Chapter 3
Viruses and Malicious Software
EXAM OBJECTIVES
Understanding viruses
Looking at malicious software
Performing software updates
Recovering an infected system
In this chapter, you find out about the different types of malicious software that you might encounter after you connect your system to the Internet or start sharing files with another system. As a service technician, you will spend most of your time trying to fix a computer that is polluted with viruses or other forms of malicious software.
Being able to protect your system from viruses and other forms of malicious software is an important skill to have. You also have to know how to perform a virus scan and remove viruses from your system.
My Computer Has a Virus!
A virus is a piece of software designed to do harm to the system in one fashion or another. The virus is typically associated with a host file, such as a word processing file or video clip; and when that file is opened, the virus is activated and does its damage to the system. The damage could be disastrous in the sense that the system no longer starts up, or it might just create a faulty system that is annoying to work with. Either way, the virus has done its job — to cause pain and suffering in your computer’s life, and yours!
Types of viruses
A number of different types of viruses can infect your system:
- Boot sector: A boot sector virus attacks the boot code contained in the boot sector of the disk. This type of virus loads every time the system boots up and sometimes may even prevent the system from booting.
- File: A file virus attaches itself to an executable file and is run, or activated, when the executable file is run. This has been one of the most popular forms of viruses for many years because the attacker simply has to trick you into running the executable.
-
Macro: A popular type of virus today is the macro virus. A few years ago, Microsoft was promoting the fact that you could program your own macros to customize Microsoft Office applications (such as Word, Excel, and Access). A macro is a set of Visual Basic for Applications (VBA) commands that performs a specific task. VBA can also be used to call other programs. For example, I created a macro in Excel that automatically starts Outlook and emails the contents of the spreadsheet to one of my business partners.
My point is that VBA is pretty much a full programming language. And the fact that VBA is a programming language is important because it can perform a lot of powerful actions, such as creating, deleting, and modifying files. Fear not, though. The following section explains how to keep yourself safe with the Office macro security settings.
 You might also encounter worm viruses or Trojan viruses, but I save those for discussion in “Understanding Malicious Software,” later in this chapter.
You might also encounter worm viruses or Trojan viruses, but I save those for discussion in “Understanding Malicious Software,” later in this chapter.
Office macro security settings
After the power of VBA became known, hackers started creating malicious macros in Word and Excel documents so that when you opened the documents, the macro would run and cause damage to your system. To prevent this from occurring, you could change the macro security settings in each Office application to control how to manage macros found in documents when the document is opened.
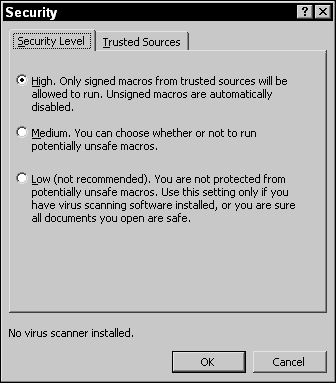
- Office 2003: To change the macro security settings in these versions of Office, choose Tools ⇒ Macro ⇒ Security in your Microsoft Office program and then choose one of the following options (shown in Figure 3-1):
- High: Only macros from trusted sources are allowed to run; all other macros are disabled. This is the highest level of security because most macro code is not created from trusted sources.
- Medium: Office prompts you to decide whether to enable or disable macro support every time you open the file. This is a good setting because if you were unaware that a file had a macro, you could choose to disable macros while the file is open — knowing that if there is malicious code in the file, it won’t run.
- Low: All macros run without your knowledge. If you have no worries about macro security, you may set this option — but never open a Microsoft Office document unless you know where it came from!
- Office 2016: Choose File ⇒ Options ⇒ Trust Center, then choose the Trust Center Settings button. From the Trust Center window that opens, select one of the following radio buttons:
- Disable All Macros without Notification: Macros are disabled but you are not notified.
- Disable All Macros with Notification: Notifies you that macros have been disabled.
- Disable All Macros Except Digitally Signed: Signed code is code that is considered safe to run on your system. Choosing this option will only run macro code that has been signed.
- Enable All Macros (Not Recommended): Allows unsigned and signed macros to run. This is not recommended as potentially dangerous code could execute and negatively change your system.
Protection from viruses
To protect your computers and servers from viruses, it is essential that you have virus protection software installed. Simply, such software, such as the program shown in Figure 3-2, knows about the different viruses and can either remove the virus or remove files from your system that contain viruses.
You can choose from many different name brands of virus-protection software, each of which has its own benefits. Some of the popular names in virus protection are
Each antivirus software product has its own benefits and features. For example, you might prefer the interface or usability of one product over another. Still, each product should offer similar features. When shopping for antivirus software, you should look for software that offers at least the following features:
- Scheduled virus scans: This is a great feature because you can have the virus scanning software scan the system in the middle of the night (when the system is not being used), and you do not have to physically perform the scan yourself. You may also choose what happens when a virus is found: say, attempt to remove the virus from the file, place the file in a quarantine area, or delete the file.
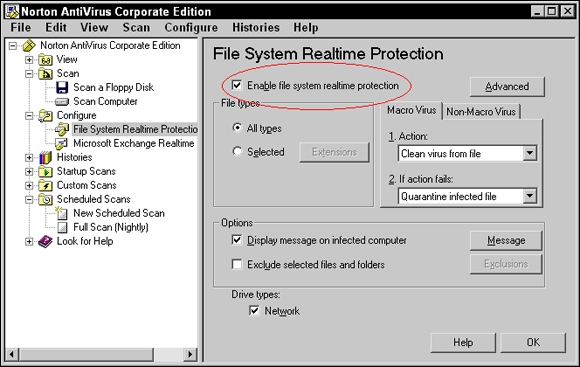
- Real-time protection: The virus protection software runs in memory all the time and scans any file that you open. The benefit of real-time protection is that you are protected from viruses between scan times. Be sure to have software that supports real-time protection and have the feature enabled (see Figure 3-3)!
- Scheduled definition updates: Virus definitions are what virus protection software uses to update its knowledge of viruses. Your virus protection software should have a feature that allows the definitions to be downloaded from its vendor site.
- Scanning email: Many virus protection software versions support scanning email messages as they arrive in your inbox. This is typical of virus protection software that runs on an email server and you usually pay an annual subscription fee for the service.
Note that today we have antivirus software and anti-malware software. Antivirus software would protect you against viruses, while anti-malware software protects you against many different forms of malicious software such as viruses, spam, spyware, and adware. An example of anti-malware is Windows Defender.
Updating virus definitions
When you perform a virus scan, your virus protection software knows only about the viruses as of the creation time of the software. This is a huge problem because new viruses appear every day.
So, to keep your software valid and to allow it to still be useful years after you purchase it, manufacturers use virus definitions as a way for the software to know the current list of viruses. The virus definitions can be updated online. So, even though your software might be two years old, you can keep it current.
 It is critical that you update your virus definitions regularly, or your virus protection software won’t know about any new viruses that are developed.
It is critical that you update your virus definitions regularly, or your virus protection software won’t know about any new viruses that are developed.
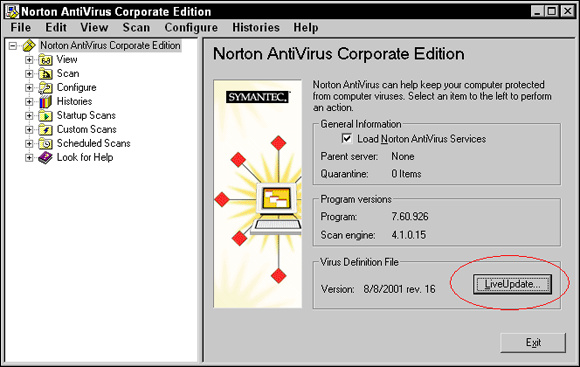
To update the virus definitions in my Norton Security (formerly Norton Antivirus), after I start the software, I see a LiveUpdate button on the main screen, as shown in Figure 3-4. To update my virus definitions, I simply click the LiveUpdate button; updating virus definitions should be this simple in most other antivirus programs as well. It is also important to notice that the antivirus software displays how up to date the virus definitions are.
Understanding Malicious Software
Other types of malicious software, outside of your typical viruses, attack systems every day. The following sections outline other types of malicious software — but understand that they are all considered types of viruses.
Trojan horses
Trojan horses are special programs that do something totally different than what the user who runs it thinks it does. For example, NetBus is a very popular Trojan virus that ships as a file called patch.exe. A hacker emails the file called patch.exe and explains in the email that this is a security patch you need to apply to make sure your system is secure. Unfortunately, patch.exe is the security hole! When you run patch.exe, it opens your system up to the hacker by opening a port so that the hacker can connect to the port at any time and control your system.
Trojan viruses are normally loaded on your system by the hacker tricking you into running the program on the system, typically through an email message. You can remove the Trojan with virus protection software.
Worms
A worm is a self-replicating virus: The worm doesn’t need to be activated by the user opening the file. Rather, a worm is a virus that runs on a system and also tries to infect other systems on the network. Worm viruses can be replicated to other systems on the network automatically, or they could replicate to a flash drive when you insert a flash drive into an infected system. Then when you take the flash drive to another computer, the worm automatically transfers from the flash drive to the other system.
Worms are loaded on your system by connecting to your system across the Internet. The worm is usually designed to infect the system by connecting through a specific piece of software. For example, the Nimda worm virus was designed to infect any system running Microsoft Web Server software (Internet Information Services [IIS]) and would replicate across the Internet infecting IIS web servers.
To prevent a worm from infecting your system, be sure to have a firewall and make sure that you are up to date with patches. For more information on firewalls, check out Book 9, Chapter 2. For more about staying up to date, read the “Preventing Problems by Staying Up to Date” section in this chapter. To remove a worm from your system, you can try your antivirus software, or you may have to download a removal tool specific for that worm. For example, Microsoft offers a malicious code removal tool that you can download from www.microsoft.com/downloads.
Spyware and adware
Spyware is software that loads on your system and then monitors your Internet activity. Adware is software that creates pop-ups from time to time advertising a particular product or service.
Both types of viruses infect your system when you surf the wrong Internet site. Spyware and adware have become a huge negative result of the Internet, so a number of products are available to eliminate spyware and adware. The most popular products used to eliminate spyware and adware are
When selecting which software to use for spyware or adware removal, be sure to go with a product that supports features similar to good antivirus software, such as real-time protection and scheduled spyware scans.
Pop-ups and phishing
To help protect your system from malicious activity when surfing the Internet, browsers such as Chrome, Firefox, Safari, and Internet Explorer (IE) have built-in pop-up blockers and prevent phishing attacks. Windows has these features enabled by default, protecting you from malicious content on the web!
A pop-up blocker prevents additional windows from launching when you are surfing a website. Websites and adware often have pop-ups appear to promote products. With a pop-up blocker enabled, though, you are notified by a yellow bar at the top of the browser indicating when a pop-up is blocked. Click the yellow bar to allow the pop-up.
Windows OSes running newer versions of IE (IE 7 or greater) have built-in phishing protection features, known as Phishing Filter, that allows you to check the authenticity of a website to ensure that it is not a known “phishing” site. If the site is a known phishing site, the browser will block the site. For more information about phishing, see Book 9, Chapter 1.
Identifying Hoaxes
It is important to understand that some malicious code that you hear about is a hoax! For example, I remember a few years back, I was playing an elf bowling program that everyone was emailing around at Christmastime. After weeks of playing this game, it was said that the program should be removed from your system because on a certain date it would do damage to your system. I removed the program from my main computer, but I ran the program on a test system after that date, and it did no harm.
You typically receive hoaxes about viruses through your email system. The email you receive is acting as a virus alert, but unfortunately, there is no actual virus to report — it is a hoax. The benefit of such hoaxes is for the creators of the actual viruses; hackers hope that you receive so many hoaxes that you eventually ignore true virus alerts.
If you receive an email or other form of notice about a virus, check it against a virus hoax list to see whether the warning message is a hoax or has merit. Most virus protection software manufacturers keep an up-to-date list. You can go to a generic hoax site like Hoaxbusters, which is found at www.hoaxbusters.org.
Preventing Problems by Staying Up to Date
One of the most popular techniques hackers use to compromise systems is to find vulnerabilities in the software we use day in and day out. For example, hackers quickly figured out a way to perform the “dot dot” attack on Windows 2000 systems after IIS was installed. With the “dot dot” attack, hackers navigate the folder structure of a web server and delete files — a serious security flaw. After Microsoft got wind of the mistake, its programmers created a fix. It is your responsibility as a network administrator to download all the fixes to problems in the software you use.
Windows Update
To make it easier for you to get security fixes (patches) and updates for Microsoft software, use the Windows Update feature within the operating system. If you choose the Windows Update command from the Start menu, you are automatically connected to the Microsoft Windows Update site, where your system is scanned for which updates are needed.
Windows Update allows you to do an express update where all critical updates are installed on your system, or a custom update (see Figure 3-6) where you get to select which updates to install (see Figure 3-6). From the Windows Update site, you install all the updates or patches that your system needs. Performing a Windows Update is a critical step to securing your systems — be sure to do it regularly. You can access Windows Update in Windows 7 and Windows 8 from the Control Panel using these steps: Navigate to the Control Panel and then choose System Security ⇒ Windows Update. From the Windows Update screen, click the Check For Updates button to manually check for updates.
 Microsoft has started using the term Microsoft Update instead of Windows Update because you can now update all the Microsoft software, not just the Windows operating system.
Microsoft has started using the term Microsoft Update instead of Windows Update because you can now update all the Microsoft software, not just the Windows operating system.
SUS and WSUS
Most companies have thousands of systems on the network, which would make it impossible to visit each system individually and run Windows Update. To solve the problem of deploying updates to thousands of systems at a time, Microsoft created Windows Server Update Services (WSUS). The WSUS software is loaded on a server and gets all of the updates from the Windows Update site. After the WSUS server downloads all the updates, you review and approve the updates. The SUS software then sends the updates to the other systems on your network. This means that you don’t have to run Windows Update on every system on your network — saving you time and money! This also gives you the added benefit of saving on bandwidth used because the clients get their updates from the WSUS server and not the Internet.
The software update service was improved a few years later to create Windows Server Update Services (WSUS). WSUS solves a number of problems that existed in the original Software Update Service (SUS) feature that Microsoft had a few years prior. Some of the benefits of WSUS over the older SUS are:
- Synchronization: In this context, synchronizing involves downloading updates from the Microsoft Update site to the SUS server. When you synchronize the SUS server with Windows Update, it takes hours because all the updates on the Windows Update site are downloaded to your SUS server. This makes no sense because you receive updates for software you don’t use, thus wasting time and space on your system. WSUS downloads a listing of updates when you choose to synchronize the WSUS server. After you get the listing of updates, you then select which updates to download — saving space and time!
- Product selection: With WSUS, you can select which Microsoft products you use so that you get a listing of updates for only those products. For example, if you aren’t using Microsoft Exchange server, it doesn’t make sense to get updates for that product. With WSUS, you can specify that you are not using that software, and the updates for that software do not appear in the list.
- Computer groups: With WSUS, you can deploy updates to selected groups of systems. This is a big improvement over SUS because with SUS, when you approve the update, the update gets sent to all the systems. With WSUS, you can create groups of computers, and when you approve an update, you assign it to a group. For example, you could create a group called Accounting and then place all the accounting computers in that grouping, which allows you to approve updates for just the accounting systems if you like.
Antivirus
A big part of keeping your system up to date is making sure that you download security fixes from the Windows Update site or from the WSUS server, but you also need to be sure that you update the virus definitions for your virus protection software. You want to make sure that you investigate how to update the virus definitions with your antivirus software. The virus protection software should also give you the opportunity to schedule virus definition updates.
Other security software
In addition to virus protection software and Windows Update, you should be aware of a number of other software products.
Microsoft has malicious software removal utilities called the Malicious Software Removal Tool (MSRT) that you can download from www.microsoft.com/downloads. The MSRT is updated the second Tuesday of every month and is designed to remove the most recent list of viruses from a system. This is a great utility to use when trying to clean an infected system. It is important to note that this is virus removal software — not virus protection software. You should always run your virus protection software, but if you need to remove a virus from an infected system you can use the Malicious Software Removal Tool!
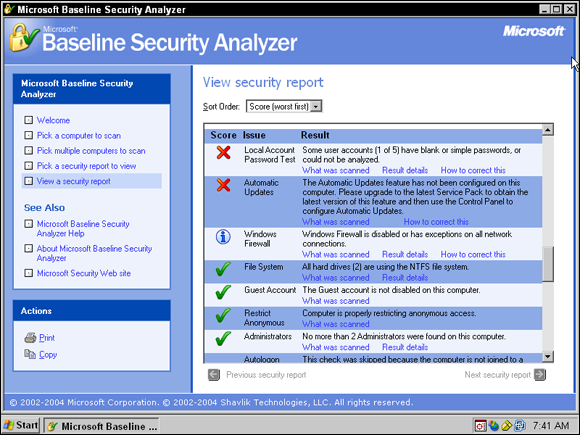
One of the most beneficial types of software out there for network administrators is vulnerability assessment software, which can scan all the systems on your network and alert you to any missing security patches or whether you are breaking any major security best practices, like not having a password on your administrator account. The Microsoft vulnerability scanner is Microsoft Baseline Security Analyzer (MBSA) (shown in Figure 3-7), which you can download from www.microsoft.com/downloads.
The MBSA identifies a number of issues surrounding the security of your system. A few examples of the types of information you will be presented with are
- Windows vulnerability checks: MBSA verifies that your current system is up to date with operating system patches. It also identifies any security best practices that have been broken.
- Weak passwords: MBSA ensures that all the user accounts have strong passwords.
- IIS and SQL Server vulnerabilities: MBSA verifies that any IIS and SQL Server machines you are using are up to date with security patches specific to those products.
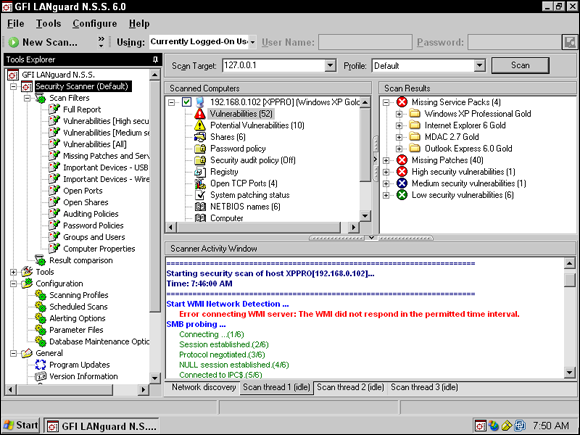
Another example of a vulnerability scanner that is a commercial product available for purchase is LANguard network security scanner from GFI (www.gfi.com/lannetscan). LANguard is very similar to MBSA but offers much more detail with regard to the overall picture of the network and how secure the systems are. LANguard (shown in Figure 3-8) has the benefit of logging the information to a Microsoft Access database or an SQL server so that you can create your own reports on the information collected. LANguard collects vulnerability information and also reports the following information:
- Information on the password policy
- Existing groups
- Existing user accounts
- Running services
- Existing shares
- NetBIOS name information
 To practice performing a Microsoft Update to your system, check out Lab 3-1. To practice using the Microsoft Baseline Security Analyzer (MBSA), check out Lab 3-2. Lab 3-1 and Lab 3-2 can be downloaded from the companion website at
To practice performing a Microsoft Update to your system, check out Lab 3-1. To practice using the Microsoft Baseline Security Analyzer (MBSA), check out Lab 3-2. Lab 3-1 and Lab 3-2 can be downloaded from the companion website at www.dummies.com/go/aplusaio.
Recovering an Infected System
One of the challenging aspects of system support is knowing how to remove a virus or malicious software from an infected system and return that system to a functioning state. The following sections are designed to help you identify a system that has been infected, list some of the tools you can use to recover the system, and then give you a list of best practices to follow to keep your systems clean of malicious software.
Common symptoms of an infected system
The first step to recovering an infected system is to be able to identify the symptoms of an infected system. The following is a listing of symptoms that indicate your system is infected with malicious software or under attack by a hacker:
- Pop-ups: If you have a lot of windows pop up when trying to surf the Internet, you most likely are infected.
- Browser redirection: If you launch your web browser and are redirected to another site outside of your default home page, you most likely are infected. If you type a website address into the browser and a different website displays, you most likely have been redirected by malicious software running on your system.
-
Security alerts: If you get a number of security alerts, you most likely are infected.
The security alert is often a pop-up created by the malicious software trying to get you to click a link.
- Slow performance: If you notice that your system is insanely slow, the system might be too busy because it is running the malicious software. Also, you may notice that the hard drive is always thrashing (working hard), which is a good sign that the malicious software is causing disk I/O.
- Internet connectivity issues: If you experience network issues where you are connected, then you are not, then you are connected again, this could be due to malicious software.
- PC/OS lockups: A great sign that your system has been infected with malicious software is when you find that your computer locks up a lot and you have to power the system off and then on again to be able to use it.
- Application crash: Another common sign your system has been infected with malicious software is if you find applications crash a lot. A good example of this is if the web browser crashes on a regular basis.
- OS updates failures: A lot of viruses will prevent you from doing a Windows update. If you find that updates happen very quickly, it is possible they are not happening at all.
- Rogue antivirus: If you find different antivirus software installed on the system or even if you find that your antivirus updates happen very quickly, it is possible that the virus has disabled your antivirus software and/or antivirus updates.
- Spam: If you receive a number of unsolicited emails, this could be due to malicious software. You most likely are receiving the spam because you have given your email address to different websites.
- Renamed system files: If you find that system files are being renamed, this is an indication of a virus. Also, if you find a number of additional folders and files on your system, you may have been hit with a virus.
- Files disappearing: If you find that a number of files are missing from your system for no reason, this could be due to a virus.
- File permission changes: If you cannot explain changes to the system, such as file permissions or even configuration changes, this could be due to a virus.
- Hijacked email: If you have people replying to messages that you did not send, your email could have been hijacked by malicious software. If your email software has been hijacked, you may receive responses from users regarding email messages they received from you, but you did not send to them. You may also experience automated replies from users for an unknown email message that you did not send.
- Access denied: If you find that you are getting access denied messages on folders and files that you should have access to, you may have been hit with a virus.
- Invalid certificate (trusted root CA): When browsing to secure sites you notice the address bar is red and you get a certificate warning that the certificate is untrusted or invalid, this may indicate that your browser has been redirected to an untrusted, unsecure website. This redirection is a great sign that your system has been infected with malicious software.
Tools used to protect the system
To protect your system from malicious software, you can use a number of tools. This chapter introduces a number of methods already, but I want to make sure that I summarize them before leaving the chapter. The following tools are useful for protecting your system from malicious software:
- Antivirus software: The most important protection method is to ensure that you have antivirus software installed and that the definitions are up to date. The A+ Certification Exams are sure to test you on this.
- Anti-malware software: If your antivirus software does not provide other malware protection such as adware protection, you may need to install additional malware protection.
- Antispyware software: Again, if your virus protection software does not protect you from spyware, you will need to install some antispyware protection software.
Tools used to remove infection
In addition to knowing what tools you need to install to help protect against viruses and malware, it is important to know what tools you can use to help remove malware from an infected system. The following tools can help you remove unwanted malware:
-
System Restore/Snapshot: The most important feature to use to help remove malicious software is the System Restore feature. Using System Restore, you can revert your system to the way it was a number of days ago. To access System Restore, go to Control Panel ⇒ System. From the System screen choose the System Protection link on the left side. To revert your system to a previous restore point, choose the System Restore button. Walk through the wizard and choose a date to revert your system to. This has saved me hours of work in the past! If you want to create a restore point, choose the Create button at the bottom of the screen.
 I have seen cases where System Restore did not work due to the virus preventing it from launching, so in that case, be sure to boot to Safe Mode first (press F8 while booting) and then run System Restore.
I have seen cases where System Restore did not work due to the virus preventing it from launching, so in that case, be sure to boot to Safe Mode first (press F8 while booting) and then run System Restore.
You can find out more about System Restore by checking out Book 7, Chapter 3.
- Event Viewer: The Event Viewer can be used to view error messages and status messages on the system and can help you identify problems with the system. Look back to Book 7, Chapter 1 to find out more about Event Viewer.
- Terminal: You could use a terminal, or command prompt, session to remove a virus or fix a system infected with a virus. The value of the terminal or command prompt is that you may find the GUI shell is locked down by the virus, so going to a command prompt is your only choice.
- Recovery Console: The Recovery Console is a command-prompt interface that helps with a number of issues such as a corrupt boot record, corrupt partition table, and disabled services. You can use the Recovery Console to fix problems related to disk errors and missing files. Look back to Book 7, Chapter 3 to find out more about the Recovery Console.
- Preinstallation environments: The Windows PE is a mini-version of Windows that can help you with issues surrounding missing files. Look back to Book 7, Chapter 3 to find out more about Windows PE.
-
Refresh/restore: Another common method to get rid of a virus on an infected Windows 8 or above system is to refresh your PC, which installs a new copy of Windows without losing your data such as photos, videos, music, or other personal files. You can also do a full restore (known as Reset), which wipes the system and resets it back to the way it was when you purchased it. If you use the Reset option, you will lose all your files.
To access these options in Windows 8, go to the bottom-right corner of the Taskbar until the charm list appears. From the charm list, choose the Settings charm ⇒ Change PC Settings (at the bottom) ⇒ Update and Recovery ⇒ Recovery. You then see the option for refresh your PC (Refresh) and remove everything (Reset).
- MSCONFIG/Safe boot: If you are having trouble running virus scan software or virus removal software because the system is unresponsive, you should boot to Safe Mode and then try a System Restore or Refresh of the system. You can also use the System Configuration Utility (MSCONFIG) to alter the boot options and boot to Safe Mode, or you could event disable software from automatically starting.
Best practice for malware removal
To be efficient with malware protection and removal, you must follow a number of best practices. The following are best practices for malware removal:
- Identify malware symptoms. The first step in virus removal is to identify a system that is showing symptoms of an infected system. For example, if you notice that the system is running really slowly and has a number of pop-ups appearing on-screen, this could be an infected system!
- Quarantine the infected system. After you identify that a system is infected, the first thing you should do is quarantine the system: Disconnect it from the network to prevent the virus from spreading to other systems!
- Disable System Restore. When a system is infected with a virus, you may consider disabling System Restore at this point, because the last thing you want is to revert to a restore point that has a virus in it!
- Remediate infected systems. After you have taken the previous steps, you are then ready to clean the infected system using some of the tools mentioned in the previous section, “Tools used to remove infection.” The proper steps you should take to ensure that the malicious software is removed is to first update your anti-malware software. Once the software has been updated, do a scan of the system and remove infections. If you have trouble running the anti-malware software, try booting to Safe Mode, which has minimal software running, or use a PE environment to boot from and then run the anti-malware software.
As a final note on best practices, I want to stress some of the best practices for scanning and removal techniques:
- Schedule scans and run updates. It is critical to ensure that you have scheduled your antivirus definition updates and have scheduled regular scans to run in the middle of the night.
- Enable System Restore and create a Restore Point. Use the System Restore feature to remove a virus from the system! System Restore should be enabled by default, but you can verify that by going to your System Properties dialog box.
- Educate the end user. Educate your end users on how to respond to a virus. Ensure that they know how to contact the response team or maybe do a virus scan.
Getting an A+
This chapter introduces the concepts of viruses and malicious software. Some key points to remember when you take the A+ Certification Exams are
- A virus is a program that does harm to your system.
- Popular types of viruses are file, boot sector, and macro viruses.
- Other types of malicious software are Trojan horse viruses, worms, and spyware.
- You may use antivirus software to remove viruses from your system and antispyware software to remove spyware from your system.
- Be sure to update your virus definitions on a regular basis so that your virus protection software can protect your system against the most popular viruses.
1. You are trying to fix a computer that is showing symptoms of being infected with a virus. You have run your antivirus software multiple times and it does not seem to be picking up any viruses. What should you do?
(A) Update the antivirus software
(B) Update the virus definitions
(C) Update Windows
(D) Apply a Trojan
2. What type of malicious software does something totally different than what the user expects?
(A) Virus
(B) Virus definitions
(C) Worm
(D) Trojan virus
3. One of the sales employees of your company has installed a new piece of software on the system, but the system will no longer boot. What type of virus can prevent the system from booting?
(A) File virus
(B) Macro virus
(C) Boot sector virus
(D) Trojans
4. Your manager is concerned about some of the malicious code running in Microsoft Office documents that she has been reading about. What type of virus might occur in a Microsoft Office document?
(A) File virus
(B) Macro virus
(C) Boot sector virus
(D) Trojans
5. What type of malicious software monitors your Internet activity?
(A) Adware
(B) Worm
(C) Spyware
(D) Trojans
6. You are troubleshooting an infected system and have tried to do a System Restore to a previous day, but the system is unresponsive due to the virus. What should you do?
(A) Reformat the drive and re-install Windows.
(B) Do a system repair from the Windows installation media.
(C) Boot to Safe Mode and run System Restore.
(D) Perform a Windows Update.
7. What is the best way to ensure that your system is up to date with security patches?
(A) Virus protection software
(B) Virus definition update
(C) Spyware
(D) Windows Update
8. You are the network technician for your company. All employees within the company are running Windows 8.1. One of your users has been hit with a computer virus. What is the best way to clean the system and keep the employee files on the computer?
(A) Refresh the PC.
(B) Re-install from the Windows DVD.
(C) Reset the PC.
(D) Format and re-install from Windows DVD.
Answers
- B. Virus definitions need to be up to date to ensure that your virus protection software knows about recent viruses. See “Updating virus definitions.”
- D. A Trojan virus is a piece of software that does something totally different than what the user expected when he installed the application. Review “Trojan horses.”
- C. A boot sector virus prevents a system from booting because it corrupts the boot sector. Check out “Types of viruses.”
- B. A macro virus is created in a programming language like VBA, which exists in the Microsoft Office suite. Peruse “Types of viruses.”
- C. Spyware is the type of malicious software that monitors Internet activity. Take a look at “Spyware and adware.”
- C. If the system is unresponsive and you cannot get to the System Restore option, try booting to Safe Mode and then running System Restore. Peek at “Best practice for malware removal.”
- D. You should perform a Windows Update regularly to download current patches to your system. Look over “Windows Update.”
- A. Starting with Windows 8, we have a Refresh the PC feature that allows you to quickly re-install Windows without losing your personal files. Study “Best practice for malware removal.”
 You might also encounter worm viruses or Trojan viruses, but I save those for discussion in “
You might also encounter worm viruses or Trojan viruses, but I save those for discussion in “ It is critical that you update your virus definitions regularly, or your virus protection software won’t know about any new viruses that are developed.
It is critical that you update your virus definitions regularly, or your virus protection software won’t know about any new viruses that are developed.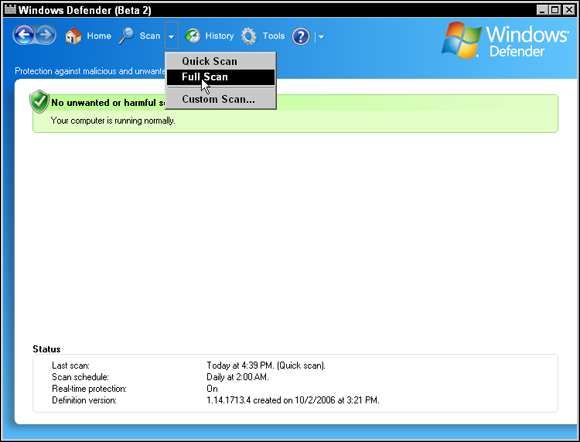

 To practice performing a Microsoft Update to your system, check out Lab 3-1. To practice using the Microsoft Baseline Security Analyzer (MBSA), check out Lab 3-2. Lab 3-1 and Lab 3-2 can be downloaded from the companion website at
To practice performing a Microsoft Update to your system, check out Lab 3-1. To practice using the Microsoft Baseline Security Analyzer (MBSA), check out Lab 3-2. Lab 3-1 and Lab 3-2 can be downloaded from the companion website at