Wireless networks have been plagued with many well-publicized issues since they became popular at the end of the 1990s. Because of such problems and the risks they pose, some people might argue that they shouldn’t be used at all. But due to their ease of use and convenience, it’s clear that wireless networks are here to stay, so you’d better do everything you can to make them as secure as possible.
Because of the many problems that have afflicted Wired Equivalent Privacy (WEP), anyone seeking to implement a secure wireless network should realize that it’s not a good solution. And, while the pre-shared key (PSK) varieties of WiFi Protected Access (WPA) and WPA2 offer better security than WEP, they still have their problems. As you’ll see in this chapter, the best solution is to use WPA or WPA2 with 802.1X to provide fine-grained authentication for your wireless network. You’ll also see how to unleash the potential of your commodity wireless router or access point (AP) by replacing its firmware with a compact Linux distribution.
For more community-minded users who want to share their wireless networks, this chapter also covers the use of captive portals. By using a captive portal, you can provide open wireless access to nearby users but still maintain some control over who can access your network.
Upgrade your SOHO wireless router into a sophisticated network device with OpenWRT.
As network device manufacturers have moved to cut costs and increase profits, many have sought to utilize open source technologies wherever they can. This has created a pool of hackable (in the good sense) devices that can easily be modified by tweaking their open source components. One such line of devices is Linksys’s WRT54G line of low-end wireless routers. These devices have proven so popular with the open source community that many alternate firmware distributions have been created for them. In fact, when Linksys recently made changes to the latest revisions of the WRT54G that prevented it from running Linux, they created a new model for fans of the earlier versions, the WRT54GL, that continued to use Linux for its firmware.
One of the more flexible firmware distributions available is OpenWRT (http://openwrt.org). The beauty of OpenWRT as opposed to other alternative firmwares is that it’s a bare-bones minimal system with a large set of precompiled packages from which you can pick and choose, installing whatever suits your needs. For instance, you can easily use OpenWRT to monitor wireless network traffic with the same tools you’d use with a Linux-based laptop. OpenWRT also supports a significant number of other routers available from Linksys and other vendors that have been built on a common hardware platform.
Tip
Before you begin installing OpenWRT, be sure to check the rather lengthy list of supported models (http://wiki.openwrt.org/TableOfHardware). Because so many models are supported, this hack covers only the most common: the Linksys WRT54G. Supported models should have links to installation notes specific to them.
For the
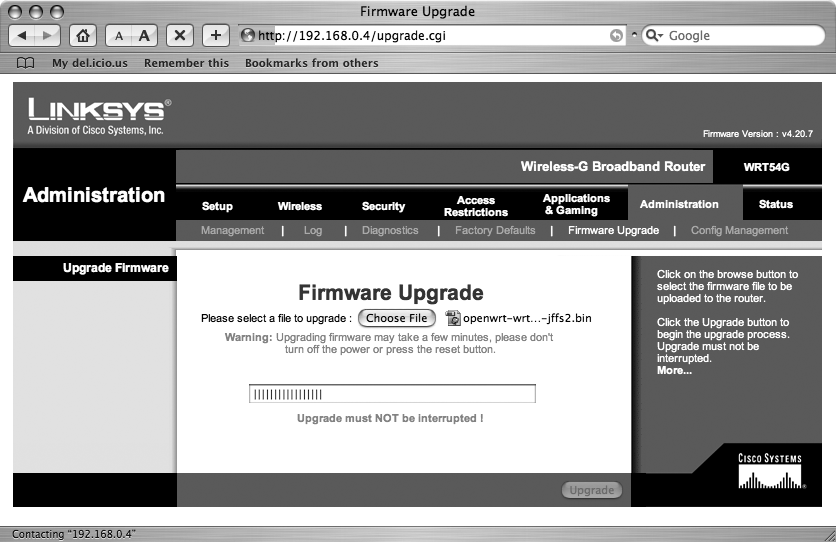
WRT54G, begin by downloading the firmware image, openwrt-wrt54g-jffs2.bin, from http://downloads.openwrt.org/whiterussian/newest/bin. Then, log into your router’s web administration interface and go to the Administration section. After it loads, click the Firmware Upgrade link and you’ll be presented with a page that allows you to upload a firmware image with which the router will reflash itself. Select the firmware image that you downloaded and click the Upgrade button. You should see a page like the one shown in Figure 7-1.
Once the router has been reflashed with the OpenWRT image, you should see a page letting you know that the upgrade was successful. The router will also automatically reboot once the upgrade has completed. After it has rebooted, you should be able to telnet to the IP address that you had the router configured to use before you installed OpenWRT, using a command like the following:
$ telnet 192.168.0.4
Trying 192.168.0.4...
Connected to 192.168.0.4.
Escape character is '^]'.
=== IMPORTANT ============================
Use 'passwd' to set your login password
this will disable telnet and enable SSH
------------------------------------------
BusyBox v1.00 (2006.03.27-00:00+0000) Built-in shell (ash)
Enter 'help' for a list of built-in commands.
_______ ________ __
| |.-----.-----.-----.| | | |.----.| |_
| - || _ | -__| || | | || _|| _|
|_______|| __|_____|__|__||________||__| |____|
|__| W I R E L E S S F R E E D O M
WHITE RUSSIAN (RC5) -------------------------------
* 2 oz Vodka Mix the Vodka and Kahlua together
* 1 oz Kahlua over ice, then float the cream or
* 1/2oz cream milk on the top.
---------------------------------------------------
root@openwrt:/# When you log in, you should see a banner like the one shown in the previous output. The banner tells you two things. If you set a password for the root account, the telnet daemon will be disabled and the SSH daemon will be enabled, so that you can connect to your router securely. The banner also tells you how to make a White Russian, which is the code name for this particular version of firmware (White Russian RC5).
Now, type reboot to reboot the router and unpack the
JFFS2 filesystem. After it has finished booting, log in again. Then set a password for the root account by running passwd, and reboot the router yet again.
You should now be able to log in via SSH:
$ ssh root@192.168.0.4
The authenticity of host '192.168.0.4 (192.168.0.4)' can't be established.
RSA key fingerprint is 26:ed:7b:ae:7f:0d:aa:63:e8:f4:c1:6c:b3:09:8b:10.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '192.168.0.4' (RSA) to the list of known hosts.
root@192.168.0.4's password:
sh: /usr/X11R6/bin/xauth: not found
BusyBox v1.00 (2006.03.27-00:00+0000) Built-in shell (ash)
Enter 'help' for a list of built-in commands.
_______ ________ __
| |.-----.-----.-----.| | | |.----.| |_
| - || _ | -__| || | | || _|| _|
|_______|| __|_____|__|__||________||__| |____|
|__| W I R E L E S S F R E E D O M
WHITE RUSSIAN (RC5) -------------------------------
* 2 oz Vodka Mix the Vodka and Kahlua together
* 1 oz Kahlua over ice, then float the cream or
* 1/2oz cream milk on the top.
---------------------------------------------------
root@openwrt:~# Now you’ll need to set a DNS server for OpenWRT to use when resolving DNS names. You might think this is as straightforward as just editing /etc/resolv.conf, but this file is created dynamically at boot according to the contents of the NVRAM. Therefore, you’ll need to set the
lan_dns NVRAM variable. You’ll also need to set the default gateway (
lan_gateway):
#nvram set lan_dns=192.168.0.2#nvram set lan_gateway=192.168.0.1#nvram commit#reboot
Now, log in again and run
ipkg update:
# ipkg update
Downloading http://downloads.openwrt.org/whiterussian/packages/Packages
Updated list of available packages in /usr/lib/ipkg/lists/whiterussian
Downloading http://downloads.openwrt.org/whiterussian/packages/non-free/Packages
Updated list of available packages in /usr/lib/ipkg/lists/non-free
Successfully terminated.This command contacts the OpenWRT package repositories and updates the list of packages that are available for installation. After it’s finished updating, you can run ipkg list to see all of the packages. If you want to see the ones that are actually installed, run ipkg list_installed instead. To install a package, simply run ipkg install
<package name>.
Out of the box, most of your wireless settings should carry over from the standard Linksys firmware to OpenWRT. However, if you’re using WPA-PSK or 802.1X instead of WEP (please do, because WEP is horribly insecure), you’ll need to install the nas package. After you’ve done that and rebooted, you should see the nas binary running:
# ps -aux | grep nas
431 root 480 S /usr/sbin/nas -P /var/run/nas.lan.pid -l br0 -H 34954 -i eth2 -A -m 132 -k XXXXXXXXXXXXXXXYou should now be able to connect to your router without reconfiguring any of your wireless clients.
In the case shown in this example, WPA-PSK is being used and the Xs correspond to the password, which is now set via the
wl0_wpa_psk NVRAM variable. For more information on what NVRAM variables you can use for configuring your router, take a look at http://wiki.openwrt.org/OpenWrtDocs/Configuration.
As you’ve seen, there are many more packages available for OpenWRT. For instance, you can easily install TcpDump or Kismet through ipkg. The possibilities are nearly limitless. For just two examples, you can set up a RADIUS server to authenticate your wireless users [Hack #77] or turn your router into a captive portal [Hack #78].