![]()
Industrial Automation and Control System Fundamental Concepts
The material in this chapter provides basic coverage of industrial automation and control system components and terminology, including supervisory control and data acquisition (SCADA) systems and distributed control systems (DCSs). However, because the focus of this book is the security of these systems, this chapter is not designed to be a comprehensive tutorial on industrial automation and control systems. The material assumes that the reader is familiar with these systems and communications terminology.
Note that the term DCS is also used to refer to digital control systems, but, unless otherwise stated, in this book DCS will denote a distributed control system.
Industrial Automation and Control Systems
Over the years, as industrial automation and control systems have evolved into distributed control systems and SCADA systems, the associated terminology has meant different things to different people. Control engineers, software engineers, plant personnel, and management have attached different meanings to commonly used terms such as distributed control systems, industrial control systems (ICSs), supervisory control systems, and SCADA systems.
This situation has been further complicated by the migration from relay logic, to programmable logic controllers (PLCs), to microcomputers, to the use of local area networks, Windows platforms, standard buses, and so on.
To establish a solid foundation for the material in this book, the definitions from ANSI/ISA-99.00.01-20071 and NIST Special Publication 800-822 will be used.
ANSI/ISA-99.00.01 defines industrial control systems, distributed control systems, PLCs, and SCADA systems as belonging to the class of industrial automation and control systems (IACSs). Specifically, ANSI/ISA-99.00.01 states that an industrial automation and control system is:
A collection of personnel, hardware, and software that can affect or influence the safe, secure, and reliable operation of an industrial process. These systems include, but are not limited to:
a. industrial control systems, including distributed control systems (DCSs), programmable logic controllers (PLCs), remote terminal units (RTUs), intelligent electronic devices, supervisory control and data acquisition (SCADA), networked electronic sensing and control, and monitoring and diagnostic systems. (In this context, process control systems include basic process control system and safety instrumented system [SIS] functions, whether they are physically separate or integrated.)
b. associated information systems, such as advanced or multivariable control, online optimizers, dedicated equipment monitors, graphical interfaces, process historians, manufacturing execution systems, and plant information management systems.
c. associated internal, human, network, or machine interfaces used to provide control, safety, and manufacturing operations functionality to continuous, batch, discrete, and other processes.
NIST SP 800-82 defines an industrial automation and control system as “a general term that encompasses several types of control systems, including supervisory control and data acquisition (SCADA) systems, distributed control systems (DCSs), and other control system configurations, such as skid-mounted programmable logic controllers (PLCs) often found in the industrial sectors and critical infrastructures.”
In this text, the ANSI/ISA-99.00.01 terminology and definitions will take precedence over others where there are differences.
SCADA Systems
ANSI/ISA-99.00.01 defines a SCADA system as “a type of loosely coupled distributed monitoring and control system commonly associated with electric power transmission and distribution systems, oil and gas pipelines, and water and sewage systems.” NIST SP 800-82 describes SCADA systems as:
Highly distributed systems used to control geographically dispersed assets, often scattered over thousands of square kilometers, where centralized data acquisition and control are critical to system operation. They are used in distribution systems, such as water distribution and wastewater collection systems, oil and natural gas pipelines, electrical power grids, and railway transportation systems. A SCADA control center performs centralized monitoring and control for field sites over long-distance communications networks, including monitoring alarms and processing status data.
ANSI C37.13 defines SCADA as a system operating with coded signals over communication channels to control remote terminal unit (RTU) equipment. The supervisory system may be combined with a data acquisition system by using coded signals over communication channels to acquire information about the status of RTU equipment for display or for recording functions.
A SCADA system comprises both hardware and software, and the classical SCADA system model includes the following components:
• Human-machine interface (HMI) – A program that provides the operator with an easy-to-read graphical and textual display of the SCADA system elements. The HMI displays warnings and alerts and supports the operator in analyzing system performance, spotting trends, and changing controls. Some commonly used HMI software packages are Wonderware, RSView, and iFIX. An HMI is typically resident in the master control center as well as on the plant floor.
• Master terminal unit (MTU) or SCADA server at a master control center – A SCADA element at the control center that provides two-way data communication and control of field devices, such as RTUs, PLCs, PACs, and IEDS. Two-way communications between the MTU and field devices are usually low bandwidth and can be implemented through a variety of technologies, including telephone, VHF/UHF radio, spread-spectrum radio, satellite, and microwave.
• Remote terminal unit (RTU) – In a typical application, the RTU serves as a data concentrator and is an interface between the MTU and field devices, such as PLCs, PACs, or IEDs. The RTU gathers information from the field devices and stores it until interrogated by the MTU. Conversely, the RTU receives commands for the field devices and passes these on to be executed. There are some PLCs or PACs that incorporate the functions of the RTU by communicating with the MTU and providing remote data acquisition and control of field devices, such as actuators and pumps.
• Programmable logic controller (PLC) – A PLC is defined as “a solid-state control system that has a user-programmable memory for storing instructions for the purpose of implementing specific functions, such as I/O control, logic, timing, counting, three-mode (PID) control, communication, arithmetic, and data and file processing.”3 A PLC uses a standard instruction set, such as IEC 61131-3, to implement control logic functions. IEC 61131-3 is a vendor-independent international standard for PLC programming languages for industrial automation. It includes standards for the following PLC programming languages:
– Function block diagram (FBD)
– Instruction list (IL)
– Ladder diagram (LD)
– Sequential function charts (SFC)
– Structured text (ST)
• Programmable automation controller (PAC) – A PAC is similar to a PLC, but has additional capabilities, such as more robust communications, higher-speed processors, integration with organizational databases, and a common development environment for integration of software and hardware components.
• Intelligent electronic device (IED) – IED is a general term for a device that can communicate directly with the MTU or through the RTU and provide direct connections for controlling and polling field equipment, such as actuators.
Classical SCADA systems provide a dependable means of collecting information from multiple RTUs. However, in many current applications, SCADA systems are used in production environments and perform calculations and data analysis in real time on a plant floor, with HMI capabilities. Thus, in many instances SCADA and HMI reside on the same system to perform operations at the equipment level in a real-time data-driven production environment. The discussions in this book are meant to encompass both classical and current SCADA environments.
The SCADA control center serves as the central location for monitoring and analyzing data acquired from the field devices and for sending control commands to these devices. Because of its criticality, in many instances there is a duplicate control center at a backup site connected to the main site by a wide area network (WAN). Additional important capabilities that reside in the control center are archiving historical data, providing operations information to business managers and accounting, and restoring lost data. This type of capability is usually provided by a data historian, a real-time relational database, and a yield accounting system.
The data historian acquires and stores data and provides for prompt recovery of that data, if required. It differs from a real-time database in that the historian only archives information and provides no outputs to other system devices. It offers additional capabilities, such as compressing data to store large amounts of data more efficiently and organizing the data into save-sets, which are histories of the system for specific time periods.
A real-time relational database supports interactive storage and retrieval of detailed contextual information when production processes are involved and can interface with business applications, other databases, forms, and XML files.
A yield accounting system interacts with the real-time relational database, processes plant production data, and generates production accounting information. Typical information provided by a yield accounting system includes:
• Inventory discrepancies
• Material balances in different areas of the plant and for the total plant
• Plant material movement
• Total amount of product made by a particular unit
• Total volume of a finished product shipped to a customer over a specified time interval
For planning and scheduling purposes, condensed versions of production data are transmitted from the yield accounting system to the enterprise resource planning (ERP) system for processing.
SCADA systems can be configured in a wide variety of architectures with various components, depending on the application and other plant and corporate requirements. Figure 1-1 is an example of a SCADA system client-server model that incorporates fundamental SCADA elements. The figure is presented to provide a conceptual view of a SCADA system and is not intended to represent all the various SCADA system architectures that are employed in the field.
Distributed Control Systems
A DCS includes a supervisory controller running on a control server and a number of distributed controllers. The supervisory controller transmits data set points to the remote controllers and acquires data from them. The distributed controllers control process elements by communicating with them over a field-bus-type network based on the information received from the supervisor.
ANSI/ISA-99.00.01-20075 classifies a distributed control system as:
A type of control system in which the system elements are dispersed but operated in a coupled manner.
NOTE: Distributed control systems may have shorter coupling time constants than those typically found in SCADA systems.
NOTE: Distributed control systems are commonly associated with continuous processes, such as electric power generation, oil and gas refining, and chemical, pharmaceutical, and paper manufacture, as well as discrete processes such as automobile and other goods manufacture, packaging, and warehousing.
NIST 800-826 defines a distributed control system as “control achieved by intelligence that is distributed about the process to be controlled, rather than by a centrally located single unit.”
In a distributed control system, subsystems have their own controller elements to manage local processes and to communicate with an operator console for overall supervisory functions. The individual controllers are integrated and communicate through local area networks. Figure 1-2 illustrates a typical distributed control system. In the figure, the engineering workstation supports distributed system security functions, serves as a development facility, and is used to set alerts and alarm conditions. The operator workstation provides the operator interface and is used by the operator to monitor the distributed control system, sense alerts and critical situations, and conduct system diagnostics.
Safety Instrumented Systems
Safety instrumented systems (SISs) have been widely used in the process industry to maintain a process in a safe condition during a hazardous situation, for example, if critical set points are exceeded or safe operating conditions are breached. SISs are sometimes referred to as safety shutdown (SSD) systems or emergency shutdown (ESD) systems.
ANSI/ISA-84.00.01-2004, Part 1(IEC 61511-1 Mod)7 defines an SIS as an “instrumented system used to implement one or more safety instrumented functions (SIFs). An SIS is composed of any combination of sensor(s), logic solver(s), and final element(s).” The standard also defines an SIF as a “safety function with a specified safety integrity level which is necessary to achieve functional safety and which can be either a safety instrumented protection function or a safety instrumented control function.” Figure 1-3 illustrates the relationship between safety instrumented functions and other process functions.
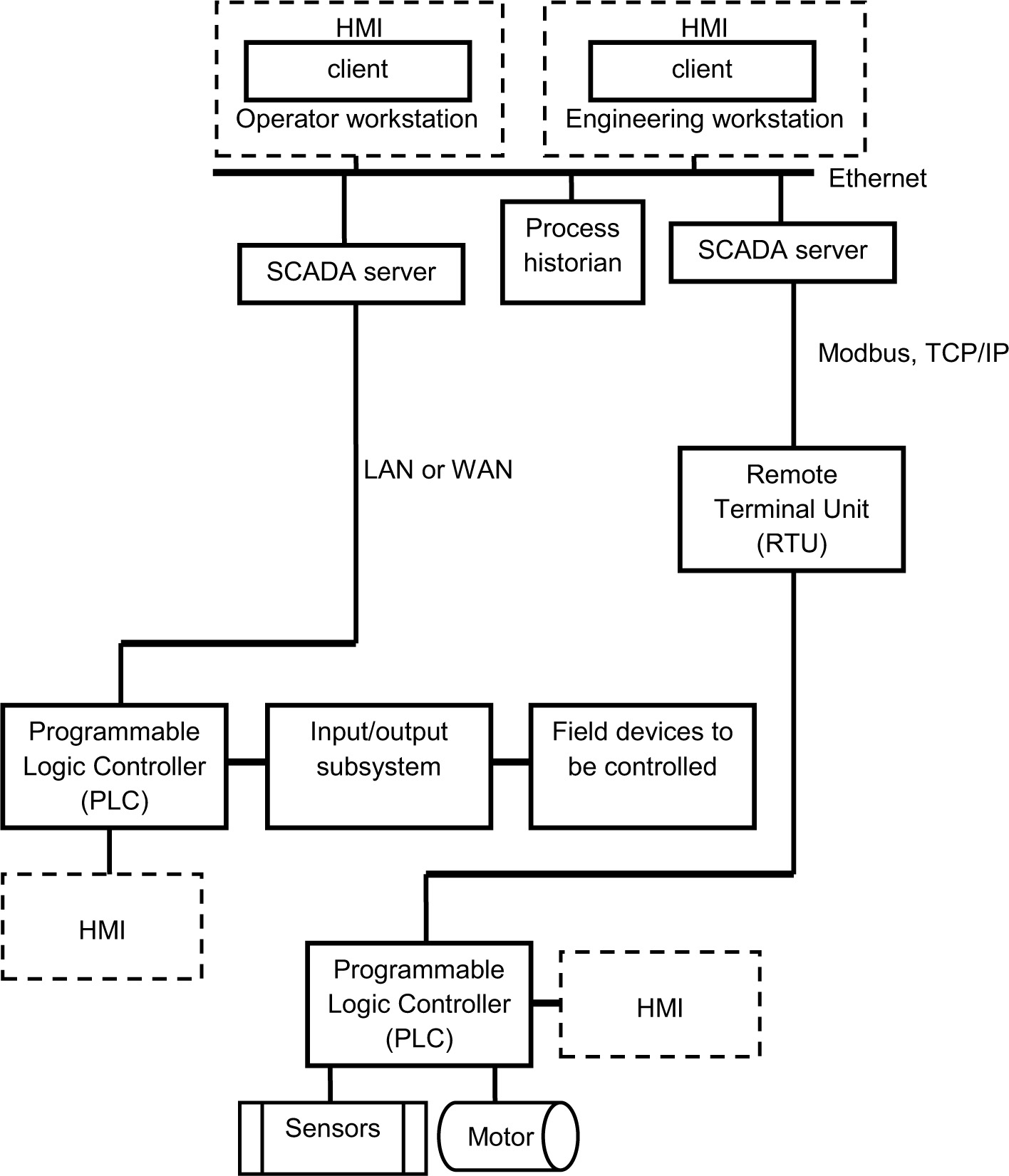
Figure 1-2. Example of a distributed control system
An SIS is usually implemented in parallel with conventional control systems to reduce the risks associated with explosive or other dangerous environments.
Figure 1-3. Safety instrumented functions vs. other process functions
[Source: ANSI/ISA-84.00.01-2004 Part 1 (IEC 61511-1 Mod)]
Thus, the proper application of an SIS should be preceded by a formal risk assessment to identify possible threats, vulnerabilities, and likelihoods of occurrence. An excellent guide to risk management is NIST SP 800-398, which takes a global, multitiered approach to risk management, where system risk is one part of a hierarchy of risk management levels. The document is aimed toward IT applications, but many of the principles are applicable to industrial automation and control systems. The document describes the following three tiers of an organization-wide risk management paradigm:
1. Tier 1 – Organization: Establishes and implements governance structures consistent with the organizational mission and goals.
2. Tier 2 – Mission/Business Processes: Designs, develops, and implements mission/business processes to support the mission defined in Tier 1.
3. Tier 3 – Information Systems: Integrates risk management activities into the system development life cycle (SDLC) of organizational information systems and addresses the resilience of organizational information systems.
NIST 800-39 will be discussed in more detail in Chapter 5 of this book.
ANSI/ISA-84.00.01-2004 Part 1(IEC 61511-1 Mod) promotes two important concepts associated with an SIS, namely the safety life cycle and safety integrity levels, and defines these terms as follows:
• Safety life cycle – Necessary activities involved in the implementation of safety instrumented function(s) occurring during a period of time that starts at the concept phase of a project and finishes when all of the safety instrumented functions are no longer available for use.
• Safety integrity level (SIL) – Discrete level (one of four) for specifying the safety integrity requirements of the safety instrumented functions to be allocated to the safety instrumented system. Safety integrity level 4 is the highest level of safety integrity; safety integrity level 1 is the lowest.
Figure 1-4 provides a flow diagram of the SIS life cycle phases and functional safety assessment steps. The clauses cited in the figure refer to clauses in the ANSI/ISA-84.00.01-2004 document.
Industrial Automation and Control System Protocol Summary
A protocol defines the rules for entities to use in communicating with each other. In order to better manage communications and compartmentalize the activities required to establish, maintain, use, and close communication links, high-level models are used. In particular, layered architectures are useful in defining the various communication functions in a hierarchical manner. Two widely popular implementations of the layered architecture paradigm are the Open Systems Interconnect (OSI) model and the Transmission Control Protocol/Internet Protocol (TCP/IP) model.
Figure 1-4. SIS life cycle and functional safety elements
[Source: ANSI/ISA-84.00.01-2004 Part 1 (IEC 61511-1 Mod)]
The OSI Model
In the early 1980s, the International Organization for Standardization (ISO) developed the Open Systems Interconnection (OSI) reference model. The model functions by encapsulating data and transferring it to an adjacent lower level, where the data is again encapsulated by the lower level, for example by adding a header. Table 1-1 summarizes the OSI model layers and the protocols associated with each layer.
Table 1-1. OSI Model Layers
|
Layer |
Role |
Protocols |
|
7-Application |
Provides for application support and verifies receiver availability. |
SMTP (Simple Mail Transport Protocol), FTP (File Transfer Protocol), SNMP (Simple Network Management Protocol) |
|
6-Presentation |
Conducts translations and conversions for the application layer, including compression, decryption, and encryption. |
MPEG (Motion Pictures Experts Group), HTTP (Hypertext Transfer Protocol), JPEG (Joint Photographic Experts Group) |
|
5-Session |
Sets up communication connections, controls the data transmission during a session, and terminates the connection. |
NFS (Network File System) - Supports file sharing, RPC (Remote Procedure Call) |
|
4-Transport |
Sets up a logical connection between the transmitter and receiver. The transport layer is connection-oriented and ensures data delivery to the receiver. |
TCP (Transmission Control Protocol), UDP (User Datagram Protocol) |
|
3-Network |
Performs error checking, addressing, routing, and node traffic control. |
IP (Internet Protocol), ICMP (Internet Control Message Protocol) |
|
2-Data Link |
Includes the media access control (MAC) sublayer and logical link control sublayer. Performs error-free packet transmission. |
PPP (Point-to-Point Protocol), ARP (Address Resolution Protocol) |
|
1-Physical |
Converts packets into electrical or optical signals for sending on the transmission media, such as wiring or cables. Defines network electrical and mechanical interfaces to the network transmission media. |
EIA-232C (RS-232C), EIA-422-B (RS-422) |
In the 1970s, the U.S. Department of Defense developed the Transmission Control/Internet Protocol (TCP/IP), which is the basic protocol of the Internet. It was developed prior to the OSI model and is named from two of its most important protocols: the Transmission Control Protocol and the Internet Protocol. The OSI model is a more formalized layered suite of protocols, but inherited some its architecture from TCP/IP. Table 1-2 summarizes the four TCP/IP layers and the protocols associated with each layer.
Table 1-2. TCP/IP Model Layers
|
Layer |
Role |
Protocols |
|
4-Application |
Provides the interface to the user. |
Telnet, FTP, SNMP, SMTP |
|
3-Host-to-Host or Transport |
Provides connection-oriented end-to-end communications, supports error-free packet delivery, and organizes data in to packets. |
TCP, UDP |
|
2-Internet |
Performs addressing and routing functions. |
IP, ARP, ICMP PPP |
|
1-Network Access |
Combines the operations of the OSI physical and data link layers |
EIA-422-B (RS-422), EIA-232C (RS-232C), IEEE 802.2 Logical Link Control |
With this background of the OSI and TCP/IP models, the salient points of some control system protocols can be reviewed. This summary is not intended to be a comprehensive coverage of all protocols in use, but a sampling of some of the popular approaches.
OPC (Object Linking and Embedding [OLE] for Process Control)
NIST 800-829 defines OPC as “a set of open standards developed to promote interoperability between disparate field devices, automation/control, and business systems.” The OPC standards specifications are now known as the Data Access Specification. OPC was built on the OLE COM (Component Object Model) and DCOM (Distributed Component Object Model) technologies of Microsoft, which specified a standard set of objects, interfaces, and methods for use in process control and manufacturing automation applications. Because of some vulnerabilities in Microsoft’s software, OPC should only be applied between the demilitarized zone (DMZ) and control networks and not used between the corporate network and the DMZ.
The following list summarizes some of the popular OPC specifications:
• OPC Alarms & Events – Supports process alarms, messaging, and event notifications on demand
• OPC Batch – Provides OPC functionality to batch processes
• OPC Command – Provides interfaces that support OPC clients and servers in managing commands sent to devices
• OPC Data Access – Provides for the transmission of data from PLCs, IEDs, and DCSs to HMI clients
• OPC Data eXchange – Supports interoperability among a variety of vendors and communication and management services among Ethernet fieldbus connections
• OPC Historical Data Access – Provides archiving of historical data
• OPC Security – Safeguards critical data through access control and integrity protection mechanisms
• OPC Unified Architecture – Defines specifications that do not use Microsoft COM in order to enhance cross-platform usage
OPC Unified Architecture
OPC Unified Architecture (OPC UA) is an OPC Foundation10 Web services technology designed to provide the functions of OPC, but to support interoperability among different platforms and achieve independence from Microsoft COM/DCOM. It can also interface easily with corporate enterprise systems and manufacturing management systems. Some of the features of OPC UA are:
• Integrated security
• Multiplatform compatibility
• Scalable
• Object-oriented
• Ability to identify specific components
• Information modeling, including how data is communicated
Modbus/TCP Model
Modbus is an OSI Layer 7 serial communication protocol that was developed by Modicon in 1979 for use with data acquisition and control systems. Modbus enables reliable communication among various control devices, including PLCs. A number of modifications to Modbus have evolved, such as Modbus/TCP, which was developed to be compatible with the TCP/IP model. Additional Modbus variants include Modbus ASCII, Modbus RTU, Modbus RTU/IP, and Modbus over UDP.
The DNP3 Protocol
The Distributed Network Protocol (DNP)3 is an open SCADA protocol that is used for serial or TCP/IP communications between control devices. It is widely used by utilities, such as water companies and electricity suppliers, for the exchange of data and control instructions between master control stations and remote computers or controllers called outstations. Figure 1-5 is an example of a SCADA application, using DNP3 with a data concentrator in a hierarchical mode.
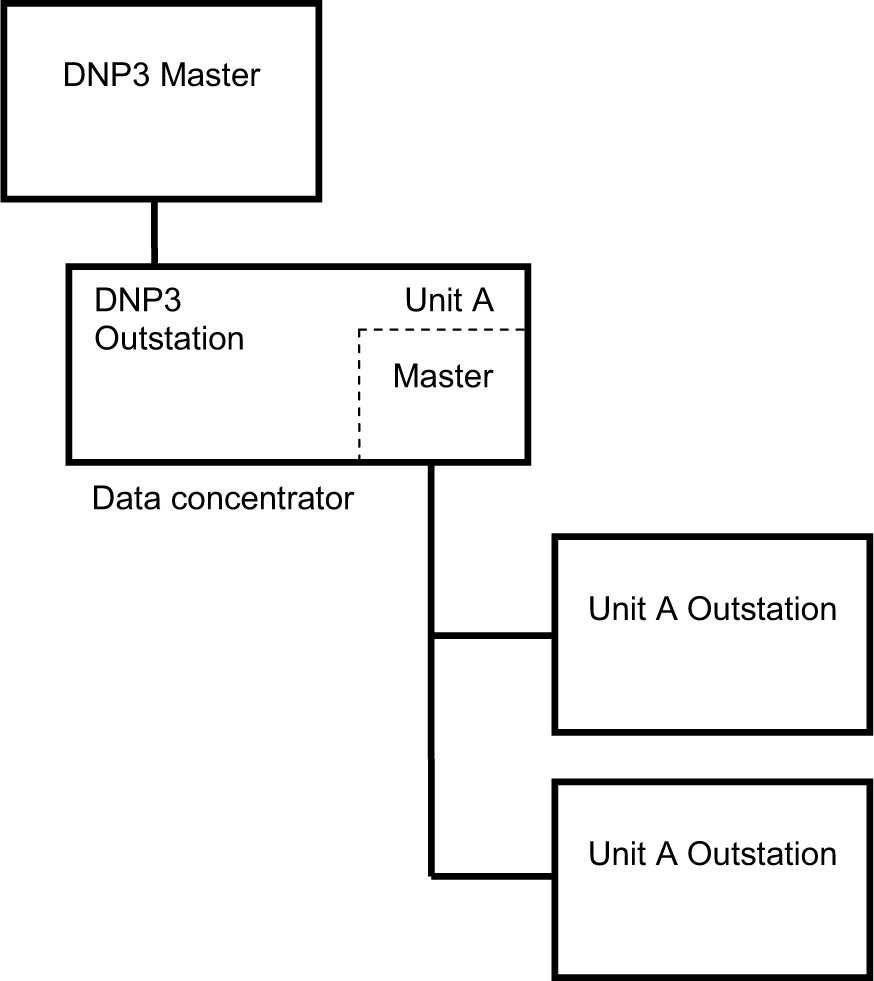
Figure 1-5. DNP3 example usage
Utility Communications Architecture 2.0/IEC61850
The Utility Communications Architecture (UCA), version 2.0, comprises a set of communications protocols for use by electric utilities. In 1999, UCA 2.0 evolved to the layered architecture standard IEC 61850 for substation automation. IEC 61850-enabled IEDs to obtain power grid condition data via an Ethernet process bus and from merge units, which provide interfaces to field devices. Legacy devices utilize an IEC 61850 wrapper around legacy protocols for compatibility. IEC 61850 includes the following features:
• Abstract definitions of services and data
• Definitions for IED communications
• IED communications through substation buses
• Mapping of services to protocols
• Object-oriented approach
• Standardized configuration language (SCL)
Figure 1-6 provides an overview of an IEC 61850-based substation.
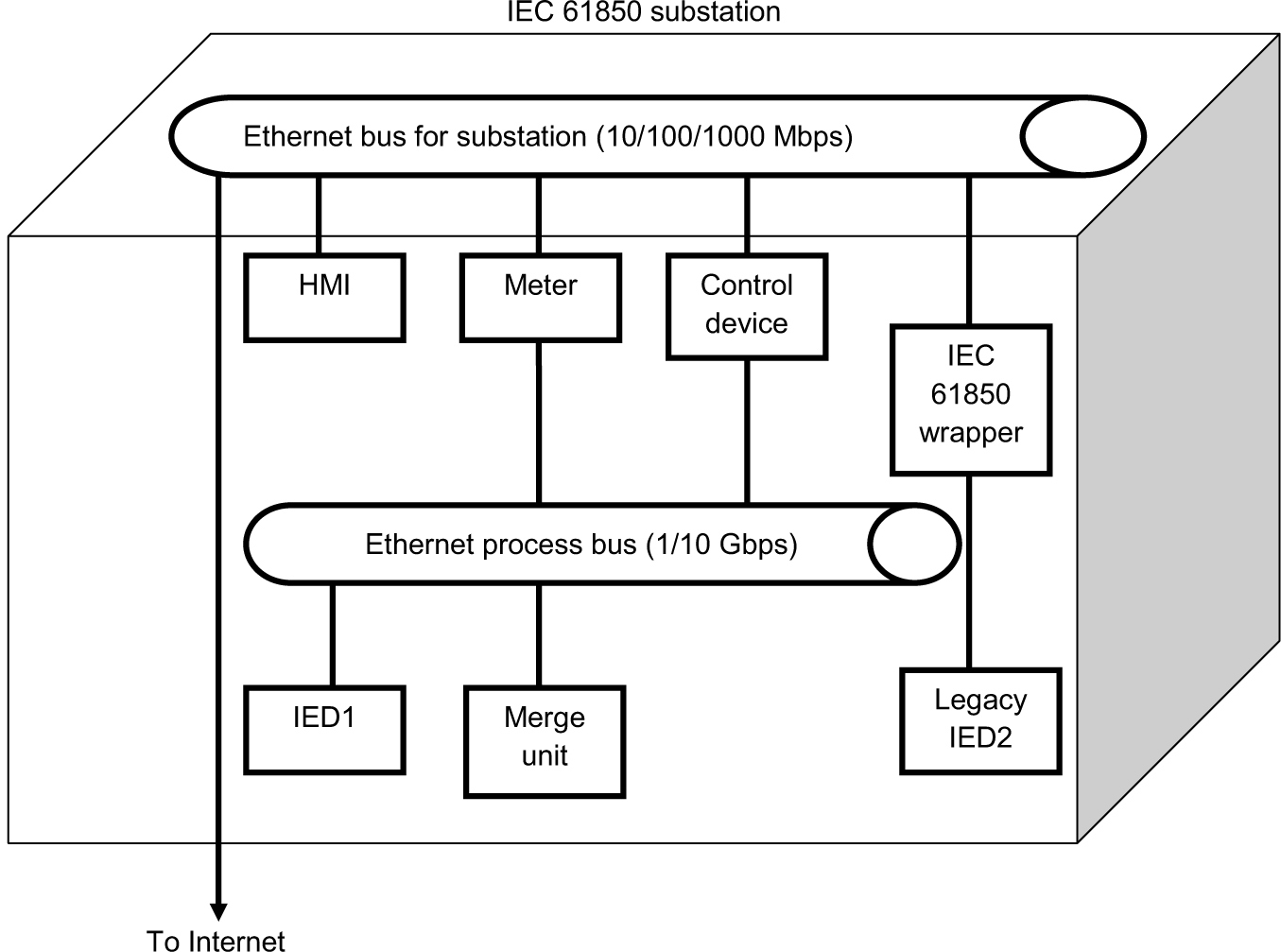
Figure 1-6. An IEC 61850 substation
Process fieldbus or Profibus is an open standard that defines the electrical, mechanical, and functional aspects of a fieldbus that addresses deterministic data acquisition implementations. It is compatible with European international fieldbus standard EN 50 170. There are three versions of Profibus: Profibus Process Automation (PA), Profibus Decentralized Peripherals (DP), and Profibus Fieldbus Message Specification (FMS). Profibus PA communicates with control devices and data acquisition components through a common serial bus and is specifically designed for use in hazardous and explosive environments through current limiting elements. Profibus DP communicates over a high-speed network with sensors and actuators through a central controller and is suited for factory automation requirements. Profibus FMS supports communications among a large number of high-level applications at moderate transmission rates.
Controller Area Network
Controller Area Network (CAN) protocols, also known as ISO Standard 11898-1, were developed in 1986 by Robert Bosch GMBH in Germany for control applications in automobile production lines. The protocol uses an altered form of Ethernet Carrier Sense Multiple Access with Collision Detection (CSMA/CD) to implement a deterministic protocol for SCADA systems. In a deterministic system, an element must respond to events in a predictable manner with a known response time. For example, when controlling a robot arm, its position must be known, and the time it takes to obtain position information must be within certain bounds. Similarly, the time it takes to send commands to the arm and have it respond must be predictable and bounded.
EtherNet/IP
EtherNet/IP is an application layer protocol designed for industrial automation and control systems applications and is a member of a family of networks that implement the Common Industrial Protocol (CIP™) at its upper layers. EtherNet/IP provides control, configuration, and data exchange capabilities on an Ethernet network. The protocol defines network entities and devices as objects and uses a TCP/IP object for the TCP/IP protocol and an Ethernet link object to set up an EtherNet/IP link. EtherNet/IP uses the Open Systems Interconnection (OSI) model and implements CIP at the session layer and above, and adapts CIP to the specific Ethernet/IP technology at the Transport layer and the lower layers. A typical EtherNet/IP architecture is shown in Figure 1-7.
OpenSAFETY11 is an application layer protocol sponsored by the Ethernet Powerlink Standardization Group12 (EPSG), which supports the communication of safety-related data over a variety of industrial networks and ensures data transfer integrity. The performance of openSAFETY data communications is a function of the network and the specific data transfer protocols being used. For example, openSAFETY can be used with Modbus and EtherNet/IP. It is compatible with IEC 61508 and can provide safe implementations up to SIL-3. An important characteristic of openSAFETY is that it employs a variable-length frame with a uniform format that supports safe distribution of values. To meet these requirements, openSAFETY verifies parameters using cyclic redundancy check (CRC) and encapsulates its messages, which independently tunnel through the extant protocols being used in the data acquisition and control network. Figure 1-8 illustrates the relationship of openSAFETY to the other protocols in the OSI layered architecture.
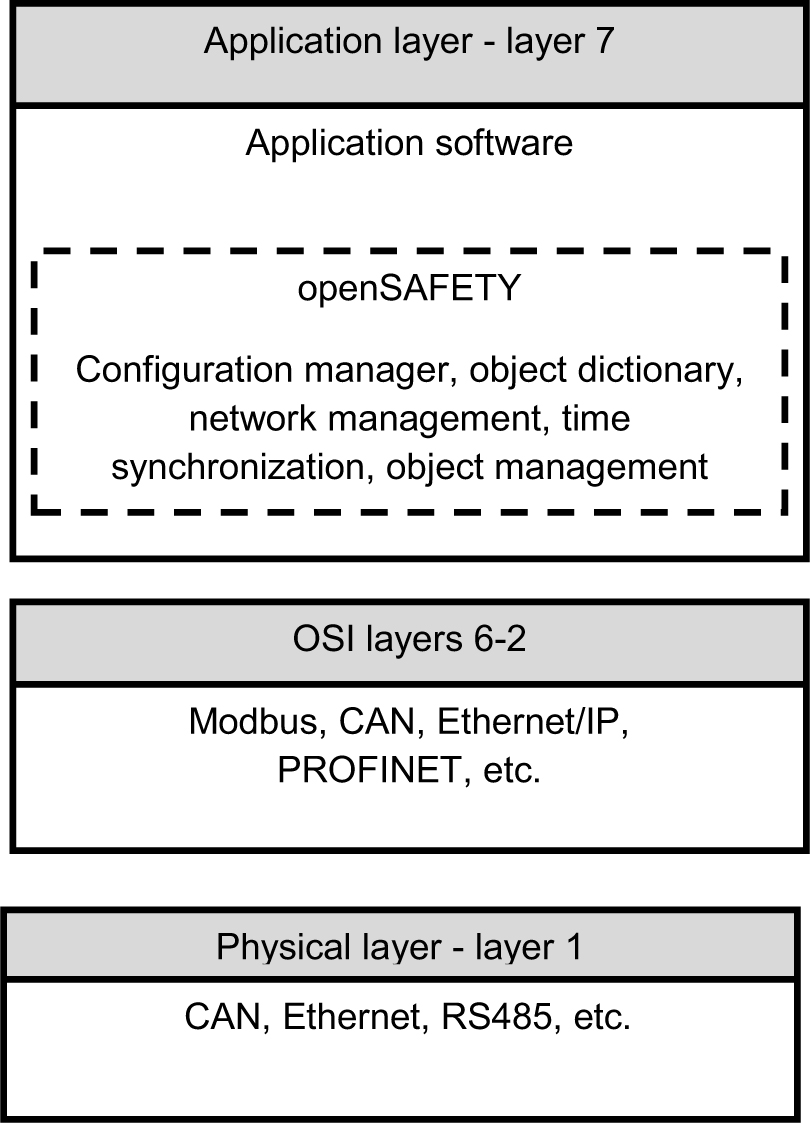
Figure 1-8. A typical openSAFETY architecture
Issues in Industrial Automation and Control Systems Security
No one questions the need to protect a nation’s critical infrastructure and essential production processes. The available means and methods required to accomplish this defense are varied and have multiple characteristics associated with them. These characteristics include:
• Hardware cost
• Software cost
• Reliability
• Level of assurance
• The effect of security controls on performance
• Maintenance issues
• Safety issues
• Effect on product quality
• Response to emergency situations
• Interfaces to management systems
• Compatibility with 24/7 operations
These issues and others will be explored in the chapters of this book to provide a foundation for securing industrial automation and control systems.
Over the past two decades, methodologies and best practices in the field of information system security have been developed, refined, and codified. They comprise a rich compendium of proven and effective measures to secure computer systems and networks. The fundamentals of these developments will be presented in Chapter 2 as a basis for the evolution of security technologies applicable to industrial automation and control systems. A number of these paradigms are not directly applicable to industrial automation and control systems, but many are, and many can be employed with modifications tailored to the unique characteristics of these systems. These adapted methods can be effective in securing industrial automation and control systems against threats, such as viruses, Trojan horses, worms, and attacks that result in the unauthorized modification and manipulation of critical data, denial of service and availability, unauthorized modification of audit logs, and general disruption of critical operations.
The information system security approaches embrace a wide variety of disciplines and include:
• Policies, procedures, and standards
• Access control mechanisms
• Physical security
• Identification and authentication technologies, such as biometrics and security tokens
• Audit trails
• Real-time monitoring of system and network information
• Risk management
• Business continuity and disaster recovery planning
• Firewalls to filter message traffic
• Intrusion detection and protection systems
• Public key and secret key cryptography
• Malware detection, isolation, and elimination
Review Questions for Chapter 1
(Please read the questions carefully and select the one BEST answer.)
1. According to NIST SP 800-82, the term “industrial control system” encompasses which of the following?
a. SCADA systems
b. Distributed control systems (DCSs)
c. Programmable logic controllers (PLCs)
d. All of the above
2. According to ANSI/ISA-99.00.01, “a collection of personnel, hardware, and software that can affect or influence the safe, secure, and reliable operation of an industrial process” is a(n):
a. Industrial automation and control system
b. Distributed control system
c. Discrete control system
d. Programmable logic controller
3. A “type of loosely coupled distributed monitoring and control system commonly associated with electric power transmission and distribution systems, oil and gas pipelines, and water and sewage systems” is defined by ANSI/ISA-99.00.01 as which of the following?
a. Distributed control system
b. SCADA system
c. Safety instrumented system (SIS)
d. Human-machine interface (HMI)
4. Which one of the following items is NOT a component of a classical SCADA system model?
a. Human-machine interface (HMI)
b. Remote terminal unit (RTU)
c. Enterprise resource planning (ERP)
d. Programmable logic controller (PLC)
5. Which of the following is NOT a characteristic of a SCADA master terminal unit (MTU)?
a. Has two-way communication with field devices
b. Usually located at the master control center
c. Has high-bandwidth communication requirements
d. Communicates through telephone, VHF/UHF radio, spread spectrum radio, satellite, and/or microwave
6. In a typical SCADA application, what component serves as a data concentrator and is an interface between the MTU and field devices?
a. HMI
b. RTU
c. Data historian
d. Relational database
7. IEC standard 61131-3 was designed to make it easier to implement control logic functions. IEC 61131-3 is which of the following?
a. Vendor-independent international standard for PLC programming languages
b. Standard guide to industrial control systems
c. Safety instrumented systems (SIS) standard for the process industry
d. Integrated enterprise-wide risk management standard
8. Which of the following is NOT a characteristic of a data historian?
a. Provides for prompt recovery of data
b. Performs data compression
c. Supports interactive storage and retrieval of detailed production information
d. Provides system histories over given time periods
9. A yield accounting system used in conjunction with a SCADA system provides which of the following functions?
a. Plant material movement
b. Inventory discrepancies
c. Material balances
d. All of the above
10. ANSI/ISA-99.00.01-2007 defines which of the following as “a type of control system in which the system elements are dispersed but operated in a coupled manner?”
a. Distributed control system
b. Discrete control system
c. Dispersed control system
d. Coupled control system
11. ANSI/ISA-84.00.01-2004 Part 1(IEC 61511-1 Mod) defines which of the following as an “instrumented system used to implement one or more safety instrumented functions (SIF)”?
a. Safety surety system
b. Failure proof system
c. Safety instrumented system
d. Safety function system
12. Necessary activities involved in the implementation of safety instrumented function(s) occurring during a period of time that starts at the concept phase of a project and finishes when all of the safety instrumented functions are no longer available for use is known as which of the following?
a. Safety duration
b. Safety life cycle
c. Safety boundary
d. Safety period
13. The safety integrity level (SIL) is a discrete level for specifying the safety integrity requirements of the safety instrumented functions to be allocated to the safety instrumented systems. Which of the following statements is TRUE?
a. Safety integrity level 4 has the lowest level of safety integrity; safety integrity level 1 has the highest.
b. Safety integrity level 4 has the highest level of safety integrity; safety integrity level 1 has the lowest.
c. Safety integrity level 3 has the highest level of safety integrity; safety integrity level 1 has the lowest.
d. Safety integrity level 3 has the lowest level of safety integrity; safety integrity level 1 has the highest.
14. The Open Systems Interconnection (OSI) reference model has how many layers?
a. Six
b. Five
c. Seven
d. Four
15. Which layer of the OSI model converts packets into electrical or optical signals for sending on the transmission media?
a. Application
b. Presentation
c. Physical
d. Session
16. What are the four layers of the TCP/IP model?
a. Application, Host-to-Host, Internet, and Network Access
b. Application, Presentation, Internet, and Network Access
c. Application, Network, Internet, and Network Access
d. Application, Host-to-Host, Internet, and Physical
17. NIST 800-82 defines which of the following as “a set of open standards developed to promote interoperability between disparate field devices, automation/control, and business systems”?
a. Modbus/TCP
b. OPC
c. DNP3
d. Profibus
18. The protocol that supports the communication of safety-related data over a variety of industrial networks and ensures data transfer integrity is known as which of the following?
a. Safety instrumented system (SIS)
b. Safety instrumented function (SIF)
c. OpenSAFETY
d. ClosedSafety
19. Which of the following statements relative to the IEC layered architecture Standard IEC 61850 for substation automation is NOT true?
a. It is a set of protocols for electric utilities.
b. IEC-enabled devices can obtain power grid condition data via an Ethernet process bus.
c. Merge units provide interfaces to field devices.
d. It is not compatible with legacy protocols.
20. Which of the following are versions of Profibus?
a. Profibus PA, Profibus CP, Profibus CIP
b. Profibus PA, Profibus DP, Profibus FMS
c. Profibus PA, Profibus CP, Profibus FMS
d. Profibus PA, Profibus CIP, Profibus FMS
References
1 ANSI/ISA-99.00.01-2007, Security for Industrial Automation and Control Systems Part 1: Terminology, Concepts, and Models, October 2007.
2 NIST Special Publication 800-82, Guide to Industrial Control Systems (ICS) Security Supervisory Control and Data Acquisition (SCADA) Systems, Distributed Control Systems (DCS), and other control system configurations, such as Programmable Logic Controllers (PLC), Final Public Draft, September 2008.
3 IEEE Std. C37.1-1994, IEEE Standard Definition, Specification, and Analysis of Systems Used for Supervisory Control, Data Acquisition, and Automatic Control, Institute of Electrical and Electronics Engineers, 1994.
4 The Automation, Systems, and Instrumentation Dictionary, 4th Edition. Research Triangle Park: ISA, 2003.
5 ANSI/ISA-99.00.01-2007, Security for Industrial Automation and Control Systems Part 1: Terminology, Concepts, and Models, October 2007.
6 NIST Special Publication 800-82, Guide to Industrial Control Systems (ICS) Security Supervisory Control and Data Acquisition (SCADA) Systems, Distributed Control Systems (DCS), and other control system configurations, such as Programmable Logic Controllers (PLC), Final Public Draft, September 2008.
7 ANSI/ISA-84.00.01-2004 Part 1 (IEC 61511-1 Mod), Functional Safety: Safety Instrumented Systems for the Process Industry Sector – Part 1: Framework, Definitions, System, Hardware and Software Requirements, September 2004.
8 NIST Special Publication 800-39, Integrated Enterprise-Wide Risk Management Organization, Mission, and Information System View, Final Public Draft, December 2010.
9 NIST Special Publication 800-82, Guide to Industrial Control Systems (ICS) Security Supervisory Control and Data Acquisition (SCADA) Systems, Distributed Control Systems (DCS), and other control system configurations such as Programmable Logic Controllers (PLC), Final Public Draft, September 2008.