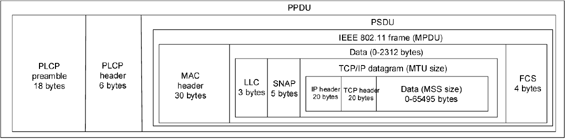
Figure 5.1. Structure of a packet transmitted via the 802.11b interface
After the commercial flop of the third generation of mobile systems, IEEE 802.11 technology is sweeping the market thanks mostly to the simplicity of its deployment and especially to the wide use of radio band. Originally, this technology helped companies in their needs to complete or replace their wired local-area networks, but network operators have quickly felt the need to make its utilization public. The objective is for it to be used alone or to integrate it with the third generation of mobile systems and thus create the fourth generation of mobile systems.
The advantage of IEEE 802.11 networks is the large bandwidth, which is becoming more and more comparable with wired local-area networks. However, these networks have two limitations. On the one hand, this type of network has no signaling or control plan to ensure the level of service required by a user. On the other hand, the advantage of mobile cellular systems is that they do have a reliable and efficient signaling and control system which is able to provide and maintain a level of service required by a user. However, their problem is the low throughput that they can offer their users.
While we wait for a reliable and efficient integration of these technologies, improvements in wireless medium and differentiation of service in IEEE 802.11 networks are needed. IEEE 802.11 technology will be able to be used commercially only if it develops the necessary mechanisms to ensure to users QoS, security and mobility handling. Multiple workgroups have been formed within the IEEE standardization organization in order to work on these issues. The a and g groups work on throughput increase in the initial standards which are IEEE 802.11 and IEEE 802.11b. The i group works on data security issues. The f group works on mobility issues. The h group is working on configuration problems and, finally, the IEEE 802.11e group is working on QoS issues within IEEE 802.11. In this chapter, we will go over the efforts of this last group, but before we do that, let us briefly explain the basic operation of IEEE 802.11b, as well as the major problems associated with providing QoS in the 802.11 environments.
Bandwidth in the wireless medium is a scarce resource compared to the wired medium. MAC level protocols used in wireless networks are distributed protocols developed in order to avoid collisions and to provide network nodes with a fair access to the shared wireless medium. In the 802.11 [IEE 97] protocol, the fundamental mechanism for medium access is DCF (distributed coordination function). This approach implements a random access scheme, based on the CSMA/CA access protocol (carrier sense multiple access with collision avoidance). The retransmission of colliding packets is controlled by rules proposed within the Backoff algorithm.
The efficiency of MAC level protocols can be measured by the use of two parameters: collision probability and the fairness factor of the channel allocation to competing nodes. Protocols used for WLAN, as with any random protocol with multiple access, use the BEB (Binary Exponential Backoff) algorithm to treat the collision problem. BEB is a very efficient mechanism for minimizing the probability of collision which in this case is of approximately 1%.
Typically, all the variations of the CSMA/CA protocol strive to achieve fair sharing [BHA 94]. A medium access protocol is considered to be not fair if it cannot provide access to medium for individual nodes without an explicit differentiation. Consequently, when multiple nodes in a network are in competition for medium access, the probability for a node to gain access should be the same as for all the nodes in the network.
When a data packet is transmitted from the application layer, headers must be added at each layer, therefore increasing the total packet size and thus the transfer time. Figure 5.1 displays the structure of a packet transmitted via the 802.11 interface and its acronyms.
Table 5.1. Acronyms used in Figure 5.1
FCS |
Frame verification sequence |
MSS |
Maximum size of segment |
MTU |
Maximum transmission unit |
SNAP |
Sub-network access protocol |
LLC |
Link control |
MPDU |
MAC protocol data unit |
PLCP |
Physical layer convergence protocol |
PSDU |
PLCP service data unit (SDU) |
PPDU |
PLCP protocol data unit (PLCP + MPDU) |
A data packet is encapsulated with a 30 byte MAC header plus 4 FCS bytes. This is the MPDU part or the PSDU part of the PPDU. The PLCP is a factor affecting bandwidth on the channel as each MPDU is transmitted. 24 bytes (192 bits) belong to the PLCP preamble; furthermore the header is independently attached to the size of the packet. Finally, the 6 bytes (48 bits) PLCP header is a preamble for PLCP of 18 bytes (144 bits) known as the long preamble. The preamble is used to signal a new data packet to the receiver. A disadvantage with PLCP is that the PLCP preamble and the header are always transmitted at a rate of 1 Mbps, independently from the data rate. This means that the time of transfer for the PLCP is constant at 192 μs with a long preamble.
The 802.11b [IEE 99b] standard offers the possibility of reducing the size of the PLCP preamble to 9 bytes (72 bits), called a short preamble. As such, it makes it possible to significantly increase the performance for higher throughputs. The version of the protocol with the short preamble enables better performances, by transmitting the short preamble at 1 Mbps and the header at 2 Mbps, which reduces transmission time to 96 μs.
A group of strict rules controls the way a transmission should behave within CSMA/CA. First, the sender must wait for a DIFS (Distributed Coordination Function InterFrame Space) period of 50 μs before the medium can be considered available. Only after this period can a data frame or a request to send be transmitted. The receivers respond with an acceptance (ACK) or a clear to send. The receiver must wait for a SIFS (short interframe space) period of 10 μs before responding.
Wireless networks provide comparable performance with cabled networks. However, radio links introduce additional problems. This is due to the quality of the signal on the radio medium. These problems linked to the radio interface and therefore not pertinent to wired networks are: transmission errors, radio signal interference due to simultaneous transmissions, signal strength that diminishes greatly due to the distance, loss of carrier and the impossibility to detect collisions via transmission monitoring techniques. Furthermore, effects caused by the reduction of the signal, the interferences from other users and the objects are also deteriorating the performance of the channel [JAK 94]. Measures presented in [DUC 92] show that packet error ratio strongly depends on the distance between the sender and the receiver. They do not, however, follow the same distribution by increasing the distance. Hence, transmission on radio links is not reliable enough. Multiple research studies [CHA 04, CRO 97, WEI 97, BIA 00, TAY 01] for the evaluation of the IEEE 802.11 DCF performance show that the network’s performance is very sensitive to the number of stations trying to access the channel.
IEEE 802.11 [IEE 97] networks are becoming the most widely used wireless access networks because they can offer a comparable performance to wired networks. Nevertheless, these networks have problems such as errors due to the radio resource, signal interference, mobility of the user and fair sharing method of the radio resource which is the CSMA/CA access mechanism. In order to adapt the transmission throughput with the quality of the link, a theoretical throughput variation function has been developed. This functionality progressively decreases theoretical throughput from 11 Mbps to 5.5 Mbps, 2 Mbps or 1 Mbps when a node detects unsuccessful frame transmissions. The multiple data transfer rate capacity represents a dynamic change of the throughput with the objective of improving the performance for this station. However, in order to ensure coexistence and interoperability between stations capable of implementing the theoretical throughput variation functionality, a set of rules that must be followed by all stations is defined within the standard.
The probability of access among others is a second functionality implemented within the CSMA/CA access method. The access method for CSMA/CA support guarantees that in the long term all stations have the same access probability. When a station captures the medium, if it has a low throughput (i.e. throughput lower than 11 Mbps) therefore monopolizing the medium for a long period of time, it then penalizes the other stations by requiring a higher throughput. In this case a degradation of the performance of the cell throughput is identified.
This performance degradation caused by the influence of a low throughput station has been studied in [HEU 03]. The authors show that the useful throughput is much lower than the theoretical throughput. They also analyze the effects of a low theoretical throughput station over the other stations that share the radio medium.
Figure 5.2 shows the degradation within the throughput value of the 802.11b cell when a single station decreases its theoretical throughput.
In wireless networks, offering guarantees in terms of delay or jitter can only happen if the medium access method enables it. The IEEE 802.11 [IEE 97] standard respects this rule. In this section, we will describe the different access methods which make it possible to offer QoS support in the MAC layer of IEEE 802.11. These access methods can be divided into two categories:
– centralized approaches: approaches based on the invitation of stations to transmit. These invitations are transmitted by a “Coordinator” node;
– distributed approaches: or service differentiation approaches. This service differentiation is obtained by an adequate spacing between transmissions. This spacing represents the priority for medium access.
In its initial standard [IEE 97], also known as the basic standard, the IEEE’s 802.11 committee proposed two medium access methods. The first is the Distributed Coordination Function (DCF). This method is similar to the Ethernet access method. It has been designed to support the transport of asynchronous data and enables all users who want to transmit data to have an equal chance to access the wireless medium. So DCF offers a fair access to medium (i.e. one station cannot have priority over another). The second access method is the Point Coordination Function (PCF). With this one, the different data transmissions between network stations are managed by a central coordination point. This access method is generally located in the AP. It has been designed to enable the transmission of delay sensitive data (i.e. to guarantee QoS to stations that require it).
In order to obtain a QoS and improve DCF and PCF access methods, the e group of IEEE 802.11 [IEE 02] is defining new priority mechanisms for the IEEE 802.11 standard. This group introduces two new access methods: the Enhanced Distribution Coordination Function (EDCF) and the Hybrid Coordination Function (HCF). A station using 802.11e will then execute these two access protocols instead of the DCF and PCF methods.
In the next section, we will examine these different access methods by separating between the distribution techniques description from the centralized techniques. Apart from these access methods proposed within the frame of standardization of wireless local networks, many other improvements exist. However, in this section we only describe studies linked to standardization.
In the following, we describe both distributed access methods proposed or discussed within IEEE 802.11: DCF and EDCF.
The DCF protocol is the access method which enables the transfer of asynchronous data in best-effort mode. The DCF method is not a MAC layer offering QoS. However, this access method is described here because it is at the core of the other distributed access methods which offer a certain degree of separation between flows and frames (QoS).
The DCF is based on Carrier Sense Multiple Access with Collision Avoidance (CSMA/CA). The general principle of CSMA/CA is to listen to the medium before transmitting and then to attempt to obtain access: if the link is unoccupied when a node wants to transmit data, the node transmits its frames. If, on the other hand, the link is occupied, the node waits for the end of the current transmission to earn the right to access the medium.
With DCF, each station watches for activity from the other stations within the same BSS (cell). When a station transmits a frame, the other stations perceive that a frame has been sent in the network. Then, in order to avoid that all the other stations continue to listen to the medium until the end of the transmission, they will update a timer called Network Allocation Vector (NAV) that makes it possible to delay all expected transmissions. The NAV is calculated with regard to the information located in the shelf life field within the transmitted frame. The other stations will not have the capacity to transmit data until the end of the NAV.
The access to the wireless medium is controlled by the use of a space between the transmission of two consecutive frames within the same BSS. These spaces, called InterFrame Space (IFS), correspond in fact to periods of inactivity on the transmission medium. The standard defines two IFS types for the DCF mode:
– Short IFS (SIFS): this is the smallest of the IFSs. It is used to separate transmissions within the same dialog (between fragments of frames, between a data frame and its ACK, etc.). This enables the station to have priority over all the other stations for accessing the medium;
– DCF IFS (DIFS): this space, larger than SIFS, is used when a station wants to start a new transmission. It must wait a DIFS time before transmitting its data on the medium.
It is important to note that the fact that SIFS is smaller than DIFS makes it possible for the access to medium to give priority to the frames of a current transmission instead of a new transmission.
So, before each data transmission, each station must sense the medium and make sure that it is available. If the medium is available during a time interval equal to DIFS, the station can then transmit. If not, the transmission is deferred until the medium becomes available. This can bring the risk of contention for access to the medium, i.e. two stations or more wait for the end of a transmission to take their turn. In order to avoid as much as possible a risk of collision caused by two almost simultaneous transmissions, a procedure, called Backoff procedure, is launched once the medium becomes available for a length equal to DIFS. More specifically, the station calculates a random timer called Backoff timer, which is called TBackoff in [5.1]. This is between 0 and a maximum value, called Contention Window (CW), and is calculated as follows:
where SlotTime is an interval of time used to define the IFS intervals as well as the timers for the different stations. Its value is dependent on the physical layer used.
If the timer has not reached the 0 value and the medium becomes busy once again, then the station freezes the timer. This timer will be unfrozen when the medium becomes available again for a time equal to DIFS. In this way, the stations that have randomly chosen high Backoff time have priority for access to the medium when it becomes available once more. When the timer reaches the 0 value and the medium is still available, the station transmits its frame. If two or more stations reach the 0 value at the same time, a collision happens and each station must generate a new random timer between 0 and 2*CW. The CW value moves between a minimum (CWmin) and a maximum (CWmax). A maximum of tries is also defined by 802.11; if this number is reached before the correct transmission, then the current transmission is simply abandoned. CWmin and CWmax values have also been the object of a standardization by the 802.11 group; they depend on the physical layer used.
If the transmitted data has been correctly received, the destination station waits for a time equal to SIFS and then transmits an acknowledgement (ACK) to confirm correct data reception. If no ACK is received by the transmitting station after a predefined time, it is then assumed that a collision has taken place and a data retransmission attempt, by using the Backoff algorithm, is executed.
It is important to note that after each successful transmission, the Backoff process is executed again by the stations in competition. This is done even when no frame is waiting for transmission. Since this procedure is executed after each transmission, it is called post-Backoff. A new procedure for the transmission of a new frame can be initiated only after the expiration of that time.
During the transmission time between the source station and the destination station, the other BSS stations update their NAV. The value calculation of the NAV includes the transmission time of the data frame and the InterFrame Spaces as well as the ACK (see Figure 5.3).
Due to Backoff’s algorithm, stations have the same probability of accessing the wireless medium. However, as it is defined, DCF does not guarantee a minimum delay and therefore cannot be used with real-time applications.
The EDCF access method is, as its name indicates1, an improvement of the basic DCF access method. This improvement is proposed in order to enable a differentiation of services between flows, at the wireless interface level.
QoS support within EDCF is possible due to the introduction of traffic categories (TC). In fact, the frames are delivered using different Backoff instances within the same station, each Backoff instance configured with parameters specific to a particular traffic category. In the contention period (CP; see section 5.3.3.1.1), each TC within the station has to be able to transmit its data and to start, if needed, a Backoff procedure independently from the other TC in the same station. The Backoff procedure in EDCF is initiated when it is detected that the medium is available for a period equal to an IFS time called arbitration IFS (AIFS). The AIFS can take any value, higher than or equal to DIFS, therefore participating to the TC characterization to which it belongs. After a wait time equal to AIFS, a Backoff timer is initialized with a value within the [1, CW + 1] interval. The minimum (CWmin[TC]) and maximum (CWmax[TC]) sizes of the Backoff window are also parameters that characterize a traffic category. The counting down procedure of the Backoff timer is the same as DCF with one exception: when the Backoff timer is initiated after having been interrupted, since the medium had become occupied again, it is decremented by 1 at the end of the AIFS time and not at the end of the first time slot following DIFS (or AIFS), as with DCF. This makes it possible to accentuate the priority of TCs that had to block their Backoff timers. After each collision a new contention window CW is calculated according to a persistence factor PF [TC]. This persistence factor is the third parameter characterizing a traffic category. In fact, contrary to the basic standard where the contention window size is simply doubled (equivalent to PF = 2), 802.11e uses the PF2 parameter to increment the contention window size for each TC, as follows:
As shown in Figure 5.4, each station can implement up to eight queues, each corresponding to a specific traffic category [TC]. If the timers of one or more TC within the same station reach the 0 value at the same time, the scheduler within the station would give priority to the traffic category with the highest priority in the station, thus avoiding a virtual collision. Other collisions can, however, happen between stations.
Figure 5.4. Virtual Backoff with 8 traffic categories [TC]: (a) on the left, DCF, equivalent to EDCF with AIFS = DIFS, CWmin = 15, CWmax = 1,023 and PF = 2; (b) on the right, EDCF

In summary, each TC is characterized by three different parameters that specify its relative priority degree:
– arbitrary interframe space time, AIFS[TC], higher than or equal to DIFS;
– progress intervals of the particular Backoff window (CWmin[TC] and CWmax[TC]);
– a persistence factor, PF[TC], for the progress of the Backoff window.
Another crucial parameter in 802.11e is the TXOP3. A TXOP is defined as the time interval during which a station has the right to transmit. It is characterized by an instant of transmission start and a maximum transmission time and it is obtained after contention (EDCF-TXOP) or with the help of the hybrid coordinator HC (polled-TXOP)4. In the case of the EDCF access method, the size of EDCF-TXOP is limited within a cell for each TC; this maximum values are transmitted inside the frame tags.
In order to introduce a service differentiation in wireless local-area networks, a certain degree of separation between different types or service classes must be offered by the MAC layer. As illustrated by the description of the EDCF access method, the introduction of this separation between service classes corresponds to the assignment of priorities to flows. This is done by using one or a combination of the three following service differentiation mechanisms:
– Backoff incrementation function;
– differentiation by the Backoff windows (CWmin);
– differentiation by DIFS (called AIFS in EDCF).
As illustrated in the previous section, each time a transmission fails due to collision, the contention window size is doubled.
By considering that the only configurable term in equation [5.3] is the multiplier 2, one possibility for introducing a certain priority is to replace, for each service class j, this multiplier by a priority (Pj) assigned to each service class. In other words, for each transmission attempt, instead of multiplying the Backoff window size by 2 it will be multiplied by Pj. Evidently, the higher the factor Pj,, the larger the Backoff window and therefore the smaller the probability that a frame belonging to this class will be transmitted quickly, and consequently the throughput will be slower.
According to [AAD 01, AAD 03], this mechanism seems to yield good results only when we consider UDP traffic and when the number of terminals in contention is high. On the other hand, when the number of terminals in contention is low, the CW value is usually at its minimum (CW = CWmin) and it is rarely incremented. Therefore, no service differentiation is noticed.
This second method was proposed due to the limitations of the previous method [AAD 03, VER 01]. Indeed, when the number of terminals in contention is low and when the CW value is mostly equal to CWmin, the idea is then to make an adequate choice of this initial value (CWmin) for each service class in order to obtain a service differentiation between these classes.
This second mechanism partially resolves the problems of the previous method. In fact, a clearer service differentiation is obtained for UDP flows when the number of terminals is small. However, this mechanism does not always make it possible to obtain a strict and clear service differentiation for TCP flows [AAD 03].
As we have seen earlier in this chapter, in DCF, priority is given to an ACK transmission compared to data frame or RTS frame transmission. This is done due to an adequate choice of InterFrame Space (IFS). In fact, the transmission of an ACK is only delayed for a time equal to SIFS when the medium becomes available again, whereas the transmission of a data or RTS frame must wait longer (time equal to DIFS). Consequently, if a station that wants to transmit is in contention with a station that must send an ACK, the ACK will access the medium in priority. This same idea has been used in order to introduce a service differentiation for data transmission. This can be made possible by using different DIFSj (or AIFSj) values, each corresponding to a service class j. In order for the priority to be given to class j instead of class j−1, DIFSj must be lower than DIFSj−1 (see Figure 5.5).
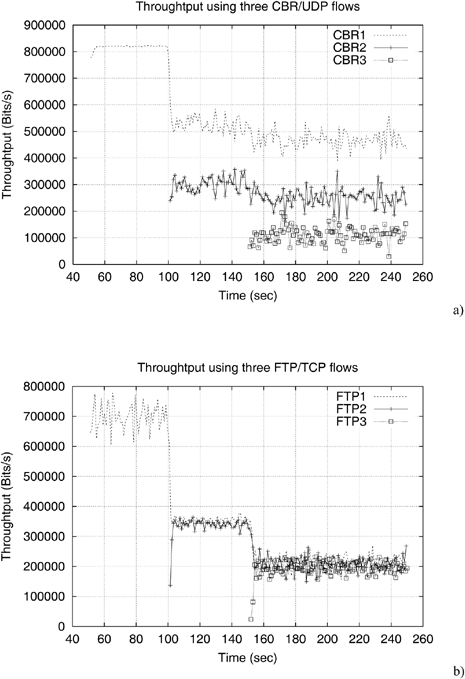
This method, more deterministic, has yielded better results than the previous methods because it enables stricter priorities between UDP flows or between TCP flows [AAD 01, AAD 03]. We have noted, however, that this differentiation was still limited within TCP flows, especially in comparison with the one obtained within UDP flows. The curves in Figure 5.6 clearly show this limitation. These curves, obtained by simulation, consider three flows from three different stations. Each one of these flows overloads the radio link, using UDP traffic (Figure 5.6(a)) for one and using TCP traffic for the other (Figure 5.6(b)). Different priority values (DIFSj) are allocated to these three flows.
Service differentiation techniques presented here and, especially the differentiation by DIFS, enable the introduction of an efficient priority between service classes for UDP traffic. However, differentiation of services for TCP traffic is either inefficient, when talking about differentiation mechanisms based on the Backoff algorithm, or insufficient, in the case of differentiation by DIFS.
Variations of these algorithms [NIA 02] have also been proposed in other works, but the authors reach the same conclusions with regards to the service differentiation within TCP traffic.
In the following section we explain the two centralized access methods proposed or discussed within IEEE 802.11: PCF and HCF.
For the support of services with time constraints, the basic IEEE 802.11 standard defines a centralized access method, known as PCF.
Coordination is done by a station called Point Coordinator (PC). PCF has by definition priority over DCF. Indeed, the time space (IFS) before each transmission from a station using PCF is lower than DIFS but remains higher than SIFS; this space is called PCF Interframe Space (PIFS).
In addition to the division in basic time units (SlotTime), the time is equally separated in what we call superframes. When PCF is used, the superframe is made up of two periods: Contention Free Period (CFP) and Contention Period (CP). These two periods continuously alternate (see Figure 5.7). During the CFP period, the PCF access method is the one used and the DCF method will be used during the CP period. A superframe may not contain a CFP period, yet it is mandatory that it includes a CP period of a length which enables the transmission of at least one MSDU with DCF.
Figure 5.6. Throughputs obtained by using a differentiation by DIFS when the medium is overloaded by 3 stations with different priorities (DIFS1=50μs, DIFS2=130μs, DIFS3=210μs) – (a) UDP traffic and (b) TCP traffic
The superframe starts with the transmission of a beacon frame; this transmission is sent even if PCF is not activated. It is the PC, generally located in the AP, which generates, at regular intervals, the beacon frames. In addition to the announcement of the start of the superframe, the beacon frame also enables the synchronization between station clocks enabling them to know when the CFP period ends, i.e. the time (TBTT5) after which a control frame CF-End will be sent (Figure 5.7).
During CFP there is no contention between stations. Indeed, the stations are invited to transmit through the PC. Thus, the PC requests particular stations, one after the other, to transmit one of its queued frames. Since the CP may also have frames to transmit, it uses, in addition to invitation frames, data frames that it piggybacks to invite the other stations to transmit. A station receiving an invitation to transmit responds by sending a data frame; in the case where the station does not respond to the invitation after a time equal to PIFS, the PC invites another station to transmit. In this way, no inactivity period higher than PIFS is authorized during CFP. The PC continues to transmit invitations until the TBTT time, allocated at CFP level, expires. A control frame (CF-End) is then transmitted to announce the end of the CFP period and the beginning of the CP period. Figure 5.8 shows an example of operations within CFP.
The PCF access method has neither been integrated in commercial products nor implemented at this time. The current cards only use the DCF method. In fact, the PCF access method has many disadvantages, such as:
– the impossibility to recognize delays between control frames. When the TBTT time is reached, the coordinator point is poised to send a control frame (CF-End). However, this can be executed only if the medium is available for a period longer than or equal to PIFS. So, if the medium is not available close to the expiration period of the TBTT timer, transmission of the CF-End frame is delayed. This means that within each CFP unexpected delays can be introduced;
– the impossibility to recognize transmission duration of stations asked to transmit. A station invited to transmit is authorized to transmit only one frame, which can be fragmented. This, added to the fact that the station can use different coding and modulation mechanisms, makes the duration of the fragmented frame transmission unpredictable and uncontrollable by the coordinator point;
– a hidden station that misses the beacon frame will have no information concerning the TBTT or the beginning of the CFP period. It might then continue to transmit using the DCF access method that is causing collisions.
These three problems can clearly deteriorate the QoS offered. Due to these three disadvantages, no strong guarantees can be offered for the transmission of a frame within the CFP.
To make up for the disadvantages of the PCF access method, a more deterministic access method, in terms of transmission time given to stations, is currently being standardized by IEEE 802.11. This technique is called HCF which stands for Hybrid Coordination Function.
The HCF method is an extension of the access rules of the EDCF method. In fact, the hybrid coordinator, HC, may, at any time, self-allocate a Transmission Opportunity (TXOP) to start an MSDU transmission. This can obviously be done only after making sure that the medium is free of any transmission during a time higher than or equal to PIFS, which is of course lower than DIFS, therefore giving it priority over EDCF.
During a CP period, each TXOP starts either when the medium has been declared free according to the EDCF rules (i.e. AIFS + Backoff timer) or when the station receives an invitation (QoS CF-Poll) from the HC to transmit. Thus, the HC may allocate a TXOP to any station during the contention period by using its priority access method to transmit the control frame QoS CF-Poll. During the CFP period, the moment of the transmission start and the maximum transmission length of each TXOP are also specified by HC still using QoS CF-Poll. The CFP period then ends after the expiration of time announced by the beacon frame (TBTT) or by sending the control frame CF-End by the hybrid coordinator.
For the hybrid coordinator to invite the stations to transmit their frames, it needs information concerning the stations’ requirements. Furthermore, this information must be updated frequently. An additional random access protocol enabling a quick resolution of collisions has therefore been defined by IEEE 802.11e to enable the HC to acquire this information. This protocol, called Controlled Contention (CC), tells the HC which station requires an invitation to transmit, when and for how long. This is done when the stations send resource requests (RR), using the Controlled Contention. The Controlled Contention happens only during specific intervals of time, called Controlled Contention Intervals or CCI. During these intervals, RR messages are the only ones authorized. Consequently, no contention is possible between these control frames and other types of frames. One last note, a CCI can be initiated by the HC at any time (CP or CFP period) by the transmission of a CC frame.
The introduction of the TXOP time, as well as its associated resource management mechanisms, is a major improvement compared to the PCF access method. Indeed, this helps the HC to manage with more ease, and more efficiency, the allocation of resources.
Previously, the resource allocation techniques had to operate without knowing beforehand how long the transmissions would last. Consequently, it was harder to efficiently share the CFP period between the different stations.
In order for the HCF to function as efficiently as possible, CCI frequency must be high. This could, however, generate a significant signaling overload.
As explained in the previous sub-sections, the introduction of QoS in 802.11 networks can be divided into two categories: 1) medium access techniques that rely on invitation, PCF and HCF, and 2) techniques based on the introduction of a service differentiation within the distributed medium access technique function, DCF.
The introduction of service differentiation techniques in the DCF function makes up for the complexity in management. However, service differentiation in the case of TCP traffic is either inefficient, in the case of differentiation mechanisms based on the Backoff algorithm, or insufficient, for differentiation by DIFS. Other variations [NIA 02] have also been proposed in other works, but the authors reach the same conclusions with regard to service differentiation within TCP traffic.
With regard to the centralized techniques, on the one hand, the PCF centralized access method does not really make it possible, in certain cases, to offer a guarantee on packet transmission. On the other hand, the HCF access method can generate a signaling overload and a considerable complexity in management. In fact, the choice for optimal size of the superframe [LIN 03] on the one hand, and the allocation of rights to transmit to the different requesting stations on the other hand, necessitate considerable signaling (during CCI periods where frequency has not been determined yet) as well as the development of complex techniques for bandwidth dispatching between stations.
[AAD 01] AAD I., CASTELLUCCIA C., “Differentiation mechanisms for IEEE 802.11”, IEEE Infocom’01, Anchorage, Alaska, April 2001.
[AAD 03] AAD I., CASTELLUCCIA C., “Priorities in WLANs”, Computer Networks, vol. 41, no. 4, p. 505-526, March 2003.
[BHA 94] BHARGAVAN V., DEMERS A., SHENKER S., ZHANG L., “MACAW: A Media-Access Protocol for Packet Radio”, in Proceedings of ACM SIGCOMM, 1994.
[BIA 00] BIANCHI G., “Performance Analysis of the IEEE 802.11 Distributed Coordination Function”, IEEE Journal of Selected Areas in Telecommunications, Wireless Series, vol. 18, March 2000.
[CHA 04] CHAOUCHI H., MUNARETTO A., “Adaptive QoS Management for IEEE 802.11 future Wireless ISPs”, ACM Wireless Networks Journal, Kluwer, vol. 10, no. 4, July 2004.
[CRO 97] CROW B. P., WIDJAJA I., KIM J. G., SAKAI P. T., “IEEE 802.11 Wireless Local Area Networks”, IEEE Communications Magazine, September 1997.
[DUC 92] DUCHAMP D., REYNOLDS N. F., “Measured Performance of a Wireless LAN”, in Proc. of 17th Conf. on Local Computer Networks, Minneapolis, 1992.
[HEU 03] HEUSSE M., ROUSSEAU F., BERGER-SABBATEL G., DUDA A., “Performance Anomaly of 802.11b”, in Proceedings of IEEE INFOCOM 2003, San Francisco, United States, 2003.
[IEE 97] “LAN MAN Standards of the IEEE Computer Society”, Wireless LAN media access control (MAC) and physical layer (PHY) specification, IEEE Standard 802.11, 1997.
[IEE 99a] “High-Speed Physical Layer in the 5GHz Band”, supplement to 802.11-1999, IEEE Standard 802.11A, 1999.
[IEE 99b] “Higher-Speed Physical Layer Extension in the 2.4 GHz Band”, supplement to 802.11-1999, IEEE Standard 802.11B, 1999.
[IEE 02] IEEE 802.11 Task Group E, “Wireless MAC and Physical Layer Specifications: MAC Enhancements for Quality of Service: part 11”, draft supplement to IEEE Standard 802.1, 2002.
[JAK 94] JAKES W. C., “Microwave Mobile Communications”, Wiley-IEEE Press, May 1994.
[LIN 03] LINDGREN A., ALMQUIST A., SCHELÉN O., “Quality of Service Schemes for IEEE 802.11 Wireless LANs – An Evaluation”, Journal of Special Topics in Mobile Networking and Applications (MONET), special issue on Performance Evaluation of QoS Architectures in Mobile Networks, vol. 8, no. 3, June 2003.
[NIA 02] NIANG I., ZOUARI B., AFIFI H., SERET D., “Amélioration de schémas de QoS dans les réseaux sans fil 802.11”, French Colloquium on Protocol Engineering, CFIP’02, Montreal, Canada, May 2002.
[TAY 01] TAY Y. C., CHUA K. C., “A Capacity Analysis for the IEEE 802.11 MAC Protocol”, ACM Baltzer Wireless Networks, vol. 7, no. 2, March 2001.
[VER 01] VERES A., CAMPBELL A. T, BARRY M., SUN L.-H., “Supporting Service Differentiation in Wireless Packet Networks Using Distributed Control”, IEEE Journal of Selected Areas in Communications (JSAC), vol. 19, no. 10, p. 2094-2104, October 2001.
[WEI 97] WEINMILLER J., SCHLAGER M., FESTAG A., WOLISZ A., “Performance Study of Access Control in Wireless LANs IEEE 802.11 DFWMAC and ETSI RES 10 HIPERLAN”, Mobile Networks and Applications, vol. 2, 1997.
1 Chapter written by Yacine GHAMRI-DOUDANE, Anelise MUNARETTO and Hakima CHAOUCHI.
1 EDCF: Enhanced DCF.
2 Note that this possible choice of the persistence factor has been removed from the latest draft but we keep it here for completeness.
3 Transmission Opportunity.
4 See HCF access method (section 5.3.3.2.1).
5 Target Beacon Transition Time.