TREND 7
Embedding Surveillance in Everyday Environments
From the Surveillance of People to the Surveillance of Things
In the “Day in the Life” story in Trend 1, relatively few of the many surveillance moments that Farah and her family encounter would be readily recognized as such without an understanding of how personal information is captured and processed behind the scenes. Much of everyday surveillance is embedded seamlessly, nearly unrecognizably, within the gadgets and settings to which we have become accustomed as essential to modern living.
The trend toward ubiquitous surveillance is enabled, in part, by placing sensors, identifiers, and cameras in everyday objects and the built environment. What once was done at specific locations or using specific devices has become a general feature of the vehicles, streets, homes, and workplaces with which we interact daily. We use cellphones to keep in touch with family and friends without thinking about the fact that we are letting the phone company know exactly where we are at all times. We browse through pictures of ourselves on Facebook without considering that Facebook is now the largest facial recognition software developer in the world; it can identify us in photos whether or not we are tagged. And digital cameras can embed both a time/date and GPS location stamp on every picture we take.
This embedding of surveillance capabilities into familiar devices and everyday environments is an ongoing trend, closely linked to both the general expansion of surveillance and the more recent expansion of mobile and location-based surveillance, two themes examined in earlier chapters. The rapid pace of technological change in digital networking and related technologies is the most obvious driver of the embedding process. Not only are the capabilities of digital sensing, recording, transmission, and processing devices growing, but such devices are also becoming cheaper and smaller on a unit basis. In sharp contrast to the expansion of cars in the early part of the twentieth century, when vehicles, roadways, and other aspects of the supporting infrastructures became highly visible in everyday settings, the even more extensive and rapid expansion of digital networking is occurring largely out of view. Although we can see people using their smartphones, laptops, and related devices, the devices themselves are just the tip of an enormous iceberg, with the bulk of the hardware invisible behind walls or underground and with the buzzing activity extending nearly everywhere via radio waves.1
As we have embraced these technologies, we have also embedded surveillance into our taken-for-granted understandings of the worlds we inhabit. Surveillance is now spoken of as a normal part of parenting, work, and travel, and many of us routinely watch others and allow ourselves to be watched as we go about our day, without thinking twice about it. Such embedding makes it difficult for us to identify, understand, debate, and democratically regulate surveillance practices as they become woven into the fabric of contemporary life.
To help us visualize and understand the surveillance around us, and to facilitate discussion, it is useful to distinguish between two distinct approaches to embedded surveillance. In the first, surveillance is the central purpose for developing new modes of capturing personal information. In the second, surveillance capabilities are introduced as an add-on to an existing activity: this approach relies on personal information that is collected as an inherent part of the initial activity or is easily generated as a by-product of it. Video surveillance cameras are an example of the former, more recognizable mode of surveillance, while incorporating keystroke monitoring in an office setting or intercepting traffic on the Internet backbone are examples of the latter. The “surveillance as add-on” approach is more widespread and more difficult to recognize. As the following discussion illustrates, in both cases, the embedded character of surveillance makes it hard to detect and thereby difficult to hold those responsible to account.
Surveillance as Central: Special Purpose Surveillance
The most obvious example of the unobtrusive embedding of devices designed specifically for surveillance purposes into our daily environment is the extraordinary growth of various types of camera surveillance. Most of this growth takes the form of surveillance cameras deployed on city streets and in shopping centres for security purposes. Indeed, the surveillance camera is probably the most familiar symbol of surveillance.
Although the United Kingdom has long been the recognized leader in the adoption of surveillance cameras, Canada is similarly moving toward making this form of monitoring a ubiquitous feature of contemporary urban life.2 Surveillance cameras are, for instance, becoming common along roadways, where they are used to spot drivers speeding or going through red lights. Taxicabs in major cities are fitted with cameras that record the face of every passenger. In these examples, stored images are normally examined only when there is evidence of an infraction or incident.
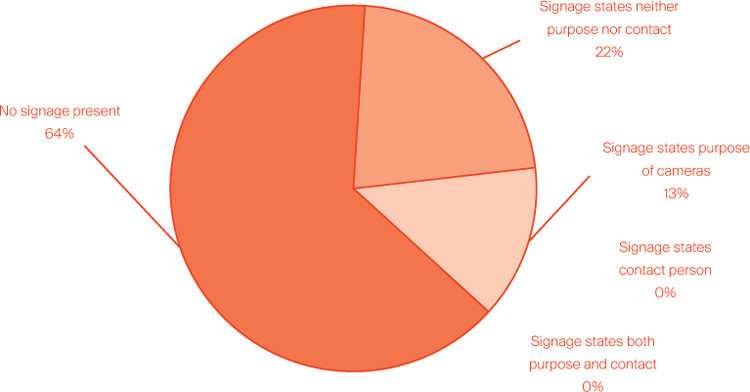
Even though such cameras are among the most visible indicators of explicit surveillance, people are largely unaware of their presence.3 This is, in part, due to the fact that such cameras are relatively small and nondescript and are often tucked unobtrusively away in ceilings and high walls outside of our usual sightlines. Few video surveillance operators draw attention to their installations. Even though businesses are required by Canadian law to post signs notifying people of the presence of video surveillance, a 2011 study found that only one-third of sampled commercial installations had any form of signage and that when such signs were posted, they were often designed and positioned so as not to be noticed.4 Furthermore, the wording of the signs consistently failed to meet even the minimum notification requirements specified by Canadian privacy law.
A more sophisticated and privacy-sensitive application of visual surveillance is the growing use of automated licence plate recognition (ALPR) systems on roadways and in parking lots. Such systems use optical character recognition (OCR) techniques to capture licence plate numbers; the plate numbers are then compared against lists containing the licence plate numbers of cars that police are looking for or are stored in databases for later use. ALPR devices are also mounted on structures above highways to collect tolls, flag suspects, or track the movements of “persons of interest.” Police use ALPR-equipped cars to scan parking lots and highways in search of vehicles that match their watch lists. They may ticket or apprehend drivers on the spot.
Surveillance as an Add-on: Transactional Surveillance
Although businesses and government agencies are rapidly embedding special purpose surveillance devices into our built environment, the surveillance capabilities that have been added into the familiar devices and transactions originally developed for other purposes are much less visible and far greater in scope, intensity, and consequence. The expanded use of computers for record keeping and transaction processing, which began in the 1960s, greatly increased the capacity for embedded surveillance across a wide range of settings. Such surveillance was initially implemented in the work environment in large offices characterized by routine work and subordinated employees. Management began to use computerized production data readily generated as a by-product of existing systems—including keystroke counts, response times, sales volumes, and throughput—to manage employee performance, a process referred to as “informating.”5 Often, this took the form of monitoring individual performance against pre-established targets and then rewarding or punishing employees accordingly. The more intensive forms of this surveillance were controversial, especially in unionized settings, and became the focus of a Canadian federal government enquiry in the early 1980s.6
Back-office automation paved the way for online customer transaction processing and customer surveillance. In the past decade, as such transactions have moved from corporate-owned, special-purpose, immobile devices—such as automated teller machines (ATMs) and point of sale (POS) terminals—to individually owned, multipurpose mobile devices—notably, smartphones—surveillance capabilities have been embedded in these as well. The News of the World phone-hacking scandal in the United Kingdom, in which reporters intercepted the voicemails of thousands of individuals, highlights the potential for conducting transaction surveillance via the telecommunications networks on which mobile devices rely.7 Such surveillance techniques are further detailed in Trend 5.
“Enhancing” ID for Surveillance
Another example of how surveillance has been unobtrusively embedded in familiar and uniquely personal items includes the recent digital “enhancement” of our identification documents. ID is central to contemporary life: we are increasingly required to present identification documents when we shop, enter buildings or other spaces, board transit vehicles, cross borders, and so on. The ID documents that we use are most often standardized plastic cards that slide smoothly into designated places in our wallets and purses. People are accustomed to presenting such cards or other ID documents for a quick visual inspection by an authorized employee before being allowed to proceed.
The embedding of surveillance capability in ID cards has developed in stages as digital technologies have become more sophisticated. First and most significant is the direct linking of ID documents with their associated databases. The computerized reading of data on the card—notably, the unique identifier—allows real-time checking against a database to determine whether the cardholder is authorized to proceed. This shifts the primary function of the ID card from its role of certifying that its holder has a particular status (e.g., authorized driver, club member, citizen) to that of primary nexus between the individual and his or her “data double”—which refers to the totality of that individual’s personal digital information. Typically, such card scanning also produces a record that is added to the person’s dossier. This linking of data collection, database storage, and automated authorization enables the fine-grained management of large populations—that is, the efficient and unobtrusive sorting of individuals into organizationally prescribed treatment categories.8
In the past decade, two further digital technologies—digital biometrics and radio frequency identification (RFID) chips—have been embedded in our familiar ID cards such as drivers’ licences, health cards, and passports. These changes have had little effect on the form or superficial appearance of the cards, but they have ushered in significantly greater surveillance potential. Often introduced in concert with an ever growing number of back-end databases and relentless attempts to more thoroughly integrate the data capture of these systems behind the scenes, RFIDS and biometrics capture personal information with breathtaking ease. By unobtrusively reading card data in a more dispersed and varied range of transactional settings, these techniques promise convenience to cardholders but, at the same time, invisibly tie them ever more tightly to their corresponding data doubles.
The Ontario Smart Card Project (OSCP) was one of the first, and is still one of the most ambitious, attempts in Canada to “enhance” conventional ID cards by incorporating digital technologies. Proposed in the late 1990s by then-premier Mike Harris’s Conservative government, the OSCP was intended to be a multipurpose card to access a wide range of government services. Users would biometrically verify or “authenticate” that they owned the card by having a part of their body measured by a fingerprint, iris, or other scanner and then compared with previously recorded versions of these images. As with many other overly ambitious, controversial ID-scheme initiatives, the project was shrouded in a dysfunctional public obscurity and got bogged down in the complexities of integrating so many diverse services within a single unified operation. Although the provincial government quietly closed the floundering project in 2001, its central ambitions of population-wide registration, integrated databases, and biometric authentication live on and play an important role in subsequent Canadian ID initiatives. Most notable in this respect is the BC Services Card, which combines the provincial health card and driver’s licence, backed by a common biometric facial database.
The response of the Bush administration to the terrorist attacks of 11 September 2001, although too late to help save the Ontario Smart Card Project, provided a spectacular and lucrative stimulus to the identity-management and security industries more widely. Canada felt the effects almost immediately. By the end of that year, the hastily drafted Canada-US Smart Border Declaration and Action Plan called for a common North American biometric identity card, even though neither the security value nor the technical effectiveness of such a measure could be demonstrated. At the same time, in a clear case of policy laundering, the US pushed the International Civil Aviation Organization (ICAO) to adopt a new “e-passport,” which includes an embedded chip that can, on request, transmit a biometric-grade digital facial image of the passport holder.9 This transmission does not require any contact, and the passport can be scanned without the passport holder’s knowledge. Canada supported this change in standard, offering to have an e-passport ready by 2005. While the federal government has repeatedly postponed the public launch of the e-passport, it has, less visibly, been incorporating the essential biometric capabilities into newly issued conventional passports.10 For example, Passport Canada introduced more rigorous standards for photos (“No smiling!”) to facilitate automated face matching at the time of passport application and for later authentication.
The US federal Western Hemisphere Travel Initiative (WHTI), which came into effect 1 June 2009, also requires the use of biometrics. Because of concerns that the new security measures might slow down border crossing, the governments of several states and provinces along the Canada-US border promoted the enhanced driver’s licence (EDL) as a border-crossing card that would be a faster, easier, and cheaper alternative to the passport.11 Following specifications set by the Department of Homeland Security (DHS), an enhanced driver’s licence includes an RFID chip. Border guards can access a digital image of the driver’s face and other information contained in the driver’s database record through scanning the card. One feature of the RFID standard adopted by the DHS is its relatively long read-range.12 Developed originally for livestock and supply-chain management, it is designed to read objects up to ten metres from the antenna. Combined with the lack of encryption or other forms of privacy protection, the DHS could hardly have chosen a less secure and more surveillance-prone standard. Complaints by civil liberties advocates and ID industry officials alike regarding the potential for privacy invasion fell on deaf DHS ears. Perhaps the only bright spot is that few Canadians or Americans have opted to use EDLS—far below anticipated numbers—although it is unclear how long people will be given the opportunity to opt out.13
Some RFID chips can be read up to ten metres from an antenna and lack encryption—security or surveillance? (Source: © iStockphoto.com/albn)
While the ambition to create a common North American biometric identity card has been scaled back because of opposition and implementation difficulties, many of its ingredients are systematically being assembled through other means. Under its REAL-ID initiative, and despite stiff resistance, the US government has attempted to turn state drivers’ licences into a de facto national ID card.14 In Canada, the federal and provincial governments have quietly worked together to develop a similar national identity-management scheme based on existing ID documents.15
Perhaps the greatest surveillance concern regarding these ID schemes in Canada is that the routine biometric enrolment of most of the adult population has been achieved without public debate and with scant indication of effective oversight. This has occurred largely through the capture of high-resolution facial images for drivers’ licences, health cards, and passports, which have then been made available for automated facial matching. These capabilities came to public attention in the wake of the June 2011 Vancouver Stanley Cup riot, when the Insurance Corporation of BC (ICBC) offered the Vancouver Police Department the use of its facial-recognition software and its “fairly fool-proof database of images” to identify criminal suspects.16 The police opted to develop its own database and did not seek the necessary court order to access ICBC’s data.
“Deep” Internet Surveillance
A third major issue concerning embedded surveillance that has emerged since 2000 is the interception and inspection of Internet traffic. Most public attention and controversy over Internet surveillance has focused on the surveillance at the “edges” of the Internet. On the user or client side of the Internet, the capture of data by surveillance software modules embedded within browsers (e.g., cookies and “web bugs”) has been controversial since the 1990s, and more recently, such software embedded in personal mobile devices (e.g., location tracking on iPhones and Android smartphones) has raised similar concerns.17 Similarly, on the server side, there are ongoing debates about the covert access to such communications as emails and social network posts that are held by Google, Facebook, Microsoft, and other major service providers.
With the extraordinary expansion of online services over the past decade, especially social networking applications, people around the globe have voluntarily, even enthusiastically, contributed enormous volumes of often highly personal information to corporate databases. Accessing this trove of fine-grained data—typically used for advertising or sold to third parties for commercial purposes—is a key feature of the business model of the corporations involved. This poses obvious privacy risks, but consumers, so far, have been willing to put up with this, whether because of a lack of knowledge or because they enjoy the convenience and immediate rewards of the services offered. These databases, and their promise of rich insights into the activities and attitudes of a significant portion of the population, have proved very attractive to state security and law enforcement agencies. In the case of the PRISM program, mentioned in Trend 6, the US National Security Agency (NSA) has embedded the means for automated access to the databases of nine major Internet service providers, thus bypassing the requirements of individual-specific court authorization that usually apply in the case of US persons. Despite their power and wealth, Internet companies have not been able to resist US government demands for bulk access to their data stores and have even invoked the same overly broad “third party” privacy exemption that the US government uses to justify the legality of its access.18 In matters concerning Canadians, however (and likewise residents of other countries), the NSA’s access to data is, in theory, unfettered by legal restraints. Similarly, under the terms of long-standing data-sharing agreements, Canadian government agencies should have access to data collected by the NSA.
Incorporating surveillance capabilities in both the client and server devices at the edges of the Internet is controversial, but it is deep within its “backbone” where the most alarming forms of Internet surveillance are being secretly embedded. Giant routers, housed in unobtrusive office towers in the cores of our major cities, switch billions of data packets every second between fibre-optic cables speeding our Internet traffic to its designated destinations. Over the past decade, governments and corporations have installed equipment that intercepts, analyzes, and selectively stores the traffic passing through these vital switches, or Internet exchange points (IXPS). Given the great and growing range of activity that is conducted via the Internet, the ability to surreptitiously monitor all the personal traffic of hundreds of millions of individuals is breathtaking in its potential ramifications.
It is a daunting technical challenge to analyze the enormous volumes of data coursing through the Internet rapidly enough for it to be useful to policing or management. Nevertheless, just as the speed and capacities of the routers have expanded, so too have the means of interception and the incentives for doing so. “Deep packet inspection” (DPI) refers to techniques that enable Internet carriers to read the content of the many messages and files they send along the net.19 A data packet is a piece of formatted computer information carried along the Internet: it consists of a “header,” containing addressing information, and a “payload,” containing the message content. Such packets can be conceptualized as a kind of electronic postcard or letter. Privacy advocates prefer the letter analogy, recognizing that while the header needs to be readable by intermediaries, the contents should be treated as confidential. Service providers, however, prefer the postcard analogy, meaning that the contents are available to anyone. Encrypting the content can protect it from prying eyes, but the header—the destination address—must remain unencrypted for the routing to work. The header information, along with other communication metadata, such as the timing, location, and duration, has traditionally enjoyed lower privacy protection. However, now that such metadata, which can be highly revealing, can be routinely collected and analyzed on a mass basis, privacy advocates argue that it should enjoy protection similar to message content.
Deep packet inspection came to public light in Canada when privacy advocates suspected that major ISPS, such as Bell and Rogers, were slowing, or “throttling,” the traffic of particular users or particular applications—notably, BitTorrent (www.bittorrent.com), a popular and free peer-to-peer Internet file-sharing service. In 2009, the same carriers told the CRTC (Canadian Radio-Television Telecommunications Commission) during hearings on Internet traffic management practices that they required DPI ability to prioritize certain traffic over others so that applications dependent on timely delivery (e.g., voice-over-IP, or VOIP) would suffer less delay than less time-sensitive applications (e.g., email and file transfers).20 Subsequent research found that at least a dozen of Canada’s largest carriers have installed DPI equipment.21 Although Telus did briefly block access to a union-support website, based on header information, there has been no direct evidence thus far that Canadian carriers are using DPI capabilities to surveil users or thwart access to legitimate sites.22 The same cannot be said of the equipment that Canadian manufacturers such as Netsweeper have sold to Middle Eastern authoritarian regimes, which use such devices for tracking opposition groups and censoring websites on political and religious grounds.23
The most extensive use of DPI techniques for population surveillance is the “warrantless wiretapping” of the US National Security Agency (NSA). Beginning around 2003, the NSA began installing surveillance equipment in the main Internet routing hubs of major US carriers, such as AT&T, Verizon, and others. This highly secretive activity came to light most dramatically when AT&T technician Mark Klein blew the whistle in 2006. Shortly after he retired from AT&T, Klein revealed that the NSA had arranged for AT&T to install fibre-optic “splitters” and related traffic-interception equipment in its main San Francisco Internet switching centre at 611 Folsom Street. With similar facilities at other Internet gateways around the country, the US government had evidently been spying on its entire population. As no warrants had been issued for these interceptions, more than forty court cases have been brought against both the carriers and the US government.24 This litigation has been stalled by congressional passage of the FISA Amendments Act of 2008, which broadened the scope of legally acceptable surveillance and granted private sector carriers retroactive immunity from prosecution.25 The American federal government has consistently blocked cases brought against it by claiming that plaintiffs lacked “standing” to bring charges, since they couldn’t establish that they had been subject to the secret surveillance, and/or by invoking a “state secrets” exemption.26
Whatever legal protections may apply to US persons, none apply to those targeted by similar Internet interception operations by the United States outside the country. The NSA refers to such operations as “upstream” collection.27 In addition to installing fibre-optic splitters within major Internet switches (infrastructure), in situations in which the switch operators are not sufficiently cooperative, the NSA has also adopted the technically more challenging route of tapping directly into the cables along the route between the switches. Since much of the international Internet traffic travels by submarine fibre-optic cable, this involves installing taps at landing stations or even in mid-ocean.28
In addition to what the NSA can access from its foreign Internet spying, Canadians are often subject to US domestic Internet interception, even when they and their communication targets are both in Canada. This is due to the fact that roughly one-third of Canadian traffic is routed through the United States, and almost always through one of the cities in which the NSA is strongly suspected of having surveillance operations (notably, New York, Chicago, and Seattle).29 This “boomerang” routing can occur even between Canadian public institutions located within the same Canadian city. For example, data packets travelling from the University of Toronto to the Ontario Student Assistance Program, which is only a few blocks from campus, are routed via New York and Chicago—both probable sites of NSA splitter operations—before finally returning to Toronto. Because the information moves through the United States, such traffic is subject to provisions of the USA PATRIOT Act (2001), which allows American government agencies to peek into information passing through the United States even when the information itself is stored outside the United States.

A Canadian boomerang Toronto-to-Toronto route (Source: http://www.ixmaps.ca/index.php)
Even Internet traffic carried by Canadian telecommunications service providers that remains entirely within Canadian borders is likely to be subject to similar forms of state-mandated network surveillance. This situation gained public prominence in 2012, when the Conservative government reintroduced “lawful access” legislation in Bill C-30—renamed at the last moment the Protecting Children from Internet Predators Act, even though the bill actually made no reference to child predators except in its title.30 The key provisions of the legislation, which sought to expand the powers of law enforcement agencies, included access to “subscriber data” when such agencies ask service providers for it. Prior judicial authorization or reasonable grounds to suspect criminal behaviour would not be required, and providers would be compelled to hand over the data requested. The bill also included new powers for law enforcement to order service providers to store existing data on a client and to produce that data on request.31
In addition, Bill C-30 required that the systems of telecommunications service providers (TSPS) be designed so as to make it easy for police to intercept online traffic.32 Given that complying with this provision would entail significant expense on the part of the carriers, for more than a year prior to presenting the bill, the government consulted extensively with Canada’s largest telecommunications companies about who should pay and about the feasibility of monitoring user behaviour in an increasingly complex “cloud-computing” environment.33 This relatively lengthy negotiation contrasted sharply with the complete lack of public consultation about lawful access during the same time period. Nevertheless, in response to a Conservative promise in the 2011 federal election to reintroduce this legislation if returned to government, civil liberties and Internet-rights advocacy organizations formed the Stop Online Spying coalition.34 As noted in Trend 3, the coalition started a letter-writing campaign, created a variety of videos, and garnered more than 145,000 signatories on its online petition, which called for the government to stop spying on citizens online.35 When the government finally introduced the bill on 14 February, it immediately ignited such public controversy that it was sent directly to committee for reworking and then was quietly and officially dropped a year later.36 The Internet surveillance that it was intended to authorize is, nevertheless, probably being carried out, and within the scope of prevailing privacy legislation. This is because the privacy statute that applies to the private sector, the Personal Information Protection and Electronic Documents Act (PIPEDA), already allows tsps to disclose to police investigators, in certain circumstances, personal information about clients without their knowledge or consent and without any need for a warrant.37
This situation illustrates several important points about the current state of Internet surveillance in Canada:
• The federal government and large private enterprises will, in secret and without public oversight, conduct surveillance and promote legislation that affects the fundamental relations between citizens and the state.
• Current privacy laws are too weak to serve as an effective bulwark against such challenges to taken-for-granted civil liberties.
• There is widespread public concern about surveillance across the political spectrum.
• Organized public opposition can play an important role in effectively resisting excessive Internet monitoring.
Conclusion
Surveillance practices pose significant challenges to privacy and other civil liberties. The embedding trend heightens these concerns in particular ways—notably, by making surveillance less and less visible even as it grows more and more commonplace. Because these practices are rarely visible from the outside and are usually bundled up with the other more legitimate activities on which they depend, it is extremely difficult to ensure the openness and transparency necessary to making those who carry out surveillance democratically accountable. Although Canadian privacy laws require organizations conducting such surveillance to bear the primary responsibility for making their practices publicly accessible, how is anybody to know whether or not they are doing this? It usually takes a highly publicized breach and a subsequent in-depth investigation to bring surveillance abuses to light. And, by that time, such violations are often a widespread industry practice and hard to remedy after the fact.
Notes
1 See Andrew Blum, Tubes: Journey to the Center of the Internet (New York: Harper Collins, 2012).
2 See Aaron Doyle, Randy Lippert, and David Lyon, eds., Eyes Everywhere: The Global Growth of Camera Surveillance (London and New York: Routledge, 2012), http://www.routledge.com/books/details/9780415696555/; Emily Jackson, “Hundreds of Unnamed Cameras Watching Vancouver,” TheThunderBird.ca, 10 December 2009, http://thethunderbird.ca/2009/12/10/hundreds-of-unnamed-cameras-watching-vancouver/; Andrew Clement, Joseph Ferenbok, Roxanna Dehghan, Laura Kaminker, and Simeon Kanev, “Private Sector Video Surveillance in Toronto: Not Privacy Compliant!” Proceedings of the 2012 iConference (New York: ACM, 2012), 354–62; and Sean P. Hier, Panoptic Dreams: Streetscape Video Surveillance in Canada (Vancouver: University of British Columbia Press, 2010).
3 See Brenda McPhail, Joseph Ferenbok, Roxanna Dehghan, and Andrew Clement, “‘I’ll Be Watching You’: What Do Canadians Know About Video Surveillance and Privacy?” iConference 2013 Proceedings (iSchools, 2013), 555–59, https://www.ideals.illinois.edu/bitstream/handle/2142/39966/276.pdf?sequence=5.
4 Andrew Clement, Joseph Ferenbok, Roxanna Dehghan, Laura Kaminker, Simeon Kanev, and Silvia Valdman, “Smart” Private Eyes in Public Places? Video Surveillance Analytics, New Privacy Threats and Protective Alternatives, Final Report, 23 July 2011, submitted to the Office of the Privacy Commissioner of Canada, http://surveillancerights.ca/downloads/Clement_Ferenbok etal - OPC - Private Eyes - Final Report with appendices.pdf, 5.
5 On the practice of “informating,” see Shoshana Zuboff, In the Age of the Smart Machine: The Future of Work and Power (New York: Basic Books, 1988).
6 See Margaret E. Fulton, In the Chips: Opportunities, People, Partnerships, report of the Labour Canada Task Force on Micro-electronics and Employment (Ottawa: Labour Canada, 1982), 89. Workplace monitoring became a bargaining issue with mail sorters at Canada Post (Canadian Union of Postal Workers [CUPW]), airline reservation agents at Air Canada (Canadian Airline Employees Association [CALEA]), and telephone operators at Bell Canada (Communications Workers of Canada [CWC]).
7 For details of the scandal, see the articles at “British Phone Hacking Scandal (Leveson Report),” New York Times, http://topics.nytimes.com/top/reference/timestopics/organizations/n/news_of_the_world/index.html.
8 David Lyon, Identifying Citizens: ID Cards as Surveillance (Oxford: Polity Press, 2009).
9 “Policy laundering” refers to the practice of national governments pushing for rulings by international bodies, often without democratic oversight, to make policy changes that would probably not be achieved through domestic legislative processes. See Ian Hosein, “International Relations Theories and the Regulation of International Dataflows: Policy Laundering and Other International Policy Dynamics,” paper presented at the annual meeting of the International Studies Association, Montréal, QC, 17 March 2004, http://citation.allacademic.com/meta/p_mla_apa_research_citation/0/7/3/8/8/pages73882/p73882-1.php; and Barry Steinhardt, “Problem of Policy Laundering,” American Civil Liberties Union (ACLU), 13 August 2004, http://26konferencja.giodo.gov.pl/data/resources/SteinhardtB_paper.pdf.
10 Passport Canada finally announced that as of 1 July 2013, all new Canadian passports issued are electronic passports. See Passport Canada, “About ePassports,” last modified 9 August 2013, http://www.ppt.gc.ca/eppt/about.aspx?lang=eng.
11 These jurisdictions include British Columbia, Manitoba, Ontario, Québec, Vermont, New York, Michigan, and Washington. See the map at http://www.getyouhome.gov/html/EDL_map.html. Several other provinces, including Saskatchewan and Nova Scotia, also considered EDLs but decided against them. Adoption has been much lower than projected and appears not have contributed to easing border congestion. See “Saskatchewan Halts New Enhanced Driver’s Licence Program,” news release, Government of Saskatchewan, 23 March 2009, http://www.gov.sk.ca/news?newsId=88eb5109-3361-4c9f-bafc-d4c226f5b897, and “Sask. Government Ditches ‘Enhanced’ Driver’s Licence Plan,” CBC News, 23 March 2009, http://www.cbc.ca/news/canada/saskatchewan/sask-government-ditches-enhanced-driver-s-licence-plan-1.808226. For Nova Scotia, see New Driver’s Licence and Identification Cards, Access Nova Scotia, http://www.novascotia.ca/snsmr/access/drivers/new-licence.asp (last updated 25 November 2013).
12 The standard specified for the EDL RFID chip is the EPC Gen2, short for EPCglobal UHF Class 1 Generation 2. For a discussion of the privacy and security controversies surrounding this particular chip, see “EPC Gen2,” Wikipedia, last modified 12 October 2013, http://en.wikipedia.org/wiki/Radio-frequency_identification#EPC_Gen2.
13 Brenda McPhail, Krista Boa, Joseph Ferenbok, Karen Louise Smith, and Andrew Clement, “Identity, Privacy and Security Challenges with Ontario’s Enhanced Driver’s Licence,” in 2009 IEEE Toronto International Conference, Science and Technology for Humanity (TIC-STH), Toronto, ON, 26–27 September 2009 (IEEE Xplore Digital Library, 2009), 904–9, doi: 10.1109/TICSTH2009.5444399.
14 See REAL ID Act of 2005, Pub. L. 109-13, http://www.gpo.gov/fdsys/pkg/PLAW-109publ13/html/PLAW-109publ13.htm.
15 Andrew Clement, Krista Boa, Simon Davies, and Gus Hosein, “Toward a National ID Card for Canada? External Drivers and Internal Complexities,” in Playing the Identity Card: Surveillance, Security and Identification in Global Perspective, ed. Colin J. Bennett and David Lyon (London and New York: Routledge, 2008), 233–50.
16 “Insurance Corporation Offers to Help ID Rioters,” CBC News, 18 June 2011, http://www.cbc.ca/news/canada/british-columbia/story/2011/06/18/bc-icbc-rioters-id.html.
17 A web bug, also known as a web beacon, a tracking bug, or a page tag, “is a graphics on a Web page or in an Email message that is designed to monitor who is reading the Web page or Email message”: Richard M. Smith, “The Web Bug FAQ,” Electronic Frontier Foundation, 11 November 1999, http://w2.eff.org/Privacy/Marketing/web_bug.html.
18 In seeking to dismiss a consumer privacy complaint, Google has drawn on a finding in the Smith v. Maryland case to the effect that “a person has no legitimate expectation of privacy in information he voluntarily turns over to third parties” (Smith v. Maryland, 442 U.S. 735 [1979], 743–44). See “Defendant Google Inc.’s Motion to Dismiss Plaintiffs’ Consolidated Individual and Class Action Complaint” (case 5:13-md-02430-LHK, document 44, filed 06/13/13, before the United States District Court, Northern District of California, San Jose Division), http://www.consumerwatchdog.org/resources/googlemotion061313.pdf, 19.
19 For more on deep packet inspection, see the DPI project website, http://www.deeppacketinspection.ca/.
20 See Telecom Regulatory Policy CRTC 2009-657, “Review of the Internet Traffic Management Practices of Internet Service Providers,” Canadian Radio-Television and Telecommunications Commission, 21 October 2009, Ottawa, http://www.crtc.gc.ca/eng/archive/2009/2009-657.htm.
21 See Office of the Privacy Commissioner of Canada, “Deep Packet Inspection Essay Project,” last modified 28 March 2013, http://dpi.priv.gc.ca.
22 “BCCLA Denounces Blocking of Website by Telus,” BC Civil Liberties Association, 26 July 2005, http://web.archive.org/web/20060101100357/http://www.bccla.org/pressreleases/05telus.htm.
23 Helmi Noman and Jillian C. York, West Censoring East: The Use of Western Technologies by Middle East Censors, 2010–2011, OpenNet Initiative, March 2011, http://opennet.net/west-censoring-east-the-use-western-technologies-middle-east-censors-2010-2011.
24 See “NSA Spying on Americans,” Electronic Frontier Foundation, n.d., https://www.eff.org/issues/nsa-spying.
25 The FISA Amendment Act is also referred to as the Foreign Intelligence Surveillance Act of 1978 Amendments Act of 2008: see www.intelligence.senate.gov/laws/pl110261.pdf.
26 One notable exception to this is Al Haramain Islamic Foundation v. Obama, which made it past the state secrets obstacle but in 2012 was denied on the technical legal basis known as “sovereign immunity.” See “Al Haramain v. Obama,” Electronic Frontier Foundation, n.d., https://www.eff.org/cases/al-haramain.
27 James Ball, “NSA’s Prism Surveillance Program: How It Works and What It Can Do,” The Guardian (UK), 8 June 2013, http://www.theguardian.com/world/2013/jun/08/nsa-prism-server-collection-facebook-google.
28 The nuclear submarine Jimmy Carter has been specially modified to conduct these underwater cable-tapping operations. See Associated Press, “New Nuclear Sub Is Said to Have Special Eavesdropping Ability,” New York Times, 20 February 2005, http://www.nytimes.com/2005/02/20/politics/20submarine.html?_r=1&.
29 Ron Deibert, Black Code: Inside the Battle for Cyberspace (Toronto: McClelland and Stewart, 2013), 43. See also Andrew Clement, “IXmaps—Tracking Your Personal Data Through the NSA’s Warrantless Wiretapping Sites,” in 2013 IEEE International Symposium on Technology and Society (ISTAS), Toronto, 27–29 June 2013 (IEEE Xplore Digital Library, 2013), 216–223, doi: 10.1109/ISTAS.2013.6613122.
30 See Meagan Fitzpatrick, “Online Surveillance Bill Could Change, Harper Signals,” CBC News, 15 February 2012, http://www.cbc.ca/news/politics/online-surveillance-bill-could-change-harper-signals-1.1150295. The bill was originally called “An Act to enact the Investigating and Preventing Criminal Electronic Communications Act and to amend the Criminal Code and other Acts” (2012): for the full text, see http://s3.documentcloud.org/documents/292611/bill-c-30.pdf.
31 Phillipa Lawson, Moving Toward a Surveillance Society: Proposals to Expand “Lawful Access” in Canada, BC Civil Liberties Association (BCCLA), 2012, http://bccla.org/wp-content/uploads/2012/03/2012-BCCLA-REPORT-Moving-toward-a-surveillance-society1.pdf, 5.
32 Ibid.
33 Anna Mehler Paperny, “Telcos in Talks with Ottawa to Shape Internet ‘Spy’ Bill: Documents,” Globe and Mail, 29 June 2012, http://m.theglobeandmail.com/technology/tech-news/telcos-in-talks-with-ottawa-to-shape-internet-spy-bill-documents/article4376958/?service=mobile.
34 The Stop Online Spying coalition had a broad membership from across Canada and was convened by OpenMedia.ca: see http://stopspying.ca.
35 See, for example, the video “(Un)Lawful Access: Canadian Experts on the State of Cybersurveillance” (2011), at http://unlawfulaccess.net/.
36 John Ibbitson, “Harper Government Kills Controversial Internet Surveillance Bill,” Globe and Mail, 11 February 2013, http://www.theglobeandmail.com/news/politics/harper-government-kills-controversial-internet-surveillance-bill/article8456096/.
37 Leo Singer, “Unwarranted Access?” National: Legal Insights and Practice Trends, Canadian Bar association, June 2012, http://www.nationalmagazine.ca/Articles/June-2012-Issue/Unwarrantedaccess.aspx.