![]()
Industrial Automation and Control System Security Training
Chapter 6 presented the application of standards and guidelines to industrial automation and control system security and subsequently developed a foundation of security controls that are effective in reducing risk and protecting these systems. Chapter 7 reinforces these concepts by developing automation and control system security training concepts, training sources, and templates for designing and generating such programs.
Background
Training for industrial automation and control system security is addressed in many different formats, philosophies, levels, and degrees of formality. Some automation and control system security issues are covered peripherally in IT-based information system security courses; others are covered in depth in courses aimed at control system engineers and technicians; and still others are somewhere in between.
Until recently, there has been a dearth of high-quality courses focused primarily on industrial automation and control system security. Most courses offered by various bodies were heavily focused on information system security and paid little attention to real-time systems used to control the nation’s manufacturing facilities, process plants, and critical infrastructure. Because of the threat of terrorism and increased concerns of natural disasters and the demands of a growing population, focus is shifting from purely information system security to the security of automation and control systems within governmental agencies, educational institutions, and private training organizations.
Training in the field of securing industrial automation and control systems is critical to supporting the goals of protecting the nation’s manufacturing and process industry base and its critical infrastructure by building a cadre of trained personnel, maintaining technological leadership, developing advanced security-related hardware and software, and raising awareness of threats to national security.
With these goals in mind, key issues are who should be responsible for such training and for what level the training should be designed. In organizations, specific individuals should be assigned the responsibility of training employees involved with the security of automation and control systems as well as vendors and outside contractors. Some of the major sources and methods of training for automation and control systems security are presented in the following sections of this chapter.
Training Sources and Approaches
Some of the useful industrial automation and control system training programs and related initiatives that are available include the following:
• Idaho National Laboratory (http://www.inl.gov/scada)
• Sandia National Laboratories (http://energy.sandia.gov/?page_id=6912)
• ISA (www.isa.org/training)
• US-CERT (http://www.us-cert.gov/control_systems)
• SANS (http://www.sans.org/security-resources/)
• National Initiative for Cybersecurity Education (NICE) (http://nist.gov/nice)
• National Security Agency (NSA) and the Department of Homeland Security (DHS) National Centers of Academic Excellence
Idaho National Laboratory
The Idaho National Laboratory, along with the Sandia National Laboratories, is home to the National SCADA Test Bed (NSTB) Program. This program was established by the U.S. Department of Energy and is focused on ensuring the “secure, reliable and efficient distribution of power.”
As described on its Web site, the NSTB program is chartered to perform the following functions:
• Assess selected control systems and control system components to identify cyber vulnerabilities. Testing is planned and conducted in collaboration with the interested industry partner and may be performed in the laboratory (test bed) environment or at the partner’s site.
• Provide control system security training through workshops that describe common cyber vulnerabilities found in control systems and effective methods for mitigation.
• Share with appropriate standards organizations information that can be used to support the development of improved industry standards applicable to control system security.
• Participate in conferences that include control system security topics to share information obtained through system assessments and analyses.
Relative to SCADA, the Idaho National Laboratory training is aimed at “IT/control system managers, IT/control system security personnel, network and control system support engineers, and control system designers and developers who are involved in or responsible for control system cybersecurity.” The course offerings are:
• Introductory SCADA Security (4 hours), comprising:
– SCADA Network Communications Overview
– Common Vulnerabilities of Control Systems
– Inadequate Policies and Procedures
– Poorly Designed Control System Networks
– Misconfigured or Unpatched Operating Systems and Embedded Devices
– Inappropriate Use of Wireless Communication
– Inadequate Authentication of Control System Communications
– Inadequate Identification and Control of Access to Control System
– Lack of Detection and Logging of Intrusion
– Dual Use of Control System Networks
– Lack of Security Checking of Control System Software/Applications
– Lack of Change Management/Change Control Procedures and Agreements
– Potential Mitigation Strategies based on multiple levels of implementation
• Intermediate SCADA Security (8 hours), covering the following material:
– General Security Observations and Pitfalls
– SCADA Network Communications Overview
– Potential SCADA Network Entry Points and Defenses
– SCADA Network Scanning and Vulnerability Identification (in a safe manner)
– Network Monitoring and Simple Intrusion Detection
– Dissecting SCADA Protocols
– Common Programming Pitfalls
– Modern Hardware and OS Mitigation Strategies
– Incident Response Essentials for the SCADA Community
• Advanced SCADA Security Red/Blue Team (5 days), with the following topics similar to those covered in Intermediate SCADA Security, but with hands-on exercises using SCADA equipment:
– General Security Observations and Pitfalls
– Control System Network Communications Overview
– Potential Control System Network Entry Points and Defenses
– Control System Network Scanning and Vulnerability Identification
– Network Monitoring and Simple Intrusion Detection
– Dissecting Control System Protocols
– Common Programming Pitfalls
– Modern Hardware and OS Mitigation Strategies
– Incident Response Essentials for the Control System Community
The Sandia National Laboratories
The Sandia National Laboratories offer a course on SCADA assessment titled “Methodologies for Assessing SCADA Systems and an Overview of Related Security and Vulnerability Concerns.” This course is offered “at Sandia’s discretion to individuals with need-to-know and by invitation.” The course is customizable and includes the following areas:
• SCADA and Other Digital Control System Uses in Infrastructures and Industry
• Vulnerabilities in SCADA Components and Systems
• Methodologies and Tools to Assess SCADA Systems in a Successful, Measurable, and Reproducible Manner
The International Society of Automation (ISA) offers a number of courses on securing industrial automation and control systems, including the following:
• Industrial Networking & Security, covering the following topics:
– TCP/IP Networking Over Ethernet, Over Serial Links (PPP) and Through Other Networks
– Making Networks Reliable: Redundancy/Name Services/Fault Tolerance/Spanning Tree
– Secure Architectures: Layering Based on Function, Firewall Placements, Use of DMZs, Patch/Virus Update Management
– Understanding Packets and Protocols: Understanding IP, TCP and UDP and Application Protocols
– Building a Plant Floor Web Server Using HTML, XML, Client/Server Side Scripting
– Network Security Issues: Risks and Vulnerabilities | Attack Methods and Technologies
– Applying: Virus Protection | Firewall Basics | Encryption Basics
– Advanced Security: VPN Technology and Application, VLAN Technology and Application, Static/Dynamic Routing
– Firewall Technology: Basic/Advanced, ACL Definitions, Stateful Inspection, HIDS/NIDS
– User Authentication: Strong Authentication, Password Strategies, Multifactor, Centralized Policy Management
– Practical Industrial Intranet Applications Using ISA-99 Recommendations and Standards
• Using ANSI/ISA-99 to Secure Your Control System, with the following topics:
– Understanding the Current Industrial Security Environment: What Is Electronic Security for Industrial Automation and Control Systems? | How IT and the Plant Floor Are Different and How They Are the Same
– How Cyberattacks Happen: Understanding the Threat Sources | The Steps to Successful Cyberattacks
– Creating A Security Program: Critical Factors for Success | Understanding ISA-99 Part 2: Establishing an Industrial Automation & Control Systems Security Program
– Using ISA-99: Risk Analysis: Business Rationale | Risk Identification, Classification, and Assessment | The DNSAM Methodology
– Using ISA-99: Addressing Risk with Security Policy, Organization, and Awareness: CSMS Scope | Organizational Security | Staff Training and Security Awareness
– Using ISA-99: Addressing Risk with Selected Security Countermeasures: Personnel Security | Physical and Environmental Security | Network Segmentation | Access Control
– Using ISA-99: Addressing Risk with Implementation Measures: Risk Management and Implementation I System Development and Maintenance I Information and Document Management
– Using ISA-99: Monitoring and Improving the CSMS: Compliance and Review | Improve and Maintain the CSMS
• Advanced Industrial Cybersecurity, focusing on the following subjects:
– TCP/IPV6 Networking: Over Ethernet | Over Serial Links (PPTP) | Using other Industrial Protocols
– Converting from IPV4 to IPV6 without Causing Security Problems
– Making Networks Secure: Local, Global, and Organizational Policies
– COTS OS: Vulnerabilities and Hardening Techniques
– Security/Performance Problems Associated with Patch/Virus Update Management
– Secure Architectures: Layering Based on Function and on Firewall/VPN Placements
– Building a Secure Plant Floor Web Server: HTML | XML | Methods to Enhance Security
– Network Security Issues: Risks and Vulnerabilities | Attack Methods and Technologies
– Applying: IPS/Virus Protection/Access-ACLs | Identification/Authentication/Nonrepudiation
– Network Security: VPN Technology and Application | VLAN Technology and Application | Managed Switch/Router Configuration
– Security Management: Access, Strong Authentication, Password Strategies, Multifactor, Centralized Policy Management
– Practical Cybersecurity Applications: ANSI/ISA-99 | NIST | NCSDOCIPEP | DHS | DOE | CPNI
• Cybersecurity for Automation, Control, and SCADA Systems, which includes the following subjects:
– Defining Industrial Cybersecurity
– Risk Assessment
– Threats and Vulnerabilities
– Security Policies, Programs, and Procedures
– Understanding TCP/IP, Hackers, and Malware
– Technical Countermeasures
– Architectural & Operational Strategies
• Introduction to Industrial Automation Security and the ANSI/ISA-99 Standards, covering the following areas:
– Understanding the Current Industrial Security Environment: What Is Electronic Security for Industrial Automation and Control Systems? | Trends in Security Incidents
– How IT and the Plant Floor Are Different and How They Are the Same
– Current Security Standards and Practices
– Creating a Security Program: Critical Factors for Success | Understanding ISA-99 Part 2: Establishing an Industrial Automation and Control Systems Security Program
– Using ISA-99: Risk Analysis: Business Rationale | Risk Identification, Classification, and Assessment
– Using ISA-99: Addressing Risk with Security Policy, Organization, and Awareness: CSMS Scope | Organizational Security | Staff Training and Security Awareness | Business Continuity Plan | Security Policies and Procedures
– Using ISA-99: Addressing Risk with Selected Security Countermeasures: Personnel Security | Physical and Environmental Security | Network Segmentation | Access Control: Account Administration, Authentication, and Authorization
– Using ISA-99: Addressing Risk with Implementation Measures: Risk Management and Implementation | System Development and Maintenance | Information and Document Management | Incident Planning and Response
– Using ISA-99: Monitoring and Improving the CSMS: Compliance and Review | Improve and Maintain the CSMS
US-CERT
The United States Computer Emergency Response Team (US-CERT) offers the following instructor-led courses:
• Introduction to Control Systems Cybersecurity – Introduces participants to industrial control system fundamentals and comparisons of IT and control system architectures. The elements of the course are:
– Cybersecurity Landscape: Understanding the Risks
– Industrial Control Systems Applications
– Current State of Cybersecurity in Industrial Control Systems
– Practical Applications of Cybersecurity
• Industrial Control System Security (ICS) for Management – Provides background and basic understanding of the current industrial control system cybersecurity landscape for managers. The course includes the following topics:
– Overview of the Elements of the Risk Equation and How It Applies to Cybersecurity of an ICS
– Threats to an ICS and Its Components
– Tools That Can Be Used to Help Mitigate the Cybersecurity Risk
• Intermediate Cybersecurity for Industrial Control Systems Part 1 – Consists of technical instruction on the protection of industrial control systems using offensive and defensive methods. The material includes:
– Current Security in ICS
– Strategies Used Against ICS
– Defending the ICS
– Preparation and Further Reading for Part 2
• Intermediate Cybersecurity for Industrial Control Systems Part 2 – Hands-on training with laboratory exercises to impart knowledge of how attacks against control systems are launched and succeed. The course topics include:
– Supervisory Control and Data Acquisition (SCADA) and Control System Overview
– Risk to Industrial Control Systems
– Exploit Demonstration
– Basic Control Security Considerations
– Network: Security, Identification, and Remediation
– Network: Defense, Detection, and Analysis
• ICS Advanced Cybersecurity – Includes hands-on training on protecting and securing industrial control systems from cyber attacks, including a Red Team/Blue Team exercise that will be conducted within an actual control systems environment. The course comprises the following subjects:
– Overview of the DHS Control Systems Security Program
– Review of Cybersecurity for Industrial Control Systems
– Demonstration Showing How a Control System Can Be Attacked from the Internet
– Hands-on Classroom Training on Network Discovery Techniques and Practices
– Hands-on Classroom Training on Network Exploitation, Network Defense Techniques and Practices
– A 12-Hour Exercise where Participants are Either Attacking (Red Team) or Defending (Blue Team)
– Red Team/Blue Team Exercise Lessons Learned and Round-Table Discussion
SANS
The SANS organization offers an advanced SCADA security hands-on training course aimed at administrators and automation system personnel. The material addresses vulnerabilities and risks to SCADA systems, effects on enterprise security, the use of open source security tools, and testing methods. The course subject areas include the following:
• Review of Industrial Control Systems (ICS), Operating System Kernels, and Network Security SCADA Penetration Testing
• SCADA Vulnerability Assessment methodology
• SCADA Vulnerability Analysis
• Embedded Device Fuzzing (an attack using random, malformed, or bad data)
• Protocol Analysis
• Methods for Compromising and Dissecting Common Security Controls Found in ICS Environments
The National Initiative for Cybersecurity Education
The National Initiative for Cybersecurity Education (NICE) is a partnership of government, industrial, educational, and professional organizations with the mission “to enhance the overall cybersecurity posture of the United States by accelerating the availability of educational and training resources designed to improve the cyber behavior, skills, and knowledge of every segment of the population.” The specific goals of NICE are to:
1. Raise awareness among the American public about the risks of online activities
2. Broaden the pool of skilled workers capable of supporting a cyber-secure nation
3. Develop and maintain an unrivaled, globally competitive cybersecurity workforce
The National Institute of Standards and Technology (NIST) has been assigned the lead in the NICE initiative and will coordinate the government activities involving the Department of Homeland Security (DHS), the Department of Defense (DoD), the Department of Education (ED), NIST, the National Science Foundation (NSF), the National Security Agency (NSA), and the Office of Personnel Management (OPM).
The objectives1 defined by NICE to achieve the desired strategic goals include the following:
1. Improve citizens’ knowledge to allow them to make smart choices as they manage online risk
2. Improve knowledge of cybersecurity within organizations so that resources are well applied to meet the most obvious and serious threats
3. Enable access to cybersecurity resources
4. Improve K-12 science, technology, engineering, and mathematics (STEM) education, emphasizing the important role of mathematics and computational thinking
5. Increase the quantity and quality of academic computer science courses in high schools
6. Increase the quantity and quality of undergraduate and graduate cybersecurity curricula for students in computer science and, more broadly, IT and security-related degree programs
7. Incentivize, support, and recognize excellence in graduate-level cybersecurity research and development
8. Develop a usable cybersecurity competency framework (human resources and curriculum focus)
9. Provide a framework for focusing on cybersecurity training to meet evolving needs
10. Study the application of professionalization, certification, and licensing standards on cybersecurity career fields
In order to advance its objectives, NICE has published a draft document, the NICE Cybersecurity Workforce Framework, which classifies the typical duties and skill requirements of cybersecurity workers. This framework was developed because cybersecurity professionals often do not fit into standard job descriptions and titles. (http://csrc.nist.gov/nice/framework/)
The NICE Cybersecurity Workforce Framework develops a vocabulary that can be used by any type of organization. It organizes cybersecurity work into the following categories:
• Design
• Operation
• Maintenance
• Incident response
• Information gathering
• Analysis
In another initiative, NIST, the U.S. Department of Education, NICE, and the National Cybersecurity Education Council (NCEC) are developing a strategic public-private partnership to promote formal cybersecurity education. The effort is designed to support the NICE goal of broadening the pool of skilled workers capable of supporting a cyber-secure nation. In order to accomplish this goal, the partnership is collaborating with state and local governments to establish and support formal cybersecurity education programs for kindergarten through 12th grade and for higher education and vocational programs.
National Security Agency (NSA) and the Department of Homeland Security (DHS) National Centers of Academic Excellence
NSA and the Department of Homeland Security (DHS) are sponsors of the National Centers of Academic Excellence initiative. This program has the goal of reducing vulnerabilities in the national information infrastructure. In order to accomplish this goal, National Centers of Academic Excellence are established in educational institutions to promote research and education in information assurance (IA). The students graduating from these institutions with training and research experience in information assurance will be able to apply their skills to securing the nation’s infrastructure and information systems.
Institutions can be designed as National Centers of Academic Excellence (CAE) in IA Education (CAE/IAE) and Research (CAE-R) programs. The designations have terms of five years, after which the institution must successfully reapply in order to retain its CAE designation.
Applicants for a National Center of Academic Excellence in IA Education designation are four-year colleges and graduate-level universities and must pass a stringent evaluation and review. To apply for designation of a National Center of Academic Excellence in research, the college or university must meet the Carnegie Foundation's classifications of Research University/Very High (RU/VH), Research University/High (RU/H) and Doctoral Research University (DRU) or the equivalent.
Training Support Guidelines
There are a number of documents that can provide guidance in setting up and conducting training applicable to industrial automation and control systems. Two of the important ones are reviewed here to provide a general understanding of their content and capabilities. These publications are:
• NIST SP 800-50, Building an Information Technology Security Awareness and Training Program (http://csrc.nist.gov/publications/nistpubs/800-50/NIST-SP800-50.pdf)
• NIST SP 800-16 Revision 1, Information Security Training Requirements: A Role- and Performance-Based Model (Draft) (http://csrc.nist.gov/publications/drafts/800-16-rev1/Draft-SP800-16-Rev1.pdf)
NIST Special Publication 800-50
NIST Special Publication 800-502, Building an Information Technology Security Awareness and Training Program, provides guidance in developing and conducting information system security training. The document is aimed at IT security, but it is useful in supporting automation and control system security awareness and training in that it provides useful principles that can be used in setting up such programs.
The publication describes the following four critical steps in the life cycle of a security awareness and training program:
1. Awareness and Training Program Design – Needs assessment is conducted and a training strategy is developed and approved. This strategic planning document identifies implementation tasks to be performed in support of established security training goals.
2. Awareness and Training Material Development – Available training sources, scope, content, and development of training material, including solicitation of contractor assistance if needed, are addressed.
3. Program Implementation – Effective communication and rollout of the awareness and training program are conducted. It also addresses options for delivery of awareness and training material (Web-based, distance learning, video, on-site, etc.).
4. Post-Implementation – Guidance on keeping the program current and monitoring its effectiveness is provided. Effective feedback methods are described (surveys, focus groups, benchmarking, etc.).
The document also defines the following three common models used in managing a security training function:
• Centralized – All responsibility resides with a central authority.
• Partially Decentralized – Policy and strategy lie with a central authority, but implementation responsibilities are distributed.
• Fully Decentralized – Only policy development resides with a central authority, and all other responsibilities are delegated to individual organizational components.
NIST SP 800-50 also provides a useful perspective of learning as a continuum, going from awareness, to training, to education, as shown in Figure 7-1.
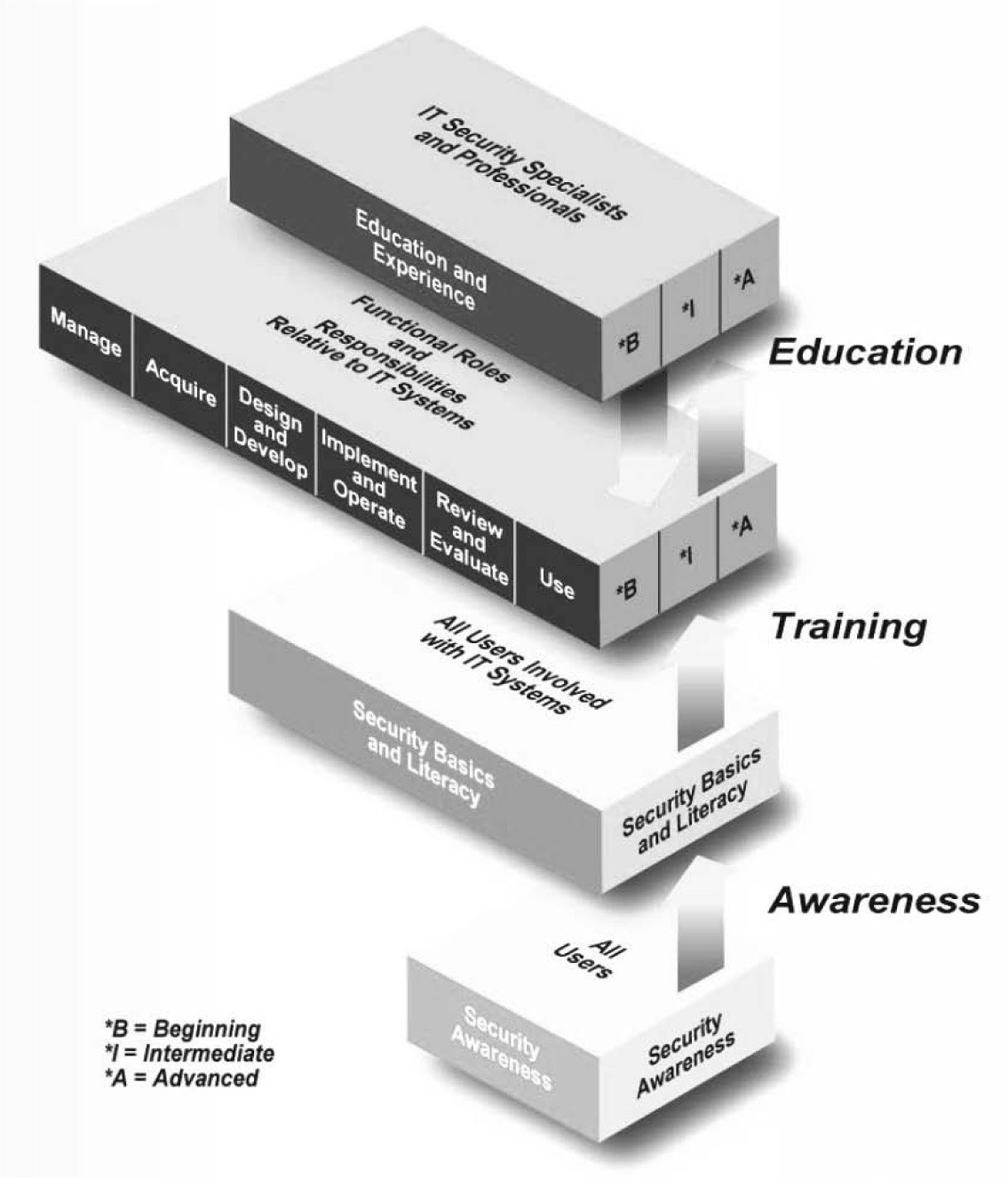
Figure 7-1. Security Learning Continuum
[Source: NIST SP 800-50, Building an Information Technology Security Awareness and Training Program, October, 2003.]
NIST SP 800-50 discusses the differences among awareness, training, and education as:
• Awareness – Focuses attention on security
• Training – Strives to produce relevant and needed security skills and competencies
• Education – Integrates all of the security skills and competencies of the various functional specialties into a common body of knowledge and strives to produce IT security specialists
This publication provides additional details on implementing awareness and training that can be applied to industrial automation and control systems.
NIST Special Publication 800-16
NIST SP 800-16, Information Security Training Requirements: A Role- and Performance-Based Model (Draft,3 complements NIST SP 800-50. As shown in Figure 7-1, it defines learning as a continuum, beginning with awareness, transitioning to training, and then moving into education. The model is role-based in that it “defines the information security learning needed as a person assumes different roles within an organization and different responsibilities in relation to information systems.” NIST SP 800-16 expands on the continuum as follows:
1. Basic Security Awareness – Required for employees, including contractor employees who are involved in any way with information systems.
2. Awareness Training (Basics and Literacy) – A transitional stage between basic awareness and role-based training. It provides the foundation for subsequent specialized or role-based training by providing a universal baseline of key security terms and concepts.
3. Role-Based Training – Focuses on providing the knowledge, skills, and abilities specific to an individual’s roles and responsibilities relative to information systems. At this level, training recognizes the differences between beginning, intermediate, and advanced skill requirements.
4. The Education Level – Focuses on developing the ability and vision to perform complex multidisciplinary activities and the skills needed to further the information security profession and to keep pace with threats and technology changes.
5. Professional Development – Intended to ensure that users, from beginner to the career security professional, possess a required level of knowledge and competence necessary for their roles. Professional development validates skills through certification and advanced education.
To implement instructional design, NIST SP 800-16 presents the five-phase ADDIE Instructional Design Model, which comprises the phases of analysis, design, development, and implementation and evaluation. The model is illustrated in Figure 7-2.
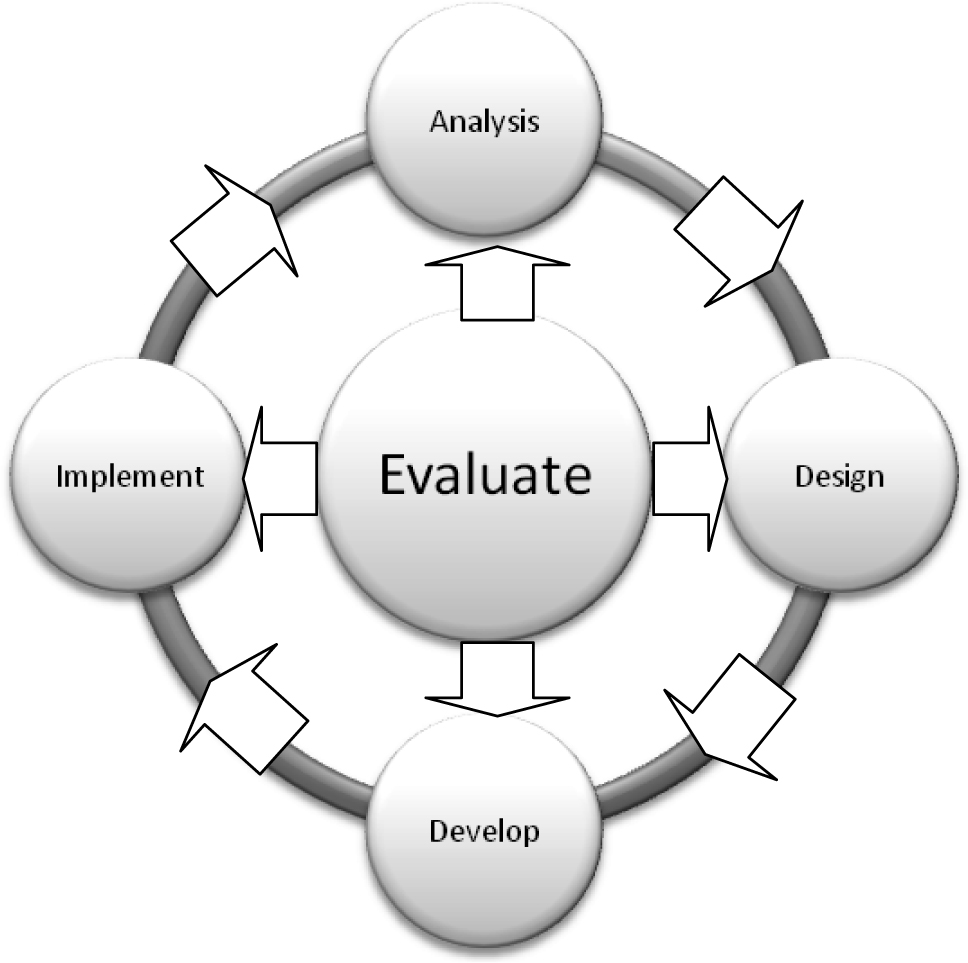
Figure 7-2. DDIE Instructional Design Model
[Source: NIST Special Publication 800-16 Revision 1, Information Security Training Requirements: A Role- and Performance-Based Model (Draft), March 2009.]
The five phases of the instructional design model consist of the following activities:
1. The Analysis Phase – Compiles an inventory of all tasks associated with each role and conducts a needs assessment to select those tasks for which training needs to be developed. Task descriptions can usually be found in position descriptions, performance plans, assignment letters, system security plans, and directives, or can be determined through interviews with current practitioners. These tasks should yield:
– The knowledge level required
– The desired behavioral outcomes
– Performance measures for each task
In addition, prerequisite knowledge should be determined.
2. The Design Phase – Develops the learning objectives for each of the tasks defined during the analysis phase. Then, the steps required to accomplish each objective have to be identified. The design phase consists of the following steps:
– Develop learning objectives (enabling and terminal)
– Identify and list steps required
– Develop performance/knowledge tests
– Develop required entry behaviors (optional)
– Sequence learning objectives
3. The Development Phase – Identifies and lists the activities that will help the training recipients achieve each objective (e.g., lecture, simulation, role-play, demonstration, lab exercise, table-top exercise). These activities are then used to select the appropriate delivery method(s). The steps of the development phase are summarized as follows:
– List activities required for each objective
– Select appropriate delivery method(s)
– Gather reference material
– Review existing course material
– Develop lesson plans and instructor guide
– Conduct expert review of course materials
4. The Implementation Phase – Tests a draft version of the course or module to a selected audience for feedback. Adjustments are then made as required. The steps in this phase are:
– Pilot course to hand-picked audience
– Make course adjustments
– Train the trainer (if required)
– Full-scale delivery
5. The Evaluation Phase – Conducts formative and summative evaluations, described as follows:
– Formative – During all phases, analysis, design, development, and implementation, a formative analysis evaluates if what is being taught is what was intended to be taught.
– Summative – Evaluates if the student was satisfied with the course and instructor, if the student achieved his or her objectives, if supervisors of the students felt the student was a more effective employee as a result of the course, and if the training program is providing the types of courses that are most needed.
NIST SP 800-16 also provides templates for training modules that provide a roadmap for teaching the module. Figure 7-3 illustrates a typical module.
Common Training Subjects
In reviewing the courses and training programs discussed in this chapter, a common set of topics can be extracted to use as a basis for training in the security of industrial automation and control systems. These proposed core topics are summarized in Table 7-1.
Figure 7-3. Example instructional module
[Source: NIST Special Publication 800-16 Revision 1, Information Security Training Requirements: A Role- and Performance-Based Model (Draft), March 2009.]
Table 7-1. Industrial Automation and Control System Core Topics
|
Topic |
Description |
|
Security Policies and Procedures |
Guiding document |
|
Incorporating Applicable Standards and Guidelines |
ANSI/ISA-99, NIST |
|
Risk Management and Countermeasures |
Risk analysis and mitigation |
|
SCADA Network Communications |
TCIP/IP, Ethernet, Wireless, etc. |
|
Common Control System Vulnerabilities and Threat Sources |
Vulnerability identification, network scanning |
|
Access Control and Authentication for Control Systems |
Multifactor, passwords |
|
Logging and Intrusion Detection |
Logging of system accesses, intrusions, and abnormal activity |
|
Change Management Procedures |
Document and confirm system changes |
|
Typical SCADA Entry Points |
Typical targets of choice |
|
Application and Control System Software |
Vulnerabilities and security weaknesses, COTS OS |
|
Security Awareness Training |
Awareness training actively conducted in accordance with security policy |
|
Incident Response |
Responding to incidents in an automation environment |
|
Encryption Methods |
Encryption in an automation/control environment |
|
Virtual Private Networks and VLANs |
Secure remote access methods and issues |
|
Firewalls and Antivirus Software |
Screening devices and methods in time-critical automation/control environments |
Summary
Training in the area of industrial automation and control system security is now offered by a variety of sources and types of institutions, including secondary schools, universities, industry, technical societies, community colleges, governmental bodies, and technical schools. This type of training was not always as available as it is now, which is the result of increased awareness of threats against automation and control systems that are critical to the nation.
This chapter reviewed some of the more prominent training programs and their content. In addition, governmental and NIST recommendations and guidelines applicable to conducting automation and control system-related training were presented to provide a basis for developing effective programs in this area. The chapter concluded with a proposed listing of fundamental cybersecurity topics for automation and control system security that can be used as a foundation for automation system-based training. Chapter 8 will explore what the future holds for security in the realm of industrial automation and control systems.
Review Questions for Chapter 7
1. What organizations host the National SCADA Test Bed (NSTB) program?
a. NIST and the NSA
b. The Idaho National Laboratory and the Sandia National Laboratories
c. ISA and SANS
d. US-CERT and NIST
2. Which of the following is NOT a function of the National SCADA Test Bed (NSTB)?
a. Assess selected control systems and control system components to identify cyber vulnerabilities
b. Develop new standards and guidelines for governmental agencies
c. Provide control system security training through workshops that describe common cyber vulnerabilities found in control systems
d. Share with appropriate standard's organizations information that can be used to support the development of improved industry standards applicable to control system security
3. What organization developed and teaches the application of 99.02.01-2009, Security for Industrial Automation and Control Systems: Establishing an Industrial Automation and Control Systems Security Program?
a. SANS
b. NIST
c. ISA
d. NSA
4. In a training program hands-on exercise, what is the function of the Red Team?
a. Mitigating
b. Scanning
c. Defending
d. Attacking
5. In a training program hands-on exercise, what is the function of the Blue Team?
a. Defending
b. Attacking
c. Scanning
d. Mitigating
6. What is fuzzing?
a. Modifying memory locations
b. An attack using random or malformed bad data
c. Scanning to determine vulnerabilities
d. Responding to an attack by counterattacking
7. The National Initiative for Cybersecurity Education (NICE) is a partnership of government, industrial, educational, and professional organizations. Which of the following is NOT one of the goals of NICE?
a. Raise awareness among the American public about the risks of online activities
b. Broaden the pool of skilled workers capable of supporting a cyber-secure nation
c. Develop and maintain an unrivaled, globally competitive cybersecurity workforce
d. Develop secure digital control systems
8. Which of the following organizations is NOT a participant in the NICE initiative?
a. NIST
b. NASA
c. Department of Homeland Security (DHS)
d. NSA
9. The NICE Cybersecurity Workforce Framework develops a vocabulary that can be used by any type of organization in categorizing cybersecurity work. Which of the following is NOT a category in this framework?
a. Penetration testing
b. Design
c. Operation
d. Maintenance
10. The U.S. National Centers of Academic Excellence initiative is sponsored by which of the following organizations?
a. NIST and the Department of Energy
b. SANS and the Department of Education
c. NSA and the Department of Homeland Security
d. The Department of Defense and the US-CERT
11. The designation of an institution as a National Center of Academic Excellence has a duration of how many years before the institution has to reapply?
a. Two years
b. Ten years
c. Five years
d. Seven years
12. Which of the following is NOT one of the critical steps in the life cycle of a security awareness and training program as described in NIST Special Publication 800-50, Building an Information Technology Security Awareness and Training Program?
a. Awareness and training program design
b. Program implementation
c. Post-implementation
d. Pre-implementation needs review
13. Which of the following is NOT one of the three common models used in managing a security training function as described in NIST Special Publication 800-50?
a. Centralized
b. Partially Decentralized
c. Partitioned
d. Fully Decentralized
14. According to NIST SP 800-50, learning is a continuum comprising which of the following elements?
a. Awareness, skill, knowledge
b. Awareness, training, education
c. Training, education, skill
d. Education, awareness, skill
15. NIST SP 800-16, Information Security Training Requirements: A Role- and Performance-Based Model (Draft), defines the following as what type of training?
“Focuses on providing the knowledge, skills, and abilities specific to an individual’s roles and responsibilities relative to information systems. At this level, training recognizes the differences between beginning, intermediate, and advanced skill requirements.”
a. Role-based training
b. Task-oriented training
c. Responsibility training
d. Knowledge and skills training
16. Which one of the following is NOT one of the five phases of the industrial design model described in NIST SP 800-16?
a. Analysis
b. Training
c. Design
d. Evaluation
17. What are the two types of evaluations in the evaluation phase of the industrial design model described in NIST SP 800-16?
a. Formative and summative
b. Formative and intuitive
c. Summative and descriptive
d. Descriptive and formative
1 National Initiative for Cybersecurity Education Strategic Plan (Draft), “Building a Digital Nation,” August 11, 2011.
2 NIST SP 800-50, Building an Information Technology Security Awareness and Training Program, October 2003.
3 NIST Special Publication 800-16 Revision 1, Information Security Training Requirements: A Role- and Performance-Based Model (Draft), March 2009.