Chapter 25. Microsoft Command Line Tools
This chapter covers the following A+ 220-1002 exam objective:
• 1.4 – Given a scenario, use appropriate Microsoft command line tools.
The command-line, that’s where the real technicians live. Anything you can do in a GUI-based system can be done in the command line, sometimes more. Get to know it. For Microsoft Windows, you should become fluent in the Command Prompt and the PowerShell and know as many commands as you can.
This chapter covers one of the most important objectives in the A+, so I suggest you take breaks after each group of commands. We’ll begin with how to navigate folders and files within the Command Prompt. By the way, when working in the command-line interface, the original name for folders was directories, so I will be using that term often. Next, we’ll discuss some of the commands that can be used to analyze and configure the hard drive and file system. Then we’ll move into some networking commands, and finally some advanced tools.
Once you get the hang of it, it’s a blast. The great thing about the command line is that it hasn’t changed much over time. Or at least, not nearly as much as the various GUI changes that Windows has undergone. Plus, many companies desire technicians that have good command line skills; which can ultimately translate to job security. Enough said.
1.4 – Given a scenario, use appropriate Microsoft command line tools.
ExamAlert
Objective 1.4 focuses on Microsoft command line tools: dir, cd, .., ipconfig, ping, tracert, netstat, nslookup, shutdown, dism, sfc, chkdsk, diskpart, taskkill, gpupdate, gpresult, format, copy, xcopy, robocopy, net use, net user; help and /?; and commands available with standard vs. administrative privileges.
Command Prompt Basics
Microsoft’s Command Prompt is its command-line interface (CLI). This is the text-based interface in which you can issue commands concerning files and folders, networking, services, and so on. You can open it in several ways, including the following:
• For all versions of Windows: Open the Search tool and type CMD (or search for a variety of words/phrases associated with the Command Prompt). Windows 10 displays the Search tool on the taskbar by default. The Search tool can be found on the Start screen or by bringing up the Charms bar in Windows 8. The Search tool can be found in Windows 7 by simply clicking Start.
• For all versions of Windows: Press Windows+R to open the Run prompt and type CMD (my personal favorite).
• In Windows 10 and 8: Right-click the Start button and select Command Prompt. Another great keyboard shortcut is Windows+X. This is the same as right-clicking the Start button.
• In Windows 10: Click Start, then on the programs list, scroll down to Windows System > Command Prompt.
• In Windows 7: Navigate to Start > All Programs > Accessories > Command Prompt.
In Windows, some commands need to be run as an administrator; to open the Command Prompt as an administrator, do one of the following:
• In all versions of Windows: Open the search tool and type CMD in the Search field; instead of pressing Enter, press Ctrl+Shift+Enter. (Make sure it is highlighted.)
• In Windows 10: Go to the programs list > Windows System, and right-click Command Prompt, click More, then select Run as administrator.
• In Windows 10 and 8: Right-click the Start button and select Command Prompt (Admin).
• In Windows 7: Click Start > All Programs > Accessories; then right-click Command Prompt and select Run as Administrator.
Running the Command Prompt as an administrator is also known as running it in elevated mode. You will be using it often.
ExamAlert
Know how to open programs from the Search tool, the Start menu, and from the Run prompt.
An additional command line environment called the PowerShell is integrated into Windows. PowerShell is a combination of the Command Prompt and a scripting language. (It is the successor to the Windows Script Host.) It enables administrators to perform administrative tasks that integrate scripts and executables. This can be opened in the following ways:
• In all versions of Windows: Use the Search tool.
• In all versions of Windows: Go to the Run prompt and type powershell.exe.
• In Windows 10: Navigate to Start > Windows PowerShell > Windows PowerShell.
• In Windows 7, you can open it by navigating to Start > All Programs > Accessories > Windows PowerShell.
It should be noted that if you use PowerShell in place of the Command Prompt, you should remember to always use a space after a command; otherwise the shell will not recognize the command. For example, typing ipconfig /all is correct, whereas ipconfig/all would not function. Remember: using a space after a command is the proper way.
For administrators who write scripts often, there is also the Windows PowerShell ISE (Integrated Scripting Environment); this allows an admin to not only run commands, but also write, test, and debug scripts with the shell and the script running in a side-by-side manner. So, you can write a script in the text editor, and “run” it over and over again, making modifications as you go. You can open this from the Run prompt by typing powershell_ise.
Navigating and Working with Directories and Files in the Command Prompt
Have I mentioned yet that just about anything you can do in Windows can also be done in the Command Prompt? It’s true. And sometimes the Command Prompt is faster than the GUI—if you can type quickly! There are three commands used to work with directories in the Command Prompt. As a reminder, directory is the original name for folder. They are more accurately called directories when working in any command line (such as the Windows Command Prompt) and folders when working in the GUI, but the two terms can be used interchangeably.
• cd: Change Directory. This command enables you to move from one directory to another. Actually, you can go from any one directory to any other using just one cd command. Two simple commands that you can issue are cd.. and cd\. The cd.. command moves you up one directory; it takes you from the current directory to the parent directory. The cd\ command takes you directly to the root of the volume that you are working in.
• md: Make Directory. This command creates directories.
• rd: Remove Directory. This command enables you to remove directories. You can also remove directories that contain files by utilizing the /S switch.
All these commands can be used such that their functions affect any folder you choose within the directory structure (which used to be known as the DOS tree, but I digress). Figure 25.1 provides a sample directory structure.
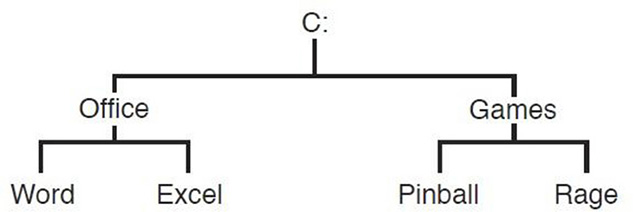
Figure 25.1 A sample directory structure
For example, let’s say that your current position is C:\Office. From here or any other location, you can do anything to any folder in the entire directory tree. Let’s give a couple examples:
• Change the current position to the Pinball folder. To do this, the command would be either cd c:\games\pinball or just cd \games\pinball.
• Make a directory called “documents” within Word. To do this, the command syntax would be md c:\office\word\documents.
• Delete the directory Excel. To do this, the command would be rd c:\office\excel.
ExamAlert
Know how to navigate the Command Prompt with the cd command, cd.. and cd\.
Some other commands you might use when working with directories and files include dir, tree, copy, xcopy, robocopy, and del.
• dir: This is the directory command. When used alone, it displays the contents of the current directory. But it can be configured to show information in any other directory. For example, dir \office\excel will show the contents of the Excel directory regardless of what directory you are currently in. You can also use the dir command to customize how content is listed. For example, /p will show information by the page, /w is wide list format, and so on. To find out more about the dir command (or any other command, for that matter), type dir /?. The /? is the switch that tells the Command Prompt to display the help file for that command. It can be placed on the end of any valid Command Prompt command.
• tree: This command shows all the directories and subdirectories within your current position. Be careful where you run this because it could list information for quite a while and cause some stress on the hard drive. For example, stay away from big directories, such as the root, which is C:\, \Windows, and \Windows\System32.
• copy: This command allows you to copy one or more files to another location. If I wanted to copy a file named test.txt from the office directory to the Excel directory, I would type copy \office\test.txt \office\excel\. Now the original file is in \office and the copy is in \excel. There are more powerful versions of this command—known as xcopy and robocopy—that we talk about next.
• xcopy: The xcopy command is meant to copy large amounts of data from one location to another; it even makes exact copies of entire directory trees. One example of its usage would be to copy the contents of a Windows DVD-ROM over to a USB flash drive so that you can use the USB flash drive as installation media. The command for this would be xcopy d:\*.* /E/F e:\. This is assuming that D: is the DVD-ROM drive and E: is the USB flash drive. *.* means all files with all extensions within the D: drive. /E indicates that all folders and subfolders will be copied including empty ones. /F displays full source and destination files while copying. For more information about xcopy, type xcopy /?.
• robocopy: (Robust File Copy) is a directory replication tool. It is meant to copy directories that contain lots of data; it can even mirror complete directory trees from one computer to another. robocopy is the successor to xcopy. Some of the advantages of this tool are that it can tolerate network interruptions, skip past junctions (such as the \Documents and Settings to \Users junction), and preserve data attributes and time stamps. robocopy does not copy individual files; it copies only directories (for example, robocopy c:\office c:\games). This will copy all the information within the \office directory to the \games directory. It also gives in-depth results of its actions. You can also use robocopy to copy information to other computers by using the \\computername\share, which is Microsoft’s Universal (or Uniform) Naming Convention (UNC).
• del: When you are done with a file and are ready to delete it, use DEL. For example, if you want to delete the test.txt file that you just copied to the Excel folder, type del \office\excel\test.txt.
Note
By the way, I created the test.txt text file within Notepad, which is available via the search tool or by going to Run and typing notepad. Notepad is Windows’ default graphical text editor that you can use for editing text and batch files. However, you might opt to use third-party text editors, especially if you plan to create batch files or do any coding (for example, in the PowerShell, HTML or PHP).
ExamAlert
Understand how to use dir, tree, copy, xcopy, robocopy, and del.
Partitioning and File System-based Commands
There are a slew of commands that you can use to make changes to your hard drive’s partitions and file systems, and check the hard drive and file system integrity. Some that you should know for the exam include: diskpart, format, defrag, and convert.
• diskpart: This utility is the command line counterpart of Windows’ Disk Management program. This program needs to be run by typing diskpart before any of the diskpart actions can be implemented. This brings the user into the DISKPART> prompt. From here, you can create, delete, and extend volumes, assign drive letters, make a partition active, and so on. Essentially, everything that you can do in Disk Management can be done with diskpart. When you are in the DISKPART> prompt, enter a question mark (?) to learn about the various options within the Diskpart program. When you finish using diskpart, type exit to return back to the standard Command Prompt.
• format: A command used to format magnetic media such as hard drives and solid-state media (such as USB flash drives) to the FAT, FAT32, or NTFS file systems. An example of formatting a USB flash drive in the command line would be format F:. The type of file system that the media will be formatted to can be specified with the switch /FS:filesystem, where file system will equal FAT32 or NTFS, and so on.
• defrag: The command line version of the Disk Defragmenter. To analyze a drive, type defrag -a. If a volume needs to be defragmented, but has less than 15 percent free space, use the -f parameter.
• convert: This command enables you to convert a volume that was previously formatted as FAT32 over to NTFS without losing any data. An example of the convert command would be convert d: /FS:NTFS, which would convert the hard drive volume D: to NTFS. Sometimes you might encounter older computers’ hard drives (or flash media) that require being formatted as NTFS for compatibility with other devices and networked computers.
Chkdsk and SFC
A good technician uses commands to analyze and possibly repair a hard drive and its system files. Two commands that can aid in this endeavor include chkdsk and SFC.
Chkdsk
Chkdsk checks a drive, fixes basic issues like lost files, and displays a status report; it can also fix some errors on the drive by using the /F switch. Here’s an example of the three stages of results when running the chkdsk command:
The type of the file system is NTFS. Volume label is WinXPC. WARNING! F parameter not specified. Running CHKDSK in read-only mode. CHKDSK is verifying files (stage 1 of 3)... File verification completed. CHKDSK is verifying indexes (stage 2 of 3)... Index verification completed. CHKDSK is recovering lost files. Recovering orphaned file ~WRL3090.tmp (59880) into directory file 28570. Recovering orphaned file ~DFA188.tmp (59881) into directory file 28138. CHKDSK is verifying security descriptors (stage 3 of 3)... Security descriptor verification completed. Correcting errors in the master file table's (MFT) BITMAP attribute. Correcting errors in the Volume Bitmap. Windows found problems with the file system. Run CHKDSK with the /F (fix) option to correct these. 31471300 KB total disk space.
I shortened the results, but notice that the utility warned that the /F switch was not specified. Also notice that the orphaned files were recovered, although they are just .tmp files and most likely not necessary for the functionality of Windows. Finally, the program found issues with the file system; to repair these, you would have to use the /F option. Be sure that you actually need to run chkdsk with the /F parameter before doing so. For example, if the system seems to function properly, but the standard chkdsk command gave an error, it might not be absolutely necessary to run chkdsk with the /F parameter.
One issue that plagues users is the infamous Missing Operating System message. If you get this, it usually means that either the drive has a few small errors, or the master boot record (MBR) on older systems has been damaged. But even though the system won’t boot, you can still run chkdsk to find and fix problems on the drive. Boot to the repair environment (if possible), or to the Windows media, access Windows RE, and then open the Command Prompt. From there, run chkdsk with either the /F switch (which fixes errors on the drive) or the /R switch (which locates bad sectors and recovers data)—or run both. This procedure can also help with Invalid Boot Disk errors. (Of course, first check that the BIOS is booting to the correct drive in the boot priority menu.)
SFC
System File Checker (SFC) is a Windows utility that checks protected system files. It replaces incorrect versions or missing files with the correct files. SFC can be used to fix problems with Edge/Internet Explorer or other Windows applications. To run SFC, open the Command Prompt and type SFC with the appropriate switch. A typical option is SFC /scannow, which scans all protected files immediately and repairs files. During this procedure, SFC writes the details of each repair to a file called CBS.log located in %systemroot%\Logs\CBS, which can be used to further analyze the system and the integrity of files. Another is SFC /verifyonly, which scans the integrity of files but does not perform a repair. If SFC finds that some files are missing, you might be prompted to reinsert the original operating system disc so the files can be copied to the DLL cache.
Note
Remember that %systemroot% is the folder where Windows was installed; by default, it is C:\Windows.
ExamAlert
Know your basic switches for chkdsk and SFC, such as chkdsk /F and sfc /scannow.
Networking Commands
There are many command line tools that we can use in Windows to help us analyze and troubleshoot a computer’s network connection; in this section, we delve into several of them. I recommend that you try all the variations of these on your computer. Some commands require that you open the Command Prompt as an administrator (elevated mode). For example, the SFC and chkdsk commands. I suggest simply running the Command Prompt as an administrator all the time (because that’s what you want to be, an administrator, right?).
The most commonly used command for analyzing a computer’s networking configuration is ipconfig. Let’s start with that.
ipconfig
The Internet protocol configuration command or ipconfig displays current TCP/IP network configuration values. This is one of the first tools you should use when troubleshooting network connectivity. When you type ipconfig, you get results similar to the following:
Windows IP Configuration Ethernet adapter Local Area Connection: Connection-specific DNS Suffix . : Link-Local IPv6 Address. . . . . : fe80::404b:e781:b150:b91a%11 IPv4 Address. . . . . . . . . . . : 192.168.0.100 Subnet Mask . . . . . . . . . . . : 255.255.255.0 Default Gateway . . . . . . . . . : 192.168.0.1
ipconfig combined with the /all switch shows more information, including whether or not DHCP is being used, the DNS server address, and the MAC address. The MAC address is the hexadecimal address that is burned into the ROM of the network adapter. This is a set of six hexadecimal numbers (for example, 00-03-FF-A0-55-16).
ExamAlert
To view additional IP configuration information, such as DNS servers and MAC addresses, use the ipconfig /all command.
This command can offer a lot of information about a problem. For example, if a user cannot connect to any Internet resources, it could be because the gateway address is improperly configured. Remember that the gateway address must be on the same network number as the IP address of the client computer. If a user can’t connect to any websites but can connect to other computers on the LAN, it could be that the DNS server address is incorrectly configured. Ipconfig also tells you whether the client computer’s IP address is obtained from a DHCP server or assigned via APIPA and whether it is a private or public address.
ipconfig can also be used to release and renew IP addresses. Sometimes this needs to be done if a computer’s IP address is not working properly and you want to obtain a new address from a DHCP server. To release the current IP address, type ipconfig/release; to renew, type ipconfig/renew.
Finally, if you are having DNS issues (for example, problems connecting to websites), you can erase the DNS cache by typing ipconfig/flushdns. Check out the various ipconfig switches by opening the Command Prompt and typing ipconfig /?. You should try this with every command in this section.
Ping
Ping tests whether another host is available over the network. It’s the easy way to see if another host is “alive.” Let’s say your gateway’s IP address is 192.168.0.1. To ping that computer, you would type ping 192.168.0.1 as an example and hopefully get the following output:
Pinging 192.168.0.1: with 32 bytes of data: Reply from 192.168.0.1: bytes=32 time<1ms TTL=64 Reply from 192.168.0.1: bytes=32 time<1ms TTL=64 Reply from 192.168.0.1: bytes=32 time<1ms TTL=64 Reply from 192.168.0.1: bytes=32 time<1ms TTL=64 Ping statistics for 192.168.0.1: Packets: Sent = 4, Received = 4, Lost = 0 (0% loss), Approximate round trip times in milli-seconds: Minimum = 0ms, Maximum = 0ms, Average = 0ms
The replies indicate that the host is alive and can be communicated with on the network. Any other message would indicate a problem (for example, the Request Timed Out or Destination Host Unreachable messages would require further troubleshooting). Keep in mind that if it’s the local computer that is configured incorrectly, you might not be able to ping anything! Also watch for the amount of time the ping took to reply back. A longer latency time could indicate network congestion.
Note
Latency is the time it takes for sent data packets to be received by a remote computer. Latency increases with distance, type of network connection used, and network congestion. For example, a ping to a computer on the LAN should have very low latency, perhaps less than 1 millisecond (ms). But a ping initiated from a computer in New York City to a computer in Los Angeles, over a cable Internet connection, might have a latency of 25 ms. This can be a very enlightening piece of the ping results.
You can also use ping to test whether a computer has TCP/IP installed properly, even if it isn’t wired to the network! To do this, use the ping 127.0.0.1 command for IPv4 and ping ::1 for IPv6. These IP addresses are known as loopback addresses; they are used for testing and are available on every host that has TCP/IP installed. They differ from the IP addresses we talked about previously (for example, 192.168.0.100) in that they work internally. Loopback ping commands essentially enable you to ping yourself, meaning you can test the local computer’s network connection without a valid IP configuration and without a physical connection to the network. Replies are simulated within the local computer; they prove if the network adapter and TCP/IP have been installed properly. However, it does not prove if TCP/IP has been configured properly for your particular network.
Note
You can also use the ping loopback and ping localhost commands, adding -4 for IPv4 and -6 for IPv6, but for testing, pinging the IP address is usually recommended.
ExamAlert
Know how to ping the local loopback IPv4 and IPv6 addresses.
You can also modify the way that ping works with switches. There are several, but three you should know for the exam are -t, -n, and -l:
• ping -t: This pings the host until the command is stopped. Remember, a host is any device or computer with an IP address. An example of this would be ping -t 192.168.0.1; the switch can go before or after the IP address. You will keep getting replies (or timeouts) until you stop the command by pressing Ctrl+C or by closing the Command Prompt. This is a great way to test cable connections. After running the command, you can plug and unplug cables and watch the screen to see which cables or ports are live. You can also use it to monitor a connection over a period of time, discerning whether there are many packet drops or whether the connection slows down at certain times.
• ping -n: This pings a host a specific number of times. For example, the syntax ping -n 20 192.168.0.1 would ping that host 20 times and then display the results. This can be a good baselining tool if you run it every day against a router or server and compare the results. (You would probably want to do a higher quantity than 20.)
• ping -l: This pings the host but you can specify the number of bytes per packet to be sent. If you look at the previous ping results, you can see that the default number of bytes is 32, but this can be increased to simulate real data. For example, ping -l 1500 192.168.0.1 would send four 1500-byte packets to the other host. This can also be beneficial when testing how a server, router, or other device reacts to larger packet sizes.
• ping -a: This resolves addresses to hostname. When pinging an IP address with -a, you also see the hostname associated with the IP address.
• ping -4: This forces the use of IPv4 and results in IPv4-based data. For example, in Windows, if you are running both IPv4 and IPv6 and type a command such as ping loopback, your results will by default be IPv6-based and might read Reply from ::1 (that is, if your system is working properly). But by adding the -4 option, you force the use of IPv4, so the command ping -4 loopback can result in Reply from 127.0.0.1. Try it!
• ping -6: This forces the use of IPv6 and results in IPv6-based data. For example, a ping -6 loopback will result in a reply from ::1.
ExamAlert
Know how to use the -t, -n, -l, -a, -4, and -6 switches with ping.
These switches can be combined as well, for example, ping -n 450 -l 1500 192.168.0.1 would send 450 pings, each 1500 bytes in size. To create a baseline, you could do this at a specific time every month, store the results, and then compare them to find possible deficiencies in performance of a server, router, and so on.
ARP
Address Resolution Protocol (ARP) resolves between IP addresses and MAC addresses, so that data communications can flow from the operating system to the physical network adapter. Every computer that runs TCP/IP has an ARP table, which is a cache of information including the IP address and MAC address of every other computer that the local system has been in contact with. The ARP command can be used to display or modify those ARP entries. If you were to type arp -a, you might get results similar to the following:
Interface: 192.168.41.202 --- 0x19 Internet Address Physical Address Type 192.168.41.1 30-b5-c2-b2-59-e6 dynamic 192.168.41.103 e8-4e-06-69-1a-99 dynamic 192.168.41.104 00-e0-4c-68-00-e9 dynamic 192.168.41.201 38-60-77-59-68-58 dynamic 192.168.41.255 ff-ff-ff-ff-ff-ff static 224.0.0.2 01-00-5e-00-00-02 static
The local system is 192.168.41.202. Every computer that it has connected to in the recent past is shown. For example, you can see that there has been a connection to 192.168.41.103; that computer’s corresponding MAC address is displayed as well. It is shown as a dynamic connection, meaning that it will time out at a specific point, usually when the computer restarts. However, you can have static connections as well, which won’t time out. Default broadcasts are set up this way automatically. Individual static connections can be added to the ARP table with the -s parameter. I personally use these for connections to servers, so as to reduce the amount of IP to MAC resolutions that are done from my system to the systems I administer the most.
Note
ARP is shown in the CompTIA A+ objectives acronym list. Know it!
Tracert
Tracert, short for trace route, builds on ping in that it send packets to destinations beyond the local computer’s network. It pings each router along the way between you and the final destination. Let’s say we ran the command tracert davidlprowse.com. An example of the tracert output follows:
Tracing route to davidlprowse.com [216.97.236.245] over a maximum of 30 hops: 1 6 ms 5 ms 5 ms bdl1.eas-ubr16.atweas.pa.cable.rcn.net [10.21.80.1] 2 10 ms 9 ms 9 ms vl4.aggr1.phdl.pa.rcn.net [208.59.252.1]
The tracert would continue for a dozen or more lines and end in the following:
18 86 ms 86 ms 86 ms unused-240-180-214.ixpres.com [216.240.180.214] 19 98 ms 96 ms 97 ms lwdc.dbo2.gi9-4.host1.23680.americanis.net [38.96.20.2] 20 97 ms 96 ms 96 ms zosma.lunarpages.com [216.97.236.245] Trace complete.
Note that there are three pings per line item measured in milliseconds (ms). Also note that every line item contains a router name and IP address. It starts by sailing through the various routers in our ISP, RCN.net. It ends at a server named zosma.lunarpages.com that hosts www.davidlprowse.com (as of the writing of this book). If you saw any asterisks in the place of the millisecond amounts, you might question whether the router is functioning properly. If the tracert stops altogether before saying Trace Complete, you would want to check your network documentation to find out which router it stopped at and/or make sure that the router is troubleshot by the appropriate personnel. As with ping, the -4 and the -6 options will force IPv4 and IPv6, respectively.
tracert /d will not resolve IP addresses to hostnames. So instead of seeing zosma.lunarpages.com on the last line, you would see only the IP address 216.97.236.245. Running numerical versions of commands can be faster because there is no name resolution to get in the way. Connecting directly by IP will always be faster than connecting by name.
Netstat
Moving on to another concept, netstat shows the network statistics for the local computer. The default command displays sessions to remote computers. In the following example, I connected to google.com and ran the netstat command. Output follows:
Active Connections TCP Music-Box:1395 8.15.228.165:https ESTABLISHED TCP Music-Box:1396 he-in-f101.google.com:https ESTABLISHED
This output shows that there are two established TCP sessions (they’re actually both to the same website) to google.com. In the local address column, we see our computer (Music-Box) and the outbound ports it uses to access the website (1395 and 1396). In the foreign address column, we see an IP address and the protocol used (https); in the second session, we see a hostname followed by the protocol (again https). The protocol used by google.com corresponds to port 443. This command can tell us a lot about our sessions (for example, whether a session times out or whether it closes completely). To see this information numerically, try using the -n switch. To see TCP and UDP sessions, use the -a switch. To see TCP and UDP in numeric format, use the -an switch. To include the executable name for each session shown, use the -nab switch.
Note
There are plenty of other netstat options, for example netstat -e which shows Ethernet statistics. For more information on netstat see the following link:
https://docs.microsoft.com/en-us/windows-server/administration/windows-commands/netstat
Nbtstat
Nbtstat displays network protocol statistics that use NetBIOS over TCP/IP connections. Nbtstat can be used to show the services running on the local computer or a remote computer. It calls this the name table. For example, you could find out what services are running, what the computer’s name is, and what network it is a part of by typing nbtstat -A 192.168.0.100 (or whatever your local IP is). The results would be similar to the following:
Computer1 <00> Unique Registered Workgroup <00> Group Registered Computer1 <20> Unique Registered
The computer and network names are easy to see: Computer1 and Workgroup. But also notice that there are numbers in alligators, such as <00> and <20>. These are the services mentioned previously. <00> is the workstation service, which is the service that allows your computer to redirect out to other systems to view shared resources. <20> is the server service that allows your computer to share resources with other systems.
The -a switch (lowercase a) shows the same name table but you invoke this information using the computer name instead of the IP address. Nbtstat has a variety of other switches that can display, purge, and reload name tables and sessions. Check out the other various switches by typing nbtstat /?.
Nslookup
Nslookup queries DNS servers to discover DNS details, including the IP address of hosts. For example, to find the IP address of davidlprowse.com, I would type nslookup davidlprowse.com. The resulting output should look something like this:
Non-authoritative answer: Name: davidlprowse.com Address: 216.97.236.245
So, from the output, we now know the IP address that corresponds to the domain name davidlprowse.com. Nslookup means name server lookup and can aid in finding DNS servers and DNS records in a domain as well. If the command nslookup is typed by itself, it brings the user into the nslookup shell. From here, several commands can be utilized; to find out more about these, type ? and press Enter. To exit the nslookup shell, type exit, press Ctrl+C, or press Ctrl+Break. The Linux equivalent of this is Dig, which can also be installed to Windows as part of the BIND tools: https://www.isc.org/downloads/.
Net
The net command is actually a collection of commands. You can use the net stop command to stop a service and the net start command to start a service from the Command Prompt. In networking, you might use the net view command to see which computers are currently available on the network or the net share command to share folders and for other users to view.
For the exam, you should know the types of net commands that enable you to view or create mapped network drives. To view any currently mapped network drives, simply type net use. To create a mapped network drive, use the following syntax:
net use x: \\computername\sharename
X: is the drive letter (in this case, X is a variable; you can use whatever drive letter you want, if it’s available, including X!). computername is the name of the remote host you want to connect to and sharename is the share that was created on that remote host.
There is a network share on another computer on my network called C$. The following syntax shows the command to connect to it and the resulting output:
net use f: \\Music-Box\c$ The command completed successfully.
In this example, we used F: as our drive letter; the computer we connected to is called Music-Box and the share is C$ (the default hidden share). For more information on the net command, type net /?. For more information on the net use command, type net use /?.
Note
See the following link for a video demonstrating how to use net share and net use between two systems:
https://dprocomputer.com/blog/?p=864
Another net command listed in the A+ objectives is net user. When typed by itself, that command will list the user accounts on the local computer. You can also create accounts from here with the net user /add %username% command; where %username% is a variable. For example, to create the user account dadams, you would type net user /add dadams. That creates a standard user account. In addition, you can activate or deactivate user accounts with the /active switch or delete accounts with the /delete switch. There is lots more; check out the command with /? for more information.
Note
Some commands are not listed in the main link I gave earlier in the chapter. For the time being, commands such as net user can be found at this link:
Advanced Commands
Let’s get into some advanced commands: tasklist, taskkill, dism, shutdown, gpupdate, and gpresult.
Tasklist
Tasklist shows all the processes running similar to the Processes tab of the Task Manager. Each process is assigned a Process Identification number or PID. These are assigned dynamically and won’t use the same number for an application twice. Tasklist also shows the memory usage of each process. An example of a process would be excel.exe (Microsoft Excel) or winword.exe (Microsoft Word).
Taskkill
Just as you can shut processes down in the Task Manager, you can also use the command line tool taskkill. Perhaps you run into a situation where certain applications or processes are frozen and you cannot open the Task Manager. If you can get to the Command Prompt, you can end these processes without restarting the computer. For example, if Microsoft Excel has stopped responding, you can find out its process ID with tasklist (say it was 4548) and close it by either typing taskkill /IM excel.exe or taskkill /PID 4548. Tasklist and taskkill are not available in the recovery environment Command Prompt in Windows 10/8/7.
ExamAlert
Use taskkill to shut down frozen processes from the Command Prompt.
DISM
The Deployment Image Servicing and Management (DISM) tool is used to scan and repair Windows operating system images, or prepare and service Windows operating system images for deployment.
First, let’s talk about basic scanning and repair of an image. Sometimes technicians will use DISM if the System File Checker (SFC) is not working properly. When SFC does repairs, it takes files from a Windows image. If the image is damaged, then SFC won’t function. So you can use the DISM utility to check the health of the image and potentially restore it to health if it is damaged. Before running DISM it is a good idea to backup files and create a restore point. Here’s an example of how you would check the health of the image:
dism /online /cleanup-image /checkhealth
This does a basic check to see if any corruption has occurred. For a more advanced analysis, replace /checkhealth with /scanhealth (which can take several minutes or more). If corruption exists, then you can attempt the same command but with the /restorehealth option. That will attempt to restore the image. If it cannot, you might need to provide a Windows image. (You can download Windows 10 from Microsoft’s website.) Once you have an image, you’ll need to mount it by double-clicking it (or right-clicking it) in File Explorer. Then, locate the actual image installation file. In Windows 10 that is X:\sources\install.esd, where X: is the mounted drive letter. Older versions of Windows use the install.wim file.Then run the same command as before, but point DISM to the image file, for example:
dism /online /cleanup-image /restorehealth /source:X:\sources\install.esd
Nowadays, it’s better to first try the Windows recovery environment options Reset your PC or Refresh your PC (depending on the version of Windows) before using DISM. DISM is really designed to prepare and service images for deployment to other systems. You can configure, append and apply images, but before you do so, they have to be mounted. Here’s an example of mounting an image for servicing:
dism.exe /Mount-Image /ImageFile:F:\images\install.esd /MountDir:G:\mounted-images\Win10-service
In this example, we’re using the Windows 10 install.esd file, but you can use other file types as well, such as install.wim for older versions of Windows, or .vhd and .vhdx files for virtual images. The current image file (install.esd) is stored in F:\images, and its mount point will be G:\mounted-images\Win10-service.
This tool comes in handy if you need to add or remove drivers or settings to and from the overall image, or to enable new Windows features. This way, you don’t have to create an entirely new image of Windows just because some additional desired features become available. After mounting the image, we can service the image with the DISM command and using parameters such as /Add-Driver /DriverName:”C:\drvlib\driver.inf”. It gets pretty in depth, and really at this point, it is Microsoft Windows Certification level content. For the A+, you should know what DISM is, and be able to spot DISM command usage.
Older versions of Windows will need an updated DISM tool which is included as part of the Windows ADK download that we mentioned earlier in the book.
Note
For more about DISM, see this link:
https://docs.microsoft.com/en-us/windows-hardware/manufacture/desktop/what-is-dism
Shutdown
The shutdown command is used to turn off the computer, restart it, send it to hibernate mode, log a person off, and so on. For example, if you want to shut down the computer after a short delay, you can type shutdown /s. For an immediate shutdown, you can type shutdown /p. The command can also be used programmatically to shut down systems at specific times while providing a pop-up window explaining the reason for the shutdown.
Gpupdate and Gpresult
Windows uses a set of policies to define rules that users and computers are effectively forced to follow. These policies can be viewed within the Local Group Policy Editor (Run > gpedit.msc) and a subset of that; the Local Security Policy (Run > secpol.msc). To properly work with these policies and tools, you should be running Windows Pro edition or higher.
You can also use commands to view and analyze that information. For example, the gpresult command which displays the Resultant Set of Policy (RSoP) information for a for a user and computer (it is designed for remote users/computers). Gpresult /R will display some basic information about the local computer, the user, and what policies are running. You can view this information for remote computers and users by using the /S switch and the name of the remote system: gpresult /S computername /R. “computername” is a variable, and is whatever the target system’s name is. To save the reported information, use the /x (for XML), or /h (for HTML) parameters.
In many cases, policy changes that were made in the Local Group Policy Editor or Local Security Policy won’t take effect until the admin logs off and logs back on. Enter the gpupdate command; which can be used by itself or by specifying a remote system. When run, it updates all policies that have been modified on the target computer, without having to logoff and log back on.
These commands can be run on Windows workstations or servers. But be very careful when using these. You have to be sure your policy changes are allowed, and you should consider scheduling them to run after work hours.
Note
For more information on gpresult and gpupdate, see the following links:
https://docs.microsoft.com/en-us/windows-server/administration/windows-commands/gpresult
https://docs.microsoft.com/en-us/windows-server/administration/windows-commands/gpupdate
ExamAlert
I know I just hit you with over two dozen commands, but try to memorize as many of them as you can! Try them on your computer, and write them down to force those little gray cells into action.
Cram Quiz
Answer these questions. The answers follow the last question. If you cannot answer these questions correctly, consider reading this section again until you can.
1. Which command can copy multiple files and entire directory trees?
![]() A. copy
A. copy
![]() B. cut
B. cut
![]() C. paste
C. paste
![]() D. robocopy
D. robocopy
2. Which command will determine if protected system files have been overwritten and replace those files with the original version?
![]() A. chkdsk
A. chkdsk
![]() B. msconfig
B. msconfig
![]() C. SFC
C. SFC
![]() D. xcopy
D. xcopy
3. Which command will show the path of routers between your computer and a web server?
![]() A. ping
A. ping
![]() B. ipconfig
B. ipconfig
![]() C. tracert
C. tracert
![]() D. nbtstat
D. nbtstat
4. You need to map a network drive to a share named data1 on a computer named Jupiter-Server. You want to use the J: drive letter. Which syntax should you use if you were to do this in the Command Prompt?
![]() A. net use J: \\Jupiter-Server\data1
A. net use J: \\Jupiter-Server\data1
![]() B. net use J \Jupiter-Server\data1
B. net use J \Jupiter-Server\data1
![]() C. net use Jupiter-Server\J\data1
C. net use Jupiter-Server\J\data1
![]() D. net use J: \Jupiter-Server\data1
D. net use J: \Jupiter-Server\data1
5. You have been tasked with bringing the policies of a Windows 10 computer up to date. You won’t be able to log off and back on, and you must use the Command Prompt. Which of the following tools should you use?
![]() A. shutdown
A. shutdown
![]() B. DISM
B. DISM
![]() C. gpupdate
C. gpupdate
![]() D. Local Security Policy
D. Local Security Policy
![]() E. nslookup
E. nslookup
6. A user’s WINWORD.EXE application is completely frozen. How can you determine the application’s process ID and then terminate the frozen application process? (Select the two best answers.)
![]() A. Use the net user command to identify the current PID of the application
A. Use the net user command to identify the current PID of the application
![]() B. Use the net user /delete command to terminate the frozen process ID
B. Use the net user /delete command to terminate the frozen process ID
![]() C. Run tasklist and record the process ID (PID)
C. Run tasklist and record the process ID (PID)
![]() D. Run taskkill /PID number
D. Run taskkill /PID number
Cram Quiz Answers
1. D. robocopy can copy an entire drive of information with just one command (including switches). Xcopy could also do the job, but robocopy takes the place of that.
2. C. SFC determines whether system files have been overwritten and replaces those files with the original versions. Chkdsk can check for errors and fix some errors but not when it concerns system files. msconfig is used to boot the system in a selective way and disable services and applications. Xcopy is used to copy large amounts of data exactly to a new location.
3. C. Tracert is used to run a trace between the local system and a remote destination. It shows all routers along the way. Ping is used to test connectivity to another system directly. Ipconfig will display the Internet Protocol configuration of the local computer. Nbtstat shows the name table cache and services running on the system.
4. A. You should use this syntax: net use J: \\Jupiter-Server\Data1. All other answers are incorrect. The Universal Naming Convention (UNC) is \\computername\sharename.
5. C. You should use gpupdate to bring the Windows 10 policies up to date. It can do this without the need for logging off and on again. The shutdown command is used to turn off or restart a computer. DISM is used to mount and service Windows image files. The Local Security Policy is where you can go to modify many policy settings (such as the password policy), but it is graphical. To enforce the changes made in the Local Security Policy, use the gpupdate command. Nslookup is used to query DNS servers to find out more information about hosts or domains, for instance the IP address of a host computer on the Internet.
6. C and D. Tasklist shows all the processes running and each process is assigned a process identification number (PID). Run tasklist and record the PID of the frozen WINWORD.EXE application first. (Quick tip: to sort the results alphabetically, type tasklist | sort. The pipe ‘|’ symbol shares the backslash key.) Then run taskkill /PID number of the WINWORD.EXE application to terminate the frozen app. A and B are invalid options as worded in the answer choices. The net user command will list the user accounts on the computer and net user with the /delete switch will remove a user account. But, listing and removing user accounts will not help you terminate a running process or application.