 901: 1.7 Compare and contrast various PC connection interfaces, their characteristics, and purpose
901: 1.7 Compare and contrast various PC connection interfaces, their characteristics, and purposeCERTIFICATION OBJECTIVES
 901: 1.7 Compare and contrast various PC connection interfaces, their characteristics, and purpose
901: 1.7 Compare and contrast various PC connection interfaces, their characteristics, and purpose
 901: 2.1 Identify the various types of network cables and connectors
901: 2.1 Identify the various types of network cables and connectors
 901: 2.2 Compare and contrast the characteristics of connectors and cabling
901: 2.2 Compare and contrast the characteristics of connectors and cabling
 901: 2.3 Explain the properties and characteristics of TCP/IP
901: 2.3 Explain the properties and characteristics of TCP/IP
 901: 2.4 Explain common TCP and UDP ports, protocols, and their purpose
901: 2.4 Explain common TCP and UDP ports, protocols, and their purpose
 901: 2.5 Compare and contrast Wi-Fi networking standards and encryption types
901: 2.5 Compare and contrast Wi-Fi networking standards and encryption types
 901: 2.7 Compare and contrast Internet connection types, network types, and their features
901: 2.7 Compare and contrast Internet connection types, network types, and their features
 901: 2.8 Compare and contrast network architecture devices, their functions, and features
901: 2.8 Compare and contrast network architecture devices, their functions, and features
 Two-Minute Drill
Two-Minute Drill
Q&A Self Test
Computer networks provide users with the ability to share files, printers, resources, and e-mail globally. Networks have become so important that they provide the basis for nearly all business transactions.
Obviously, a discussion of the full spectrum of network details and specifications is too broad in scope to be contained in this book. However, as a computer technician, you should be aware of basic networking concepts so you can troubleshoot minor problems on established networks. This chapter focuses on basic concepts of physical networks; Chapter 14 guides you through simple small office/home office (SOHO) network installation, and Chapter 16 provides the basis for troubleshooting common network problems.
CERTIFICATION OBJECTIVES
 901: 1.7 Compare and contrast various PC connection interfaces, their characteristics, and purpose
901: 1.7 Compare and contrast various PC connection interfaces, their characteristics, and purpose
 901: 2.5 Compare and contrast Wi-Fi networking standards and encryption types
901: 2.5 Compare and contrast Wi-Fi networking standards and encryption types
 901: 2.7 Compare and contrast Internet connection types, network types, and their features
901: 2.7 Compare and contrast Internet connection types, network types, and their features
This section begins by describing the types of networks based on how they are connected (topology) and based on the area they service (LAN, WAN, PAN, and MAN), along with wide area network (WAN) technologies and connection types, as required by CompTIA A+ 901 exam objective 2.7. The discussion of the wireless networking standards contains the information as required by CompTIA A+ 901 exam objective 2.5, but a portion of that objective, Encryption types, is covered in Chapter 15. CompTIA A+ 901 exam objective 1.7 is included here only for the brief explanation of interfaces used in a PAN, such as infrared and Bluetooth.
For a computer professional working with PCs, the networked computer is the norm, not the exception. A computer not connected to a network is a standalone computer, and this has become a nearly extinct species, as more and more PCs network together—even within homes.
To understand networks, you must first be familiar with basic network performance and classifications, which describe networks by speed, geography, and scale, beginning with the smallest networks up to globe-spanning ones.
We classify networks by geographic area types, and there are specific technologies designed for each of them. Network builders select these technologies for the capabilities that match the distance needs of the network.
You may have your own personal area network (PAN), if you have devices such as smartphones, tablets, or printers that communicate with each other and/or your desktop computer. A PAN may use a wired connection, such as Universal Serial Bus (USB) or FireWire, or it may communicate wirelessly using one of the standards developed for short-range communications, such as Infrared (IR), also known as Infrared Data Association (IrDA), or Bluetooth.
Infrared (IR) is not a popular technology anymore, but you may still encounter it on old laptops or peripherals, such as old wireless keyboards and mice. IR-enabled devices can communicate with each other over a very short distance (1 meter), and because IR uses an infrared light, the communicating devices must maintain line-of-sight between the IR ports on the two devices.

As you learned in Chapter 7, Bluetooth uses radio waves, which do not require line-of-sight, but the signal can be disrupted by physical barriers as well as interference from other signals. The Bluetooth standard describes three classes, with power requirements and distance limits. The Bluetooth standard commonly used with computer peripherals and mobile devices is Class 3, limited to a distance of 1 meter, or Class 2, limited to about 10 meters.
A local area network (LAN) is a network that covers a much larger area than a PAN, such as a building, home, office, or campus. Typically, distances measure in hundreds of meters. A LAN may share resources such as printers, files, or other items. LANs operate very rapidly, with speeds measured in megabits or gigabits per second, and have become extremely cost effective. While there are many LAN technologies, the two most widely used in SOHO network installations are Ethernet and several Wi-Fi standards.
Most wired LANs use hardware based on standards developed by the 902.3 subcommittee of the Institute of Electrical and Electronics Engineers (IEEE). Ethernet is the word created to describe the earliest of these networks, and we continue to use this term, although there really are many Ethernet standards—all under the 902.3 umbrella. These standards define, among other things, how computer data is broken down into small chunks, prepared, and packaged before the Ethernet network adapter (also known as a network interface card, or NIC) places it on the Ethernet network as a chunk of data called an Ethernet frame. Ethernet standards also define the hardware and media that control and carry the data signals.
Early implementations of Ethernet were half-duplex, meaning that while data could travel in either direction, it could only travel in one direction at a time. Later implementations are capable of full-duplex communication, in which the signals travel in both directions simultaneously, but they usually auto-negotiate and automatically use either half- or full-duplex, depending on what is in use on the network. Networks today are usually full-duplex, unless a network has very old hardware.
Depending on the exact implementation, Ethernet supports a variety of transmission speeds, media, and distances. All Ethernet standards using copper cabling, either unshielded twisted-pair (UTP) or shielded twisted-pair (STP), support a maximum cable length of 100 meters between a NIC and a hub or switch. Learn more about hubs and switches later in this chapter, in the section “Devices for Connecting to LANs and the Internet.” The maximum distances for fiber-optic cable (a.k.a. fiber) installations vary, depending on the exact cable type in use. Here is a summary of several Ethernet levels and their speeds:
 10BaseT/Ethernet For many years the most widely used implementation, 10BaseT transfers data at 10 Mbps over UTP copper cabling in half-duplex mode with a maximum cable length of 100 meters.
10BaseT/Ethernet For many years the most widely used implementation, 10BaseT transfers data at 10 Mbps over UTP copper cabling in half-duplex mode with a maximum cable length of 100 meters.
 100BaseT/Fast Ethernet Using the same cabling as 10BaseT, 100BaseT or Fast Ethernet operates at 100 Mbps and uses different NICs, many of which are also capable of the lower Ethernet speeds, auto-detecting the speed of the network and working at whichever speed is in use. Early 100BaseT NICs were half-duplex, but later ones support full-duplex.
100BaseT/Fast Ethernet Using the same cabling as 10BaseT, 100BaseT or Fast Ethernet operates at 100 Mbps and uses different NICs, many of which are also capable of the lower Ethernet speeds, auto-detecting the speed of the network and working at whichever speed is in use. Early 100BaseT NICs were half-duplex, but later ones support full-duplex.
 1000BaseT/Gigabit Ethernet Supporting data transfer rates of 1 Gbps over UTP, there are several Gigabit Ethernet standards, but the most common one is 1000BaseT. It is capable of full-duplex operation using four-pair UTP cable with standard RJ-45 connectors (see the description of cable later in “Transmission Medium”).
1000BaseT/Gigabit Ethernet Supporting data transfer rates of 1 Gbps over UTP, there are several Gigabit Ethernet standards, but the most common one is 1000BaseT. It is capable of full-duplex operation using four-pair UTP cable with standard RJ-45 connectors (see the description of cable later in “Transmission Medium”).
 10 GbE/10-Gigabit Ethernet WANS and some high-end LANs use one of the many standards of 10-Gigabit Ethernet, which operates at speeds of up to 10 Gbps in full-duplex mode over either copper (10GBaseT) or fiber. There are many 10-Gigabit Ethernet fiber standards for both WANs and LANS, and we will only briefly mention two of them here. The 10GBaseSR standard is one of the standards used for fiber-optic LANs, whereas 10GBaseSW is one of the standards used for fiber-optic WANs.
10 GbE/10-Gigabit Ethernet WANS and some high-end LANs use one of the many standards of 10-Gigabit Ethernet, which operates at speeds of up to 10 Gbps in full-duplex mode over either copper (10GBaseT) or fiber. There are many 10-Gigabit Ethernet fiber standards for both WANs and LANS, and we will only briefly mention two of them here. The 10GBaseSR standard is one of the standards used for fiber-optic LANs, whereas 10GBaseSW is one of the standards used for fiber-optic WANs.
Wireless LAN (WLAN) communication (local area networking using radio frequency, or RF) is very popular. The most common wireless LAN implementations are based on the IEEE 802.11 group of standards, also called Wireless Fidelity (Wi-Fi). There are several 802.11 standards, and more were proposed. These wireless standards use either 2.4 GHz or 5 GHz frequencies to communicate between systems. The range on these systems is relatively short, but they offer the advantage of not requiring cable for network connections.
In many homes and businesses, Wi-Fi networks give users access to the Internet. In these instances, the wireless communications network uses a wireless router connected to a broadband connection, such as a cable modem or digital subscriber line (DSL) modem.
Wi-Fi, long a standard feature on laptops, is also available on most smartphones and tablets. In large corporations, users with wireless-enabled laptops and other devices can move around the campus and continue to connect to the corporate network through a Wi-Fi network that connects to the corporate wired network. And many public places, such as libraries, restaurants, and other business, offer free or pay access to Wi-Fi networks that connect to broadband Internet services. Such a point of connection to the Internet through a Wi-Fi network is called a hotspot. On an interesting twist on this concept, cellular providers and manufacturers of cellular-enabled mobile devices have cooperated to provide a newer type of service called a mobile hotspot. You can create a mobile hotspot by connecting to the Internet with your smartphone’s cellular service, and then using the smartphone’s Wi-Fi connectivity to allow other nearby Wi-Fi-enabled devices to share that Internet connection.
Here is a brief description of several 802.11 standards and their features:
 802.11a The 802.11a standard was developed by the IEEE at the same time as the slower 802.11b standard, but the “a” standard was more expensive to implement. Manufacturers, therefore, tended to make 802.11b devices. 802.11a uses the 5 GHz band, which makes 802.11a devices incompatible with 802.11b and the subsequent 802.11g devices. Because 802.11a devices do not provide downward compatibility with existing equipment using the 802.11b or newer 802.11g standards, they are seldom used. An 802.11a network has speeds up to 54 Mbps with a range of up to 150 feet.
802.11a The 802.11a standard was developed by the IEEE at the same time as the slower 802.11b standard, but the “a” standard was more expensive to implement. Manufacturers, therefore, tended to make 802.11b devices. 802.11a uses the 5 GHz band, which makes 802.11a devices incompatible with 802.11b and the subsequent 802.11g devices. Because 802.11a devices do not provide downward compatibility with existing equipment using the 802.11b or newer 802.11g standards, they are seldom used. An 802.11a network has speeds up to 54 Mbps with a range of up to 150 feet.
 802.11b The 802.11b standard was the first widely popular version of Wi-Fi, with a speed of 11 Mbps and a range of up to 300 feet. Operating in the 2.4 GHz band that is also used by other noncomputer devices such as cordless phones and household appliances, these devices are vulnerable to interference if positioned near another device using the same portion of the radio spectrum.
802.11b The 802.11b standard was the first widely popular version of Wi-Fi, with a speed of 11 Mbps and a range of up to 300 feet. Operating in the 2.4 GHz band that is also used by other noncomputer devices such as cordless phones and household appliances, these devices are vulnerable to interference if positioned near another device using the same portion of the radio spectrum.
 802.11g 802.11g replaced 802.11b. With a speed of up to 54 Mbps and a range of up to 300 feet, it also uses the 2.4 GHz radio band. 802.11g devices are normally downward compatible with 802.11b devices, although the reverse is not true.
802.11g 802.11g replaced 802.11b. With a speed of up to 54 Mbps and a range of up to 300 feet, it also uses the 2.4 GHz radio band. 802.11g devices are normally downward compatible with 802.11b devices, although the reverse is not true.
 802.11n The 802.11n standard has speeds of up to 100+ Mbps and a maximum range of up to 600 feet. The standard defines speeds of up to 600 Mbps, which actual implementations do not achieve. MIMO (multiple input/multiple output) makes 802.11n speeds possible using multiple antennas to send and receive digital data in simultaneous radio streams that increase performance.
802.11n The 802.11n standard has speeds of up to 100+ Mbps and a maximum range of up to 600 feet. The standard defines speeds of up to 600 Mbps, which actual implementations do not achieve. MIMO (multiple input/multiple output) makes 802.11n speeds possible using multiple antennas to send and receive digital data in simultaneous radio streams that increase performance.
 802.11ac The 802.11ac standard has multistation throughput of 1 Gbps, and a single-link throughput of 500 Mbps. It accomplishes these higher speeds by using a wider RF bandwidth than 802.11n, more MIMO streams (up to eight), and high-density modulation.
802.11ac The 802.11ac standard has multistation throughput of 1 Gbps, and a single-link throughput of 500 Mbps. It accomplishes these higher speeds by using a wider RF bandwidth than 802.11n, more MIMO streams (up to eight), and high-density modulation.
When considering a wireless network, determining its speed and range can be nebulous at best. In spite of the maximums defined by the standards, many factors affect both speed and range. First, there is the limit of the standard, and then there is the distance between the wireless-enabled computer and the wireless access point (WAP), a network connection device at the core of a wireless network. Finally, there is the issue of interference, which can result from other wireless device signals operating in the same band or from physical barriers to the signals. In Chapter 14, you will learn about installing a WLAN to avoid interference and devices that will extend the range of the signals. You will also learn about the configuration options for wireless networks, including the use of identifiers for the wireless devices, secure encryption settings, and settings for keeping intruders out.

A metropolitan area network (MAN) is a network that covers a metropolitan area, connecting various networks together using a shared community network, and often providing WAN connections to the Internet. A MAN usually runs over high-speed fiber-optic cable operating in the gigabits-per-second range. Synchronous Optical Networking (SONET) is one long-established fiber-optic WAN technology. Although people tend to be less aware of MANs, they nonetheless exist. In fact, a MAN may well be somewhere between you and the Internet.

A wide area network (WAN) can cover the largest geographic area. A WAN connection is the connection between two networks over a long distance (miles). The term WAN is used to describe a wired WAN connection versus a wireless wide area network (WWAN), a wireless connection between two networks over a long distance. The generic term for these connected networks is an internetwork, if it is a public network. The most famous, and largest, internetwork is the Internet itself. An intranet is a private internetwork, generally owned by a single organization. Your Internet connection from home is a WAN connection, even when the network at home consists of but a single computer. WANs, which traditionally used phone lines or satellite communications, now also use cellular telecommunications and cable networks.
WAN speeds range from thousands of bits per second up into the billions of bits per second. At the low end today are 56 Kbps analog modems (56,000 bits per second). At the high end of WAN speeds are parts of the Internet backbone, the connecting infrastructure of the Internet, running at many gigabits per second.
![]()
The speed of your communications on any network is a function of the speed of the slowest part of the pathway between you and the servers you are accessing. The weakest link affects your speed.
A dial-up network connection uses an analog modem (described in Chapter 2) rather than a network card, and uses regular phone cables instead of network cables. In a dial-up connection, you configure the client computer to dial the remote host computer and configure the host computer to permit dial-up access. Once a dial-up connection is established, the client communicates with the host computer as though it were on the same LAN as that computer. If the host computer is already part of a LAN, and if the host configuration allows it, the client computer can access the network to which the host is connected. Some home PCs still use a modem connection for dial-up Internet access. In this case, the host computer is just a gateway to the Internet. This is the slowest, but cheapest, form of Internet access, and in some areas, it may be all that is available.
WAN connections that exceed the speed of a typical dial-up connection come under the heading of broadband WAN. Broadband speeds are available over cellular, Integrated Services Digital Network (ISDN), DSL, cable, and satellite technologies. WAN connections can connect private networks to the Internet and to each other. Generally, these connections are “always on,” meaning that you do not have to initiate the connection every time you wish to access resources on the connected network, as you do with dial-up. If you wish to browse the Web, you simply open your web browser. Unless you are using dial-up, your connection to the Internet is a broadband WAN connection, and we will explore your Internet connection options here.
Line-of-Sight Wireless As implied by the name, line-of-sight wireless technology cannot tolerate obstructions such as forests, mountains, or buildings between the service provider tower and the Internet-connecting site. On-site equipment includes a dish to receive and transmit microwave signals to and from the tower, as well as a modem device connected to a computer.
One technology that uses both line-of-sight and non-line-of-site is Worldwide Interoperability for Microwave Access (WiMAX). Line-of-sight is much faster than non-line-of-site, and both types of WiMAX are used in cellular networks (described next) as well as by various Internet service providers (ISPs) and carriers as a wireless “last mile” connection option for homes and businesses, in which case it is line-of-sight wireless service.
Cellular Long used mainly for voice, the cell networks provide cellular WAN Internet data connections, also referred to as wireless WAN (WWAN). These data services vary in speed from less than dial-up speeds (28.8 Kbps) to a range of broadband speeds, depending on the cellular provider and the level of service you have purchased. Because the trend in cellular is to provide broadband speeds, we include it under broadband WAN.
In the United States, the move away from the original analog cellular networks (the first and second generations) to all-digital cellular networks supports this trend to higher speeds. The first two common digital cellular networks in the United States were based on two standards: Code Division Multiple Access (CDMA), used by Verizon and Sprint, and Global System for Mobile Communications (GSM), used by T-Mobile and AT&T. Cell providers add other technologies that speed things up. For instance, both Verizon and Sprint have used Evolution Data Optimized (EVDO) on their networks in the past. Both CDMA and GMS are Third Generation (3G) digital mobile broadband technologies.
A later and faster 3G technology is High Speed Packet Access (HSPA), with various implementations. The earlier 3G ran at a minimum of 144 Kbps, but eventually 3G service ranged from 400 Kbps to over 4 Mbps.
The next big technology leap was Fourth Generation (4G), which is less of a standard and more of a marketing term associated with several different standards with a range of speeds. The expectation is that a 4G network provides many megabits per second, but the actual speeds vary by cellular provider (carrier). At this writing, a number of large cities in the United States enjoy 4G access offered by several cell providers. The 4G technologies include HSPA+, WiMAX, and LTE. T-Mobile and AT&T both use HSPA+ 21/42. The 21 and 42 indicate maximum speeds of 21 Mbps and 42 Mbps, but actual tests are usually much lower—around 10 Mbps. Sprint’s 4G service for mobile devices is called Worldwide Interoperability for Microwave Access (WiMAX), with speeds around 10 Mbps over a maximum distance of 30 miles. T-Mobile and Verizon use Long Term Evolution (LTE); both call their offering 4G LTE, although it lacks some of the technical criteria for true 4G. More carriers are moving to LTE.
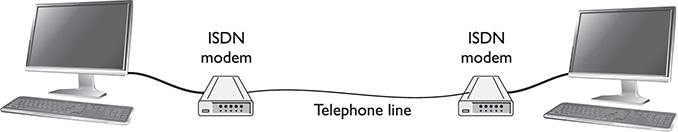
ISDN Integrated Service Digital Network (ISDN) was an early international standard for sending voice and data simultaneously over digital telephone wires. These days, newer technologies such as DSL and cable have largely replaced it. ISDN uses existing telephone circuits or higher-speed conditioned lines to get speeds of 64 Kbps or 128 Kbps. In fact, the most common ISDN service, Basic Rate Interface (BRI), includes three channels: two 64 Kbps channels, called B-channels, that carry the voice or data communications, and one 16 Kbps D-channel that carries control and signaling information. ISDN connections use an ISDN modem on both ends of the circuit. Figure 13-1 shows an ISDN connection between two computers. This connection uses a conditioned phone line provided by the phone company.
FIGURE 13-1 An ISDN network connection between two computer systems
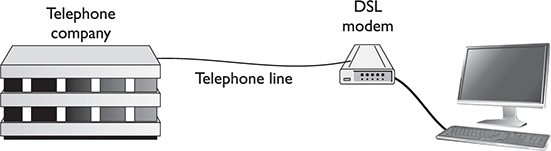
DSL Digital subscriber line (DSL) uses existing copper telephone wire for the communications circuit. A DSL modem splits the existing phone line into two bands to accomplish this; voice transmission uses the frequency below 4000 Hz, and data transmission uses everything else.
Figure 13-2 shows the simplest configuration with a single computer connected directly to the DSL modem. If you have multiple computers, you would connect a router between the computer and the modem and then have each computer connect to the router, either via wireless signal or Ethernet cable. If your DSL modem also contains a built-in router, so much the better—all the computers would then connect to the combo device. Not shown in the figure is that you can also connect your phones, adding a special filter to each phone jack in your house or office and connecting the phones via phone cable and RJ-11 connectors. DSL separates the total bandwidth into two channels: one for voice, the other for data. Voice communications operate normally, and the data connection is always on and available.
DSL service is available through phone companies, which offer a large variety of DSL services, usually identified by a letter preceding DSL, as in ADSL, CDSL, SDSL, VDSL, and many more. Therefore, when talking about DSL in general, the term xDSL is often used. Some services, such as asymmetrical digital subscriber line (ADSL), offer asymmetric service in that the download speed is higher than the upload speed. The top speeds, including the newer variations of ADSL (ADSL2 and ADSL2+), can range from 1.5 Mbps to 25 Mbps for download and between 0.5 Mbps and 3.3 Mbps for upload. An inexpensive version of DSL, Consumer DSL (CDSL) service, targets the casual home user with lower speeds than this range. CDSL service is limited to download speeds of up to 1 Mbps and upload speeds of up to 160 Kbps. It is now rare to see a provider offer a service labeled “CDSL.” Other, more expensive services aimed at business offer much higher rates. Symmetric DSL (SDSL) offers matching upload and download speeds. Table 13-1 shows some DSL services and their maximum data transfer speeds. Most of these services are available as second-generation services with higher speeds, indicated with a “2” at the end of the name, as in ADSL2, ADSL2+, VDSL2, and HDSL2.
TABLE 13-1 DSL Download and Upload Services with Maximum Speeds
Cable Cable television service has been around for several decades, but in the last decade, providers have also been offering broadband Internet service as well. Cable is currently the fastest available Internet service for home use, with speeds of between 30 and 100 Mbps depending on the plan you buy. However, whereas DSL service is point-to-point from the client to the ISP, a cable client shares the network with their neighboring cable clients. It is like sharing a LAN that, in turn, has an Internet connection, so speed degrades as more people share the local cable network. Cable networks use coaxial cable to connect a cable modem to the network. Many cable modems also function as wireless routers, to share the Internet connection with multiple computers in the home or office.
T-Carrier Developed by Bell Labs in the 1960s, the T-carrier system multiplexes voice and data signals onto digital transmission lines. Where previously one cable pair carried each telephone conversation, the multiplexing of the T-carrier system allows a single pair to carry multiple conversations. Over the years, the T-carrier system has evolved, and telephone companies have offered various levels of service over the T-carrier system. For instance, a T1 circuit provides full-duplex transmissions at 1.544 Mbps, carrying digital voice, data, or video signals. A complete T1 circuit provides point-to-point connections, with a channel service unit (CSU) at both ends. On the customer side, a T1 multiplexer or a special LAN bridge, referred to as the customer premises equipment (CPE), connects to the CSU. The CSU receives data from the CPE and encodes it for transmission on the T1 circuit. T1 is just one of several levels of T-carrier services offered by telephone companies over the telephone network.
Satellite Satellite communications systems have come a long way over the last several years. Satellite communications systems initially allowed extensive communications with remote locations, often for military purposes. These systems usually use microwave radio frequencies and require a dish antenna, a receiver, and a transmitter. Early satellite communications systems were very expensive to maintain and operate. Today, a number of companies offer relatively high bandwidth at affordable prices for Internet connections and other applications. Satellite connections are available for both fixed and mobile applications, with speeds ranging from 5 to 25 Mbps. Different satellite speed plans are available to fit different budgets. An average speed is around 10 Mbps at this writing. As with TV satellite service, you must have a place to mount the dish antenna with a clear view of the southern sky.
![]()
The problem with satellite service is not so much the raw speed, but the latency (that is, the delay) between a request and a response. Because the signal must travel into space and back, there is an unavoidable delay each time your computer requests data, which makes satellite service seem slower than raw speed tests would have you believe.
Fiber In order to compete with cable companies, AT&T, Verizon, and a few other telecommunications companies offer fiber-optic cabling to the home in most areas. Where available, subscribers can have the combined services of phone, Internet, and television. The Internet access speeds vary by provider and service level, but look for speeds greater than 100 Mbps.
Permanent Virtual Circuit (PVC) A virtual circuit (VC) is a communication service provided over a telecommunications network or computer network. A VC logically resembles a circuit passing over a complex routed or switched network, such as the phone company’s frame relay or asynchronous transfer mode (ATM) network. A permanent virtual circuit (PVC) is a virtual circuit, created and remaining available, between two endpoints that are normally some form of data terminal equipment (DTE). Telecommunications companies provide PVC service to companies requiring a dedicated circuit between two sites that require always-on communications.
Virtual Private Network (VPN) A virtual private network (VPN) is not in itself a WAN connection option, but rather a way to create a simulated WAN-type point-to-point connection across a complex unsecured network. For instance, at one time, if you wanted to connect the computers in a small district office to your employer’s private internetwork, you either used a very slow dial-up connection or a fast but expensive physical point-to-point connection. Today, you would connect a single computer or network to the private internetwork over the Internet in a way that keeps your data secure and appears to be a point-to-point connection. You would still need a physical connection to the Internet, preferably a WAN connection, and on top of that you would run special software on both ends of the connection that create a VPN. This is one of several tunneling techniques used to secure network traffic by encapsulating the original packets within other packets. A VPN uses special tunneling protocols for this purpose, and each endpoint of the tunnel must be assigned an IP address.
Testing Broadband Speeds
Regardless of the broadband service you use, they all vary in the actual speeds they provide from moment to moment. Connect to one of the many broadband speed-testing sites on the Internet and test yours now.
1. Open your favorite search engine and enter a search string that will locate an Internet speed testing website. We used network speed test.
2. From the results listed in the search engine, select a site (we chose www.internetfrog.com). Often sites suggest downloading and running other software to test your computer, so be careful to only select the speed test and not to download or run programs you do not want.
3. Follow the instructions for testing your connection. Some sites test as soon as you connect, and some test sites ask you to select a city near you. The test may take several minutes.
4. View the results (see Figure 13-3). Are the results congruent with the service you expect from your broadband connection?
FIGURE 13-3 The speed of a broadband Internet connection can vary.

5. Time permitting, try this at another time, or even on another day, and compare your results.
While the range of a network, the distance over which signals are viable, is one important defining characteristic of a network, bandwidth is another. Bandwidth is the amount of data that can travel over a network within a given time. It may be expressed in kilobits per second (Kbps), kilobytes per second (KBps), megabits per second (Mbps), and even gigabits per second (Gbps)—that is, thousands of bits per second, thousands of bytes per second, millions of bits per second, and billions of bits per second, respectively.
Another network characteristic related to bandwidth is latency. Latency is the amount of time it takes a packet to travel from one point to another. In some cases, latency is determined by measuring the time it takes for a packet to make a round trip between two points. This can be a more important measurement, as it is does not measure the speed at which the packets travel, but the length of time it takes a packet to get from point A to point B. It is like measuring the actual time it takes you to travel by car from Los Angeles to San Francisco. The actual time of travel varies by the amount of traffic you encounter and the interchanges you pass through. The same is true for a packet on a network.

CERTIFICATION OBJECTIVES
 901: 2.3 Explain the properties and characteristics of TCP/IP
901: 2.3 Explain the properties and characteristics of TCP/IP
 901: 2.4 Explain common TCP and UDP ports, protocols, and their purpose
901: 2.4 Explain common TCP and UDP ports, protocols, and their purpose
This section details the topics required for CompTIA A+ 901 exam objective 2.3, including a comparison of IPv4 and IPv6, the types of IP addresses based on usage (public, private, and APIPA), the two methods for assigning IP addresses (static and dynamic), and such important TCP/IP terms as client-side DNS, DHCP, subnet mask, and gateway. Coverage of CompTIA A+ 901 exam objective 2.4 is also included in this section because it is part of the TCP/IP story. It includes an explanation of both TCP and UDP protocols, as well as other TCP and UDP protocols and related services, and the ports used by TCP and UDP.
The software on a network is what gives us the network that we know and use. This is the logical network that rides on top of the physical network. In this section, we’ll explore several aspects of networking that are controlled by software, including the network roles, protocol suites, and network addressing of the logical network.
You can describe a network by the types of roles played by the computers on it. The two general computer roles in a network are clients, the computers that request services, and servers, the computers that provide services.
In a peer-to-peer network, each computer system in the network may play both roles: client and server. They have equal capabilities and responsibilities; each computer user is responsible for controlling access, sharing resources, and storing data on their computer. In Figure 13-4, each of the computers can share its files, and the computer connected to the printer can share the printer. Peer-to-peer networks work best in a very small LAN environment, such as a small business office, with fewer than a dozen computers and users. Microsoft calls a peer-to-peer network a workgroup, and each workgroup must have a unique name, as must each computer.
FIGURE 13-4 A peer-to-peer network

A client/server-based network uses dedicated computers called servers to store data and provide print services or other capabilities. Servers are generally more powerful computer systems with more capacity than a typical workstation. Client/server-based models also allow for centralized administration and security. These types of networks are scalable in that they can grow very large without adding administrative complexity to the network. A large private internetwork for a globe-spanning corporation is an example of a client/server-based network. When configuring the network, the network administrator can establish a single model for security, access, and file sharing. Although this configuration may remain unchanged as the network grows, the administrator can make changes, if needed, from a central point. Microsoft calls a client/server network with Microsoft servers a domain. The domain must have a unique name, and each client or server computer must have a unique name.
Organizations use client/server environments extensively in situations that need a centralized administration system. Servers can be multipurpose, performing a number of functions, or dedicated, as in the case of a web or e-mail server. Figure 13-5 shows a network with servers used for e-mail and printing. Notice in this example that each of the servers is dedicated to the task assigned to it.
FIGURE 13-5 A client/server environment where dedicated servers perform assigned functions

A network operating system (NOS) is an operating system that runs on a network server and provides file sharing and access to other resources, account management, authentication, and authorization services. Microsoft Windows Server operating systems, UNIX and Linux are examples of network operating systems. The distinction is clouded somewhat by the ability of desktop operating systems to allow file sharing, but desktop operating systems do not provide the robust services that, coupled with high-performance servers and fast network connections, add up to reliable server operating systems.
A network client is software that runs on the computers in a network and that receives services from servers. Windows, macOS , and Linux, when installed on desktop computers that have a network connection, automatically install a basic network client that can connect to servers and request file and print services. In each case, the automatically installed clients can only connect to a certain type of server. In the case of Windows, it is a Windows server. Novell has client software that comes in versions the Linux and Windows operating systems can use for accessing Novell servers.
Beyond a basic file and print client, Windows and other OSs usually come with an e-mail client, a browser (web client), and other clients, depending on the options you select during installation. You can add other clients. For instance, if you install an office suite such as Microsoft Office, you will have a more advanced e-mail client (Outlook in the case of Office) than the one that comes with the OS.
Every computer network consists of physical and logical components controlled by software. Standards, also often called protocols, describe the rules for how hardware and software work and interact together. Ethernet, detailed earlier in this chapter, is a standard for the physical components, such as cabling and network adapters, as well as for the software that controls the hardware, such as the firmware in the network adapters and device drivers that allows the network adapters to be controlled from the operating system.
However, in most discussions about networks and related documentation, the term “protocol” describes certain software components that work on top of such underlying protocols as Ethernet. These protocols control communication at a higher level, including the addressing and naming of computers on the network, among other tasks. They combine into suites that include a group of protocols built around the same set of rules, with each protocol describing a small portion of the tasks required to prepare, send, and receive network data.
The CompTIA 220-901 and 220-902 exams require that A+ candidates understand the basics of the TCP/IP protocol suite because it is the most common protocol suite used on LANs and WANs, as well as on the Internet. It actually involves several protocols and other software components, and together, we call these a “protocol stack.”
TCP/IP replaced two older protocol suites that were used on many early computer networks—namely, Microsoft’s NetBEUI and Novell’s IPX/SPX. You may encounter these in some organizations or hear about them from long-time network techs.
Transmission Control Protocol/Internet Protocol (TCP/IP) is by far the most common protocol suite on both internal LANs and public networks. It is the Internet’s protocol suite. TCP/IP requires some configuration, but it is robust, usable on very large networks, and routable (a term that refers to the ability to send data to other networks). At each junction of two networks is a router that uses special router protocols to send each packet on its way toward its destination.
Although the TCP/IP suite has several protocols, the two main ones are the Transmission Control Protocol (TCP) and the Internet Protocol (IP). There are many subprotocols, such as UDP, ARP, ICMP, and more. We’ll describe UDP later in the discussion about common ports, Address Resolution Protocol (ARP) is used to resolve an IP address to a MAC address, and Internet Control Message Protocol (ICMP) is described in Chapter 16.
Although TCP/IP is actually a protocol suite, techs commonly refer to this suite as “the TCP/IP protocol.” On the job, take your cue from the experienced techs, and use the terms they use for easy communication.
TCP/IP allows for cross-platform communication, meaning that computers using different OSs (such as Windows and Linux) can send data back and forth, as long as they are both using TCP/IP. We now briefly describe the two cornerstone protocols of the TCP/IP suite as well as NetBIOS, a leftover from the NetBEUI suite.

Messages sent over a network are broken up into smaller chunks of data, and each chunk is placed into a logical container called a packet. Each packet has information attached to the beginning of the packet, called a header. This packet header contains the IP address of the sending computer and that of the destination computer. The Internet Protocol (IP) manages this logical addressing of the packet so that routing protocols can route it over the network to its destination. We will describe addressing later in “Network Addressing.”
When preparing to send data over a network, the Transmission Control Protocol (TCP) breaks the data into chunks, called datagrams. Each datagram contains information to use on the receiving end to reassemble the chunks of data into the original message. TCP places this information, both a byte-count value and a datagram sequence, into the datagram header before giving it to the IP protocol, which encapsulates the datagrams into packets with addressing information.
When receiving data from a network, TCP uses the information in this header to reassemble the data. If TCP is able to reassemble the message, it sends an acknowledgment (ACK) message to the sending address. The sender can then discard datagrams that it saved while waiting for an acknowledgment. If pieces are missing, TCP sends a non-acknowledgment (NAK) message back to the sending address, whereupon TCP resends the missing pieces.
An excellent 13-minute movie describing how TCP/IP works in an amusing and interesting fashion is available for viewing at www.warriorsofthe.net and is well worth watching.
Networked Basic Input/Output System (NetBIOS) and Networked Basic Input/Output System Extended User Interface (NetBEUI) are very old technologies that you may never encounter. However, the CompTIA A+ 220-901 and 220-902 exam objectives include both of these in their Acronyms list, so here is the short lecture. People often confuse NetBEUI with NetBIOS, perhaps because NetBEUI was the original protocol suite within which NetBIOS was a single protocol. NetBEUI was the default protocol suite on Microsoft networks in the 1980s and 1990s. It was appropriate only for small networks because it was limited to a single network segment and could not route network traffic beyond that segment. TCP/IP has replaced NetBEUI as well as other outdated network protocol suites.
NetBIOS is a single protocol for managing names on a network. In a Windows network, you can use NetBIOS names and the NetBIOS protocol with the TCP/IP suite. NetBIOS only requires a computer name and a workgroup name for each computer on the network. NetBIOS naming has limited value in modern networks, and the Internet-style names of the DNS protocol (which requires TCP/IP) have replaced it. Learn more about DNS later in the topic “DNS Server.”
NetBIOS over TCP/IP (NetBT) is a software component that supports the NetBIOS naming system and name resolution on a TCP/IP network. While even Microsoft has pretty much abandoned the use of the NetBIOS naming system, some organizations are still using old apps that depend on finding network resources based on the old NetBIOS system. Since virtually all networks today use the TCP/IP protocol suite, these systems must have NetBT enabled, as must the servers or networked printers that the old software is accessing.
NetBT on the client computer uses several methods to resolve a NetBIOS name to an IP address. First, it looks in the local computer’s local NetBIOS cache of recently resolved NetBIOS names. If it does not find the name in the cache, it then sends a query to the WINS server (described a bit later in the section “Primary WINS Server”). If the WINS server does not have the name in its list of NetBIOS names and IP addresses, the client sends out a NetBIOS broadcast on the local network querying for the name. If the server/computer in question has NetBT enabled and it is functioning, it will respond and the client is done searching. That may be more than you will ever need to know about NetBT, but in Chapter 16 we revisit this topic and how to troubleshoot for NetBT problems.
Identifying each computer or device directly connected to a network is important. We do this at two levels: the hardware level, in which the network adapter in each computer or network device has an address, and the logical level, in which a logical address is assigned to each network adapter.
Every NIC, and every device connected to a network, has a unique address, placed in ROM by the manufacturer. This address, usually permanent, is called by many names, including Media Access Control (MAC) address, physical address, Ethernet address (on Ethernet devices), and NIC address. For the sake of simplicity, we will use the term “physical address” in this book.
A MAC address is 48 bits long and usually expressed in hexadecimal. You can view the physical address of a NIC several ways. It is usually, but not always, written on a label attached to the NIC. Figure 13-6 shows the label on a wireless USB NIC. The words “MAC Address” appear above the physical address. The actual address on this NIC is six two-digit hexadecimal numbers, but on this label, the numbers are not separated. It is easier to read these numbers if separated by a dash, period, or space, like this: 00-11-50-A4-C7-20.
FIGURE 13-6 The physical address of a NIC, labeled “MAC Address,” and shown on the NIC

Locating this address is not always so easy. You can also discover the address of a NIC through Windows. Use the IPCONFIG command-line utility that is installed on a Windows computer with the TCP/IP protocol suite. This command lets you view the IP configuration of a network connection and perform certain administrative functions. To see the physical address as well as the rest of the IP configuration for a connection, simply open a Command Prompt window (as described in Chapter 10) and type the ipconfig /all command. The physical address is in the middle of the listing. Notice that it shows six two-digit hexadecimal numbers, each separated by a dash.
This physical address identifies a computer located in a segment of a network. However, you use logical addresses to locate a computer that is beyond the local network segment.
In addition to the hardware address, a computer in a TCP/IP network must have a logical address that identifies both the computer and the network. This address comes under the purview of the IP protocol. Internet Protocol version 4 (IPv4) and its addressing scheme have been in use for over the past three decades. It offers almost 4.3 billion possible IP addresses, but the way they have been allocated throughout the world reduces that number. The Internet is currently transitioning to Internet Protocol version 6 (IPv6) with a new addressing scheme that provides many more addresses.
An IP address identifies both a computer, a host in Internet terms, and the logical network on which the computer resides. This address allows messages to move from one network to another on the Internet. At the connecting point between networks, a special network device called a router uses its routing protocols to determine the route to the destination address before sending each packet along to the next router closer to the destination network. Each computer and network device that directly attaches to the Internet must have a globally unique IP address. Both versions of IP have this much and more in common. Following are explanations of these addressing schemes to help you distinguish between them.
IPv4 Addresses An IPv4 address is 32 bits long, usually shown as four decimal numbers, 0–255, each separated by a period—for example, 192.168.1.41. Called dotted-decimal notation, this format is what you see in the user interface. However, the IPv4 protocol works with addresses in binary form, in which the preceding address looks like this: 11000000.10101000.00000001.00101001.
IPv4 addresses are routable because an IP address contains within it both the address of the host, called the host ID, and the address of the network on which that host resides, called the network ID (netID). A mask of 1s and 0s separates the two parts. When you put the mask over an address, the 1s cover up the first part, or network ID, and the 0s cover up the remaining part, or host ID. The address portion that falls under the 1s is the network address, and the address portion that falls under the 0s is the host address. In the preceding example, with a mask of 11111111.11111111.11111111.00000000, or 255.255.255.0, the network ID is 11000000.10101000.00000001.00000000, and the host ID is 00101001 (see Figure 13-7). In dotted-decimal form, the network ID is 192.168.1.0, and the host ID is 41. Often called a subnet mask, this mask is an important component in a proper IP configuration. After all, the IP address of a host does not make any sense until masked into its two IDs. When you enter the subnet mask into the Windows user interface in the Properties dialog box of the NIC, you will enter it in dotted-decimal notation, but we commonly use a shorthand notation when talking about the subnet mask, and you will see this notation in some user interfaces. For instance, a subnet mask of 255.255.255.0 is easily represented as /24. Therefore, using our example address from earlier, rather than saying the IP address is 192.168.1.41, with a subnet mask of 255.255.255.0, you can put it together as 192.168.1.41/24.
FIGURE 13-7 The subnet mask defines the network ID and host ID portions of an IP address.

The Internet Assigned Numbers Authority (IANA) oversees the allocation of IP addresses for use on the Internet. They did this directly in the early years, and now do it through a group of Regional Internet Registries (RIRs) that allocate IP addresses to the largest Internet service providers. In the early years of IPv4, IANA divided the IP address pool into groupings of addresses, called Class IDs, with five classes, each defined by the value of the first octet of the IP address, as Table 13-2 shows.
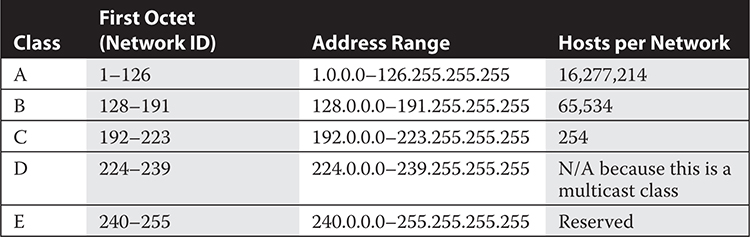
So, the organization that received a Class A network ID of 12 actually has more than 16,277,214 host IDs. Obviously, this scheme is a very inefficient way to allocate IP addresses. In fact, the organization can subnet this Class A network into smaller networks, wasting individual host IDs in the process. Today some organizations have returned all or part of their original allotment, and the large ISPs give out portions of these classful networks using subnetting rules called Classless Inter-Domain Routing (CIDR).

IPv6 Addresses In preparation for the day when ISPs and the Internet routers are fully IPv6 ready, all modern Windows versions support both IPv6 and IPv4, as do most new network devices. In fact, some high-speed internetworks already use IPv6. IPv6 has 128-bit addressing, which theoretically supports a huge number of unique addresses—340,282,366,920,938,463,463,374,607,431,768,211,456 to be exact. We show an IPv6 address in eight groups of hexadecimal numbers separated by colons, such as this: 2002:470:B8F9:1:20C:29FF:FE53:45CA. Sometimes the address will contain a double colon (::)—for example, 2002:470:B8F9::29FF:FE53:45CA. This means there are consecutive groups of all 0s, so :: might be shorthand for :0000:0000:0000. Global unicast addresses, the public IPv6 addresses, have a prefix of 001.
IPv6 addresses use a network mask the same way IPv4 addresses do—to distinguish which portion of the address identifies the network. As is often done with IPv4, the mask is expressed with a front slash (/) and the number of bits in the mask; for example, 2002:470:B8F9:1:20C:29FF:FE53:45CA/64 implies a 64-bit network mask.
June 6, 2012, was international World IPv6 Launch Day. Major websites such as Google, Facebook, Yahoo!, and others enabled IPv6 on their websites to assess real-world connectivity for a 24-hour period, but until ISPs around the globe enable IPv6 routing, true end-to-end IPv6 connectivity on the Internet will not be realized.
You can see both IPv4 and IPv6 data by using IPCONFIG at a command prompt, or from a GUI interface. In Windows Vista or Windows 7, access IP address information by clicking Start and entering network connections in the Search box. From the results list, select View Network Connections. Then in the Network Connections section of the Control Panel, double-click the connection you wish to view. This opens the Connection Status dialog box for the connection. Click the Details button to display the Network Connection Details dialog box. Figure 13-8 shows the details for a single network connection as seen in the Windows 7 Network Connection Details dialog box. Notice that this connection has both IPv4 (dotted-decimal) and IPv6 (hexadecimal) addresses. Only the IPv4 protocol has addresses for the default gateway, DHCP server, and DNS server, indicating that this computer is configured for a IPv4 network. These three addresses are described in the next section.
FIGURE 13-8 The Network Connection Details dialog box in Windows 7
When you view the IP configuration for the NIC on your PC, you may be surprised to see other IP addresses besides that of the NIC. These include addresses labeled Default Gateway, DHCP Server, DNS Servers, and (sometimes) Primary WINS Server.
Default Gateway When your IP protocol has a packet ready to send, it examines the destination IP address and determines if it is on the same IP network (in the earlier example, this is 192.168.1.0) as your computer. If it is, then it can send the packet directly to that computer (host ID 41 in the example). If the destination IP address is on another IP network, then your computer sends it to the IP address identified as the default gateway. This address is on your network (same IP network ID), and it belongs to a router that will send the packet on to the next router in its journey to its destination. Without a default gateway, your computer does not know what to do with packets that have a destination address beyond your IP network. IPv6 also requires a default gateway setting to route packets to remote networks. This can be configured manually or delivered via a Dynamic Host Configuration Protocol (DHCP) device that supports IPv6.
DNS Server A DNS client uses the DNS server IP address for name resolution. The Domain Name Service (DNS) manages access to Internet domain names, like mcgraw-hill.com. The server-side service maintains a database of domain names and responds to queries from DNS clients (called resolvers) that request resolution of Internet names to IP addresses. A client will do this before sending data over the Internet, when all it knows is the domain name. For instance, if you wish to connect to a McGraw-Hill web server, you might enter www.mcgraw-hill.com in the address bar of your browser. Then, your computer’s DNS client (the resolver) sends a request to a DNS server, asking it to resolve the name to an IP address. Once the DNS server has the answer (which it most likely had to request from another DNS server), it sends a response to your computer. The IP protocol on your computer now attaches the address to the packets your computer sends requesting a web page. IPv4 clients query a DNS server for “A” records, which map to an IPv4 address. IPv6 clients query an IPv6 DNS server for “AAAA” (quad A) records to resolve names to IP addresses. Note that an IPv6 address (128 bits) is four times longer than an IPv4 address (32 bits)!
Primary WINS Server Windows Internet Name Service (WINS) has a function similar to that of DNS, but it resolves NetBIOS names rather than DNS host names. WINS works in Microsoft networks, but the need for it has diminished over the years. Newer versions of Windows and its client/server environment, Active Directory, can locate computers strictly by DNS name. Sometimes the WINS service is required on a network because of old operating systems or applications that only know how to work with NetBIOS names and depend on querying the WINS service. In that case, the address of the WINS server must be included in the IP configuration.
Assigning IP Addresses to NICs There are two ways to assign an IP address to a network host: manually (or statically) and automatically (or dynamically). We will discuss assigning an address manually here and automatically in the next section when we discuss DHCP. When you assign an address manually in Windows, you must open the Properties dialog box for the NIC and enter the exact IP address (obtained from your network administrator), subnet mask, and other configuration information, which includes the addresses for the default gateway, DNS server, and (if necessary) WINS server. An IP address configured in this manner is a static address. This address is not permanent, because an administrator can easily change it, but some documentation uses the term permanent rather than static.

DHCP Server When you install any nonserver version of Windows, the Setup program installs the TCP/IP protocol suite and configures the computer (or its network card, to be more specific) as a DHCP client, meaning it configures it to obtain an IP address automatically from a DHCP server. A NIC configured as a DHCP client will send a request out on the network when Windows starts.
Now, you would think that a client computer without an IP address would not be able to communicate on the network, but it can in a very limited way. Using a special protocol called BOOTP, the computer sends a very small message that a Dynamic Host Configuration Protocol (DHCP) server can read. It cannot communicate with other types of servers until it has an IP address. A properly configured DHCP server will respond by sending the DHCP client an IP address and subnet mask (also using BOOTP). This configuration is the minimum it will assign to the client computer. In most cases, the server will provide the other IP configuration addresses, including default gateway, DNS server, and primary WINS server. Only Windows networks that require this last address get that one.
A DHCP server does not permanently assign an IP address to a client. It leases it. Lease is the term used, even though no money changes hands in this transaction between a DHCP client and a DHCP server. When one-half of the leased time for an IP address (and its associated configuration) has expired, the client tries to contact the DHCP server in order to renew the lease. As long as the DHCP server has an adequate number of unassigned IP addresses, it will continue to reassign the same address to the same client each session. In fact, this happens every day for a computer that is turned off at the end of the workday, at which point the DHCP client will release the IP address, giving up the lease.
Exercise 13-2 walks you through using a command that displays the physical address and IP address for your network card.
Viewing the Physical and IP Addresses of a NIC
To view the physical and IP addresses of a NIC, follow these steps:
1. Open a command prompt.
2. In the Command Prompt window, enter the command ipconfig /all and press ENTER.
3. The result should look something like Figure 13-9 (Windows 7), only with different addresses.
FIGURE 13-9 Use the ipconfig /all command to view the physical address and the IP address of a NIC and the other addresses that are part of the IP configuration.

4. The address of the NIC is in the middle, labeled Physical Address. Notice that the physical address is six pairs of hexadecimal numbers separated by hyphens.
5. Three lines below that is the NIC’s IPv6 address, and one line below that is the IPv4 address.
6. Locate the other addresses discussed in the preceding text, including those of the default gateway, DNS server, DHCP server (if present), and WINS server (if present).
7. When you run this command on a Windows Vista, Windows 7, or Windows 8/8.1 computer, you will also see IPv6 information.
Special IP Addresses You use public IP addresses on the Internet, and each address is globally unique. But there are some special IP addresses that are never allowed for computers and devices connected directly to the Internet. They are as follows:
 Loopback addresses Although it is generally believed that the address 127.0.0.1 is the IPv4 loopback address, any Class A address with a network ID of 127 is a loopback address, used to test network configurations. If you send a packet to a loopback address, it will not leave your NIC. Sounds like a useless address, but you will use it for testing and troubleshooting in Chapters 14 and 16. Also, note that the IPv6 loopback address is ::1 (0:0:0:0:0:0:0:1).
Loopback addresses Although it is generally believed that the address 127.0.0.1 is the IPv4 loopback address, any Class A address with a network ID of 127 is a loopback address, used to test network configurations. If you send a packet to a loopback address, it will not leave your NIC. Sounds like a useless address, but you will use it for testing and troubleshooting in Chapters 14 and 16. Also, note that the IPv6 loopback address is ::1 (0:0:0:0:0:0:0:1).
 Private IPv4 addresses If a network is not directly connected to the Internet, or if you wish to conceal the computers on a private network from the Internet, you use private IP addresses. Millions of locations all over the world use these addresses and they are, therefore, not globally unique because they are never used on the Internet. In Chapter 14, we will describe how you can use these addresses on your private network, yet still access resources on the Internet, thanks to methods that hide your address when you are on the Internet. The private address ranges include the following:
Private IPv4 addresses If a network is not directly connected to the Internet, or if you wish to conceal the computers on a private network from the Internet, you use private IP addresses. Millions of locations all over the world use these addresses and they are, therefore, not globally unique because they are never used on the Internet. In Chapter 14, we will describe how you can use these addresses on your private network, yet still access resources on the Internet, thanks to methods that hide your address when you are on the Internet. The private address ranges include the following:
 10.0.0.0 through 10.255.255.255 (1 Class A network)
10.0.0.0 through 10.255.255.255 (1 Class A network)
 172.16.0.0 through 172.31.255.255 (16 Class B networks)
172.16.0.0 through 172.31.255.255 (16 Class B networks)
 192.168.0.0 through 192.168.255.255 (256 Class C networks)
192.168.0.0 through 192.168.255.255 (256 Class C networks)
 Private IPv6 addresses The FC00::/7 range has been set aside for private IPv6 network addressing. These addresses will not be routable by IPv6 Internet routers, but internal routers within an organization can route them much like they do IPv4 private addresses. The proper term for this type of address is a Unique Local Address (ULA).
Private IPv6 addresses The FC00::/7 range has been set aside for private IPv6 network addressing. These addresses will not be routable by IPv6 Internet routers, but internal routers within an organization can route them much like they do IPv4 private addresses. The proper term for this type of address is a Unique Local Address (ULA).
 Automatic Private IP Addressing (APIPA) address If a DHCP client computer fails to receive an address from a DHCP server, the client will give itself an address with the 169.254 /16 network ID. If a computer uses this range of addresses, it will not be able to communicate with other devices on the network unless they also have addresses using the same network ID, which means the other computers must also be using an APIPA address. These clients will not have a default gateway address and, therefore, will not be able to communicate beyond the local network. IPv6 behaves similarly, except that the self-assigned IPv6 address will have a prefix of FE80 and is always present, even if a routable IPv6 address was configured either statically or via DHCP. This is referred to as a “link local address.”
Automatic Private IP Addressing (APIPA) address If a DHCP client computer fails to receive an address from a DHCP server, the client will give itself an address with the 169.254 /16 network ID. If a computer uses this range of addresses, it will not be able to communicate with other devices on the network unless they also have addresses using the same network ID, which means the other computers must also be using an APIPA address. These clients will not have a default gateway address and, therefore, will not be able to communicate beyond the local network. IPv6 behaves similarly, except that the self-assigned IPv6 address will have a prefix of FE80 and is always present, even if a routable IPv6 address was configured either statically or via DHCP. This is referred to as a “link local address.”
It isn’t enough for a packet to simply reach the correct IP address; each packet has additional destination information, called a port, which identifies the exact service it is targeting. For instance, when you want to open a web page in your browser, the packet requesting access to the web page includes both the IP address (resolved through DNS) and the port number of the service. In this case, it would be HTTP for many web pages and HTTPS for a secure web page where you must enter confidential information. All the services you access on the Internet have port numbers. These include the two services just mentioned, plus FTP, POP3, SMTP, Telnet, SSH, and many more. Each port is also associated with a protocol. The most common protocols for communicating with Internet applications are TCP and UDP. TCP is used for communications that are connection-oriented, which is true of most services you are aware of using, whereas Universal Datagram Protocol (UDP) is used for connectionless communications, in which each packet is sent without establishing a connection. Therefore, in Table 13-3, we identify the protocol along with the port number for common TCP/IP services.
TABLE 13-3 Protocol and Port Numbers for Common Internet Services




CERTIFICATION OBJECTIVES
 901: 2.1 Identify the various types of network cables and connectors
901: 2.1 Identify the various types of network cables and connectors
 901: 2.2 Compare and contrast the characteristics of connectors and cabling
901: 2.2 Compare and contrast the characteristics of connectors and cabling
 901: 2.8 Compare and contrast network architecture devices, their functions, and features
901: 2.8 Compare and contrast network architecture devices, their functions, and features
In this section we will detail the features and characteristics of network cabling, including fiber-optic, twisted-pair, and coaxial cabling, as well as their connectors, as required by CompTIA A+ 901 exam objectives 2.1 and 2.2. We will also survey the various hardware devices used on networks—some of them for connecting networks to each other, and some for allowing client computers and devices to access networks. Knowledge of these is required for CompTIA A+ 901 exam objective 2.8.
Network hardware includes many network connection devices that are part of the infrastructure of small networks, as well as large internetworks, and of the largest internetwork, the Internet itself. We limit the hardware we describe in this section to the network adapters used in PCs, the medium that connects these adapters to the network, the devices that connect networks to one another, and a few miscellaneous devices included in the CompTIA A+ 220-901 exam objectives.
While we previously mentioned network interface cards in this chapter, we now focus on this particular type of network hardware device. Each computer on a network must have a connection to the network provided by a NIC, also called a network adapter, and some form of network medium that makes the connection between the NIC and the network. NICs are identified by the network technology used (Ethernet or Wi-Fi) and the type of interface used between the NIC and the PC, such as the PCI and PCIe interfaces introduced in Chapter 3, or the USB or FireWire interfaces defined in Chapter 4, or for a laptop, the PC Card or ExpressCard interfaces explored in Chapter 7.
Most NICs come with status indicators, as lights on the card itself, and/or software that displays the status on the notification area of the taskbar. You can use these when troubleshooting, as described in Chapter 16.
The transmission medium for a network carries the signals. These signals may be electrical signals carried over copper-wire cabling, light pulses carried over fiber-optic cabling, or infrared or radio waves transmitted through the atmosphere. In these examples, the copper wire, fiber-optic cable, and atmosphere are the media. When it comes to wired media, one important issue is plenum versus PVC, which we will explore next, and then we’ll look at the basics of twisted-pair, coaxial, and fiber-optic cabling.
Many commonly used network cables use a polyvinyl chloride (PVC) outer sheath to protect the cable. PVC is not fire resistant, and, by code, you cannot use it in overhead or plenum areas in offices, those spaces in a building through which air conditioning and heating ducts run. Plenum cable uses a special fire-resistant outer sheath that will not burn as quickly as PVC. Plenum cable frequently costs more, but most areas require it. Most of the standard cables discussed in this chapter are available in plenum-grade ratings.
Twisted-pair cable is the most popular cable type for internal networks. The term “twisted pair” indicates that it contains pairs of wires twisted around each other. These twists help “boost” each wire’s signals and make them less susceptible to electromagnetic interference (EMI). The most common type of twisted-pair wiring is unshielded twisted-pair (UTP), which, although it has a plastic sheathing, does not have actual metal shielding.
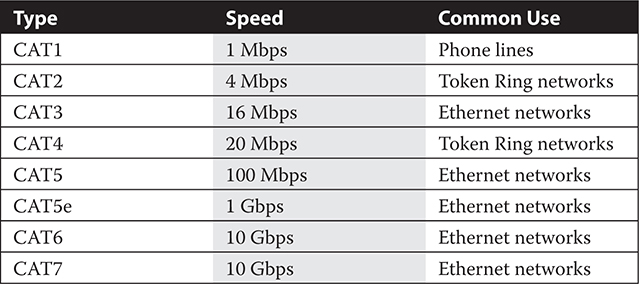
There are several standards for twisted-pair cables, each with a different number of wires, certified speed, and implementation. We often refer to these standards as CAT (short for “category”) followed by a number—for example, CAT3 or CAT4. Currently, CAT5, CAT5e, and CAT6 are the most common twisted-pair cable types. Table 13-4 summarizes twisted-pair cable standards. CAT5e is an enhanced and more stringently tested version of CAT5 that offers better transmission characteristics than CAT5. CAT6 and CAT7 cable offer even higher bandwidth and improved signal-handling characteristics.
The telecommunications standards organization, Telecommunication Industry Association/Electronics Industry Alliance (TIA/EIA), developed the TIA/EIA 568 standards for telecommunications cabling. TIA/EIA standards are now labeled per the standards group, the American National Standards Institute (ANSI), with an ANSI prefix. A portion of these standards, now called ANSI/TIA/EIA-568-B standard, includes pin assignments for connecting eight-wire cabling to Ethernet connectors. One pin assignment is called T568A, and the other is T568B. Technically, as long as you standardize on one pin assignment, either is fine. However, T568B is recommended, and the use of T568A is only recommended if you want to create a cross-over cable, which you can accomplish by using the T568A standard on one end and the T568B standard on the other, as the main difference is in the assignment of the two wires that these two standards reverse.
According to the ANSI/TIA/EIA standard for CAT5e copper cable (TIA/EIA 568-5-A), the maximum length for a structured wiring cable segment, is 100 meters (328 feet) without need for a switch or a hub (repeater). With a repeater, you can run up to five segments for 10BaseT. For 100BaseT, you can use two hubs for a cable run of up to 200 meters (656 feet). Using modern switches with 100M and Gigabit LANs raises these limits. Consult the switch vendor’s specifications for details.
Twisted-pair cable is also available as shielded twisted-pair (STP), with an extra insulating layer that helps prevent data loss and blocks EMI. However, due to the expense of STP, UTP is more commonly used.
You can identify a twisted-pair cable by its use of RJ-45 connectors, which look like regular RJ-11 phone connectors but are slightly larger, as they contain eight wires, whereas RJ-11 connectors contain four wires.
![]()
The oldest cabling you should normally encounter in a business is CAT5, although it is certainly possible to find very old installations of CAT3 cabling, which is not adequate for modern networks.
The type of cabling used to connect a cable modem to a cable network is coaxial cable, which consists of a central copper wire surrounded by an insulating layer, which is itself surrounded by a braided metal shield that protects the signals traveling on the central wire from outside interference. We also described coaxial cabling in Chapter 5, with a drawing of a cable and its components shown in Figure 5-15. A plastic jacket encases all of this. Coaxial cable used for standard cable television and high-definition TV (HDTV), as well as cable-modem Internet access, is usually RG-6 cable with a 75 Ohm rating. Theoretically, signals can travel up to 300 meters at 500 Mbps over RG-6 coax cables, but the practical limit is 50 Mbps, which still makes this medium very popular for broadband Internet connections. The specific distance and speed vary, depending on the type of signal and the devices generating the signal. Sometimes people use RG-59 cable to carry closed-circuit TV (CCTV) signals, although modern CCTV implementations use standard network cabling such as CAT5e UTP. Compared to RG-59, RG-6 cabling has a thicker conductive core and as a result can transmit data over longer distances. Expect an RG-6 cable to connect to the cable wall jack and cable modem with either F-connectors that you must securely screw on or Bayonet Neill-Concelman (BNC) connectors that lock with a simple quarter-turn twist.
A splitter is a box that allows two cables to join to a single cable. Splitters are most common on coaxial cable, such as when splitting the incoming signal from a cable TV/Internet provider into two branches: one for the TV and one for the cable modem. Splitters do affect signal strength, so don’t use them unnecessarily. If you think that splitting may be degrading the signal to the point where errors are occurring, ask a service technician from the cable company to check the lines.
![]()
Splitters are also available for UTP cable, but you probably don’t want one. If you want to share a single incoming network signal with multiple devices, use a switch or router.
Fiber-optic cable (fiber for short) has commonly been used to join separate networks over long distances, but until recently, LANs seldom used fiber-optic cable. Increasingly, however, many new homes, apartments, and businesses have both fiber and copper wiring installed when being built. Also, some phone companies are using fiber to connect directly to homes and businesses.
Fiber transmits light rather than electrical signals, so it is not susceptible to EMI. It is capable of faster transmission than other types of cable, but it is also the most expensive cable.
A single light wave passing down fiber cabling is a mode. Two variants of fiber used in fiber-optic cables are single-mode fiber (SMF) and multimode fiber (MMF). Single-mode fiber allows only a single light wave to pass down the cable, but supports faster transmission rates over longer distances. Multimode fiber allows multiple light waves to pass simultaneously and is usually larger in diameter than single-mode fiber; each wave uses a certain portion of the fiber cable for transmission. There are many Ethernet standards for fiber-optic cabling, with a wide range of maximum speeds and distances. Multimode fiber is used most often in LANs with speeds up to 1 Gbps and a maximum range of 1000 meters, whereas single-mode fiber has a range of dozens of miles with speeds in the terabits per second.
Fiber-optic data transmission requires two cables: one to send and another to receive. Connectors enable fiber-optic cable to connect to transmitters, receivers, or other devices. Over the years, the various standards for connectors have continued to evolve, moving toward smaller connectors. Here are brief descriptions of four types of connectors used with fiber-optic cable:
 Straight-tip (ST) A straight, round connector used to connect fiber to a network device. It has a twist-type coupling.
Straight-tip (ST) A straight, round connector used to connect fiber to a network device. It has a twist-type coupling.
 Subscriber connector (SC) A square snap coupling, about 2.5 mm wide, used for cable-to-cable connections or to connect cables to network devices. It latches with a push-pull action similar to audio and video jacks.
Subscriber connector (SC) A square snap coupling, about 2.5 mm wide, used for cable-to-cable connections or to connect cables to network devices. It latches with a push-pull action similar to audio and video jacks.
 Lucent connector (LC) Also called local connector, has a snap coupling and, at 1.25 mm, is half the size of the SC connector.
Lucent connector (LC) Also called local connector, has a snap coupling and, at 1.25 mm, is half the size of the SC connector.
 Mechanical Transfer Registered Jack (MT-RJ) Resembles an RJ-45 network connector and is less expensive and easier to work with than ST or SC.
Mechanical Transfer Registered Jack (MT-RJ) Resembles an RJ-45 network connector and is less expensive and easier to work with than ST or SC.
Figure 13-10 shows ST and SC connectors.
FIGURE 13-10The ST and SC connectors used with fiber-optic cable
Most LANs now connect to other LANs or through WAN connections to internetworks, such as the Internet. A variety of network connection devices connects networks. Each serves a special purpose, and a single device may contain two or more of these functions.
A repeater is a device used to extend the range of a network by taking the signals it receives from one port and regenerating (repeating) those signals to another port. Repeaters are available for various networks. For instance, on an Ethernet network, you would use an Ethernet repeater, and on a Wi-Fi network you would use a wireless repeater (often called a signal booster) to boost the signal between wireless networks. In both cases, the repeater must be at the appropriate level and speed for the network (Ethernet, Fast Ethernet, Gigabit Ethernet, 802.11b, 802.11g, 802.11n, etc.).
A bridge is a device used to connect two networks, and it passes traffic between them using the physical address of the destination device. Bridges segment large networks into smaller networks and only forward network traffic to the segment where the recipient station resides. A bridge is specific to the hardware technology in use. For instance, an Ethernet bridge looks at physical Ethernet addresses (MAC addresses) and forwards Ethernet frames with destination addresses that are not on the local network. Bridges are now seldom used since a switch functions as both a bridge and a hub.
A hub is a device that is the central connecting point of a classic 10BaseT Ethernet LAN. It is little more than a multiport repeater, because it takes a signal received on one port and repeats it on all other ports. An active hub will regenerate the signal and send it on to all devices connected to the network. A passive hub is simply a wiring panel or punch-down block for connecting or disconnecting devices.
Connections between networks usually require some form of routing capability. In the case of a connection to the Internet, each computer or device connected to the network requires a TCP/IP address. In order to reach a computer on another network, the originating computer must have a means of sending information to the other computer. To accomplish this, routes are established, and a router, a device that sits at the connection between networks, stores information about destinations.
A router is specific to one protocol suite. The type of router used to connect TCP/IP networks is an IP router, using routing protocols that work with the IP protocol. Routers use several specialized router protocols to update their list of routes dynamically, such as routing information protocol (RIP), a protocol that dates to the 1980s and is now essentially obsolete even though it has been updated a few times and most routers still support it. An IP router knows the IP addresses of the networks to which it connects and the addresses of other routers on those networks. At the least, a router knows the next destination to which it can transfer information.
Many routers include bridging circuitry, a hub, and the necessary hardware to connect multiple network technologies together, such as a LAN and a T1 network, or a LAN to any of the other broadband networks. The Internet has thousands of routers managing the connections between the millions of computers and networks connected to it. Figure 13-11 shows a router between a LAN and a WAN.
FIGURE 13-11 A router connecting a LAN to a T1 network
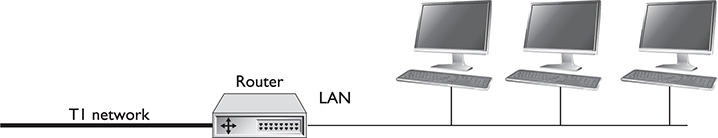
After the introduction of 100BaseT, the switch replaced the classic hub. This is a more intelligent device that takes an incoming signal and sends it only to the destination port. This type of switch is both a bridge and a hub. At one time switches were very expensive, but now small eight-port switches are inexpensive and commonly used, even in very small LANs. As always, each computer or other device in a network attaches to a switch of the type appropriate for the type of LAN. For example, computers using Ethernet cards must connect to an Ethernet switch; wireless devices attach wirelessly to a wireless hub, more often called a wireless access point (WAP) or wireless router. Devices may combine these functions, as in the case of a WAP or wireless router that includes an Ethernet switch (look for one or more RJ-45 connectors). This last scenario is very common.
In corporate networks with many clients, the sheer number of individual Ethernet cables running from individual PCs to routers is staggering. A patch panel can help keep the cable connections orderly by providing a central point into which the cables for many workstations can connect. See Figure 13-12. Some high-capacity switches also serve as patch panels, physically organizing a large number of cables as well as distributing local network data.
FIGURE 13-12 A patch panel (Photo: https://commons.wikimedia.org/wiki/File:In_Floor_Patch_Panel_Fiber.jpg [Creative Commons license])
Power over Ethernet (PoE) passes electrical power through twisted-pair Ethernet cabling. It allows one cable to serve as both data and electrical conduit to a device. It allows you to set up network devices in locations where there is no AC outlet, and power them via the same Ethernet cable that connects them to the network. PoE is popular for use with security cameras, paging systems, wall clocks that get the time from the network, and routers placed in out-of-the-way locations.
A switch that supports PoE has power injection built in. In other words, it is able to inject power into the cables that run to the PoE devices. A device called a midspan injector (or PoE injector) can be used to add PoE capability to regular non-PoE network switches and routers.
A wireless access point (WAP) allows wireless clients to connect to a wired network. Most access points also have built-in routing capability and, as such, are called wireless routers. Modern access points are configurable in “isolation mode,” which isolates wireless clients from one another, usually for security or privacy purposes.
Note that this discussion does not apply to DSL or cable modems. Computers are digital devices. Most local telephone lines are still analog. A modem allows computer-to-computer communication over analog telephone lines. Modems can be external devices that connect to a piece of computing equipment via a serial cable, or they can be internal expansion cards. Either way, they have at least one RJ-11 telephone jack so that they can plug into an analog phone line. Many network administrators still use modems today to remotely connect to network equipment (such as a router) in case the Internet connection fails or the router is misconfigured.
A firewall restricts or allows the flow of network traffic based on a set of rules. A firewall can be a hardware device or it can be software. Hardware firewalls run on network devices such as dedicated firewall appliances or routers or on a dedicated computer. Software firewalls run within an operating system and apply IP packet filtering, a service that inspects (or filters) each packet that enters or leaves the network; apply a set of security rules defined by a network administrator; and do not allow packets that fail inspection to pass between networks. When you change the rules to allow a certain type of traffic through a firewall, you are making an exception. To allow or deny traffic, you can base a firewall rule on many attributes, including:
 Type of packet Defined by port; TCP 80 (HTTP website) traffic might be allowed where TCP 25 (SMTP outbound e-mail) traffic might be denied.
Type of packet Defined by port; TCP 80 (HTTP website) traffic might be allowed where TCP 25 (SMTP outbound e-mail) traffic might be denied.
 Source/destination SMTP traffic to a specific host might be allowed, but all other destination SMTP hosts could be denied.
Source/destination SMTP traffic to a specific host might be allowed, but all other destination SMTP hosts could be denied.
Ethernet over Power (EoP) is a type of broadband Power Line Communication (PLC), an alternative to traditional networking. (Don’t confuse it with Power over Ethernet, PoE, described earlier in this overview of connection devices.) EoP uses the existing power lines in a home or office as conduits for network data, using adapters to translate and send the data. The HomePlug AV standard (IEEE 1901) is the specification that defines this type of equipment. At one point, EoP was poised to become an important technology, because it allowed people to create Ethernet networks without running cable through the walls of existing buildings. However, because of the popularity of Wi-Fi, it has never realized its potential.
Identifying Network Hardware
See what network hardware you can identify in your home, office, or school.
1. If you have a PC in your home and it has a connection to the Internet, locate and identify the network components.
2. If you use a dial-up connection, look for the modem, the telephone cable between the modem and the phone jack on the wall, and the RJ-11 connectors at either end of the telephone cable.
3. If you have a DSL connection, look for the Ethernet cable that runs between your computer and the hub/switch or modem. Examine the RJ-45 connectors on either end of the cable. The cable may connect to a single box that performs all of these functions.
4. If you have cable Internet service, look for an Ethernet cable between your computer and the cable modem, and then look for a coaxial cable between the modem and the wall connector.
5. At school or work, all you may find is an Ethernet cable connecting your computer to a wall jack that connects to the cable in the walls that connects to the network. Ask the network administrator to describe how you connect to the Internet through the network.

IT professionals preparing for the CompTIA A+ 220-901 and 220-902 exams must understand the basic concepts of computer networks. More in-depth knowledge is required for other exams, such as the CompTIA Network+, Security+, and Server+ exams. Basic concepts include network topologies—the geographic classifications of networks into LANs, MANs, and WANs. You must understand LAN technologies, such as Ethernet and Wi-Fi, and the various WAN connection methods, including dial-up and broadband WAN connections like ISDN, cable, DSL, satellite, and cellular. Be able to identify the most common cabling types, connectors, and common network adapters used in PCs.
Understand that TCP/IP is a protocol suite designed for the Internet and now used on most LANs and interconnected networks. Understand network-addressing concepts, including physical addresses assigned to network adapters and logical addresses assigned and used through the network protocols.
Understand the various addresses that are part of an IP configuration and their roles. These include the IP address and subnet mask of the network adapter, default gateway, and the DNS server, DHCP server, and WINS server addresses.
Be prepared to distinguish between various network hardware, including adapters, the transmission medium, network-to-network connection devices (repeater, bridge, and router), and devices for connecting computers to a network (hub and switch).
 TWO-MINUTE DRILL
TWO-MINUTE DRILL
Here are some of the key points covered in Chapter 13.
 Networks fall into several classifications, including PAN, LAN, MAN, and WAN.
Networks fall into several classifications, including PAN, LAN, MAN, and WAN.
 PAN technologies include the use of standards for wireless transmissions over very short distances. These include infrared (IR/IrDA), limited to about 1 meter, and Bluetooth, which has a range of up to 10 meters.
PAN technologies include the use of standards for wireless transmissions over very short distances. These include infrared (IR/IrDA), limited to about 1 meter, and Bluetooth, which has a range of up to 10 meters.
 Common LAN technologies include Ethernet in wired LANs and Wi-Fi in wireless LANs.
Common LAN technologies include Ethernet in wired LANs and Wi-Fi in wireless LANs.
 Ethernet has several implementations, each with increasing speeds, including 10BaseT at 10 Mbps, 100BaseT at 100 Mbps, 1000BaseT at 1 Gbps over UTP, and 10GBaseT with speeds up to 10 Gbps. In addition, fiber-optic cable supports very high speeds.
Ethernet has several implementations, each with increasing speeds, including 10BaseT at 10 Mbps, 100BaseT at 100 Mbps, 1000BaseT at 1 Gbps over UTP, and 10GBaseT with speeds up to 10 Gbps. In addition, fiber-optic cable supports very high speeds.
 The Wi-Fi standard 802.11a supports speeds up to 54 Mbps using the 5 GHz frequency. Other Wi-Fi standards are more popular. These include 802.11g, which also supports speeds of up to 54 Mbps but uses the same frequency (2.4 GHz) as its predecessor, 802.11b. 802.11g equipment is usually downward compatible with the slower and older 802.11b equipment.
The Wi-Fi standard 802.11a supports speeds up to 54 Mbps using the 5 GHz frequency. Other Wi-Fi standards are more popular. These include 802.11g, which also supports speeds of up to 54 Mbps but uses the same frequency (2.4 GHz) as its predecessor, 802.11b. 802.11g equipment is usually downward compatible with the slower and older 802.11b equipment.
 The 802.11n Wi-Fi standard provides speeds of up to 100 Mbps and beyond. The standard actually defines speeds of up to 600 Mbps. The 802.11ac standard hits 1 Gbps.
The 802.11n Wi-Fi standard provides speeds of up to 100 Mbps and beyond. The standard actually defines speeds of up to 600 Mbps. The 802.11ac standard hits 1 Gbps.
 Dial-up WAN connections are the slowest and require initiation of the connection every time a user wishes to connect to a remote resource.
Dial-up WAN connections are the slowest and require initiation of the connection every time a user wishes to connect to a remote resource.
 Broadband WAN connections, all offering speeds faster than dial-up, include cellular, ISDN, DSL, cable, T-carrier, satellite, line-of-sight wireless, PVC, VPN, and fiber.
Broadband WAN connections, all offering speeds faster than dial-up, include cellular, ISDN, DSL, cable, T-carrier, satellite, line-of-sight wireless, PVC, VPN, and fiber.
 The roles played by the computer on the network describe the network. The two most general roles are those of clients and servers.
The roles played by the computer on the network describe the network. The two most general roles are those of clients and servers.
 A network in which any computer can be both a client and a server is a peer-to-peer network.
A network in which any computer can be both a client and a server is a peer-to-peer network.
 A client/server network is one in which most desktop computers are clients and dedicated computers act as servers.
A client/server network is one in which most desktop computers are clients and dedicated computers act as servers.
 An NOS is an operating system that runs on a network server and provides file sharing and access to other resources, account management, authentication, and authorization services. Examples of NOSs are Microsoft Windows Server operating systems, Novell Server operating systems, and Linux.
An NOS is an operating system that runs on a network server and provides file sharing and access to other resources, account management, authentication, and authorization services. Examples of NOSs are Microsoft Windows Server operating systems, Novell Server operating systems, and Linux.
 A network client is software that requests services from compatible servers. Windows, macOS, and Linux, when installed on desktop computers that have a network connection, automatically install a basic network client.
A network client is software that requests services from compatible servers. Windows, macOS, and Linux, when installed on desktop computers that have a network connection, automatically install a basic network client.
 A protocol suite is a group of related protocols that work together to support the functioning of a network. TCP/IP is the dominant protocol suite as well as the protocol suite of the Internet.
A protocol suite is a group of related protocols that work together to support the functioning of a network. TCP/IP is the dominant protocol suite as well as the protocol suite of the Internet.
 TCP/IP supports small-to-large networks and interconnected networks called internetworks. The Internet is the largest internetwork.
TCP/IP supports small-to-large networks and interconnected networks called internetworks. The Internet is the largest internetwork.
 Network addressing occurs at both the physical level and the logical level. Every Ethernet network adapter from every Ethernet NIC manufacturer in the world has a unique physical address, also called a MAC address, which is 48 bits long and is usually shown in hexadecimal notation.
Network addressing occurs at both the physical level and the logical level. Every Ethernet network adapter from every Ethernet NIC manufacturer in the world has a unique physical address, also called a MAC address, which is 48 bits long and is usually shown in hexadecimal notation.
 Internet Protocol is concerned with logical addresses. An IPv4 address is 32 bits long and is usually shown in dotted-decimal notation, as in 192.168.1.41. IPv6 has 128-bit addressing, which theoretically supports a huge number of unique addresses.
Internet Protocol is concerned with logical addresses. An IPv4 address is 32 bits long and is usually shown in dotted-decimal notation, as in 192.168.1.41. IPv6 has 128-bit addressing, which theoretically supports a huge number of unique addresses.
 An IPv4 and IPv6 address configuration includes a subnet mask, which determines the host ID and network ID portions of the address. In addition, the IP configuration may include addresses for a default gateway, DNS server, primary WINS server, and DHCP server.
An IPv4 and IPv6 address configuration includes a subnet mask, which determines the host ID and network ID portions of the address. In addition, the IP configuration may include addresses for a default gateway, DNS server, primary WINS server, and DHCP server.
 In addition to an IP address, a packet will contain a port number identifying the service on the target computer that should receive the packet’s contents.
In addition to an IP address, a packet will contain a port number identifying the service on the target computer that should receive the packet’s contents.
 A network adapter provides the connection to the network medium. Network adapters (network interface cards) are available for the various networking technologies, such as Ethernet and Wi-Fi.
A network adapter provides the connection to the network medium. Network adapters (network interface cards) are available for the various networking technologies, such as Ethernet and Wi-Fi.
 Physical transmission media include twisted-pair, fiber-optic, and coaxial cable.
Physical transmission media include twisted-pair, fiber-optic, and coaxial cable.
 Networking requires various network connection devices. A repeater is a device used to extend the range of a network by taking the signals it receives from one port and regenerating (repeating) those signals to another port.
Networking requires various network connection devices. A repeater is a device used to extend the range of a network by taking the signals it receives from one port and regenerating (repeating) those signals to another port.
 A bridge is a device used to connect two networks and pass traffic between them based on the physical address of the destination device.
A bridge is a device used to connect two networks and pass traffic between them based on the physical address of the destination device.
 A hub is a device that is the central connecting point of a 10BaseT Ethernet LAN, with all network devices on a LAN connecting to one or more hubs.
A hub is a device that is the central connecting point of a 10BaseT Ethernet LAN, with all network devices on a LAN connecting to one or more hubs.
 More intelligent devices called switches or switching hubs now replace hubs on Ethernet networks. These take an incoming signal and send it only to the destination port.
More intelligent devices called switches or switching hubs now replace hubs on Ethernet networks. These take an incoming signal and send it only to the destination port.
 An IP router sits between networks and routes packets according to their IP addresses.
An IP router sits between networks and routes packets according to their IP addresses.
 Many routers combine routing and bridging, and connect multiple network technologies, such as a LAN and a T1 network.
Many routers combine routing and bridging, and connect multiple network technologies, such as a LAN and a T1 network.
 A patch panel is like a switchboard for networking connections, helping to organize cables.
A patch panel is like a switchboard for networking connections, helping to organize cables.
 Power over Ethernet (PoE) enables you to deliver power to devices through the same network cable that carries its data. A midspan injector can add PoE capability to non-PoE equipment.
Power over Ethernet (PoE) enables you to deliver power to devices through the same network cable that carries its data. A midspan injector can add PoE capability to non-PoE equipment.
 A wireless access point (WAP) is a wireless switch.
A wireless access point (WAP) is a wireless switch.
 A dial-up modem uses a telephone line to connect to a remote network.
A dial-up modem uses a telephone line to connect to a remote network.
 A firewall is hardware or software that restricts the flow of network traffic based on a set of rules.
A firewall is hardware or software that restricts the flow of network traffic based on a set of rules.
 Ethernet over Power (EoP), also called HomePlug AV, allows you to use the existing power wires in a building as LAN data cables.
Ethernet over Power (EoP), also called HomePlug AV, allows you to use the existing power wires in a building as LAN data cables.
The following questions will help you measure your understanding of the material presented in this chapter. Read all of the choices carefully because there might be more than one correct answer. Choose all correct answers for each question.
1. What is the standard for fiber-optic Ethernet WANs?
A. 10GBaseSR
B. 1000BaseT
C. Fast Ethernet
D. 10GBaseSW
2. Which of the following statements is true about a LAN versus a WAN?
A. A LAN spans a greater distance than a WAN.
B. A WAN spans a greater distance than a LAN.
C. A LAN is generally slower than a WAN.
D. A WAN is used within a home or within a small business.
3. Which of the following is a PAN technology?
A. Ethernet
B. Satellite
C. Bluetooth
D. 802.11a
4. What is the type of network that connects many private networks in one metropolitan community?
A. PAN
B. MAN
C. WAN
D. LAN
5. Of the following technologies, which is downward compatible with 802.11b?
A. 802.11a
B. 802.11g
C. Bluetooth
D. IrDA
6. Which of the following is usually the slowest WAN connection?
A. Dial-up
B. DSL
C. Cable
D. Satellite
7. Which of the following WAN technologies uses a network originally created for television transmissions?
A. DSL
B. Cellular
C. Cable
D. Dial-up
8. Which of the following is a term that describes the amount of time it takes a packet to travel from one point to another?
A. Bandwidth
B. KBps
C. Latency
D. MBps
9. Which statement describing IPv4 versus IPv6 differences is correct?
A. IPv6 uses a subnet mask, while IPv4 uses 128-bit addressing.
B. IPv4 uses 128-bit addressing, while IPv6 uses 32-bit addressing.
C. IPv4 uses 32-bit addressing, while IPv6 uses 128-bit addressing.
D. IPv4 uses double colons to indicate consecutive groups of 0s.
10. Which port is the correct one for Hypertext Transfer Protocol (HTTP) and web page transmission to a browser?
A. TCP 80
B. UDP 53
C. TCP 443
D. TCP 110
11. What protocol used on the Internet is concerned with the logical addressing of hosts?
A. TCP
B. IP
C. UDP
D. ARP
12. What protocol adds the old Microsoft naming system to TCP/IP?
A. NetBEUI
B. NetBIOS
C. DHCP
D. DNS
13. What divides an IP address into its host ID and network ID components?
A. Default gateway
B. DNS server
C. DHCP server
D. Subnet mask
14. A NIC has this type of a permanent address assigned to it by the manufacturer.
A. IP address
B. Physical address
C. Host ID
D. Automatic address
15. A packet with a destination address not on the local network will be sent to the address identified by which label in the IP configuration?
A. Default gateway
B. DNS server
C. DHCP server
D. Subnet mask
16. Which of the following statements is correct?
A. CAT5 cable can transmit 1 Gbps.
B. CAT6 cable can transmit 10 Gbps.
C. CAT5, CAT5e, and CAT6 segments can all be a maximum of 200 meters long.
D. CAT5e cable can transmit 10 Gbps.
17. Which of the following is not a network medium?
A. Plenum
B. Twisted-pair cable
C. Fiber-optic cable
D. Atmosphere
18. Which type of cable uses ST, SC, LC, or MT-RJ connectors?
A. STP
B. UTP
C. Fiber-optic
D. Coaxial
19. Thousands of this type of device exist on the Internet between networks, direct the traffic of the Internet using the destination IP address of each packet, and pass the packets to their destinations along the interconnected networks of the Internet.
A. Router
B. Modem
C. NIC
D. Hub
20. Which of these uses the electrical wires in a home or business network to transmit Ethernet data?
A. EoP
B. WAP
C. PoE
D. Repeater
1.  D. 10GBaseSW is the standard for fiber-optic Ethernet WANs.
D. 10GBaseSW is the standard for fiber-optic Ethernet WANs.
 A is incorrect because 10GBaseSR is the standard for 10-Gigabit Ethernet over twisted-pair cable. B is incorrect because 1000BaseT is the standard for 1 Gbps Ethernet on twisted-pair cable. C is incorrect because Fast Ethernet is the common name for 100BaseT, which carries data at 100 Mbps on twisted-pair cable.
A is incorrect because 10GBaseSR is the standard for 10-Gigabit Ethernet over twisted-pair cable. B is incorrect because 1000BaseT is the standard for 1 Gbps Ethernet on twisted-pair cable. C is incorrect because Fast Ethernet is the common name for 100BaseT, which carries data at 100 Mbps on twisted-pair cable.
2.  B. A WAN spans a greater distance than a LAN.
B. A WAN spans a greater distance than a LAN.
 A, C, and D are all incorrect because they are not true.
A, C, and D are all incorrect because they are not true.
3.  C. Bluetooth is a personal area network (PAN) technology used to connect devices and computers over very short distances.
C. Bluetooth is a personal area network (PAN) technology used to connect devices and computers over very short distances.
 A, B, and D are all incorrect because none of these is a PAN technology. Ethernet is a wired LAN technology, satellite is a WAN technology, and 802.11a is a set of WLAN standards.
A, B, and D are all incorrect because none of these is a PAN technology. Ethernet is a wired LAN technology, satellite is a WAN technology, and 802.11a is a set of WLAN standards.
4.  B. MAN, a metropolitan area network, is the type of network that connects many private networks in one community.
B. MAN, a metropolitan area network, is the type of network that connects many private networks in one community.
 A is incorrect because a PAN is a personal area network that only connects devices in a very small (usually a few meters) area. C is incorrect because this type a wide area network connects over long distances. D is incorrect because a local area network is limited to a distance of hundreds of meters and would not span an entire metropolitan community.
A is incorrect because a PAN is a personal area network that only connects devices in a very small (usually a few meters) area. C is incorrect because this type a wide area network connects over long distances. D is incorrect because a local area network is limited to a distance of hundreds of meters and would not span an entire metropolitan community.
5.  B. 802.11g is downward compatible with the slower 802.11b standard because they both use the 2.4 GHz bandwidth.
B. 802.11g is downward compatible with the slower 802.11b standard because they both use the 2.4 GHz bandwidth.
 A is incorrect because the 802.11a Wi-Fi standard operates in the 5 MHz band, which makes it totally incompatible with 802.11b. C is incorrect because Bluetooth is a standard for very short distances and is not downward compatible with 802.11b. D is incorrect because IrDA is a standard for very short-range infrared communications, which is totally incompatible with 802.11b.
A is incorrect because the 802.11a Wi-Fi standard operates in the 5 MHz band, which makes it totally incompatible with 802.11b. C is incorrect because Bluetooth is a standard for very short distances and is not downward compatible with 802.11b. D is incorrect because IrDA is a standard for very short-range infrared communications, which is totally incompatible with 802.11b.
6.  A. Dial-up is usually the slowest WAN connection, at an advertised rate of 56 Kbps but with a top actual rate of about 48 Kbps.
A. Dial-up is usually the slowest WAN connection, at an advertised rate of 56 Kbps but with a top actual rate of about 48 Kbps.
 B, C, and D are all incorrect because each of these is a broadband service with maximum speeds that go up to many times that of dial-up.
B, C, and D are all incorrect because each of these is a broadband service with maximum speeds that go up to many times that of dial-up.
7.  C. Cable is the WAN technology that uses a network originally created for television transmissions.
C. Cable is the WAN technology that uses a network originally created for television transmissions.
 A is incorrect because DSL uses the telephone network, not a network created for television transmissions. B is incorrect because cellular uses the cellular network, originally created for voice transmissions but which was upgraded to digital and can be used for broadband data transmissions. D is incorrect because dial-up uses the telephone network, not a network created for television transmissions.
A is incorrect because DSL uses the telephone network, not a network created for television transmissions. B is incorrect because cellular uses the cellular network, originally created for voice transmissions but which was upgraded to digital and can be used for broadband data transmissions. D is incorrect because dial-up uses the telephone network, not a network created for television transmissions.
8.  C. Latency is the term for the time it takes a packet to travel from one point to another. A is incorrect because bandwidth is the amount of data that can travel over a network within a given time.
C. Latency is the term for the time it takes a packet to travel from one point to another. A is incorrect because bandwidth is the amount of data that can travel over a network within a given time.
 B and D are both incorrect because these terms mean kilobytes per second and megabytes per second, respectively, which describe the amount of data that can travel over a network.
B and D are both incorrect because these terms mean kilobytes per second and megabytes per second, respectively, which describe the amount of data that can travel over a network.
9.  C. IPv4 uses 32-bit addressing, while IPv6 uses 128-bit addressing.
C. IPv4 uses 32-bit addressing, while IPv6 uses 128-bit addressing.
 A is incorrect because IPv4 uses 32-bit addressing. IPv6 can use a subnet mask also. B is incorrect because it is just the opposite. D is incorrect because it is IPv6 that uses the double colons to indicate consecutive groups of 0s.
A is incorrect because IPv4 uses 32-bit addressing. IPv6 can use a subnet mask also. B is incorrect because it is just the opposite. D is incorrect because it is IPv6 that uses the double colons to indicate consecutive groups of 0s.
10.  A. TCP 80 is the correct port number for HTTP and web page transmission to a web browser.
A. TCP 80 is the correct port number for HTTP and web page transmission to a web browser.
 B is incorrect because UDP 53 is the port for Domain Name Service used by clients to perform DNS queries against DNS servers. C is incorrect because TCP 443 is the port for secure web page transmission. D is incorrect because TCP 110 is the port for Post Office Protocol that retrieves e-mail from a POP3 mail server.
B is incorrect because UDP 53 is the port for Domain Name Service used by clients to perform DNS queries against DNS servers. C is incorrect because TCP 443 is the port for secure web page transmission. D is incorrect because TCP 110 is the port for Post Office Protocol that retrieves e-mail from a POP3 mail server.
11.  B. IP is the protocol used on the Internet that is concerned with the logical addressing of hosts.
B. IP is the protocol used on the Internet that is concerned with the logical addressing of hosts.
 A is incorrect because TCP is not concerned with the logical addressing of hosts. C is incorrect because UDP is not concerned with the logical addressing of hosts. D is incorrect because ARP is not concerned with the logical addressing of hosts.
A is incorrect because TCP is not concerned with the logical addressing of hosts. C is incorrect because UDP is not concerned with the logical addressing of hosts. D is incorrect because ARP is not concerned with the logical addressing of hosts.
12.  B. NetBIOS is the protocol that adds the old Microsoft naming system to TCP/IP.
B. NetBIOS is the protocol that adds the old Microsoft naming system to TCP/IP.
 A is incorrect because this old Microsoft network protocol suite had NetBIOS as just a part. C is incorrect because DHCP is the protocol used for automatically allocating IP addresses. D is incorrect because DNS is the protocol that supports Internet-style names.
A is incorrect because this old Microsoft network protocol suite had NetBIOS as just a part. C is incorrect because DHCP is the protocol used for automatically allocating IP addresses. D is incorrect because DNS is the protocol that supports Internet-style names.
13.  D. A subnet mask divides an IP address into its host ID and network ID components.
D. A subnet mask divides an IP address into its host ID and network ID components.
 A is incorrect because the default gateway is the name of the router address to which a computer directs packets with destinations beyond the local network. B is incorrect because the DNS server is where a network client sends queries to resolve DNS names into IP addresses. C is incorrect because the DHCP server is what automatically assigns IP addresses to DHCP client computers.
A is incorrect because the default gateway is the name of the router address to which a computer directs packets with destinations beyond the local network. B is incorrect because the DNS server is where a network client sends queries to resolve DNS names into IP addresses. C is incorrect because the DHCP server is what automatically assigns IP addresses to DHCP client computers.
14.  B. The physical address is the type of permanent address assigned to a NIC by the manufacturer.
B. The physical address is the type of permanent address assigned to a NIC by the manufacturer.
 A is incorrect because an IP address is not a permanent address but a logical address not permanently assigned to a NIC. C is incorrect because the host ID is the portion of an IP address that identifies the host. D is incorrect because an automatic address usually refers to an IP address assigned to a PC by a DHCP server.
A is incorrect because an IP address is not a permanent address but a logical address not permanently assigned to a NIC. C is incorrect because the host ID is the portion of an IP address that identifies the host. D is incorrect because an automatic address usually refers to an IP address assigned to a PC by a DHCP server.
15.  A. The default gateway is the address to which the router sends packets that have addresses not on the local network.
A. The default gateway is the address to which the router sends packets that have addresses not on the local network.
 B is incorrect because this server resolves DNS names. C is incorrect because the DHCP server assigns IP addresses automatically. D is incorrect because a subnet mask is not an address but a mask used to divide an IP address into its host ID and network ID components.
B is incorrect because this server resolves DNS names. C is incorrect because the DHCP server assigns IP addresses automatically. D is incorrect because a subnet mask is not an address but a mask used to divide an IP address into its host ID and network ID components.
16.  B. CAT6 can indeed transmit 10 Gbps.
B. CAT6 can indeed transmit 10 Gbps.
 A is incorrect because CAT5 can only transmit 100 Mbps. C is incorrect because each of these cable categories requires a repeater or a switch at 100 meters. D is incorrect because CAT5e can only transmit 1 Gbps.
A is incorrect because CAT5 can only transmit 100 Mbps. C is incorrect because each of these cable categories requires a repeater or a switch at 100 meters. D is incorrect because CAT5e can only transmit 1 Gbps.
17.  A. Plenum is not a network medium, but rather a characteristic of certain network media (cables), indicating the cable sheath is fire resistant and appropriate to run in plenum space.
A. Plenum is not a network medium, but rather a characteristic of certain network media (cables), indicating the cable sheath is fire resistant and appropriate to run in plenum space.
 B, C, and D are all incorrect because all are networking media.
B, C, and D are all incorrect because all are networking media.
18.  C. Fiber-optic cable uses ST, SC, LC, or MT-RJ connectors.
C. Fiber-optic cable uses ST, SC, LC, or MT-RJ connectors.
 A, B, and D are all incorrect because they do not use ST, SC, LC, or MT-RJ connectors.
A, B, and D are all incorrect because they do not use ST, SC, LC, or MT-RJ connectors.
19.  A. A router is the device that exists on the Internet and passes IP packets from many sources to destinations along the Internet.
A. A router is the device that exists on the Internet and passes IP packets from many sources to destinations along the Internet.
 B is incorrect because a modem does not pass packets along the Internet, although it is a beginning point for a single computer to send packets. C is incorrect because a network interface card (NIC) is simply a device for connecting a single computer to a network. D is incorrect because a hub is an older device used at the heart of a LAN but not an Internet device.
B is incorrect because a modem does not pass packets along the Internet, although it is a beginning point for a single computer to send packets. C is incorrect because a network interface card (NIC) is simply a device for connecting a single computer to a network. D is incorrect because a hub is an older device used at the heart of a LAN but not an Internet device.
20.  A. Ethernet over Power (EOP) uses power lines for Ethernet networking.
A. Ethernet over Power (EOP) uses power lines for Ethernet networking.
 B is incorrect because a wireless access point (WAP) does not user power lines. C is incorrect because Power over Ethernet (PoE) delivers electrical power over UTP Ethernet cable. D is incorrect because a repeater amplifies an Ethernet signal via standard Ethernet cable, not power lines.
B is incorrect because a wireless access point (WAP) does not user power lines. C is incorrect because Power over Ethernet (PoE) delivers electrical power over UTP Ethernet cable. D is incorrect because a repeater amplifies an Ethernet signal via standard Ethernet cable, not power lines.