Advertisers always want to measure the effectiveness of their marketing campaigns. Since the Internet spans the world, it's very difficult to track how many people look at a particular ad and who they are. To meet these two needs, advertisers created a special tracking device called a web bug.
When you visit a website, your browser asks it to send all the text and graphic images contained on that page. Thus, a webserver needs to know the IP address of the visitor's computer in order to send the reply to his or her browser.
When a webserver sends a web page to your browser, it is encoded as HyperText Markup Language (HTML) instructions that tell your browser how to display and position text and graphics, the name of the different graphic files in the page, and other data about the page, such as the name of the server that sent it to your computer. In the following example of an HTML graphics statement, the graphic file is called dotclear.gif, its width and height are both one pixel, and the server that sent it is located at http://ad.doubleclick.net (it's this server that uses the web bug to retrieve information about your computer).
<IMG SRC=http://ad.doubleclick.net/dotclear.gif width=1" height="1">
The example above is actually a web bug, so tiny in size that it's essentially invisible. When the server sends the web bug to a browser, the DoubleClick.net server can immediately identify the following:
Web bugs typically appear on web pages, but they can also appear inside banner ads, pop-up/pop-under ads, or HTML files send through email or posted in newsgroups. In their simplest usage, web bugs help advertisers determine how many people have visited a particular website and viewed a particular web page. On a more insidious level, web bugs can be used with browser cookies to track which websites a particular person visits and tailor advertisements specific to that individual's interests.
Cookies are small text files that contain unique information about you and your last visit to a specific website. For example, a cookie from Amazon.com can store a user ID to match your computer to its database that lists the last 20 items you browsed, along with any recent purchases.
Normally, cookies can only be used by the website that created and placed them on your computer. So a cookie placed on your computer by Amazon.com can't be read or used by any other websites, such as Barnes & Noble or Borders bookstores.
Unfortunately, circumventing this restriction is what webservers like DoubleClick do when they place web bugs (and cookies) on your computer. Only DoubleClick's servers can read its own cookies, but since DoubleClick's web bugs appear on so many websites, they can effectively track what you do across multiple websites. Visit sites like Amazon.com, Best Buy, and CompUSA and DoubleClick's web bug/cookie combination can track what you've done on each site and thus create a more detailed profile of your browsing habits than any single website could do on its own. Armed with this information, DoubleClick can create unique customer profiles linked to specific IP addresses, essentially spying on your buying habits without your approval (or knowledge).
To learn more about what type of information web bugs can retrieve off your computer, visit the Analyze Your Internet Privacy site (http://network-tools.com/analyze) and Cookie Central (www.cookiecentral.com).
The next time you receive spam, there's a good chance that it will contain HTML code (where a web bug can hide). The reason is simple. As soon as you view spam (such as in the Preview pane of an email program like Thunderbird or Outlook Express), your computer retrieves the text and graphic images defined by that HTML code. As soon as your computer requests the web bug, the web bug's server can identify not only your IP address and operating system, but also when you viewed the spam. This information can be particularly important because it tells the spammer that someone actually viewed the spam so the email address is valid (and can be sold to other spammers too).
Many email programs let you block graphics from being viewed, but you may want to test your email program by taking the web bug test at www.nthelp.com/OEtest/oe.htm. This test will send you an email and after you open it in your email program, you can return to the website to see if the server managed to determine if you opened the "spam" or not.
Even if you're using a supposedly "secure" email program like Thunderbird, you may find yourself being victimized by web bug spam if you rely on the program's default settings. Thunderbird will only strip away HTML graphics or web bugs if it properly identifies the message as spam. Since Thunderbird won't identify the web bug test message from the nthelp.com site as spam, it will let the test message's web bug slip through, which also means that any spam that can slip past Thunderbird's spam filters will also be able to verify your email address, too. (In my limited testing with different email programs, both Outlook Express and Thunderbird failed to block the nthelp.com's test message, but Microsoft Entourage on Mac OS X did block the test message web bug.)
If a recipient doesn't view the web bug in his email, it could mean that the email address isn't valid or that this particular person didn't bother to read it. In either case, the advertiser will likely remove that person's email address from its distribution list and avoid sending advertisements that will be ignored.
Some companies accused of planting web bugs in email marketing messages include Experian (www.experian.com), Digital Impact (www.digitalimpact.com), and Responsys (www.responsys.com). By browsing their websites, you can get a better idea how email marketing firms work and how spam (better known by businesses by its euphemism of "email marketing") has now become a profitable and legitimate business model that includes clients such as Victoria's Secret, Microsoft, Marriott, and New York Life. Like it or not, spam, in one form or another, has become just another marketing strategy.
Newsgroups are another area where web bugs have started to appear. If you leave a message on a newsgroup as plain text, anybody can read the message anonymously. But if your newsgroup message contains HTML code, viewing that HTML newsgroup message causes the viewer's computer to request the HTML text and graphics from a server; this server must then identify the computer's IP address to send the requested HTML text and graphics.
By itself, HTML code can be harmless—except it allows a server to identify the IP address of the person reading the message and the time and date they read it. The extremely paranoid believe that HTML code (and web bugs) can identify people who subscribe to politically incorrect newsgroups, while others believe that governments might use web bugs to track down anyone trading child pornography or illegal MP3 files. By reading HTML code in newsgroup messages, you are no longer anonymous in a newsgroup, which is one major advantage of newsgroups in the first place.
Since web bugs often work with cookies to track your browsing habits, your first line of defense is to make sure your browser refuses all cookies. Since this won't always be practical, especially when you visit online shopping sites which need the user to have cookies enabled, you should download the free Bugnosis tool (www.bugnosis.org).
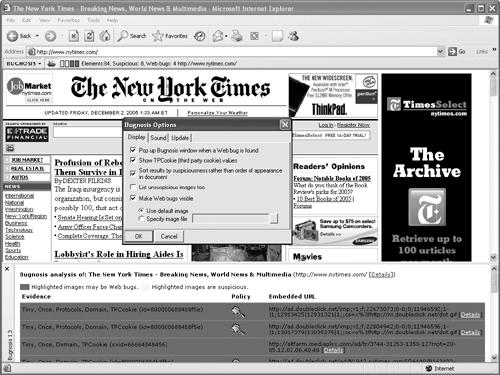
As you browse different websites, Bugnosis scans each page, gives an audible warning, and highlights suspicious web bugs. By using Bugnosis with Internet Explorer, you can see how prevalent web bugs are, especially if Bugnosis finds suspicious GIF images on favorite websites such as the New York Times (www.nytimes.com), the Detroit News (www.detnews.com), or the Direct Marketing News site (www.dmnews.com) as shown in Figure 19-8. Despite Bugnosis's help, there's still no fool-proof way to determine if you're browsing a web page with a web bug hidden on it.
One of the largest email and Internet marketing companies is DoubleClick (www.doubleclick.com), which offers Internet users a way to store a special cookie on their browser that prevents your computer from receiving any advertisements from DoubleClick.
Just visit the DoubleClick site, click the link for "Privacy at this Website," and scroll down to find the directions to opt out from DoubleClick's advertising. To opt out of other Internet marketing companies, visit the Network Advertising Initiative (NAI) site (www.networkadvertising.org/optout_nonppii.asp).
Even if you decide to opt out from DoubleClick's ads, you may still find yourself bombarded by pop-up and pop-under advertisements from other marketers. So to learn how to stop pop-up and pop-under ads from wrecking your Internet experience, visit the Web Ad Blocking site (www.ecst.csuchico.edu/~atman/spam/adblock.shtml).
If you only visit a handful of sites on a regular basis, you can configure your browser to let you choose to accept or reject all cookies from every site you visit. If you visit different sites on a regular basis, this can be a nuisance, but if you only visit a few sites, this might be one acceptable way to block cookies and keep others from spying on your browsing habits.