Chapter 9
Keeping It Safe: Reviewing Slack’s Security and Privacy Settings
IN THIS CHAPTER
 Configuring Slack’s security and account settings
Configuring Slack’s security and account settings
 Reviewing Slack’s different privacy settings
Reviewing Slack’s different privacy settings
 Examining Slack’s message- and file-retention policies
Examining Slack’s message- and file-retention policies
At a bare minimum, Slack lets you and your coworkers easily share content in a far more targeted way than email ever could. Take this argument to its logical conclusion: Employees can contribute to a comprehensive and easily searchable knowledge repository. I can think of few more prized assets for any organization in the Information Age.
But what if this asset quickly turned into a massive liability? That is, what if organizations couldn’t secure all of their sensitive employee communication, intellectual property, and key documents from prying eyes and bad actors? Put differently, creating a comprehensive trove of knowledge is downright dangerous if firms couldn’t lock it down. Without substantial safeguards in place, organizations and employees would be justifiably loathe to hop on the Slack train.
It’s time to cover Slack’s most important security and privacy controls.
Getting Acquainted with Slack Security
Allow me to start by stating the obvious: No application, system, individual, firm, or data source is entirely secure. Hackers are remarkably clever, and organizations are always playing defense. Always. Former Cisco Systems CEO John Chambers summed it up perfectly when he said, “There are two types of companies: those who have been hacked, and those who don’t yet know they have been hacked.”
That’s not to say that organizations are powerless against black hats. As I tell my students when I cover enterprise security, there are plenty of surefire ways to decrease the chances that bad actors cause chaos in an organization. They include updating software in a timely manner, requiring strong passwords, enabling two-factor authentication, educating employees, and using firewalls and virtual private networks (VPNs).
Security and Slack’s Evolution
As I covered in Chapter 1, in 2014 Slack’s management decided to change the company’s focus from a video game to a collaboration tool. At the time, there was no guarantee that its new direction would ultimately bear fruit. Put differently, in the company’s early days with only a handful of employees, it was fair for everyone to ask, “Why devote its limited time and money on security to a communication tool that relatively few people use?”
Well, we’re not in Kansas anymore for two reasons. First, since 2014, Slack has become far more popular. (That’s one reason that you’re reading this book. You won’t find any For Dummies books for niche products.) Second, a long with popularity, Slack has increased in importance. Customers use the collaboration tool to perform a burgeoning number of essential company functions.
Slack has responded on both fronts. Since its nascent days, the company has spent considerable resources on beefing up its security features. In a way, it had no choice. Consider what would happen if Slack’s management failed to take security considerations seriously. Many organizations would dismiss using it outright and opt for another collaboration and communication tool. (Chapter 3 describes how Slack faces plenty of competition.) For years now, Slack has not been the only pretty girl at the ball.
Configuring Slack’s Access and Security Settings
At a high level, Slack provides two types of measures for protecting workspace data:
- Customer-driven measures: Security-related measures that Slack’s customers can take.
- Slack-driven measures: Security features that exist whether its customers activate them or not. That is, Slack ships them with the app.
If you’re thinking that different organizations may require vastly disparate levels of security, trust your instincts. A government agency that possesses sensitive citizen and infrastructure information requires greater controls than your local pizzeria or vintage clothing store. To this end, Slack provides a wide array of powerful security options — all of which I can’t possibly cover in this book.
Confirming sign-ins via email
Say that you attempt to log into a Slack workspace from an unrecognized browser. Slack wants to ensure that it is really you and not a black hat. As such, expect to receive a confirmation email similar to the one shown in Figure 9-1.
Resetting your password
From time to time, people forget their passwords. Like just about every application these days, Slack easily lets you reset it.
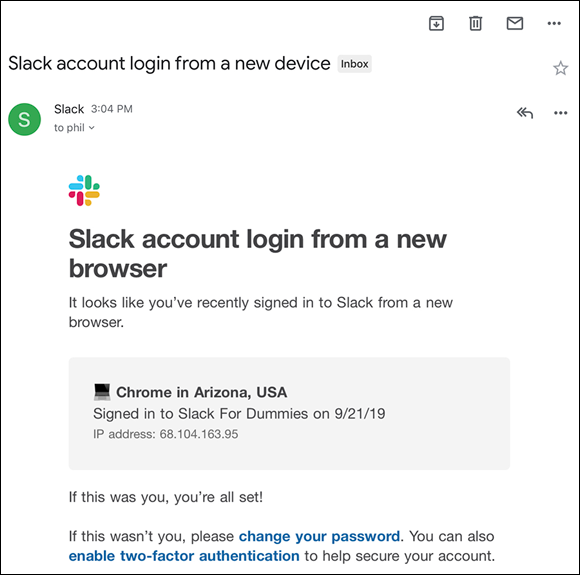
FIGURE 9-1: Slack email confirmation.
While signed out of Slack
Follow these directions to reset your password if you can’t log into your Slack workspace:
- Go to
http://slack.com/signin. -
Enter your workspace URL and click on the green Continue button.
(See Chapter 2 for more information on this topic.)
-
Below the sign-in form and underneath the green Sign in button, click on Forgot password.
Slack takes you to a page that requires you to input your email address.
-
Enter your email address.
Make sure that it's the same one that Slack has on file.
-
Click on the green Get Reset Link button.
Slack sends you an email with a link. Check your inbox.
 If your email is tied to multiple workspaces, then Slack’s email will contain links to all of them. Put differently, your login credentials may apply to more than one workspace.
If your email is tied to multiple workspaces, then Slack’s email will contain links to all of them. Put differently, your login credentials may apply to more than one workspace. - In the email, click on the Choose a New Password button.
- Enter your new password and then confirm it.
- If they both match, then click on the green Change my password button.
While signed in to Slack
If you’re still logged into Slack and forgot your password, then follow these steps:
- Click on the main menu.
-
Choose View profile from the menu.
Slack opens your profile on the right side of your screen.
- Click on the three vertical dots that appear below your profile picture.
-
Click on Account settings.
Slack opens a window or tab in your computer’s default browser.
-
Click on the expand button to the right of Password.
If you don’t see this option, then your company requires single sign-on to sign in to Slack.
 In a nutshell, single sign-on or SSO allows people in an organization to log into disparate applications, systems, and web services via a single set of credentials.
In a nutshell, single sign-on or SSO allows people in an organization to log into disparate applications, systems, and web services via a single set of credentials. - Type your current password and then enter your new password.
- Click on the green Save Password button.
Viewing access logs
Like many software vendors, Slack generates access logs for its customers. Collectively, these records of user activity and changes provide organizations with information on who did what and when. Access logs can be invaluable when investigating instances of misuse or hacks or even identifying problems. See Figure 9-2 for a sample access log.
To view an access log, follow these steps:
- Click on the main menu.
-
From the drop-down menu, select Settings & administration and then Workspace settings.
Slack shows you the data to which you have access.
Slack opens your profile on the right side of your screen.
At the right of the page, you see the words Access Logs.
- (Optional) If you’d like, you can download the data that Slack displays here as a comma-separated value (CSV) file by clicking on the white Download Access Logs button and saving the file.
Guests are only able to view their own activity. Workspace Owners and Admins can see far more information about who logged in, the device used, the time of day, the Internet Protocol (IP) address, and when.
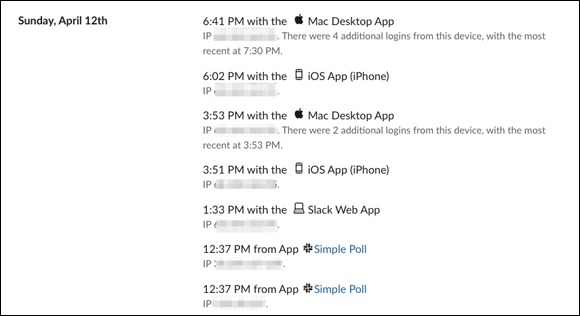
FIGURE 9-2: Example of a simple Slack access log.
Enabling two-factor authentication
What happens if someone gains access to your email address and password? It’s not hard to imagine an unsavory sort posting horrible messages and lascivious photos in Slack under your name. In a professional context, such behavior may result in your suspension, demotion, or even termination.
Like many companies, Slack wants to minimize the chance that these events happen. To this end, Slack encourages its customers to activate an additional security measure called two-factor authentication — usually abbreviated as 2FA. Rolled out in March 2015, 2FA adds an additional level, or factor, to signing in — hence its name. What’s more, organizations can opt to deploy this individually or require all Slack workspace members to use it to sign in.
To set up 2FA, make sure that you have your phone handy and follow these steps.
-
Download a Time-Based, One-Time Password (TOTP) app.
Popular ones include Google Authenticator, Duo Mobile, or Authy. (I have used the first two and found them to be intuitive. iPhone fans can also use the 1Password app.)
- Go to
my.slack.com/account/settingsand log in, if prompted. - Click on the white Expand button under the item labeled Two-Factor Authentication.
-
Click on the Set Up Two-Factor Authentication button.
 If you don’t see this option, then someone in your organization with greater permissions has disabled it. For example, a Workspace Owner may have required single sign-on and 2FA. The organization also may have prohibited Admins and members from disabling this feature.
If you don’t see this option, then someone in your organization with greater permissions has disabled it. For example, a Workspace Owner may have required single sign-on and 2FA. The organization also may have prohibited Admins and members from disabling this feature. -
Elect how you’d like to receive authentication codes.
You can use choose to receive a SMS text message or use one of the authentication apps mentioned in Step 1. If you want to receive a SMS text message, proceed to Step 6. Otherwise, skip to Step 7.
 To paraphrase Walter White in one of my favorite Breaking Bad scenes, I prefer option B: I use an authentication app. If you do as well, then continue to Step 6.
To paraphrase Walter White in one of my favorite Breaking Bad scenes, I prefer option B: I use an authentication app. If you do as well, then continue to Step 6.Check your inbox. Slack sends you an email similar to the one displayed in Figure 9-3.
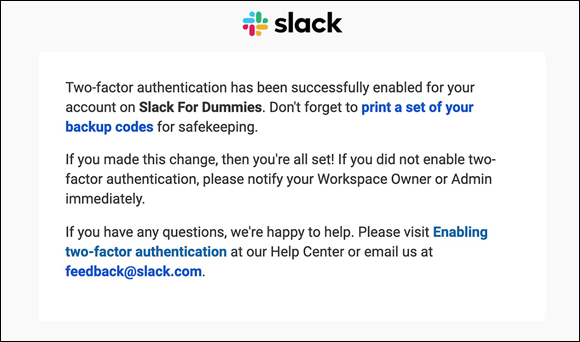
FIGURE 9-3: Slack email confirming individual 2FA activation.
-
Verify your activation using the one-time code texted to you.
To do so, select your country from the menu and enter your complete mobile phone number. Remember to include your area code. Slack sends a six-digit verification code to your device. Enter this code in your browser on the Slack 2FA configuration page and then click on the gray Verify code and enable button. Slack then sends you a text message that contains a one-time authentication code.
You’ll need to enter these codes whenever you sign in to your workspace after having logged out. When you enter the code, Slack takes you to the workspace.
 I encourage you to click on the link to view your specific workspace backup codes. Either print them or save them in a file on your computer or phone. If you lose your secondary device, then those codes will let you log back into your Slack workspace. Note that you can use each code only once.
I encourage you to click on the link to view your specific workspace backup codes. Either print them or save them in a file on your computer or phone. If you lose your secondary device, then those codes will let you log back into your Slack workspace. Note that you can use each code only once. -
Alternatively, verify your account using an authentication app.
To do so, open your preferred authenticator app on your smartphone, click on the + icon on the app, and scan the barcode in the browser.
In your browser, enter the code that appears at the bottom of the app. You have succeeded in enabling 2FA. Slack sends you an email indicating as much.
Say that you’ve been using Slack without enabling 2FA. A yellow triangle icon appears over your workspace icon to the left of the sidebar, as shown in Figure 9-4. This means that you have to sign back in. Once you do, that yellow icon disappears.

FIGURE 9-4: Slack workspace icon indicating that member needs to sign in again after enabling 2FA.
Additional security features
Slack also provides granular security and access options including
- Manage session duration: Perhaps your company wants people to log in to Slack every week or every month.
- Whitelist workspaces: This option prevents employees on a company network from signing on to unapproved workspaces.
- Enable and tweak single sign-on or (SSO): Slack’s options here include resetting all sessions, changing SSO provider, and more.
- Reset all workspace passwords: This option is especially useful in the event of an organization-wide breach.
Enhancing Security via Slack Enterprise Grid
Slack’s newest and most expensive plan offers a number of enhanced security options for large organizations. I touch upon many of them throughout this book, but I want to call specific attention to one of them here.
Slack Enterprise Key Management or EKM offers its most security conscious customers an extra layer of protection against bad actors. Customers on the Enterprise Grid plan have the ability to configure settings at a remarkably granular level.
EKM accomplishes this objective by offering additional encryption keys to unlock access to different features. For example, Workspace Owners and Admins can control access to specific channels, messages, and files. They can also just as easily revoke their access. Finally, EKM provides Owners and Admins with enhanced member-activity logs showing who did what when and where they accessed data within Slack.
It’s not hard to envision beneficial applications of EKM. Perhaps CYE Industries doesn’t want Larry to share an especially sensitive file with others. Maybe Cheryl wants to know exactly where and on what device Larry accessed that file. CYE’s management can even revoke Larry’s access to that file for a predetermined period of time.
No, Enterprise Grid isn’t cheap. However, consider the benefits for large organizations in healthcare and financial services and other highly regulated industries. These customers are often willing to pay for Slack’s premium security features. As such, EKM is right up their alley.
Examining Privacy in Slack
If the last few years have taught us anything, it’s that we have reached a turning point with respect to privacy: Companies can no longer treat it as an afterthought.
Case in point: Facebook, the social network with 2.5 billion monthly active users. Wunderkind CEO Mark Zuckerberg has long emphasized “connecting the world” over user privacy. The company’s recent claims that it now supports intelligent privacy regulation indicate that it may finally be taking a markedly different approach with how it treats user data.
It’s an understatement to claim that balancing competing interests with privacy is extremely challenging. The potential for conflict is real and nuanced. For example, Slack’s customers may want the unfettered ability to view and export all messages and files in their workspaces. (Chapter 11 covers exporting data in more detail.) For their part, employees may be reluctant to use Slack if Big Brother is watching. What to do?
Fortunately, Slack provides a number of safeguards designed to protect user data.
Message encryption
Forget Slack for a moment. Generally speaking, people who send encrypted messages via Signal or other secure messaging apps need not worry about prying eyes. Say that bad actors intercept those messages. It doesn’t matter: the content is indecipherable gobbledygook. (The technical term here is ciphertext.)
Slack uses end-to-end encryption on all DMs as well as all content posted in public and private channels. As a result, no third-party can intercept them while they’re in transit — that is, moving from sender to recipient. Let me be crystal clear: Slack users can rest assured that their messages remain secure.
That doesn’t mean, though, that Workspace Owners can never access members’ private messages. And here’s where things get a bit more nuanced.
For starters and by default, Slack prohibits Workspace Owners and Admins from accessing others’ content in private channels and DMs. (Public channels are a different story.
Still, scenarios exist in which organizations may need to access private employee correspondence. Examples here include meeting legitimate legal, law enforcement, or regulatory requirements.
Slack doesn’t grant these requests for access willy-nilly. To acquire private employee information, Workspace Owners need to submit an application to Slack, and the company needs to approve it.
Second, your organization’s billing plan is also a factor here. All things being equal, Org Owners and Admins may be able to obtain data from private channels and DMs if Slack grants them approval. (Chapter 11 has much more to say about the limitations and process of exporting data from Slack.)
What data Workspace Admins can Access
You may be understandably concerned about the content that Workspace Owners can view. Here’s how to find out who can view and download what in Slack:
-
Go to
slack.com/account/teamand log in to your workspace.Slack displays a simple three-tab web page.
- Click on the Retention and Exports tab on the right.
-
Scroll down to What data can my admins access.
Slack displays information on how long the workspace stores conversation history and the type of data that Admins can access.
-
Read which types of messages Workspace Owners can potentially view and export.
At a minimum, Workspace Owners can view and export messages in public channels. They may also be able to do the same with private messages and channels under extenuating circumstances. Again, the organization needs to submit an application to Slack.
A few notes are in order here. First, hold your outrage. It's downright silly to claim that senior management and auditors should never be able to access critical organizational communications under any circumstances at all. Do a simple Google search of the Tyco, Enron, WorldCom, and Wells Fargo scandals. All of these financial crimes left plenty of digital breadcrumbs. If company auditors hadn’t been asleep at the wheel, maybe these companies wouldn’t have fallen so far from grace.
Second, this ability should not be a revelation to you, nor should it discourage you from using email over Slack. Make no mistake: IT folks at your company can already access your work emails. If you think otherwise, then you’re sorely mistaken.
Finally, just because Workspace Owners may be able to view this information doesn’t necessarily mean that they will.
Workspace message-retention settings
How long do you want to keep messages in your Slack workspace? Do you want to hold on to them indefinitely? Alternatively, do you want to purge them once they reach a certain age?
I’d argue for the first option, but perhaps your company legitimately needs to delete older messages. Workspace Owners and Admins can establish message-retention settings for their workspaces by following these steps:
- Click on the main menu.
-
From the drop-down menu, select Settings & administration and then Workspace settings.
Slack launches a window or tab in your default browser.
- Under the Settings tab, scroll down to Message Retention & Deletion.
- Click on the white Expand button to the right.
-
Select the desired settings for public and private channels and DMs.
Note that you can apply different settings to different items. Options here include
- Keeping everything
- Keeping all messages but not tracking message revisions
- Deleting messages and their revisions after a certain period of time
- Letting workspace members override these settings
- If desired, select the box to allow workspace members to override these settings and click on the green Save button.
Setting message retention policies for a specific channel
On occasion, organizations want to override global message-retention settings for specific channels. Perhaps conversations in one channel are particularly important or sensitive and need to go poof.
Say that you want to routinely purge channel messages after a certain period of time. That is, you don’t want to have to remember to delete them after three months or whatever. If your role permits, then follow these steps:
- Click on the channel whose settings you want to customize.
-
Click on the information (i) icon in the top right-hand corner.
Slack displays a four-pane tab with the word Details above it.
-
Click on the More icon on the far right.
Slack displays a new pane underneath your mouse.
- From the drop-down list, click on Edit message retention.
-
Select the box for Use custom retention settings for this conversation.
This step allows Slack to automatically delete messages after a fixed time period. In other words, you can override Slack’s global options for all channels in the workspace.
-
Enter the number of days or years after which Slack will delete messages and their revisions.
The maximum at present is 100 years.
-
Click on the Save button.
 Slack warns you that there’s no going back. Not even Slack will be able to retrieve messages that you delete after this period.
Slack warns you that there’s no going back. Not even Slack will be able to retrieve messages that you delete after this period. - Select the radio button next to Yes, apply these new settings and then click on the red Apply Settings button.
Override message retention settings for individual DMs and conversations
Sometimes we no longer need to view old messages. Of course, you can manually delete them as needed. (See Chapter 4 for additional actions that you can perform on DMs and conversations.) But what if you want a conversation with a colleague to disappear at some point in the future?
- Click on the conversation whose settings you want to customize.
-
Click on the information (i) icon in the top right-hand corner.
Slack displays a three-pane tab with the word Details above it.
-
Click on the More icon on the far right.
Slack displays a panel underneath our mouse.
- Click on Edit message retention.
- Click on the radio-box Use custom retention settings for this conversation.
- Click on the green Save button.
- Under the text Delete messages and their revisions after: enter the number of days or years that Slack should store this conversation.
-
Click on the green Save button.
Slack warns you that you are overriding your workspace’s default message-retention settings for this conversation.
- Click on the Yes, apply these new settings box.
- Click on the red Apply Settings button.
File-retention settings
Remember that Slack’s default content setting is inclusion. That is, Slack keeps all employee and guest files forever in workspace. Yes, Slack retains user content even if the individual leaves the company and/or the workspace. Of course, you can easily modify that setting:
- Click on the main menu.
- From the drop-down menu, select Settings & administration and then Workspace settings.
- Under the Settings tab, scroll down to File Retention & Deletion.
-
Click on the white Expand button to the right.
Your two options are
- Keep all files: This option is the default.
- Keep all files, only for a set number of days: If you enter a value here, then Slack warns you that it will automatically delete files when their age hits that value. Click on the red Confirm Settings button.
Understanding Slack’s Tricky Regulatory Environment
When it comes to privacy, we all have our own opinions. Maybe you believe that we should finally rein in the unfettered power of Google, Facebook, and other tech leviathans. Alternatively, you might opt for a more laissez-faire approach: It should be an individuals’ responsibility to make informed decisions about the data they put out there. Perhaps you fall somewhere in between these two poles.
Regardless of your convictions, one thing is certain: All companies must abide by legislation in the countries in which they do business. Slack is no exception to this rule. This chapter closes with a few thoughts on how Slack is navigating key privacy issues in a tricky regulatory environment. Current privacy legislation may not affect your organization at the moment. It’s a good bet, though, that at some point it will.
Restrictions on data and file retention
If you live and work in Europe, then you’ve most likely heard of General Data Protection Regulation (GDPR). At a high level, this 2018 legislation represents the European Union’s most recent attempt to restrict what companies do with its citizens’ data. The EU takes privacy far more seriously than the United States does, but that’s a topic for a much longer conversation over beers.
Slack is committed to helping its European customers understand and comply with GDPR. For more information on this topic, see https://slack.com/gdpr.
Don’t be surprised if more countries follow the EU’s lead by passing more meaningful privacy legislation in the near future. I’m not clairvoyant, but I suspect that forthcoming privacy laws will impact your organization’s ability to retain Slack messages and files in the years to come.
Data residency
Like many contemporary tech companies, Slack embraced cloud computing as a foundational technology from the get-go. (See Chapter 1 for more information about Slack’s technology stack.) In layman’s terms, this choice confers significant benefits to its users: They can access Slack and its data wherever they are as long as they are connected to the Internet. Thanks to cloud computing, Slack works anywhere, whether you’re working at your desk in Manhattan, embarrassing yourself on the golf course, or visiting museums in Timbuktu. People of a certain age remember when such convenience was a pipe dream.
In a practical way, then, users may not even know — much less care about — the physical location in which their organization’s Slack’s data ultimately resides. Legally, though, that exact location is starting to matter a great deal. Increasingly governments around the world are passing laws mandating where companies can store their citizens’ data. To wit, many large employers now have to deal with data residency: Laws may require them to physically store and process customer, user, and employee data within the borders of a specific country. What’s more, fines for violating data residency statutes can be substantial, especially in the EU. In response, many multinational organizations are beginning to define their own policies in this vein.
Again, Slack’s got you covered. Customers on Slack’s Plus and Enterprise Grid plans can easily port their data to physical locations in different countries if the legal or regulatory need arises. For more on this subject, visit bit.ly/slack-dr.