how BitLocker-protected removable drives can be recovered
For each of these GPOs, you can also enable the Do Not Enable BitLocker Until Recovery Information Is Stored In Active Directory check box to keep users from enabling BitLocker unless the device is connected to the domain and the backup of BitLocker recovery information to Active Directory has succeeded.
Once BitLocker recovery information has been saved in Active Directory, the recovery information can be used to restore access to a BitLocker-protected drive by using the Manage-bde command-line tool introduced earlier.
Note Bitlocker Faqa
You need to take some time to review BitLocker. It is an important feature that protects against data loss. Read the BitLocker FAQ at https://docs.microsoft.com/windows/device-security/bitlocker/bitlocker-frequently-asked-questions.
In an Azure Active Directory environment, you can locate the BitLocker key within the Azure Active Directory Admin Center. Locate the device, and if the Windows 10 machine has been encrypted, you can use the BitLocker recovery key or provide it to the user to recover his or her device.
To view or copy the BitLocker keys within Azure Active Directory, you need to be either the device owner or have one of the following roles assigned.
Global Administrator
Helpdesk Administrator
Security Administrator
Security Readers
Intune Service Administrator
Thought experiments
In these thought experiments, demonstrate your skills and knowledge of the topics covered in this chapter. You can find the answers to these thought experiments in the next section.
Scenario 1
Adatum has 3,000 workstations currently running Windows 10. Most of the users belong to the Active Directory domain, but 50 research engineers in the R&D department do not. The research engineers need to access special 3D printing hardware that is located within their secure area. Adatum needs to ensure that only the research engineers can use the specialized printing devices.
As a consultant for Adatum, answer the following questions:
What type of group will you use for the research engineers?
How will you ensure that only the research engineers are able to print to the 3D printer?
You find that a user has been using the 3D printer for personal use outside of normal office hours. How would you investigate this matter?
Scenario 2
You have recently implemented a new network-shared storage facility for your organization. This storage is formatted using NTFS and has been shared to groups containing users within Active Directory. Users of the design department will use the local storage to store CAD drawings in two folders: Current Projects and New Projects. The files within the New Projects folder are confidential. You notice that users who are not part of the design department are able to access the CAD files.
You must ensure that the network-shared storage facility is accessed by the design department personnel only.
Answer the following questions for your manager:
How will you ensure that only design department personnel can access the storage?
What share-level permissions should you grant on the storage?
You need to confirm to your manager that members of the organization who are not in the design department do not have access to the files contained in the storage. How will you reassure your manager?
You need to provide an audit trail of the access to the New Projects folder. How will you proceed?
Scenario 3
Your organization wants to use Group Policy to configure power settings on the sales department laptops. All laptops are identical. You add a new Group Policy to remove the sleep feature on the laptops. Some members of the sales department report that they can still put their laptops into sleep mode. You access one of the sales departmental laptops and confirm the GPO has not been applied.
Answer the following questions for your manager:
What GUI tool could you use to verify whether the GPO is being delivered to the laptop?
Some members of the sales department work out of the office, often in rural locations. How could location affect the effectiveness of the GPO?
How could you ensure that all members of the sales department receive the GPO?
What command line tool could you use to verify what GPOs have been delivered to the laptop?
Scenario 4
Adatum Corporation uses Microsoft 365 and has an IT security policy in place that requires company laptop devices to be encrypted at all times. Many of the remote workers operate from home, and the IT policy allows these users to choose a corporate-owned device from an authorized device list. Employees selected various devices, including the Surface laptop, which comes pre-installed with Windows 10 Home.
All company data is stored in Microsoft 365 cloud-based storage, such as OneDrive for Business and SharePoint Online. The sales department often needs to leave customers with USB thumb drives that contain presentations, which include sensitive information.
How will you respond to the security manager, who has raised the following concerns?
The Surface laptops do not currently support EFS or BitLocker Drive Encryption. What should you do first?
You need to recommend an encryption solution for the company data stored on the sales department laptop devices so that they comply with the IT security policy. What should you recommend?
How will your encryption solution be deployed to the remote staff?
Thought experiment answers
This section provides the solutions for the tasks included in the Thought experiments section.
Scenario 1
Create a Research Engineers Local Group.
Add only the research engineers to the Research Engineers Local Group and grant print permissions for the 3D printer to the research engineers local group.
Investigate the logs within the Event Viewer, and look for instances in which a print job has been sent to the 3D printer outside of normal office hours. You could enable logging within the Microsoft-Windows-PrintService Operational logs.
Scenario 2
Create a design department security group, add all the design department personnel to the group, and give the design department group NTFS access to the storage.
You should give full-access, share-level permissions for the design department group.
You should use the Effective Access feature to verify the NTFS permissions in place. In the Advanced Security settings for the shared folders, evaluate the effective access permissions for a user or group that is not a member of the design department group.
Enable Auditing for success and failure in Group Policy, and then enable auditing on the New Projects folder to track both successful access to the folder and failed attempts.
Scenario 3
Use the Resultant Set of Policy (RSoP) tool to diagnose and troubleshoot group policy settings.
The GPOs are only delivered once the user connects to and logs into the Active Directory Domain. If members are unable to connect their laptops to the organization, such as by using a VPN or via a wired or a Wi-Fi network, they might be using cached credentials, and therefore, they will not receive the new GPO.
Ask the members of the sales department to connect to the corporate network using a VPN or via the internal wired or Wi-Fi network. Once connected, they should then log on so that they can receive the new GPO.
Use the GPResult tool to display a report of the GPOs that have been applied to a system.
Scenario 4
You need to upgrade the device license on the Surface Laptops to Windows 10 Pro or Windows 10 Enterprise before encryption can be used.
You could ensure that devices use BitLocker Drive Encryption. In this way, all data stored on the device will be encrypted.
The Surface Laptops can be joined to Azure Active Directory by the user or by using Windows Autopilot. Once joined, they can be auto-enrolled into Microsoft Intune. Once managed by Intune, they will receive device policies to enforce encryption.
Chapter summary
Local accounts are local to the Windows 10 device, and the password is stored in the SAM database.
Most settings are configured within the Settings app and not the Control Panel.
The Administrator has full permissions and privileges on a Windows 10 device and can manage all the objects on the computer.
The Creator Owner is a special identity that has special administrator level permissions to the resources over which they have ownership.
Azure Active Directory (Azure AD) is a cloud-based identity authentication and authorization service.
Devices can be joined or registered to Azure AD.
Azure AD supports registering of Bring Your Own Device (BYOD) scenarios for multiple types of devices, including Windows 10, iOS, Android, and macOS.
Only Windows 10 devices can be joined to Azure AD.
Existing Windows 10 devices can be joined to Azure AD using the Accounts section of the Settings app.
The Device Enrollment Manager (DEM) account in Microsoft Intune is a special account that allows you to enroll up to a maximum of 1,000 devices.
Windows 10 supports NTFS as the default file system.
The Quick Access area is new in Windows 10 and appears at the uppermost left area of the File Explorer navigation pane. It shows the frequently used files and folders.
Effective Permissions is useful to determine the permissions a particular user would have through NTFS permissions.
Windows 10 NTFS uses 6 Basic Permissions and 13 Advanced Permissions for securing files and folders.
When applying permissions to groups, an explicit Allow setting will override an implicit Deny permission.
Use the ICACLS command line tool to configure and view permissions on files and folders on a local computer and reset them to defaults.
Inheritance of permissions can be useful when applying permissions to a large environment because the permissions will be automatically propagated based on the default inheritance setting.
You can use the Effective Access feature to ensure that your NTFS permissions are as expected.
If you have administrative privileges, you can take ownership of an object, such as a file, and allocate it to another user or group.
You can reset the permissions of all the folders, files, and subfolders using the command-line tool icacls <file name> /reset.
Only files stored on a NTFS-formatted hard drive have a Security tab in their File properties.
Windows 10 uses a feature called Network Discovery, which uses a new layer two protocol called Link Layer Topology Discovery (LLTD) to identify other devices present on the local subnet.
Share permissions can be Read, Change, or Full.
The registry is a database, which is split into multiple separate files known as hives.
You use the built-in Registry Editor (Regedit.exe) tool to view, search, and modify the registry’s contents.
Local Security Policy allows you to configure security policies, such as a password or audit policy, on a local computer.
User rights policies are used to determine what rights a user or group of users have on a device and relate to activities or tasks that the user can perform.
User Rights Assignments policies affect what users can do to a system, and Security Permissions affect which access permissions a user has.
Use the Resultant Set of Policy (RSoP) tool to check and troubleshoot group policy settings.
Use the GPResult command line tool to verify what group policy objects have been applied to a user or computer.
The Windows Security app collects and displays the security status of your device and will trigger notifications through the Action Center.
User Account Control (UAC) helps protect the operating system from unauthorized configuration changes and app installations.
UAC elevation prompts can be prompts for consent or prompts for credentials.
Whenever UAC prompts the user for consent, it uses a feature called Secure Desktop to focus the activity only on the UAC prompt and prevents malware from interacting with the UAC process.
Windows 10 is protected by the Windows Defender Firewall, which acts as a network barrier.
You can Allow an app through the Windows Defender Firewall or create connection security rules using Windows Defender Firewall with Advanced Security.
Windows 10 supports two encryption technologies: Encrypting File System (EFS) and BitLocker.
Windows 10 Home does not support encryption.
You should always create a Data Recovery Agent (DRA) whenever EFS is used within an enterprise, so that encrypted files can be recovered.
EFS can be managed though the GUI or by using the command line tool cipher.exe.
BitLocker Drive Encryption enables you to encrypt an entire hard disk.
Devices with a Trusted Platform Module (TPM) can securely store the encryption keys that BitLocker uses.
BitLocker supports versions 1.2 and 2.0 of the TPM specification.
BitLocker offers users several key-protection options, including storing the key protectors on a TPM, smart card, or a USB drive with a startup key on it. BitLocker also allows you to require a PIN on start up.
On a modern Windows device, BitLocker Drive Encryption will be already enabled when shipped. When the user signs in to the device for the first time with a Microsoft account, the recovery key is saved to his or her Microsoft account.
For personal and small-business users, a BitLocker recovery key is stored in their Microsoft accounts at https://onedrive.live.com/recoverykey.
On devices without a TPM, you can configure the Require Additional Authentication At Startup GPO setting to allow BitLocker to be used without a compatible TPM.
Before upgrading your computer—for example, performing a BIOS firmware upgrade—you should suspend BitLocker Drive Encryption. By default, after a reboot, protection will be automatically resumed.
If a device enters BitLocker recovery mode, you will need to recover the drive by supplying the 48-digit recovery password.
The BitLocker recovery password can be stored in Active Directory or Azure Active Directory.