Figure 20.1. (a) Non-ambient living room (b) ambient living room (source: HomeLab Philips)

In the last few years, new terminologies such as pervasive computing, ubiquitous computing, ambient intelligence, wearable computing, context awareness and always best served (ABS) have emerged. We do not know what terms to use when we talk about the famous third age of technology: the age where computing is such an important part of our lives. The goal of this ever present information technology, however, is always the same in its design which is to make our environment easier by creating, in a manner which is transparent to the user, a physical relationship with the information technology and telecommunications world. The environment becomes more conscious, adaptive and attentive to the user.
This chapter introduces ambient intelligence and its problems, with the emphasis on a very important aspect communication networks. Ambient networks are actually an environment which enables users to easily access different rich and varied services throughout one or more access networks that might be wireless. These networks offer a global connectivity. They are completely transparent and only show the necessary functions to their users.
The chapter is organized as follows: section 20.2 introduces ambient intelligence and its specific problems; section 20.3 presents ambient networks and their different components such as wireless networks (local networks – WLAN, personal networks – WPAN, etc.), ad hoc and sensor networks and the integration of these different environments, as well as an explanation of the available services within these networks; finally section 20.4 concludes the chapter.
Ambient intelligence refers to a new paradigm in information technology in which the processing of information is spread between all the objects within the network and the environment of customers who can then be assisted by an ambient intelligence of that environment. Ambient intelligence is a new paradigm whose goal is to create an intelligent daily work area that is user-friendly and that is integrated within the walls of our homes, in our offices and just about anywhere else. An example of an ambient living room and of a non-ambient living room is shown in Figure 20.1.
In order to offer this functionality to users, a study has to be made in the different information technology areas. As shown in Figure 20.2, ambient intelligence is based on three technologies: ubiquitous computing1, which consists of integrating microprocessors in everyday objects; ubiquitous communication, which enables these same objects to communicate between themselves and with the user through a wireless network and man-machine intelligent interfaces that enable users to control and interact with these objects in the most natural way possible.
Ambient intelligence promises a world filled with small electronic elements, inexpensive, interconnected, autonomous, sensitive to context and with a certain degree of intelligence, all this in our own everyday environment be it personal or professional (in our cars, buildings, trees, the street, etc.). Their use would be multiple; from prevention (fires, accidents) to assistance (guidance, remote control) and comfort (see the example in Figure 20.1). One of their main qualities would be their total transparency, they would be present but completely invisible and interaction with them should also be transparent.
ISTAG (IST Advisory Group) [IST] published a document in 2001 entitled Scenarios for Ambient Intelligence in 2010. It groups together four scenarios, showing what an ambient world could be: the first scenario Maria, road warrior talks about ease of travel with the help of ambient intelligence. It includes avoiding customs formalities, handling customs without us, using a rental car without the need for keys, which also possesses an automatic guidance system and the hotel room which is personalized (temperature, music and lighting). The other three scenarios are entitled Dimitrios and the digital me (D-Me), Annette and Solomon in the ambient for social learning and Carmen: traffic, sustainability and commerce.
Ambient intelligence is not really a subject for research per se. It is in the middle of multiple other research areas, which are not usually cooperative. Since ambient intelligence is related to so many different areas, large organizations are the only ones able to launch research studies on the subject. Therefore, consortiums have recently been put in place between laboratories and large companies in order to promote research in this domain (ITEA Ambience project [AMB], for example).
These domains are organized in three main areas [BAS 03]:
– internal ambient agents (ubiquitous computing);
– interaction between digital ambient agents (ambient networks);
– interface between human and ambient agents (man-machine interface).
An ambient system is usually composed of small multiple interconnected systems. They must be small, inexpensive and as simple as possible. These aspects which are particular to ambient systems are mostly processed at hardware level and concern the following research areas: machine architecture (electronics, energetics, nanotechnologies, etc.) and software agents in general (AI, logic, etc.). Intelligent and communicating objects must integrate perfectly and adapt to people’s daily lives. A good example is that of the camera in the movie Minority Report which, by analyzing the character’s retina, identifies him and sends him a targeted ad according to his consumer habits.
This axis concerns the ubiquitous communication concept and therefore the all-to-all connection and makes all ambient agents communicating. These agents can transmit information with the help of wireless communication support. The goal for ubiquitous computing is to be grouped with ubiquitous communication, processing and data transmission thus becoming an integral part of all objects of everyday life. Let us remember that protocol IPv6 has been designed with these potential applications in mind.
One of the first objectives is therefore to spread wireless communication networks and to make the technology behind the scenes transparent to the user. A second objective is to give the user access to information no matter the location or context.
In order to attain these goals, an important part of the research specifically deals with local and wireless personal networks (WLAN, WPAN), ad hoc and sensor networks. Another part deals with distributed software systems architecture which enables the access to information and services from any terminal, anywhere. These studies focus on with middleware, which requires standards definition (UpnP, HAVi and JINI, for example) enabling interoperability between components of an ambient network.
This axis is the backbone of this chapter and it is detailed in section 20.3.
Finally, the third axis deals with areas studying interaction between humans and ambient agents, in particular, the IHM design area, the automatic processing of the language as well as the sociological aspects of relations between the human and the digital societies. The goal is for this interaction to be more user-friendly and thus more natural.
The ambient network, as shown in Figure 20.3, is a spontaneous environment that enables users (terminals of any type) to access rich and personalized services through one or more fixed or wireless access networks (integration of infrastructures, wired or wireless). This type of network must provide a global connectivity and free itself from its computing nature in order to show only the accessible functions in an intuitive manner.
The fact that this network is ambient implies that it must also guide the user with the help of a group of functions that adapt to his preferences, his current location, the actual context and the capabilities of his terminal. In order to fulfill these objectives, different aspects must be taken into account [AND 03]:
– wireless terminals: there are more and more devices used in our daily lives (phone, PDA – Personal Digital Assistant, sensor, etc.) that are linked through different types of networks, often wireless. Different studies are being done in order to make these terminals less expensive, easier to use, smaller and less power hungry. In section 20.3.3, we will see a category of these terminals, the sensors;
– links: ambient networks use different types of links and different characteristics (bandwidth, delay, coverage). Currently, different networks coexist without real integration. Terminals will have a choice between different technologies: wired (DSL, for example) or wireless such as WLAN (802.11b, 802.11a, 802.11g), WPAN (Bluetooth, 802.15) or UMTS/GPRS. We will present these wireless technologies in section 20.3.1;
– ambient network integration: the user takes advantage of a connectivity that is always present offered by ambient networks and demands adequate application performance in spite of the fact that he may move from one location to another or when he changes terminals. The network must negotiate communications in the name of the user and configure the services found while taking into account the application’s quality of service (QoS) constraints. The complete process should be designed with minimum user intervention. However, the integration of these ambient networks, the mobility management (vertical handover between these different technologies), QoS management and security remain open concerns. These problems are explained in detail in section 20.3.4;
– ad hoc networks: most wireless networks are based on a fixed infrastructure. In order to widen the coverage, new wireless communication solutions are emerging. Among the solutions that eliminate the need for fixed infrastructure in order to communicate are ad hoc networks. The major goal of ad hoc networks is to spread mobility notions to enable access to information and to “anywhere anytime” communication. One of the biggest challenges with those networks is routing since each station can be used by other stations to process data routing. Ad hoc networks are studied in section 20.3.2;
– service discovery: once the ambient network is operational, it should then offer a group of services. The devices in an ambient network can offer their services while others can discover which services are available. These aspects are studied in section 20.3.5.
In an ambient environment, the terminals can choose between different wireless technologies. In this section, we will talk about cellular networks GPRS/UMTS, micro networks, known as wireless LANs – WLANs and nanonetworks, known as wireless personal area network (WPAN).
GPRS (general packet radio service) network is a step up from GSM in packet mode. It is stacked over the GSM network and it benefits from the same radio interface but possesses a new core network adapted to packet transfer. The purpose is to use available slots in the TDMA frame within the GSM to transport packets. The theoretical throughput varies between 9.6 and 171.2 Kb/s based on the number of slots dedicated to packet mode. However, for many reasons, in practice, the useful throughput is of approximately 10 Kb/s output and 30 to 40 Kb/s input. GPRS service enables point-point connections in connected or disconnected mode and multipoint in broadcast or multicast mode. It offers a standardized access to the Internet as well as data exchange volume pricing.
GSM and GPRS can be associated with EDGE, which is a new more powerful radio interface modulation system. Raw throughput is then three times higher, but the deployment of EDGE is more expensive, the hardware modifications are more significant and it can reduce the reach of BTSs (base transceiver station). E-GPRS is EDGE’s main application which respects the specifications of the third generation at a lower cost than those of the UMTS. It therefore becomes the transition solution toward the third generation.
The third generation of mobile networks has not been completely defined. The ITU (International Telecommunication Union) standards organization has launched an international program in the form of a request for proposal, the IMT 2000, to define an international standard. The UMTS (Universal Mobile Telecommunications System) is one of the propositions retained and is backed by Europe and Japan (3GPP), among others. The USA supports the CDMA 2000.
In its current version, the UMTS uses the core of the GSM/GPRS network which corresponds to a compatibility and profitability concern. Globally, the architecture remains the same. The user domain is still made up of a terminal with a chip (U-SIM). The main differences are found in the radio area; the antennae or base stations are called Node B (instead of BTS) and Node B hubs are RNCs (BSC – base station controller).
Theoretical throughput has obviously increased: from 144 Kb/s in rural zones to up to 2 Mb/s in the case of low mobility with good radio conditions (they are inferior in practice). However, this version of UMTS, release 99, is considered too heavy and the following ones will be designed to reduce this complexity. In time, the third generation should no longer be based on the second generation architecture but it should work progressively on an all-IP architecture. The B Node, the gateway to RTC as well as a certain number of servers, will be directly interconnected on one IP network.
A wireless micro network (WLAN) is a network where the stations are no longer linked physically but instead they are linked through wireless support. Although there is no longer a physical link between the different stations of a WLAN, it still retains the same functions as LANs: the interconnection of machines capable of sharing data, services or applications. The WLAN is not an alternative to LAN and it is not designed to replace it. Generally speaking, WLAN is used as an extension to an existing LAN. There are currently two WLAN standards derived from two different standard organizations that are incompatible between themselves: Hiperlan and IEEE 802.11.
IEEE 802.11 [BRI 97, LAN 99] is the first WLAN standard since 2001. It is currently very successful due to its ease of installation, its performance and its competitive price. It relies on IEEE 802’s MAC technique, with a different access technique to the CSMA/CA2 channel. Within the unlicensed 2.4 GHz band, this wireless local network has a cellular architecture described in Figure 20.4. A group of stations, usually one or more computers (laptops or desktops) equipped with an 802.11 network interface card, get together to establish communication between themselves and form a set of basic services or BSS (basic set service). The zone occupied by stations within a BSS is a Basic Set Area (BSA) or a cell. The different APs are linked together through any wireless or wired network.
The most widely used version is 802.11b, also called Wi-Fi (wireless fidelity). This version offers a throughput of 11 Mb/s and does not propose any real handover mechanism. Its security is also weak because it is possible to listen for carriers and thus intercept network traffic (security mechanisms exist but they are insufficient). However, this technology is still young and it evolves rapidly toward versions offering better performance. 802.11a offers communication speed of up to 54 Mb/s within the 5 GHz band. 802.11e and 802.11i propose the introduction of QoS and better security.
Originally from Europe (ETSI – European Telecommunication Standards Institute), the Hiperlan (high performance radio LAN) standard is often cited as a direct competitor to IEEE 802.11, which has retained some aspects of it. Standards developers have favored ATM interfaces, which may explain the competitive advantage of 802.11, based on Ethernet.
The current standard defines two types of Hiperlan, both using the 5 GHz band ratified during the European Conference of Postal and Telecommunications Administrations (ECPT): Hiperlan 1 and Hiperlan 2. Hiperlan 1 offers speeds between 10 and 20 Mb/s, whereas Hiperlan 2 should reach throughputs of 54 Mb/s. This standard is designed better than 802.11, but it is pricey and slow in coming.
The IEEE 802.15 group, called WPAN, was established in 1999 in order to study nanonetworks or networks with a reach of approximately 35 feet and whose objective is to create connections between the different terminals of one user or of multiple users. The network can interconnect a laptop, a cell phone, a PDA or any other device of this type.
In order to reach those goals, industrial groups have been put in place such as Bluetooth or HomeRF.
Supported by thousands of manufacturers, Bluetooth technology is set to become the norm in the WPAN world. A Bluetooth chip integrates all the components on a surface of 5/16th by 5/16th of an inch, and at a very low cost. It uses frequencies within the unlicensed 2.4 GHz band. The terminals interconnect to become a piconet (maximum of 8 terminals), which can also be interconnected to form a scatternet (see Figure 20.5).
Figure 20.5. Bluetooth network architectures: (a) piconet to only one slave, (b) piconet with many slaves and (c) scatternet

Version 1.0 of Bluetooth enables a communication between two terminals with a maximum throughput of 1 Mb/s which may not be enough for some applications. The goal of the 2.0 workgroup is to increase this throughput and to put in place enhancements (handover, routing optimization, coexistence with the other networks within the 2.4 MHz band).
Another technology, which emerged from home automation, competes with Bluetooth: HomeRF. A base station communicates with different units in a range of 165 feet within the 2.4 GHz band. Basic throughput is at 1.6 Mb/s but should increase. Its characteristics are comparable to those of Bluetooth but it is not endorsed by as many manufacturers as Bluetooth.
Due to the commercial success of wireless local networks, mobile equipment development has been steadily growing. The user is becoming more and more mobile with the help of PDAs and laptops. In this context, new, more powerful wireless communication solutions are starting to come out. Among these main solutions, which eliminate the need for a fixed communication infrastructure, are ad hoc networks.
Ad hoc networks are particular wireless local network architectures based on technologies such as Wi-Fi. However, while each Wi-Fi network user is connected via a radio base, in an ad hoc network the terminals can also communicate between each other without outside help and thus without any infrastructure. They can even serve as relays for each other. It is a sort of “soft architecture”, progressive and automatic. The key is flexibility and autonomy, since the network evolves according to accesses and current users. It can also be completely independent of any infrastructure. Besides, the reach of the signal is scaled according to the number of users and the throughputs can be preserved, but they must be shared with a Wi-Fi radio base.
Figure 20.6. Example of an ad hoc network (the circles represent the radio reach of each ad hoc station)
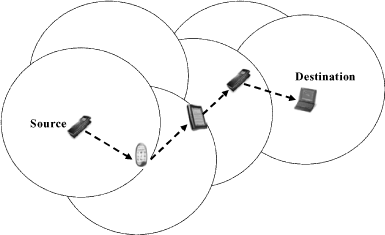
Each station can be called by other stations to route data. In this way, when a transmitting station is out of reach of the destination station, network connectivity is maintained by intermediary stations. An example of an ad hoc network is illustrated in Figure 20.6 in which a transmitting station communicates with a destination station by using intermediary nodes. Globally, there are two families of ad hoc routing protocols: “proactive” routing protocols, which anticipate the request for packet transmission and “reactive” routing protocols that react to the demand. Between these two families, another approach is starting to emerge, “hybrid” protocols that are based on both proactive and reactive protocols. You will find below a general overview of these protocols and their main characteristics.
Proactive routing protocols in mobile ad hoc networks are based on the same principle as the routing protocols used in wired networks. The two main methods used are “link state” and “distance vector”. These two methods require a periodic routing data update that must be transmitted by the different network routing nodes. The most important protocols in this class are LSR (link state routing) [HUI 95], OLSR (optimized link state routing) [CLA 03] and DSDV (dynamic destination-sequenced distance vector) [PER 94].
Routing protocols that belong to this category create and maintain the routes as needed. When the network needs a route, a route search procedure is launched. The most important protocols in this class are DSR (dynamic source routing) [JOH 03b] and AODV (Ad hoc on demand distance vector) [PER 03].
The main goal of ad hoc networks is to extend mobility notions in order to enable access to information and to communicate “anywhere anytime”. IETF3’s MANET Group [MANET] research shows that development of these wireless and infrastructureless networks is growing rapidly. Developers are already imagining all sorts of applications: military, obviously, to create mobile tactical networks, but also civil for emergency procedures, communications with vehicles, reconfiguration of wireless networks in companies or even the creation of temporary networks surrounding special events. Without a doubt, the major advantages of this new generation of mobile networking are flexibility and low cost.
The absence of a fixed infrastructure, however, poses a number of non-trivial problems such as security, adoption of global network management policies (invoicing, QoS offering) and the autonomy of batteries [SEN 03].
Sensor network technology is still very young, miniaturization is insufficient, but the trend is there to stay: from flower pots to vehicles, from bridge structures to production chains. We will see more and more sensors in all aspects of our lives, designed to measure a large number of signals and to communicate them to control centers via wireless networks. We can find these network applications anywhere permanent data collection can be useful; health, war, climatology, process control and seismology. In fact, sensors can function within large machines, at the bottom of an ocean, in biologically or chemically contaminated areas, in a battlefield far into enemy lines, inside a building or a home.
In order to get there, though, the challenges remain significant. However, laboratories and companies are starting to offer innovative products in that sector.
But what is a sensor node? As shown in Figure 20.8, a sensor node is made up of four basic components: a detection unit, a processing unit, a communication unit and a battery. There might be other components such a tracking system, a power generator and a motor. The detection unit is often composed of two sub-units: the detector and the analog-digital converter (ADC). Analog signals transmitted by the sensor are converted into digital signals through an ADC and are then introduced into the processing unit. The processing unit, which usually has a small storage unit associated with it, manages the necessary procedures in order to collaborate with the other nodes in the network in order to complete assigned tasks. The communication unit links the node to the network. One of the most important components of a sensor node is the battery. Batteries can be fed by power generators such as solar batteries. Most of the routing techniques in sensor networks require an exact location of the sensors. It is therefore common practice that a sensor node has its own tracking system. The motor can be necessary at times in order to move a sensor node.
A sensor network is composed of a large number of sensor nodes deployed either one by one or in bulk and in an ad hoc manner inside or very close to the observed phenomenon. The position of the sensors does not need to be predetermined. This aspect is important for areas that are inaccessible, for example (biologically or chemically contaminated areas). However, and at any moment, other sensor nodes can be redeployed in order to replace failing nodes or if there is a change in the task to accomplish.
The differences between sensor and ad hoc networks presented previously are summarized below:
– the number of nodes is a lot higher in sensor networks than in ad hoc networks. In a sensor network the distance between the nodes is often less than 33 feet and the density can be higher than 6 nodes/f3;
– sensor nodes are deployed either randomly or placed one by one by a robot or a human;
– sensors can fail (loss of power, physical damage, interference, etc.). This breakdown should not affect the global task of the sensor network. Therefore, reliability and fault tolerance are the main characteristics of sensor networks;
– the topology of a sensor network can change very frequently;
– sensor nodes mainly use broadcast communication, whereas most ad hoc networks are based on point-to-point communication;
– sensors are nodes limited in power, computing capabilities and memory.
So, contrary to ad hoc networks, the design of a sensor network is influenced greatly by different factors such as fault tolerance, scaling, cost of production that must be low, the environment, the network’s topology, hardware constraints, the transmission medium as well as energy consumption.
The authors of [AKY 02] explain the layered architecture of a sensor network which comprises a physical layer, a data link layer, a network layer, a transport layer and an application layer. For the authors, energy consumption is the main factor to take into consideration for each of these layers. For example, in the case of routing, routes are often traced according to energy metrics. They list different algorithms; here are the most important:
– routing based on residual power: in this type of routing, the route chosen is the one with the maximum of the sums of residual energy (Er) of the nodes in the route;
– routing based on transmission power: in this type of routing, the route chosen is the one with the minimum of the sums of required transmission power (Et) of the links in the route.
The authors also mention a group of research studies that are needed for each of these protocol layers.
Without a doubt, the major advantages of these networks are their flexibility, fault tolerance and deployment speed. These advantages will make the networks an integral part of our daily lives. However, new technologies are needed due to the specific constraints of this type of network.
The different ambient networks form a cell hierarchy of different sizes and throughputs (Wi-Fi, UMTS, Bluetooth, etc.). At one geographic point, one or more of these networks will be available. This concept of hierarchy has been explained clearly for the first time in the article The Case for Wireless Overlay Network [KAT 96]. The promise consists of ending competition between the different networks and to make them coexist in order to offer the best technology for each type of application. A user wanting to use a service can not only choose one available access network, but the most adequate and that which will satisfy his needs the most. He may also change networks if another network is better than the one he is using. This process should be designed for a minimal user involvement. This philosophy has produced what we call ABC for “always best connected”.
In order to illustrate this concept, we can use the classic example that we see in the majority of articles about this problem and which is shown in Figure 20.9 [GUS 03].
The ABC concept enables a better connectivity for the user by using terminals and access technologies that are most adapted to the needs and context. However, an ABC scenario, where we allow the user to choose the best access networks and terminals available, can create significant complexity not only technical but also in terms of policy between the different access operators and service providers. Therefore, different aspects must be considered [GUS 03]: user’s experience, agreements between these access operators and service providers and technical solutions for the terminal and the network.
User experience concerns the manner in which to supply ABC service to the users. Many factors have been identified [GUS 03]: subscription or payment for ABC service, information delivery, mobility management and user interaction:
– subscription: the simplest scenario is that the user has only one subscription to one access operator, which makes invoicing much more simple. That way, a unique identifier is associated with the user for all visited ambient networks. This is similar to the notion of roaming in cellular networks. On the other hand, this implies that the access networks which will communicate authentification and authorization information through an AAA infrastructure (Authentication, Authorization and Accounting) are adequate.
EXAMPLE.– Laetitia wakes up in the morning and links her laptop to the Internet using a DSL connection (supplied by her Wanadoo service provider). She wants to check her email and connects to her company network via a VPN (Virtual Private Network) connection. She can then read and send email. Laetitia starts a download on her laptop and realizes that she is late for a meeting. She unplugs her computer from the DSL modem and leaves her house. When the laptop is disconnected from the DSL, it commutes automatically to the access network that is available, in her case GPRS (provided by Orange). The VPN connection is maintained and the download continues. In the subway in Paris, she starts a conversation on NetMeeting with colleagues in Holland by using her PDA. The PDA is linked by using GPRS. Due to the limited text/voice capabilities of her PDA and the GPRS network, NetMeeting adapts and grants access only to voice/text services. When Laetitia arrives at her office, she transfers her NetMeeting session from her PDA to her laptop, which is now linked to the WLAN of the company. Because the capabilities of the laptop and the WLAN are much better, NetMeeting adapts by adding a video service.
– information delivery: a major part of user experience is the behavior of the application. Applications must adapt to environmental changes in order for the delivery of information to be the fastest and adjust to the terminal’s capabilities and the access network’s technology while optimizing the presentation of information. The applications may, autonomously or by using the user profile, require a QoS (QoS) in order to provide an optimal execution;
– mobility management: in its most simple form, ABC service provides the possibility for the user to access different network technologies without any mobility management behind. Therefore, another service to consider consists of offering the possibility for a terminal to move between the different technologies, while maintaining current connections. That is what is called a vertical handover and is the object of section 20.3.4.3. Other services could also enable a user to transfer a session from one terminal to another, without any loss of data or having to restart the application (see the example of Laetitia above);
– user interaction: the user should have the tools that provide necessary ABC information while giving him the possibility of changing the access manually, for example. These tools must be simple and easy to use by an average user.
The user can go from one network to another. This implies that there are agreements between the access operators in order to manage the roaming, agreements between access operator and the service provider, agreements between the access operator and the company’s network and between the operator and/or the ABC service provider. Another point to consider is the subscriptions, user profiles and AAAs management.
Terminals, network servers, applications and services are some of the entities affected when an ABC solution is put in place. In fact, a user would need a more intelligent terminal with the capability to access multiple networks: a multi-interface terminal, also called multimode. Certain studies [KAT 98] propose only having one interface among the actual ones that communicate at a given time, in order to optimize network change latency. Other more recent studies describe simultaneous data reception over different interfaces. This approach is therefore technically possible, but it poses certain problems such as energy consumption.
There are different physical architectures involved in the realization of multiinterface terminals [ARE 01, KON 00]. The most simple consists of setting different radio interfaces in parallel, as shown in Figure 20.10(a). However, in this way, the terminal is not progressive: it cannot adapt to the arrival of a new network. On the other hand, as presented in Figure 20.10(c), a single programmable interface can connect to any frequency with any received signal process. This solution is obviously the most flexible. An intermediate solution exists and is presented in Figure 20.10(b): a fixed number of radio-frequency receivers are controlled by a unique signal process unit, which is configured by necessary parameters. These different approaches are still being discussed based on economic, performance and adaptability criteria. A major criterion is energy consumption, which is essential in portable terminals [STE 96].
The change of interface is called a vertical handover: the terminal changes access networks without necessarily changing its geographic position as is the case with classic handover, also called horizontal handover (change of base station in a same access technology). This change must be done transparently to the user, without interfering with his current services.
Many studies have been done. The first article on this subject [KAT 98] exposes the different problems to take into account: latency, power supply problem for interfaces that must remain active, overload, etc. This study considers that the best network is the lowest in the hierarchy, i.e. the one having the largest throughput. However, the choice for the best network is more complex and must take other criteria into account. This is the subject of another article [WAN 99] which proposes separating the choice of the best network and the handover mechanism. After picking up parameters on the different available networks and the user’s preferences, the terminal executes a cost function for each network and retains the best. The user has very little input: it takes into account only certain aspects such as cost or performance. However, application requirements such as QoS parameters are not taken into account.
Multiple interface management is often seen as a particularity of Mobile IP [PER 96, JOH 03a] or more generally as a mobility problem. Instead of having only one temporary multicast address, we have either multiple, or a unique temporary multicast address. Therefore, an interface change corresponds to a temporary address change. Each article [WAN 99, KAT 98, ZHA 98, CHE 96] defines an extension of the Cellular IP, Mobile IP or a Mobile IP-like protocol which enables multi-interface and mobility management.
One of the objectives of ambient networks is to enable mobile user to access and provide services independently from time and place. From there, a new requirement (function) has come out, that of discovering automatically and without external interference the group of desired services available within the current domain of the mobile terminal. A new function needs a new tool and therefore several studies are in place in industrial and research contexts, thus introducing service discovery (SD) protocols.
A service discovery protocol is a process supplying automatic and spontaneous mechanisms for the location of services provided in a network. It enables servers to publish, or notify their services and clients to discover these services in some form of necessary autoconfiguration.
In order to illustrate the requirement for service discovery protocols, we can use the classic example found during each protocol specification. Let us imagine a mobile terminal that enters a network for the first time and that wishes to print a document. It must locate the network printers, compare them according to their capabilities (printing postscript documents, printing in color, printing as fast as possible, etc.) and then choose one for its document. Service discovery protocols enable the execution of this location task, spontaneously, without operator intervention. Figure 20.11 illustrates an example of a meeting room where a new lecturer wants to project his presentation and print it in order to give copies to the different participants.
Service discovery protocols eliminate the need to know the name or address of the equipment within the service. The user only has to name the service, by entering its type, and to supply the list of attributes needed. The discovery protocol will take care of matching the user’s description with the address of the appropriate service, thus providing an automatic configuration mechanism for the applications within local networks.
Different approaches exist concerning the design of service discovery protocols: the reactive approach and the proactive approach.
This is an on-demand concept, where the discovery process is only executed when there is a user request for a specific service. There are two variables: a distributed approach, and a centralized approach.
Within the distributed reactive approach, a request is sent over the network (for example, in multicast) specifying the wishes of the user requiring a specific service. On the service side, a service agent, always monitoring the network, hears this request and responds to it (unicast) if it corresponds to the service that implements it. The client then has to choose between all the responses obtained. This method is better suited to small networks with limited spread. It presents the disadvantages linked to transmission in wireless networks.
The centralized reactive approach requires that a services directory is present. Each available service is registered in this directory by the delivery of a registration request at launch. As soon as the client has a request for a specific service, he just needs to notify the central node of his request in order to receive the required information and therefore communicate with the appropriate service. In the case where multiple services are available, the choice can be made either at directory level or by the client. As with any technology implementing a centralized philosophy, this approach presents the disadvantage of failures. The SLP (Service Location Protocol) service discovery protocols and Jini are examples of reactive protocols.
This is a prepared-type approach which anticipates clients’ requests. Each service agent periodically broadcasts a message announcing its presence on the network. Therefore, at each moment, any element that is present possesses a complete list and updates of the available services. A new client in the network will receive this list and will be able to use the services directly when needed, without additional obligations.
This approach is distributed and distinguishes itself by very short response times. In fact, as soon as the use of a service becomes necessary, you only need to view the list on your local network to obtain it. The downside is that it consumes large amounts of bandwidth, thus decreasing the network’s performance. The UPnP (Universal Plug and Play) service discovery protocol is an example of proactive protocols.
In conclusion, if our objective is to shorten response times, this approach seems the most logical one. On the other hand, if our major concern is to conserve bandwidth, it is best to use a reactive method.
Ambient intelligence is a nice name, representing a new paradigm in information technology and grouping a multitude of technologies. People, in an ambient world, are assisted by a digital environment that is sensitive, adaptable and responsible for their needs, habits, movements and emotions.
Ambient intelligence is located at the junction of many domains which are not usually cooperative (IA, IHM, telecoms, etc.) and that we have introduced in this chapter. This new paradigm has set innovative communication technologies, often wireless, which enable the formation of ambient networks that will contribute to people’s quality of life. The future communication networks will supply a global connectivity and therefore will assist, in a transparent manner, the user with very advanced services. They will make the underlying technology invisible to the user. Access to information and control of the environment will become more transparent to the location, terminal and context (new user interfaces, rapid response time, control of different types of wireless terminals, availability and security, etc.).
This chapter describes different aspects of ambient networks where user satisfaction is the dominant factor: wireless communication networks and their integration, mobility management, ad hoc networks, sensor networks as well as the discovery of available services. One of the major qualities of these networks would be their total transparency: they would be present, but completely invisible to us, interaction with them should be just as transparent.
In order to achieve these objectives somewhat futuristic and promised by ambient networks, several questions are still open. We expect them to offer global and varied connectivity at minimum cost, a larger capacity and QoS guarantees. The terminals must also be more sophisticated, more user-friendly and equipped with more natural interfaces, multimodal and auto-configurable. Accumulating these multiple functions obviously generates a large number of challenges and a considerable complexity.
[AKY 02] AKYILDIZ I. F., SU W., SANKARASUBRAMANIAM Y., CAYIRCI E., “A Survey on Sensor Networks”, IEEE Communications Magazine, vol. 40, no. 8, p. 102-114, August 2002.
[AMB] ITEA Ambience project, http://www.extra.research.philips.com/euprojects/ambience.
[AND 03] ANDRZEJ D., “Ambient Networking”, Smart Object Conference – SOC’2003, Grenoble, France, May 2003.
[ARE 01] ARETZ K., HAARDT M., KONHÄUSER W., MOHR W., “The Future of Wireless Communications Beyond the Third Generation”, Computer Networks, vol. 37, no. 1, p. 83-92, September 2001.
[BAS 03] BASKIOTIS N., FEREY N., Cours en introduction à l’intelligence ambiente, 2003.
[BRI 97] BRIAN P. CROW, WIDJAJA I., KIM J. G., SAKAI P. T., “IEEE 802.11 Wireless Local Area Networks”, IEEE Communication magazine, p. 116-126, September 1997.
[CHE 96] CHESHIRE S., BAKER M., “Internet Mobility 4×4”, ACM SIGCOMM, p. 318-329, Stanford, August 1996.
[CLA 03] CLAUSEN T. (ED.), JACQUET P. (ED.), “Optimized Link State Routing Protocol”, MANET working group, IETF, http://www.ietf.org/rfc/rfc3626.txt, October 2003.
[GUS 03] GUSTAFSSON E., JONSSON A., “Always Best Connected”, IEEE Wireless Communications, p. 49-55, February 2003.
[HUI 95] HUITEMA C., Routing in the Internet, Prentice Hall, 1995.
[IST] ISTAG – IST Advisory Group, http://www.cordis.lu/ist/istag.html.
[JOH 03a] JOHNSON D., PERKINS C., “Mobility Support in IPv6”, Mobile IP Working Group, IETF Internet-Draft, draft-ietf-mobileip-ipv6-24.txt, June 2003.
[JOH 03b] JOHNSON D. B., MALTZ D. A., HU Y.-C., “The Dynamic Source Routing Protocol for Mobile Ad-Hoc Networks (DSR)”, MANET working group, IETF Internet Draft, draft-ietf-manet-dsr-09.txt, April 2003.
[KAT 96] KATZ R. H., BREWER E. A., “The Case for Wireless Overlay Networks”, Proc. SPIEE Multimedia and Networking Conference (MMNC’96), p. 77-88, San Jose, CA, January 1996.
[KAT 98] KATZ R. H., STEMM M., “Vertical Handoffs in Wireless Overlay Networks”, Mobile Networks and Applications, vol. 3, no. 4, p. 335-350, 1998.
[KON 00] KONHÄUSER W., MOHR W., “Access Network Evolution Beyond Third Generation Mobile Communications”, IEEE Communication Magazine, December 2000.
[LAN 99] LAN/MAN Standards Committee, ANSI/IEEE Std. 802.11: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications, IEEE Computer Society, 1999.
[MANET] IETF MANET Working Group (Mobile Ad-Hoc NETworks), www.ietf.ora/html.charters/manet-charter.html.
[PER 94] PERKINS C. E., BHAGWAT P., “Highly Dynamic Destination-Sequenced Distance-Vector Routing for Mobile Computers”, ACM SIGCOMM’94, p. 234-244, October 1994.
[PER 96] PERKINS C., “IP Mobility Support”, IETF RFC 2002, October.
[PER 03] PERKINS C. E., BELDING-ROYER E. M., DAS S. R., “Ad-Hoc On-Demand Distance Vector (AODV) Routing”, MANET working group, IETF, http://www.ietf.org/rfc/rfc3561.txt, July 2003.
[SEN 03] SENOUCI S., Application de techniques d’apprentissage dans les réseaux mobiles, PhD Thesis, Pierre and Marie Curie University, Paris, October 2003.
[STE 96] STEMM M., GAUTHIER P., HARADA D., KATZ R. H., “Reducing Power rd Consumption of Network Interfaces in Hand-Held Devices”, Proc. 3 Workshop on Mobile Multimedia Communications (MoMuC-3), September 1996.
[WAN 99] WANG H. J., KATZ R. H., GIESE J., “Policy-Enabled Handoffs Across Heterogeneous Wireless Networks”, Second IEEE Workshop on Mobile Computing Systems and Applications (WMCSA‘99), New Orleans, LA, February 1999.
[ZHA 98] ZHAO X. et al., “Flexible network support for mobility”, MOBICOM’98, p. 145-156, October 1998.
1 Chapter written by Sidi-Mohammed SENOUCI.
1 Ubiquitous computing by Marquez Weiser: it is the exact opposite of virtual reality. Whereas virtual reality immerses people inside a world generated by the computer, ubiquitous computing forces the computing devices to integrate in people’s everyday lives. Virtual reality relies mostly on computing power. Ubiquitous computing is the result of a difficult integration of human factors, information technology and social sciences.
2 CSMA/CA: Carrier Sense Multiple Access with Collision Avoidance.
3 IETF: Internet Engineering Task Force.