Implementing Users and Groups
In this section, you find out how to create user accounts that can be used to log on to the system and how to create groups to organize users together as a single object that permissions can be assigned to.
Creating user accounts
To secure the Windows OS from unauthorized access, you can create a user account for each person who is allowed to use the system. Anyone without a user account will be unable to log on to the system and, as a result, will not be able to use the computer. The other benefit of creating user accounts is that even if a person has a user account and logs onto the system, he might not be able to access a file because you have not given permission to that user to access the file.
Creating accounts in Computer Management
To create a user account on a Windows system, go to Control Panel ⇒ Administrative Tools ⇒ Computer Management. In the Computer Management console that opens, expand Local Users and Groups and select the Users folder (shown in Figure 2-1). In the Users folder, you will notice some user accounts on the right side. These user accounts are built-in accounts, meaning that they were built by the OS or by a piece of software you have installed. Note that the home editions of Windows do not have a Computer Management console, so you will have to manage user accounts through the Control Panel.
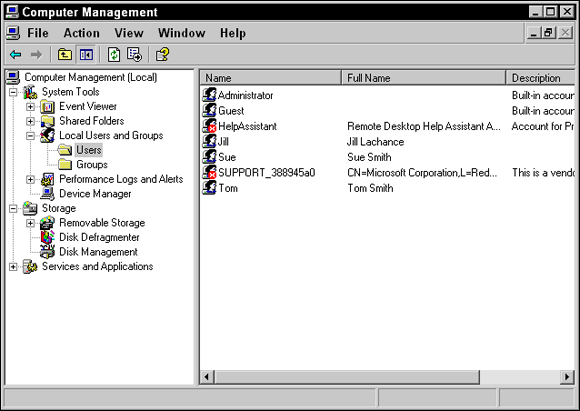
FIGURE 2-1: Creating user accounts and groups in the Computer Management console.
Two built-in accounts you should be familiar with for the A+ Exams are
- Administrator: The administrator account is the built-in account in Windows that has full access to the system and can manage all aspects of the computer. During the installation of Windows, you were asked what you wanted to set as the password for the administrator account; you use that password to log on with the username of administrator. When you do log on as administrator, you can change any settings on the system. A normal user account cannot change major settings on the system such as the time, installing software, or any changes that affect the system. To make these types of changes, you need to log on as administrator to make changes.
- Guest: Users can use the guest account if they don’t have an actual user account. When they try to access the system, they are authenticated as guest. The guest user inherits any permissions the guest account has on the system. There is one hook to this scenario, though. By default, the guest account is disabled, meaning that it is not available for use. Because of the security concerns of not requiring someone to log on, Microsoft has disabled the account. A disabled account appears with a red X on it and cannot be used.
Now that you have identified the two major built-in accounts, you can create your own user accounts. To create your own user accounts in the Computer Management console, right-click the Users folder and choose New User. The New User dialog box appears (shown in Figure 2-2). Fill in the following account details:
- User Name: This is the name that the user uses to log on to the system. Typically, it is a short version of the full name. For example, the full name Glen Clarke might get truncated to gclarke as the username. A username is also known as the logon name.
- Full Name: This is typically the person’s first name and last name: for example, Glen Clarke as the full name.
- Description: This is a description of the user account. I typically put the person’s job role here: for example, Accountant.
- Password: Type what you want for the user accounts password. The user needs to know this password to log on to the system. Be sure to use good practices with passwords, such as not using words found in the dictionary and using a combination of uppercase and lowercase letters, numbers, and symbols. See the preceding chapter for more information about strong passwords.
- Confirm Password: Type the password again in this box. This ensures that you typed what you thought you typed.
- User Must Change Password at Next Logon: Set this option if you want to force the user to change the password the first time he logs on. This ensures that you don’t know the user’s password because the password you originally set is overwritten.
- User Cannot Change Password: Set this option if you don’t want the user to be able to change the password. This ensures that the password you set is the password that the user must use.
- Password Never Expires: In a password policy, you can specify that passwords must be changed every so many days. That policy applies to all users except for any accounts that have Password Never Expires activated. You might use this option if you have two employees sharing a user account.
- Account Is Disabled: If you want to disable an account at any time, you can set this option. A disabled account is unusable until you enable it again.
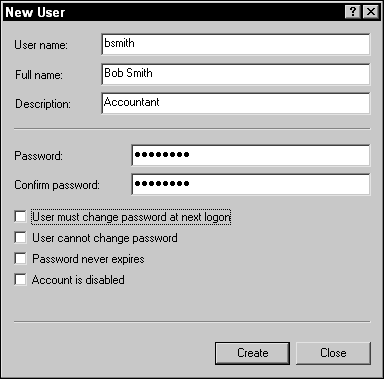
FIGURE 2-2: Creating a user account in Windows.
After you enter all the account information, click the Create button and then click Close to dismiss the New User dialog box. The user account has been created, and you can start using it right away to log on to Windows.
Creating accounts in Control Panel
It is also possible to create user accounts from within the Control Panel. In Windows 7, click User Accounts from the Control Panel and then select Family Safety ⇒ User Accounts ⇒ Manage Another Account. At this point you can select a user account you want to alter or create a new user account by choosing the Create a New Account link.
In Windows 8.1, you can also manage user accounts from the Control Panel by selecting User Accounts and Family Safety ⇒ User Accounts ⇒ Manage Another Account (Figure 2-3). Choose the account you want to alter and then choose the action on the left side that represents the change to the account you want to make. If you want to create a new account, click the link for Add a New User in PC settings from the Manage Another Account screen. This takes you to the PC settings screen where you can add a new user account.
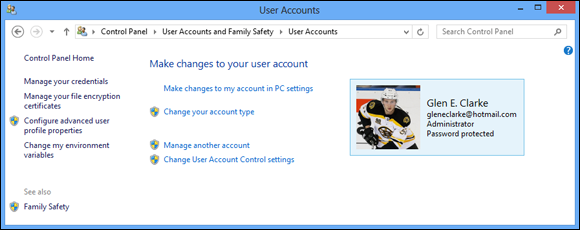
FIGURE 2-3: Creating a user account via Control Panel.
One user account setting you can change is the type of account. In Windows you can create a standard user account (the default), which is just a plain account with no administrative permissions. You can also create an Administrator account, which has permissions to alter settings on the computer.
To change the account type after the fact, simply go to Control Panel ⇒ User Accounts and Family Safety ⇒ User Accounts ⇒ Manage Another Account, and then select the account you want to alter. On the left side of the screen you will see settings you can change. Choose Change Account Type and then choose either Standard User or Administrator.
Creating groups
A group in Windows is a collection of user accounts. The benefit of using groups when managing access to resources is that you don’t need to assign the same permissions multiple times. Instead, you assign the permission to the group, and anyone who is a member of the group receives the permission.
Like user accounts, Windows offers a number of built-in groups. A built-in group has predefined capabilities within Windows. For example, printer operators can manage all printers on the system, and anyone who is a member of the printer operators group will have that capability. The following is a list of some of the popular built-in groups found in Windows OSes:
- Administrators: This group has full access to the system and can change any setting on the system. The administrator account is a member of this group by default, which is why the administrator account is allowed to change any setting on the system.
- Backup Operators: Members can perform backups and restores on the system.
- Account Operators: Members can create user accounts. This group is available on Windows servers. The benefit of using this group is that if you want someone to be able to manage user accounts, you can place that person in this group instead of in the administrators group and he or she will only be able to manage the user accounts — not the entire system.
- Printer Operators: Members can change any settings on the printers. Essentially, members of this group are trained to troubleshoot the printing environment and then assigned the task of managing all printing problems on the network.
- Users: All user accounts that are created are members of the users group. You can assign permissions to the users group knowing that all users will get the permission.
- Power Users: The power users group is the group on Windows client OSes prior to Windows Vista that allows its users to create user accounts and manage the printing environment. Use this group if the desktop OS does not have an account operator or a printer operator group.
If the built-in groups do not satisfy your needs, create your own groups:
- Click Start and then right-click Computer (in Windows 7 and Vista) and choose Manage. (In Windows 8.1, right-click the Start icon and choose Computer Management.)
- In the Computer Management console, expand Local Users and Groups.
- Right-click the Groups folder in Local Users and Groups and then choose New Group, as shown in Figure 2-4.
-
In the New Group dialog box that appears, type the name you want to use for the group.
In this example, I use Accountants (shown in Figure 2-5).
- Fill in a description for the group in the Description text box.
-
To begin adding members to the group, click the Add button.
The Select Users dialog box appears.
-
Type the name of the user account you want to add and then click the Check Name button on the right side.
Windows should underline the account name, indicating that the user account exists and that you can add it to the group membership.
- Repeat Step 7 for each account you want to add to the group.
- After you add all the accounts to the group, click OK and then click Create to create the group.
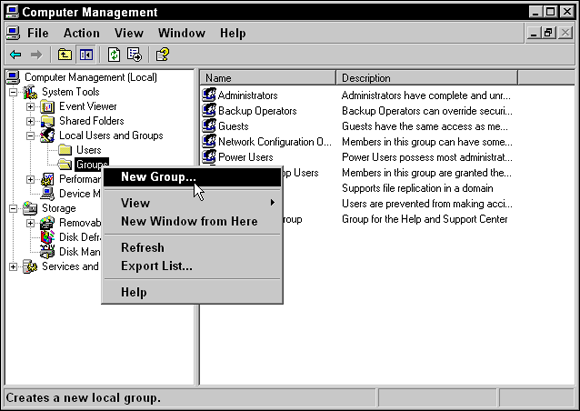
FIGURE 2-4: Creating a new group in Computer Management.
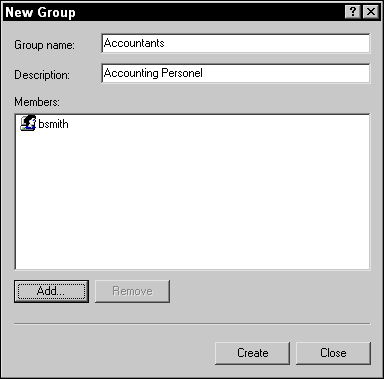
FIGURE 2-5: Fill in information for your new group.
After you create the users and place them into their appropriate groups, you are now ready to assign them permissions.
 Two default accounts are built in to Windows: administrator and guest. The administrator account has full access to the system, and the guest account is used for temporary access to the system. Also note that the guest account is disabled by default.
Two default accounts are built in to Windows: administrator and guest. The administrator account has full access to the system, and the guest account is used for temporary access to the system. Also note that the guest account is disabled by default. To practice creating users and groups, take a look at Lab 2-1 on the book’s companion website at
To practice creating users and groups, take a look at Lab 2-1 on the book’s companion website at 
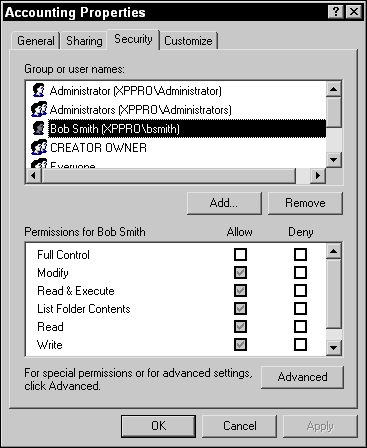
 Permissions can be configured only on a partition formatted for NTFS. To obtain an NTFS partition, you can format the partition for NTFS (but lose all existing data), or you can convert the drive to NTFS by using the
Permissions can be configured only on a partition formatted for NTFS. To obtain an NTFS partition, you can format the partition for NTFS (but lose all existing data), or you can convert the drive to NTFS by using the  If someone can take ownership of the resource, that person can change the permissions. The Full Control permission should be used sparingly so that not everyone has the permission to change permissions on you.
If someone can take ownership of the resource, that person can change the permissions. The Full Control permission should be used sparingly so that not everyone has the permission to change permissions on you.
 The share permission is inherited for the entire folder structure of the share, which is known as permission propagation. Also, remember that administrative shares are already created in Windows, such as the root of every drive. You can connect to them with syntax such as
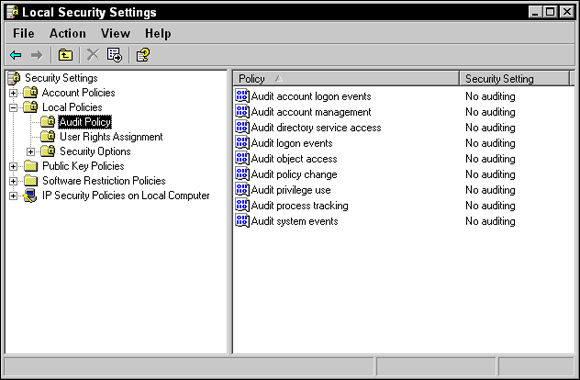
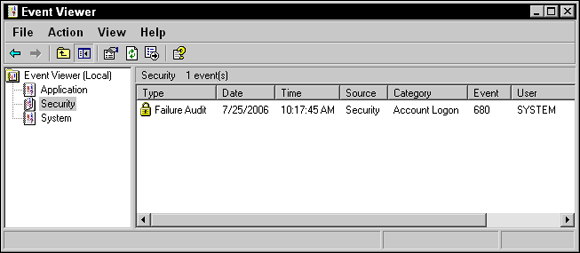
The share permission is inherited for the entire folder structure of the share, which is known as permission propagation. Also, remember that administrative shares are already created in Windows, such as the root of every drive. You can connect to them with syntax such as  After you enable Object Access Auditing, you need to go to the Security page in the properties of a file, folder, or printer and click the Advanced button. Click the Auditing tab and choose which users and which permissions to audit for. You must perform this step on any folder, file, or printer you want to audit.
After you enable Object Access Auditing, you need to go to the Security page in the properties of a file, folder, or printer and click the Advanced button. Click the Auditing tab and choose which users and which permissions to audit for. You must perform this step on any folder, file, or printer you want to audit.