Figure 21.1. Topology in infrastructure mode
Ambient networks, and more importantly wireless networks, are the main networks that surround us. In time, the user will have the possibility of connecting to one of these networks and of changing it during his communication. The ambient Internet is starting to emerge with the first wireless networks and more specifically with the explosion of Wi-Fi networks. The objective of this chapter is to give an overview of this first vision of the ambient Internet.
After an introduction of the technology used in these Wi-Fi networks, we will explain in detail its functionality and its improvement throughout the changes before concluding on its prospects.
After the first fundamental experiment on radio conduction executed by the French physicist Edouard Branly in 1890 in his laboratory at the Institut Catholique de Paris1 and the transmission of the first wireless telegram between Wimreux and Douvre by the Italian physicist Gulglielmo Marconi to Edouard Branly in 1899, wireless communication, i.e. using radio waves, has continuously progressed.
With the emergence of laptop computers, the notion of mobility has grown rapidly. The need to connect without wires in order to attain real wireless communication has quickly become a necessity.
At the beginning, many solutions have been proposed by companies, but due to their diversity, they were not interoperable. Defining a common norm has quickly become necessary in order to develop this market.
Two organizations intervened in this approach:
– IEEE (Institute of Electrical and Electronics Engineers) is responsible for the technological certification that is the 802.11 standard;
– WECA (Wireless Ethernet Compatibility Alliance) has created the Wi-Fi (wireless fidelity) label in order for the manufacturers to validate their products’ interoperability. WECA has since been replaced by the Wi-Fi Alliance.
The IEEE was already responsible for the standardization of wired networks for the cabling, the physical layers and linking, under the 802 (LAN, Local Area Network) label. IEEE 802.11 has then become the name for this standard which guarantees interoperability and Wi-Fi is its commercial name.
There are different needs for wireless connections:
– the interconnection of peripherals to a computer or between different pieces of equipment together within a close proximity, WPANs (wireless personal area network);
– local networks of computers to cover an office or a building, within 300 feet, WLANs (wireless local area network);
– metropolitan networks covering an area or a city of several miles, WMANs (wireless metropolitan area network);
– extended networks to cover a territory of hundreds of miles, WWANs (wireless wide area network).
Wi-Fi/IEEE 802.11 is a part of WLANs. It connects desktop computers, laptops or PDAs (personal digital assistant) equipment types through radio waves. The current performance can reach 54 Mb/s covering about three hundred feet. The main service offered is the Internet access without bothersome cables where the network is ensured through bridges.
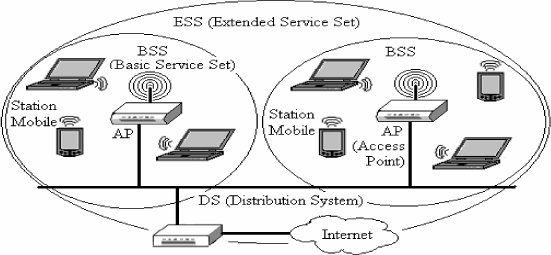
Topology is based on the cell. A cell is called a BSS (Basic Set Service). It is used in two modes:
– the infrastructure mode (see Figure 21.1) is a topology where the cell is centered around a base station that is called Access Point (AP) and a BSS is therefore controlled by an AP. The APs can be linked together by a Distribution System (DS) that plays the role of backbone between BSSs in order to form an ESS (Extended Set Service);
– the ad hoc2 mode (see Figure 21.2) is a topology without infrastructure made up of IBSSs (Independent BSS) and there are no APs in this case. It connects mobile stations which are in the same reciprocal coverage zone and therefore they “see” each other.
There are two kinds of hardware in Wi-Fi/IEEE 802.11 networks:
– wireless stations which are laptop computers or PDAs equipped with a WNIC (wireless network interface card);
– access points which are boxes that control the exchanges and ensure bridge function with the cable network.
Wireless technology must resolve numerous problems that cable networks do not face. Among others, there is the necessity to find an available and adequate global bandwidth to support it (see Appendix B for the concerns that this problem causes with the diversity of amendments d, h and j), controlling signal degradation3, user mobility, preserving communication confidentiality, taking into account limited battery life, being concerned for human health4, etc.
This list is compatible with all those with the norm IEEE 802, which is close to the ones defined within OSI (open system interconnection) (see Figure 21.3). There is a physical layer compatible to that of OSI and a linking layer made up of two sublayers contrary to that of OSI:
– an MAC (medium access control) sub-layer which determines the way that the radio channel is allocated, i.e. which is the next station authorized to transmit;
– an LLC (logical link control) sub-layer which presents to the higher network layer a homogenous interface whatever the type of IEEE 802 network used.
The goal of this layer is to transmit a MAC frame from one station to another. Electric engineering is the competency required in order to achieve its goal. The major differences concern the properties of the frequencies used (sensitivity, directivity, reach) and the modulations providing the appropriate throughputs and responses based on the requirements.
It is divided in two sub-layers:
– underneath, PMD (physical medium dependent) controls coding and modulation;
– above, PLCP (physical layer convergence protocol) listens to the support and provides a CCA (clear channel assessment) to the MAC layer to indicate that the support is available.
Several types exist.
This transmission which broadcasts frequencies at 0.85 µ or 0.95 µ offers two throughputs of 1 and 2 Mb/s according to the encoding system used.
It does not go through the bulkheads and therefore it enables good area isolation. However, it is sensitive to sun rays. It has not been successful.
Two transmission methods by radio wave within the low reach 2.4 GHz5 band use spread spectrum techniques.
The band is divided in 79 channels6 of 1 MHz each with a GFSK (Gaussian frequency phase keying) modulation. A random number generator produces the sequence for the frequencies to follow. Two stations which feed their generator with the same starting value (seed) at the same time as they are synchronized can communicate. Dwell time for each frequency is parameterizable but must be lower than 400 ms.
The advantages are: a fair allocation within the total allocated spectrum, an important improvement in security (listening-in is impossible without knowing the sequence and the utilization period of each frequency), good resistance to multipath propagation over long distances (because the utilization period over a frequency is short), good immunity to radio interference, a 26 network colocation in one location.
The disadvantage is its low throughput, which stays limited to 2 Mb/s.
The band is divided in 14 channels7 of 20 MHz with 1 channel per BSS.
Throughputs are limited to 1 Mb/s with Binary Phase Shift Keying (BPSK) modulation of 1 bit per baud and 2Mb/s and a Quadrature Phase Shift Keying (QPSK) modulation of 2 bits per baud.
In order to limit noise effects, a technique (chipping) enables the extension of 1 data bit into 11 bits used by a Barker sequence. A theoretical maximum colocation of 3 BSS is possible.
This technique offers a maximum theoretical throughput of 54 Mb/s. It is used in the IEEE 802.11a 5 GHz8 band. It uses 52 frequencies of which 48 are attributed to data and 4 to synchronization.
It is a complex coding technique which is based on a phase leading modulation to offer high throughputs even with QAM (Quadrature Amplitude Modulation). At 54 Mb/s, 216 data bits are coded in 288 bits9 symbols.
This offers the advantage of an efficient use of the spectrum in number of bits per hertz and a good immunity against multipath propagation interferences.
This technique is also used in the IEEE 802.11g 2.4 GHz band.
This technique, which works in the 2.4 GHz band, offers a maximum theoretical throughput of 11 Mb/s. It is used in the IEEE 802.11b norm.
A CCK (complementary code keying) coding technique is added to QPSK modulation.
Wi-Fi proposes the adjustment of throughputs according to the quality of transmission which is related to the environment and the distance. This mechanism (variable rate shifting) enables the automatic variation of the maximum throughput for each station from 11 to 5.5, then 2 and finally 1 Mb/s in the worst of cases. In the case of IEEE 802.11a products, the different throughputs go from 54, 48, 36, 24, 18, 12, 9 to 6 Mb/s.
The advantage is mandatory communication in the worst case scenario. On the other hand, the disadvantages can be numerous: high throughput stations must wait for slower exchanges from low throughput stations and real-time flows (video flows, for example) would suffer from this variation.
The goal of this sub-layer is to determine the way in which the channel is allocated, i.e. which station will be the next one able to transmit. Computer engineering is the competency required in order to achieve this goal. It also controls frame addressing and formatting, error control from CRC, fragmentation and reassembly, Quality of Service (QoS), energy, mobility, security.
The characteristics of the radio medium are completely different from those of wired medium.
Indeed, contrary to Ethernet, it is impossible to transmit and listen at the same time (in full-duplex) to detect if a collision is happening during the transmission. The CSMA/CD (carrier sense multiple access with collision detection) technique is therefore ineffective. Furthermore, there are inherent problems with the radio medium.
In fact, let us consider 3 stations (see Figure 21.4a) on the same frequency A, B and C where A and B see each other, B and C see each other, but A and C do not see each other. A communicates with B. C also wants to communicate with B, but cannot detect that A is communicating with B. If C transmits, then there is a collision in B. This situation is called “hidden station problem”. Here, A is hidden from C and vice versa.
This situation brings up another problem (see Figure 21.4b). B sees A and C, but A and C still do not see each other. A transmits to a D station which is not within B’s reach. B chooses not to communicate with C due to the perceived activity in the cell shared with A. This situation is called “shown station problem”. In this case B is shown by A.
In order to resolve these problems the IEEE 802.11 norm accepts two modes of operation.
In this mode, the coordination function is distributed. It resembles Ethernet where it does not call on any centralized entity. It is distributed evenly between all stations in the cell (AP included in infrastructure mode). All transmitters therefore have an equal opportunity to access support (it is a sort of best effort). It is viable for asynchronous applications. This is a mandatory mode in IEEE 802.11. It is the only usable one in ad hoc mode.
The recommended technique is CSMA/CA (carrier sense multiple access with collision avoidance). It stems from the traditional CSMA. Two listening methods are possible.
Each frame is separated by an appropriate inter frame space (IFS) as we will see later (see Figure 21.8).
The transmitting station listens to the channel (see Figure 21.5) and initializes a transmission counter N to 0.
IF the channel is available
THEN
IF it remains available for a time higher than a DIFS (DCF Inter Frame Spacing)
THEN
(1) The station can transmit the data. It informs the group of listening stations of the theoretical maximum exchange time. This time is placed in a NAV field within the data frame (see Figure 21.10).
The transmission is done in its entirety no matter what (collision, interference, etc.).
The receiving station verifies if the CRC (Cyclic Redundancy Check) of the received message is valid, then sends or not an ACK (acknowledgment) after a SIFS (Short IFS) such as SIFS>DIFS in order to ensure that the current exchange is not interrupted by a new exchange from other stations.
IF the receiving station does not receive an ACK,
THEN
It considers that the message has not been received and will attempt to resend it (N is incremented) a certain number of times and go to (2).
OTHERWISE
Go to (2).
OTHERWISE
(2) The transmitting station listens to the channel and tries to extract the NAV field in order to find out the theoretical maximum time for the current exchange to avoid disruption. Once the channel is available again.
IF it stays available for a time higher than a DIFS
THEN
IF no random delay has been drawn (Timer Backoff)
THEN
Draw a random delay (Timer Backoff) between 0 and (CWmax=2K+N-1)*time_slot; where CWmax is the Contention Window, N is the retransmission number and K is the minimum size of the contention window
Waiting for an event:
EITHER the Timer Backoff has expired
THEN to transmit go to (1).
OR the channel is busy once again (by another station whose Timer Backoff has expired previously)
THEN the current Timer Backoff is reduced according to the elapsed time (entire time_slot number because all stations are synchronized) then go to (2)
OTHERWISE
Go to (2).
By multiplying by two the contention window size for each collision (because N is incremented in this case), the stochastic wait algorithm in the case of exponential collision (Backoff) enables a greater reduction of the probability that a collision will happen for all the stations that have drawn the same Timer Backoff.
The only time when this algorithm is not used is when a transmitting station notices that the channel is available when needed and that it remains that way during a DIFS (the case where the first two algorithm tests are true).
This is derived from MACAW (Multiple Access With Collision Avoidance For Wireless LAN) which starts a preliminary exchange between 2 parties to send a signal to the environment that an exchange will take place.
This enables the resolution of the “hidden station” problem and thus reduces collision risks.
In this example A and B see each other and A wishes to transmit to B (see Figure 21.6):
– A listens to the virtual channel (VC);
– if the channel is available, then A requires permission to transmit by sending an RTS (request to send) which is a little 30 byte frame;
– B receives the RTS and decides whether to reject or accept the request;
– if B accepts the request then B transmits an invitation to transmit CTS (clear to send) after an SIFS;
– A receives the CTS, also waits for an SIFS then transmits the data;
– after the transmission and the wait time for an SIFS, A receives an ACK transmitted by B. If the acknowledgement is not received then the complete transmission has to be restarted.
After the RTS/CTS exchange, A and B are sure that the channel has been reserved for the data transmission without collision. Indeed:
– let us presume that C sees A but not B:
- seeing the RTS, C declares the virtual channel busy and will therefore not transmit until the timer expires (network allocation signal) indicated in a NAV (network allocation vector) field (see Figure 21.10) which is located in the RTS frame;
- therefore C does not collide with the current exchange with A,
- A can then receive the CTS and the ACK without collision;
– or D sees B but not A:
- seeing the CTS, D declares the virtual channel busy and therefore does not transmit until the timer expiration indicated in a NAV field which is located in the CTS frame,
- then D will not collide with the current exchange with B,
- B can then receive data without collision.
This support allocation mechanism does not decrease the probability of collision over RTS/CTS control frames. In fact:
– the RTS frame can collide with B with a transmission from D; in this case the channel is not globally reserved because no CTS has been sent;
– the CTS frame can collide within the coverage zone for B; in this case the channel is not globally reserved in this zone and therefore data reception from B can be disrupted by an activity within this same zone.
On the other hand, the cost of retransmission of these little 30 byte frames is much lower than the cost of a data frame that would be a maximum of 2,500 bytes.
Since radio transmissions are noisy and unreliable and the probability that a transmission is successful is inversely proportional to the size of the frame, the IEEE 802.11 protocol accepts fragmentation of long frames in order to limit disruptions.
Fragmentation is done for frames whose size is larger than a certain threshold (fragmentation threshold).
Each fragment is numbered (Fragi) and acknowledged (ACKi) through a “stop-and-wait” source protocol. The virtual channel is reserved by RTS/CTS which contains the NAV of the first fragment. Then, each fragment contains the NAV of the next fragment in the manner of RTS/CTS in order to extend channel reservation until the last fragment. ACK, RTS, CTS and Fragment are separated by SIFSs in order to guarantee continuity of exchange. This enables transmission by bursts (see Figure 21.7).
An error will only produce the retransmission of a fragment and not of the entire frame. This increases effective throughput. The size of the fragment is not set by the norm, it is different for each cell and can be adjusted by the base station.
In this mode, the coordination function is centralized on the base station (AP) to control the cell’s activity. It sends an offer to transmit (poll) to each station that needs this service. Data exchange can be either increasing or decreasing. Stations are all polled one at a time. Collisions are therefore impossible since the channel is allocated successively for each station. The standard only proposes the mechanism, but it indicates nothing for frequency, order and polling evenness between the stations.
This mode is optional. It can be used alternately with the DCF mode. It is recommended for real-time applications such as voice or video. Its centralized character makes it useless in ad hoc mode.
The AP can take control of the support because it has a PIFS (PCF IFS) timer that is smaller than the one in the DCF mode (PIFS < DIFS). Therefore, it has the most priority than all the other types of exchange. PCF mode frames are also separated by the smallest SIFS timer (SIFS < PIFS < DIFS) in order to guarantee continuity.
Even if this mode enables a certain bandwidth guarantee, it is still not implemented in current cards.
The exchanges that we have shown are done with the help of 4 different time intervals (IFS = Inter Frame Space) (see Figure 21.8):
– the short inter-frame interval (SIFS, Short ISF) enables a current exchange to continue without interruption. It precedes: a CTS after an RTS, an ACK or ACKi after data or a fragmenti+1 after an ACKi;
– the PCF (PIFS, PCF IFS) inter-frame interval enables a base station to send a beacon frame or an invitation to transmit (poll);
– the DCF (DIFS, DCF IFS) inter-frame interval enables any station to transmit a frame within the traditional contention rules controlled by the backoff algorithm;
– the extended inter-frame interval (EIFS, Extended IFS) enables a station to signal that it has received an erroneous or unknown frame without interfering with the other exchanges (that is why it has the lowest transmission priority) and therefore it has the longest timer.
This interval delay order makes it possible to define priorities and to complete more urgent exchanges that are current before the less urgent exchanges.
In infrastructure mode, the base station broadcasts a beacon frame at regular intervals (10 to 100 times a second) which enables all the stations to communicate in the BSS and which contains such system parameters as:
– the sequence of the frequencies to use and the maintenance times for these frequencies (for FHSS);
– clock synchronization;
– the reminder for new stations to subscribe to the list of stations called to transmit for a certain throughput in order to guarantee corresponding bandwidth and services that can use it in PCF mode;
IEEE 802.11 controls power management in order to ensure optimized energy usage for mobile stations that only have limited power capacity. Two modes are proposed:
– the continuous aware mode by default;
– the power save polling mode where mobile stations decide to go in sleep mode. They subscribe to this service through AP. They only become active when AP sends a transmission of its beacon frame which contains information in a TIM (Traffic Information Map) table on data that might have been received during sleep mode. If that is the case, stations request to receive the data from AP and they return to sleep mode. Once that is done, the AP will buffer the new received data until the new beacon frame. This mechanism decreases power consumption but also decreases transmission throughput.
At physical level, a frame is made up of 4 fields (see Figure 21.9):
– a preamble for synchronization and beginning of frame marking;
– a PLCP (Physical Layer Convergence Protocol) header to define the length and throughput of data;
– encapsulated MAC data;
– a CRC (Cyclic Redundancy Check);
At MAC level, IEEE 802.11 defines 3 types of frames.
This frame encapsulates IP packets. It is made up of the following fields (see Figure 21.10):
– a control frame (2 bytes) with the 11 following sub-fields (see Figure 21.11):
- current protocol version in the cell (2 bits),
- the type (data, control, management) (2 bits),
- the sub-type (e.g., RTS, CTS) (4 bits),
- to DS: the AP sends the frame toward the intercellular Distribution System (1 bit),
- from DS: the frame comes from the intercellular Distribution System (1 bit),
- a fragment will follow (more fragments) (1 bit),
- indicates that it is the retransmission of a frame (retry) (1 bit),
- sleep/active switch for power management (1 bit),
- indicates whether there are more frames for the receiver (more data) (1 bit),
- indicates whether the core of the frame is encrypted with WEP (Wireless Equivalent Privacy) (1 bit),
- indicates to the receiver to process according to the order of received frames (1 bit);
– duration in milliseconds (1 CTS + 1 Data or Control + 1 ACK + 3 SIFS) corresponding to the time the data frame will occupy and its acknowledgement in order for the other stations to manage the NAV reservation mechanism (2 bytes);
– 4 address sub-fields in the IEEE 802 format (24 bytes):
- destination (@1) (6 bytes),
- source (@2) (6 bytes),
- destination base station if transmitting to another cell (@3) (6 bytes),
- source base station if receiving from another cell (@4) (6 bytes); – Sequence number (2 bytes):
- fragmented frame number (12 bits),
- fragment number in this frame (4 bits); – data (up to 2,312 bytes);
– an FCS (Frame Check Sequence) control (4 bytes).
These frames manage the connection via association and authentification mechanisms. Their format is essentially the same as the data frame format. The difference is indicated in the frame control type field.
These frames manage access control to support via RTS, CTS and ACK frames.
They are made up of 4 fields (see Figure 21.12):
– a frame control (2 bytes);
– NAV duration (2 bytes);
– address sub-fields in the IEEE 802 format (6 or 12 bytes):
- destination one for CTS, ACK and RTS,
- source only for RTS.
– an FCS (Frame Check Sequence) control (4 bytes).
The IEEE 802.11 standard lists 9 services of which 5 are for distribution and 4 are for stations.
They manage the members of a cell and the interaction with the other cells in the case of mobility. They are controlled by the base stations.
– the association that takes place after authentification enables a mobile station to connect to a base station in infrastructure mode or to other mobile stations in ad hoc mode. This can be done at the beginning, in active mode (after sleep mode). Two modes are possible according to the power of the received signal and the power consumption necessary for the exchange:
- passive listening where AP regularly sends a beacon frame with synchronization information,
- active listening where the mobile station transmits a request frame (probe request frame) to the AP which indicates its identity and its capabilities (throughput, whether PCF is required or not, power management) and waits for a response;
– dissociation of the base station’s initiative (for maintenance reasons, for example) or of the mobile station (for start or extinction reasons, for example);
– reassociation enables the implementation of the move from one mobile station to another without communication loss10 (see section 21.3.3). In order to do this, the mobile station regularly tests the strength of received signals on every channel. It can decide to associate with another channel and this enables the creation of WLANs by recovery of cells whose channel frequencies are disjointed in order to avoid interference;
– the distribution indicates how to route frames to destination from a base station. If the destination is local, then the base station sends it directly. If not, then the base stations routes it to the distribution system;
– integration makes it possible to adapt the addressing strategy if the frames are on a different network.
These are used for intracellular activity:
– authentification happens either after having accepted the new mobile station in the cell by reassociation mechanism or after the listening mechanism for the authorization to exchange; there are two mechanisms for this function:
- by default, where all stations are accepted (open system authentification),
- if the WEP is activated (shared key authentification) then the AP sends a challenge to the mobile station for the password (or the secret key) that was assigned to it. The mobile station enters its key and then returns to the AP. If the result is correct, the mobile station is registered in the cell;
– authentification cancellation will terminate a session;
– confidentiality can be guaranteed by data encryption (WEP; see section 21.3.1);
– data delivery, which is the main objective for a communication system, is not optimal in the case of wireless networks and therefore higher layers must also manage the detection and correction of errors which are not controlled by the IEEE 802.11 level.
The first IEEE 802.11 norm provided a maximum theoretical throughput of 1 Mb/s. It quickly became clear that this value was considered a limit that would impede its commercial development. The first enhancement was the first normalized IEEE 802.11b amendment offering a maximum theoretical throughput of 11 Mb/s.
It was followed by the second normalized IEEE 802.11a amendment offering a maximum theoretical throughput of 54 Mb/s. The way was then paved for other amendments in order to improve the norm and respond to market demand and take advantage of the solutions provided by the IEEE with the help of engineers and researchers. The list of amendments can be found in Appendix B.
No need for alligator clips to connect to a wireless network. An antenna is sufficient to hear what can be received wherever it is11. It is therefore normal to protect ourselves from unwanted threats.
Wi-Fi/IEEE 802.11 exposes 3 security mechanisms:
– the first one is mandatory. It controls the access to the network. It starts at the network’s name or SSID (Service Set ID). A station that does not have it cannot access the network;
– the second is optional. It also controls access to the network from the MAC address list (ACL, Access Control List) of the cards authorized to connect. A station without the right MAC address cannot connect to the network;
– the third is optional. It authenticates, encrypts and verifies the integrity of the data. It is a secure data linking protocol (at MAC level) called WEP (Wired Equivalent Privacy) which enables a confidentiality similar to cable systems. Since by default there are, this objective seems easy to reach. It belongs to the family of symmetrical algorithms with a shared secret key of 40 or 104 bits.
It is based on the RC4 (Ron’s Code 4) algorithm made up of two parts:
– production of a key (key scheduling algorithm) by concatenation of the shared secret key and of an IV (Initialization Vector) to generate a state table;
– which in turn makes it possible to generate a pseudo random sequence through a PRNG (Pseudo Random Number Generator) derived from the RC4.
At transmission (see Figure 21.13):
– clear IV is transmitted in the frame;
– the secret key and the IV are concatenated (key scheduling algorithm);
– the result is injected in the PRNG/RC4;
– clear data is mixed by an operator or exclusive to the sequence generated by the PRNG/RC4 and then transmitted in the frame;
– an ICV (Integrity Check Value) is executed from the data and then mixed by the operator or exclusive to the sequence generated by the PRNG/RC4 and then transmitted in the frame;
– the header and the CRC of the MAC frame are not encrypted in order to let the other stations listen to the information useful for proper execution of the access protocol.
At reception (see Figure 21.14):
– the IV is extracted from the frame;
– then concatenated with the secret key (key scheduling algorithm);
– the result is injected in the PRNG/RC4;
– the encrypted data are mixed by an operator or exclusive to the sequence generated by the PRNG/RC4;
– an ICV’ integrity control is executed from the encrypted data;
– the ICV integrity control is extracted from the frame;
– the ICV and the ICV’ are compared in order to verify data integrity, i.e. to ensure that they were not modified.
The concern is that there are generally significant problems with these security measures. Indeed, the SSID circulates clearly on the network and can therefore be exploited again (spoofing), a MAC address can also be processed again and make the ACL useless and the RC4 key is breakable if we have a certain number of encrypted frames.
IEEE 802.11i recommends using the AES (Advanced Encryption Standard) to improve encryption and authentification. It is a fast and reliable algorithm but a heavy consumer of resources.
While we are waiting for this solution integrated to Wi-Fi, there are other ways to secure such a network, such as:
– regularly changing the key;
– IEEE 802.1x (port-based network access control) for authentification and key management;
– EAP (Extensible Authentification Protocol) for authentification;
– RADIUS (Remote Authentification Dial-In User Service) for authorization and authentification;
– AAA (Authentification, Authorization, Accounting) for accounting, authorization and authentification;
– VPN (Virtual Private Network) for offering a secure end-to-end tunnel via IPSec;
– a smart card for authentification and other services.
In practice, we must not hesitate to multiply the protection in order to make a system that is less vulnerable. In the case of Wi-Fi, in addition to the solutions that were just explained, we must opt for the infrastructure mode rather than the ad hoc mode which offers no security, not use DHCP (Dynamic Host Configuration Protocol) but instead attribute fixed IP addresses and set the transmission power to the minimum desired coverage zone.
In the meantime, the Wi-Fi alliance proposes a new encrypting protocol with the name WPA (Wi-Fi protected Access).
Quality of Service (QoS) is critical for real-time applications (such as voice, video, multimedia, etc.). In order to achieve this we must define priorities between data in order to best guarantee its delivery when it is required. PCF mode is a good start in offering QoS but it is not or barely implemented in current cards. And it is still pretty much elementary.
In amendment e, this is done at frame level (MAC), which is the lowest and therefore the fastest. Priority management is executed by reducing IFSs. in this way priority flows (at short IFS) will always go before the flows with less priority (at longer IFS).
For this, amendment e proposes 2 methods:
– the EDCF (Extended DCF) is an improvement from DCF which implements 8 priority levels that represent 8 traffic categories (TC) through 8 queues which have their own AIFS (Arbitration IFS), contention window (CW) persistent factor (PF) such as DIFS < AIFS < EIFS and the CW is doubled in the case of collision only if PF = 2, as in the case of the traditional backoff algorithm. If two traffic classes wish to transmit at the same time, the class with the most priority, determined by a TxOP (Transmission Opportunities) timer is selected;
– the HCF (Hybrid Co-ordination Function) combines the EDCF and the PCF in such a way that it is possible to transmit bursts of PCF even within the core of the EDCF. This is done in order to guarantee access to the support of the periodic traffics.
In the meantime, priority management can be assured by delaying acknowledgements of low priority packets at IP level. We can only hope that this amendment will not have the same outcome as PCF.
The goal is to maintain communication during handover12.
Juxtaposing cells (BSS) one next to the other by linking them through a backbone forms a coverage surface (ESS) as large as needed (see Figure 21.15).
This juxtaposition is done by recovering neighboring cells that must have different sequences. In this way, a mobile station can see multiple APs in a given area.
In the case of mobility it can choose the AP which corresponds best to it in each area. The handover describes the mechanism which makes it possible to go from one cell (BSS) to another without interrupting the current communication.
This mobility relies upon the proprietary Inter-Access Point Protocol (IAPP). Security can be assured by the RADIUS protocol. Protocols such as DHCP or Mobile IP are recommended to ensure distribution of correct IP addresses. While we are waiting for f (standardized mechanism), the association/reassociation/ dissociation mechanisms are used via cellular IP/Mobile IP.
The handover recommends the development of ambient networks which enable a connection to the Internet from anywhere, at any time and at reduced cost. They are at the junction between wireless networks and mobility.
IEEE 802.11g, which has been finalized since 2003 and considered as an extension of a and b, uses the ISM band of 2.4 GHz as well as CCK coding and OFDM transmission techniques in order to reach a throughput of 54 Mb/s.
g is compatible with b in the sense that it operates in the same frequencies and when all the correspondents are in g, then the exchange is done in g. However, when a station connects in b then all exchanges are done in b.
IEEE 802.11b proposes a maximum theoretical throughput of 11 Mb/s. By taking out the overhead caused by headers, signaling, IFS timers and backoff and by retransmissions and possibly by encryptions, it is practically decreased by half to 6 Mb/s. It is the same with amendments a and g which propose a maximum theoretical throughput of 54 Mb/s for a practical throughput which almost never exceed 22 Mb/s.
The future standard 802.11n will be officialized at two times. A first version, envisaged in 2007, will ensure the compatibility of the materials of different marks. It will be necessary to wait until 2008 for the final standard. It is greatly inspired by the HiperLAN13 norm. It must offer throughputs of 108 and even 320 Mb/s, with the characteristic that practical throughputs should be close to these theoretical throughputs with a desirable efficient range of 100 feet. It integrates new compression algorithms, better error and interference management as well as a new antenna technology. It must enable the control of power, the control of frequencies currently communicating, use both 2.4 and 5 GHz bands and integrate i, e and f amendments. This new standard would constitute a technological break that would require a change of all the cards. Considering these requirements, ensuring compatibility between cards of different manufacturers will remain a challenge.
Wi-Fi/IEEE 802.11 is really a revolution in information technology in general and in Internet access in particular. It rapidly deploys WLANs in the form of HotSpots14. It brings to the Internet what the laptop computer has brought to information technology: mobility.
The attraction for Wi-Fi/IEEE 802.11 is explained by its ease of deployment, its integration with existing infrastructure, the low cost of material and the wide utilization spectrum.
The liberalization of Wi-Fi usage outside15 brings new operators, the WISPs (Wireless Internet Service Providers).
Apart from HotSpots there are other uses for Wi-Fi, such as interoffice connection for linking together two sites with a distance of 300 feet with two directional antennae, management of production centers, warehouses, workshops with hardened material, real-time follow up of patient files in hospitals, applications linked to mobility for companies where the personnel need their computers and can go from offline to online and work wherever they need to.
Uses linked to transport are also expanding rapidly. The transport mode obviously being the car, it can now communicate. Concept cars already exist with Wi-Fi and TabletPCs. The vehicle must be linked outside via GPRS/UMTS and even Wi-Fi. Services offered can be: downloading files (e-fuel) in gas stations and parking areas, help with navigation, access to the Internet, vehicle follow-up by the dealer (communicating black box), vehicle follow-up in the case of theft, user mobility services offered in urban or rural areas.
The IEEE 802.11 produces 6 norms (see Table 21.1): 3 for low throughput (1 InfraRed, 2 FHSS and DSSS spread spectrum radio waves) and 3 for high throughput (with a, b and g amendments). This may seem like a lot and contradictory with the objective of a norm that is supposed to define a common technical base to continue the economic expansion. The latter enables manufacturers to make products according to requirements, but also to develop new services and therefore generate new needs. In fact, this objective is the source for the diversity of the solutions. Furthermore, the economic challenges generate significant pressures to create a new standard that would help define a common base for interoperability. An important dynamic exists around WLAN and especially Wi-Fi/IEEE 802.11 definitions. This process seems to frantically auto-fill.
Reservation mechanisms by virtual channel (VCS) and PCF are rarely implemented. The WEP is considered somewhat weak. There is a good probability that theoretical throughputs will be compared to processor frequencies in the next few years. Progress is therefore necessary. It will mainly be:
– physical aspects through other types of coding and modulation:
- to improve throughputs in amendment IEEE 802.11n,
- to improve range, coverage;
– software aspects with:
- QoS in amendment IEEE 802.11e,
- a better handover control in amendment IEEE 802.11f,
- better security in amendment IEEE 802.11i.
Wi-Fi/IEEE 802.11 is currently the main technology used with WLANs and the ambient Internet. Products exist, but do not technically respond to all requirements. It may very well become a master player of future 4G systems. There is still significant development potential with it. At the very least, it will have a place as a complement to other products and techniques. It could even become a serious competitor due to its rapid growth. In order to achieve this, multiple amendments are being finalized. Can we presume that these amendments might be assembled in one standard that will put together all the solutions to the known problems? Will amendment n finally be the standard that we have been waiting for?
Wi-Fi/IEEE 802.11 plays its part in this trio: miniaturization of electronic components, energy autonomy and mobility. The future is promising.
Wi-Fi/IEEE 802.11 and wireless networks in general16 constitute an alternative and a complement to cable networks. There is still a lot of work to be done to reach maturity. Reinforcing security, making installation and management easier, facilitating coexistence, developing interoperability among them and mobile telephony are among the improvements yet to happen17. These rapidly deploying networks are expected to grow quickly. There is no doubt that wireless networks and Wi-Fi/IEEE 802.11 in particular constitute the future of networks in general.
Normalization organism:
– IEEE: http://www.ieee.org;
– IEEE for the 802.11norm: http://IEEE 802.org/11/;
Standardization organism:
– WECA: http://www.weca.net.
The first basic IEEE 802.11 norm offers 3 types of products: 1 in IR and 2 in radio in the ISM band at 2.4 GHz with DSSS and FHSS modulations for a maximum throughput of 2 Mb/s (finalized in 1997, corrected in 1999).
The list of known amendments:
– a: 54 Mb/s in the 5 GHz band over 8 modulation channels OFDM for ranges of approximately 300 feet outside and 30 inside with a maximum throughput at 15 feet; incompatible with the basic IEEE 802.11 norm and amendment b (finalized in 2001);
– b: 11 Mb/s in the 2.4 GHz band over a maximum of 14 channels with HR-DSSS modulation for ranges of approximately 900 feet outside and 90 feet inside with a maximum throughput at 30 feet; compatible with basic IEEE 802.11 norm (finalized in 1999);
– c: enables the definition of a bridge with 802.11 frame at linking level (finalized in 1998);
– d: equivalent to b but adapted to the regulations of countries in terms of frequencies and transmission power (finalized in 2001);
– e: for QoS at MAC level (applies to a, b and g); project approved in 2000;
– f: for handover management between APs of one DS via the IAPP protocol in order to enable interoperability of APs and DS of different manufacturers (project approved in 2000);
– g: 54 Mb/s in the 2.4 GHz band with CCK/OFDM modulation; compatible with basic IEEE 802.11 norm and amendment b (finalized in 2003);
– h: equivalent to a but adapted to regulations of European countries in terms of frequencies and transmission power (finalized in 2003);
– i: to improve security and authentification at MAC level (applies to a, b and g), replacing WEP and based on IEEE 802.1x (project approved in 2000);
– j: equivalent to h but adapted to Japanese regulations (project approved in 2002);
– k: must supply information to optimize network resources by adding other information such as position determination technology in order to offer new services (project approved in 2002);
– l: not used for risk of confusing it with i;
– m: workgroup that must correct interpretation errors of the norm (project approved in 2003);
– n: increase of throughputs to 108, maybe even 320 Mb/s, enables power management, management of current communication frequencies, uses both 2.4 and 5GHz bands, integrates amendments i, e and f (project approved in September 2003, expected for 2005/2006);
– o: not used for risk of confusing it with 0.
[MAL 02] MALES D., PUJOLLE G., Wi-Fi par la pratique, Eyrolles, April 2004.
[MUL 02] MÜHLETHALER P., 802.11 et les réseaux sans fil, Eyrolles, 2002.
[STD 97] IEEE Std 802.11-1997. Part 11 “Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications”, IEEE, 1997.
[STA 99] IEEE Std 802.11a-1999. Part 11 “Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications”, IEEE, 1999.
[STB 99] IEEE Std 802.11b-1999. Part 11 “Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications”, IEEE, 1999.
[STX 01] IEEE Std 802.1x “Standard for Local and Metropolitan Area Networks: Port Based Access Control”, IEEE, 2001.
[AES 01] FIPS PUB 197AES “Advanced Encryption Standard (AES), FIPS, 2001.
1 Chapter written by Denis BEAUTIER.
1 http://museebranly.isep.fr, website of Branly from the Institut Supérieur d’Electronique de Paris museum (ISEP, http://www.isep.fr), engineering school founded in 1955 in order to transmit the knowledge acquired in Branly’s research laboratory.
2 It is not possible in the ad hoc mode to route information from one mobile station to another through intermediate mobile stations as is the case with ad hoc networks. In order to have this functionality, you must install an appropriate protocol such as OLSR (optimized link state routing protocol) proactive protocol (i.e. by updating possible routes before activation) or AODV (ad hoc on demand distance vector) reactive protocol (i.e. by flooding during route activation).
3 The attenuation, reflection, diffraction, diffusion, fading (produced by the echo’s multiple paths), the Doppler effect and the electromagnetic interference (such as microwave ovens, garage door remote controls, etc.) can provide degradation of signal and affect wireless transmissions.
4  of the human body is made up of water. Water resonance frequency is at around 2.5 GHz and this frequency is used in Wi-Fi. We can naturally wonder if Wi-Fi use might have consequences on the human body.
of the human body is made up of water. Water resonance frequency is at around 2.5 GHz and this frequency is used in Wi-Fi. We can naturally wonder if Wi-Fi use might have consequences on the human body.
5 We are referring here to the 2.4000-2.4835 GHz band also called ISM (Industrial, Scientific, Medical) band. The transmission power is controlled in France by ART (Autorité de Régulation des Télécommunications), in Europe by ETSI (European Telecommunications Standard Institute) and in the USA by the FCC (Federal Communication Commission).
6 35 or 79 channels for France according to the band, 79 for Europe and the USA.
7 13 channels for France and Europe, 11 for the USA.
8 It is the U-NII (unlicensed national information infrastructure) band.
9 In order to ensure compatibility with the European HiperLAN/2 system (see footnote 13).
10 It could also be that a fixed station notices that another access point is better in terms of signal or load quality than the one on which it is connected. Wi-Fi integrates a load balancing mechanism to avoid this kind of situation.
11 WarDriving is a technique which consists of recording what is happening in a given area with the objective of penetration or even mapping via a GPS (Global Positioning System).
12 This concerns horizontal handover between cells of a same network. It should not be confused with vertical handover which operates between cells of different networks such as between Wi-Fi, GPRS (General Packet Radio Service), UMTS (Universal Mobile Telecommunications System) or CDMA 2000 (Code Division Multiple Access 2000) without interruption of communication. Roaming enables the access of its usual network through another one via a disconnection of its home network and a reconnection to the new one.
13 HiperLAN is a WLAN technology standardized by the ETSI (European Telecommunications Standard Institute) which does not benefit from international support although it offers excellent security, QoS, coverage and throughput services, among others.
14 Public access points to the Internet via a wireless connection in high traffic areas such as train stations, airports, universities, shopping centers, hotels, specific events, user groups, etc.
15 CraieFiti (war-chalking) indicates the presence of access points and their characteristics with easily recognizable symbols.
16 The explosion of wireless networks does not only concern Wi-Fi but also HiperLAN (WLAN), BlueTooth (WPAN, IEEE 802.15.1), ZigBee Alliance (micronetworks – mesh network), UWB (UltraWide Band), WiMAX (IEEE 802.16), etc.
17 We can already see the merging of PDAs and cell phones.