Chapter 4. Smartphones, Tablets, and Other Mobile Devices, Part 2
This chapter covers the following A+ 220-1001 exam objectives:
• 1.6 – Given a scenario, configure basic mobile device network connectivity and application support.
• 1.7 – Given a scenario, use methods to perform mobile device synchronization.
Nice to see you again! This is the last chapter dealing with mobile devices. We’ll be discussing networking and synchronization. Ask yourself: What do users need? They need Wi-Fi, Bluetooth, and e-mail. They need cellular connections for voice calls as well as for data. And let’s not forget the need to synchronize data to computers, automobiles and the cloud. That’s what this chapter is all about. Now that you know, it’s time to begin.
1.6 – Given a scenario, configure basic mobile device network connectivity and application support.
ExamAlert
Objective 1.6 concentrates on the following concepts: wireless technologies, Bluetooth setup, e-mail configuration, radio updates, and VPNs.
In this objective you are expected to know how to set up wireless connections such as Wi-Fi, hotspots, and Bluetooth, and also wired connections such as USB tethering. Be ready to understand configurations for the various types of e-mail including POP3, IMAP, and cloud-based e-mail configurations. Finally, prepare to learn how cellular connections work, and the various updates, identification codes, and technologies used by smartphones’ mobile connections.
These are the basics of network connectivity when it comes to mobile devices, but it’s still a lot to know—and much of it is unknown to the typical end-user. That’s where you, the tech, come in. Support those mobile devices!
Note
For simplicity, most of the time I use the term cellular to refer to smartphone connectivity to a telecommunications provider, meaning 3G, 4G, 5G, and so on.
Enabling Wireless Functions
You will most definitely be called upon to enable and disable various wireless and cellular functionality. In this section we’ll discuss how to connect to Wi-Fi, setup a mobile hotspot, and define airplane mode.
Cellular connections such as 3G, 4G, LTE, 5G, and beyond are commonplace on smartphones. If you purchase a smartphone from a telecommunications provider, then you get cellular access. These are enabled by default, unless you turn on airplane mode. We’ll talk more about cellular technologies later, but for now keep in mind a couple things:
• Cellular connections can be slow when transmitting data. That could be due to the distance from the nearest cell tower, or a general lack of service availability.
• Cellular connections can cost the customer money. That’s why all mobile devices are equipped with an embedded wireless antenna to connect to wireless LANs (WLANs). This Wi-Fi antenna can potentially allow access to 802.11a, b, g, n, and ac networks. The wireless configuration works similar to a wireless connection on a PC, laptop, or tablet. See Chapter 6, “SOHO Networks and Wireless Protocols”, for a detailed description of connecting to wireless networks.
In general, the mobile device must first search for wireless networks before connecting. On a typical mobile device, this is done in Settings > Wi-Fi, or Settings > Network > Wi‑Fi. Figure 4.1 shows a typical Wi-Fi screen is shown in Figure 4.1
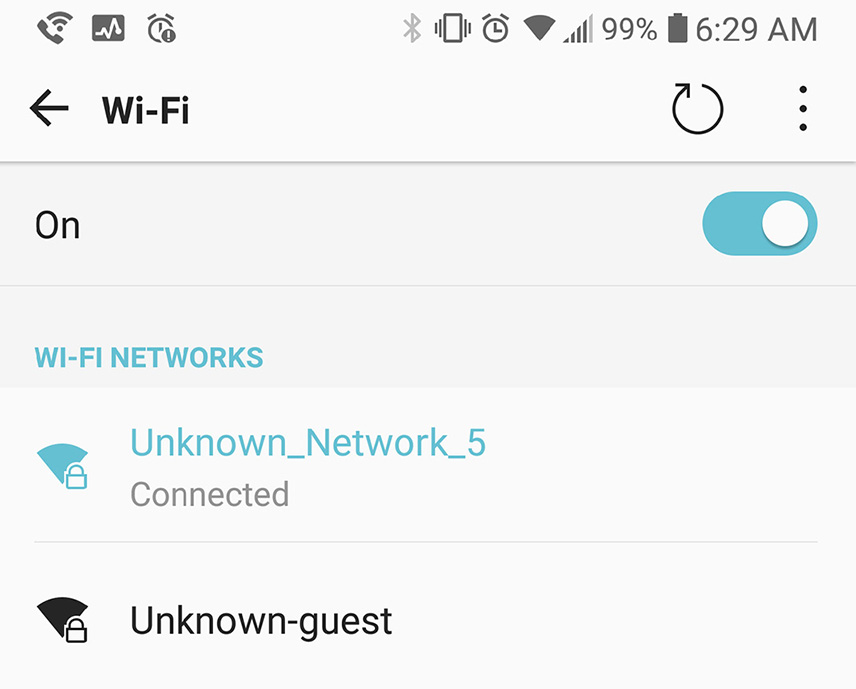
Figure 4.1 Wi-Fi Settings Screen in Android
In the Wi-Fi settings screen, perform the following general steps:
1. Most devices usually scan for wireless networks automatically, or you can tap Add Wi-Fi Network (or similar name) to add one manually.
2. When adding a network manually, enter the SSID of the wireless access point in the Add Wi-Fi Network window.
3. Enter the passcode for the network. If the code is correct, then the wireless adapter in the mobile device gets an IP address, allowing it to communicate with the network. If a wireless network uses WPA2 and the mobile device isn’t compatible, you should search for an update to the operating system to make it WPA2-compliant or consider a newer device!
4. Check for the universal wireless icon at the top of the screen (in the notification bar) to verify connectivity.
ExamAlert
Understand how to connect to a Wi-Fi network in Android and iOS.
If you bring your mobile device into a secure area or on to an airplane, you will most likely be asked to place the device in airplane mode. This is a mode that will disable all wireless connectivity including (but not limited to) cellular, Wi-Fi, and Bluetooth. This can be done by pressing and holding the power button and selecting airplane mode, or by swiping down on the notification bar and accessing the quick settings dropdown.
Once in airplane mode, you should see the airplane icon in the notification bar. However, keep in mind that this is primarily designed to disable cellular access. On many devices, a user can still re-enable Wi-Fi or Bluetooth even when airplane mode is on. Sometimes a user might complain that there is no wireless connectivity. Always check if the device has been placed in to airplane mode and disable it from the same locations mentioned previously.
So, you know how to setup Wi-Fi. But what if you want to share that connection with other computers such as laptops or tablets? That’s where the mobile hotspot comes in. When you configure a mobile hotspot, the mobile device shares its Internet connection with other Wi-Fi capable devices. For example, if a user has a smartphone that can access the Internet through a cellular network, it can be configured to become a portable Wi-Fi hotspot for other mobile devices (or desktops/laptops) that are Wi-Fi capable but have no cellular option. Beware of the hotspot option; most providers have a fairly low consumer bandwidth cap (data transmission limit) for data transferred through the hotspot by default, even if the plan is called “unlimited.”
Enabling hotspots is easy, it is often done in Settings > Network (and possibly in a section called “tethering”). Figure 4.2 shows an example. The first time, you will be asked to supply a password and the wireless protocol to be used, which can be modified later. As of the writing of this book it is recommended to use WPA2, and of course, set a strong password. An example of the configuration screen is also shown in Figure 4.2.
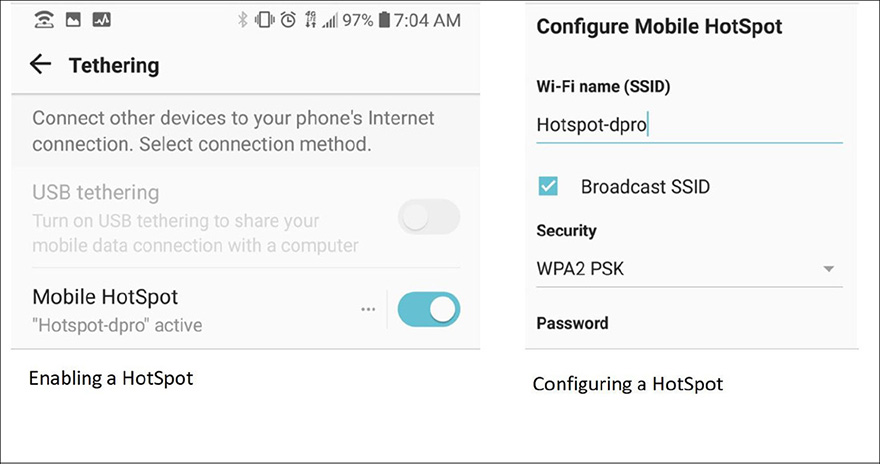
Figure 4.2 Hotspot Configuration in Android
When a hotspot is enabled on a smartphone, Wi-Fi is automatically disabled. So, the smartphone will only be able to connect via the cellular network—but it is designed this way on purpose, expecting to only be used when there is no Wi-Fi connection available. Other Wi-Fi-ready systems (laptops, PCs, tablets, etc…) need only look for, and connect to the Wi-Fi network that was created, for example hotspot-dpro in Figure 4.2. Running a mobile hotspot can also be a great backup option in case the main Internet connection in a small office or home office fails temporarily.
USB Tethering
USB tethering is when a mobile device is connected to a desktop or laptop computer via USB; that desktop or laptop (running Windows or macOS) can then share the phone’s mobile Internet connection. So, USB tethering is the wired equivalent of a mobile hotspot—but it’s designed for just one computer to share the Internet connection. The option for USB tethering is displayed in Figure 4.2—it is grayed out (disabled) until a USB cable is plugged in. As with mobile hotspots, turning this feature on will automatically disable the mobile device’s Wi-Fi connection. That means that Wi-Fi-based services, such as Wi-Fi calling, will be unavailable while USB tethering is activated.
ExamAlert
Remember that a mobile hotspot shares a smartphone’s Internet connection wirelessly, and USB tethering shares the connection in a wired fashion. In both cases, Wi-Fi and Wi-Fi related services will be shut down while the hotspot or tether is active. Normally, a hotspot and USB tethering cannot run at the same time.
Bluetooth
Bluetooth is a wireless standard for transmitting data over short distances. It is commonly implemented in the form of a headset or printer connection. It is also used to create a wireless personal area network (WPAN) consisting of multiple Bluetooth-enabled mobile devices.
To connect a Bluetooth device to a mobile device, Bluetooth first needs to be enabled. Then the Bluetooth device needs to be synchronized to the mobile device. This is known as pairing or linking. It sometimes requires a pin code. Once synchronized, the device should automatically connect and should function at that point. Finally, the Bluetooth connection should be tested. Following are the steps involved in connecting a Bluetooth device to a typical mobile device. Before you begin, make sure the Bluetooth device is charged (if applicable). The typical procedure for making a Bluetooth connection is as follows:
1. Turn on Bluetooth in the Settings of the mobile device.
2. Prepare the device by turning it on and pressing (and sometimes holding) the Bluetooth button.
3. Scan for devices on the mobile device.
4. Pair to the desired device.
5. Enter a pin code if necessary. Some devices come with a default pin of 0000.
ExamAlert
For the exam, remember this procedure for Bluetooth connectivity.
1. Turn on Bluetooth in the Settings of the mobile device.
2. Prepare the device by turning it on and pressing (and sometimes holding) the Bluetooth button.
3. Scan for devices on the mobile device.
4. Pair to the desired device.
5. Enter a pin code if necessary. Some devices come with a default pin of 0000.
When finished, the screen will look similar to Figure 4.3. Note the Bluetooth icon at the top of the screen. This icon indicates whether Bluetooth is running on the device. It will remain there even after you disconnect the Bluetooth device, but in a grayed out state. To disconnect or reconnect the Bluetooth device, simply tap the device on the screen. It will remain paired but nonfunctional until a connection is made again. (Typically, devices are listed in bold if they are connected.) You can also unpair and/or forget the device in the settings for that device. Unpairing removes the link between the smartphone and the Bluetooth device, but the mobile device will remember the Bluetooth device. “Forgetting” removes the connection altogether.
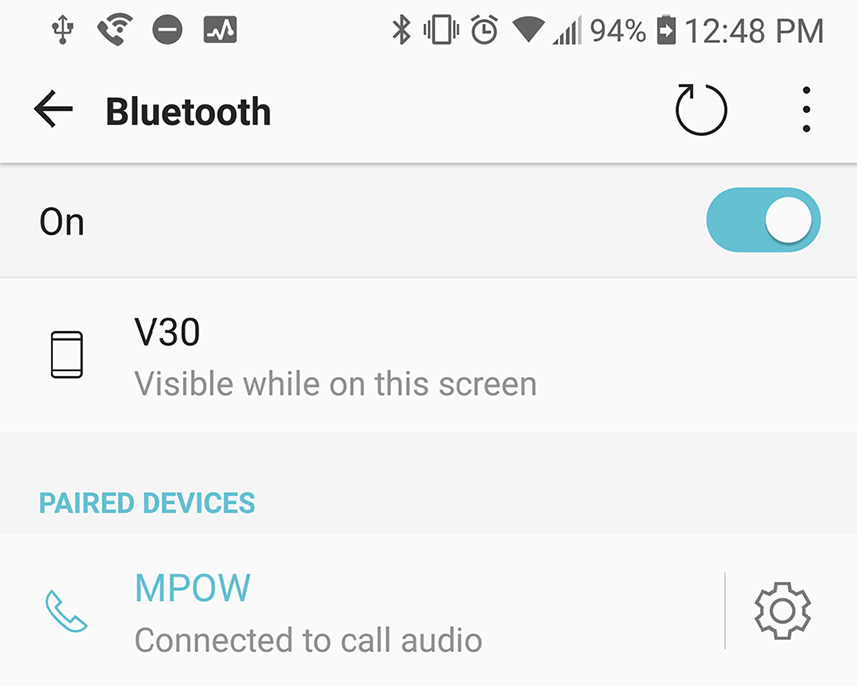
Figure 4.3 Bluetooth Paired Devices Screen in Android
Bluetooth devices can be connected to only one mobile device at a time. If you need to switch the Bluetooth device from one mobile device to another, be sure to unpair or disconnect it, or going further, “forget” it from the current connection before making a new one.
ExamAlert
Know how to configure Bluetooth devices in Android and iOS.
Note
Troubleshooting is just as important as configuration. We’ll discuss Wi-Fi and Bluetooth troubleshooting in Chapter 20, “Troubleshooting Video Issues and Mobile Devices” and Chapter 22, “Troubleshooting Wired and Wireless Network Problems”.
E-mail Configuration
Although there are many other types of communication available to mobile users, e-mail still accounts for an important percentage. You should know how to configure a mobile device for web-based e-mail services such as Gmail, Yahoo!, and so on. You should also know how to configure POP3, IMAP, and connections to Microsoft Exchange Servers.
Integrated Commercial Provider E-mail Configuration
Mobile devices can access web-based e-mail through a browser, but this is not necessary nowadays due to the “app”—most commercial providers offer integrated e-mail configuration for Android and iOS. For example, most Android-based devices come with a Gmail application built in, allowing a user to access Gmail directly without having to use the browser. Devices also might have a proprietary e-mail application. Apple iOS devices allow connectivity to Gmail, Yahoo!, and a host of other e-mail providers as well. Apple users might also connect to the iCloud for mail features. Users of other devices might use Microsoft’s Outlook online or for more users and for collaboration a company might opt for Exchange online. As you can see, there are a lot of options when it comes to mail services for mobile devices.
Connecting to these services is simple and works in a fashion that is similar to working on a desktop or laptop computer. Choose the type of provider you use, enter a username (the e-mail address) and password (on Apple devices, an Apple ID is also required), and the user will have access. In more advanced cases a user may have to select the protocol and ports to be used. That’s where you as the admin come in—we’ll discuss those in a little bit.
When troubleshooting user issues with e-mail, make sure that the username and password are typed correctly. Using onscreen keyboards often leads to mis-typed passwords. Also make sure that the mobile device is currently connected to the Internet.
Corporate and ISP E-mail Configuration
When you need to connect a mobile device to a specific organization’s e-mail system, it gets a little more complicated. You need to know the server that you want to connect to, the port you need to use, and whether security is employed. Look at the following e-mail configuration information and Figure 4.4 for an example.
• Incoming server name: secure.dpro42.com
• POP3 Port (SSL/TLS): 995
• Outgoing server name: secure.dpro42.com
• SMTP Port (SSL/TLS): 465
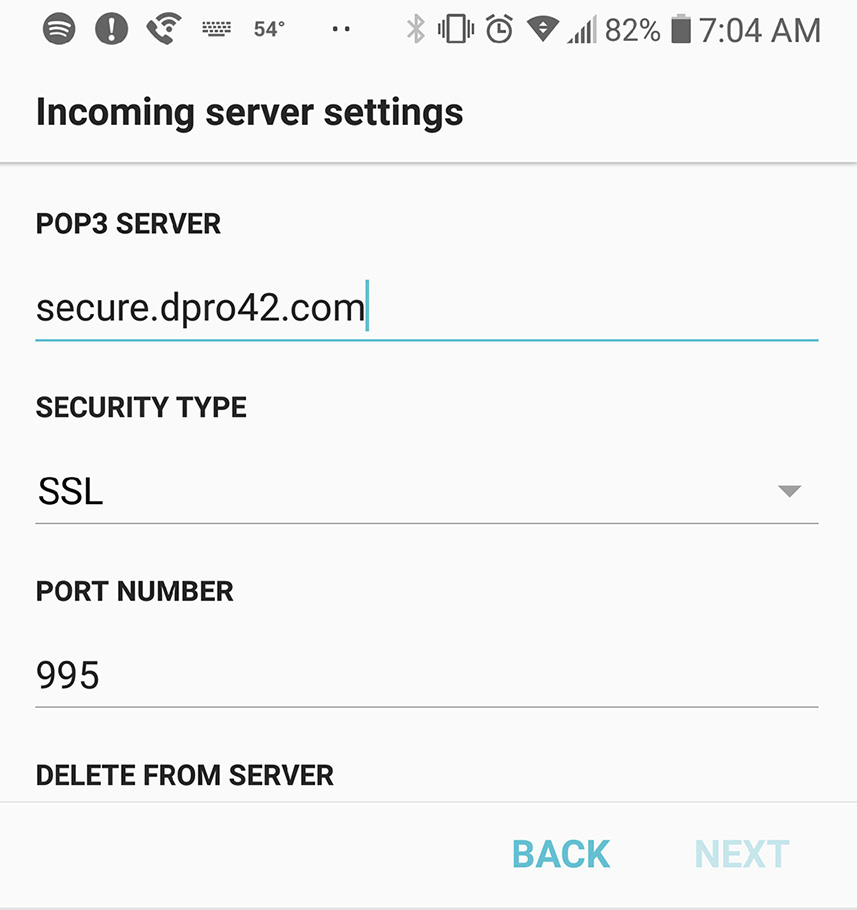
Figure 4.4 E-mail Server Settings Screen in Android
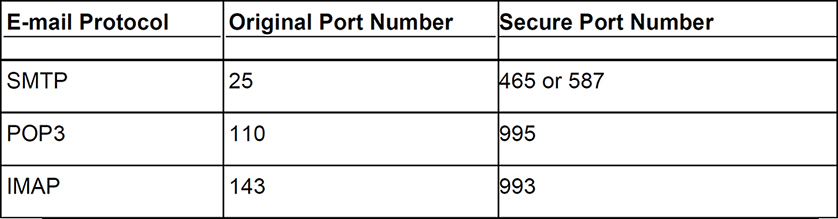
The figure shows a manual configuration of an e-mail client in Android. At this stage, the e-mail client is asking for the incoming server, meaning the one we use for receiving mail. It just so happens that the same server takes care of incoming mail and outgoing mail: secure.dpro42.com, but sometimes it could be two different servers. So, we added the name of the server into the POP3 Server field. Then we specified the security type. In this case we selected Secure Sockets Layer (SSL) instead of “no security” which is important. Most of the time we want to have encrypted e-mail sessions to our e-mail server so as to avoid eavesdropping and tampering. This could be SSL or Transport Layer Security (TLS) depending on the server configuration. Then we select the port, which according to our previous documentation, is 995. That is the default secure port for POP3 e-mail connections that make use of SSL/TLS. However, this can vary depending on what protocol you are using for e-mail, and what type of security you implement. As a technician configuring the client e-mail, you have to go by the documentation provided by the network administrator. As an admin, it’s generally a good idea to go with the default secure port numbers, but in reality you can choose which port to use (within reason), and as long as the client configures that port to connect, it should be successful. See Table 4.1 for a list of original and secure ports used by the various e-mail protocols.
Table 4.1 Example E-mail Configuration
ExamAlert
Know the e-mail protocols and default ports like the back of your hand!
In Table 4.1, I say “original” port number because these are what we used for many years until encrypted e-mail sessions became necessary. The secure port numbers are defaults, but it can vary. This will depend on whether you have to select SSL or TLS, or if another secure technology is used, or if the admin simply decided to go with a different port number. Here’s the thing: most ports can work in a secure fashion—if configured properly—, but it’s the most common defaults in Table 4.1 that you should know for the exam. These are what e-mail server programs and client applications will typically default to.
Note
Another protocol you might implement when setting up secure e-mail is S/MIME (Secure/Multipurpose Internet Mail Extensions). This is used for authentication and message integrity and is built-in to some e-mail clients.
Cellular Radio Technologies
Hey, listen! Without a properly working radio in your smartphone, you won’t hear anything. This section is designed to teach you the basics about cellular voice calls and data transmissions. You see, most people can’t live without their radios—and ultimately, that’s what the phone is.
Originally, cellular phones used the Global System for Mobile Communications (GSM) to make voice calls and GSM or the general packet radio service (GPRS) to send data at 2G speeds through the cellular network. Extensions of these standards—the Universal Mobile Telecommunications System (UMTS) and Enhanced Data rates for GSM Evolution (EDGE)—are used to attain 3G speeds. 4G and 4G LTE speeds can be attained only when a mobile device complies with the International Mobile Telecommunications Advanced (IMT-Advanced) requirements, has a 4G antenna, and is in range of a 4G transmitter. Devices manufactured during the writing of this book most commonly use 4G and LTE (which builds on 4G by using an updated radio interface/antenna in the mobile device and by utilizing core network infrastructure improvements). However, the fifth generation of cellular (5G) is also available. This is known as the ITU IMT-2020 standard, and has data transfer rates of up to 20 Gbps.
Most devices cannot shut off the cellular antenna by itself (unless you shut down the device itself). However, every device manufactured now is required to have an “airplane mode,” which turns off any wireless antenna in the device, including disabling the connection to the cellular network, and disabling Wi-Fi, and Bluetooth. This can be accomplished by either going to Settings > Airplane Mode or by holding the Power button down and selecting Airplane Mode. You will find that some airlines don’t consider this to be acceptable and for security purposes will still ask you to turn off your device altogether, either for the duration of the flight or at least during takeoff and landing. Some devices can also limit or disable cellular data usage—often known as “mobile data”.
ExamAlert
Know what airplane mode is and how to configure it on Android and Apple devices.
Let’s get a little more into it and briefly discuss some additional mobile technology and acronyms, such as PRL updates, baseband updates, radio firmware, IMEI versus IMSI and VPN.
PRL stands for preferred roaming list. It is used by cellular providers (such as Sprint, Verizon, and U.S. Cellular) that utilize code division multiple access (CDMA) technology instead of GSM. It’s a database that contains information about the provider’s radio bands, sub-bands, and service provider IDs. Ultimately, it allows a phone to connect to the correct tower; without the database, the phone might not be able to roam outside the provider’s network. When necessary, PRL information is sent as an update over the air. However, you can also update it manually by dialing a number that is unique to each provider. You can find out the PRL version number you are using within the About section on some phones.
When a phone uses GSM, that technology and its radio functions are controlled by a chip and software package that is collectively referred to as “baseband.” Baseband updates are necessary to communicate properly with GSM cell towers. If an older phone won’t update properly, it must be taken to the provider for a wired, manual update. Baseband is also referred to as radio firmware in that it controls network connectivity for GSM. Other wireless antennas such as Wi-Fi and GPS are controlled by the operating system’s drivers.
Warning
Do not attempt a radio firmware (baseband) update if your phone does not require it. A faulty update can easily make the phone inoperable.
Note
A less commonly used acronym on the CompTIA A+ objectives is PRI, which stands for product release instructions. This is an over-the-air informational update defining what to expect from an operating system update, and in the past for mobile devices it may have included settings and codes.
Now onto IMEI and IMSI—these are both identification technologies. IMEI stands for International Mobile Station Equipment Identity and it identifies phones used on 3GPP-based networks (GSM, UMTS, and LTE). You can find this ID number in Settings > About > Status (or something similar), or on older phones it is printed inside the phone either on or near the battery. It is used only to identify the device. However, International Mobile Subscriber Identity (IMSI) is used to identify the user. For GSM, UMTS, and LTE networks, this ID is loaded into the subscriber identity module (SIM) card. For CDMA networks, the ID is loaded directly into the phone or to a removable user identity module (R-UIM), which is similar to a SIM card.
ExamAlert
Know that the IMEI ID identifies the device and the IMSI ID identifies the user of the device.
Today’s mobile devices can also use virtual private networking (VPN) technology to make secure connections—tunneling though the provider’s radio network. The VPN data is also updated frequently as updates to mobile operating systems are released, as synchronization:cellular radio technologies GSM well as for security purposes. For more information about VPNs as they relate to computers and networks in general, see Chapter 7, “Networked Hosts and Network Configuration.”
You can find the versions of most of these technologies (and the types of radio technology used) within the About (or About device). Take a look at your own mobile device’s settings; for example, the radio technologies you are connecting to, the baseband version, and the IMEI.
Note
Sometimes, finding the information you are looking for can be a bit of a chore; the level of difficulty varies according to the device and the version of OS installed to it. Plus, the various IDs, signal levels, types of technologies used, and so on can be dispersed among different areas of the phone. Consider using a cell tower analyzer, radio signal analyzer, or network signal information app to see this data in a more visual and centralized manner.
All of these radio network technologies can be affected by a mobile phone update, such as a version update. To prevent network connectivity issues, consider waiting until a new mobile OS version has been thoroughly tested before you update your phone.
Cram Quiz
Answer these questions. The answers follow the last question. If you cannot answer these questions correctly, consider reading this section again until you can.
1. Which of the following connections require a username, password, and SMTP server? (Select the two best answers.)
![]() A. Bluetooth connection
A. Bluetooth connection
![]() B. Wi-Fi connection
B. Wi-Fi connection
![]() C. POP3 connection
C. POP3 connection
![]() D. Exchange connection
D. Exchange connection
![]() E. IMAP connection
E. IMAP connection
2. When manually configuring a Wi-Fi connection, which step occurs after successfully entering the SSID?
![]() A. Select POP3.
A. Select POP3.
![]() B. Check whether the device is within range of the WAP.
B. Check whether the device is within range of the WAP.
![]() C. Enter a passcode for the network.
C. Enter a passcode for the network.
![]() D. Scan for networks.
D. Scan for networks.
3. Which of the following allows other mobile devices to wirelessly share your mobile device’s Internet connection?
![]() A. NFC
A. NFC
![]() B. Airplane mode
B. Airplane mode
![]() C. IMAP
C. IMAP
![]() D. Mobile hotspot
D. Mobile hotspot
4. Which of the following identifies the user of the device?
![]() A. IMSI ID
A. IMSI ID
![]() B. IMEI ID
B. IMEI ID
![]() C. S/MIME
C. S/MIME
![]() D. VPN
D. VPN
Cram Quiz Answers
1. C and E. POP3 and IMAP e-mail connections require an incoming mail server (either POP3 or IMAP) and an outgoing mail server (SMTP). Bluetooth and Wi-Fi connections do not require a username or SMTP server. Bluetooth might require a PIN, and Wi-Fi will almost always require a passcode. Exchange connections require a username and password, but no SMTP server. The Exchange server acts as the incoming and outgoing mail server.
2. C. After you enter the SSID (if it’s correct) you would enter the passcode for the network. POP3 has to do with configuring an e-mail account. If you have already entered the SSID, then you should be within range of the wireless access point (WAP). Scanning for networks is the first thing you do when setting up a Wi-Fi connection.
3. D. Mobile hotspot technology (sometimes referred to as Wi-Fi tethering) allows a mobile device to share its Internet connection with other Wi-Fi capable devices. Another possibility would be USB tethering, but that is done in a wired fashion. NFC stands for near field communication—a technology that allows two mobile devices to send information to each other when they are in close proximity. Airplane mode will disable all wireless connectivity including (but not limited to) cellular, Wi-Fi, and Bluetooth. IMAP is another e-mail protocol similar to POP3.
4. A. International Mobile Subscriber Identity (IMSI) or IMSI ID is used to identify the user of the device. IMEI stands for International Mobile Station Equipment Identity and identifies the phone used. In other words, the IMEI ID identifies the device itself. S/MIME (Secure/Multipurpose Internet Mail Extensions) is used for authentication and message integrity and is built-in to some e-mail clients. In other words, it is used to encrypt email. Virtual private networking (VPN) technology is used to make secure connections—tunneling though the provider’s radio network.
1.7 – Given a scenario, use methods to perform mobile device synchronization.
ExamAlert
Objective 1.7 focuses on the following concepts: synchronization methods, types of data to synchronize, mutual authentication with SSO, software requirements for syncing apps, and sync connection types.
In this objective you learn how to synchronize mobile devices to other computers either on the local area network, on the Internet, or located in a car, truck or vehicle. You should be well-versed with synchronizing many data types including contacts, e-mail, calendars; even passwords if the user desires it. It’s also important to know how to authenticate to networks using the single-sign-on (SSO) method but also understand what SSO is and how it operates.
Synchronization Methods
A person might want to synchronize a mobile device’s data somewhere else so that he or she can have availability to that data from anywhere. It also offers peace of mind in the case that the mobile device is lost or stolen—that data will be available on the other system when a new mobile device is procured. And of course, even though mobile devices today can store a lot of data, there’s always the need for more. External systems allow for a much greater amount of storage, and redundancy of data.
A person can choose to synchronize data to an individual computer that is physically nearby, or an automobile, or to the cloud which is the most common.
Synchronizing to the Cloud
For simplicity, we can refer to the cloud as any computer that you synchronize to on the Internet. Generally, this means using some type of service. You might synchronize your mobile device’s data to Google Drive, Microsoft OneDrive, iCloud, Dropbox, or one of several others. Making this happen entails creating an account, installing the appropriate app on the mobile device (if not already there), and specifying what folders, files, and other data you would like to synchronize. The first time, the application will copy the data over to the cloud recipient. Subsequent synchronizations will copy new files and append changed files.
When it comes to popular services such as Gmail, you might question whether a person is really “synchronizing” anymore. You are, it’s just that the data is all stored on their servers and you are simply accessing it from a mobile device, or PC, or laptop. A person who signs up for a Gmail account allows Google to automatically synchronize mail, contacts, and the calendar so that the information can be viewed on the mobile device or on the PC (when connected to the Google website). However, because the data is stored on a Google server, security should be a concern. If you choose to use a service such as this, you should use an extremely strong password, change it every month or so, and use a secure browser when connecting to Gmail from a desktop computer. On the mobile device side, make sure the Gmail app is updated often to patch any security vulnerabilities. The same concepts hold true for other similar services. Utilizing the cloud presents many configuration and security concerns which we will discuss more in the networking chapters of this book.
Note
Keep in mind that you might also backup your data, but this is different than synchronization. For example, you might backup an Android-based device’s apps, call history, contacts, device settings, SMS text messages, and other items that are normally stored locally. You could back up this data to a server on the cloud owned by the manufacturer of the mobile device, or you could use a separate service such as Google Drive. Either way, this is done separately from synchronization.
Synchronizing to the Desktop
Today, synchronizing to the desktop is not nearly as common as syncing to the cloud. But it might be necessary, or desired, by some users. When you connect mobile devices to a Windows PC via a USB connection, they are typically seen automatically and are represented as a device in File Explorer under This PC. On the mobile device you might have to change the USB options from Charging to File transfer or another similar option in order to see the device in Windows. At this point, you can copy files back and forth between the mobile device and the PC manually or rely on automatic synchronization software from the manufacturer of the mobile device or from a third-party. This software can be configured to synchronize the folders of your choice automatically when the mobile device is connected.
If you use the mobile device’s built-in contacts and e-mail programs, the information within those programs can be transferred to the PC’s corresponding programs. For example, the calendar and contacts can be synchronized with Microsoft Outlook.
There are third-party tools available when a user wants to synchronize an Android device with a PC or Mac via Bluetooth or Wi-Fi. On another note, Google Sync (using Exchange ActiveSync) can be used to synchronize e-mail, contacts, and calendars between a variety of devices (iOS-based devices, Windows devices, etc…) with an Exchange Server. Android-based devices use G Suite and don’t require Google Sync to make connections to Exchange Servers.
ExamAlert
Know the various ways to synchronize data between an Android and a PC.
When you plug in an iPad/iPhone to a PC via USB, Windows should automatically recognize it and install the driver for it. At that point, you can move files between the PC and the device. The device shows up in File Explorer as Apple iPad or Apple iPhone directly inside of the This PC/Computer location of File Explorer.
To synchronize data such as contacts, calendars, and so on, PC users need to use iTunes for Windows. From iTunes, a user would select Sync Contacts or Sync Calendars, for example. This information can be synchronized to Microsoft Outlook and Windows Contacts. Mac users benefit from the simplicity of synchronization across all Apple products. They can use iTunes, or they can use the iCloud to store, back up, and synchronize information across all Apple devices. This can be done by USB or via Wi-Fi (when the various Apple devices are on the same wireless network). Calendar items can also be synced from the Apple-based device (such as an iPad) by going to Settings > Mail, Contacts, Calendars. Then scroll down and select Sync. iCloud can also be downloaded for Windows.
Windows 10 devices can be synchronized together with the Sync Center (Control Panel > All Control Panel Items > Syn Center). This allows you to choose individual synchronize settings such as Theme, Passwords, Language preferences, Ease of Access, and other Windows settings, but a user would have to sign in with a Microsoft account in order to synchronize.
ExamAlert
Know the various ways to synchronize data between mobile devices and PCs or Macs.
Synchronizing to the Automobile
It had to happen—computers in cars. Not only that, but people want to harness the power of their smartphone in conjunction with their automobile’s computer and display. It’s easy with tools such as Android Auto and Apple CarPlay. These apps can be used independently on the mobile device or can be synchronized to an automobile’s computer that has the proper firmware/software installed. Then, the user can make use of the automobile’s larger screen for easier accessibility, better viewing, and increased safety. Generally, these platforms are supported on higher-level trims of a vehicle. For integration of these platforms, the mobile device usually has to be plugged in via USB, and a high-quality cable should be used to avoid interruptions.
In reality, this isn’t as much “synchronizing” as it is screen sharing. The larger screen in the automobile is used to display, and control, the common apps you might need: phone, maps, music player, and so on—Apple CarPlay and Android Auto will limit the amount and type of apps you can use in the automobile for safety reasons.
Take a look at Figure 4.5 for an example of Android Auto running on a smartphone connected to an automobile via USB. Of course, most smartphones can multitask, so you can potentially use both screens at the same time with different apps running on each—of course, only when parked!
Figure 4.5 Example of Android Auto
If a vehicle does not support Android Auto or Apple CarPlay, it might support Bluetooth (BT). If that is the case, then a smartphone or tablet can be synchronized to the vehicle via BT by pairing the automobile to the device in the same manner described earlier in the chapter. Then the user can operate voice calls and texting hands-free. If the vehicle is not equipped with any computer or BT integration, then a replacement head unit (stereo) could be purchased allowing BT and USB integration as well as Apple CarPlay or Android Auto.
Types of Data to Synchronize and Authentication
There are all kinds of data types that you might be interested in synchronizing. For the average worker, the three that usually come to mind are: e-mail, contacts, and calendar. The typical employee needs to be able to access these quickly and from various locations. That’s why services such as Google, Yahoo! and so on are so enticing—they allow integration of many services under one roof with one login. This is an example of single sign-on (SSO). SSO is when a user is authenticated to multiple services simply by logging in with a single username and password. The services might be accessed with separate apps, but it is all linked together. This suite of apps utilizes mutual authentication in the form of SSO, which is a type of federated identity management or FIM.
However, there is a lot more to synchronize when it comes to mobile devices, some of which a user might not want synced up. For example, location data, social media data, recorded voice data, and other information that can tell a lot about the user—data that the user might not want to share. These things are often enabled by default in most of today’s services. To disable them, a user has to dig through the settings of the mobile device, and in some cases has to log through a web browser to do so.
Then there’s pictures, videos, music, and plain old documents in general. Most services such as the ones that Google and Apple provide will have a location to store files such as these (for example Google Drive) and it is often associated with the SSO account. Or, a user might decide that for security purposes, the data should be stored locally at home or at a small office: enter the NAS—network attached storage. These boxes can be setup to synchronize this data from a mobile device automatically. The benefit is that the data is stored at the home or office and behind a firewall, not on the cloud, which might be desired in some cases. Or, the user might decide to sync up this data to a desktop system. In that case, the desktop computer needs to meet several requirements including: OS version, hardware specs, drivers, and perhaps need a special program installed to communicate with the mobile device.
It seems like anything can be synchronized: website bookmarks, e-books, you name it. Even passwords. Every web browser out there has the ability to store and possibly synchronize passwords. There are also third-party programs that act as password vaults that you can access anywhere because they are stored on the cloud. However, most organizations frown at this practice because of the security implications. Generally, if a password vault is to be used, a locally saved one will be the most secure. But even locally stored vaults (such as KeePass) can be set up on the Internet. If a password vault has to be used for synchronization purposes, and it has to be on the cloud, then some security procedures should be implemented. For example, use a very strong master password to open the vault. Store the vault in an encrypted fashion on a secure server (which is chapter unto itself). Update any password storing software often. Limit the people who have access to the master password, and add that information to any offboarding scheme. Audit the vault so that you will have a log of who accessed the vault, what they did, and when. Remember the W’s!
ExamAlert
Implement strong master passwords for any password vaults.
Cram Quiz
Answer these questions. The answers follow the last question. If you cannot answer these questions correctly, consider reading this section again until you can.
1. Which of the following is the most common connection method when synchronizing data from a mobile device to a PC?
![]() A. Wi-Fi
A. Wi-Fi
![]() B. Bluetooth
B. Bluetooth
![]() C. USB
C. USB
![]() D. Lightning
D. Lightning
2. Which of the following is used to synchronize contacts from an iPad to a PC? (Select the best answer.)
![]() A. Gmail
A. Gmail
![]() B. Google Play
B. Google Play
![]() C. iTunes
C. iTunes
![]() D. Sync Center
D. Sync Center
3. What is it known as when a user connects to several services using several apps but with only one username and password?
![]() A. Android Auto
A. Android Auto
![]() B. SSO
B. SSO
![]() C. iTunes
C. iTunes
![]() D. BT
D. BT
![]() E. Exchange ActiveSync
E. Exchange ActiveSync
Cram Quiz Answers
220-1001 Answers
1. C. USB is the most common connection method used when synchronizing data from a mobile device to a PC. Though Wi-Fi and Bluetooth are also possible, they are less common. Lightning is the port found on some of Apple’s mobile devices, but still ends in USB when connecting to a PC or Mac.
2. C. PC users need iTunes to synchronize contacts and other data from an iPad to a PC. While Gmail can work to synchronize contacts, it is all based on web storage; nothing is actually stored on the iPad. Google Play is a place to get applications and other items for Android. Sync Center is a Control Panel utility that enables synchronization across Windows 10 devices.
3. B. SSO (single sign-on) is a type of authentication where a user logs in once but is granted access to multiple services. Android Auto is a screen sharing/synchronizing app used on Android-based mobile devices to communicate with a properly equipped automobile. iTunes is a music/media program that can be used to sync up a mobile device to a PC or Apple device. BT is short for Bluetooth. Exchange ActiveSync is a client-based protocol that allows a user to sync a mobile device with an Exchange Server mailbox.