Chapter 9
Establish Secure Storage and Handling
Abstract
When digital evidence is preserved in long-term or off-line storage, it must be done so securely and be available when required. Regardless of the storage option used, the authenticity, confidentiality, and integrity of digital evidence must always be maintained in a highly available approach.
Keywords
Forensic viability; Governance; Handling; Least privilege; Secure storageThis chapter discussed the fifth step for implementing a digital forensic readiness program as the need to establish governance over the secure storage and handling of collected digital evidence. Following a defense-in-depth approach of layered administrative, technical, and physical controls, organizations must ensure that the proper handling of digital evidence will support the preservation of its authenticity and integrity.
Introduction
Taking into account the safeguards and controls implemented to ensure collected digital evidence is admissible in a court of law, organizations must now determine how they will uphold these requirements as their digital evidence is being handled by several individuals and technologies. Likewise, as digital evidence is being transferred from one storage facility to another, such as long-term or off-line storage, consideration must be given to ensure the data is securely preserved and readily available when needed.
Establishing a governance framework over the handling and storage of digital evidence can be achieved by following the traditional approach of implementing complimentary administrative, technical, and physical controls. Through the combination of these different controls in a layered fashion, organizations can ensure that their digital evidence will be handled correctly and stored securely.
Secure Storage Attributes
Storage solutions such as an Enterprise Data Warehouse (EDW), discussed further in Appendix I: Data Warehouse Introduction, provides a centralized repository for aggregating digital evidence from multiple data sources. While it can be complex to implement, when done correctly an EDW can generate significant benefit such as allowing digital evidence to be analyzed over a longer period of time for improved data mining and analytics.
However, as discussed previously in chapter “Establish Legal Admissibility,” there are several administrative, technical, and physical controls that must be implemented to ensure that digital evidence being collected into any storage solution will be admissible in a court of law. Having identified the safeguards required to maintain admissibility, organizations must now determine how to properly implement these controls to ensure that their digital evidence is being handled correctly, throughout its entire lifecycle, and that its authenticity and integrity are maintained as it is transferred between different storage facilities.
Least Privilege Access1
Even though the modern threat landscape has changed, the delivery channels and attack vectors used by potential intruders and attackers continue to rely on the absence or weakness in both system and application access controls. In the context of admissibility in a court of law, the deficiencies in strong access controls are a blueprint for disaster when it comes to preserving the authenticity and integrity of digital evidence in secure storage.
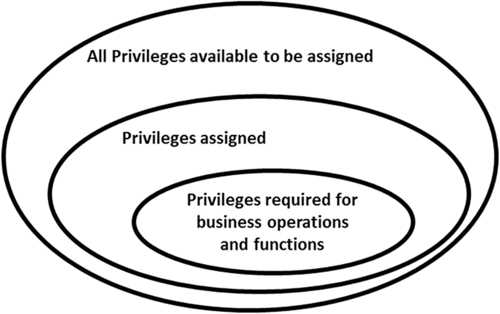
One of the fundamental cornerstones in the information security discipline is the concept of applying the principle of least privileged access. Generally, implementing least privilege implies that subjects2 only have access to the objects3 that are absolutely necessary as part of normal business operations and functions. However, as illustrated in Figure 9.1, when privileges are assigned they are typically granted beyond the scope of what is necessary permitting access that is otherwise not required.
Exercising rigid controls over subjects that have administrative access into storage solutions housing digital evidence is critical. Without enforcing the use of least privilege access to these secure storage facilities, organizations cannot demonstrate admissibility in a court of law because the potential for unauthorized subject access puts into questions the authenticity and integrity of their digital evidence.
End-to-End Cryptography
Outlined previously in chapter “Establish Legal Admissibility,” cryptography supports several information security-centric services that are fundamental to the digital forensic discipline. Supporting several use cases for preserving digital evidence, examples of how cryptography can be applied were identified as data-at-rest4 controls, used to guarantee that unauthorized access to the storage medium does not expose the digital evidence (eg, full disk encryption), or data-in-transit5 control, used for securing the transmission of digital evidence across any type of network infrastructure (eg, Internet protocol security6).
Additionally, following along with the principles of least privilege access, digital evidence being stored should only be readable by those authorized. Through the use of cryptography, organizations can achieve a much stronger data-in-use7 security control mechanism that will allows for the authenticity and integrity of the digital evidence to be maintained.
As digital evidence is being collected it should be encrypted, using a mechanism such as a secret key, to help enforce the principle of least privilege and restrict access to only those authorized subjects. As an example, while the application of an encrypted file system (EFS) contributes to the protection of data-at-rest, it also provides data-in-use controls where only those users in possession of the secret key can access and read the digital evidence.
Integrity Checking
Outlined previously in chapter “Establish Legal Admissibility,” integrity monitoring is an essential security control to guarantee the authenticity and integrity of digital evidence. With the known-good state of digital evidence captured, ongoing verification and validation must be implemented to ensure that no alteration to preserved digital evidence has been made.
When digital evidence is being preserved in a storage solution such as an EDW, integrity checks should be scheduled in alignment with the organization requirements for regulatory compliance and to effectively demonstrate legal admissibility. However, if digital evidence has been transferred into off-line storage, such as backup tapes, routinely performing integrity checks cannot be easily achieved. In this situation, organizations must take an alternate approach to preserving the authenticity and integrity of their digital evidence as follows:
1. Prior to digital evidence being transferred to off-line storage, an integrity check must be completed by comparing the known-good state (set #1) to the current state of the digital evidence (set #2) through a cryptographic hash values such as the message digest algorithm family8 (eg, MD5) or the secure hashing algorithm family9 (eg, SHA-2).
3. After all digital evidence have been transferred to off-line storage, a new set of hash values (set #3) is produced and compared against set #2 to guarantee the authenticity and integrity of digital evidence has been preserved.
Physical Security
Outlined previously in chapter “Establish Legal Admissibility,” physical security controls are designed to control and protect an organization’s assets (ie, people, building, systems, etc.) by reducing the risk of harm, damage, or loss. While physical security controls may not always have the same direct interaction with digital evidence that technical controls have, they provide layers of defense that deter, detect, deny, and delay potential intruders and attackers from accessing digital evidence preserved in any type of storage solution.
Where digital evidence is preserved in a storage solution, physical security controls are focused on reducing the risk of unauthorized access to the infrastructure housing the digital evidence. However, if digital evidence has been transferred into off-line storage, such as backup tapes, the scope of physical security controls extends beyond protecting only the infrastructure.
Digital evidence housed in off-line storage is subject to the same requirement for demonstrating authenticity and integrity in order for it to be admissible in a court of law. For example, the Good Practices Guide for Computer-Based Electronic Evidence, developed by the Association of Chief of Police Officers (ACPO) in the United Kingdom, was created with four overarching principles that must be followed when handling evidence in order to maintain evidence authenticity:
• Principle #1: No action taken by law enforcement agencies or their agents should change data held on a computer or storage media which may subsequently be relied upon in court.
• Principle #2: In circumstances where a person finds it necessary to access original data held on a computer or on storage media, that person must be competent to do so and be able to give evidence explaining the relevance and the implications of their actions.
• Principle #3: An audit trail or other record of all processes applied to computer-based electronic evidence should be created and preserved. An independent third party should be able to examine those processes and achieve the same result.
• Principle #4: The person in charge of the investigation (the case officer) has overall responsibility for ensuring that the law and these principles are adhered to.
When digital evidence has been transferred to off-line storage such as backup tape, a chain of custody for this new storage medium must be established to guarantee its authenticity and integrity by tracking where it came from, where it went after seizure, and who handled it for what purpose. From this point forward, the chain of custody must accompany the off-line storage and be maintained throughout the lifetime of the evidence. A chain of custody template has been provided as a reference in the Templates section of this book.
Furthermore, tapes should be stored using physical security controls that are intended to deny or delay potential intruders and attackers access to digital evidence. Achieving these layers of defenses can be accomplished by implementing the following physical security controls:
• Off-line storage medium, such as backup tape, should be placed in an evidence bag that, at a minimum, supports the following characteristics:
• Bags contain a secure pouch to store the media and an externally accessible pouch for accompanying documentation
• Proper labeling is affixed to correctly and efficiently identify the contents
• Tamper proof tape or locking mechanism is used to seal evidence inside
• Chain of custody is placed in the externally accessible pouch
Physical access to digital evidence in off-line storage must also be controlled following the same security principles of least privilege access. Once digital evidence has been properly sealed in evidence bags, these bags should be stored in a secure locker, safe, or library for long-term retention. It is important that at all times the chain of custody is updated to demonstrate ownership and location of the digital evidence.
Administrative Governance Foundations
Forensic viability can only be accomplished when digital evidence has been tracked and protected right from the time it was created and meets the requirements for legal admissibility throughout its entire lifecycle. Although technical and physical security controls have a more direct contribution to the secure handling and storage of digital evidence, they cannot be effective unless there is an organizational requirement to adhere to. Therefore, to guarantee that digital evidence is forensically viable, organizations must have an established governance framework in place to ensure the collection, preservation, and storage of digital evidence is done properly.
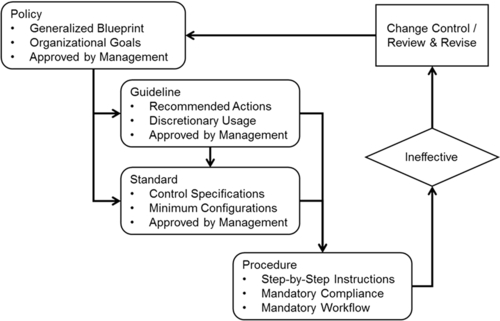
Ultimately, the objective of this governance framework is to establish direction on how the organization will preserve the authenticity and integrity of their digital evidence. Management, with involvement from key stakeholders such as legal, privacy, security, and human resources, must work together to define a series of documents that describe exactly how the organization will go about achieving these goals. Illustrated in Figure 9.2, and discussed further in chapter “Evidence Management,” an information security management framework consists of a hierarchy of different types of documents that have direct influence and precedence over other documents.
Within the context of guaranteeing forensic viability of digital evidence, governance documentation should be created to address the following areas:
Personnel
• Provide continuous training and awareness regarding the governance framework to all stakeholder involved in the collection, preservation, and storage of digital evidence.
• As acknowledgment of their adherence with the governance framework, stakeholders should be required to sign the necessary document to indicate their understanding of and commitment to them. Management, legal, privacy, security, and human resources should all be involved to ensure that these signed documents can be legally enforced.
• Require enhanced background checks to be routinely conducted for personnel who have access to digital evidence.
Evidence Storage
• Provide clear guidance and direction regarding the installation and updates to hardware and software components.
• Ensure storage solutions are designed and architected to meet the requirement and specification of their intended business strategy and/or function.
• Enforce the principle of least privilege access and implement the use of multifactor authentication mechanism including:
• Something you have (eg, smart card)
• Something you know (eg, password)
• Something you are (eg, fingerprint)
• Apply a layered defense-in-depth approach to physical security using a combination of control that are designed to deter, detect, deny, and delay potential intruders and attackers.
Evidence Handling
• Apply integrity monitoring and checks to ensure digital evidence has not been tampered or modified from its know-good and authenticated state;
• Prohibit the alteration or deletion of original source data;
• Restrict the storage of, transmission of, and access to digital evidence without the use of cryptographic encryption;
• Enforce the principle of least privilege access to only authorized personnel;
• Ensure that the long-term storage of digital evidence uses any form of storage medium that is write once read many (WORM);
• Seal digital evidence in appropriate containers (ie, evidence bag, safe) to preserve authenticity and integrity during long-term storage;
• Define the long-term retention and recovery strategies for digital evidence.
Incident and Investigation Response
• Require that each incident and investigation is tracked and reported separately.
• Ensure that digital evidence used is proven to be authentic to the original source.
Assurance Controls
• Require routinely audits and control assessments are conducted.
Essentially, the culture and structure of each organization influences how these governance documents are created. Regardless of where (internationally) business is conducted or the size of the organization, there are five simple principles that should be followed as generic guidance for achieving a successful governance framework:
• Keep it simple: All documentation should be as clear and concise as possible. The information contained within each document should be stated as briefly as possible without omitting any critical pieces of information. Where documentation is drawn out and wordy, it is typically more difficult to understand, less likely to be read, and harder to interpret for implementation.
• Keep it understandable: Documentation should be developed in a language that is commonly known throughout the organization. Leveraging a taxonomy, as discussed in Appendix F: Building A Taxonomy, organizations can avoid the complication of using unrecognized terms and slangs.
• Keep it practicable: Regardless of how precise and clear the documentation might be, if it cannot be practiced then it is useless. An example of an unrealistic documentation would be a statement indicating that incident response personnel is to be available 24 hours a day; even though there is no adequate mean of contacting them when they are not in the office. For this reason, documentation that is not practicable is not effective and will be quickly ignored.
• Keep it cooperative: Good governance documentation is developed through the collaborative effort of all relevant stakeholders, such as legal, privacy, security, and human resources. If key stakeholders have not been involved in the development of these documents, it is more likely that problems will arise during its implementation.
• Keep it dynamic: Useful governance document should be, by design, flexible enough to adapt with organizational changes and growth. It would be impractical to develop documentation that is focused on serving the current needs and desires of the organization without considering what could come in the future.
Backup and Restoration Strategies
Even though digital evidence has been put into off-line storage for long-term retention, there might come a time when it is needed in support of a business risk scenario, as discussed previously in chapter “Define Business Risk Scenarios.” When this time comes, it is critical that in addition to the integrity of digital evidence being authenticated, the data itself must also be restored and made readily available so that there is no delay in the investigative process.
The recovery time objective (RTO)10 that an organization accepts for restoring digital evidence from backups is what drives the type of backup strategy that will be implemented. RTO is commonly represented in units of time as minutes, hours, days, or longer depending on the needs for restoring digital evidence. When setting the RTO targets, it is important that organizations realize that lower values will result in more expensive backup solutions than the higher values. Recognizing that every organization has different RTO targets for restoring digital evidence, Table 9.1 provides an approximation of values and the backup solution required to meet the service levels.
Table 9.1
| RTO Value | Backup Solution Required |
| <1 hour | Near real-time data replication |
| 1–6 hours | Data replication |
| 6–24 hours | Data restoration from online backup media |
| 2–14 days | Data restoration from off-line backup media |
Near Real-Time Data Replication
Meeting service levels with this type of backup solution requires that data is synchronously replicated across multiple identical and distributed instances of the storage solution. Because this type of backup strategy requires multiple instances of the storage solution to be highly available for near real-time data clustering, it is considered to be the most expensive, complex, and resource intensive.
Data Replication
Performed on a consistent schedule, this backup solution replicates data to two or more identical and distributed instances of the storage solution. Similar to the requirements of the near real-time strategy, this type of solution still requires the implementation of two or more identical and distributed instances of the storage solution. However, with more moderate RTO targets, this type of backup solution is considered to be just as expensive but slightly less complex and resource intensive.
Data Restoration From Online Backup Media
With data replications set to occur on a schedule, this backup solution replicates data to highly available online media; such as network attached storage. Service levels for this type of strategy are reduced to allow for data to be restored into the production storage solution when required, which makes this type of backup solution less expensive, complex, and resource intensive.
Data Restoration From Off-line Backup Media
Discussed previously in this chapter, data can be transferred to off-line media, such as backup tapes, for long-term storage. This type of backup strategy is the least expensive because it does not have the complexities of implementing additional storage infrastructures. However, the RTO targets for this solution are extremely relaxed because of the time required to restore from off-line media.
Summary
Preserving the authenticity and integrity of digital evidence extends beyond the implementation of technical and physical security controls. Through the implementation of a governance framework that ensures forensic viability right from when data is created, organizations can ensure that legal admissibility of digital evidence is maintained during secure handling and storage.