

Secure your identity and your computer
Now that you’ve gotten your feet wet with e-mail and the Internet, I want to mention some precautions to take when venturing further on the information superhighway. As an overall guide, use the same instincts you use in your everyday life when you’re on the Internet. If an e-mail you receive seems fishy, assume it is. If you’re not comfortable giving your credit card information online, don’t. Let your gut be the judge and caution be your guide, and all will be fine.
Settle yourself into a nice comfortable chair before you read on, and remember the scenarios below are possibilities, not probabilities. Do not be intimidated by the information; become empowered by it.
Before the advent of personal computers, when someone mentioned a hacker it was either someone who chopped things in to pieces or had a terrible cough. My introduction to a computer hacker was in the movie War Games, where Matthew Broderick plays a teenage hacker who unwittingly hacks into (i.e., gains access to) the military’s computer system. In computer-speak, a hacker is a highly skilled programmer. The problem is that those skills can be used with good or bad intentions. The connotation of a hacker is usually negative and refers to someone who breaks through security codes on the computer to access otherwise protected information. Why would someone choose to hack? Some hack to gain access to a cache of credit card numbers or to gather personal data from a computer. But others hack just because they can. In the computer geek community there is a prestige to being able to break a code. Hackers don’t necessarily do any damage, but they make their mark in the hackers’ hall of fame.
“I love the idea of having access to so many different things on the Internet. I just want to be assured that no one in turn has access to my personal information.”
—Cindy
What can you do to protect your computer from hackers? Your first line of defense is a firewall. Think of your computer’s relationship to the Internet as a swinging door. It swings open when you send a request out (i.e., ask to connect to a website) and it swings open again when you receive a response to your request (i.e., you connect to the website). At both moments when the door is open, the computer is vulnerable. Uninvited guests can sneak in and view the contents of your computer or leave behind a program that may make your computer susceptible to junk mail or worse. With a firewall, these points of entry and exit are protected from intruders. (Imagine your front door protected by a wall of fire.) Chances are very good that your computer came with a firewall preinstalled. Let’s see if it is activated.
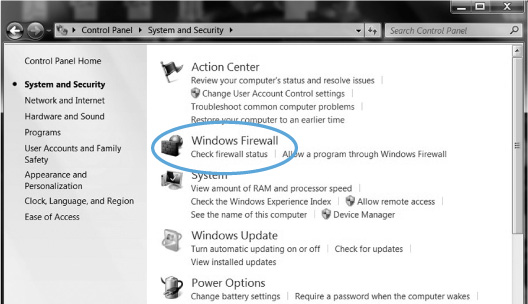
• Windows Security Center. Here’s where you can see the status of your computer’s firewall.
To check for a firewall on your computer if you have a PC:
• Click on Start or  in the bottom left of your screen.
in the bottom left of your screen.
• Click on Control Panel  .
.
• Double-click on System and Security  .
.
• Click on Check Firewall Status.
• If your firewall indicates that it is ON, you are protected. If it indicates that it is OFF, click on the Windows firewall icon  . In the General options section, click the bullet next to the ON option to active your firewall.
. In the General options section, click the bullet next to the ON option to active your firewall.
To check for a firewall on your computer if you have a Mac:
• Click on  in top left corner.
in top left corner.
• Click on System Preferences.
• Single-click on Security  .
.
• Click on Firewall tab.
• Click on Start to enable your firewall. Click on Advanced to see more options.
• You may need to click the lock in the bottom left and type a password, if a password was created at setup.
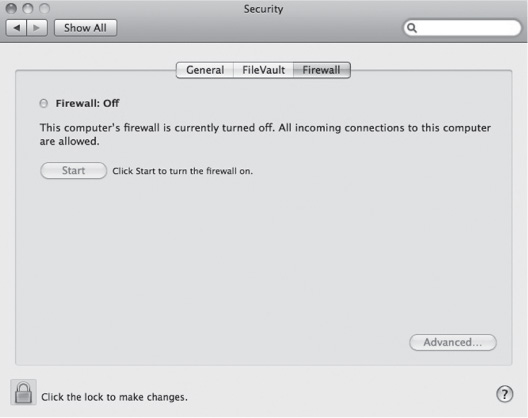
• Mac Sharing window with Firewall. Here’s where you can see the status of your computer’s firewall.
Here you can read about firewalls and activate the one that came preinstalled on your computer. One thing to remember: If at a later date you decide to add software to your computer, the firewall may have to be turned off during the installation process to avoid interference.
Another preventive measure to take against hackers is to ask the provider of your high-speed connection to the Internet whether they offer any protection in the way of a router. A router is a device that also thwarts hackers by scrambling information needed to access your computer. If your ISP doesn’t offer a router, you can purchase one on your own. If you use a dial-up to connect to the Internet, chances are your computer will be below a hacker’s radar because your Internet connection will be slow.
With these protections in place, it’s unlikely that a trespasser will gain access to your computer but not impossible. Therefore it is wise not to store certain information on your computer. For example, do not have your Social Security number, bank PIN (Personal Identification Number), or any other passwords recorded on your computer. If you can’t think of any place to store your password information other than your computer, at least name the document after your first pet or your childhood hero or the person in the world you trust the most—anything other than “passwords” as the file name.
• A router can protect your computer from hackers.
Speaking of passwords, there are some basic do’s and don’ts when choosing a password. Most passwords can be cracked in a matter of minutes. Let’s see… your birth date or that of someone in your immediate family, a family member’s name, your anniversary, some configuration of your street address. Am I getting close? Please don’t make it that easy for someone who doesn’t respect your privacy as much as I do.
Most important, as I mentioned on page 171, your bank or ATM PIN should not be the same as your e-mail password. If someone were to hack the passwords of your e-mail provider, they could then gain access to your bank account. Instead, have your bank PIN be an exclusive password for the bank and nothing else.

When choosing a password for your e-mail or a website, assume the password must be at least six characters in length. It’s more difficult to guess a password consisting of a combination of letters and numbers. Even better, because passwords are often case sensitive, throw in a couple of capital letters to up the ante. The trick with any of these choices, however, is you need to remember your password. Write down the password as soon as you choose it. Do not rely on your memory.
So, what to use to inspire your choice of a random sequence of letters and numbers? Think of something not in public records about yourself but that you’ll never forget.
EJNJ18 = my siblings’ and parents’ first initials and my age when I moved out of the house.
Elephant3 = my favorite stuffed toy and the number of wisdom teeth I had removed.
7haRRiet = number of days in the week and my favorite children’s book character.
Starting to get the picture?
Identity theft is not as attributable to computer use as we are led to believe. Most identity theft occurs the old-fashioned way—by sleight of hand. Your purse or wallet containing vital information about you is stolen. Your trash is rummaged through, revealing your credit card numbers and more. You give information over the phone to someone who sounds legitimate but is not. Here are ways you can protect yourself…

The key to stealing someone’s identity is his or her Social Security number. You should never carry your Social Security number in your wallet. For some, doing so may be an old habit, but it’s time to break the habit. Your full name, date of birth, and your mother’s maiden name are all public record. With a little investigation, such information can be uncovered. But your Social Security number, which is often used by financial institutions as identification, is not public record. Give your Social Security number to a thief, and identity theft becomes a cakewalk. Your Social Security number may appear on your health insurance card. If it does, contact your insurance company and have them reassign a nine-digit number that in no way resembles your Social Security number. You will not be the first person to call and ask that this be done. It is now common practice.
Make a copy of the front and back of your driver’s license and your credit cards. Keep the photocopies in a safe place. If your wallet is stolen this information will facilitate the calls you should make immediately to cancel your cards. File a police report. This reinforces the validity of your claim of loss to the credit card companies. Call credit-reporting organizations to place a fraud alert on your name and Social Security number.
Here are some phone numbers to get you started:
Equifax: 1-800-525-6285
Experian: 1-888-397-3742
Trans Union: 1-800-680-7289
Social Security Administration (fraud line): 1-800-269-0271
It’s also a good idea to check your credit report annually to be sure you’re not carrying a bad report due to fraud or an error. Visit annualcreditreport.com for a free credit report.

When the time comes to throw away expired credit cards, always cut along the magnetic strip. The magnetic strip, when left intact, contains all the pertinent information for that credit card, making it way too easy for a thief. Then cut up the rest of the card into small pieces and distribute them over time into different waste bins. Without sounding too paranoid, the same should be done with any correspondence revealing your credit card or Social Security numbers. Maybe this is the year to ask Santa for a paper shredder.
What about the seemingly lovely person who calls you at home to verify information for your own protection or to enter you in a contest or to send you a promotional gift? Never, never, never release personal information over the phone. You have no idea who is really at the other end of the line. Have the caller give you the information to confirm, or, better yet, ask the caller to give you their number so you can call back to confirm if it is a legitimate company placing the call. You will stop them in their tracks.
None of the scenarios just described involved a computer at all, but somehow computers receive the blame for identity theft. However, be aware of dangers when surfing the net.
Whenever you want to take a break from all of this doom and gloom, do. Then come back after you’ve seen the silver lining on the cloud to finish up this precautionary tale.

Glad you returned. I had faith you would. Now let’s learn about the world of phishing. And, no, I didn’t spell that wrong. What makes phishing truly clever and deceitful is that the sender’s e-mail address will read as though it came from your bank and if you click through to the website, it will be designed to look just like your bank’s website.
• Here’s an example of an e-mail that looks legitimate but is actually phishing.
So, what are you to do? Know that no bank and any other financial institution will ever ask you to confirm critical information through e-mail. It just isn’t secure enough. Banks try their best to protect their customer’s information. They know e-mail is not the place for such sensitive content.
If you think you’ve received a phishing e-mail you can forward it to reportphishing@antiphishing.org. They will review the e-mail and the links and post it on their website to warn others.
Is your home mailbox flooded with mail-order catalogs? How do you think the catalog companies got hold of your mailing address? Yup. You ordered a little something from one catalog, and that catalog in turn sold your mailing address to another and another and another. Suddenly, yours is the most popular mailbox in town.
Spam is electronic junk mail and now accounts for half of all e-mail. The proliferation of spam occurs in the same way as junk snail mail. However, with e-mail you actually have an option not offered by the U.S. Postal Service. When you create your primary e-mail address, you can also create a second e-mail identity to use when you shop online, join an online newsletter, or in any other instance where you’re asked for your e-mail address by a commercial enterprise. You’ll only give your primary e-mail address to friends, family, and business associates. This will significantly decrease the spam received at your primary e-mail address. For example,
janedoe@yahoo.com = address exclusively for friends and family
janedshopping@yahoo.com = address for shopping, newsletters, etc.
Beware that some spammers are so stealthy, spam can appear in your inbox with your e-mail address as the sender. Not to worry. Your e-mail address has not been hijacked. The spammers disguised their information targeting you specifically to entice you to open the e-mail. Once you’ve opened the e-mail and clicked through to whatever is being pitched, your e-mail address is certain to be sold to other mailing lists. Rule of thumb: If you don’t recognize the sender’s e-mail address (or it is suspicious) and the subject is not something very specific to you, do not open the e-mail. Don’t let your curiosity get the better of you; there is no satisfaction found in spam. Promptly trash the e-mail.
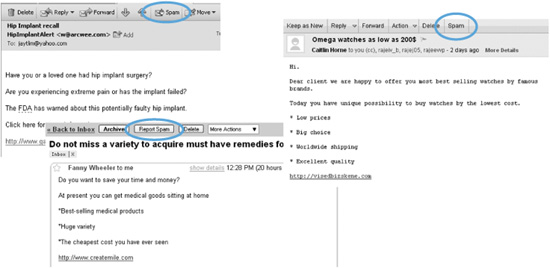
• Click to report spam. Your e-mail service will be notified that you have received spam.
• If an e-mail you wanted to receive has been sent to the Spam or Junk folder in error, you can correct the mistake.
Most e-mail providers now have filters to divert spam into a junk or bulk mail folder instead of your inbox. The targeted e-mail remains in the folder for a limited time until your e-mail company deletes it. Unfortunately, these filters cannot always identify what is junk and what is not. Junk mail may still make its way into your inbox, and sometimes an e-mail you wanted to receive is misdirected to the junk folder. Your e-mail service offers a method to redirect the e-mail from the Junk folder to your Inbox. Look at the Menu bar for options to Move or Not Junk Mail or some other option to redirect the e-mail to the intended folder. To be sure you receive e-mail from people you want, add their e-mail address to your e-mail address book.
“I used to get all hung up about the names that have been given to different things on a computer like bytes, hertz, and cookies. Now I don’t give it a thought and I just have fun on my computer.”
—Paul
Like Hansel and Gretel, who left a trail of bread crumbs to follow on their way back home, cookies leave a trail for a website to find its way back to information about your activities during previous visits to the site. A cookie is actually a file left behind on your computer by a website that you’ve visited. There are advantages to a website leaving cookies behind. It allows a site to personalize your Internet experience. Here’s an example: You visit Amazon (amazon.com) and buy an Agatha Christie murder mystery. The next time you open Amazon’s website, the home page says, “Hello, (your name). We have recommendations for you.” It’s like a doorman remembering your name or a salesclerk who remembers your favorite perfume. It was a cookie placed on your computer when you bought Agatha’s book that provided Amazon with this information for your next visit.
If you choose to bank online, more often than not the ID the bank uses to identify you will be your account number. Rather than you typing your account number every time you visit the site, your bank places a cookie on your computer so your bank ID will automatically be remembered. For security purposes, your password will be required every time you visit the site, but that is as it should be.
Cookies do not allow access to any other information on your computer besides the data the website has chosen to save. No website can view another website’s cookies. A cookie is all about recognizing you and your preferences or past history with a certain website.
The only threat posed by cookies is they enable an unwelcome visitor to your computer to view information now stored on your computer by the cookies. Frankly, my shopping habits aren’t anything anyone wants to know about, but your cookies may contain more significant information—possibly your credit card numbers. I don’t choose to allow websites to store my credit card information. If you do allow for that, the information will be stored in a cookie. If you want to delete the cookies on your computer, you can do so without harm to your computer. The only downside to cleaning out your cookies is some websites that previously recognized you won’t anymore. You’ll just have to introduce yourself all over again. At that point a new cookie will be placed on your computer so you’ll be recognized on your next visit to that website.
When you choose to delete cookies from your computer, you could access the folder they are stored in and pick and choose what to delete, but it’s difficult to always recognize what website the cookie is for and what information it contains. I prefer to delete them all and reintroduce myself to websites. (Because of the possible deletion of cookies after registration to a site, I print a document with all my registration information—website, user name or ID, and password—in case I need to refer to it later.) Let’s remove the cookies accumulated on your computer.
If you use Firefox to access the Internet, follow the steps below in the Click and Go to delete cookies. If you use Internet Explorer (the big blue E icon) to access the Internet, follow the steps at top right in the Click and Go to delete Cookies. If you use Safari to access the Internet, follow the steps at bottom right in the Click and Go to delete cookies.
While you’re in the Internet Options window of Internet Explorer there are other points of interest. Do you see above Delete Cookies there is Delete Files? The files referred to are temporary files allowing a website previously visited to open up faster on your computer. Over time the contents of this folder can slow down the computer. If your computer operates more slowly than in the past, access the Internet Options window and click on Delete Files. Wait for the hourglass to go away before continuing on with your next computer task. You may notice things run a bit faster after you’ve deleted those files. Other computer housecleaning tips can be found in Chapter 25, “Troubleshooting.”
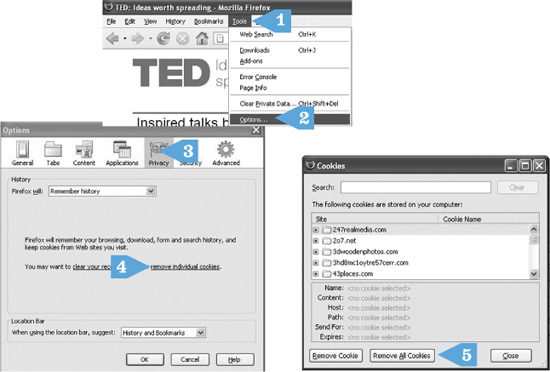
CLICK AND GO
1. Click Tools.
2. Click Options.
3. Click Privacy.
4. Click Remove Individual Cookies.
5. Click Remove All Cookies.
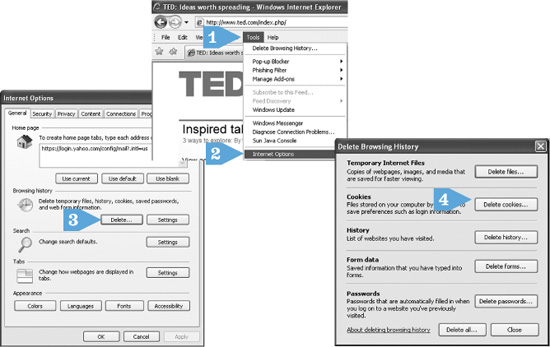
• Here is how to delete cookies with Firefox.
CLICK AND GO
1. Click Tools.
2. Click Internet Options.
3. Click Delete.
4. Click Delete Cookies.
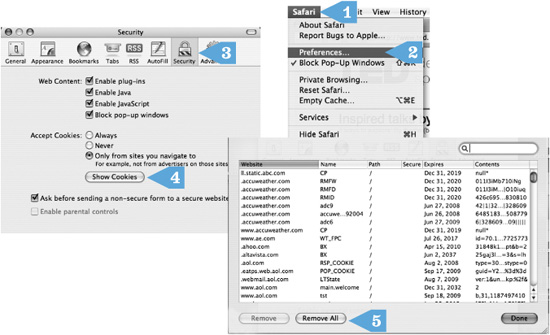
• Here is how to delete cookies with Internet Explorer.
CLICK AND GO
1. Click Safari.
2. Click Preferences.
3. Click Security.
4. Click Show Cookies.
5. Click Remove All.
Below the Temporary Internet Files portion of the window you’ll see History. History is where the computer stores the websites you’ve visited in the past. This is all well and good unless you’ve traveled somewhere on the Internet you’d rather not have others know about. No confessions necessary. If you don’t want someone to see the websites you’ve visited, click on Clear History. This won’t protect you if the Feds confiscate your computer and want to investigate past behavior, but it will prevent a curious spouse or grandchild from tracking your Internet activities.
Don’t forget the old-fashioned techniques used by would-be thieves… their keen eyes and sticky fingers. When typing a password in a public place, try to have all of your fingers in motion over the keys to make it more difficult for someone to see what you actually type. If you have a laptop and you’re in a public space, in order to protect the information on it from curious eyes, do not walk away from your computer when it is on. Frankly, when in a public place I wouldn’t walk away from my laptop at any time for fear that someone would steal it and make it their own.
What a terrible note to end on! But if you learn the potential pitfalls, it’s easier to avoid them. There was also a lot of computer jargon to absorb in this chapter. Don’t worry. I don’t expect you to remember it all! You can always come back and review. Why not treat yourself to a few cookies (the edible kind) and a cooling drink and take a break before you journey to the next chapter?
Q: Is the Internet safe?
A: Yes. It is as safe as any other place you visit in the “real” world. You just have to use the same precautions and common sense when you’re visiting the Internet as you would traveling someplace you’ve never been before.
A: Spyware is software installed on your computer without your consent. Spyware can monitor your computer behavior, sending that information back to advertisers, along with diverting you from a desired website to another. One way to avoid spyware is not to download (or add) any programs onto your computer without being sure of the source and certain that you need the software offered. You can install anti-spyware software on your computer. This is a topic best dealt with by asking friends or relatives in the know or a computer professional who can help install anti-spyware software and/or help remove any spyware that was found on your computer.
Q: I use a laptop computer, not a desktop. Do I need to connect wirelessly?
A: Not necessarily. You can connect to the Internet using an Ethernet cable, as you would with most desktops. (An Ethernet cable looks like a phone cable, but the cable itself is a bit fatter and the end you plug into the computer is wider.) The only advantage of a wireless connection is that you could work on your laptop anywhere in your home and be able to connect to the Internet without a cable.
Q: How will I know if someone has accessed my computer without my permission?
A: Unfortunately, you won’t. It will only be after they have used that information (e.g., shopped with your credit card) that you will know. Unless they are stupid enough to change settings on your computer so it will appear different to you, but that would be like leaving their glove in your home after they’ve broken in. If you are suspicious that your computer has been hacked, call in a tech support person to check things out for you.
Q: Who do I contact if I think my computer has been broken into?
A: If you have any evidence that your credit card number(s) or your identity has been in any way jeopardized, call the police and file a report (they may want to see the computer) and call the numbers listed on page 220 in this chapter. Bring your computer to a technical support person and have them go over the computer to see what evidence of intrusion they can find. While they have your computer, be sure to have them take the necessary steps to make it as secure as possible.
Q: I hired someone to hook up my printer. He insisted on turning off my firewall while doing the installation. Was he legit?
A: Yes. Sometimes when installing (or copying) new software onto a computer it is necessary to turn off the firewall. Just be sure to turn it back on after installation (see page 216).
Q: What can I do to let people know that the e-mail I’m sending is from me and not someone pretending to be me?
A: First of all, know that getting your e-mail address hijacked by someone else is far from a regular occurrence. That said, the subject and the body of every e-mail should be specific and personal. Don’t send an e-mail with the subject “hi” or “thinking of you.” Instead, type “enjoyed seeing you at Yolanda’s birthday” or “how’s life with the new puppy?” I know that an e-mail is from my mom because she always signs off “L, M” = Love, Mom. I always sign off “ML, P” = Much Love, Peach. It’s our code, which was secret until now… oops!