Hackers are people and, like most people, hackers paradoxically embrace their individuality while immersing themselves in their collective identity as rebels, free thinkers, mischief makers, and technology wizards. Despite appearances to the contrary, people do not become hackers because of how they look, what they wear, or how they speak. People become hackers by virtue of how they think and what they do.
In the world of hacking, there are "good" hackers (called white hat hackers) and there are "bad" hackers (called black hat hackers). In between are the so-called gray hat hackers, who cross the border between good and bad depending on what's convenient for them at the time (like most people in the world).
Even the definition of hacker remains controversial. Some people lump both good and bad hackers together, but others define hacker as someone who's simply curious, and use the term cracker for someone who's deliberately malicious.
Whatever you call them, hackers are people, and like any group of people (Americans, police officers, teachers, accountants, Christians), some will be good and some will be bad. But unlike most other groups, hackers often rely exclusively on technology, in the form of computers and the Internet, to communicate with each other.
Finding a hacker on the Internet is fairly easy if you know where to look, just as you can find a drug dealer or a policeman if you know where to look in a city (depending on the city, the policeman might be the drug dealer).
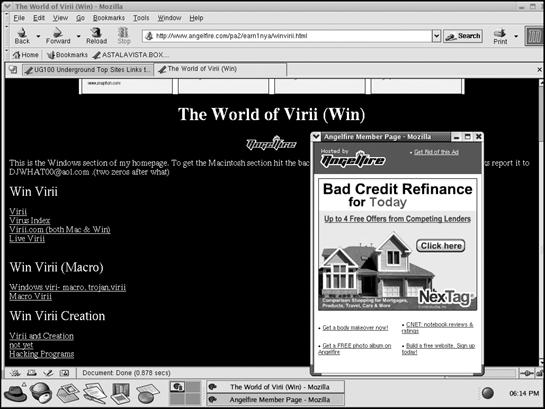
There are two kinds of hacker websites: those run by hackers and those run by reformed hackers who have decided that it's more profitable to become security professionals. Initially, many hackers created websites using free web hosting services such as Tripod (www.tripod.lycos.com), Geocities (http://geocities.yahoo.com), and AngelFire (http://angelfire.lycos.com). Such websites are often short-lived, as hackers grow tired of updating them. Besides, few people are interested in visiting personal websites that bombard visitors with advertisements, as shown in Figure 7-1.
On rare occasions, an ambitious hacker may actually spend the time and money to create a website with a descriptive domain address. Like their free web hosting counterparts, these hacker websites rarely last long because anything considered too controversial (such as live computer viruses and software patches designed to circumvent Microsoft Windows' product activation feature) can quickly get the website operator in trouble with the authorities, who will shut it down. It's said that when hackers started distributing a program that disabled Windows XP from running its product activation feature, for example, Microsoft quickly shut down any websites that offered it.
Although individual hackers rarely set up websites anymore, groups of hackers often do so to provide a platform for their views and a place where they can release their hacker tools or make a profit selling hacker merchandise such as T-shirts or CDs. Some of the more stable hacker group websites are listed in this section.
This site provides both current and archived news about computer security, including a list of allegedly fraudulent people and organizations in the computer security business (www.attrition.org).
AusPhreak offers a meeting site for Australian and international hackers to gather and share ideas (www.ausphreak.com).
One of the oldest hacker groups and one of the largest in Europe, Chaos Computer Club is perhaps best known for its loose affiliation with a West German hacker, Karl Koch, who was accused of breaking into American government computer networks and selling military secrets to the Soviet KGB intelligence agency (www.ccc.de).
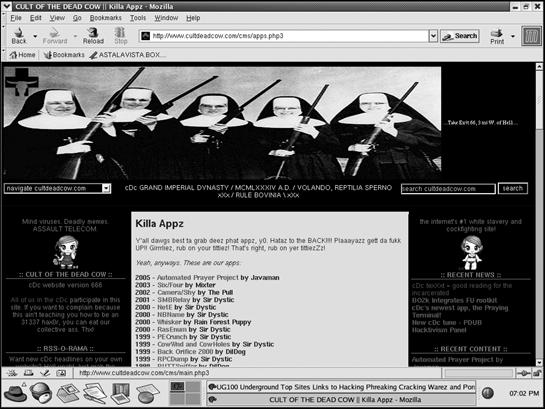
The Cult of the Dead Cow (see Figure 7-2) is known for releasing a variety of hacker tools with great fanfare. Some of their more notable hacker tools include the remote-access Trojan horse dubbed Back Orifice, a steganography tool for hiding information in images called Camera/Shy, and an anonymous peer-to-peer tunneling protocol called Six/Four (www.cultdeadcow.com).
New Order offers hacker software, security exploits, and lists of interesting projects such as GhostProxy, which is designed to let you browse the Internet anonymously; MD5 Reverse Lookup Database, for helping you crack MD5 encrypted files (also known as hashes) used to protect passwords; and Slut-Box, a server specifically set up to allow people to practice breaking into a computer without getting arrested (http://neworder.box.sk).
Provides plenty of hacker tools and research papers geared towards finding exploits in popular programs (www.nmrc.org).
Website of security professionals who donate their time to creating useful tools for hacking or for catching hackers (www.shmoo.com).
Hacker tools and news are posted on Underground News along with the latest rumors circulating around the computer industry (www.undergroundnews.com).
The main reason most hackers no longer set up their own websites is because there's no money in it. Between the cost of running a website, the time needed to design and maintain it, and the possible legal liabilities of offering programs that encourage piracy, most hackers choose the more lucrative route of calling themselves "security professionals" instead. Rather than risk going to jail for hacking, such reformed hackers/security professionals sell their hacking skills to the highest bidder.
One prominent hacker group, dubbed L0pht Heavy Industries, transformed itself from a hacker group to a computer security firm called @Stake, which in turn was bought out by Symantec. Given the choice between serving prison time or getting paid to hack legally, it's easy to see why hackers would opt to become security professionals.
This source for hacker news, virus source code, and Trojan horse programs also offers various forums where security professionals can chat and exchange information (www.antionline.com).
Gathers information from firewalls to track the different types of hacker attacks occurring around the world (www.dshield.org).
Hideaway.net provides news, information, and links to different types of security software and anonymous web browsing sites (www.hideaway.net).
Home of the Nmap security scanner, this site also lists the top security tools to protect your computer and network from attack (www.insecure.org).
Provides both historical and current information and tools about hackers and the latest exploits (http://packetstormsecurity.org).
A massive directory of links to various computer security resources, news, companies, and security threats is available at Security News Portal (www.securitynewsportal.com).
This site organizes links to various hacker and computer security resources in categories for easy browsing (www.secureroot.com), as shown in Figure 7-3.
Home of the BugTraq mailing list of the latest exploits in different software, SecurityFocus also provides a library of security programs along with a security-related job bank (www.securityfocus.com).
Another huge directory of different computer security companies, hacker groups, and security software tools is available at Startplaza.nu (www.startplaza.nu).
This site provides white papers examining computer security issues with a special emphasis on VoIP (www.sys-security.com).
British security website that provides real-time security alerts and updates for government and military organizations (and anyone else who visits their website, too)—www.securitywizardry.com.
This site packages coverage of computer security (focusing exclusively on Windows) as well as an online Trojan horse scanner, an email vulnerability scanner, and a network security scanner (www.windowsecurity.com).
Wiretapped specializes in cryptography and network monitoring with plenty of links to packet capturing, network mapping, and network intrusion detection software (www.wiretapped.net).
To find more hacker and security-related websites, you could use an ordinary search engine, such as Google, but you'll wind up sifting through lots of irrelevant links. For a more targeted alternative, use the specialized hacker search engine, AstalaVista (www.astalavista.com). AstalaVista can help you track down everything from the latest source code for the newest worm or virus to the current version of a port scanner designed to probe another computer's defenses.
If AstalaVista can't find a hacker website for you, it also provides a list of additional hacker search engines you can use instead, as shown in Figure 7-4, or you can try http://astalavista.box.sk.