![]()
Future Industrial Automation and Control System Approaches and Issues
Chapter 7 emphasized the importance of training to the cybersecurity of industrial automation and control systems. It pointed out sources of that training, identified government and industrial initiatives in promoting security awareness and training, and reviewed effective methodologies for implementing a cybersecurity training program applicable to industrial automation and control systems. Chapter 8 looks into future trends and methodologies that will affect automation and control systems and provides guidelines for taking advantage of these developments.
Automation and Control System Trends
Because industrial automation and control systems are complex, their future characteristics will be affected by advances in a number of domains. These domains include hardware, software, virtualization, storage, mobile devices, cloud computing, communications, HMI, networking, encryption, security, artificial intelligence, standards, and robotics. Advances in these technologies will influence capabilities, performance, reliability, trustworthiness, cost, maintenance, training, and rates of adoption. In addition, increased and more stringent regulatory requirements will require increasing effort and result in higher costs to meet compliance, traceability, environmental, and legal obligations.
Software, hardware, and the control systems that use them will be more adaptable, more secure, more efficient, and self-healing as improvements in these areas are made. Some of the important elements that will characterize future software, hardware, and control systems are summarized in Figures 8-1, 8-2, and 8-3, respectively.
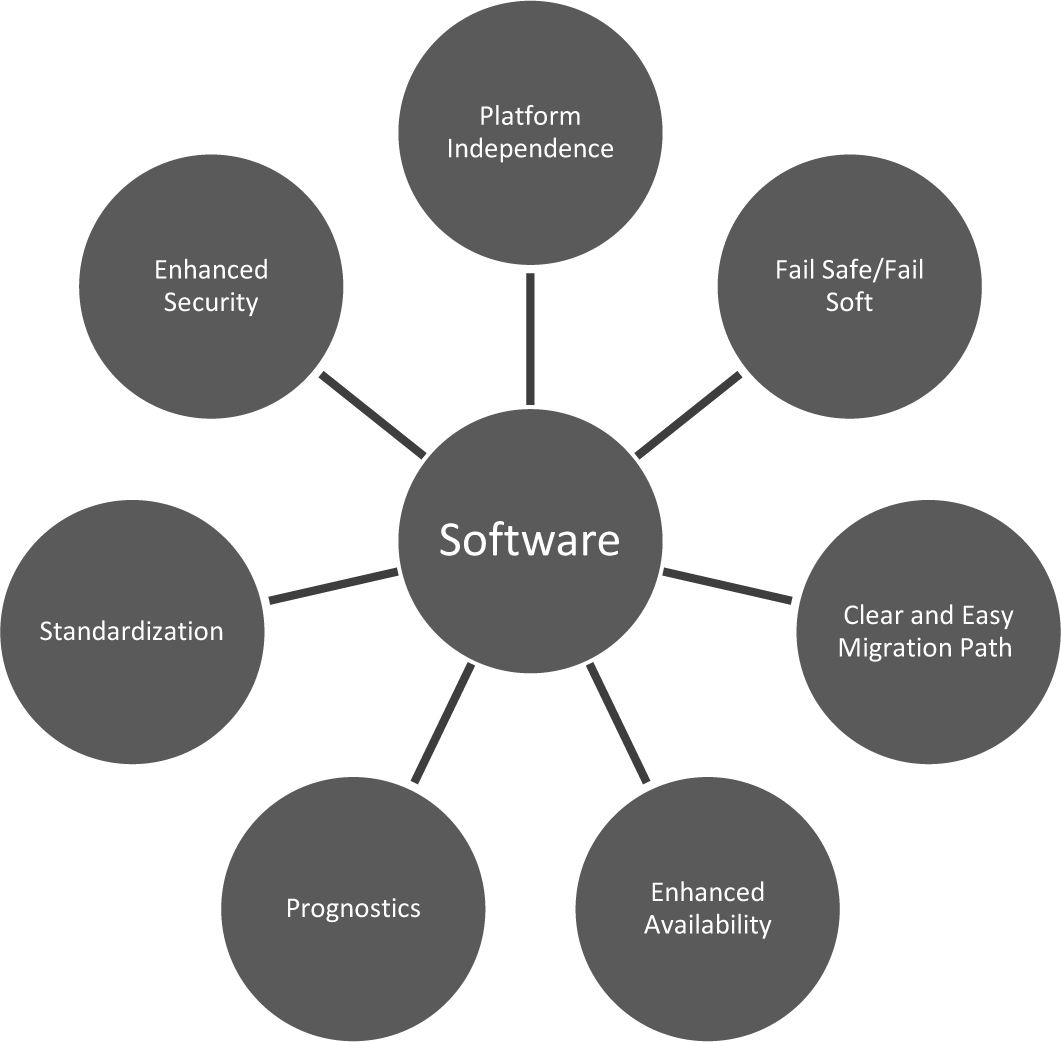
Figure 8-1. Future software characteristics
It is interesting to note that there are some common threads implicit and explicit among these three areas. These commonalities include the following characteristics:
• Adaptive and self-organizing
• Self-diagnosis
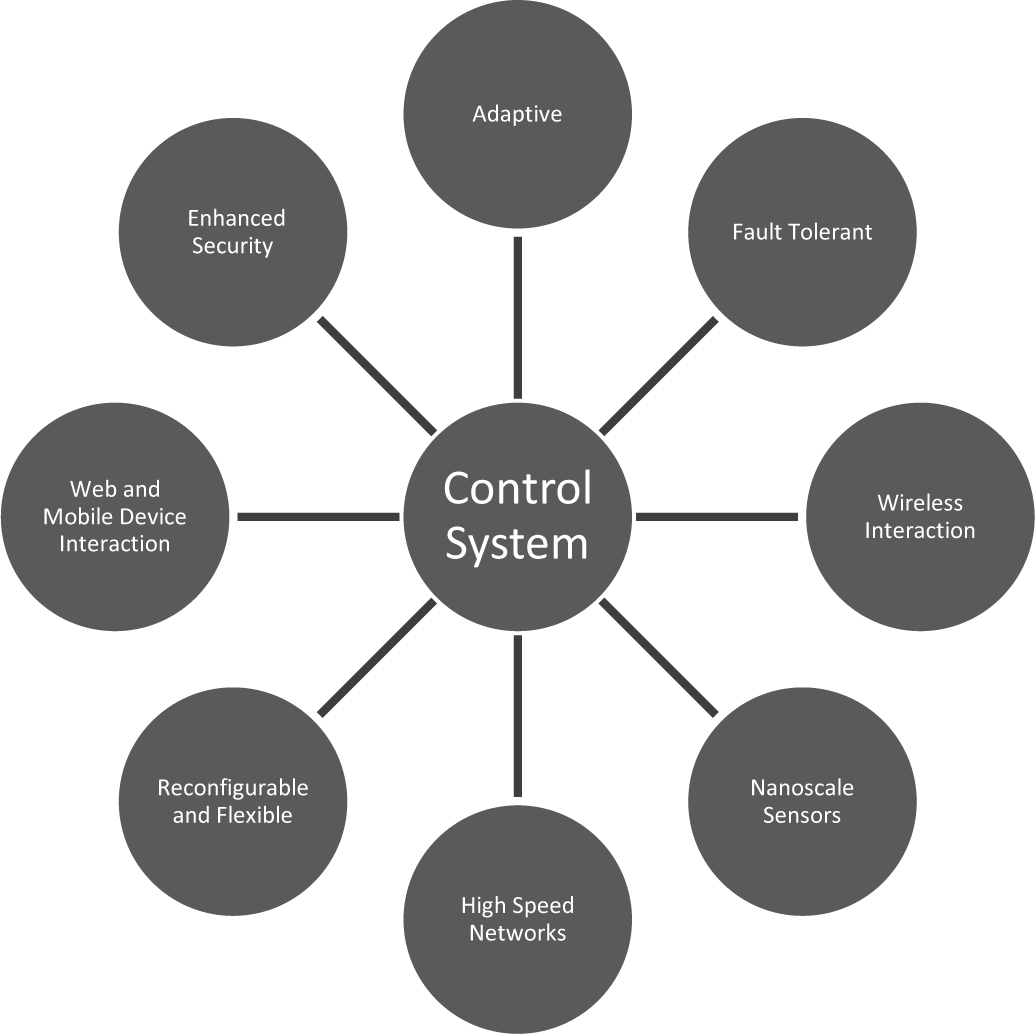
Figure 8-3. Future control system characteristics
• Resilience
• Prognostics
• Enhanced availability
• Intrinsic security
• Availability of and adherence to standards
• Wide use of wireless technology
• Incorporation of Web-based and mobile devices
• Use of self-powered nanotechnology sensors and devices
• Higher-speed processing
• Agent-based (A software agent is a computer program that performs tasks for a user using assumptions based on past behavior or defined preferences.)
• Reconfigurable
In the hardware realm, advances in chip technology will yield higher performance multi-core computing engines using less power than conventional single core designs. Processor workloads can be assigned to those cores with the highest power efficiency and those that are best able to complete the required processing. In addition, cores not needed can be powered down or run at diminished capacity to save energy. In order to take advantage of high performance, multi-core designs, software must be developed to support efficient partitioning of tasks among the cores and not waste the available capabilities of such systems. These capabilities will result in automation systems with faster response times, lower costs, increased computational power, and support for semi-autonomous operation.
The continuous improvement in tablet computers and intuitive HMIs (human-machine interfaces) will provide remote platforms from which to monitor and control processes as well as to conduct maintenance functions. Many of these functions will be performed wirelessly. Correspondingly, wireless security will have to keep pace to reduce or eliminate exposure to threats against mobile devices.
Another technology that will become increasingly important in industrial automation and control systems is virtualization. Virtualization is based on the concept of a virtual machine (VM) running on a physical computing platform under the control of a virtual machine monitor (VMM), known as a hypervisor. Virtualization reduces the effort required to maintain hardware and software systems by eliminating the binding of software to specific hardware platforms through the logical partitioning of physical computing resources into multiple execution environments, including servers, applications, and operating systems. Thus, applications can be centrally managed, and cybersecurity mechanisms can be distributed among virtualization servers, using virtual instances. The control and automation software applications and operating system no longer have to be individually installed and maintained on every client. A typical virtual server can support a variety of client instances on a single hardware platform through protocols, such as the remote desktop protocol (RDP). Additional advantages of virtualization are summarized as follows:
• Alarm management capabilities can be easily implemented to identify critical system situations or system errors.
• Clients can be deleted or added rapidly without affecting plant operation.
• Existing systems can be ported to different hardware platforms with a minimum of effort.
• Software updates can be applied during system operation.
For cloud computing, virtualization provides a level of freedom of choice for the customer and efficiencies and cost savings for cloud providers. The migration to virtualized clouds will, in many instances, be initially through hybrid clouds while customers test and evaluate the cloud paradigm in the context of their own business requirements. As users become accustomed to employing cloud computing, they will embrace the ability to have large numbers of servers available on demand and, conversely, rapidly reducing the number of servers they are using when they are not required. Virtualization, if applied properly, can also result in minimal ramp-up times, reduction of time to develop and market applications, and rapid acquisition or reduction of resources, as requirements vary. Cloud computing was covered in detail in Chapter 4.
Regarding virtualization security, conventional attacks such as denial of service can be used against VMs while other attacks exploit specific VM vulnerabilities. Because multiple VMs share the same physical hardware, a vulnerability in one VM can be exploited to attack other VMs or the host systems. Some of the vulnerabilities of the virtual environment include the following:
• Keystroke logging – Logging of keystrokes and screen updates allows information to be passed across virtual terminals in the VM and written to host files, thus permitting the monitoring of encrypted terminal connections inside the VM
• One VM accessing another VM – Monitoring of one VM by another VM using hacker techniques through a virtual hub or switch
• Shared clipboard technology – Allows data to be transferred between VMs and the host, providing a means of moving data between malicious programs in VMs of different security realms
• Host VM monitoring – Monitoring of network packets coming from or going to a VM by the host enables the host to affect the VM by the following actions and, if the host is compromised, in a negative way:
– Adjusting the number of CPUs, amount of memory, amount and number of virtual disks, and number of virtual network interfaces available to a VM
– Monitoring and configuring resources available to the VMs, including CPU, memory, disk, and network usage of VMs
– Monitoring the applications running inside the VM
– Starting, stopping, pausing, and restarting VMs
– Viewing, copying, and modifying data stored on the VM’s virtual disks
Penetration Testing of Industrial Automation and Control Systems
With more assessment tools and methods for evaluating computer systems and networks being available in general, there will be increased pressure to apply these approaches to industrial automation and control systems in the future. One particularly effective vulnerability assessment method that is widely used and specified in many evaluation paradigms is penetration testing. However, penetration testing of industrial automation and control systems, if not properly conducted, can cause damage to these systems and disrupt operations. The commonly used penetration testing tools create additional traffic on automation and control systems and, if applied to such systems that have limited memory and processing capability, can severely impact their safety and performance. However, if done properly, penetration testing can provide valuable insight into the security posture of industrial automation and control systems.
Some useful guidelines for conducting penetration testing on automation and control systems are:
• Document and understand the automation/control system configuration to identify areas of high risk
• Identify all routes of access to the automation/control system from outside elements, including the corporate network
• Where possible, conduct testing on independent test systems in a controlled laboratory setting
• In laboratory test systems, ensure that intrusion detecting systems and firewall configurations are duplicates of those in the production system
• Evaluate testing procedures and approaches in a laboratory test setting before applying them to online production systems
• Understand the proper operation of the automation/control system to be tested in order to more effectively identify the results of attack scenarios
• Conduct testing on redundant automation/control system components
• Use passive data collection techniques when possible
• Be cognizant of risks when conducting testing on active, operational systems, and have recovery procedures in place in the event of a system failure caused by the testing
• Conduct penetration testing from computers external to the network to simulate an attacker’s approach
A penetration test is usually conducted with no prior knowledge of the automation/control system, that is, with a “black box” approach. Penetration testing begins with a reconnaissance phase comprising the following steps:
• Footprinting – Gathering information about the target automation/control network in order to develop a mapping of the network and associated systems
• Scanning – Conducting a scan of the network to discover applications and open ports, services running on ports, and information about the operating system
• Enumerating – Using the results of the scanning phase to develop a complete map of the network, discover vulnerable resources, and identify valid user accounts
Following reconnaissance, the network can be assessed for vulnerabilities by acquiring access to the automation/control system. If an attack was launched on the system, the acquiring access phase is where the actual attack is implemented. In this phase, an attacker could access the operating system and network, obtain higher-level system privileges, launch buffer overflow and denial of service attacks, and insert viruses and Trojan horses.
Some of the common assessment tools used in penetration testing include Nmap, Metasploit, Nessus, STAT Scanner, Wireshark, Ettercap, and software debuggers.
Formal Methods Used to Quantify and Standardize Important Concepts and Applications
In many fields, as advances occur, formal methods evolve to quantify and standardize important concepts and applications. Three such methods that can be applied to industrial automation and control systems are information security continuous monitoring (ISCM), the Smart Grid maturity model (SGMM), and the automation maturity model (AMM).
ISCM Strategy
NIST SP 800-1371, Information Security Continuous Monitoring (ISCM) for Federal Information Systems and Organizations, defines the process for developing an ISCM strategy and implementing an ISCM program. ISCM is defined as “maintaining ongoing awareness of information security, vulnerabilities, and threats to support organizational risk management decisions.”
ISCM comprises the following steps:
1. Define an ISCM strategy based on risk tolerance that maintains clear visibility into assets, awareness of vulnerabilities, up-to-date threat information, and mission/business impacts.
2. Establish an ISCM program, determining metrics, status monitoring frequencies, control assessment frequencies, and an ISCM technical architecture.
3. Implement an ISCM program and collect the security-related information required for metrics, assessments, and reporting. Automate collection, analysis, and reporting of data where possible.
4. Analyze the data collected and report findings, determining the appropriate response. It may be necessary to collect additional information to clarify or supplement existing monitoring data.
5. Respond to findings with technical, management, and operational mitigating activities or acceptance, transference/sharing, or avoidance/rejection.
6. Review and Update the monitoring program, adjusting the ISCM strategy and maturing measurement capabilities to increase visibility into assets and awareness of vulnerabilities, further enable data-driven control of the security of an organization’s information infrastructure, and increase organizational resilience.
The ISCM process is depicted in Figure 8-4.
In the ISCM process, the status of automation security in a facility can be determined by establishing appropriate metrics. The metrics are defined through the following activities:
• Maintaining an understanding of threats and threat activities
• Assessing all security controls
• Collecting, correlating, and analyzing security-related information
• Providing actionable communication of security status across all tiers of the organization
• Active management of risk by organizational officials
Figure 8-4. The ISCM Process
[Source: NIST SP 800–137, Information Security Continuous Monitoring (ISCM) for Federal Information Systems and Organizations, September, 2011.]
NIST SP 800-137 defines the process for managing information security and information system-related risk as the risk management framework (RMF). The RMF integrates information system security and risk management activities as illustrated in Figure 8-5. It applies equally well to both automation and control systems and information systems.
The frequency of monitoring security controls for effectiveness and relevance is a function of the following criteria as presented in NIST 800-137:
• Security control volatility – Security control volatility is a measure of how frequently a control is likely to change over time subsequent to its implementation. Volatile security controls are assessed more frequently, whether the objective is establishing security control effectiveness or supporting calculation of a metric.
• System categorizations/impact levels – In general, security controls implemented on systems that are categorized as high-impact are monitored more frequently than controls implemented on moderate-impact systems, which are in turn monitored more frequently than controls implemented on low-impact systems.
• Security controls or specific assessment objects providing critical functions – Security controls or assessment objects that provide critical security functions (e.g., log management servers, firewalls) are candidates for more frequent monitoring.
• Security controls with identified weaknesses – Existing risks documented in security assessment reports are considered for more frequent monitoring to ensure that risks stay within tolerance.
• Organizational risk tolerance – Organizations with a low tolerance for risk (e.g., organizations that process, store, or transmit large amounts of proprietary and/or personally identifiable information [PII], organizations with numerous high-impact systems, organizations facing specific persistent threats) monitor more frequently than organizations with a higher tolerance for risk.
• Threat information – Organizations consider current credible threat information, including known exploits and attack patterns when establishing monitoring frequencies. For instance, if a specific attack is developed that exploits a vulnerability of an implemented technology, temporary or permanent increases to the monitoring frequencies for related controls or metrics may help provide protection from the threat.
• Vulnerability information – Organizations consider current vulnerability information with respect to technology products when establishing monitoring frequencies. For instance, if a specific product manufacturer provides software patches monthly, an organization might consider conducting vulnerability scans on that product at least that often.
• Risk assessment results – Results from organizational and/or system-specific assessments of risk (either formal or informal) are examined and taken into consideration when establishing monitoring frequencies. For instance, if a system-specific risk assessment identifies potential threats and vulnerabilities related to nonlocal maintenance (NIST SP 800-53, MA-4), the organization considers more frequent monitoring of the records kept on nonlocal maintenance and diagnostic activities.
• Reporting requirements - Reporting requirements do not drive the ISCM strategy but may play a role in the frequency of monitoring.
Figure 8-5. The Risk Management Framework
[Source: NIST SP 8GG-137, Information Security Continuous Monitoring (ISCM) for Federal Information Systems and Organizations, September, 2G11.]
The ISCM process Respond step conducts a response to findings with technical, management, and operational mitigating activities or acceptance, transference/sharing, or avoidance/rejection. In accordance with NIST SP 800-137, the Respond activity mitigation recommendations are developed using the security automation domain concepts presented in Appendix D of NIST SP 800-137. Note that the usage of the term “security automation domain” in the ISCM process is not the same as “automation and control system security” as conventionally used. Appendix D defines a security automation domain as “an information security area that includes a grouping of tools, technologies, and data. Data within the domains is captured, correlated, analyzed, and reported to present the security status of the organization that is represented by the domains monitored.” The 11 security automation domains that support continuous monitoring and that are used to categorize the remediation recommendations are illustrated in Figure 8-6.
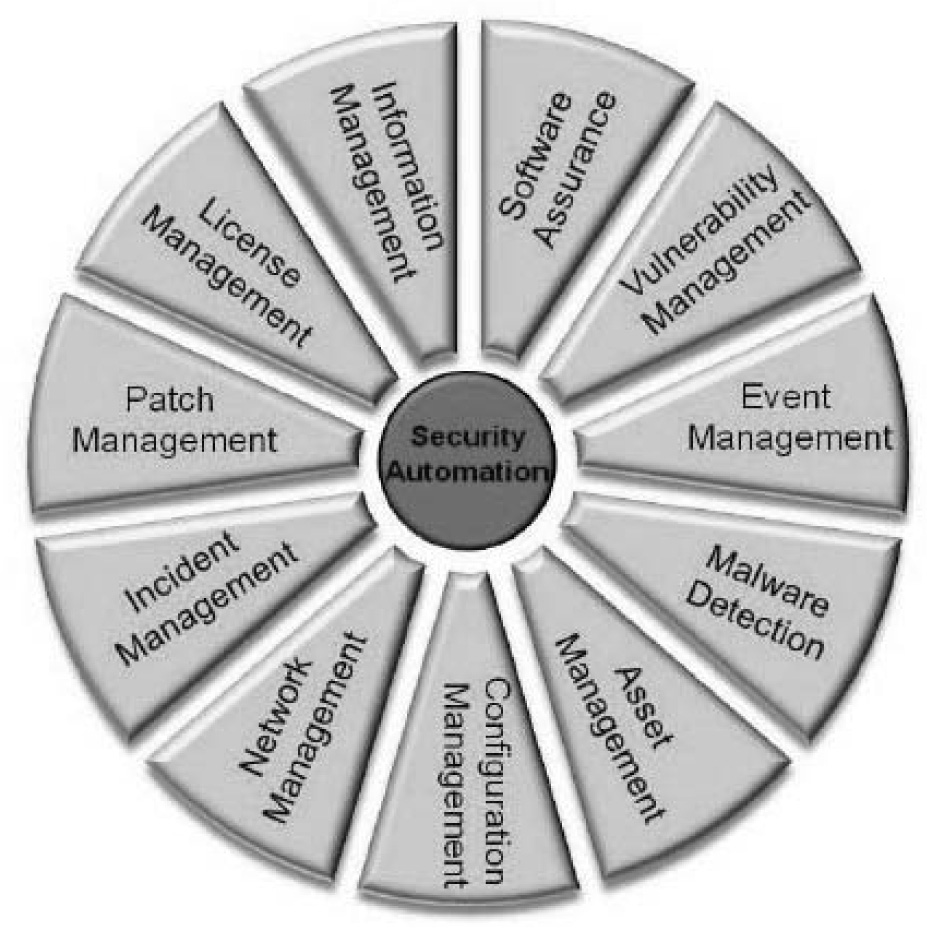
Figure 8-6. The Security Automation Domains
[Source: NIST SP 800-137, Information Security Continuous Monitoring (ISCM) for Federal Information Systems and Organizations, September, 2011.]
Appendix D recommends sets of NIST SP 800-53 security controls that are applicable to the security automation domains. These controls are given in Table 8-1.
Table 8-1. NIST SP 800-53 Security Controls Applicable to Security Automation Domains
|
Security Automation Domain |
Controls |
|
Vulnerability Management and Patch Management |
SI-2, Flaw Remediation; CA-2, Security Assessments; CA-7, Continuous Monitoring; CM-3, Configuration Change Control; IR-4, Incident Handling; IR-5, Incident Monitoring; MA-2, Controlled Maintenance; RA-5, Vulnerability Scanning; SA-11, Developer Security Testing; and SI-11, Error Handling. |
|
Event Management and Incident Management |
AU-2, Auditable Events; AU-3, Content of Audit Records; AU-4, Audit Storage Capacity; AU-5, Response to Audit Processing Failures; AU-6, Audit Review, Analysis, and Reporting; AU-7, Audit Reduction and Report Generation; AU-8, Time Stamps; AU-12, Audit Generation; CA-2, Security Assessments; CA-7, Continuous Monitoring; IR-5, Incident Monitoring; RA-3, Risk Assessment; and SI-4, Information system Monitoring. |
|
Malware Detection |
CA-2, Security Assessments; CA-7, Continuous Monitoring; IR-5, Incident Monitoring; RA-3, Risk Assessment; SA-12, Supply Chain Protection; SA-13, Trustworthiness; SI-3, Malicious Code Protection; SI-4, Information System Monitoring; SI-7, Software and Information Integrity; and SI-8, Spam Protection. |
|
Asset Management |
CA-7, Continuous Monitoring; CM-2, Baseline Configuration; CM-3, Configuration Change Control; CM-4, Security Impact Analysis; CM-8, Information System Component Inventory; and SA-10, Developer Configuration Management. |
|
Configuration Management |
AC-2, Account Management; AC-3, Access Enforcement; AC-5, Separation of Duties; AC-7, Unsuccessful Login Attempts; AC-9, Previous Logon (Access) Notification; AC-10, Concurrent Session Control; AC-11, Session Lock; AC-19, Access Control for Mobile Devices; AC-20, Use of External Information Systems; AC-22, Publicly Accessible Content; CA-2, Security Assessments; CA-7, Continuous Monitoring; CM-2, Baseline Configuration; CM-3, Configuration Change Control; CM-5, Access Restrictions for Change; CM-6, Configuration Settings; CM-7, Least Functionality; IA-2, Identification and Authentication (Organizational Users); IA-3, Device Identification and Authentication; IA-4, Identifier Management; IA-5, Authenticator Management; IA-8, Identification and Authentication (Non-Organizational Users); IR-5, Incident Monitoring; MA-5, Maintenance Personnel; PE-3, Physical Access Control; RA-3, Risk Assessment; SA-7, User Installed Software; SA-10, Developer Configuration Management; and SI-2, Flaw Remediation. |
|
AC-4, Information Flow Enforcement; AC-17, Remote Access; AC-18, Wireless Access; CA-7, Continuous Monitoring; CM-2, Baseline Configuration; CM-3, Configuration Change Control; CM-4, Security Impact Analysis; CM-6, Configuration Settings; CM-8, Information System Component Inventory; SC-2, Application Partitioning; SC-5, Denial of Service Protection; SC-7, Boundary Protection; SC-10, Network Disconnect; SC-32, Information System Partitioning; and SI-4, Information System Monitoring. |
|
|
License Management |
CA-7, Continuous Monitoring; CM-8, Information System Component Inventory; and SA-6, Software Usage Restrictions. |
|
Information Management |
AC-4, Information Flow Enforcement; AC-17, Remote Access; CA-3, Information System Connections; CA-7, Continuous Monitoring; CM-7, Least Functionality; SC-9, Transmission Confidentiality; and SI-12, Information Output Handling and Retention. |
|
Software Assurance |
CA-7, Continuous Monitoring; SA-4, Acquisitions; SA-8, Security Engineering Principles; SA-11, Developer Security Testing; SA-12, Supply Chain Protection; SA-13, Trustworthiness; SA-14, Critical Information System Components; and SI-13, Predictable Failure Prevention. |
|
[Source: NIST SP 800-137, Information Security Continuous Monitoring (ISCM) for Federal Information Systems and Organizations, September, 2011.] |
|
The Smart Grid Maturity Model (SGMM)
The Smart Grid maturity model (SGMM)2 was initially developed by electric power utilities and is now maintained by the Carnegie Mellon University Software Engineering Institute (SEI). As stated in the SGMM definition document, “The model provides a framework for understanding the current state of Smart Grid deployment and capability within an electric utility and provides a context for establishing future strategies and work plans as they pertain to Smart Grid implementations.” Even though the model is focused on the Smart Grid, its fundamental principles and concepts are applicable and extendable to automation systems.
The SEI provides a suite of SGMM product components to support the model as follows:
1. Smart Grid Maturity Model Definition – The formal description of the model that includes an overview of the model architecture and is the basis for the other product suite elements.
2. Smart Grid Maturity Model Matrix – A summary of the expected characteristics contained in the model in a tabular format.
3. Smart Grid Maturity Model Compass Assessment – Survey for completion by or on behalf of utilities. Compass questions are designed to collect demographic and performance data and to characterize the status of the responding utility’s Smart Grid implementation in the context of the SGMM.
4. Smart Grid Maturity Model Navigator Process – Process developed to help organizations chart a technical, organizational, and operational path through their grid modernization effort.
5. Smart Grid Maturity Model Training – Two courses that support the transition and use of the SGMM.
The scope of the SGMM is illustrated in Figure 8-7:
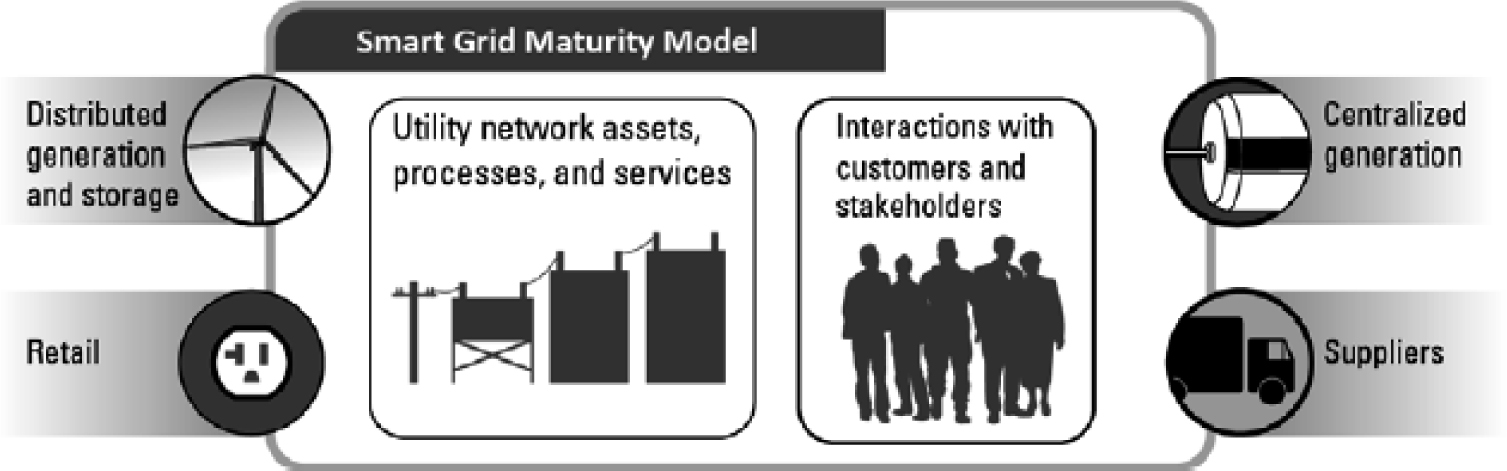
Figure 8-7. The scope of the SGMM
[Source: The Smart Grid Maturity Model, SGMM Model Definition, A framework for Smart Grid transformation, Technical Report CMU/SEI-2011-TR-025, Version 1.2, September 2011.]
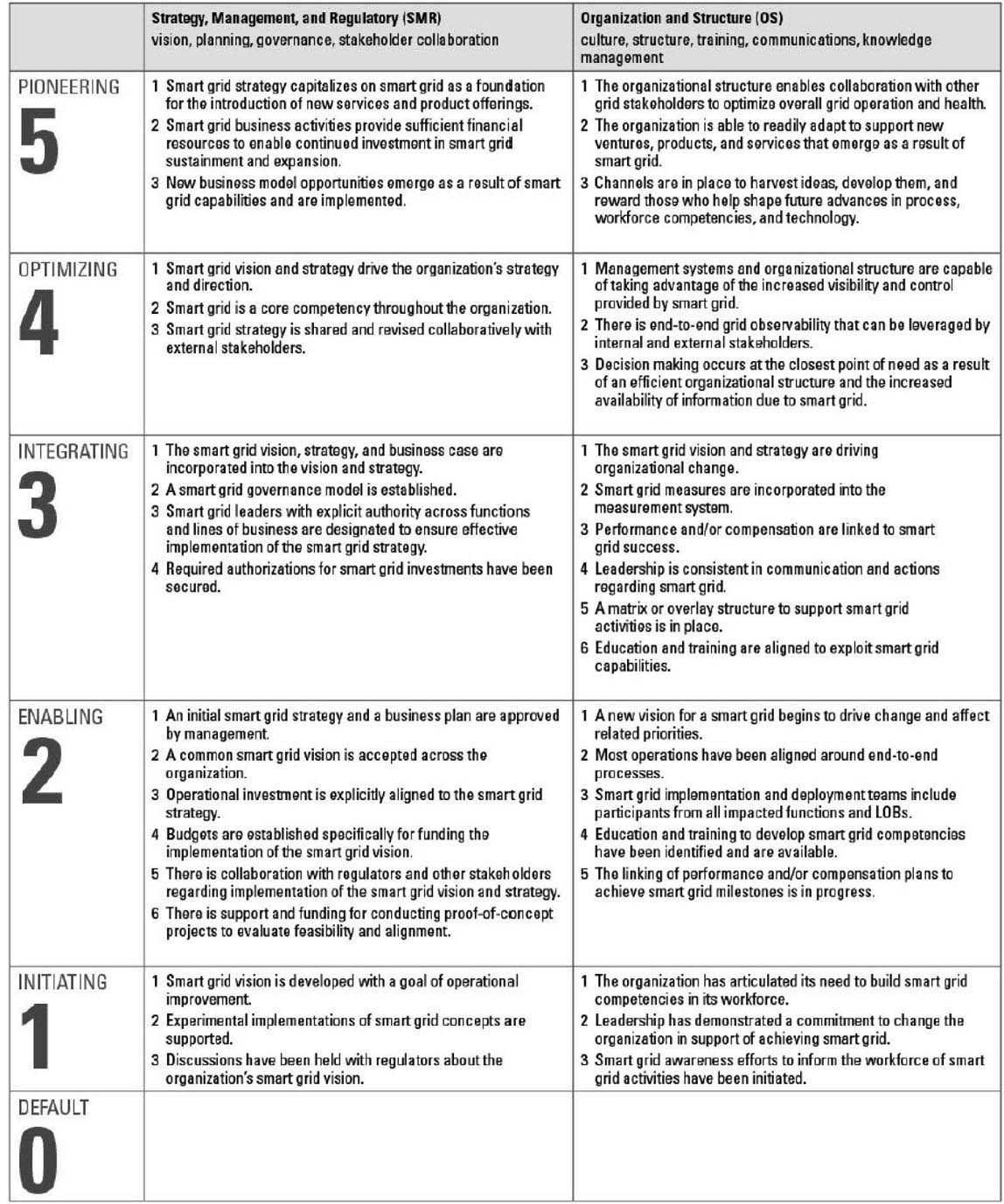
The model comprises eight domains with each domain having six defined levels of maturity, ranging from Level 0 (lowest) to Level 5 (highest). The model defines a domain as “a logical grouping of Smart Grid characteristics” with each characteristic comprising “a concise, declarative statement to support the consistent evaluation of its implementation and its independence from other characteristics at the same level within the model. The model also requires that for a given level of maturity to be achieved, the expected characteristics for that level and all lower levels in that domain must be sufficiently implemented.” The eight domains of the SGMM are listed as follows:
1. Strategy, Management, and Regulatory (SMR) – Represents the capabilities and characteristics that enable an organization to successfully develop a Smart Grid vision and strategy, establish internal governance and management processes, and promote collaborative relationships with stakeholders to implement that strategy and vision.
2. Organization and Structure (OS) – Represents the organizational capabilities and characteristics that enable an organization to align and operate as required to achieve its desired Smart Grid transformation.
3. Grid Operations (GO) – Represents the organizational capabilities and characteristics that support the reliable, secure, safe, and efficient operation of the electrical grid.
4. Work and Asset Management (WAM) – Represents the organizational capabilities and characteristics that support the optimal management of assets and workforce resources (i.e., people and equipment) that are central to meeting Smart Grid goals.
5. Technology (TECH) – Represents the organizational capabilities and characteristics that enable effective strategic technology planning for Smart Grid capabilities and the establishment of rigorous engineering and business processes for the evaluation, acquisition, integration, and testing of new Smart Grid technology.
6. Customer (CUST) – Represents the organizational capabilities and characteristics that enable customer participation toward achieving the benefits of the Smart Grid transformation.
7. Value Chain Integration (VCI) – Represents the organizational capabilities and characteristics that underlie an electric utility’s ability to achieve its Smart Grid goals by successfully managing the utility’s organizational interdependencies with both the supply chain for the production of electricity and the demand chain for its delivery.
8. Societal and Environmental (SE) – Represents the organizational capabilities and characteristics that enable an organization to contribute to achieving societal goals regarding the reliability, safety, and security of our electric power infrastructure, the quantity and sources of the energy we use, and the impact of the infrastructure and our energy use on the environment and our quality of life.
An SGMM compass assessment provides an organization with a maturity rating for each of the model’s eight domains. The model states that “the six levels of maturity represent defined stages of an organization’s progress toward achieving its Smart Grid vision in terms of automation, efficiency, reliability, energy and cost savings, integration of alternative energy sources, improved customer interaction, and access to new business opportunities and markets.” The maturity levels are hierarchical in that an organization must reach a Level 1 before progressing to the next levels in sequence. The levels of maturity within each domain are described by a group of expected characteristics and a group of optional informative characteristics.
Expected characteristics are defined as “the capabilities and characteristics that an organization must implement or exhibit to achieve the corresponding maturity level within a domain. Each expected characteristic is presented as a concise, declarative statement to support the consistent evaluation of its implementation and its independence from other characteristics at the same level within the model.” Informative characteristics give an additional perspective that provides information concerning whether an organization has achieved a given level of maturity within a domain.
The six maturity levels defined in the SGMM, which are stages of an organization’s progress toward achieving its Smart Grid vision, are summarized in Figure 8-8.
The characteristics of each maturity level are summarized as follows:
• Level 0: Default – The default or entry level of the model across the eight domains of utility. This level precedes an organization’s taking significant initial steps toward the adoption of Smart Grid technology.
• Level 1: Initiating – This level denotes that an organization is taking the first implementation steps toward a Smart Grid within a domain.
• Level 2: Enabling – Level 2 focuses on implementing features that will enable an organization to achieve and sustain grid modernization.
• Level 3: Integrating – Level 3 Smart Grid deployments are being integrated across the organization.
• Level 4: Optimizing – At Level 4, Smart Grid implementations within a given domain are being fine-tuned and used to further increase organizational performance.
• Level 5: Pioneering – Organizations at Level 5 are achieving new results with a given domain and advancing the state of the practice.
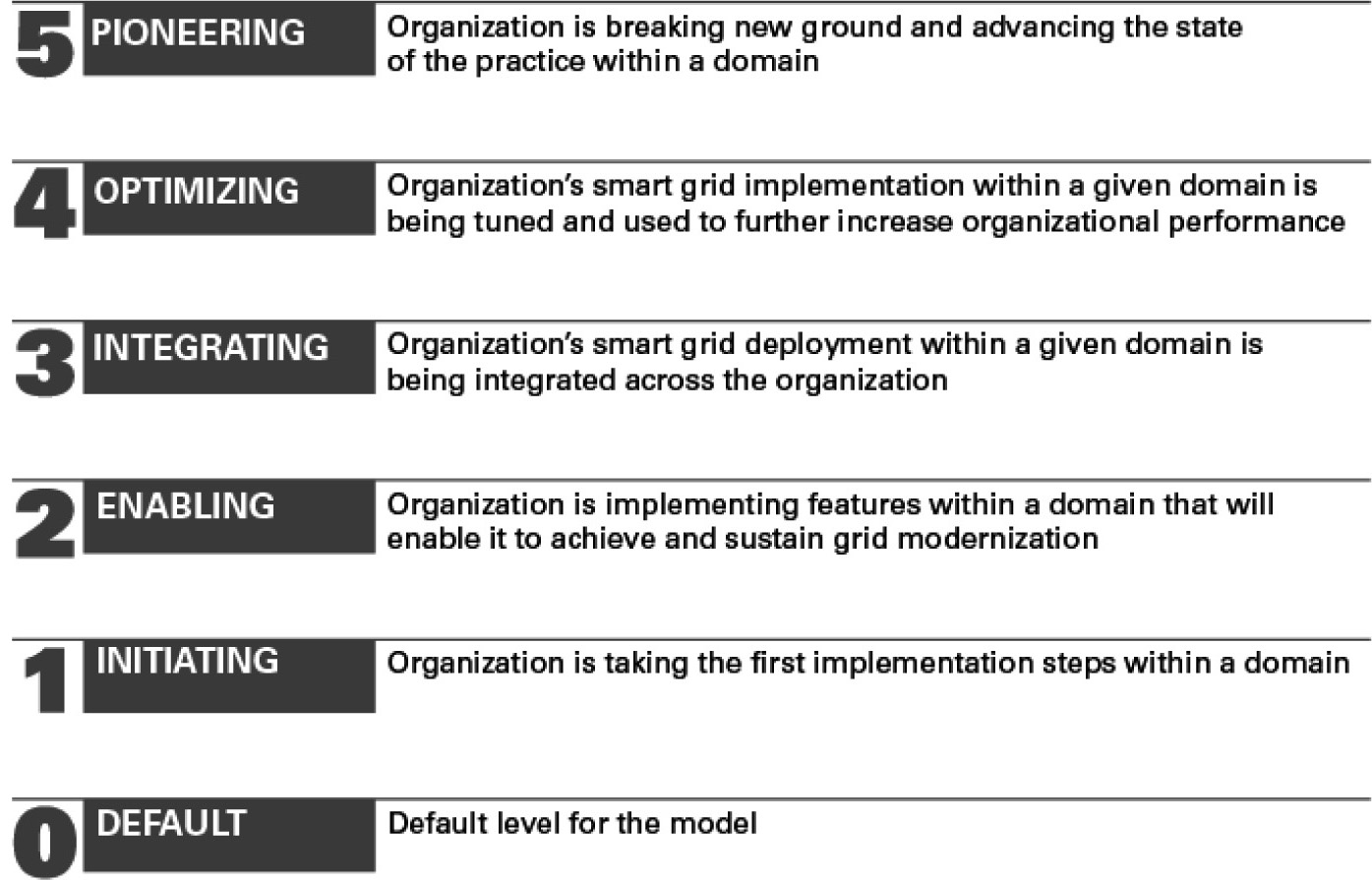
Figure 8-8. The SGMM maturity levels
[Source: The Smart Grid Maturity Model, SGMM Model Definition, A framework for Smart Grid transformation, Technical Report CMU/SEI-2011-TR-025, Version 1.2, September 2011.]
The maturity rating for each domain in an organization is determined by the SGMM Compass survey, which comprises both domain-specific and organizational attribute questions. A typical domain maturity profile determined by a SGMM assessment is shown in Figure 8-9.

Figure 8-9. Typical SGMM maturity profile
[Source: The Smart Grid Maturity Model, SGMM Model Definition, A framework for Smart Grid transformation, Technical Report CMU/SEI-2011-TR-025, Version 1.2, September 2011.]
The Smart Grid Maturity Model Matrix
The SGMM Matrix document provides a tabular instantiation of the SGMM model for easy reference. It is presented in Table 8-2.
Automation Maturity Model
In a publication6 by the California-Nevada Section of the American Water Works Association (AWWA), Philip Gaberdiel6 of Westin Engineering proposed an Automation Maturity Model™ (AMM) to measure the capability of an organization’s industrial automation and control system. The capability implies an increasing level of automation system security, also. The model defines the following six maturity levels of an automation system:
• Level 0 – Local hardwired control
• Level 1 – Local digital control
• Level 2 – Remote manual control
• Level 3 – Remote auto control
• Level 4 – Enhanced operations
• Level 5 – Optimized operations
The Automation Maturity Model is illustrated in Figure 8-10.
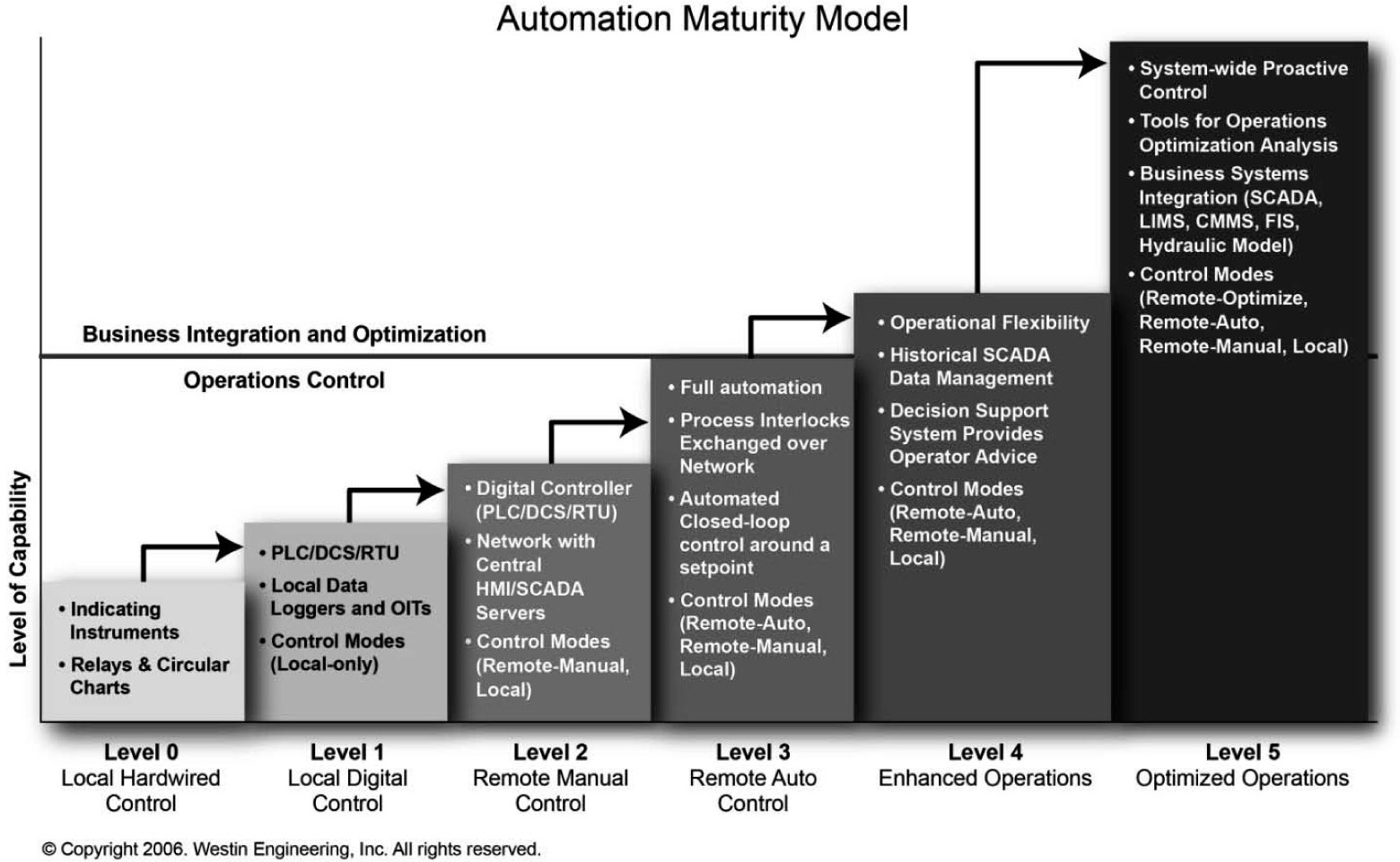
Figure 8-10. The Automation Maturity Model (AMM)
[Source: Phil Gaberdiel, Westin Engineering]
In the model, an automation system at Level 0 is based on relays and instruments read locally, comprising hardware control. Level 1 describes an automation system with local digital control, using PLCs, RTUs, and data loggers, while Level 2 comprises digital controllers and networked HMI/SCADA servers providing remote manual control. A Level 3 remote auto control system includes full automation with automated closed loop controls. Level 4, enhanced operations, has characteristics of operational flexibility, application of decision support systems, and historical SCADA data management. Level 5 achieves optimized operation through the use of operations optimization analysis tools, business systems integration, and systems-wide, proactive control.
Future Smart Grid Issues and Automation Security Issues
Because of the increased number of computational components and sensors that are associated with manufacturing systems, processing plants, and the Smart Grid, the electromagnetic environment will be of increased concern in the future. Even though the following material provides examples relating to the Smart Grid, the issues and countermeasures apply equally to automation systems.
In addition government/industry initiatives such as NIST 7628 are emerging to address future specific Smart Grid cybersecurity and privacy issues. These two areas are explored in the following sections.
Smart Grid Electromagnetic Radiation Issues
As discussed in Chapter 5, electromagnetic fields have the potential of causing serious interruptions and malfunctions not only in substations, but in “green” energy sources and production facilities. Additional interference that can affect sensitive instrumentation and home-based devices will be present from the increased number of transmitting stations.
In a paper titled High Power Electromagnetic (HPEM) Threats to the Smart Grid 3, William Radasky describes ongoing efforts to understand and mitigate the effects of electromagnetic radiation on future instantiations of the Smart Grid. Toward this end, an Electromagnetic Interoperability Issues Working Group (EMIIWG) was formed in 2010. The EMIIWG is a subgroup of the Smart Grid Interoperability Panel (SGIP), which was established to investigate the interoperability among interconnected components of the Smart Grid. The paper describes the scope of the EMIIWG as addressing the following issues:
• Enhancing the immunity of Smart Grid devices and systems to the detrimental effects of natural and man-made electromagnetic interference, both radiated and conducted.
• Developing recommendations for the application of standards and testing criteria to ensure electromagnetic compatibility (EMC) for the Smart Grid, with a particular focus on issues directly related to interoperability of Smart Grid devices and systems.
• Determining impacts, avoidance, generation and mitigation of and immunity to electromagnetic interference.
Specific tasks of the EMIIWG associated with these areas of concern include:
1. Review potential electromagnetic issues and the existing state of EMC of the power grid and associated systems, including current and proposed Smart Grid enhancements.
2. Segment the Smart Grid devices and systems and electromagnetic environments into a minimal set of categories for which electromagnetic issues and EMC requirements can be identified. These categories should be compatible with the environment classifications of IEC 61000-2-54, where possible.
3. Prioritize or rank the categories in (2) according to the potential impact on Smart Grid reliability. The priorities should consider the extent and severity of possible failures and the availability requirements for the relevant interface as defined in NISTIR 76285 (see discussion of NIST 7628 in next section).
4. Identify and/or propose EMC terminology and definitions applicable to the Smart Grid and compatible with international standards.
5. Identify and compile the source-victim matrix for each category identified in (2).
6. Identify or develop EMC performance metrics for systems in each category identified in (2).
7. Identify appropriate EMC standards and requirements to meet performance metrics.
8. Identify areas where EMC standards are not available and identify appropriate standards development organizations (SDO)s where such standards should be developed.
9. Identify and propose priority action plans to address standards or guidelines in high-priority categories if needed.
10. Propose strategic recommendations for EMC of Smart Grid systems, beginning with the highest priority categories. These recommendations should reflect a long-term strategy to maintain EMC as the Smart Grid evolves.
11. Consider the need, and if appropriate, the nature of a conformity assessment program for EMC for coordination with the SGIP Smart Grid Testing and Certification Committee.
A critical task in the above list is task 2, which is basic to the determination of the appropriate EM environment for Smart Grid equipment, which is supported by IEC 61000-2-5. The paper High Power Electromagnetic (HPEM) Threats to the Smart Grid, describes the process steps of IEC 61000-2-5 as the following:
1. Define the location classes with regard to the types of exposures (both conducted and radiated) and the distances expected from particular types of emitters.
2. Compile a comprehensive list of radiated and conducted phenomena and disturbance levels along with formulas to compute field levels where appropriate (include formulas for near-field exposure).
3. Combine the results to develop recommendations for disturbance levels for a given “location” for all applicable phenomena.
Related and important guidance documents that will affect the future characteristics of the Smart Grid as well as industrial control systems are NIST Interagency or Internal Reports (NISTIRs), particularly those of NISTIR 7628, cited earlier in this chapter.
NIST 7628
NIST 7628, Introduction to NISTIR 7628 Guidelines for Smart Grid Cybersecurity, is a three-volume document that provides a methodical approach to implementing customized cybersecurity and privacy protection strategies for Smart Grid implementations. It was developed by the Cybersecurity Working Group of the Smart Grid Interoperability Panel and is designed to apply to a variety of Smart Grid–related domains, such as electric vehicle charging stations, utilities, manufacturers, and providers of energy management services. Its approach is also directly applicable to process plants, manufacturing operations, and automation systems, in general. It brings together techniques from information system security, information technology, control systems, telecommunications, and manufacturing.
Volume 1 of NIST 7628 addresses the following topics:
• Risk assessment processes to identify high-level security requirements
• High-level architectures
• Logical interface architectures used to identify and define categories of interfaces within and across the Smart Grid domains
• High-level security requirements for the logical interface categories
• Technical cryptographic and key management issues across the scope of Smart Grid systems and devices
Volume II deals with privacy issues in homes and electric vehicles, including:
• Evolving Smart Grid technologies and their relationships with individuals
• Behaviors of groups of individuals and individuals in their dwellings
• Behaviors of groups of individuals and individuals in electric vehicles
• Privacy issues affecting individuals in their premises and electric vehicles
• Recommended privacy practices for participants within the Smart Grid
• Recommendations to consumers involving Smart Grid privacy issues and associated mitigation approaches
Volume III of NIST 7628 is an examination of Smart Grid high-level security requirements, such as:
• Vulnerability categories
• Research and development topics focused on achieving increased security and resilience characteristics for the Smart Grid
• Description of the Cybersecurity Working Group (CSWG) effort to support the evaluation of proposed standards relative to the security needs developed in NIST 7628
The future environment of industrial automation and control systems will be affected by advances in a number of related and seemingly unrelated fields. Breakthroughs in physics, semiconductors, software engineering, artificial intelligence, communications, information technology, and so on will translate into opportunities and challenges in automation and control systems. No longer can technical personnel rely on narrow control disciplines and ignore the wider technological community if they want to take advantage of progress in those arenas.
In this book, a number of proven, effective techniques have been presented and explored with the goal of providing the management and technical personnel associated with industrial automation and control systems the background and tools to significantly affect the security of our critical automation systems. These methodologies must be embraced and coupled with the latest technological knowledge in order to maximize the security and efficiency of tomorrow’s automation and control systems.
Review Questions for Chapter 8
1. The technology that eliminates the binding of software to specific hardware platforms is known as which of the following?
a. Artificial intelligence
b. Virtualization
c. Cloud computing
d. Software as a service
2. A hypervisor is which of the following?
a. A virtual machine monitor
b. An advanced HMI
c. A manager
d. An alarm mechanism
3. NIST SP 800-137, Information Security Continuous Monitoring (ISCM) for Federal Information Systems and Organizations, defines the process for developing an ISCM strategy and implementing an ISCM program. Which one of the following best describes the ISCM strategy?
a. Providing security mechanisms to reduce risks to automation systems
b. Developing security policies to specify management intent for information systems and automation systems
c. Maintaining ongoing awareness of information security, vulnerabilities, and threats to support organizational risk management decisions
d. Maintaining ongoing awareness of risk mitigation alternatives
4. Which of the following is NOT one of the ISCM program steps?
a. Define
b. Establish
c. Respond
d. Mitigate
5. In the ISCM process, the status of automation security in a facility can be determined by establishing appropriate metrics. Which of the following activities is NOT used to define the metrics?
a. Evaluating applicable mitigation approaches
b. Assessing all security controls
c. Providing actionable communication of security status across all tiers of the organization
d. Collecting, correlating, and analyzing security-related information
6. NIST SP 800-137 defines the process for managing information security and information system–related risk as which of the following?
a. Risk Management Framework (RMF)
b. Risk-Impact Criteria (RIC)
c. Vulnerability Analysis (VA)
d. Risk-Vulnerability Matrix (RVM)
7. Security control volatility, system categorizations/impact levels, organizational risk tolerance, and security controls with identified weaknesses are associated with what characteristic discussed in NIST 800-137?
a. The necessity of adding compensating controls
b. The risk impact levels
c. The level of risk
d. The frequency of monitoring security controls for effectiveness
8. Appendix D of NIST SP 800-137 defines a term as “an information security area that includes a grouping of tools, technologies, and data.” What is this term?
a. Security automation domain
b. Compensating domain
c. Risk management domain
d. Risk mitigation domain
9. The SEI-maintained Smart Grid Maturity Model (SGMM) is described best by which of the following statements?
a. Provides a framework for understanding the current state of Smart Grid deployment and capability within an electric utility and provides a context for establishing future strategies and work plans as they pertain to Smart Grid implementations
b. Provides a management perspective of Smart Grid deployment and capability within an electric utility and develops guidelines for Smart Grid implementations
c. Provides a targeted hierarchical methodology applicable to Smart Grid evaluation and maintenance within an electric utility and provides a basis for implementing effective Smart Grid controls
d. Provides a Smart Grid assurance model and algorithms for future deployment and implementation of Smart Grid systems
10. Which of the following is NOT one of the eight domains of the SGMM?
a. Strategy, Management, and Regulatory (SMR)
b. Organization and Structure (OS)
c. Metering and Monitoring (MAM)
d. Work and Asset Management (WAM)
11. Which of the following is NOT one of the six maturity levels defined in the SGMM?
a. Default
b. Evaluating
c. Initiating
d. Integrating
12. The SGMM maturity rating for each domain in an organization is determined by which of the following means?
a. The SGMM Domain survey
b. The SGMM Risk survey
c. The SGMM Level survey
d. The SGMM Compass survey
13. NIST 7628, Introduction to NISTIR 7628 Guidelines for Smart Grid Cybersecurity, is a three-volume document that provides a methodical approach to implementing customized cybersecurity and privacy protection strategies for Smart Grid implementations. Which of the following areas is NOT addressed in the volumes comprising NISTIR 7628?
a. Risk assessment processes
b. Privacy issues
c. Cost evaluation matrices
d. Research and development topics
14. Which of the following describes the optimizing level (Level 4) of the SGMM?
a. Focuses on implementing features that will enable an organization to achieve and sustain grid modernization
b. Smart Grid implementations within a given domain are being fine-tuned and used to further increase organizational performance
c. Smart Grid deployments are being integrated across the organization
d. Organizations are achieving new results with a given domain and advancing the state of the practice
15. What entity in the SGMM is defined as “the stages of an organization’s progress toward achieving its Smart Grid vision in terms of automation, efficiency, reliability, energy and cost savings, integration of alternative energy sources, improved customer interaction, and access to new business opportunities and markets?”
a. Maturity
b. Capability
c. Characteristics
d. Value
16. In the ISCM process, the status of automation security in a facility can be determined by establishing appropriate metrics. The metrics are defined through the following activities, except one, which is not applicable. Which of the following is NOT applicable?
a. Maintaining an understanding of threats and threat activities
b. Conducting security awareness training
c. Collecting, correlating, and analyzing security-related information
d. Active management of risk by organizational officials
17. What technology reduces the effort required to maintain hardware and software systems by eliminating the binding of software to specific hardware platforms through the logical partitioning of physical computing resources into multiple execution environments, including servers, applications, and operating systems?
a. Virtualization
b. Cloud computing
c. Distributed computing
d. Multi-core chips
18. Which of the following statements is FALSE regarding penetration testing of industrial automation and control systems?
a. If not properly conducted, penetration testing can cause damage to automation systems and disrupt operations.
b. Penetration testing tools do not create additional traffic on automation networks and do not affect systems with limited memory capacity.
c. If executed properly, penetration testing can provide important information regarding the security of automation systems.
d. It is useful to use nonintrusive methods when conducting penetration testing.
19. Penetration testing conducted with no prior knowledge of the automation system is known as which of the following?
a. Black box
b. White box
c. Grey box
d. Auto box
20. Which of the following is NOT a component of the reconnaissance phase of penetration testing?
a. Footprinting
b. Scanning
c. Controlling
d. Enumerating
21. Which of the following is NOT one of the maturity levels of the Automation Maturity Model?
a. Local digital control
b. Remote auto control
c. Optimized operations
d. Enabled control
22. What level of the Automation Maturity Model is characterized by full automation and automated closed-loop control around a set point?
a. Local digital control
b. Enhanced operations
c. Remote auto control
d. Optimized operations
References
1 NIST Special Publication 800-137, Information Security Continuous Monitoring (ISCM) for Federal Information Systems and Organizations, September 2011.
2 The Smart Grid Maturity Model, SGMM Model Definition, A Framework for Smart Grid Transformation, Technical Report CMU/SEI-2011-TR-025, Version 1.2, September 2011.
3 Radasky, W. “EMC and the Smart Grid,” Interference Technology 2011, EMC Test and Design Guide, 2011.
4 IEC 61000-2-5 Edition 2, Description and Classification of Electromagnetic Environments, Geneva: International Electrotechnical Commission, May 2011.
5 Introduction to NISTIR 7628, Guidelines for Smart Grid Cybersecurity, The Smart Grid Interoperability Panel Cybersecurity Working Group, September 2010.
6 Gaberdiel, P. “Taking Your SCADA System to the Next Level,” SOURCE, Volume 25, Number 3, CA-NV Section, AWWA, Summer, 2011.