 901: 2.4 Explain common TCP and UDP ports, protocols, and their purpose
901: 2.4 Explain common TCP and UDP ports, protocols, and their purposeCERTIFICATION OBJECTIVES
 901: 2.4 Explain common TCP and UDP ports, protocols, and their purpose
901: 2.4 Explain common TCP and UDP ports, protocols, and their purpose
 902: 1.5 Given a scenario, use Windows Control Panel utilities
902: 1.5 Given a scenario, use Windows Control Panel utilities
 902: 1.6 Given a scenario, install and configure Windows networking on a client/desktop
902: 1.6 Given a scenario, install and configure Windows networking on a client/desktop
 902: 2.3 Identify basic cloud concepts
902: 2.3 Identify basic cloud concepts
 902: 2.4 Summarize the properties and purpose of services provided by networked hosts
902: 2.4 Summarize the properties and purpose of services provided by networked hosts
 Two-Minute Drill
Two-Minute Drill
Q&A Self Test
In this chapter, you will learn about the services, protocols, and applications that comprise the world’s largest network: the Internet. You’ll learn how the Internet addresses clients and servers, what protocols make activities like the Web and e-mail possible, and what kinds of servers businesses and organizations make available online to provide the services that people rely on in their daily lives. You’ll also learn what cloud computing entails, and the levels of services that cloud providers offer.
CERTIFICATION OBJECTIVES
 901: 2.4 Explain common TCP and UDP ports, protocols, and their purpose
901: 2.4 Explain common TCP and UDP ports, protocols, and their purpose
 902: 2.4 Summarize the properties and purpose of services provided by networked hosts
902: 2.4 Summarize the properties and purpose of services provided by networked hosts
This section examines the nuts and bolts of the Internet, including some of the common protocols and services listed in CompTIA A+ 901 exam objective 2.4. It also looks at the roles of various types of servers listed in 902 exam objective 2.4, including web servers, file servers, mail servers, proxy servers, and so on. This section also covers Internet appliance concepts and legacy/embedded systems, also listed in 902 exam objective 2.4.
You probably use the Internet every day as a consumer, but there’s a lot more to it than meets the eye. In this section you’ll learn about the physical structure of the Internet, how service providers make a living while helping people connect, and how domain names, IP addresses, protocols, and services create a balanced online ecosystem. You’ll also learn about the types of Internet-based servers, and about embedded systems and Internet appliances.
The Internet is a huge, global wide area network (WAN), with the hardware provided collaboratively by businesses all over the world. No one company “owns” the Internet because it is a joint venture. Physically the Internet’s layout resembles a mesh of routers, with many alternate paths available between any two points. This redundancy makes the Internet a fairly reliable and stable network, because even if many pathways are blocked at once, there is nearly always a way for a packet to reach its destination.
The group of main routes of the Internet, its super-highway system, is referred to as the backbone. This backbone is composed of high-speed fiber-optic networks that join together at connections called network access points. A small number of companies own these high-speed backbone networks; those companies are called Tier 1 providers. Tier 1 providers work cooperatively; they do not charge each other fees to connect to one another. You probably don’t know the names of these Tier 1 providers, because they don’t sell anything directly to the public, so they don’t advertise where you would be likely to see it.
Tier 1 providers make their money from Tier 2 providers, who own smaller, regional Internet segments. The big-name companies in this arena, like Earthlink and Comcast, are Tier 2 providers. Tier 2 providers manage their own small segments of the Internet, and they rent the use of their segments to individuals on a monthly basis, functioning as Internet service providers (ISPs). They also sell connectivity to smaller providers, Tier 3 providers, who are even smaller and more localized.
The lesson from that overview of the tier system is simply that you can’t connect to the Internet directly, all by yourself. You have to contract with an ISP, which is either a Tier 2 or Tier 3 provider, and which grants you the right to connect into their little segment of the Internet and from there gain access to the rest of the world.
As we mentioned in the preceding section, an Internet service provider (ISP) is a company in the business of providing Internet access to users. When you connect to the Internet from your home or office, you connect through your ISP. While you are on the Internet, your ISP relays all data transfers to and from locations on the Internet. Traditionally, ISPs were phone companies, but now ISPs include cable companies and organizations that lease phone or cable network usage.
The ISP you select will depend on the type of connection available to you. For instance, a cellular provider will be your ISP if you chose to connect to the Internet via the cellular network, and a cable company will be your ISP if you connect over the cable network. As for DSL, at first local phone companies mainly offered this service, but many other companies now offer DSL using the telephone network, and some telephone companies are now offering Internet access via their fiber-optic networks. Meanwhile, some ISPs specialize in satellite Internet access. See Chapter 13 for in-depth discussions of connectivity types.
In addition to Internet connection services, ISPs now provide a number of other services. Some of these services, such as e-mail, are free, and the cost of others, such as hosting web servers, is based on the complexity of the web services provided. For example, an e-commerce site in which you sell products and maintain customer lists is a service that would come at additional cost. You also are not limited to purchasing Internet services from your ISP. You now have a huge variety of sources for all of these services.
Whenever you visit a website, you enter or select the Uniform Resource Locator (URL) of the website you want to visit—in other words, its web address. A URL consists of a domain name, such as microsoft.com, plus additional information that points to a particular folder and page on that website, like this:
https://www.microsoft.com/en-us/windows
Let’s break down that URL into its component parts.
We’ll start at the beginning. A URL starts with the protocol, which is https in the example. HTTPS is a secure form of Hypertext Transfer Protocol, the main protocol used for web pages.
The next part, www.microsoft.com, is known as a fully qualified domain name (FQDN). It’s called that because it contains both a host name (www) and a domain (microsoft.com). Let’s look at these parts separately:
 The host name is the name of the server or service within the domain. Some small websites have only one host, and it’s usually www (traditional for websites). However, larger sites may have several hosts, representing different services or services. For example, Microsoft has support.microsoft.com and www.microsoft.com, to name only two of many.
The host name is the name of the server or service within the domain. Some small websites have only one host, and it’s usually www (traditional for websites). However, larger sites may have several hosts, representing different services or services. For example, Microsoft has support.microsoft.com and www.microsoft.com, to name only two of many.
 The domain includes a top-level domain, or TLD (in this case, com), and a second-level domain, or SLD (in this case, microsoft). The top-level domain describes the general category of domain; com is short for “commercial,” for example. There are several dozen top-level domains, with names like edu (for education), gov (for government), mil (for military), and org (for organization), as well as individual country codes like ca (for Canada) and uk (for United Kingdom).
The domain includes a top-level domain, or TLD (in this case, com), and a second-level domain, or SLD (in this case, microsoft). The top-level domain describes the general category of domain; com is short for “commercial,” for example. There are several dozen top-level domains, with names like edu (for education), gov (for government), mil (for military), and org (for organization), as well as individual country codes like ca (for Canada) and uk (for United Kingdom).
 The ending part of the address is the file path of the host’s server—in this case, en-us/windows. Just like in local file paths, slashes separate directories. On the host server, there is a folder called en-us, and within that is a folder called windows.
The ending part of the address is the file path of the host’s server—in this case, en-us/windows. Just like in local file paths, slashes separate directories. On the host server, there is a folder called en-us, and within that is a folder called windows.
![]()
If you leave off the host name when typing a URL into a browser, the browser will usually assume www as the host name.
The irony of all these text-based names is that the Internet (as a computer network) doesn’t actually use any of them. They are a figment of our collective imagination. The real addresses on the Internet are IP addresses, assigned by the Internet Assigned Numbers Authority (IANA). So how do the IP addresses and domain names connect to one another? They do so through a series of servers called Domain Name System (DNS) servers.
A DNS server receives a domain name and looks it up in a giant table it maintains to find its IP address match. Then it provides that IP address to the requesting computer. That’s all it does, millions of times a minute, 24/7. There are thousands of DNS servers all over the world performing this task, all at once.
Maintaining a complete table of every IP address and domain name would be nearly impossible for any single DNS server, no matter how capable, and looking up addresses would take too long. Therefore, the work of DNS servers is split up according to top-level domains. One DNS server only parses between top-level domains, routing a request to the appropriate server. For example, a server says “microsoft.com, that’s a dot-com, so I’ll send it to the dot-com DNS server.” Then another server receives the request that has a table of only the dot-com IP addresses and domains. It looks up the IP address for the requested domain, and sends it back to the requesting computer.


There are many Internet services, enabling activities like web browsing, mail delivery, and instant messaging. In this section, we will describe a few of these services. Some of them have been covered elsewhere in the book, but we provide them here for easy study reference, all being related to Internet usage.
Simple Mail Transfer Protocol (SMTP) transfers e-mail messages between mail servers (discussed later in this chapter). Clients also use this protocol to send e-mail to mail servers. When configuring a computer to access Internet e-mail, you will need the address or name of an SMTP server to which your mail client software will send mail.
Post Office Protocol (POP) is the protocol used to allow client computers to pick up (receive) e-mail from mail servers. The current version is POP3.
Internet Message Access Protocol (IMAP) is a protocol used by e-mail clients for communicating with e-mail servers. IMAP allows users to connect to e-mail servers and not only retrieve e-mail, which removes the messages from the server as they do with the POP protocol, but also manage their stored messages without removing them from the server. The current version is IMAP4.
Hypertext Markup Language (HTML) is the language of web pages. Web designers use the HTML language to create web page code, which your web browser converts into the pages you view on your screen.
The World Wide Web (WWW) is the graphical Internet consisting of a vast array of documents located on millions of specialized servers worldwide. The Hypertext Transfer Protocol (HTTP) is the information transfer protocol of the Web. Included in HTTP are the commands web browsers use to request web pages from web servers and then display them on the screen of the local computer.
The Secure Sockets Layer (SSL) is a protocol for securing data for transmission by encrypting it. Encryption is the transformation of data into a code that no one can read unless they have a software key or password to convert it back to its usable form (decrypt it). When you buy merchandise online, you go to a special page where you enter your personal and credit card information. These web merchants almost universally use some form of SSL encryption to protect the sensitive data you enter on this page. When you send your personal information over the Internet, it is encrypted and only the merchant site has the key to decrypt it. As with most computing technologies, there are improvements to SSL, and a newer encryption technology, Transport Layer Security (TLS), for secure transmission over the Internet.
Hypertext Transfer Protocol over Secure Sockets Layer (HTTPS) is a protocol that encrypts and decrypts each user page request, as well as the pages downloaded to the user’s computer. The next time you are shopping on a website, notice the address box in your browser. You will see the Uniform Resource Locator (URL) preceded by “HTTP” until you go to pay for your purchases. Then the prefix changes to “HTTPS,” because the HTTPS protocol is in use on the page where you will enter your personal information and credit card number.
At one time, all access to mainframes or minicomputers was through specialized network equipment called terminals. At first, a terminal was not much more than a display, a keyboard, and the minimal circuitry for connecting to the mainframe. People called it a “dumb terminal.” With the growing popularity of PCs in the 1980s, it wasn’t unusual to see both a terminal and a PC on a user’s desktop, taking up a great deal of space. Eventually, by adding both software and hardware to a PC, the PC could emulate a terminal and the user would switch it between terminal mode and PC mode.
The Telnet utility provides remote terminal emulation for connecting to computers and network devices running responsive server software, and it works without concern for the actual operating system running on either system. The original Telnet client was character based, and it was a popular tool for network administrators who needed to access and manage certain network equipment, such as the routers used to connect networks.
Although Telnet supports the use of credentials for a terminal emulation session, it sends those credentials in clear text that many methods can pick up, such as a device that connects to the network and collects the traffic. To overcome that limit, the Secure Shell (SSH) service has replaced Telnet because it secures all traffic using a tunneling technique similar to a VPN (described in Chapter 14). It is used to connect to terminal servers that require sophisticated security protocols.
File Transfer Protocol (FTP) is a protocol for computer-to-computer (called host-to-host) file transfer over a TCP/IP network. The two computers do not need to run the same operating system; they only need to run the FTP service on the server computer and the FTP client utility on the client computer. FTP supports the use of user names and passwords for access by the FTP client to the server. FTP is widely used on the Internet for making files available for download to clients.
Another file transfer method is secure copy (SCP), which uses Secure Shell (SSH) for encrypting data. SCP lacks the file management capabilities of other methods, such as Secure FTP (SFTP). Therefore, SFTP, which also uses SSH, is often preferred.
The Internet Relay Chat (IRC) protocol supports text messaging over a TCP/IP internetwork in real time, something commonly called chat. The latest version is Internet Relay Chat web extension (IRCwx), but it is still widely referred to as IRC. Groups of people can chat simultaneously using IRC, or it can be used between just two people.
The Network News Transfer Protocol (NNTP) is used by news servers that support newsgroups, to which users can subscribe. Using news reader software, the client to the news server, a subscriber connects and selects articles to read.
Windows computers (and many others worldwide) keep their date and time settings up to date thanks to a time service. Network Time Protocol (NTP) is an Internet protocol that has been improved upon over its 30-year lifespan as a service that synchronizes a computer’s real-time clock (described in Chapter 3) with a network time server. Windows is configured to synchronize with an Internet-based time server. To view the time server settings on your computer, open the Control Panel Date and Time applet and click the Internet Time tab. The time server for the Windows computers in our office is time-a.nist.gov. You can select another time server by clicking the Change Settings button on the Internet Time tab.
Often, when you create a new account of almost any type on the Internet, after you have created your user name (often an e-mail address) and password, you may encounter a challenge test—a test that a human can easily pass but a computer cannot. You enter a response to continue. A popular type of challenge-response is Completely Automated Public Turing test to tell Computers and Humans Apart (CAPTCHA). A CAPTCHA usually consists of an image of one or two hard-to-read words, or at least a string of characters. To pass the test and proceed with creating your new account, you must enter the characters you see into a box. This ensures that a computer program is not attempting to automatically create accounts for nefarious reasons, such as for sending spam. To learn more about CAPTCHA, point your browser to www.captcha.net.
Servers are essential to Internet operation. Different kinds of servers perform different important roles in your Internet experience, and you probably don’t even notice what kind of server is serving you at any given moment. For example, the DNS server (discussed earlier in the “Domain Names, IP Addresses, and DNS Servers” section) makes it possible for you to visit websites by typing user-friendly, text-based domain names instead of having to remember an IP address consisting of a long string of numbers.
Make sure you understand the role of each of these server types. We cover them here in the Internet chapter because the majority of them pertain to the Internet, but several of these could be part of any network, not necessarily an Internet-enabled one.
While the World Wide Web (the Web) is just one on the many services that exist on the Internet, it alone is responsible for most of the huge growth in Internet use that began after the Web’s introduction in the 1990s. Web technologies changed the look of Internet content from all text to rich and colorful graphics. A web server provides the graphical content, called web pages, that we access by client software, called a web browser. There are many choices of web server software, but the most popular may be Apache HTTP Server, open source software that runs on a wide range of operating systems including Windows and several versions each of Linux and UNIX.
Microsoft’s web server software, Internet Information Services (IIS), only runs on Windows and supports the traditional HTML content as well as the transfer services HTTP and HTTPS web transfer services. It also supports other services, such as File Transfer Protocol (FTP), Simple Mail Transfer Protocol (SMTP), and Network News Transfer Protocol (NNTP).
A file server, as the name implies, makes files available to users. There are file servers on business networks that deliver private files to employees, and there are file servers on the Internet that provide the same service to the public, or to users who have the appropriate credentials with which to log in.
One common type of file server uses the FTP protocol (File Transfer Protocol), and is referred to as an FTP server. An FTP server can be open to the public to log into via an anonymous connection, or can require a user name and password. As you learned in Chapter 14, FTP is not particularly robust in security, so some FTP servers use SFTP (Secure FTP) instead.
Users can access an FTP server via most web browsers, although the interface may be somewhat awkward. Most people who use FTP servers frequently use special FTP software, such as the free program FileZilla.
A print server manages multiple printers that connect to it, and makes those printers available to users. Print servers are much more common on business networks than on the Internet. Part of a print server’s job is to hold the incoming print jobs in memory until they can be parsed out to the available printers. A print server can be a full-fledged computer with printers attached to it, or it can be a network appliance that’s basically just a box with a network connection and some printer ports. In the latter case, you would configure the print server by talking to it via a web browser using its IP address.
As you learned in Chapter 14, a DHCP server assigns IP addresses to clients that request them. Your ISP may have a DHCP server that it uses to assign IP addresses to its customers, providing dynamic IP addressing for Internet usage. That’s the norm, because it is most efficient. Unused IP addresses can be dynamically assigned to other customers whenever they become available. An alternative is a static IP address assignment, which you would want if you were hosting your own web server. Most ISPs charge more if you want that.
We talked about DNS servers earlier in this chapter; recall that they translate between IP addresses and domain names. There are DNS servers all over the Internet, publicly available for use. The use of a DNS server is invisible to the end user.
A mail server manages e-mail accounts. A company might have its own e-mail server, for example, that stores incoming messages for each user and then forwards them to the individual client PC whenever that user’s e-mail application connects to the server. (That’s called a store-and-forward system.) Similarly, your ISP has its own mail servers that receive mail on your behalf and then deliver it to you when you open your e-mail program and connect. Some ISPs have a single mail server for both incoming and outgoing mail; others have two separate servers (more common).
When you configure an e-mail application, you might need to enter the addresses of your mail server(s). These are usually three-part names with the parts separated by periods, like this: pop.mymail.com. The incoming mail servers are usually either POP or IMAP, and the outgoing mail server is usually SMTP. You learned about these and other protocols earlier in this chapter, in “Internet Services and Protocols.”
An authentication server is in charge of logging users into and out of a secure system. Corporate networks use authentication servers to allow users to access networked computers on a domain; if you sign in to your company’s network each morning at work, you can thank an authentication server. The Internet also has authentication servers. For example, if you sign into your account at an online store like Amazon.com, an authentication server checks your credentials and grants you access.
In many instances, an Internet connection includes a proxy server, a network service that handles the requests for Internet services, such as web pages, files on an FTP server, or mail for a proxy client, without exposing that client’s IP address to the Internet. There is specific proxy server and client software for each type of service. Most proxy servers combine these services and accept requests for HTTP, FTP, POP3, SMTP, and other types of services. The proxy server will often cache a copy of the requested resource in memory, making it available for subsequent requests from clients without having to go back to the Internet.
A client PC can be configured to use a specific proxy server. Some content filtering programs do that, for example—they set the PC to go through a proxy server online that only allows “clean” content through, according to the rules of the filtering. Some ISPs also recommend you use their proxy server for better performance. Satellite Internet providers sometimes provide a proxy server on which commonly accessed pages are cached. To learn how to configure a Windows client to use a proxy server, see “Using a Proxy Server,” later in this chapter.
CompTIA A+ 902 exam objective 2.4 lists legacy/embedded systems. While it’s not clear what CompTIA may be referring to here, we surmise that they want you to be aware that there are embedded systems nearly everywhere you look around you, and that there are servers all over the world that talk to them.
Most people think of the typical desktop or laptop PC when they picture an Internet connection, or perhaps a smartphone or tablet connection. All those are great for single-user Internet connectivity, of course, but a wide variety of devices connect to the Internet that you might not think of, from street lights and traffic signals to wristwatches and refrigerators. These computing components are called embedded systems. Believe it or not, it is estimated that 98 percent of all microprocessors manufactured today are for embedded systems, not for personal computers. For example, there’s probably a microprocessor in your car that can report error codes to a technician, and in some cases can even upload those error codes to a server.
The “legacy” part may refer to the fact that these systems typically stay in service for many years, long past their technology being state-of-the-art. One of the dangers of a legacy system is that it may be more subject to hacking because it lacks the latest security precautions. For example, an ATM running on Windows XP is (theoretically) more easily hacked than one running Windows 10, because support for Windows XP ended in 2014 and Microsoft has not released any new security patches for it.
There are two different meanings to the term “Internet appliance.” If you enter the term into your search engine of choice, you will probably find that an Internet appliance is described as a consumer device whose main function is to provide easy access to Internet services. A modern example of this might be a Chromebook, for example—a lightweight, skimpily equipped laptop that runs Chrome OS and that does very little except connect to the Internet.
However, if you look at the subtopics under “Internet appliance” in A+ 902 exam objective 2.4, you’ll realize that the preceding definition is not what CompTIA means. Instead, the exam objective is referring to a class of server applications and services designed to protect servers (and thereby protect users). While as a PC technician you will not be called upon to set up or configure such services, you should understand what they are and what they do. The objectives specifically refer to three kinds of Internet appliance: IDS, IPS, and UTM.
An intrusion detection system (IDS) is a security application that monitors packets, looking for evidence of security intrusions such as worms, viruses, and password-cracking attempts. Even though IDS is listed under the umbrella of Internet appliances, an IDS is useful on any network, not just on the Internet. An IDS can’t take direct action to prevent an intrusion, but it can report what it detects to another application, like a firewall, and can signal to a human network administrator to look out for a problem.
An intrusion prevention system (IPS) is similar to an IDS in that it also actively monitors network traffic, but it has more muscle behind it—an IPS can stop an attack on its own. That makes it a more effective tool in the fight against malicious attacks, but it also can bog down the network, so it’s not used on systems where latency can cause a problem.
Unified threat management (UTM) is the principle of creating a unified package of appliances that work together to reduce the threat of harm from attacks. A UTM solution might include IDS, IPS, VPN, firewalls, antimalware applications, and other tools.
CERTIFICATION OBJECTIVES
 902: 1.5 Given a scenario, use Windows Control Panel utilities
902: 1.5 Given a scenario, use Windows Control Panel utilities
 902: 1.6 Given a scenario, install and configure Windows networking on a client/desktop
902: 1.6 Given a scenario, install and configure Windows networking on a client/desktop
In this section, we cover the Internet options listed under CompTIA A+ 902 exam objective 1.5. The specific items listed in the objective are actually the names of tabs in the Internet Options dialog box, and we go through that dialog box tab by tab here. One of the settings in that dialog box deals with using a proxy server, so we use that opportunity to cover the proxy settings topic listed under 902 exam objective 1.6.
When it comes to Internet-related settings, Windows is merciful to PC techs, providing most of the available settings in one place: the Internet Options (or Internet Properties) dialog box. This dialog box contains many important settings that affect the user’s Internet usage experience, including security, privacy, connectivity, and convenience.
To access the Internet Options dialog box, you can use either of these methods:
 Open the Internet Explorer browser and then choose Tools | Internet Options.
Open the Internet Explorer browser and then choose Tools | Internet Options.
 Open the Control Panel and choose Network and Internet | Internet Options.
Open the Control Panel and choose Network and Internet | Internet Options.
![]()
The dialog box has a different title depending on the method you choose for opening it. When opening through IE, it’s Internet Options; when opening through the Control Panel, it’s Internet Properties. The dialog box content is the same either way.
Some of the settings in this dialog box pertain only to the Internet Explorer browser; they don’t affect Windows in general. For example, if you delete the browsing history, it’s deleted only for IE, not for any other browsers you might have installed. Other settings affect your entire Internet connection, regardless of browser, like the proxy server setting.
The Internet Options dialog box contains seven tabbed pages, and in the following sections we look at each of them in depth.
On the General Settings tab, shown in Figure 15-1, there are many settings that affect the overall operation and appearance of Internet Explorer.
FIGURE 15-1 The General tab of the Internet Options dialog box

 Home Page You can specify the URL of the page that you want to always open when you start IE. You can specify additional pages to have multiple tabs open at startup; place each URL on its own line in the Home Page box.
Home Page You can specify the URL of the page that you want to always open when you start IE. You can specify additional pages to have multiple tabs open at startup; place each URL on its own line in the Home Page box.
![]()
An easy way to set a home page is to display that page and then, on the General tab, click Use Current.
 Startup Choose whether to start with the home page (specified previously) or with the tabs from the last session.
Startup Choose whether to start with the home page (specified previously) or with the tabs from the last session.
 Tabs Click the Tabs button to open the Tabbed Browser Settings dialog box. From here you can fine-tune how tabs are used. For example, you can choose what to display on a new tab when opened, and you can enable tab groups.
Tabs Click the Tabs button to open the Tabbed Browser Settings dialog box. From here you can fine-tune how tabs are used. For example, you can choose what to display on a new tab when opened, and you can enable tab groups.
 Browsing History You can clear your browsing history by clicking Delete and specifying in the Delete Browsing History dialog box what information you want to clear. See Figure 15-2. The Settings button in this section opens the Website Data Settings dialog box, where you can control how history data is cached to your hard drive. For example, you can set a limit for the size of temporary Internet files, and you can choose how many days of browsing history should be retained.
Browsing History You can clear your browsing history by clicking Delete and specifying in the Delete Browsing History dialog box what information you want to clear. See Figure 15-2. The Settings button in this section opens the Website Data Settings dialog box, where you can control how history data is cached to your hard drive. For example, you can set a limit for the size of temporary Internet files, and you can choose how many days of browsing history should be retained.
FIGURE 15-2 You can clear your browsing history, both for privacy and to save disk space.

 Appearance The buttons in this section enable you to change how Internet Explorer appears. You can control the colors, languages, fonts, and accessibility.
Appearance The buttons in this section enable you to change how Internet Explorer appears. You can control the colors, languages, fonts, and accessibility.
Security in a browser context means the ability to prevent your computer from being harmed by malware. When you crank up the security settings to a high level, you minimize the chance that visiting a website with malicious code will infect your computer and cause problems. High security settings may prevent some websites from performing as intended, though; for example, some shopping sites won’t work with security settings at their highest levels.
The security zones feature of the Security tab (see Figure 15-3) allows you to differentiate between risky sites and safe ones. A security zone is a group of settings that is applicable to a certain trust level for websites. There are four zones: Internet, Local Intranet, Trusted Sites, and Restricted Sites. Internet is the default zone. The other three zones enable you to assign websites to them. To control which sites are in a zone, click the zone and then click the Sites button. Using zones enables you to have different security settings for sites that you trust, like your banking institution, and sites that you don’t trust, like an adult content site (not that you would ever visit one of those).
FIGURE 15-3 Change the security settings for a particular zone.
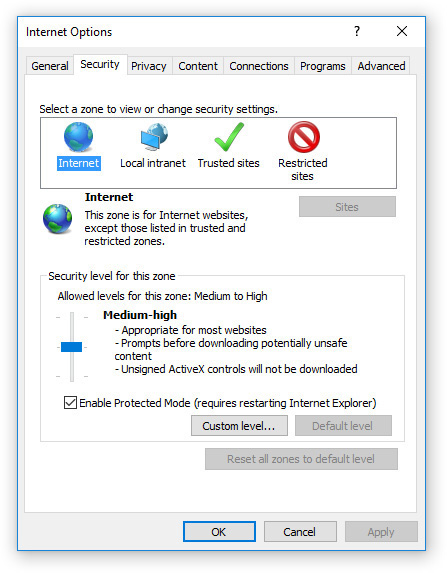
To change the security level for a zone, click the zone icon at the top, and then drag the slider bar up or down. You can also click Custom Level and fine-tune the security settings for the chosen zone.
Privacy in a browser context means the ability to limit the amount of your personal information that gets shared with others. This can include your browsing history, your location, and any information stored in cookies. You can choose which information you want to share through the Privacy tab (see Figure 15-4).
A cookie is a small text file stored on your computer that remembers your settings for a particular website. If you ever revisit a website where you’ve previously signed in and the page greets you by name, that’s a cookie at work.
Cookies come from two different sources. A first-party cookie comes from the website you are actually visiting. First-party cookies can actually be helpful. A third-party cookie comes from another source, such as an advertisement on the web page. Third-party cookies have no benefit to you as a user.
On the Privacy tab, you can click the Advanced button to open the Advanced Privacy Settings dialog box. From there you can choose how to handle first-party and third-party cookies. Your choices are to allow them, block them, or prompt each time one tries to write to your hard disk. You can click the Sites button on the Privacy tab to open a dialog box where you can indicate certain websites to always allow or always block from using cookies.
Also on the Privacy tab you can allow or prevent websites from requesting your physical location, and you can enable and configure the Pop-Up Blocker feature. Click the Settings button next to Pop-up Blocker to open a dialog box where you can allow certain websites to use pop-ups, while continuing to forbid most websites in general from doing so. You can also set an overall blocking level (Medium is the default).
In Figure 15-4 notice that you can choose whether to disable toolbars and extensions in InPrivate mode. This is a special high-privacy browsing mode that IE provides. You might use it when visiting a website that you don’t trust, for example, or one that you don’t want any record to be made of your having visited. By default this mode disables all toolbars and extensions. However, if there’s an app on the website that requires a certain extension to be loaded, you might need to allow toolbars and applications.
FIGURE 15-4 On the Privacy tab you can control the use of cookies and pop-ups.
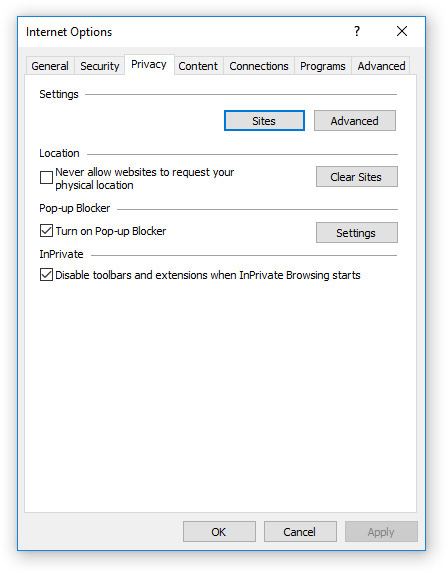
To use InPrivate browsing, press ctrl-shift-p, or press alt to see the menu bar and then choose Tools | InPrivate Browsing.
On the Content tab (see Figure 15-5), you can control what security certificates are allowed, and you can view the certificates and publishers you have chosen to trust. You can also clear the SSL state, so that any security that is currently in effect must be reauthenticated.
FIGURE 15-5 On the Content tab you can control security certificates, AutoComplete, and feed settings.
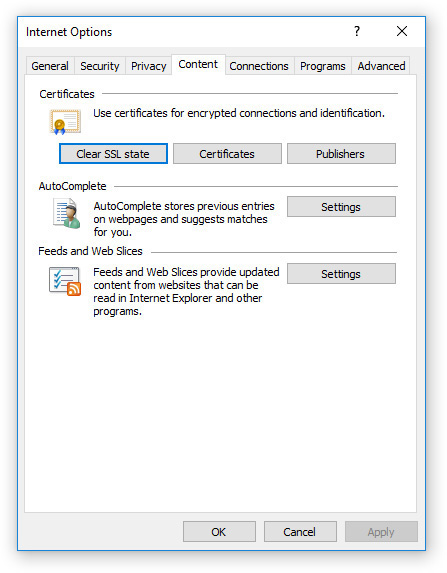
Also on the Content tab you can manage AutoComplete, which is the setting that fills in previously typed data for you after you type the first few letters of it. It’s very handy, but it can also be a privacy concern if you don’t want someone who sits down at your computer to see previous information that’s been saved, like your address or phone number that you’ve typed into an online registration form.
You can also adjust settings for feeds and Web Slices here. Feed refers to a Really Simple Syndication (RSS) feed, which can deliver updated content from some websites. Web Slices is a different brand of content syndication.

The Connections tab controls settings for all of Windows, not just for Internet Explorer. On it you can click Setup to run a Windows wizard that steps you through the process of connecting to the Internet (if you don’t already have a connection). You can also add a dial-up or VPN connection here. (The main thing you may want to explore on the Connections tab, though, is setting up a proxy server, explained next.
If your network has a proxy server, you can configure your browser to send requests to the proxy server, which will forward and handle all requests. If you set this up from within other browsers, like Chrome or Firefox, it applies only when using them. However, when you set up a proxy server using the Internet Options dialog box in IE, or the Internet Properties dialog box from the Control Panel, the proxy server applies to Windows itself (all browsers).
Windows provides options for four types of proxy servers: HTTP, Secure (HTTPS), FTP, and Socks. You should already be familiar with the first three of those. Socks is a proxy server protocol. If you have a proxy server for other services not supported by Windows, you will need to install a proxy client provided by the vendor of the server software.
To configure Windows to use a proxy server, follow these steps:
1. On the Connections tab of the Internet Options dialog box, click the LAN Settings button to open the Local Area network (LAN) Settings dialog box.
2. Under Proxy Server, click to place a check in the box labeled Use a Proxy Server for Your LAN (These Settings Will Not Apply to Dial-up or VPN Connections).
3. Enter the IP address in the Address box and the port number (obtained from your network administrator or from the documentation for the proxy server) in the Port box. Click Advanced if you need to add more addresses and ports for other services. Figure 15-6 shows this dialog box.
FIGURE 15-6 Proxy server settings for Windows
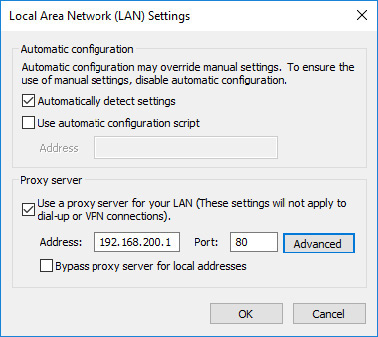
4. Click OK twice to close all open dialog boxes, or click only once to keep the Internet Options dialog box open for the next section.
On the Programs tab (see Figure 15-7), you can control what programs operate using your Internet connection. You can control add-ons, set a default HTML editor, and access Windows’ default programs and file associations controls. (You can also access those controls from the Control Panel directly; the buttons in the dialog box are just shortcuts to those.) Of these, the most important setting to know about for exam prep is the one for managing browser add-ons, covered next.
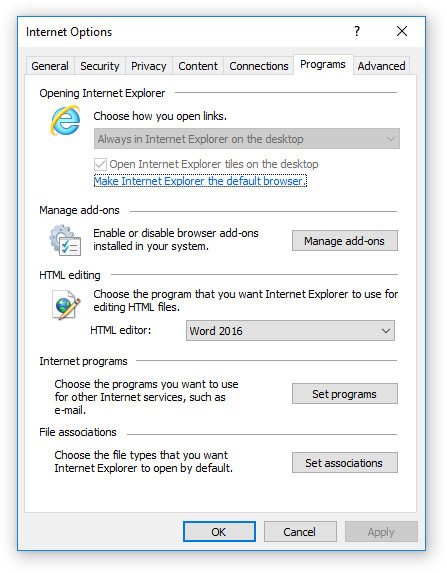
You can add functionality to a browser by installing an add-on, a small program that is inserted into an app (such as a browser) but not fully controlled by the app. Also called a plug-in or browser helper object (BHO), an add-on is usually free and available as a download. For instance, if you have the Adobe Acrobat add-on installed, you can view PDF files in your browser.
Because the browser does not fully control an add-on, add-ons are malware targets. As a result, the trend is moving away from using add-ons and using HTML5 instead to create rich, interactive web page content that does not require an add-on.
To control add-ons, click the Manage Add-ons button on the Programs tab, opening the Manage Add-ons dialog box. From here you can enable or disable toolbars and extensions, specify your default search provider, work with accelerators, and enable or disable tracking protection.
 Toolbars and Extensions These are the traditional kinds of add-ons, adding some capability to the browser. Select an item and then view its details in the lower pane. Click Enable or Disable to turn it on or off. See Figure 15-8.
Toolbars and Extensions These are the traditional kinds of add-ons, adding some capability to the browser. Select an item and then view its details in the lower pane. Click Enable or Disable to turn it on or off. See Figure 15-8.
FIGURE 15-8 The Manage Add-ons dialog box
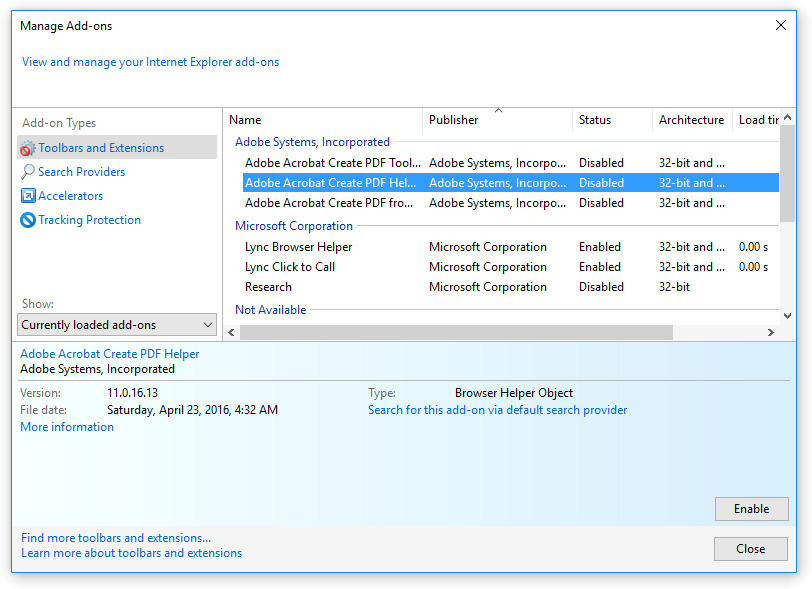
 Search Providers When you type keywords directly into the address bar in IE, a default search provider takes them and runs a query. You can control which search provider does this work for you. The default one for IE is Bing, Microsoft’s search engine. To add others to the list, click the Find More Search Providers hyperlink at the bottom of the dialog box.
Search Providers When you type keywords directly into the address bar in IE, a default search provider takes them and runs a query. You can control which search provider does this work for you. The default one for IE is Bing, Microsoft’s search engine. To add others to the list, click the Find More Search Providers hyperlink at the bottom of the dialog box.
 Accelerators An accelerator is a helper program that works with certain kinds of content. For example, you might have a translation accelerator that works when it detects a foreign language in use. You can choose which accelerator to use for various kinds of content. Click Find More Accelerators at the bottom of the dialog box to get others besides the default-provided Microsoft ones.
Accelerators An accelerator is a helper program that works with certain kinds of content. For example, you might have a translation accelerator that works when it detects a foreign language in use. You can choose which accelerator to use for various kinds of content. Click Find More Accelerators at the bottom of the dialog box to get others besides the default-provided Microsoft ones.
 Tracking Protection Some advertisers attempt to track you across multiple websites that you visit. If you’ve ever shopped for an item and then seen an ad for that same item minutes later in Facebook, you know you’ve been tracked. You can get and enable tracking protection lists that deny your information to any advertisers on the tracking list provided. Click Get a Tracking Protection List Online to find lists.
Tracking Protection Some advertisers attempt to track you across multiple websites that you visit. If you’ve ever shopped for an item and then seen an ad for that same item minutes later in Facebook, you know you’ve been tracked. You can get and enable tracking protection lists that deny your information to any advertisers on the tracking list provided. Click Get a Tracking Protection List Online to find lists.
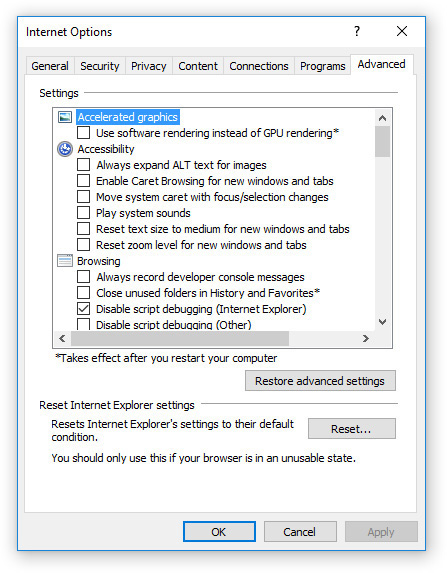
On the Advanced Settings tab you’ll find a long list of less common browser settings you can adjust. Most of these are for IE only, and don’t affect your use of other browsers. For example, you can enable certain accessibility options, allow or block certain kinds of content, and choose whether or not to underline hyperlinks. It’s a real grab-bag of settings! See Figure 15-9.

Configuring Internet Options
To explore the Internet options available in Windows and Internet Explorer, follow these steps:
1. Open the Control Panel and choose Network and Internet | Internet Options.
2. On the General tab, in the Home Page box, replace the current URL with the URL of a page of your choice. (We like http://news.google.com for a home page to get the latest news headlines, but choose one that you will enjoy.)
3. On the General tab, click Settings, and then click the History tab. Change the Days to Keep Pages in History value if desired. Click OK.
4. Click the Security tab. Click Trusted Sites, and click the Sites button. Add a site to your list of trusted sites, and then click Close.
5. On the Security tab, click the Custom Level button. Examine the custom security settings available. Make a change, and click OK. Notice that the slider is gone.
6. Click Default Level to return the security settings to their defaults. The slider returns.
7. On the Privacy tab, click Advanced. Set Third-party Cookies to Block, and click OK.
8. On the Content tab, click the Settings button for AutoComplete. Review the settings there. Adjust any as desired and click OK.
9. On the Programs tab, open the HTML Editor drop-down list to see your choices for HTML editing. Make a different choice if desired.
10. Click OK to make the changes and close the dialog box, or click Cancel to abandon the changes.
 902: 2.3 Identify basic cloud concepts
902: 2.3 Identify basic cloud concepts
This section covers all the topics from CompTIA A+ 902 exam objective 2.3, which deals with cloud computing. These topics include characteristics of a cloud environment, types of cloud services, and types of cloud deployment. For the CompTIA A+ exams you don’t need to know how to actually implement cloud services, but you should be able to describe how clouds work.
A cloud is an online location that offers one or more types of computing services to users. For example, a cloud-based file storage system like OneDrive or Dropbox enables people to store, access, and share files from any Internet-connected computing device. A cloud-based application might allow users to perform tasks online that normally are accomplished on a local PC, like editing a business document, or to interact with an online application to place orders or collaborate with others. In the following sections we’ll look at some key cloud-related terms you should understand.

The National Institute of Standards and Technology (NIST) defines cloud computing as having five key characteristics. The following descriptions of those characteristics come directly from NIST SP 800-145, “The NIST Definition of Cloud Computing.”
 On-demand self-service A consumer can unilaterally provision computing capabilities, such as server time and network storage, as needed automatically without requiring human interaction with each service provider.
On-demand self-service A consumer can unilaterally provision computing capabilities, such as server time and network storage, as needed automatically without requiring human interaction with each service provider.
 Broad network access Capabilities are available over the network and accessed through standard mechanisms that promote use by heterogeneous thin or thick client platforms (e.g., mobile phones, tablets, laptops, and workstations).
Broad network access Capabilities are available over the network and accessed through standard mechanisms that promote use by heterogeneous thin or thick client platforms (e.g., mobile phones, tablets, laptops, and workstations).
 Resource pooling The provider’s computing resources are pooled to serve multiple consumers using a multi-tenant model, with different physical and virtual resources dynamically assigned and reassigned according to consumer demand. There is a sense of location independence, in that the customer generally has no control over or knowledge of the exact location of the provided resources, but may be able to specify location at a higher level of abstraction (e.g. country, state, or datacenter). Examples of resources include storage, processing, memory, and network bandwidth.
Resource pooling The provider’s computing resources are pooled to serve multiple consumers using a multi-tenant model, with different physical and virtual resources dynamically assigned and reassigned according to consumer demand. There is a sense of location independence, in that the customer generally has no control over or knowledge of the exact location of the provided resources, but may be able to specify location at a higher level of abstraction (e.g. country, state, or datacenter). Examples of resources include storage, processing, memory, and network bandwidth.
 Rapid elasticity Capabilities can be elastically provisioned and released, in some cases automatically, to scale rapidly outward and inward commensurate with demand. To the consumer, the capabilities available for provisioning often appear unlimited and can be appropriated in any quantity at any time.
Rapid elasticity Capabilities can be elastically provisioned and released, in some cases automatically, to scale rapidly outward and inward commensurate with demand. To the consumer, the capabilities available for provisioning often appear unlimited and can be appropriated in any quantity at any time.
 Measured service Cloud systems automatically control and optimize resource use by leveraging a metering capability at some level of abstraction appropriate to the type of service (e.g., storage, processing, bandwidth, and active user accounts). Resource usage can be monitored, controlled, and reported, providing transparency for both the provider and consumer of the utilized service.
Measured service Cloud systems automatically control and optimize resource use by leveraging a metering capability at some level of abstraction appropriate to the type of service (e.g., storage, processing, bandwidth, and active user accounts). Resource usage can be monitored, controlled, and reported, providing transparency for both the provider and consumer of the utilized service.
For more information about NIST publication SP 800-145, see http://nvlpubs.nist.gov/nistpubs/Legacy/SP/nistspecialpublication800-146.pdf.
Three basic cloud service models are defined in NIST SP 800-145, based on what is being provided. An organization can choose among these to find the best fit for the services they wish to implement.
Software as a Service (SaaS) enables users to run software from the cloud’s server, rather than downloading and installing it on their own individual computers. For example, Microsoft Office Online is SaaS.
Platform as a Service (PaaS) provides developers a cloud-based environment on which to deploy their own applications that they can in turn offer to consumers in a cloud environment. For example, if a company wanted to provide a Human Resources application to their employees that could be accessed online, they might use PaaS to develop it.
Infrastructure as a Service (IaaS) allows companies and developers to create and control their own platform. They can provision servers, storage, networks, and virtual machines as needed to create PaaS and SaaS to offer to consumers. For example, a company might create their own fully immersive suite of tools online, including a nonstandard user interface.
Another way that NIST SP 800-145 classifies clouds is according to where the hardware and software running the cloud are located or hosted.
A private cloud is operated on a network that only one company or organization has access to. It may be managed either internally within the company or by a contractor, but the key feature here is that the server or virtual machine being used is for internal use only. It’s hosted at the company’s own data center, where all the data is protected behind a firewall. A private cloud scores high on control and security, but it can be expensive to maintain.

A community cloud is a cloud where several companies or organizations have agreed to cooperate to share a private cloud. It’s the equivalent of a co-op of friends buying a house together. It cuts down on costs, but there is more administration involved because the parties must agree on its management.
A public cloud operates on a network open for public use, such as the Internet. The cloud content is hosted at the vendor’s data center, and the vendor is responsible for server management and security. Even though you don’t manage the server’s security, your data remains separate from that of other customers, and you can still require people using your cloud services to sign in securely.
A hybrid cloud is a conjunction of two or more of these cloud types. They remain separate clouds, but they are connected in some way. For example, a business might have two clouds: a private one for sensitive internal data, and a public one for interacting with customers. Those two clouds could be joined together to provide employees seamless access to both kinds of data.
Be able to explain how the Internet is structured, including Tier 1, 2, and 3 providers, domain names, IP addresses, and DNS servers. Make sure you can identify the protocols and services involved in Internet usage, including those for web, mail, file transfer, chatting, time lookup, and authentication.
Be able to explain the functions of the many kinds of servers in use on the Internet, including web, file, print, DHCP, DNS, mail, authentication, and proxy, and understand the presence and purpose of legacy and embedded systems and Internet appliances.
Know how to access the Internet Options dialog box in Windows and what settings you can configure on each of its tabs.
Make sure you understand the cloud concepts outlined in the publication NIST SP 800-145, including the five characteristics of cloud computing, the differences among SaaS, PaaS, and IaaS, and various deployment models, such as private, community, public, and hybrid.
 TWO-MINUTE DRILL
TWO-MINUTE DRILL
Here are some of the key points covered in Chapter 15.
 The Internet is a huge, global WAN. No one company owns it. Its major pathways collectively are called the backbone.
The Internet is a huge, global WAN. No one company owns it. Its major pathways collectively are called the backbone.
 Backbone networks are owned by Tier 1 providers. Tier 2 providers are large ISPs that purchase access from Tier 1 providers. Tier 3 providers are small ISPs and individual companies.
Backbone networks are owned by Tier 1 providers. Tier 2 providers are large ISPs that purchase access from Tier 1 providers. Tier 3 providers are small ISPs and individual companies.
 Which ISP you should select depends on the type of connection you want. Some ISPs provide only one kind of connection; others offer a choice, such as DSL versus dial-up.
Which ISP you should select depends on the type of connection you want. Some ISPs provide only one kind of connection; others offer a choice, such as DSL versus dial-up.
 A website’s address is its Uniform Resource Locator (URL). In a URL, the first part is the protocol, such as http. The next part is the host name, such as www. The domain name consists of a top-level domain like .com and a second-level domain like microsoft. Forward slashes (/) separate the parts of the page’s path on the host.
A website’s address is its Uniform Resource Locator (URL). In a URL, the first part is the protocol, such as http. The next part is the host name, such as www. The domain name consists of a top-level domain like .com and a second-level domain like microsoft. Forward slashes (/) separate the parts of the page’s path on the host.
 A domain name that includes a host name as well as a top-level domain and a second-level domain is a fully qualified domain name (FQDN).
A domain name that includes a host name as well as a top-level domain and a second-level domain is a fully qualified domain name (FQDN).
 Domain Name System (DNS) servers translate between domain names and IP addresses.
Domain Name System (DNS) servers translate between domain names and IP addresses.
 Protocols for mail delivery include SMTP, POP, and IMAP.
Protocols for mail delivery include SMTP, POP, and IMAP.
 HTML is the language of web pages. HTTP is the protocol used to display web pages.
HTML is the language of web pages. HTTP is the protocol used to display web pages.
 Secure web pages use SSL or TLS to encrypt the data for transmission, and use HTTPS as the protocol to display the pages.
Secure web pages use SSL or TLS to encrypt the data for transmission, and use HTTPS as the protocol to display the pages.
 Telnet is a very old protocol used to emulate a terminal environment. SSH is a secure version of Telnet.
Telnet is a very old protocol used to emulate a terminal environment. SSH is a secure version of Telnet.
 FTP is a file transfer protocol employed by many online file servers. Secure copy (SCP) uses SSH for encrypting data. SFTP is a secure version of FTP.
FTP is a file transfer protocol employed by many online file servers. Secure copy (SCP) uses SSH for encrypting data. SFTP is a secure version of FTP.
 IRC is a protocol for online text messaging. It is used as part of the very popular Internet Relay Chat service.
IRC is a protocol for online text messaging. It is used as part of the very popular Internet Relay Chat service.
 NNTP is a protocol that accesses news servers that support newsgroups.
NNTP is a protocol that accesses news servers that support newsgroups.
 NTP is a protocol that is used to keep clocks synchronized online.
NTP is a protocol that is used to keep clocks synchronized online.
 CAPTCHA is a service used to create a test that only a human can pass, such as finding text in a graphical image, so online users can prove they are not a machine.
CAPTCHA is a service used to create a test that only a human can pass, such as finding text in a graphical image, so online users can prove they are not a machine.
 A web server is an online server that provides web pages to requesting clients.
A web server is an online server that provides web pages to requesting clients.
 A file server makes files available to users.
A file server makes files available to users.
 A print server manages multiple printers and makes them available to users.
A print server manages multiple printers and makes them available to users.
 A DHCP server assigns IP addresses dynamically to clients.
A DHCP server assigns IP addresses dynamically to clients.
 A mail server stores and forwards e-mail messages on behalf of clients.
A mail server stores and forwards e-mail messages on behalf of clients.
 An authentication server manages and checks user identities to safeguard secure resources.
An authentication server manages and checks user identities to safeguard secure resources.
 A proxy server points Internet requests for data to an alternative server that manages the requests, such as directing them to cached copies or declining to display certain content.
A proxy server points Internet requests for data to an alternative server that manages the requests, such as directing them to cached copies or declining to display certain content.
 A legacy system is one with old hardware or software. An embedded system is a computer that is inside an object that is not primarily a computer, like a microwave oven or a clock/radio.
A legacy system is one with old hardware or software. An embedded system is a computer that is inside an object that is not primarily a computer, like a microwave oven or a clock/radio.
 The term Internet appliance can refer to a consumer device that accesses the Internet or (per 902 exam objective 2.4) to a class of server applications and services designed to protect Internet servers. In that latter meaning, two key types are IDS and IPS.
The term Internet appliance can refer to a consumer device that accesses the Internet or (per 902 exam objective 2.4) to a class of server applications and services designed to protect Internet servers. In that latter meaning, two key types are IDS and IPS.
 Unified threat management (UTM) is the principle of creating a unified package of appliances that work together to reduce the threat of harm from attacks.
Unified threat management (UTM) is the principle of creating a unified package of appliances that work together to reduce the threat of harm from attacks.
 In Windows you can access Internet settings from the Control Panel or from inside Internet Explorer. The two methods produce identical dialog boxes except for the names, Internet Properties and Internet Options, respectively.
In Windows you can access Internet settings from the Control Panel or from inside Internet Explorer. The two methods produce identical dialog boxes except for the names, Internet Properties and Internet Options, respectively.
 On the General tab of the dialog box you can change the home page, configure IE tabs, and manage browsing history.
On the General tab of the dialog box you can change the home page, configure IE tabs, and manage browsing history.
 On the Security tab you can define the security settings for different security zones: Internet, Local intranet, Trusted sites, and Restricted sites.
On the Security tab you can define the security settings for different security zones: Internet, Local intranet, Trusted sites, and Restricted sites.
 On the Privacy tab you can control cookie settings and block pop-ups, as well as configure InPrivate browsing.
On the Privacy tab you can control cookie settings and block pop-ups, as well as configure InPrivate browsing.
 On the Content tab you can control security certificates and publishers and clear the SSL state. You can also manage AutoComplete, feed, and Web Slices settings.
On the Content tab you can control security certificates and publishers and clear the SSL state. You can also manage AutoComplete, feed, and Web Slices settings.
 On the Connections tab you can set up a new Internet connection, including dial-up, VPN, or LAN. You can also configure a proxy server.
On the Connections tab you can set up a new Internet connection, including dial-up, VPN, or LAN. You can also configure a proxy server.
 On the Programs tab you can control add-ons, which include toolbars and extensions, search providers, accelerators, and tracking protection.
On the Programs tab you can control add-ons, which include toolbars and extensions, search providers, accelerators, and tracking protection.
 On the Advanced tab is a long list of less common browser settings you can adjust.
On the Advanced tab is a long list of less common browser settings you can adjust.
 The five characteristics of a cloud environment are: on-demand self-service, broad network access, resource pooling, rapid elasticity, and measured service.
The five characteristics of a cloud environment are: on-demand self-service, broad network access, resource pooling, rapid elasticity, and measured service.
 Software as a Service (SaaS) allows users to run software from the cloud’s server.
Software as a Service (SaaS) allows users to run software from the cloud’s server.
 Platform as a Service (PaaS) provides developers a cloud-based environment on which to deploy their own applications.
Platform as a Service (PaaS) provides developers a cloud-based environment on which to deploy their own applications.
 Infrastructure as a Service (IaaS) allows companies to create and control their own platform.
Infrastructure as a Service (IaaS) allows companies to create and control their own platform.
 A private cloud is hosted on a private server inside a company’s firewall.
A private cloud is hosted on a private server inside a company’s firewall.
 A community cloud is a cloud where several companies share a private cloud.
A community cloud is a cloud where several companies share a private cloud.
 A public cloud operates on an open network, such as the Internet. Even though the network itself is public, you can still require users to sign into your cloud.
A public cloud operates on an open network, such as the Internet. Even though the network itself is public, you can still require users to sign into your cloud.
 A hybrid cloud is a joining of two or more other cloud types.
A hybrid cloud is a joining of two or more other cloud types.
The following questions will help you measure your understanding of the material presented in this chapter. Read all of the choices carefully because there might be more than one correct answer. Choose all correct answers for each question.
1. Which type of companies own and control the Internet backbone?
A. Tier A
B. Tier B
C. Tier 1
D. Tier 2
2. From what kind of company do individuals get Internet connectivity?
A. ISP
B. DNS
C. Tier 1
D. DHCP
3. Which of these is a FQDN?
A. http
B. www
C. sycamoreknoll.com
4. Which of these is a host name?
A. http
B. www
C. sycamoreknoll.com
5. What kind of server translates between IP addresses and domain names?
A. DHCP
B. ISP
C. DNS
D. FQDN
6. Which of these is a mail protocol?
A. HTML
B. IMAP
C. Telnet
D. FTP
7. Which of these is the protocol for a secure web page?
A. SFTP
B. HTTPS
C. SSH
D. POP
8. Which of these is a protocol for synchronizing clocks?
A. NNTP
B. IRC
C. FTP
D. NTP
9. What kind of server would you use for FTP?
A. Web
B. File
C. Mail
D. Authentication
10. What kind of server assigns IP addresses to clients?
A. Web
B. DNS
C. File
D. DHCP
11. What kind of server handles requests for Internet services for a client without exposing the client’s IP address to the Internet?
A. DNS
B. Proxy
C. Mail
D. Authentication
12. What can an IPS do that an IDS can’t?
A. Detect security intrusions
B. Manage printers
C. Stop a detected attack
D. Host an FTP site
13. On which tab of the Internet Options dialog box can you change the home page used for IE?
A. Appearance
B. General
C. Advanced
D. Home
14. Internet, Local intranet, Trusted sites, and Restricted sites are the four types of what?
A. Security zones
B. Cookies
C. Privacy settings
D. Web servers
15. What kind of cookie comes from the website you are visiting?
A. First-party
B. Second-party
C. Third-party
D. Fourth-party
16. _____ is a high-privacy browsing mode in Internet Explorer.
A. First-party
B. InPrivate
C. Add-on
D. Proxy
17. HTTP, HTTPS, FTP, and Socks are four types of what?
A. DHCP servers
B. Websites
C. LANs
18. Which of these is not one of the five characteristics of cloud computing?
A. Rapid elasticity
B. Resource pooling
C. Measured service
D. Private server
19. Which of these refers to users running applications from a cloud’s server, rather than downloading the application?
A. Infrastructure as a Service
B. Platform as a Service
C. Software as a Service
D. Hardware as a Service
20. A cloud that operates via the Internet is a __________ cloud.
A. Hybrid
B. Community
C. Public
D. Private
1.  C. Tier 1 providers own and control the backbone.
C. Tier 1 providers own and control the backbone.
 A and B are both incorrect because tiers are numbered, not lettered. D is incorrect because this refers to large ISPs.
A and B are both incorrect because tiers are numbered, not lettered. D is incorrect because this refers to large ISPs.
2.  A. Individuals contract with an Internet service provider (ISP) for Internet service.
A. Individuals contract with an Internet service provider (ISP) for Internet service.
 B is incorrect because DNS is a type of server that translates between IP addresses and domain names. C is incorrect because Tier 1 refers to an owner of the Internet backbone; Tier 1 owners do not provide Internet accounts to individuals. D is incorrect because DHCP is a service that dynamically assigns IP addresses to clients.
B is incorrect because DNS is a type of server that translates between IP addresses and domain names. C is incorrect because Tier 1 refers to an owner of the Internet backbone; Tier 1 owners do not provide Internet accounts to individuals. D is incorrect because DHCP is a service that dynamically assigns IP addresses to clients.
3.  D. A fully qualified domain name (FQDN) includes both a host and a domain.
D. A fully qualified domain name (FQDN) includes both a host and a domain.
 A is incorrect because it is a protocol. B is incorrect because it is a host name. C is incorrect because it is a domain name but it lacks a host name.
A is incorrect because it is a protocol. B is incorrect because it is a host name. C is incorrect because it is a domain name but it lacks a host name.
4.  B. www is a host name.
B. www is a host name.
 A is incorrect because it is a protocol. C is incorrect because it is a domain name but it lacks a host name. D is incorrect because it is an FQDN.
A is incorrect because it is a protocol. C is incorrect because it is a domain name but it lacks a host name. D is incorrect because it is an FQDN.
5.  C. A Domain Name System (DNS) server translates between IP addresses and domain names.
C. A Domain Name System (DNS) server translates between IP addresses and domain names.
 A is incorrect because a DHCP server dynamically assigns IP addresses to clients. B is incorrect because ISP refers to an Internet service provider, a company that provides Internet service. D is incorrect because FQDN describes a web address that includes a host name.
A is incorrect because a DHCP server dynamically assigns IP addresses to clients. B is incorrect because ISP refers to an Internet service provider, a company that provides Internet service. D is incorrect because FQDN describes a web address that includes a host name.
6.  B. IMAP, Internet Mail Access Protocol, is a mail protocol.
B. IMAP, Internet Mail Access Protocol, is a mail protocol.
 A is incorrect because HTML is the language used to create web pages. C is incorrect because Telnet is a terminal emulation protocol. D is incorrect because FTP is a file transfer protocol.
A is incorrect because HTML is the language used to create web pages. C is incorrect because Telnet is a terminal emulation protocol. D is incorrect because FTP is a file transfer protocol.
7.  B. HTTPS is a secure form of HTTP, a web protocol.
B. HTTPS is a secure form of HTTP, a web protocol.
 A is incorrect because SFTP is a protocol for secure file transfer. C is incorrect because SSH is for secure terminal emulation or file transfer. D is incorrect because POP is a mail protocol.
A is incorrect because SFTP is a protocol for secure file transfer. C is incorrect because SSH is for secure terminal emulation or file transfer. D is incorrect because POP is a mail protocol.
8.  D. Network Time Protocol (NTP) is for synchronizing clocks.
D. Network Time Protocol (NTP) is for synchronizing clocks.
 A is incorrect because NNTP is a protocol for news feeds. B is incorrect because IRC is a protocol for online text messaging. C is incorrect because FTP is a protocol for file transfers.
A is incorrect because NNTP is a protocol for news feeds. B is incorrect because IRC is a protocol for online text messaging. C is incorrect because FTP is a protocol for file transfers.
9.  B. A file server would be used for FTP, which is a file transfer protocol.
B. A file server would be used for FTP, which is a file transfer protocol.
 A is incorrect because a web server delivers web pages. C is incorrect because a mail server is used for e-mail. D is incorrect because an authentication server verifies user identities.
A is incorrect because a web server delivers web pages. C is incorrect because a mail server is used for e-mail. D is incorrect because an authentication server verifies user identities.
10.  D. A Dynamic Host Configuration Protocol (DHCP) server assigns IP addresses.
D. A Dynamic Host Configuration Protocol (DHCP) server assigns IP addresses.
 A is incorrect because a web server delivers web pages. B is incorrect because a DNS server translates between IP addresses and domain names. C is incorrect because a file server allows users to upload and download files.
A is incorrect because a web server delivers web pages. B is incorrect because a DNS server translates between IP addresses and domain names. C is incorrect because a file server allows users to upload and download files.
11.  B. A proxy server protects the client’s IP address from the Internet, among its other benefits.
B. A proxy server protects the client’s IP address from the Internet, among its other benefits.
 A is incorrect because a DNS server translates between IP addresses and domain names. C is incorrect because a mail server sends and receives e-mail. D is incorrect because an authentication server verifies user identities.
A is incorrect because a DNS server translates between IP addresses and domain names. C is incorrect because a mail server sends and receives e-mail. D is incorrect because an authentication server verifies user identities.
12.  C. An intrusion prevention system (IPS) can stop a detected security attack.
C. An intrusion prevention system (IPS) can stop a detected security attack.
 A is incorrect because both an IPS and an IDS can detect security intrusions. B and D are both incorrect because they are not functions of either an IPS or an IDS.
A is incorrect because both an IPS and an IDS can detect security intrusions. B and D are both incorrect because they are not functions of either an IPS or an IDS.
13.  B. You can set the home page on the General tab.
B. You can set the home page on the General tab.
 A is incorrect because Appearance is not an Internet Options tab; it is a button on the General tab. C is incorrect because the Advance tab contains advanced settings (not including the home page). D is incorrect because Home is not an Internet Options tab.
A is incorrect because Appearance is not an Internet Options tab; it is a button on the General tab. C is incorrect because the Advance tab contains advanced settings (not including the home page). D is incorrect because Home is not an Internet Options tab.
14.  A. These are all security zones, found on the Security tab.
A. These are all security zones, found on the Security tab.
 B, C, and D are all incorrect because they are not classified using these types.
B, C, and D are all incorrect because they are not classified using these types.
15.  A. A first-party cookie comes from the website you are visiting.
A. A first-party cookie comes from the website you are visiting.
 B and D are incorrect because there is no such thing as second-party or fourth-party cookies in cookie classification. C is incorrect because a third-party cookie is a cookie from an advertiser.
B and D are incorrect because there is no such thing as second-party or fourth-party cookies in cookie classification. C is incorrect because a third-party cookie is a cookie from an advertiser.
16.  B. InPrivate is the high-privacy browsing mode in IE.
B. InPrivate is the high-privacy browsing mode in IE.
 A is incorrect because first-party is a kind of cookie. C is incorrect because an add-on is an extension that adds new features to the browser. D is incorrect because a proxy is a type of server.
A is incorrect because first-party is a kind of cookie. C is incorrect because an add-on is an extension that adds new features to the browser. D is incorrect because a proxy is a type of server.
17.  D. HTTP, HTTPS, FTP, and Socks are four types of proxy servers.
D. HTTP, HTTPS, FTP, and Socks are four types of proxy servers.
 A, B, and C are all incorrect because HTTP, HTTPS, FTP, and Socks are not types of these items. HTTP and HTTPS are protocols for delivering web pages, and FTP is a file server protocol.
A, B, and C are all incorrect because HTTP, HTTPS, FTP, and Socks are not types of these items. HTTP and HTTPS are protocols for delivering web pages, and FTP is a file server protocol.
18.  D. Private server is not one of the five characteristics.
D. Private server is not one of the five characteristics.
 A, B, and C are all incorrect because each is one of the five characteristics.
A, B, and C are all incorrect because each is one of the five characteristics.
19.  C. Software as a Service (SaaS) is the term for running an application from a cloud.
C. Software as a Service (SaaS) is the term for running an application from a cloud.
 A is incorrect because IaaS refers to creating an entire infrastructure environment in the cloud. B is incorrect because PaaS refers to having developers create their own cloud applications on a supplied platform. D incorrect because Hardware as a Service is not a recognized cloud service model.
A is incorrect because IaaS refers to creating an entire infrastructure environment in the cloud. B is incorrect because PaaS refers to having developers create their own cloud applications on a supplied platform. D incorrect because Hardware as a Service is not a recognized cloud service model.
20.  C. A public cloud is one that operates via a public network such as the Internet.
C. A public cloud is one that operates via a public network such as the Internet.
 A is incorrect because a hybrid cloud joins two or more other types of clouds. B is incorrect because a community cloud is a deployment in which several organizations share a private cloud. D is incorrect because a private cloud is a deployment where the company running it also controls and manages the server and network.
A is incorrect because a hybrid cloud joins two or more other types of clouds. B is incorrect because a community cloud is a deployment in which several organizations share a private cloud. D is incorrect because a private cloud is a deployment where the company running it also controls and manages the server and network.