SSH is a protocol, not a product. It is a specification of how to conduct secure communication over a network.[3]
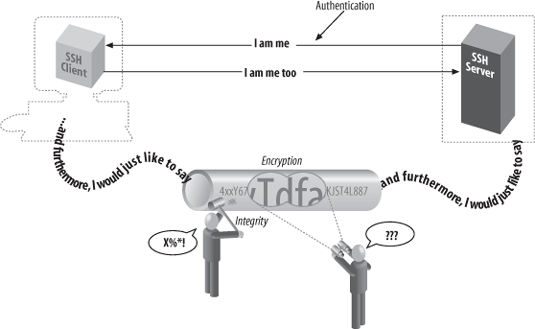
The SSH protocol covers authentication, encryption, and the integrity of data transmitted over a network, as shown in Figure 1-2. Let's define these terms:
- Authentication
Reliably determines someone's identity. If you try to log into an account on a remote computer, SSH asks for digital proof of your identity. If you pass the test, you may log in; otherwise, SSH rejects the connection.
- Encryption
Scrambles data so that it is unintelligible except to the intended recipients. This protects your data as it passes over the network.
- Integrity
Guarantees the data traveling over the network arrives unaltered. If a third party captures and modifies your data in transit, SSH detects this fact.
In short, SSH makes network connections between computers, with strong guarantees that the parties on both ends of the connection are genuine. It also ensures that any data passing over these connections arrives unmodified and unread by eavesdroppers.
The first SSH product, created by Tatu Ylönen for Unix, was simply called "SSH." This caused confusion because SSH was also the name of the protocol. In this book, we use more precise terminology to refer to protocols, products, and programs, summarized in the sidebar "Terminology: SSH Protocols and Products." In short:
Protocols are denoted with dashes: SSH-1, SSH-2.
Products are denoted in mixed case, without dashes: OpenSSH, Tectia, PuTTY, etc.
Client programs are in lowercase: ssh, scp, putty, etc.
[3] Although we say "the SSH protocol," there are actually two incompatible versions of the protocols in common use: SSH-1 (a.k.a. SSH-1.5) and SSH-2. We distinguish these protocols later.