“Why do I need a wireless network?” was a question people used to regularly ask. You will not hear this question much anymore, though. The main reasons why people want wireless networks these days are increased mobility and to avoid cabling issues.
When wireless networks started, they had access speeds of 1–2 Mbps; current standards have network speeds higher than 100 Mbps. At one time, wireless networking equipment was a premium addition to a network, but this equipment has become a commodity and is inexpensive enough that anybody can start up a wireless network.
Components of a wireless network
The two main components of wireless networks are clients and access points. Clients are computers with wireless network cards; these cards work just the same as wired network cards, but without the wires. Access points, which act as a consolidation point for multiple wireless clients, have a connection to a traditional wired network. Some new access points allow linking multiple access points through wireless links, extending the range and coverage of a wireless network without having all access points connected to a wired network, thereby saving on wiring costs.
Most laptops now include wireless network cards as an integrated feature, and wireless network cards are available for desktop computers, connecting through PCI, PCI Express (PCIe), or USB. It is great that many computers have integrated wireless cards, but be prepared as new technology arrives on the scene since you will likely end up using an expansion option on your computer to add an updated wireless card to your computer.
Wireless networks used to command a premium, but wireless networking components have become a commodity. You now have several choices, all less than $100. The difference in price between the inexpensive units and expensive units is based on the strength of the radios, the features that are available on the unit, and the brand.
If you work with a wireless network that has an access point, the network client runs in infrastructure mode, which has access points making up the underlying network infrastructure. If the network is composed only of clients joined to form a network, the network runs in ad hoc mode, which is typically used only when people need to exchange files or work together in a location without an access point. This type of work situation often happens when people use a temporary location — say, a conference room — to work on a project for a couple of days. Instead of relying on a 4–8-port mini-switch or hub with which files could be shared, folks can just use an ad hoc wireless network. Both wireless network types are shown in Figure 2-1.
 Most wireless networks are composed of access points and wireless clients, so unless the question specifies ad hoc, access points should be expected to be on the network.
Most wireless networks are composed of access points and wireless clients, so unless the question specifies ad hoc, access points should be expected to be on the network.
Connecting to a network
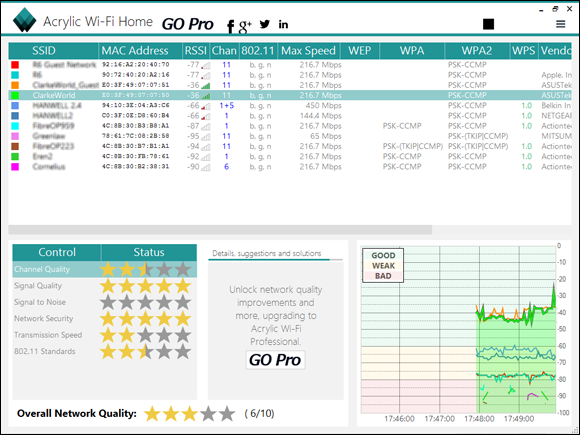
Every wireless network is identified by an SSID (Service Set Identifier), which is used by all clients on the network, identifying them as members of the network. The SSID is a case-sensitive name of 32 or fewer characters. Every manufacturer sets a default SSID. However, for security and to reduce confusion with neighboring access points, this default should be changed to a unique name. To connect to a wireless network, you need to know the SSID.
 Some manufacturers refer to the SSID as a BSSID (Basic Service Set Identifier) or an ESSID (Extended Service Set Identifier). The IEEE 802.11-1999 wireless network standard defines an ESSID as a set of access points using the same SSID and channel, and operating as a single BSSID to their wireless network clients.
Some manufacturers refer to the SSID as a BSSID (Basic Service Set Identifier) or an ESSID (Extended Service Set Identifier). The IEEE 802.11-1999 wireless network standard defines an ESSID as a set of access points using the same SSID and channel, and operating as a single BSSID to their wireless network clients.
After your wireless network card driver is installed you can then connect to the wireless network by its SSID.
Windows 7, Vista, and Windows 8.1
If you use the default Windows 7, Vista, and 8.1 software, open the Network and Sharing Center and click the View Status link next to your wireless card. This provides you with information such as connection speed, SSID, and signal strength. If you are not yet connected to the network, click the Manage Wireless Connections link in the Network and Sharing Center. From there, you can choose to add a new wireless network manually or by viewing from the networks in your area that are broadcasting their SSIDs.
To configure a connection to one of the networks, simply select the network and then click the Connect button. When connecting to a wireless network, if you need to enter a security key, you are prompted to enter the required information. Both the Network and Sharing Center and the Wireless Network Connection Status dialog box are shown in Figure 2-2.
Wireless standards
Wireless networks are defined by several standards, and the performance and security features for wireless networks are constantly improving. What’s more, because of constant improvements, new standards continually emerge. Gordon Moore of Intel predicted that the components in a processor’s integrated circuit would double every 24 months. This statement has since been named Moore’s Law, and has been applied to many areas of the computing industry. As Moore’s Law is applied to more sections of the computer industry, wireless is just another section of the industry that falls to those general rules, with speed doubling every two years.
The main wireless standards currently in use are 802.11a, 802.11b, 802.11g, and 802.11n, with other standards on the horizon. Each of these technologies is based upon published standards, and the upcoming ones are usually based upon several draft standards. Some hardware manufacturers have started to supply hardware capable of supporting the upcoming standards and using some of the new features. Typically, if the manufacturer can meet the hardware standards, the software can be updated later via a firmware update.
To go along with the standard features, many vendors choose to implement additional features not in the standard or make propriety enhancements, like many of the vendors who advertise special speed enhancements.
The following sections outline the main features of each of the 802.11 wireless networking standards.
802.11a
Released in 1999 (but not actively shipping until component supply issues were resolved), 802.11a networks operate in the 5 GHz radio spectrum. Other devices, such as newer cordless phones, also run in this unlicensed spectrum. Overall, the 5 GHz space is less occupied by devices compared with the 2.4 GHz space used by most other wireless devices. For 802.11a networks, there are 12 non-overlapping signal channels.
The network rated speed of 802.11a is 54 Mbps, but in most situations you can expect to see about half that speed. The typical range for this type of network is about 100 feet (30 meters).
Although the 5 GHz frequency range is unlicensed, its use for wireless networking has been approved only in the United States, Canada, and Japan; and prior to 2002, only in some European countries. Regulatory changes in 2002 and 2003 opened the 5 GHz frequency range throughout the European Union.
802.11b
Released in 1999, 802.11b technology was able to beat 802.11a technology to the market because it was built on DSSS (Direct-Sequence Spread Spectrum) technology. As such, components required for it were all readily available for production facilities. 802.11b operates in the 2.4 GHz radio spectrum, which is heavily cluttered with cordless phones, Bluetooth (see the “Bluetooth” section, later in this chapter), and spill-over interference from microwave ovens.
The network rated speed of 802.11b is 11 Mbps, but in most situations you can expect to see about 6.5 Mbps because 802.11b is a CSMA/CA (Carrier Sense Multiple Access/Collision Avoidance) network, which sends “I’m going to send data” broadcast messages prior to sending its data, which increases the traffic on the network. (See Book 8, Chapter 1 for the lowdown on CSMA/CA.) The typical range for this type of network is about 100 feet (30 meters).
Wireless networks in the 2.4 GHz range have 14 channels available for use. Eleven channels are acceptable everywhere, the United Kingdom and some European countries allow up to 13 channels, and Japan allows all 14 channels. Channels are defined by the center frequency that they use. Some vendors use wider channels than others, overlapping their neighboring channels. Typically channels 1, 6, 11, and 14 are thought to be non-overlapping, so in North America there are three channels that are normally non-overlapping and will not interfere with each other. See Figure 2-3 for a channel diagram of the 802.11b/g spectrum. The point here is if you are experiencing intermittent problems with a wireless system, try changing the channel on the wireless router to either 1, 6, or 11, as you could be experience problems due to interference with other wireless devices running on the same channel.
802.11g
Released in 2003, 802.11g is an updated version of 802.11b, still running in the 2.4 GHz spectrum but allowing faster data transfer speeds to put it on a performance par with 802.11a. Because it operates in the 2.4 GHz spectrum, it is also backward compatible with 802.11b, making migration to 802.11g an easy step for many organizations because they could update the back-end infrastructure and then update the wireless clients in a manner that fits within the corporate requirements.
The network rated speed for 802.11g is 54 Mbps, but in most situations you can expect about half that speed because the throughput is reduced as distances between the client and access point increase, and the signal suffers from greater interference. Because wireless networks are a shared medium further reduces throughput as the number of users sharing an access point increases the competition for the wireless signal. The typical range for this type of network is about 100 feet (30 meters).
With all the benefits that are available with 802.11g, many companies began producing products well before the standards were ratified.
802.11n
802.11n represents the latest improvements to networking in the 2.4 GHz and 5 GHz spectrums. Originally planned as a replacement for 802.11b/g, the standard now allows for radios operating in the 5 GHz spectrum of 802.11a. Again, this solution suffers from an already congested spectrum. The biggest change that you will see with this technology is the implementation of multiple transmitters and receivers and multiplexing of signals. This technology is referred to as MIMO (Multiple-Input Multiple-Output).
The network-rated speed is up to 200 Mbps (600 Mbps when multiplexed or connected over multiple radios). As with most wireless technology, you should expect typical transfer rates at about half that — in the 300 Mbps area. The typical range for this type of network is about 165 feet (50 meters).
802.11ac
The newest of wireless standards is the 802.11ac wireless standard, which uses the 2.4 GHz or 5 GHz frequency range. The 802.11ac wireless standard has different transfer rates depending on the implementation, but expect them to be faster than 802.11n. Transfer rates could be from around 500 Mbps to gigabits per second depending on the number of antennas and configuration of the access point. For example, a two-antenna access point could reach speeds of 867 Mbps, while a three-antenna access point could reach speeds of 1.27 Gbps.
 Although there is a lot of talk about cordless phones causing interference with wireless networking, there has been a big boost in 6 GHz phone sales because they do not interfere with 802.11b/g/n/ac networks.
Although there is a lot of talk about cordless phones causing interference with wireless networking, there has been a big boost in 6 GHz phone sales because they do not interfere with 802.11b/g/n/ac networks.
Securing wireless networks
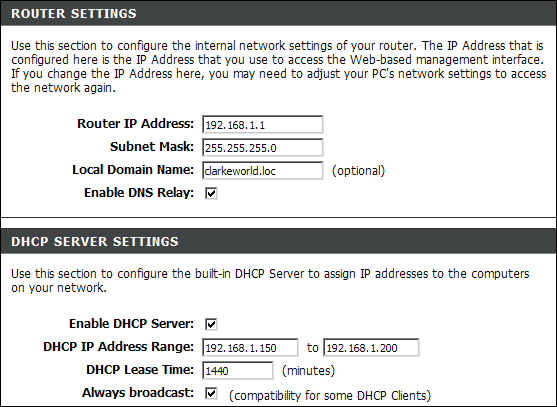
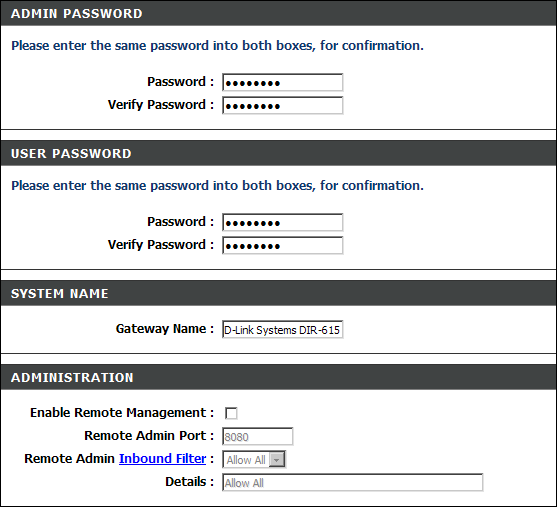
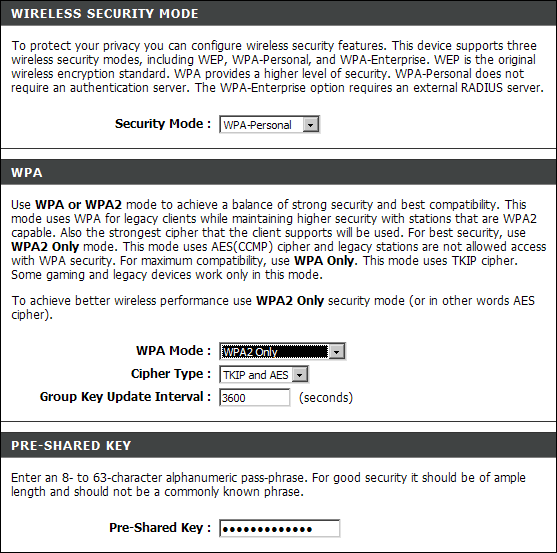
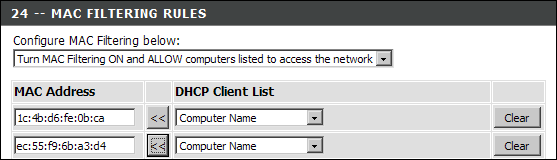
With the proliferation of wireless technology, security has come to the forefront of many conversations, which is odd because it should have been prominent from the very beginning. The main steps you can take to improve wireless security include password management, SSID management, MAC address filtering, WEP, WPA, WPA2, DMZ, DHCP settings, and updating the firmware. Many of these configuration settings can be seen in Figure 2-4. The configuration screens for most access points are accessed using a web browser and connecting to the IP (Internet protocol) address of the access point, as I did when connecting to the Linksys access point shown in Figure 2-4.
 It is important to note that although I discuss common security options for wireless networks, most security methods are easily bypassed by a determined hacker. WEP and WPA are fairly easy encryption methods to crack and MAC filtering is fairly easy to bypass. For the A+ Exams you need to know steps to take to secure wireless, but know in the real world that you should implement many security measures.
It is important to note that although I discuss common security options for wireless networks, most security methods are easily bypassed by a determined hacker. WEP and WPA are fairly easy encryption methods to crack and MAC filtering is fairly easy to bypass. For the A+ Exams you need to know steps to take to secure wireless, but know in the real world that you should implement many security measures.
Passwords
All access points ship with a default Administrator username and password. A quick search of the Internet will give you the default usernames and passwords for most manufacturers and models. Usually, in addition to an owner’s manual, a new access point will ship with a Quick Start guide containing an abridged set of steps to follow to apply a basic configuration to the access point. This guide typically includes the default IP address, username, and password used by the access point. When wireless networks started to become widespread, these guides did not suggest changing the default passwords, but most of them now offer the suggestion in the initial setup steps — if not actually forcing you to do it before making any other configuration changes.
 Changing the Administrator password should be the first step in the setup procedure. Until you change the password, any people within the range of your access point can make any configuration changes they wish.
Changing the Administrator password should be the first step in the setup procedure. Until you change the password, any people within the range of your access point can make any configuration changes they wish.
SSID broadcasting
Security through obscurity is not the best security measure, but it provides one more layer to your overall network security. Most operating systems such as Windows, Linux, and MAC OS, try to make it easy for you to connect to wireless networks by displaying the SSIDs for wireless networks in range of your computer if the access points are broadcasting their SSID. This allows you to select the SSID or wireless network that you want to connect to and quickly configure it. By disabling the broadcasting of your SSID, your network will not show up in the list of detected wireless networks within Windows or other operating systems. If you are not on the list, most people won’t even know your network is there — and therefore, won’t connect to it. Windows 7 will display nonbroadcasting SSIDs as wireless networks named “Other Network.” Connecting to the “Other Network” will require the user to know the actual SSID.
 Disabling SSID broadcasting is only a mild security setting, as you discover in the section, “Troubleshooting Issues,” later in this chapter. If someone wants to gain access to your wireless network, disabling SSID broadcasts won’t slow him very much nor prevent that person from knowing that a wireless network exists.
Disabling SSID broadcasting is only a mild security setting, as you discover in the section, “Troubleshooting Issues,” later in this chapter. If someone wants to gain access to your wireless network, disabling SSID broadcasts won’t slow him very much nor prevent that person from knowing that a wireless network exists.
MAC address filtering
Media Access Control (MAC) address filtering is another step that will slow most casual users from gaining access to your network, but it is not considered strong security on its own. Most access points allow you to perform different types of filtering, and most allow you to at least filter traffic by MAC addresses that are hard-coded onto each network adapter on your wireless network.
Implementing this security step means that for each new network card that you want to operate on your network, you need to adjust your access points. Even with the MAC address restriction in place on your access point, an unscrupulous person can use a network sniffer like AirSnort to see some traffic on the wireless network. In this traffic, such a person can see the MAC addresses of clients who are communicating on your wireless network. By taking this information and using a network card or operating system that allows him to manually control the MAC address, the individual can imitate one of the valid MAC addresses that are allowed to be used on your network. The timing on this is important because if two computers on a network have the same MAC address, all sorts of communication errors can happen.
 As I mention previously, MAC address filtering keeps the casual user out of your network, but it shouldn’t be your sole security measure. If somebody wants to get onto your network, this will not slow him down very much.
As I mention previously, MAC address filtering keeps the casual user out of your network, but it shouldn’t be your sole security measure. If somebody wants to get onto your network, this will not slow him down very much.
WEP
The security measures I’ve discussed thus far do not deal with encryption. Wired Equivalent Privacy (WEP) was the first attempt to secure wireless networks by using encryption. Early WEP used a 64-bit key, which was a 40-bit encryption key joined with a 24-bit initialization vector (IV). This was easily breakable. Newer WEP uses a 104-bit encryption key joined with the 24-bit IV, providing a higher level of security.
WEP was fairly easy to configure on both the access point and the client and again provides security against the casual wireless user. One of the main drawbacks to WEP is that technology has not substantially changed on how security keys are managed, such as IVs being sent over the network in plain text. And, if an intruder captures enough traffic from your network, he can deduce your WEP keys, giving him full access to your network. The answer to this problem is WPA.
WPA
WiFi Protected Access (WPA) and WPA2 (also called 802.11i) are all about improving security on wireless networks. Rather than using a single WEP key, WPA uses per-session keys that are agreed upon by the wireless client and the access point after an initial handshaking process. This technology was created in response to the weaknesses that were found in WEP. No security is unbreakable, and creating a better mousetrap just seems to create smarter mice. Still, the security settings available in WPA2 make wireless networks as secure as they can be. As of this writing, the time needed to break the keys used would render the broken keys mostly useless because they would have already been changed on the network.
You can implement WPA in one of two modes:
- WPA Enterprise: With WPA enterprise when a client connects to the wireless network they are sent to a RADIUS server to authenticate before they can gain access to the wireless network. Authentication is typically done via a username and password which increases the level security over a simple wireless key.
- WPA Personal: Is the mode you use at home, which involves setting up a pre-shared key on your router. Anyone wanting to connect must use that same pre-shared key in order to connect.
In your list of security methods, you can choose TKIP (Temporal Key Integrity Protocol), which uses a 128-bit encryption key and a 48-bit IV to secure the data. In addition, after every 10,000 packets of data have been sent, new TKIP keys are generated and used. This regular changing of the keys keeps the network more secure.
WPA2
WPA2 builds upon the security of WPA and operates in either Enterprise mode or Personal mode like WPA does. WPA2 improves the encryption by rotating keys, but also by using a more advanced encryption algorithm known as Advanced Encryption Standard (AES). AES allows for encryption keys of 128, 192, or 256 bits.
 WPA2 encryption is the most common security method used to secure wireless networks because the data is encrypted with the password you use (known as the key), and the password acts as a method of authorizing the client (only systems that know the password can connect).
WPA2 encryption is the most common security method used to secure wireless networks because the data is encrypted with the password you use (known as the key), and the password acts as a method of authorizing the client (only systems that know the password can connect).
VPNs and DMZs
Although it requires more setup, you can treat your wireless network as a hostile remote network. By hostile, I mean that the network contains many individuals who would like to gain access to the company’s private information stored on its corporate network. Some companies have faith that the security settings that they configured on their wireless access points will keep all unwanted visitors or trespassers off their network. And that is not an unreasonable thought, given the current security settings that are available. However, for those companies that do not trust these security levels available in the current wireless technology, or who are afraid of the smarter mouse arriving on the scene sooner rather than later, other steps can be taken to provide even more secure wireless.
Most companies today have a connection to the Internet coming into their organization, and they treat the Internet as a large hostile remote network. To prevent their private data from being accessed, companies use a firewall where the Internet meets their network, allowing them to inspect and control the data that moves between their network and the Internet. If they have data that they would like some people on the Internet to be able to access (such as data on a web server or an FTP server), they may implement a second firewall, making another private network. This strategy provides some protection from unwanted visitors gaining access to the web or FTP server but offers less protection than their normal private network because some people have a right to access the server. In most cases, this more open private net will be placed between the hostile Internet and the private corporate network, creating a less hostile, but still not absolutely safe, Demilitarized Zone (DMZ).
It is also common for companies to have remote workers who need access to the corporate network while they are away from the office. This access is given through a special secure channel: a Virtual Private Network (VPN). A VPN relies upon secure authentication and data encryption methods to create a secure and private connection through a firewall to a corporate network. Most often, this security is handled by SSL (Secure Sockets Layer) or IPSec (IP Security), which are two industry standard methods of encrypting TCP/IP or Internet data.
 More information about firewalls, VPNs, DMZs, SSL, and IPSec can be found in Book 9, Chapters 1 and 2.
More information about firewalls, VPNs, DMZs, SSL, and IPSec can be found in Book 9, Chapters 1 and 2.
So, by segregating your wireless users into their own DMZ or private segment (protected from the Internet), you can keep any potential wireless intruder away from your private corporate data because users of that wireless network do not have direct access to the corporate network. For your users to access corporate data, they use the same remote access methods, such as a VPN connection, that they would use when on the road. These additional security steps can be layered atop the previously discussed techniques, such as using WPA2 encryption, forcing users to take more steps to get access to your corporate data, but making the connection more secure.
DHCP server settings
A DHCP (Dynamic Host Configuration Protocol) server provides automatic TCP/IP configuration to network clients by changing normal items that DHCP provides, such as a default gateway or DNS settings for name resolution, or by disabling DHCP altogether. By failing to distribute accurate TCP/IP information to unwanted visitors, and using manual TCP/IP configurations to users, you are implementing another rudimentary security step. This security based on DHCP settings might prevent most casual users from getting ready access to information or gaining access to the Internet through your wireless network. Still, any unwanted intruder who wants to gain access will be able to find correct TCP/IP settings by using a standard packet capture utility, such as Wireshark (www.wireshark.org).
Client isolation
This option, available on many network switches, has found its way to wireless networks as well. When this setting is enabled, wireless clients can talk to the rest of the network but cannot communicate with other clients on the same wireless access point.
Firmware
Not to be forgotten when setting up new wireless networks (or periodically after a network is set up) is to check for firmware updates for your wireless network components or driver updates for your network cards. These updates are how new security features are retrofitted into your wireless products.
 Take care when doing this because features are occasionally removed, or you might encounter problems with the new code in the firmware.
Take care when doing this because features are occasionally removed, or you might encounter problems with the new code in the firmware.
 Many people have opted to stop using the firmware from their hardware manufacturer and instead use a third-party or open source firmware, such as DD-WRT (
Many people have opted to stop using the firmware from their hardware manufacturer and instead use a third-party or open source firmware, such as DD-WRT (www.dd-wrt.com). This firmware works on a variety of hardware platforms, which are listed on its website.
 Most tasks handled by infrared technology have switched to use newer 802.11 networks and Bluetooth technologies, which use radio frequencies (RF).
Most tasks handled by infrared technology have switched to use newer 802.11 networks and Bluetooth technologies, which use radio frequencies (RF). Wireless networking should not be used for a primary network because of its limitations, such as obstructions and interference. (See “
Wireless networking should not be used for a primary network because of its limitations, such as obstructions and interference. (See “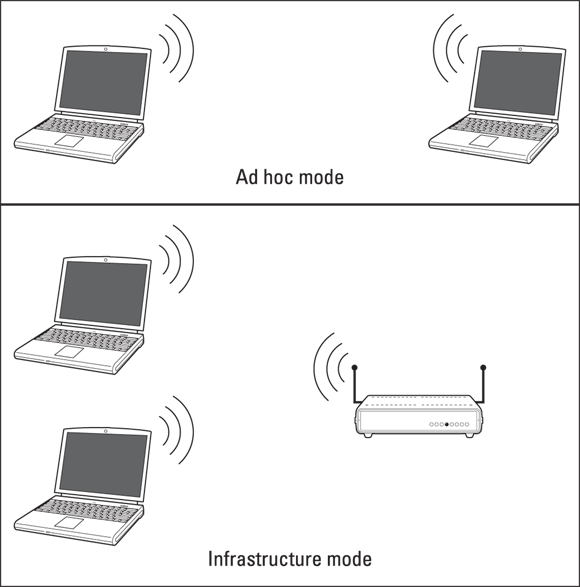
 Some manufacturers refer to the SSID as a BSSID (Basic Service Set Identifier) or an ESSID (Extended Service Set Identifier). The IEEE 802.11-1999 wireless network standard defines an ESSID as a set of access points using the same SSID and channel, and operating as a single BSSID to their wireless network clients.
Some manufacturers refer to the SSID as a BSSID (Basic Service Set Identifier) or an ESSID (Extended Service Set Identifier). The IEEE 802.11-1999 wireless network standard defines an ESSID as a set of access points using the same SSID and channel, and operating as a single BSSID to their wireless network clients.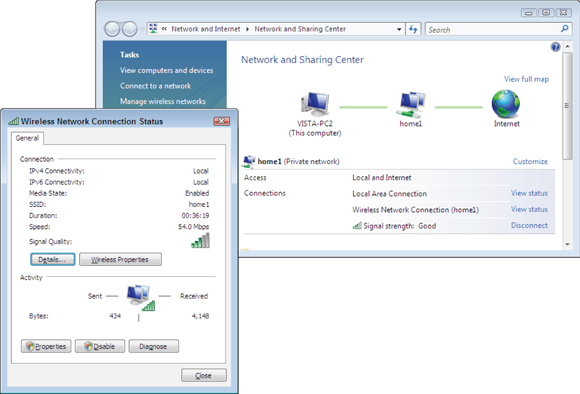

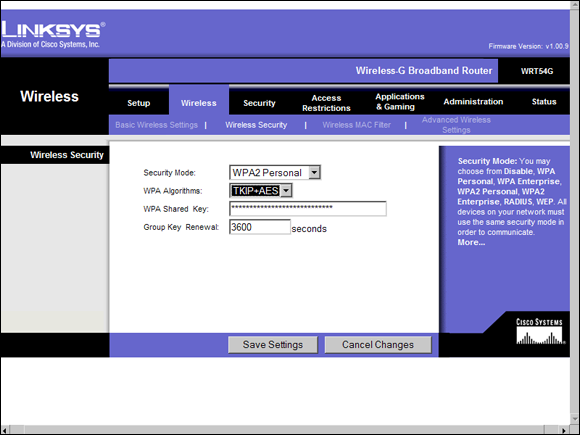
 Changing the Administrator password should be the first step in the setup procedure. Until you change the password, any people within the range of your access point can make any configuration changes they wish.
Changing the Administrator password should be the first step in the setup procedure. Until you change the password, any people within the range of your access point can make any configuration changes they wish. More information about firewalls, VPNs, DMZs, SSL, and IPSec can be found in Book 9,
More information about firewalls, VPNs, DMZs, SSL, and IPSec can be found in Book 9, 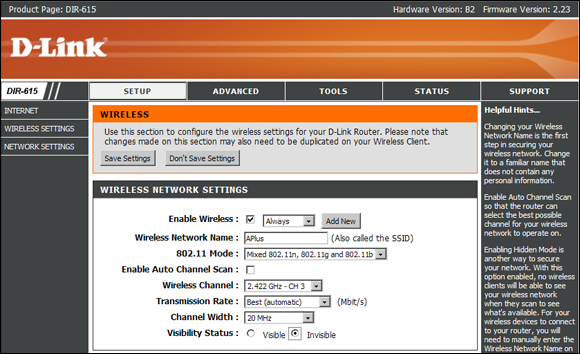
 (A) 1 meter
(A) 1 meter